Malware Incident Response Static Analysis CIS 6395 Incident












- Slides: 39

Malware Incident Response Static Analysis CIS 6395, Incident Response Technologies Fall 2016, Dr. Cliff Zou

Aknowledgement Many slides come from Dr. Lang’s previous teaching of this class https: //zeltser. com CS 155: Computer and Network Security (Stanford Univ. ) ◦ https: //crypto. stanford. edu/cs 155 old/cs 155 spring 09/lectures/10 -malware. ppt

Malware - Short for “malicious software” is software designed to harm or surreptitiously access a computer system without the owner’s informed consent Types of malware: ◦ Computer viruses - a computer program that can replicate itself and spread from one computer to another through human intervention ◦ Worms - a program that actively transmits itself over a network to infect other computers without human intervension ◦ Trojan horses - malicious programs disguised as something innocuous or desirable ◦ Spyware /keylogger ◦ Dishonest adware ◦ Backdoor ◦ Rootkits - malicious program installed on a system which stays concealed to avoid detection and disinfection ◦ Other malicious or unwanted software or programs

Some History Malware’s most common pathway from attacker to victim is through the Internet via e-mail and the Web “Elk Cloner” (1981) is one of the first known microcomputer viruses that spread "in the wild, " – outside the computer system or lab in which it was written. ◦ Designed as a boot sector virus that infected Apple II operating systems and spread from disk to disk Fred Cohen from the University of Southern California wrote his paper "Computer Viruses - Theory and Experiments“ in 1984 that was the first paper to explicitly call a self-reproducing program a "virus" The first mobile phone virus, Cabir, appeared in 2004. In Sept. 2001, Code Red worm started a new phase of malware fast and world-wide automatic spreading In 2004, Bagle mass-mailing worm formed Bagle botnet to facilitate spam email proxy/relay

What to Infect by Malware Executable Interpreted file Kernel Service Master Boot Record (MBR) Hypervisor

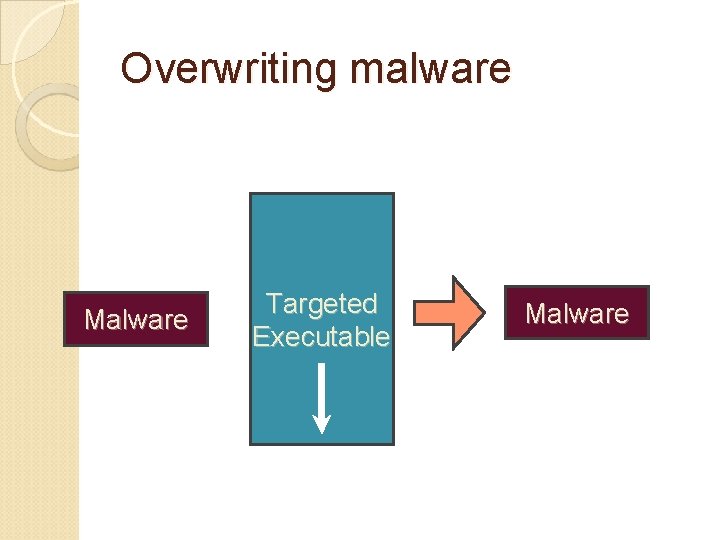
Overwriting malware Malware Targeted Executable Malware

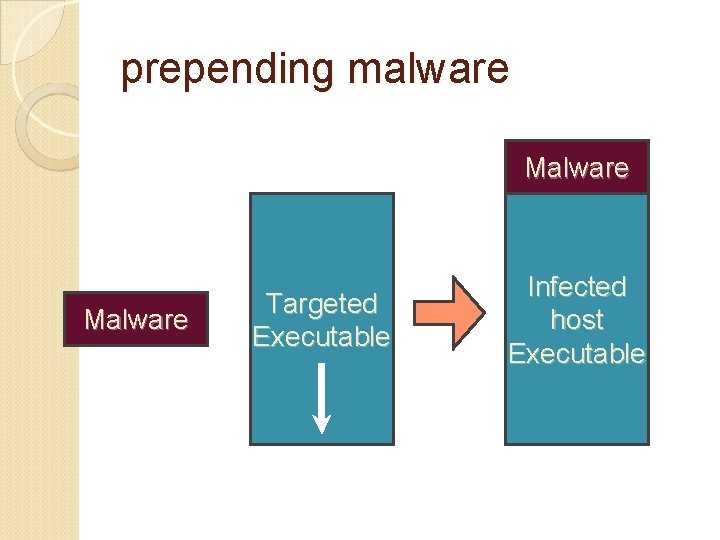
prepending malware Malware Targeted Executable Infected host Executable

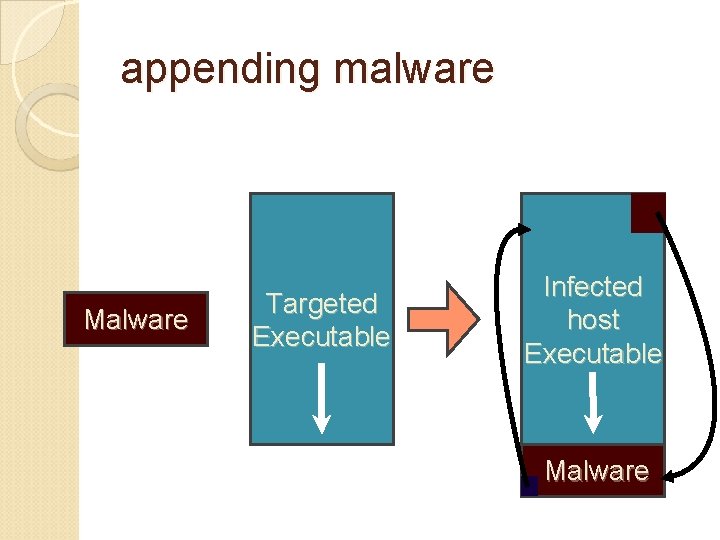
appending malware Malware Targeted Executable Infected host Executable Malware

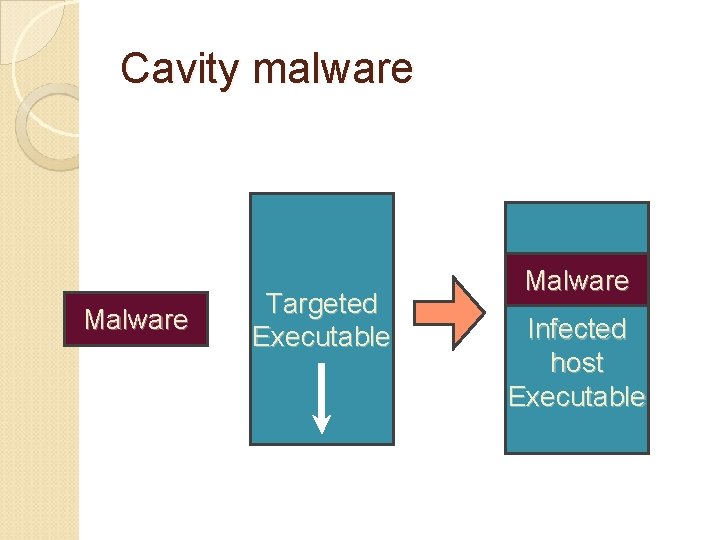
Cavity malware Malware Targeted Executable Malware Infected host Executable

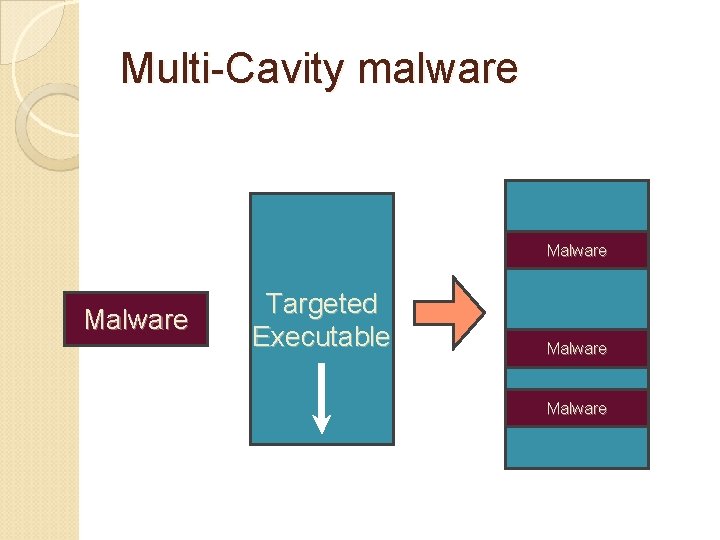
Multi-Cavity malware Malware Targeted Executable Malware

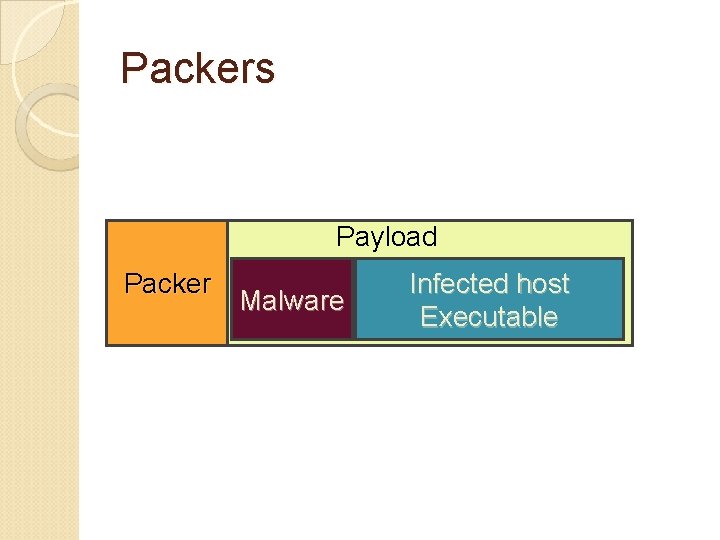
Packers Payload Packer Malware Infected host Executable

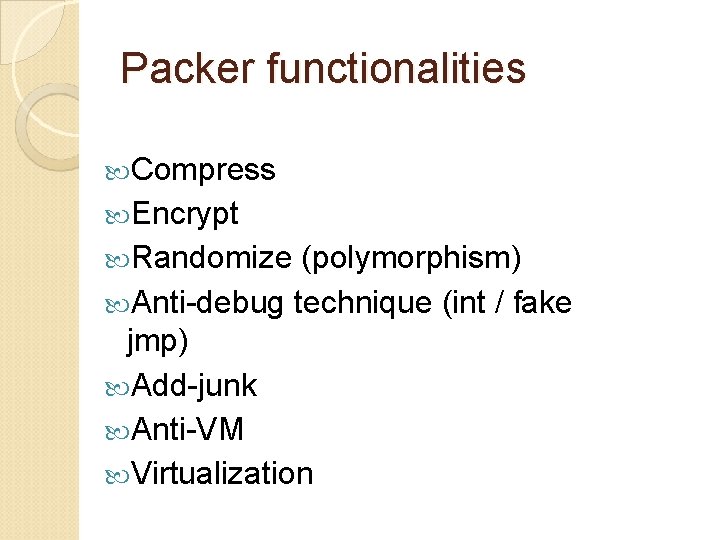
Packer functionalities Compress Encrypt Randomize (polymorphism) Anti-debug technique (int / fake jmp) Add-junk Anti-VM Virtualization

Cheat Sheet for Analyzing Malicious Software https: //zeltser. com/reverse-malware-cheat-sheet/ General Approach ◦ Set up a controlled, isolated laboratory in which to examine the malware specimen. ◦ Perform behavioral analysis to examine the specimen’s interactions with its environment. ◦ Perform static code analysis to further understand the specimen’s inner-workings. ◦ Perform dynamic code analysis to understand the more difficult aspects of the code. ◦ If necessary, unpack the specimen. ◦ Repeat steps 2, 3, and 4 (order may vary) until sufficient analysis objectives are met. ◦ Document findings and clean-up the laboratory for future analysis.

Types of Computer Code Source Code - text written in a particular highlevel computer language (e. g. , C++, Java) Compiled, object, or binary machine code a computer can directly read and execute e. g. , executable files of extension. exe on Windows Shell scripts, batch files, or code written in a scripting language such as Python, Perl, Ruby; scripts are typically in human-readable format and “interpreted” when they are run, not “compiled” into machine code in advance (http: //en. wikipedia. org/wiki/Scripting_language )

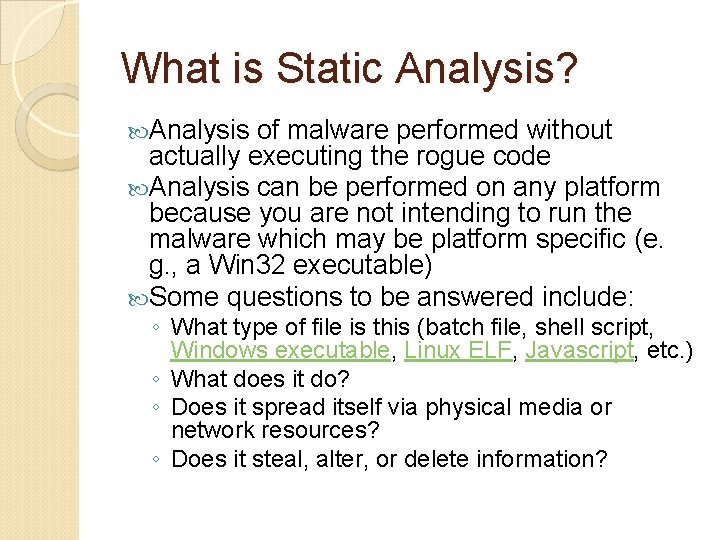
What is Static Analysis? Analysis of malware performed without actually executing the rogue code Analysis can be performed on any platform because you are not intending to run the malware which may be platform specific (e. g. , a Win 32 executable) Some questions to be answered include: ◦ What type of file is this (batch file, shell script, Windows executable, Linux ELF, Javascript, etc. ) ◦ What does it do? ◦ Does it spread itself via physical media or network resources? ◦ Does it steal, alter, or delete information?

General Procedures Determine the type of file you are examining, its internal structures (sections and headers) Review the ASCII and Unicode strings contained within the binary file Submit the code to a virus program or online scanner such as http: //www. virustotal. com; signature analysis may help determine the name and functionality of the malware Perform additional online research to determine the malware’s purpose and capabilities

Where to Get Malware Samples for Analysis? https: //zeltser. com/malware-sample- sources/ ◦ http: //www. tekdefense. com/downloads/ma lware-samples/ ◦ http: //thezoo. morirt. com/ It contains close to 100 malware binary and source codes. ◦ http: //openmalware. org/ You can search to find the malware binary code you want

File Analysis Techniques and Tools File (Unix/Linux command) - Used to determine the file type ◦ command: file <program name> ◦ “/usr/share/file/magic. mgc” file offers approximately 5, 000 different file types that Linux will recognize with the file command ◦ Hex Editor – Be. Hex. Editor (GUI-based, Free): https: //sourceforge. net/projects/hexbox/files/hexbox/Be. Hex Editor%201. 6. 0/ Strings (Windows & Unix) - find the printable strings in an object or other binary file ◦ command: strings -a <program name> ◦ -a - this option causes strings to look for strings in all sections of the object file Bin. Text (Windows) - Finds ASCII, Unicode and Resource strings in a file, http: //www. mcafee. com/us/downloads/free -tools/bintext. aspx

Windows Portable Executable (PE) Analysis Tools Five PE Analysis Tools Worth Looking At ◦ https: //blog. malwarebytes. com/threat-analysis/2014/05/fivepe-analysis-tools-worth-looking-at/ PE Studio (free version available, portable) https: //www. winitor. com/ Exeinfo PE - view detailed information about an Windows exe file including packers used http: //exeinfo. atwebpages. com/ PEBrowse Professional: static-analysis and disassembler for Win 32/Win 64 executables

PE File Format The Portable Executable (PE) format is a file format for executables, object code, and DLLs, used in 32 -bit and 64 -bit versions of Windows operating systems. The main competitors to PE are ELF (used in Linux and most other versions of Unix) and Mach-O (used in Mac OS X). A PE file consists of a number of headers and sections that tell the dynamic linker how to map the file into memory

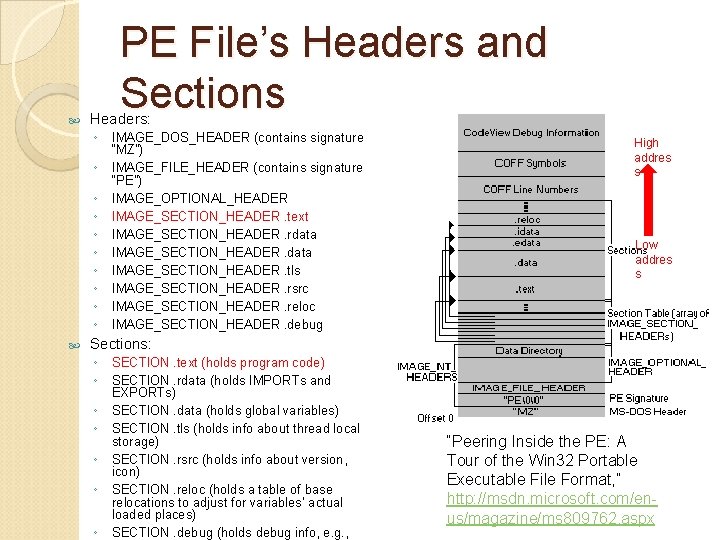
PE File’s Headers and Sections Headers: ◦ ◦ ◦ ◦ ◦ IMAGE_DOS_HEADER (contains signature “MZ”) IMAGE_FILE_HEADER (contains signature “PE”) IMAGE_OPTIONAL_HEADER IMAGE_SECTION_HEADER. text IMAGE_SECTION_HEADER. rdata IMAGE_SECTION_HEADER. tls IMAGE_SECTION_HEADER. rsrc IMAGE_SECTION_HEADER. reloc IMAGE_SECTION_HEADER. debug High addres s Low addres s Sections: ◦ ◦ ◦ ◦ SECTION. text (holds program code) SECTION. rdata (holds IMPORTs and EXPORTs) SECTION. data (holds global variables) SECTION. tls (holds info about thread local storage) SECTION. rsrc (holds info about version, icon) SECTION. reloc (holds a table of base relocations to adjust for variables’ actual loaded places) SECTION. debug (holds debug info, e. g. , “Peering Inside the PE: A Tour of the Win 32 Portable Executable File Format, ” http: //msdn. microsoft. com/enus/magazine/ms 809762. aspx

Windows EXE vs. DLL Files Differences between EXE and DLL files (http: //en. wikipedia. org/wiki/Dynamiclink_library#Symbol_resolution_and_binding) ◦ Dynamic-link library, or DLL, is Microsoft's implementation of the shared library concept in the Microsoft Windows and OS/2 operating systems DLLs provide a mechanism for shared code and data, allowing a developer of shared code/data to upgrade functionality without requiring applications to be re-linked or re-compiled The code in a DLL is usually shared among all the processes that use the DLL. However, the data sections of a DLL are usually private; that is, each process using the DLL has its own copy of all the DLL's data. ◦ It is not possible to directly execute a DLL, since it requires an EXE for the operating system to load it through an entry point ◦ An EXE file uses an import address table (IAT) to list all referenced DLLs and, at run-time, the IAT is filled with appropriate addresses that each point directly to a function of the separately loaded DLL.

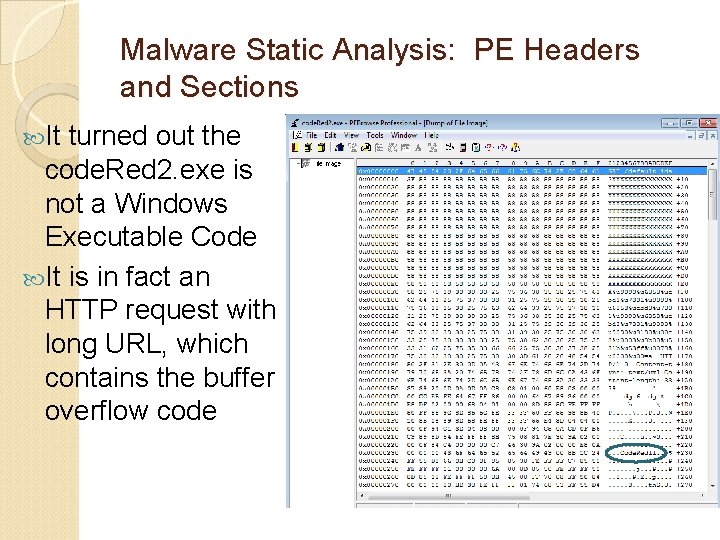
Malware Static Analysis: A Case Study Code. Red. 2 downloaded from http: //openmalware. org The executable file is compressed with password of “infected” When unzipping, it might trigger anti-virus alert and stop your unzipping action ◦ unzip it under your Win 7 VM (or any Win VM) since it has no anti-virus software to prevent this unzipping ◦ The malware PE code is named “malware. exe”, but don’t execute the malware code! ◦ In Linux, unzip it by “unzip -P infected zip. File. Name”

Code Red 2 The first Internet-wide fast spreading worm https: //en. wikipedia. org/wiki/Code_Red _II ◦ Incident: Aug. 4 th, 2001 ◦ Exploit a buffer overflow hole in Windows IIS server Appear in Web server log as:

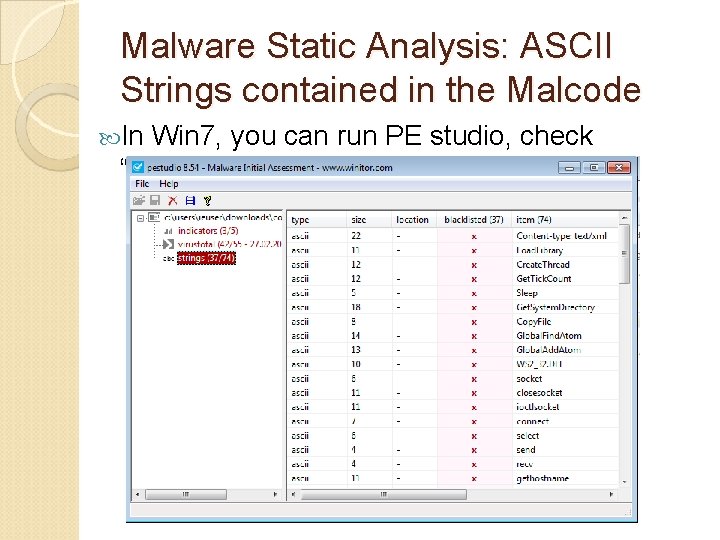
Malware Static Analysis: ASCII Strings contained in the Malcode In Win 7, you can run PE studio, check “strings” tab:

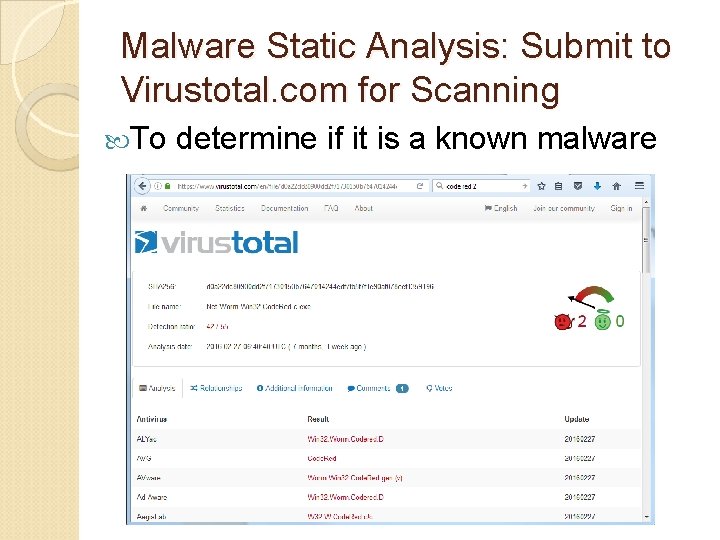
Malware Static Analysis: Submit to Virustotal. com for Scanning To determine if it is a known malware

Malware Static Analysis: PE Headers and Sections It turned out the code. Red 2. exe is not a Windows Executable Code It is in fact an HTTP request with long URL, which contains the buffer overflow code

Other Analysis on Code Red II http: //www. unixwiz. net/techtips/Code. R ed. II. html https: //www. grc. com/coderedii. htm

Malware Static Analysis: A Case Study Worm. My. Doom. I downloaded from http: //openmalware. org The executable file is compressed with password of “infected” When unzipping, it might trigger anti-virus alert and stop your unzipping action ◦ unzip it under your Win 7 VM (or any Win VM) since it has no anti-virus software to prevent this unzipping ◦ The malware PE code is named “malware. exe”, but don’t execute the malware code! ◦ In Linux, unzip it by “unzip -P infected zip. File. Name”

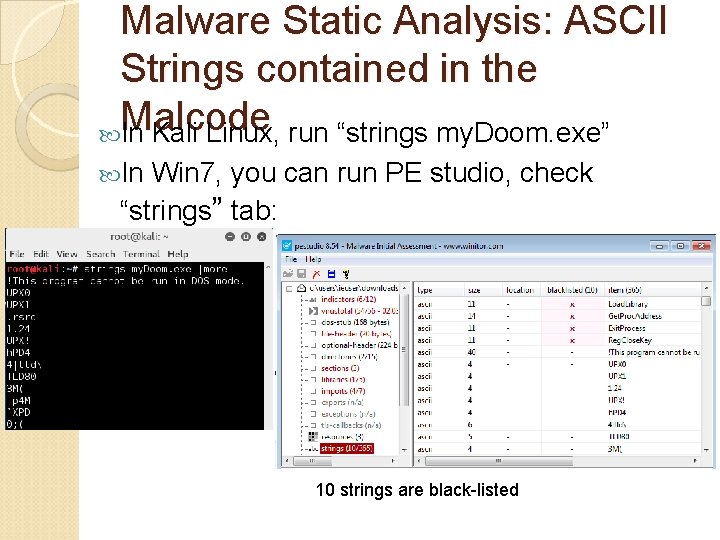
Malware Static Analysis: ASCII Strings contained in the Malcode In Kali Linux, run “strings my. Doom. exe” In Win 7, you can run PE studio, check “strings” tab: 10 strings are black-listed

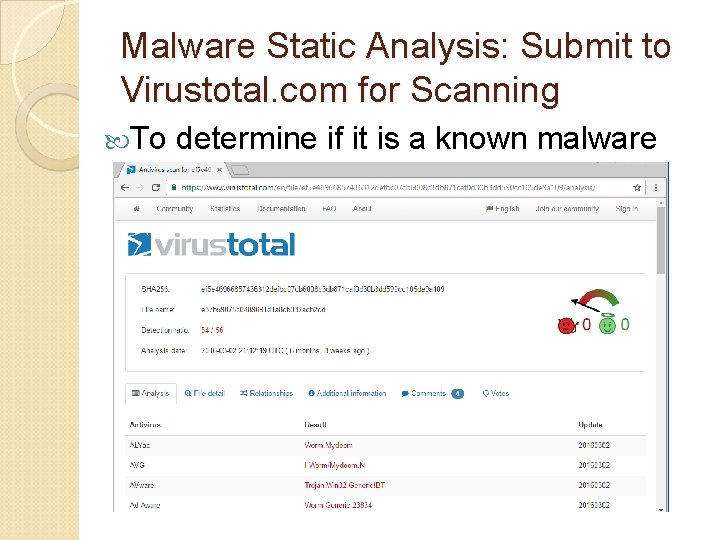
Malware Static Analysis: Submit to Virustotal. com for Scanning To determine if it is a known malware

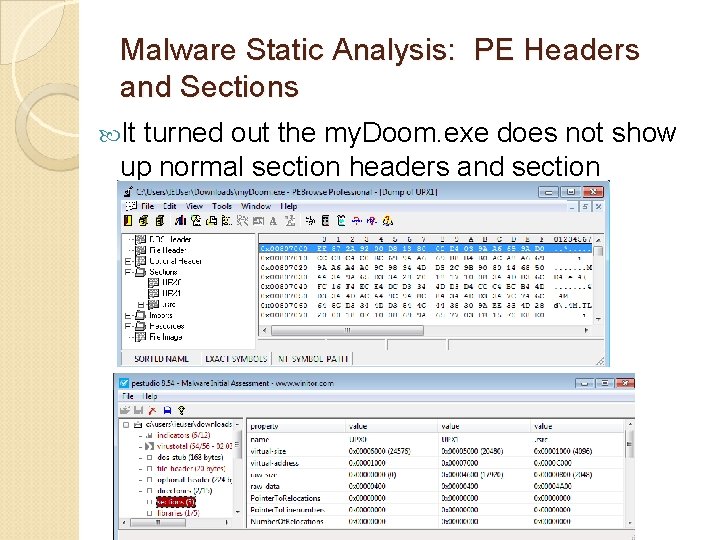
Malware Static Analysis: PE Headers and Sections It turned out the my. Doom. exe does not show up normal section headers and section contents

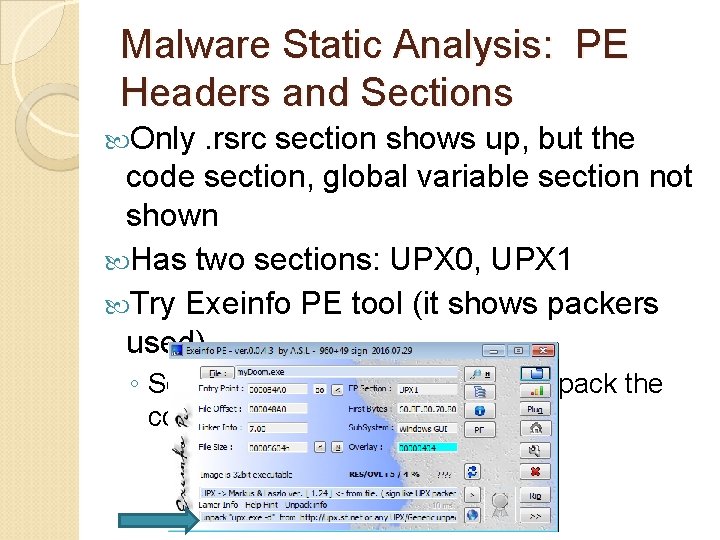
Malware Static Analysis: PE Headers and Sections Only . rsrc section shows up, but the code section, global variable section not shown Has two sections: UPX 0, UPX 1 Try Exeinfo PE tool (it shows packers used) ◦ So we can use “upx. exe -d” to unpack the code

Malware Static Analysis: Unpack a Malcode Exeinfo PE tells us to find upx. exe from http: //upx. sf. net ◦ Executable packer commonly used by virus writers ◦ Can compress wide range of files Windows PE executables, DOS COM files, and many more ◦ To unpack: upx. exe -d -o dest. exe source. exe Listing of executable packers - http: //en. wikipedia. org/wiki/Executable_compression

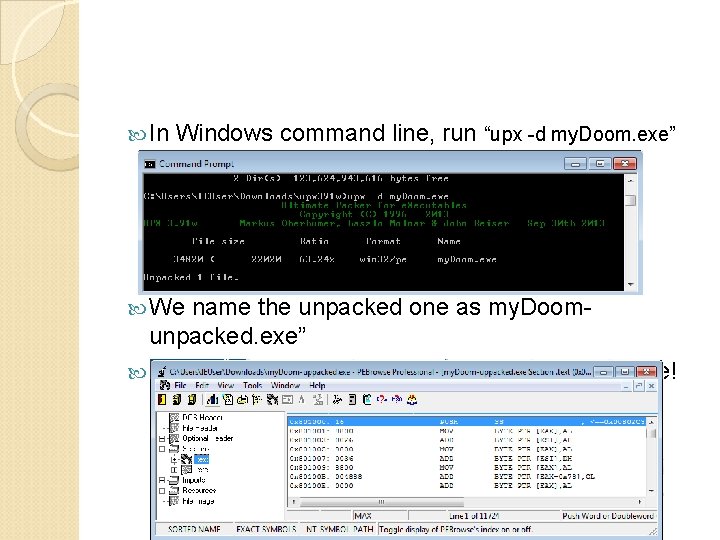
In Windows command line, run “upx -d my. Doom. exe” We name the unpacked one as my. Doomunpacked. exe” Now we can see the code section of the malcode!

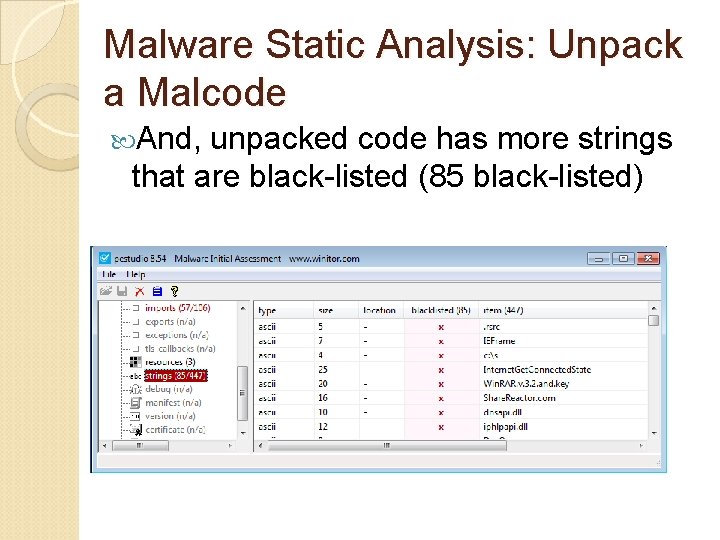
Malware Static Analysis: Unpack a Malcode And, unpacked code has more strings that are black-listed (85 black-listed)

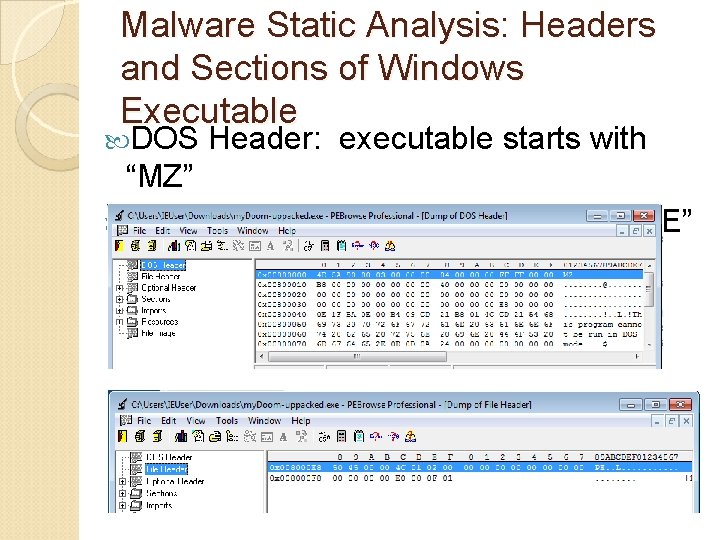
Malware Static Analysis: Headers and Sections of Windows Executable DOS Header: executable starts with “MZ” File Header: executable starts with “PE”

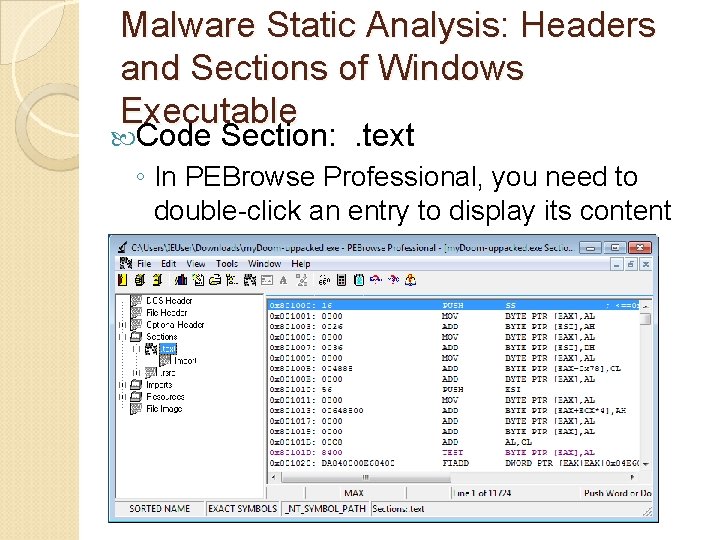
Malware Static Analysis: Headers and Sections of Windows Executable Code Section: . text ◦ In PEBrowse Professional, you need to double-click an entry to display its content

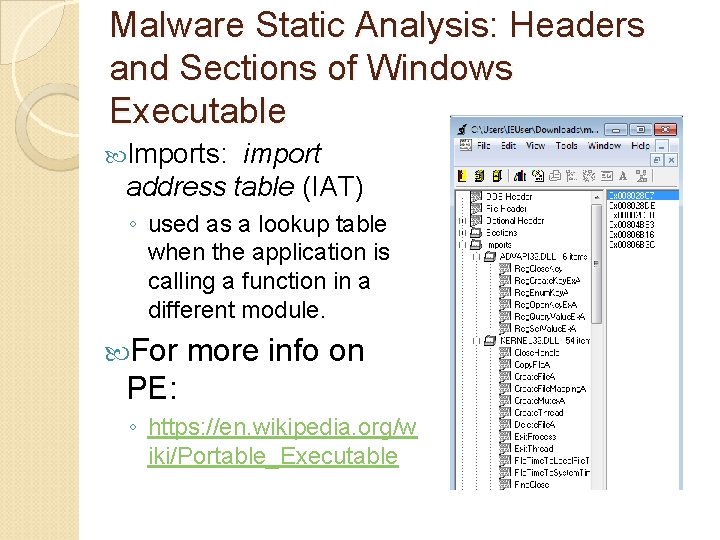
Malware Static Analysis: Headers and Sections of Windows Executable Imports: import address table (IAT) ◦ used as a lookup table when the application is calling a function in a different module. For more info on PE: ◦ https: //en. wikipedia. org/w iki/Portable_Executable