Safety Issues for Online Kids and the rest




- Slides: 29

Safety Issues for Online Kids (and the rest of the family) navigators. com/parentguide. html Russ Haynal Internet Instructor, Speaker, and Paradigm Shaker Phone : 703 -729 -1757 21015 Forest Highlands Ct russweb@navigators. com Ashburn, VA 20147 (put “training” in email subject) http: //navigators. com Rev. 09/2006

Online resources Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • There are many websites ready to assist you • Some sites are for adults while other sites are geared towards the kids. Page 2

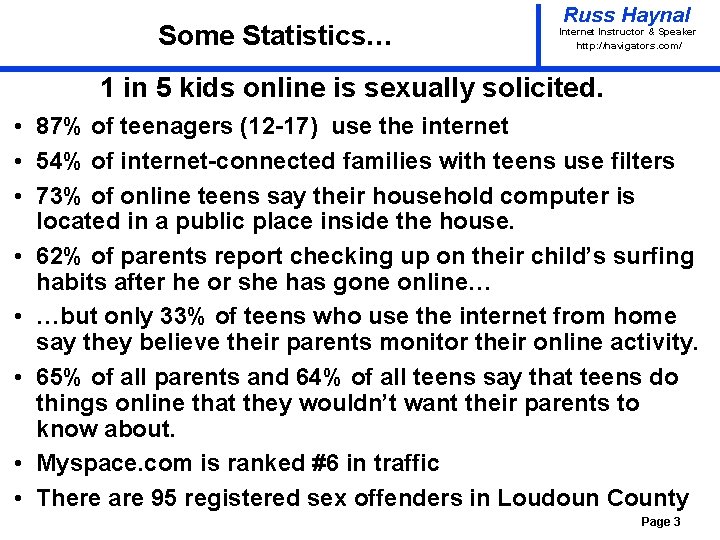
Some Statistics… Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ 1 in 5 kids online is sexually solicited. • 87% of teenagers (12 -17) use the internet • 54% of internet-connected families with teens use filters • 73% of online teens say their household computer is located in a public place inside the house. • 62% of parents report checking up on their child’s surfing habits after he or she has gone online… • …but only 33% of teens who use the internet from home say they believe their parents monitor their online activity. • 65% of all parents and 64% of all teens say that teens do things online that they wouldn’t want their parents to know about. • Myspace. com is ranked #6 in traffic • There are 95 registered sex offenders in Loudoun County Page 3

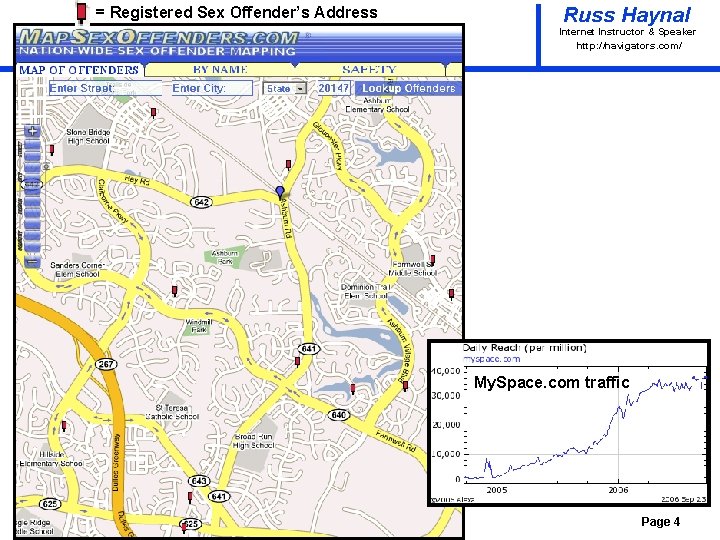
= Registered Sex Offender’s Address Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ My. Space. com traffic Page 4

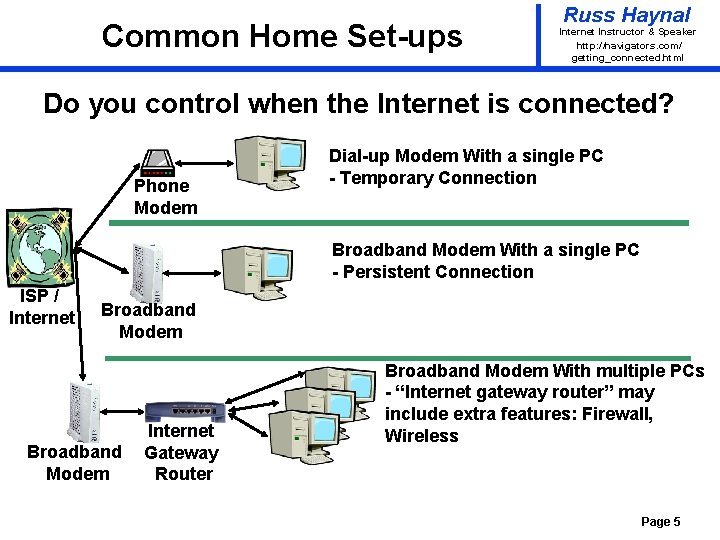
Common Home Set-ups Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ getting_connected. html Do you control when the Internet is connected? Phone Modem Dial-up Modem With a single PC - Temporary Connection Broadband Modem With a single PC - Persistent Connection ISP / Internet Broadband Modem Internet Gateway Router Broadband Modem With multiple PCs - “Internet gateway router” may include extra features: Firewall, Wireless Page 5

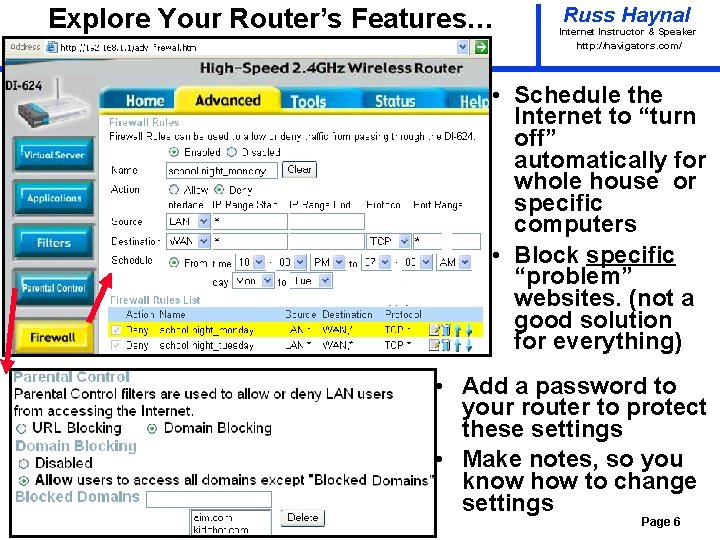
Explore Your Router’s Features… Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Schedule the Internet to “turn off” automatically for whole house or specific computers • Block specific “problem” websites. (not a good solution for everything) • Add a password to your router to protect these settings • Make notes, so you know how to change settings Page 6

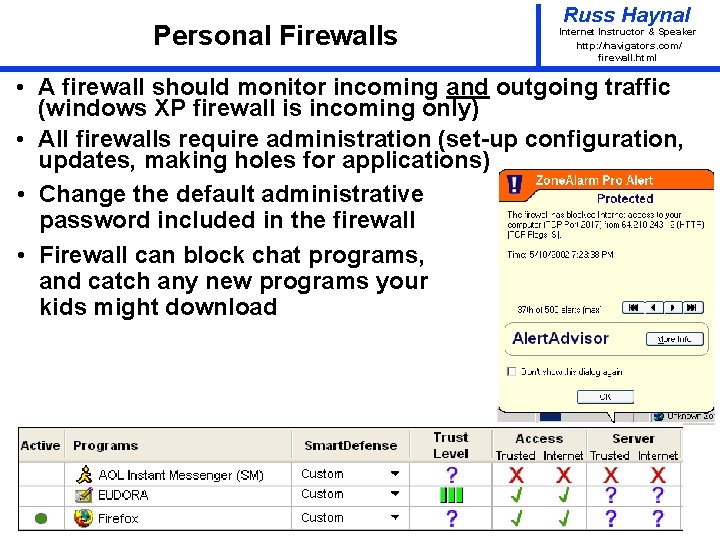
Personal Firewalls Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ firewall. html • A firewall should monitor incoming and outgoing traffic (windows XP firewall is incoming only) • All firewalls require administration (set-up configuration, updates, making holes for applications) • Change the default administrative password included in the firewall • Firewall can block chat programs, and catch any new programs your kids might download Page 7

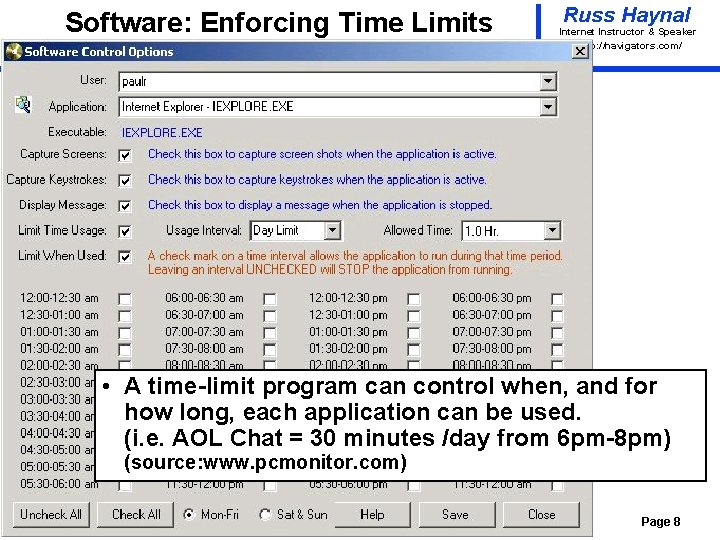
Software: Enforcing Time Limits Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • A time-limit program can control when, and for how long, each application can be used. (i. e. AOL Chat = 30 minutes /day from 6 pm-8 pm) (source: www. pcmonitor. com) Page 8

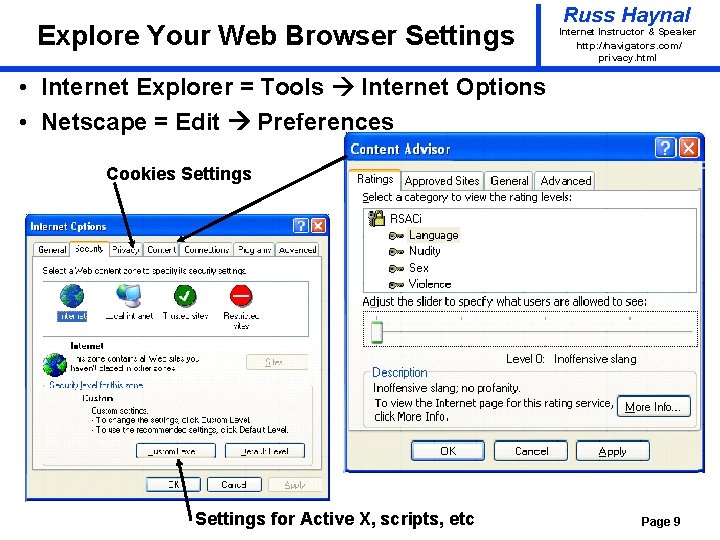
Explore Your Web Browser Settings Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ privacy. html • Internet Explorer = Tools Internet Options • Netscape = Edit Preferences Cookies Settings for Active X, scripts, etc Page 9

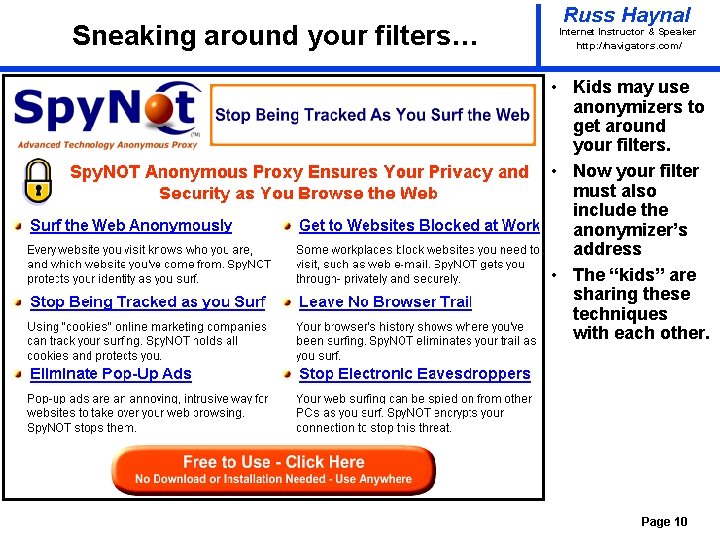
Sneaking around your filters… Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Kids may use anonymizers to get around your filters. • Now your filter must also include the anonymizer’s address • The “kids” are sharing these techniques with each other. Page 10

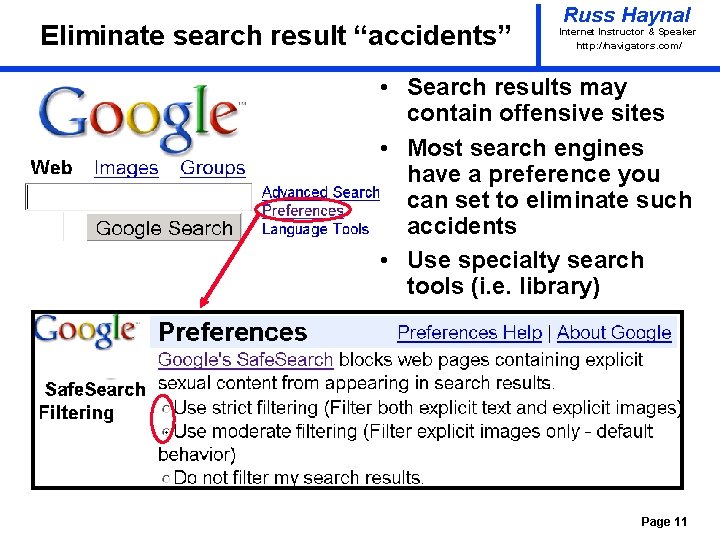
Eliminate search result “accidents” Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Search results may contain offensive sites • Most search engines have a preference you can set to eliminate such accidents • Use specialty search tools (i. e. library) Page 11

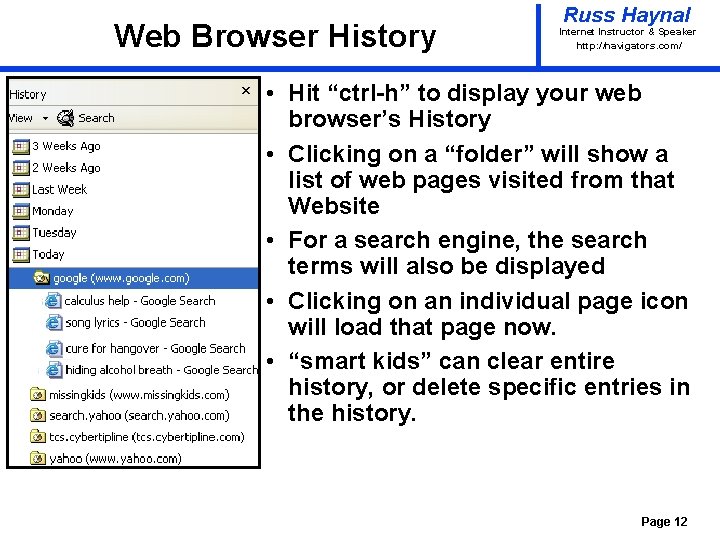
Web Browser History Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Hit “ctrl-h” to display your web browser’s History • Clicking on a “folder” will show a list of web pages visited from that Website • For a search engine, the search terms will also be displayed • Clicking on an individual page icon will load that page now. • “smart kids” can clear entire history, or delete specific entries in the history. Page 12

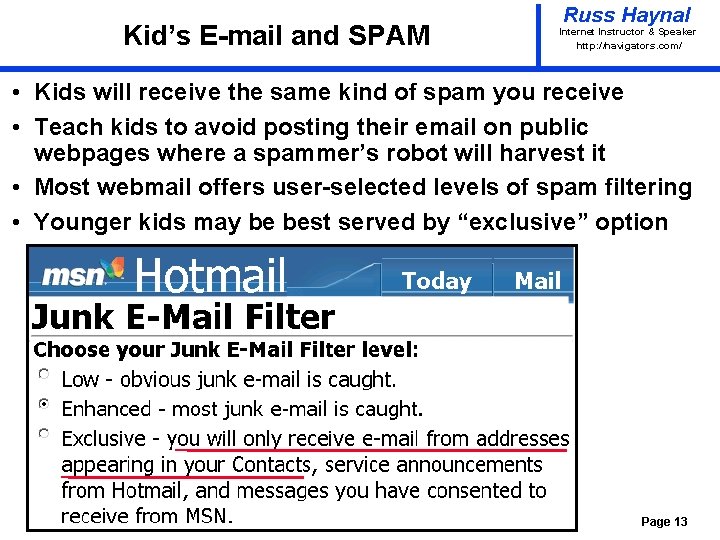
Kid’s E-mail and SPAM Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Kids will receive the same kind of spam you receive • Teach kids to avoid posting their email on public webpages where a spammer’s robot will harvest it • Most webmail offers user-selected levels of spam filtering • Younger kids may be best served by “exclusive” option Page 13

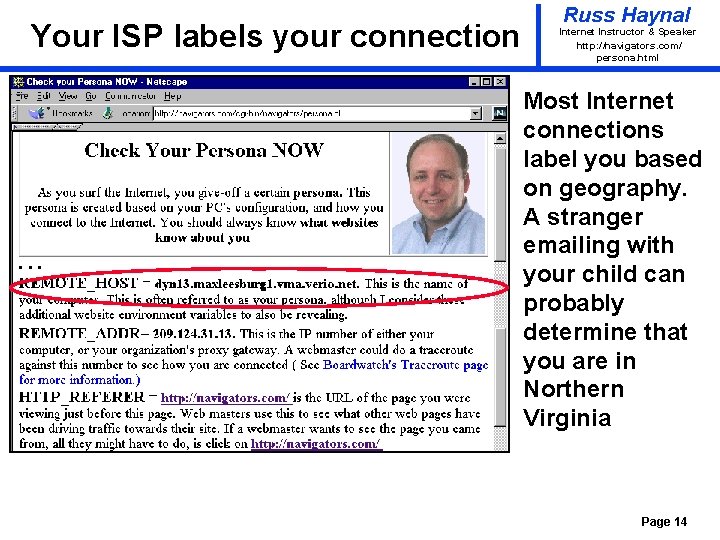
Your ISP labels your connection Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ persona. html Most Internet connections label you based on geography. A stranger emailing with your child can probably determine that you are in Northern Virginia Page 14

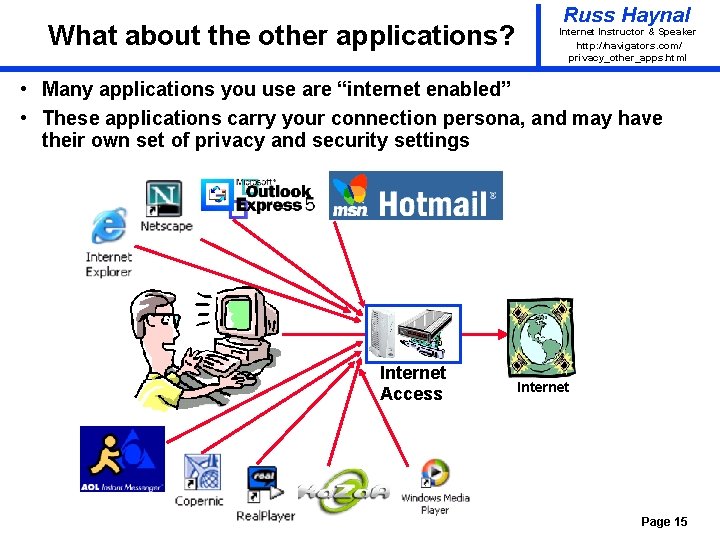
What about the other applications? Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ privacy_other_apps. html • Many applications you use are “internet enabled” • These applications carry your connection persona, and may have their own set of privacy and security settings Internet Access Internet Page 15

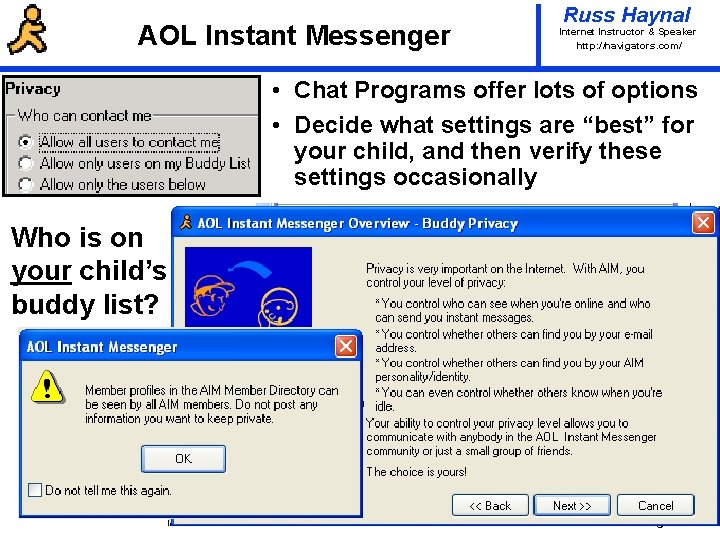
AOL Instant Messenger Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Chat Programs offer lots of options • Decide what settings are “best” for your child, and then verify these settings occasionally Who is on your child’s buddy list? Page 16

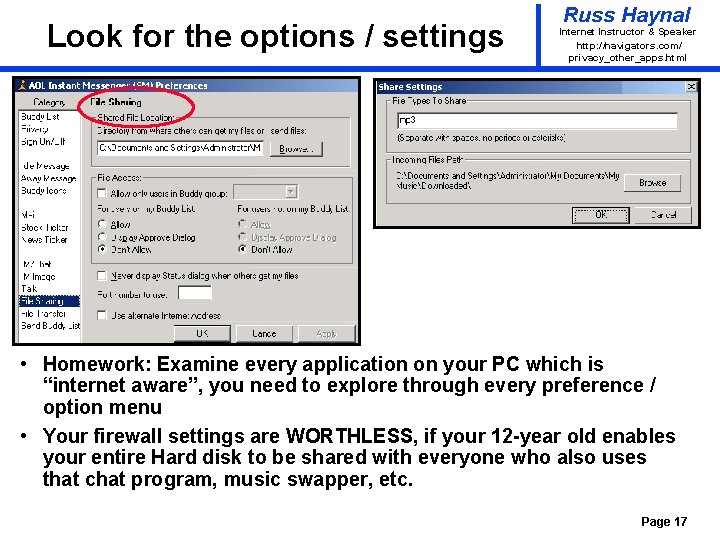
Look for the options / settings Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ privacy_other_apps. html • Homework: Examine every application on your PC which is “internet aware”, you need to explore through every preference / option menu • Your firewall settings are WORTHLESS, if your 12 -year old enables your entire Hard disk to be shared with everyone who also uses that chat program, music swapper, etc. Page 17

Blog = online diary / guestbook Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Millions of kids now have their own blog • A blog may include all of the following – Journal entries from your child – Postings from friends – Links to friend’s blogs – Photographs (especially cool or outrageous ones) – Personality tests – can be quite detailed • Whatever gets posted, may be read by parent, teacher, coach, college admissions officer, sexual predator, etc. Page 18

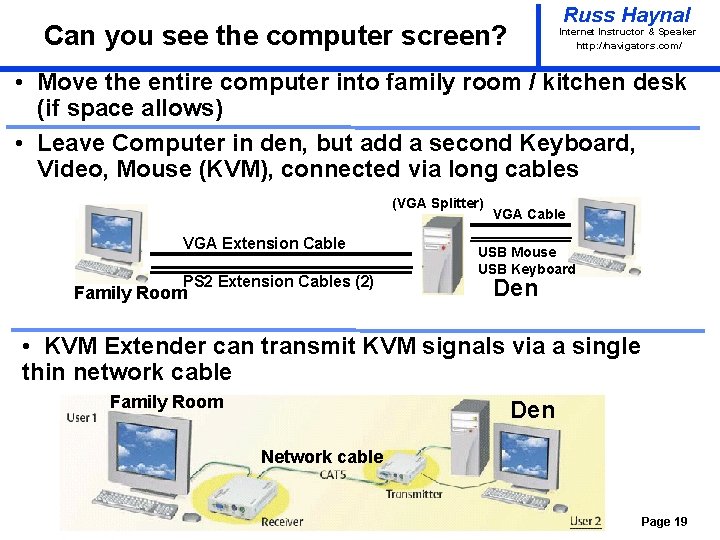
Russ Haynal Can you see the computer screen? Internet Instructor & Speaker http: / /navigators. com/ • Move the entire computer into family room / kitchen desk (if space allows) • Leave Computer in den, but add a second Keyboard, Video, Mouse (KVM), connected via long cables (VGA Splitter) VGA Extension Cable PS 2 Extension Cables (2) Family Room VGA Cable USB Mouse USB Keyboard Den • KVM Extender can transmit KVM signals via a single thin network cable Family Room Den Network cable Page 19

Summary Russ Haynal navigators. com/parentguide. html Internet Instructor & Speaker http: / /navigators. com/ Your Options: • • • Do nothing… Require password for internet access Time constraints on when access is available Move computer screen to a visible location Know what applications are being installed and how they are configured (AOL IM, Kazaa, hotmail – email filter options, etc) Install parent control software – Blacklists, vs. logs – Monitoring web vs monitoring everything (key logger) – Time limit specific applications such as chat Talk/listen to child – let them understand how they can be tracked – email articles to them about online predator cases. Yes this takes time and effort (welcome to parenting) Next, What about the neighbor’s computer, where your child goes instead? • What happens when the child moves out? Page 20

Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Extra topics that anyone who owns a computer needs to know…. Page 21

Identity theft Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ privacy. html Identity Theft is the fastest growing crime in America 9. 900, 000 victims during 2003 • Identity theft occurs when someone has collected enough personal information about you, that they can “impersonate” you. • They can use your identification information to access your existing financial accounts, investment accounts, etc. • They can use your identification information to establish new accounts (checking, credit card, loans) based on your name/credit history. • They run up debt, write bad checks, and then move on. All debt incurred is now yours. • They can collect your personal Information through traditional means – dumpster diving, scam solicitations, corrupt employee. • Now add the risk from Internet/PC usage: • Hacker gains access to your PC: bank account information, investment software, cookies, auto-complete password, auto web form fill-ins’ and family genealogy (birth date, mother’s maiden name) • Hacker gains access to your relative’s PC which has a genealogy program. Page 22

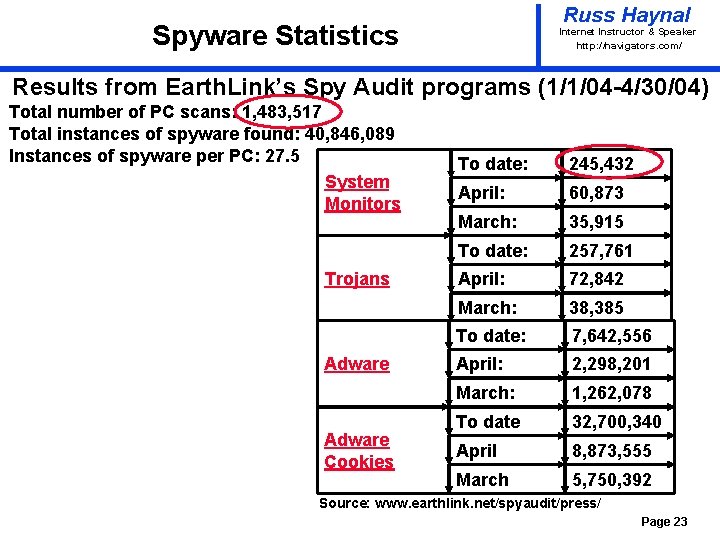
Russ Haynal Spyware Statistics Internet Instructor & Speaker http: / /navigators. com/ Results from Earth. Link’s Spy Audit programs (1/1/04 -4/30/04) Total number of PC scans: 1, 483, 517 Total instances of spyware found: 40, 846, 089 Instances of spyware per PC: 27. 5 System Monitors Trojans Adware Cookies To date: 245, 432 April: 60, 873 March: 35, 915 To date: 257, 761 April: 72, 842 March: 38, 385 To date: 7, 642, 556 April: 2, 298, 201 March: 1, 262, 078 To date 32, 700, 340 April 8, 873, 555 March 5, 750, 392 Source: www. earthlink. net/spyaudit/press/ Page 23

Piggy Back Applications (Spyware, Adware) Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ privacy_other_apps. html • Some Free program include piggy-back programs (they provide revenue to the free program) • For example: a stealth p 2 p network application is bundled with Kazaa – Buried in the user agreement: – "You hereby grant “Brilliant” the right to access and use the unused computing power and storage space on your computer/s and/or Internet access or bandwidth for the aggregation of content and use in distributed computing, " • “Brilliant” now has the keys to your computer. • 150 million copies of Kazaa have been downloaded. • How hard would it be for a hacker to also access these capabilities? • Programs such as ad-aware (by lavasoft) and “Spybot Search and destroy”, can be used to identify /remove such programs. Page 24

Anti-Virus Software Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ virus. html • Every machine should have updated anti-virus software installed, and running • AV software will occasionally scan every file on your machine for viruses • AV software should automatically examine every incoming file (via, floppy disk, email attachment, web download, peer-to peer download) • The heart of most AV programs is a “dictionary” of pre-defined viruses which is compared to your files. The dictionary may have over 60, 000 definitions. • AV programs will also monitor certain sensitive system resources for any changes – You may need to disable AV software when installing certain kinds of programs. Important: the virus definition dictionary must to be updated frequently (Over 3, 000 new viruses were discovered during the first half of 2002) Page 25

Keep your system up to date Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ privacy. html • My New Laptop, pre-loaded with Windows XP Professional, required 8. 2 MB of Critical Updates the very first time I launched Windows Update. • “windows update” requires Internet Explorer Version 5. 01 or higher Page 26

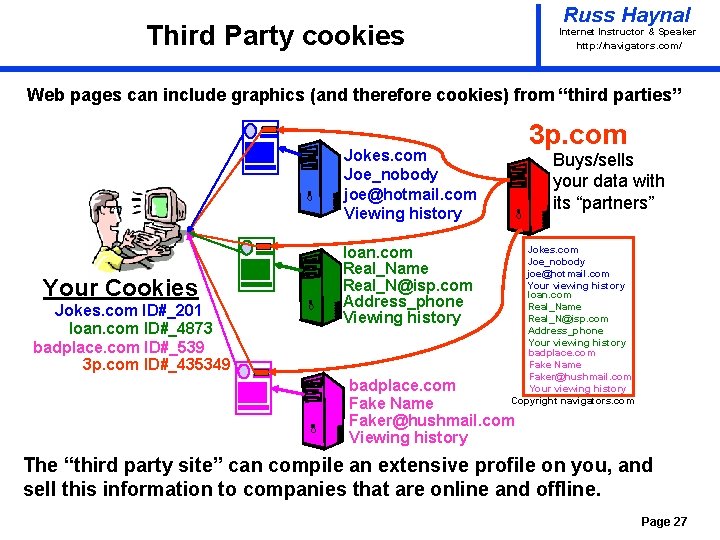
Russ Haynal Third Party cookies Internet Instructor & Speaker http: / /navigators. com/ Web pages can include graphics (and therefore cookies) from “third parties” 3 p. com Jokes. com Joe_nobody joe@hotmail. com Viewing history Your Cookies Jokes. com ID#_201 loan. com ID#_4873 badplace. com ID#_539 3 p. com ID#_435349 loan. com Real_Name Real_N@isp. com Address_phone Viewing history Buys/sells your data with its “partners” Jokes. com Joe_nobody joe@hotmail. com Your viewing history loan. com Real_Name Real_N@isp. com Address_phone Your viewing history badplace. com Fake Name Faker@hushmail. com Your viewing history Copyright navigators. com badplace. com Fake Name Faker@hushmail. com Viewing history The “third party site” can compile an extensive profile on you, and sell this information to companies that are online and offline. Page 27

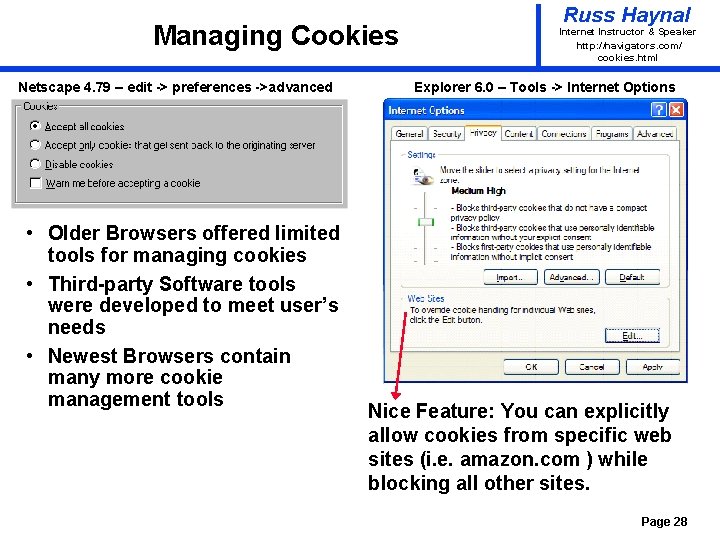
Managing Cookies Netscape 4. 79 – edit -> preferences ->advanced • Older Browsers offered limited tools for managing cookies • Third-party Software tools were developed to meet user’s needs • Newest Browsers contain many more cookie management tools Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ cookies. html Explorer 6. 0 – Tools -> Internet Options Nice Feature: You can explicitly allow cookies from specific web sites (i. e. amazon. com ) while blocking all other sites. Page 28

Public Terminals Russ Haynal Internet Instructor & Speaker http: / /navigators. com/ • Public terminals = Library, Kinkos, Hotel Lobby, Cyber Café, etc • Is there any kind of consistent “administration” to guarantee the integrity of these computers? For a public terminal, you should always assume that the machine has been compromised, and that a “keystroke logger” is quietly capturing all keystrokes. ( usernames, passwords, credit cards, etc) Page 29
 Kids r kids west cobb
Kids r kids west cobb Cingulum rest preparation
Cingulum rest preparation Rest seat
Rest seat Canine rest seat
Canine rest seat Rest rest perturbed spirit
Rest rest perturbed spirit An object at rest stays at rest
An object at rest stays at rest Online virtual worlds for kids
Online virtual worlds for kids Safety issues with ict
Safety issues with ict Health and safety in ict
Health and safety in ict Online safety and netiquette
Online safety and netiquette Formuö
Formuö Novell typiska drag
Novell typiska drag Tack för att ni lyssnade bild
Tack för att ni lyssnade bild Vad står k.r.å.k.a.n för
Vad står k.r.å.k.a.n för Shingelfrisyren
Shingelfrisyren En lathund för arbete med kontinuitetshantering
En lathund för arbete med kontinuitetshantering Personalliggare bygg undantag
Personalliggare bygg undantag Tidbok yrkesförare
Tidbok yrkesförare A gastrica
A gastrica Vad är densitet
Vad är densitet Datorkunskap för nybörjare
Datorkunskap för nybörjare Stig kerman
Stig kerman Hur skriver man en tes
Hur skriver man en tes Magnetsjukhus
Magnetsjukhus Nyckelkompetenser för livslångt lärande
Nyckelkompetenser för livslångt lärande Påbyggnader för flakfordon
Påbyggnader för flakfordon Kraft per area
Kraft per area Publik sektor
Publik sektor Jag har gått inunder stjärnor text
Jag har gått inunder stjärnor text Presentera för publik crossboss
Presentera för publik crossboss


















































