Overview on Hardware Security Electronic Design Contest 2017























- Slides: 36

Overview on Hardware Security Electronic Design Contest - 2017

Outline Overview of modern cryptography Modern hardware design practices Example of Hardware Attacks Introduction to Side Channel Analysis Differential fault analysis of ciphers Cache attacks on ciphers Power analysis of cipher implementations Testability of cryptographic hardware Overview of Hardware Trojans

3 Hardware Security Definition: implement security protection mechanisms in hardware E. g. , design trusted hardware, as opposed to (in addition to) trusted software CS 660 - Advanced Information Assurance - UMass. Amherst

4 Trusted or Trustworthy A component of a system is trusted means that the security of the system depends on it failure of component can break the security policy determined by its role in the system A component is trustworthy means that the component deserves to be trusted e. g. , it is implemented correctly determined by intrinsic properties of the component Trusted or trustworthy computation? CS 660 - Advanced Information Assurance - UMass. Amherst

5 Why Hardware Security Software security: software protect software! Vulnerable to attacks Is the antivirus/hardware untouched? Easy infiltration Fast spread Hardware security: hardware protect software Attacks need physical access Software infiltration much more difficult CS 660 - Advanced Information Assurance - UMass. Amherst

Overview of Modern Cryptography

Introduction Cryptography: protect information from illegal access. In the last three decades, cryptography has grown beyond designing ciphers to encompass also other activities like design of signature schemes for signing digital contracts. The design of cryptographic protocols for securely proving one’s identity has been an important aspect of cryptography of the modern age. Yet the construction of encryption schemes remains, and is likely to remain, a central enterprise of cryptography

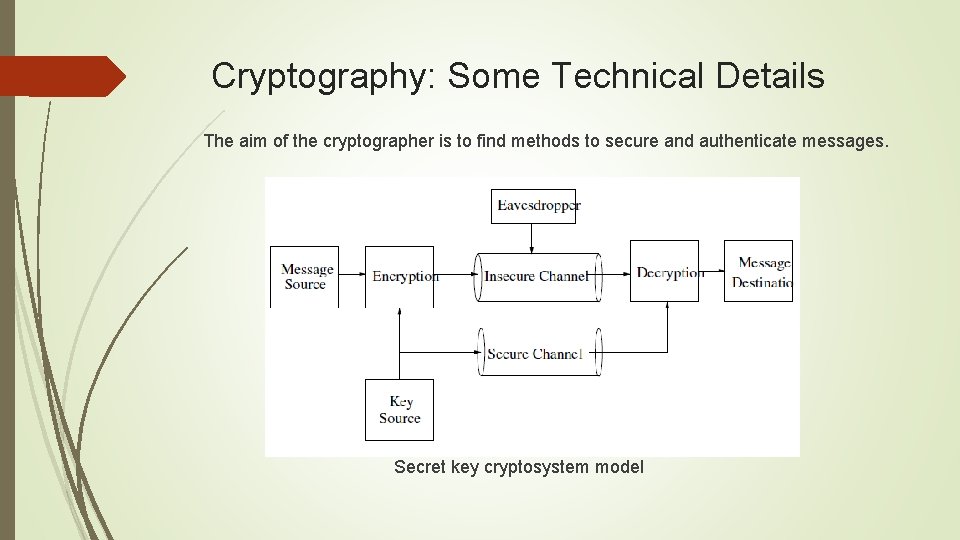
Cryptography: Some Technical Details The aim of the cryptographer is to find methods to secure and authenticate messages. Secret key cryptosystem model

Cryptography: Some Technical Details Example of Cryptographic Algorithm: Block Ciphers (Example: AES) RSA Elliptic Curve Cryptosystems BC 3

Modern Hardware Design Practices

Introduction Design of cryptographic algorithms in dedicated hardware provides significant opportunities for speed up due to their parallelism. Field Programmable Gate Arrays (FPGAs) are reconfigurable platforms to build hardware. Advantage: Hardware: in extracting parallelism, and achieving better performance Software: in terms of programmability.

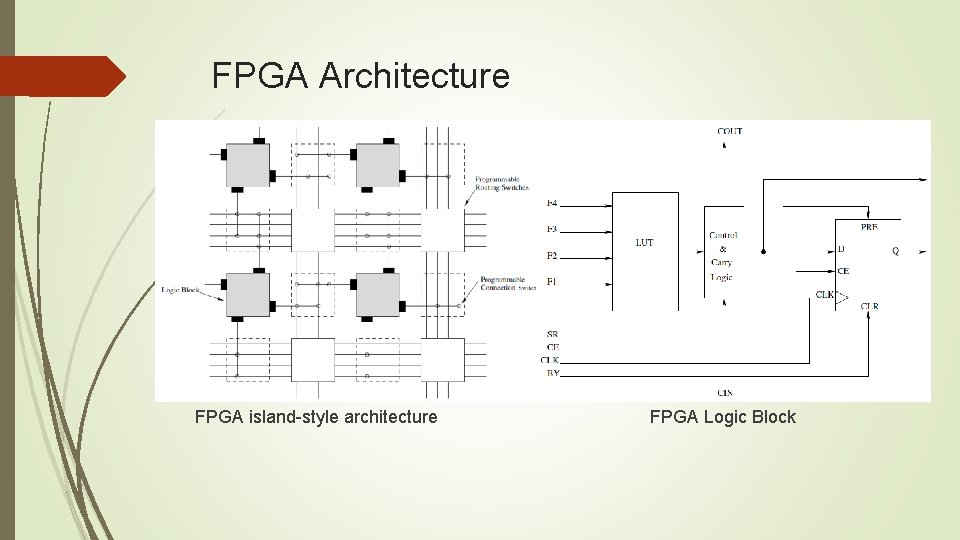
FPGA Architecture FPGAs are reconfigurable devices offering parallelism and flexibility, on one hand, while being low cost and easy to use on the other. Moreover, they have much shorter design cycle times compared to ASICs. The reconfigurability aspect of FPGAs also makes them suited for cryptographic applications. FPGAs do not require sophisticated equipment for production, they can be programmed in house. This is a distinct advantage for cryptography as no third party is involved, thus increasing trust in the hardware circuit

FPGA Architecture FPGA island-style architecture FPGA Logic Block

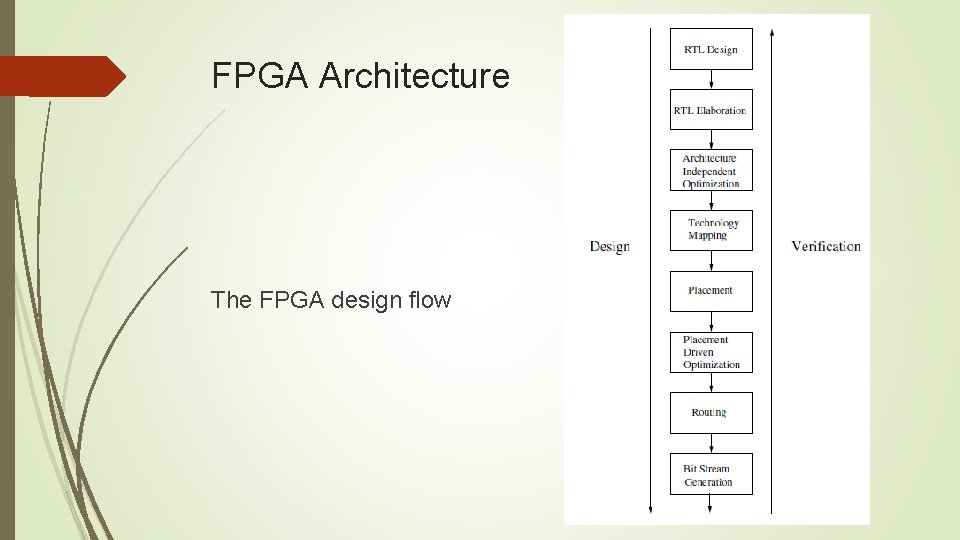
FPGA Architecture The FPGA design flow

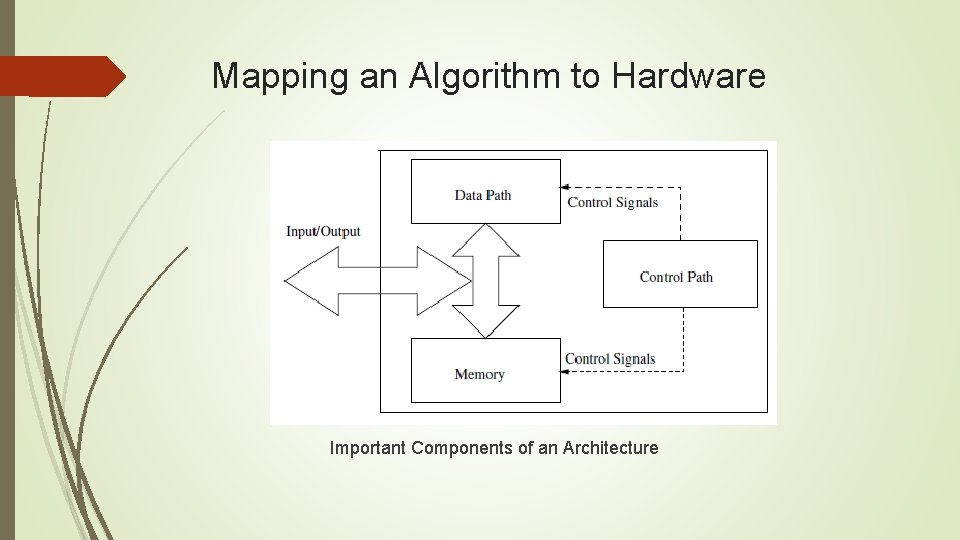
Mapping an Algorithm to Hardware Important Components of an Architecture

Enhancing the Performance of a Hardware Design Performance of a hardware design is often stated through: Critical path, by limiting the clock frequency. Resource consumed (customize the design for the target architecture to ensure that the resource used is minimized)

Example of Hardware Attacks • Side Channel Analysis • Differential fault analysis of ciphers • Cache attacks on chippers • Power analysis of chipper implementations

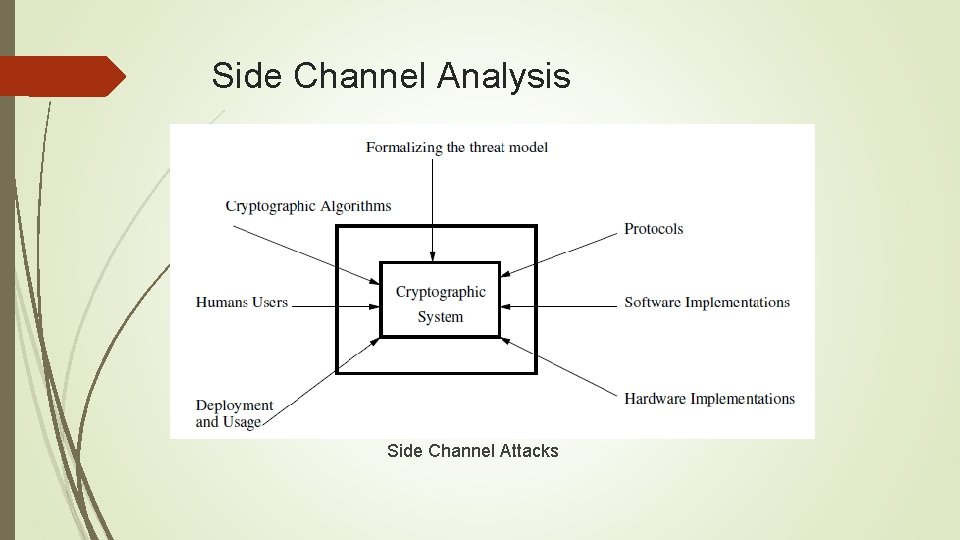
Side Channel Analysis Examples of such side channels are timing, power, electromagnetic radiations, visual, acoustics, cache, testability features of hardware devices and there may be many more. A very closely related class of attacks is called as fault attacks, where the device under the induction of faults, perform wrong computations. The adversary uses the correct ciphertexts and the faulty ciphertexts and obtains the keys.

Side Channel Analysis Side Channel Attacks

Side Channel Analysis Examples of such side channels are timing, power, electromagnetic radiations, visual, acoustics, cache, testability features of hardware devices and there may be many more. A very closely related class of attacks is called as fault attacks, where the device under the induction of faults, perform wrong computations. The adversary uses the correct ciphertexts and the faulty ciphertexts and obtains the keys.

Side Channel Analysis There are several forms of popular side channels attacks on hardware and embedded systems are: Timing Attacks Power Attacks Fault Attacks Design for Testability attacks Cache Attacks

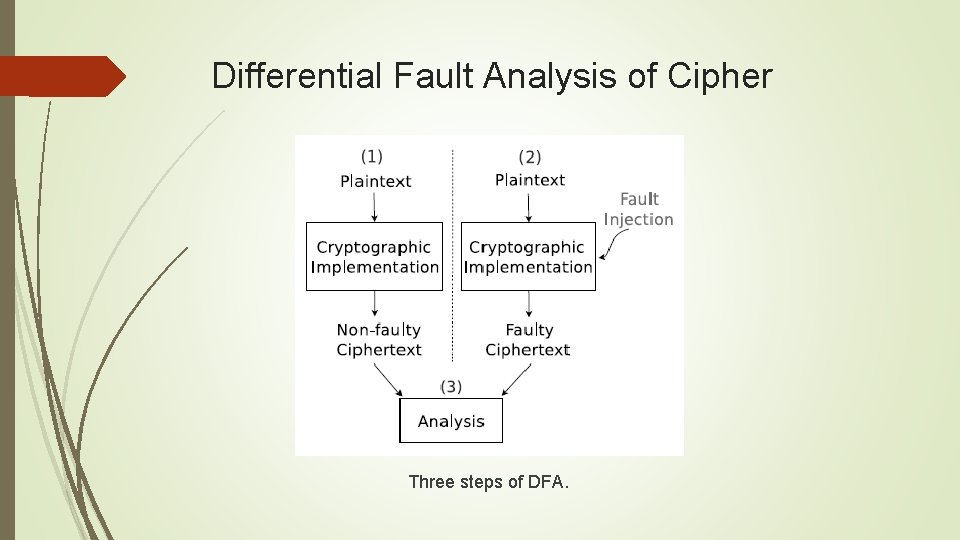
Differential Fault Analysis of Cipher The first fault attack was applied to the RSA cryptosytem. Biham and Shamir proposed a new fault based attacking technique which is wildly known as Differential Fault Analysis (DFA) DFA attack is a very powerful attack model which can threaten a large class of ciphers. As the faults are induced during the encryption process, the fault propagation patterns give some relations between the input and output difference if certain Sboxes.

Differential Fault Analysis of Cipher Three steps of DFA.

Differential Fault Analysis of Cipher The faults can be of varying nature but can be categorized as follows: Bit model Single byte Multiple byte

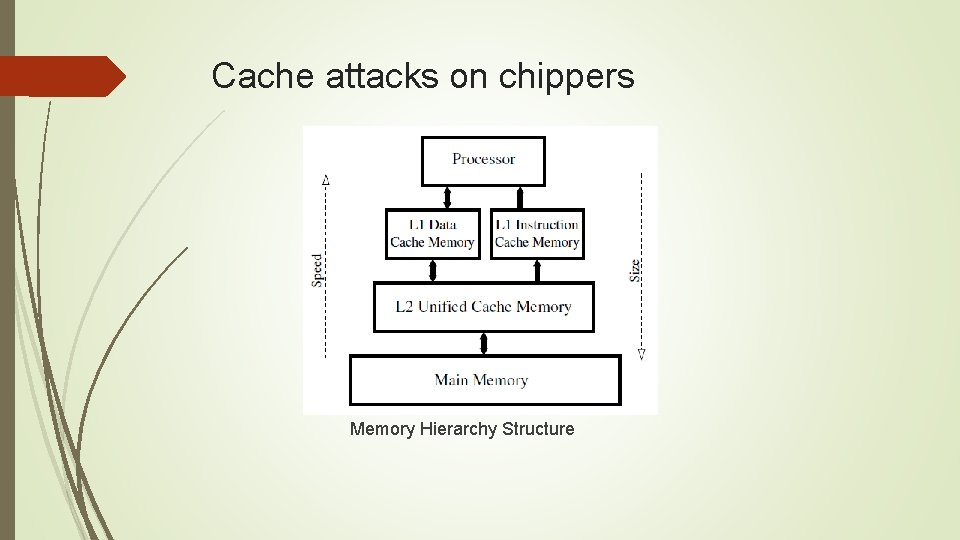
Cache attacks on chippers Memory Hierarchy Structure

Cache attacks on chippers Example of cache attacks: 1. Trace-driven cache attacks 1. Trace-driven attacks on AES 2. Trace-driven attacks based on included cache miss 2. Access-driven cache attacks 1. Access-driven attacks on Block chipper 2. Asynchronous access-driven attacks

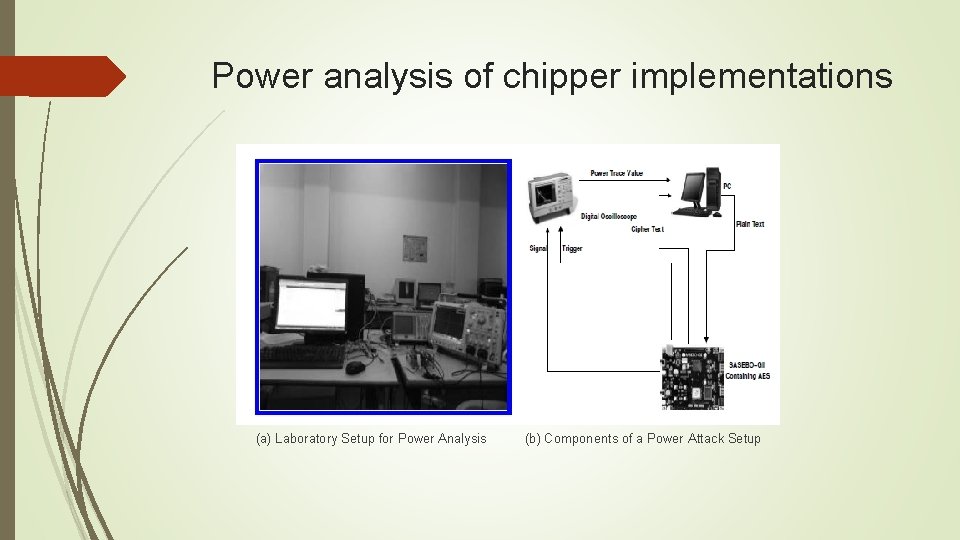
Power analysis of chipper implementations A successful power attack on a cryptographic device requires proper understanding of the power characteristic of the device. However, the central requirement of a power attack is the capability to obtain an accurate power trace.

Power analysis of chipper implementations (a) Laboratory Setup for Power Analysis (b) Components of a Power Attack Setup

Testability of Cryptographic Hardware

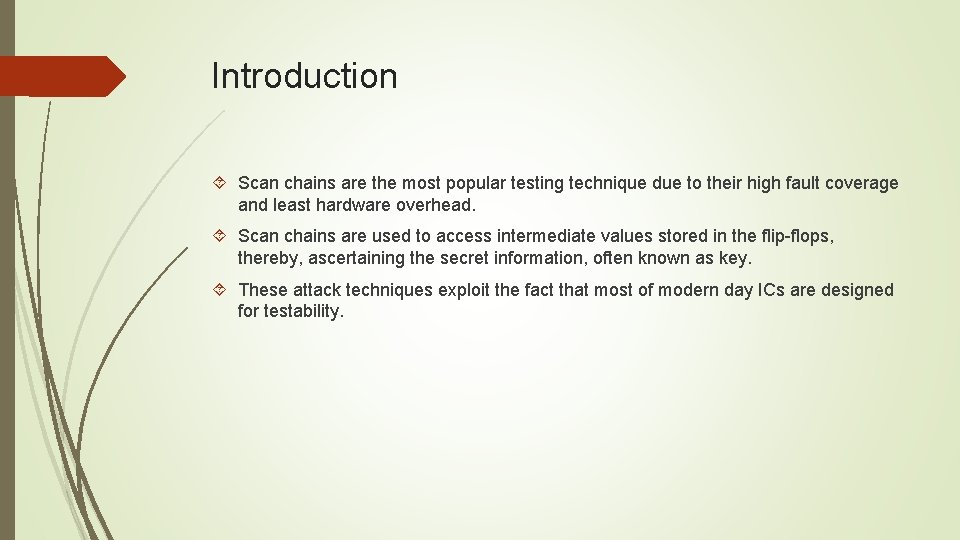
Introduction Scan chains are the most popular testing technique due to their high fault coverage and least hardware overhead. Scan chains are used to access intermediate values stored in the flip-flops, thereby, ascertaining the secret information, often known as key. These attack techniques exploit the fact that most of modern day ICs are designed for testability.

Introduction Example of Scan Attacks Scan Chain Based Attacks on Cryptographic Implementations Scan Chain Based Attack on Stream Ciphers

Overview on Hardware Trojan

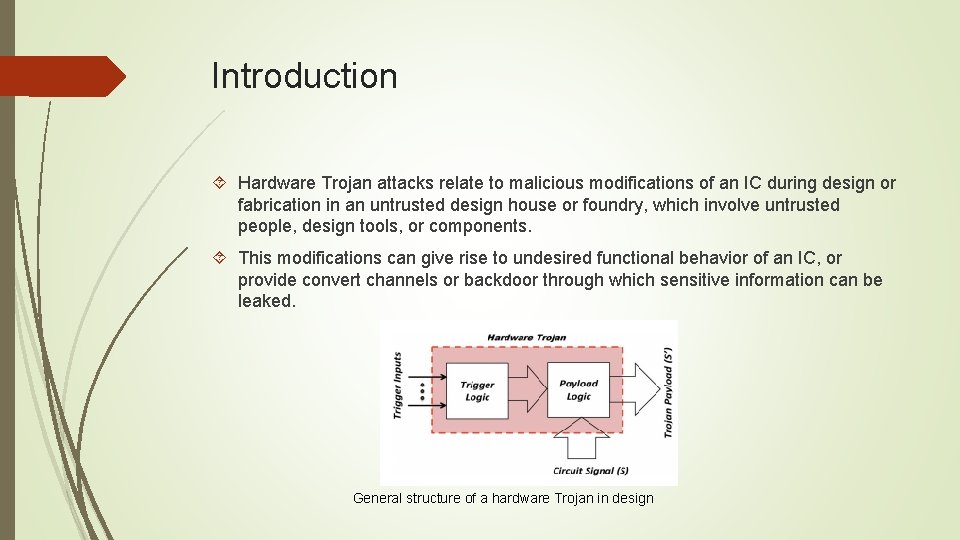
Introduction Hardware Trojan attacks relate to malicious modifications of an IC during design or fabrication in an untrusted design house or foundry, which involve untrusted people, design tools, or components. This modifications can give rise to undesired functional behavior of an IC, or provide convert channels or backdoor through which sensitive information can be leaked. General structure of a hardware Trojan in design

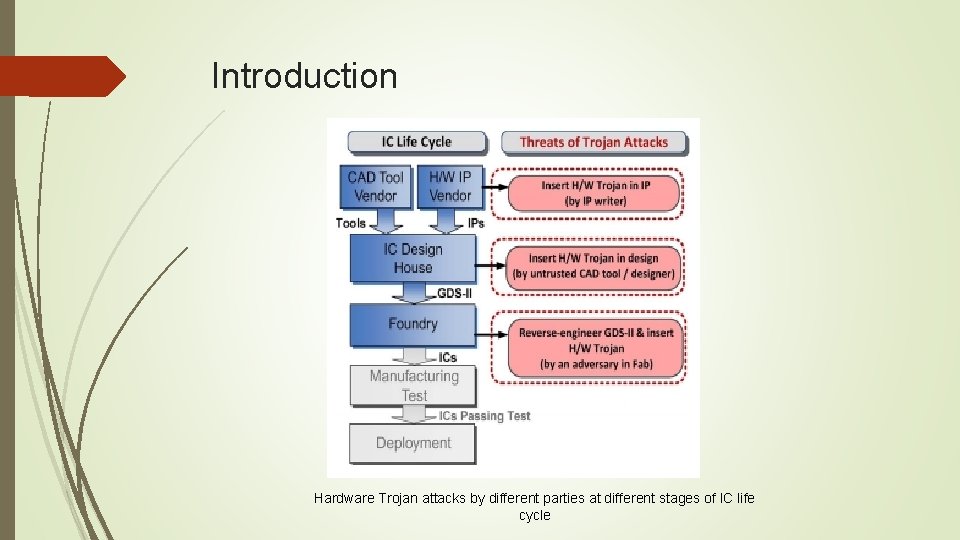
Introduction Hardware Trojan attacks by different parties at different stages of IC life cycle

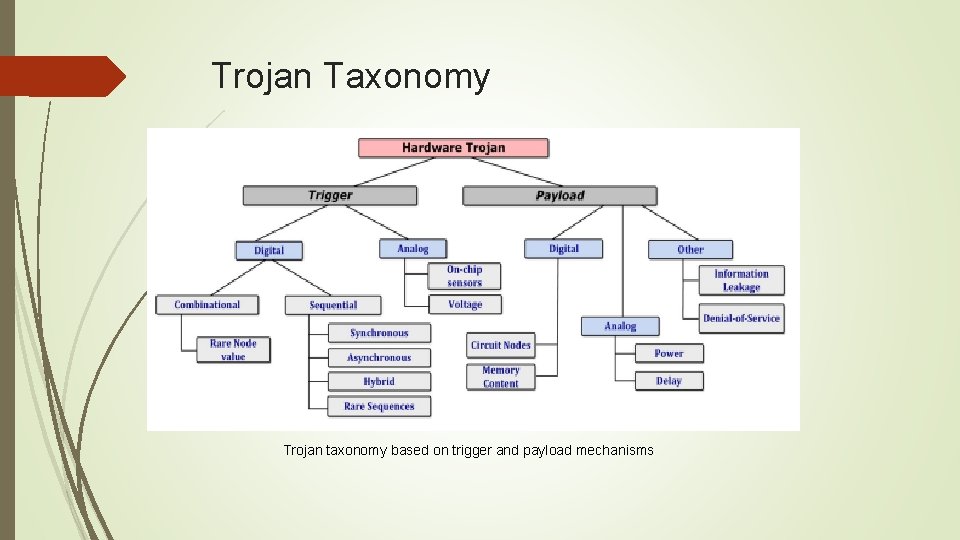
Trojan Taxonomy Trojan taxonomy based on trigger and payload mechanisms

Thank you