What is REST API A REST Representational State










- Slides: 18

What is REST API ? A REST (Representational State Transfer) Server simply provides access to resources and the REST client accesses and presents the resources. Resource is identified by URIs/ Global IDs. REST uses various representations to represent a resource like Text, JSON and XML. JSON is now the most popular format being used in Web Services REST is NOT A Protocol A Standard Replacement of SOAP

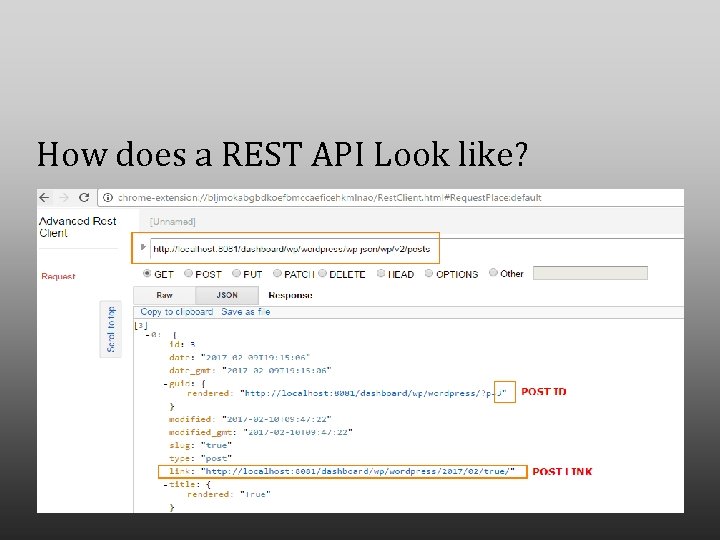
How does a REST API Look like?

HTTP Methods GET (read) POST (create)(Not idempotent) PUT (replace/update) DELETE PATCH (updating an existing resource)

HTTP Status Code 200 OK - Response to a successful REST API action. 204 No Content 400 Bad Request 401 Unauthorized 403 Forbidden 404 Not Found 405 Method Not Allowed 429 Too Many Requests (DOS due to rate limit)

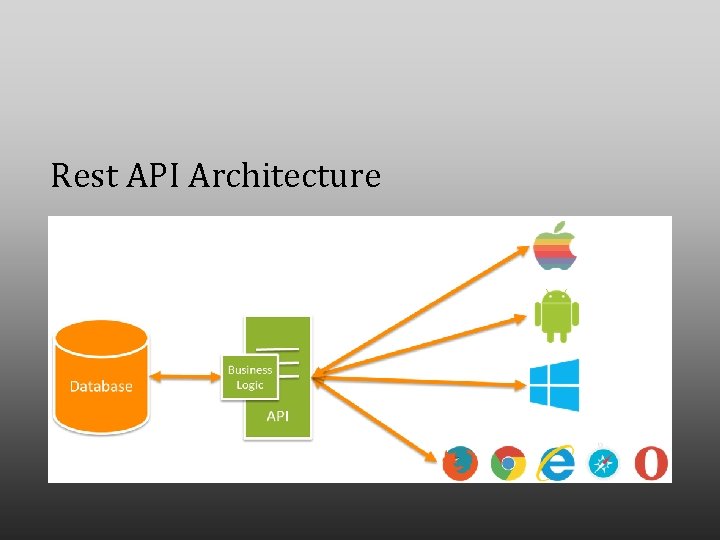
Rest API Architecture

API Vulnerabilities

Authentication and Authorization Common mistakes made during development phase: HTTP Basic Authentication Host: example. org GET / HTTP/1. 1 Authorization: Basic Zm 9 v. Om. Jhcg== HTTP Digest Authentication GET /users/username/account HTTP/1. 1 Host: example. org Authentication: hmac username: [digest]

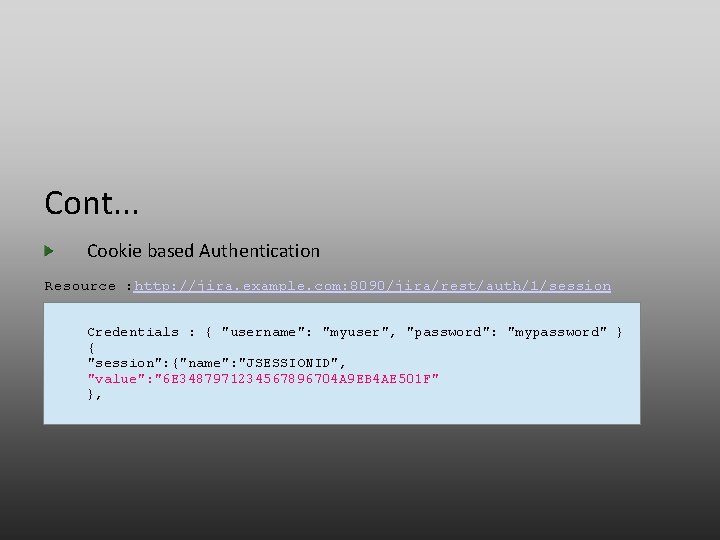
Cont. . . Cookie based Authentication Resource : http: //jira. example. com: 8090/jira/rest/auth/1/session Credentials : { "username": "myuser", "password": "mypassword" } { "session": {"name": "JSESSIONID", "value": "6 E 3487971234567896704 A 9 EB 4 AE 501 F" },

Mitigation Avoid Session based authentication HTTP authentication over HTTPS Oauth 1. 0 (Fb app) Oauth 2. 0 API Keys

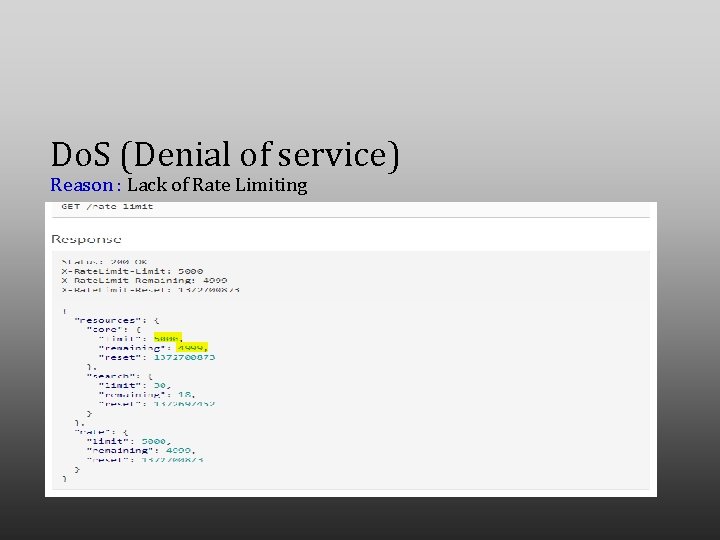
Do. S (Denial of service) Reason : Lack of Rate Limiting

Cont. . Set Rate Limit to avoid Do. S User rate limits (Set with user API) Server rate limits( Limit of specific Resource ) Regional data limits (Based on time and situation)

Service Information Leakage Mitigation : Configure API properly Hide server finger print

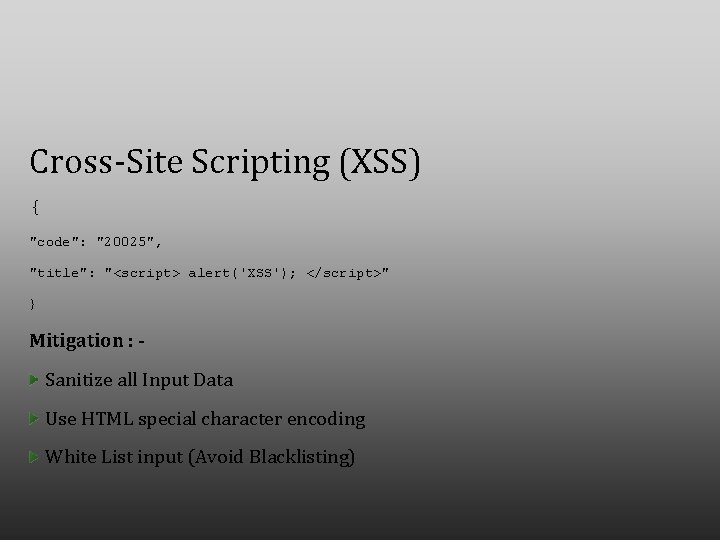
Cross-Site Scripting (XSS) { "code": "20025", "title": "<script> alert('XSS'); </script>" } Mitigation : Sanitize all Input Data Use HTML special character encoding White List input (Avoid Blacklisting)

CORS for REST APIs CORS(Cross-Origin Resource Sharing) is a security mechanism that allows a web page from one domain or Origin to access a resource with a different domain (a cross-domain request). Lack of CORS headers allow attacker to perform Cross-Site Request Forgery (CSRF).

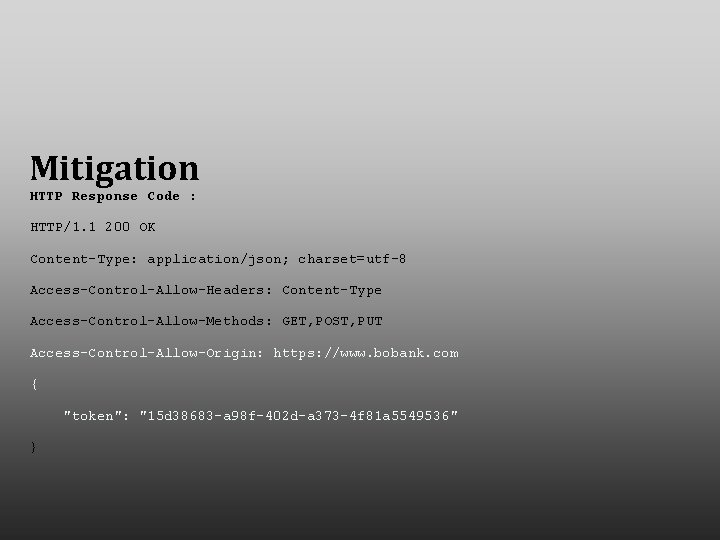
Mitigation HTTP Response Code : HTTP/1. 1 200 OK Content-Type: application/json; charset=utf-8 Access-Control-Allow-Headers: Content-Type Access-Control-Allow-Methods: GET, POST, PUT Access-Control-Allow-Origin: https: //www. bobank. com { "token": "15 d 38683 -a 98 f-402 d-a 373 -4 f 81 a 5549536" }

SQL Injections Input : http: //petstore. com/api/v 1/pet/123 Malicious Input : http: //petstore. com/api/v 1/pet/’%20 or%20’ 1’=’ 1 Mitigation : Sanitize user Input White List input (Avoid Blacklisting)

HPP (HTTP Parameter Pollution) Malicious Payload : security_token=attackertoken&blog. ID=attackerblogidvalue&blog. ID=vict imblogidvalue&authors. List=goldshlager 19 test%40 gmail. com(attacker email)&ok=Invite Mitigation : Server side parameter verification.

Avoid API Risk Build API Security into Software Development and Deployment Processes Validate User and App Identity Encrypt the Message Channel Monitor, Audit, Log and Analyze Your API Traffic