On the Limitations of Finite State Models as








- Slides: 24

On the Limitations of Finite State Models as Sources of Tests for Access Control and Authentication Aditya Mathur Professor of Computer Science Purdue University May 22, 2007 Joint work with: Professor Arif Ghafoor, ECE Graduate Students: Ammar Masood, ECE and K. Jayaram, CS 1

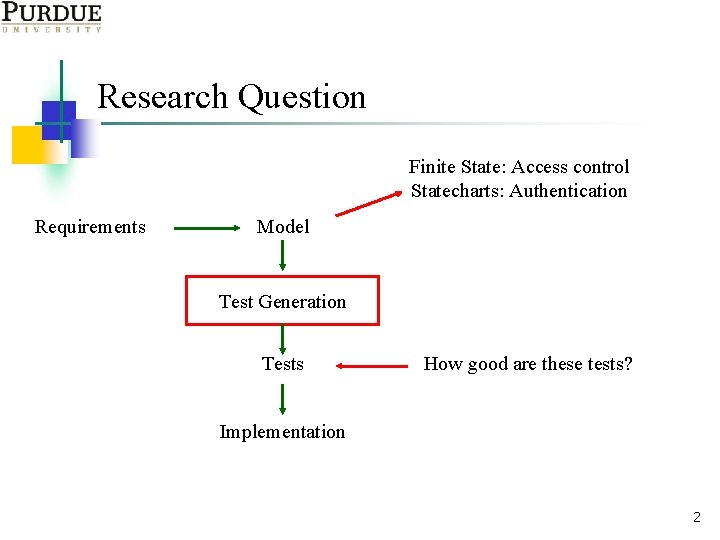
Research Question Finite State: Access control Statecharts: Authentication Requirements Model Test Generation Tests How good are these tests? Implementation 2

Summary: Role Based Access Control Policy: n Users, roles, permissions n Users assigned to roles, roles to permissions. n User roles activated prior to access. n n Static and dynamic separation of duty constraints (SSo. D) based on activation and inheritance hierarchy relations. Allowable input requests for RBAC policy enforcer (e. g. assign, de-assign, activate, and de-activate) 3

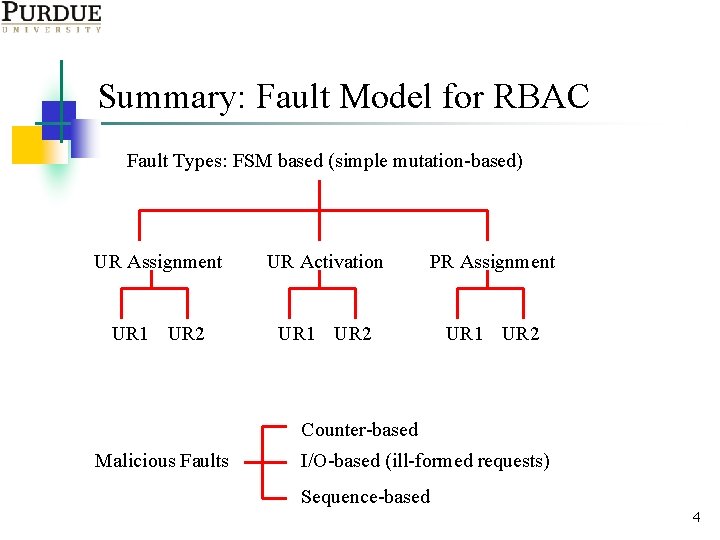
Summary: Fault Model for RBAC Fault Types: FSM based (simple mutation-based) UR Assignment UR Activation PR Assignment UR 1 UR 2 Counter-based Malicious Faults I/O-based (ill-formed requests) Sequence-based 4

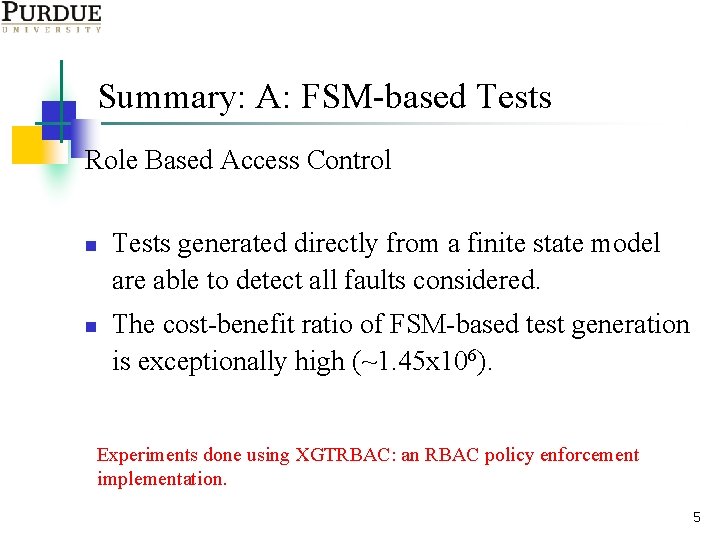
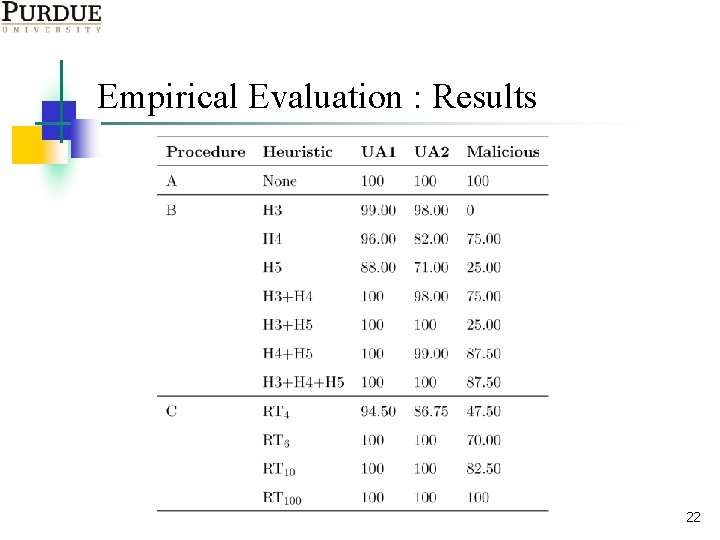
Summary: A: FSM-based Tests Role Based Access Control n n Tests generated directly from a finite state model are able to detect all faults considered. The cost-benefit ratio of FSM-based test generation is exceptionally high (~1. 45 x 106). Experiments done using XGTRBAC: an RBAC policy enforcement implementation. 5

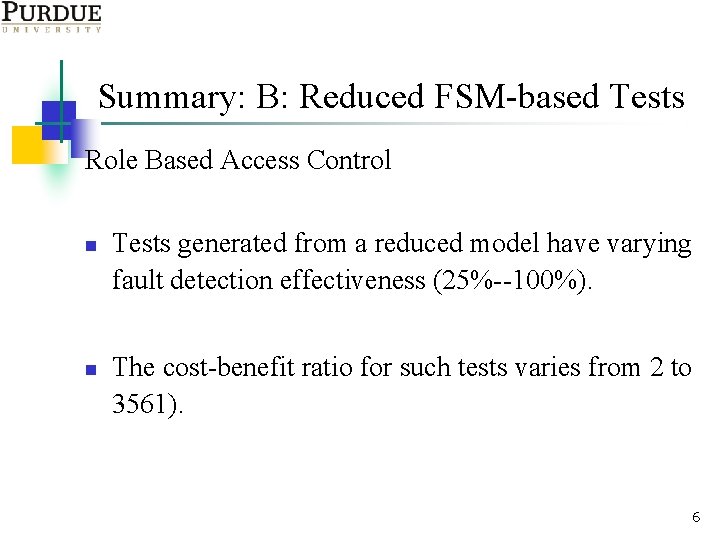
Summary: B: Reduced FSM-based Tests Role Based Access Control n n Tests generated from a reduced model have varying fault detection effectiveness (25%--100%). The cost-benefit ratio for such tests varies from 2 to 3561). 6

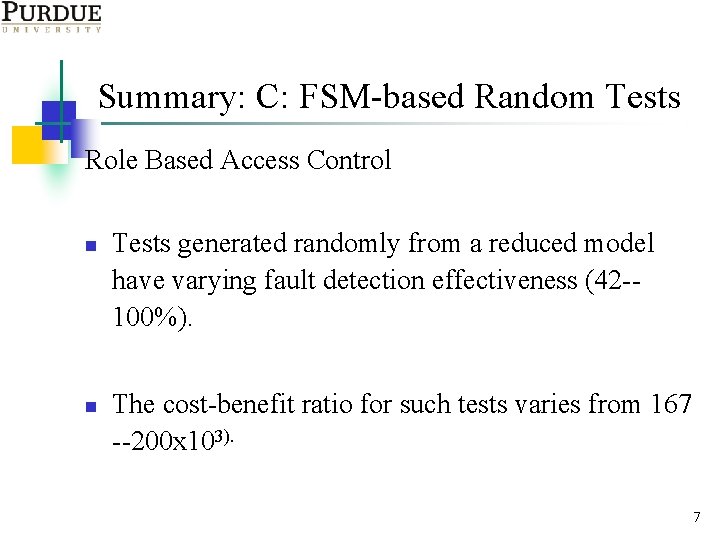
Summary: C: FSM-based Random Tests Role Based Access Control n n Tests generated randomly from a reduced model have varying fault detection effectiveness (42 -100%). The cost-benefit ratio for such tests varies from 167 --200 x 103). 7

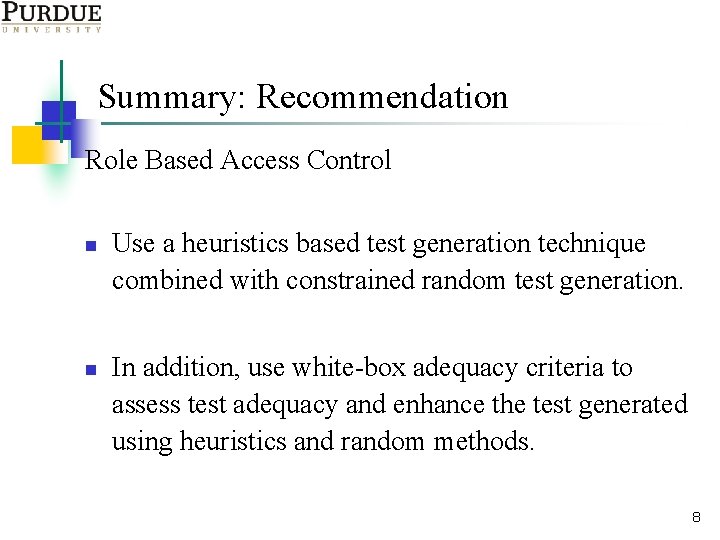
Summary: Recommendation Role Based Access Control n n Use a heuristics based test generation technique combined with constrained random test generation. In addition, use white-box adequacy criteria to assess test adequacy and enhance the test generated using heuristics and random methods. 8

Summary: Authentication Transport Layer Protocol: Gnu. TLS n n Client-server application. Developed to conform to RFC 2246. Uses the TLS protocol for authenticating a user and a session. Handshake, renegotiate to establish and re-establish sessions. 30 K LOC 9

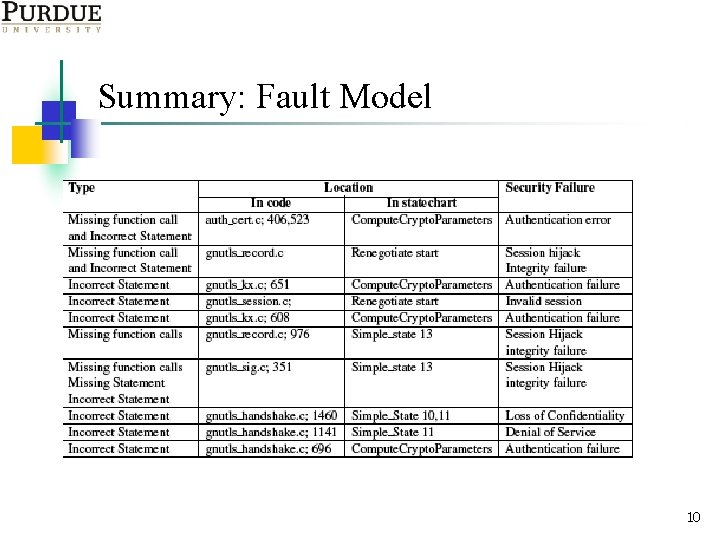
Summary: Fault Model 10

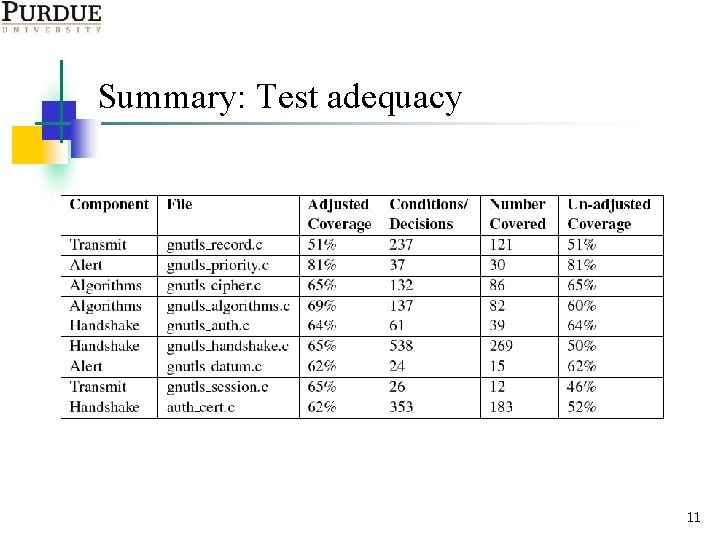
Summary: Test adequacy 11

Summary: Recommendation Authentication n Tests generated from statechart models must be augmented using tests generated using an orthogonal test generation technique. It might be difficult to detect malicious code using any test generation strategy that does not account for code coverage. Negative testing must be performed. [We do not have sufficient data to support this recommendation. ] 12

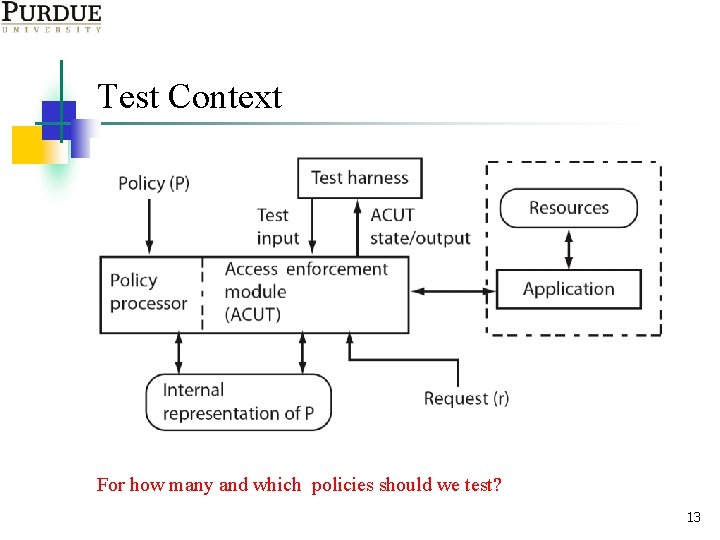
Test Context For how many and which policies should we test? 13

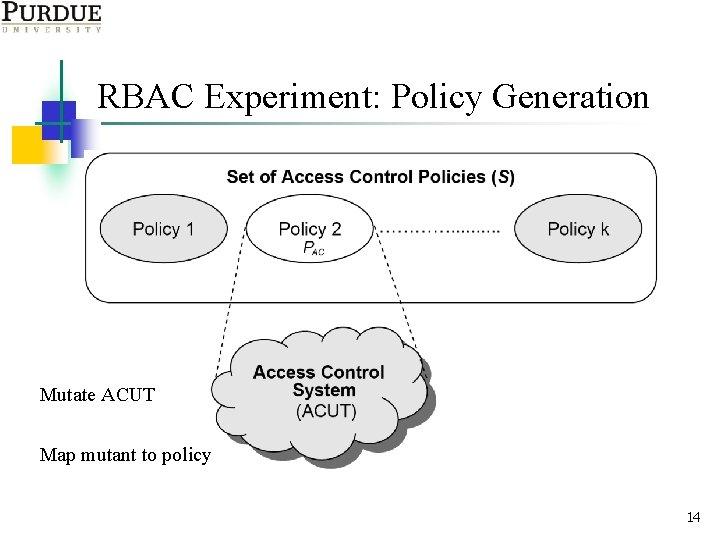
RBAC Experiment: Policy Generation Mutate ACUT Map mutant to policy 14

What are we trying to show? Conformance to expected behavior: 15

Conformance Testing Procedures Used n n n A: Transform a policy to FSM and generate tests directly. B: Use one or more heuristics to reduce the FSM and generate tests from the scaled down model. C: Randomly select paths of fixed length from the original model. 16

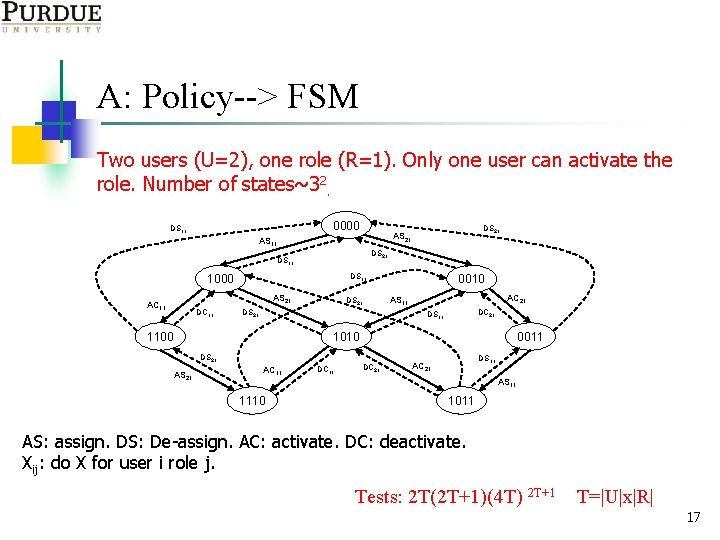
A: Policy--> FSM Two users (U=2), one role (R=1). Only one user can activate the role. Number of states~32. 0000 DS 11 DS 21 DS 11 1000 AS 21 AC 11 DS 21 AS 11 DS 21 0010 AC 21 AS 11 DC 21 DS 11 1100 1010 0011 DS 21 AC 11 DC 21 DS 11 AC 21 AS 11 1110 1011 AS: assign. DS: De-assign. AC: activate. DC: deactivate. Xij: do X for user i role j. Tests: 2 T(2 T+1)(4 T) 2 T+1 T=|U|x|R| 17

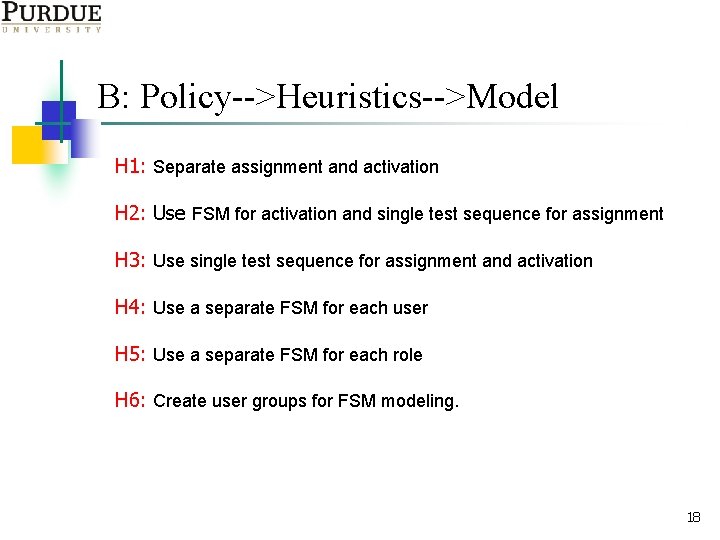
B: Policy-->Heuristics-->Model H 1: Separate assignment and activation H 2: Use FSM for activation and single test sequence for assignment H 3: Use single test sequence for assignment and activation H 4: Use a separate FSM for each user H 5: Use a separate FSM for each role H 6: Create user groups for FSM modeling. 18

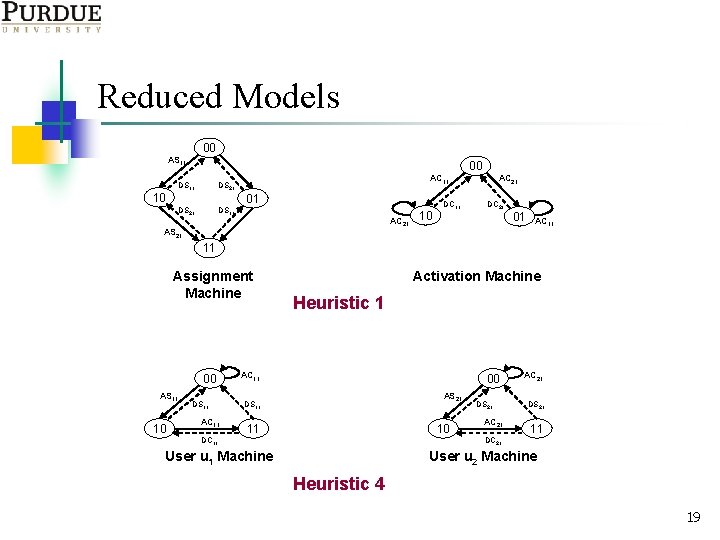
Reduced Models 00 AS 11 00 DS 11 DS 21 DS 11 10 AC 11 01 AC 21 AS 21 10 DC 11 AC 21 DC 21 01 AC 11 11 Assignment Machine 00 AS 11 10 DS 11 AC 11 Activation Machine Heuristic 1 AC 11 00 AS 21 DS 11 10 11 DS 21 AC 21 DS 21 11 DC 21 DC 11 User u 1 Machine User u 2 Machine Heuristic 4 19

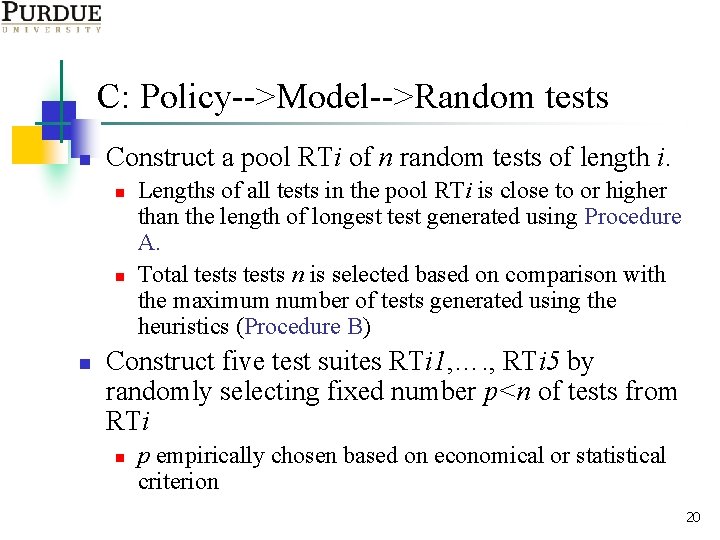
C: Policy-->Model-->Random tests n Construct a pool RTi of n random tests of length i. n n n Lengths of all tests in the pool RTi is close to or higher than the length of longest test generated using Procedure A. Total tests n is selected based on comparison with the maximum number of tests generated using the heuristics (Procedure B) Construct five test suites RTi 1, …. , RTi 5 by randomly selecting fixed number p<n of tests from RTi n p empirically chosen based on economical or statistical criterion 20

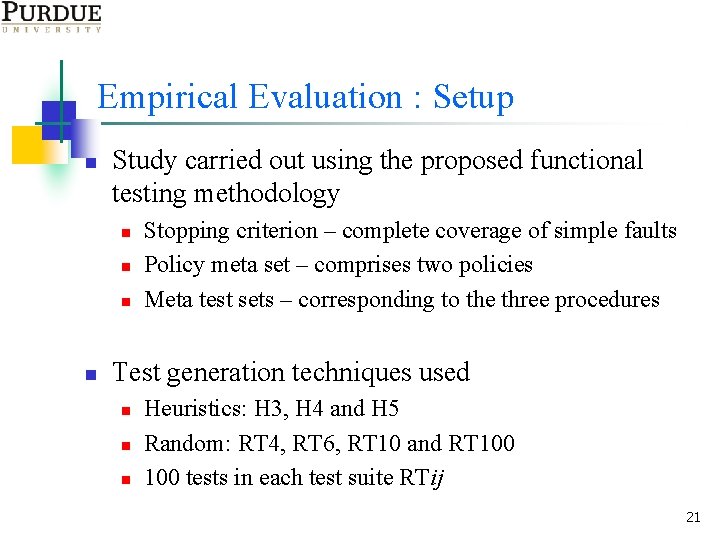
Empirical Evaluation : Setup n Study carried out using the proposed functional testing methodology n n Stopping criterion – complete coverage of simple faults Policy meta set – comprises two policies Meta test sets – corresponding to the three procedures Test generation techniques used n n n Heuristics: H 3, H 4 and H 5 Random: RT 4, RT 6, RT 10 and RT 100 tests in each test suite RTij 21

Empirical Evaluation : Results 22

Empirical vs. Simulation 23

Future Work n Test generation for TRBAC systems n n n Extending the temporal constraints in TRBAC specification Extension of TRBC fault model Conducting an empirical evaluation Validation of global meta-policy in collaborative environments Regression testing techniques for access control systems 24
 Limitations of finite state machine
Limitations of finite state machine Finite subordinate clauses
Finite subordinate clauses What is finite verb
What is finite verb Learning objectives of non finite verbs
Learning objectives of non finite verbs Finite and non-finite verb
Finite and non-finite verb Finite and non finite
Finite and non finite Tcp header
Tcp header Contoh soal teori bahasa dan automata
Contoh soal teori bahasa dan automata Finite state machine sequential circuits
Finite state machine sequential circuits Finite state machine with datapath
Finite state machine with datapath Finite state machine minimization
Finite state machine minimization Finite automata dikelompokkan menjadi
Finite automata dikelompokkan menjadi Vhdl finite state machine
Vhdl finite state machine Traffic light finite state machine
Traffic light finite state machine Transport layer primitives
Transport layer primitives Finite state machine vhdl
Finite state machine vhdl 3 floor elevator fsm
3 floor elevator fsm Fsa dinyatakan dalam 5 tupel, kecuali
Fsa dinyatakan dalam 5 tupel, kecuali Finite state machine vending machine example
Finite state machine vending machine example Transition graph in automata
Transition graph in automata Transfer function steady state error
Transfer function steady state error Finite state machine
Finite state machine Ospf finite state machine
Ospf finite state machine Finite state machine
Finite state machine Finite state machine game
Finite state machine game