M Peter Adler JD LLM CISSP CIPP Adler








































- Slides: 43

M. Peter Adler JD, LLM, CISSP, CIPP Adler Info. Sec & Privacy Group LLC Federal E-Discovery Rules – Hindrance or Opportunity? EDUCAUSE LIVE! January 9, 2007

Agenda n Overview of the 12/1/06 Amendments to the Federal Rules of Civil Procedure concerning Discovery of Electronically Stored Information (ESI). n ESI Retention and Destruction Program Key Elements n Overlap with Privacy and Security Programs n Relationship with Litigation/Litigation n 2 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Discovery “The pretrial devices that can be used by one party to obtain facts and information about another party in order to assist the party’s preparation for trial. ” - Blacks Law Dictionary n The Federal Rules of Civil n And the following tools to Procedure provides the following discovery tools: n n n ensure or excuse discovery: Depositions Upon Written or Oral Written Questions (Rules 30, 31 and 32) Written Interrogatories (Rule 33) Production of Document or Things (Rule 34) Permission to Enter Upon Land for Inspection and Other Purposes (Rule 34) Physical and Mental Examinations (Rule 35) Requests for Admission (Rule 36) n n n Motion to Compel (Rule 37(a)) Protective Orders (Rule 26(c)) Sanctions (Rule 37 (b), (c)&(d)) 3 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Potential Sources of ESI n Configuration of computers n n n n workstations and file servers Mirror disks Swap files Removable media (diskettes, fobs, tapes, etc. ) Metadata n Temporary files and fragments n Histories n Embedded comments Audit trails and log files Access control lists (ACL) EDI and VAN Legacy Systems n n n n n Internet information Corporate intranets Email Home Computers and laptops PDAs Backup tapes and facilities “Deleted” files Peripherals Non-textual electronic devices See also, Chapters I and IV of the Federal Guidelines for Searching and Seizing Computers for additional sources of Electronic Evidence n http: //www. usdoj. gov/criminal/cyb ercrime/s&smanual 2002. htm 4 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Overview of Federal Rules of Civil Procedure Relating to ESI n New and amended rules of civil procedure governing the treatment of electronically stored information (ESI) were effective December 1, 2006. n These Rules are broken into the following categories: n Early attention to ESI discovery issues: Rules 26(a) and (f) and 16 (b) n Better management of discovery of ESI that is not reasonably accessible: Rule 26(b)(2) n Procedure for assertions of privilege after production: Rule 26(b)(5) n Interrogatories and Requests for Production of ESI: Rules 33(d) and 34(a) and (b) n Sanctions pertaining to ESI: Rule 37(f) n Note: As always, the Amended Rules may be subject to Local rules that impose more specific obligations on the parties. 5 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Early Attention to ESI Discovery Issues n Rules 26(f) and 16(b) n Require that parties to a federal case consider, at the start of the case, the manner in which ESI will be preserved, maintained and provided. n Rule 26(a) n As part of their automatic initial disclosures, the Rule has been amended to include copies or descriptions of the categories or locations of ESI that the disclosing party may use to support its claims or defenses. 6 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Rule 26(f) Amendments n “(f)…discuss any issues relating to preserving discoverable information and to develop a proposed discovery plan…concerning: n n (3) any issues relating to disclosure or discovery of electronically stored information, including the form or forms in which it should be produced; (4) any issues relating to claims of privilege or protection as trial-preparation material, including – if the parties agree on a procedure to assert such claims after production – whether to ask the court to include their agreement in an order; ” 7 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Rule 26(f) ESI Issues to be Discussed n Topics for discovery and time period n Sources within the parties control that should be searched for ESI n Whether the information is reasonably accessible to the party that has it (including burden and cost of retrieval) Rule 26(b)(2)(B) n Form or forms in which the information may be produced (See Rule 34(b)) n Issues relating to preservation of discoverable information n Balance between competing needs to preserve relevant evident and continued operations. (Rule 37) n See discussion on ESI retention program n Assertions of privilege or of protection as trial preparation materials (Rule 26(b)(5)) n Can parties through agreement prepare procedures for asserting such claims and avoiding waiver of privilege? 8 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Meeting of Parties: Timing n The parties should meet to address ESI issues as soon as possible under Rule 26(f) provides that the parties are to confer 21 days before the Rule 16(b) scheduling conference. n The Rule 16(b) scheduling conference is to be held 120 days after the complaint is filed. n That leaves 99 days to get the ESI issues worked out. n 9 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Early Attention to Electronic Discovery: Rule 16(b) Pretrial Conference n n Form 35, is appendix to the Rules intended to serve as a model for a joint report of the parties to the court on the outcome of the Rule 26(f) conference; and the basis for the Rule 16(b) pretrial conference with the judge The Rule 16(b) pretrial conference will result in a scheduling order delimiting time for discovery, filing motions and other pretrial activities. n Amended Rule 16(b) provides that the scheduling order may include: n n provisions for disclosure or discovery of ESI any agreements the parties reach for asserting claims of privilege or protection as trial-preparation material after production 10 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Early Attention to Electronic Discovery: Automatic Initial Discovery Rule 26(a) n Rule 26(a) provides that litigants must include, as part of their automatic initial disclosures, the following information (except when it is used solely for impeachment): n n The name, and if known, the address and telephone number of each individual likely to have discoverable information that the disclosing party may use to support its claim or defenses, identifying the subjects of the information; and A copy of or a description by category and location of ESI that are in the possession, custody or control of the party and that the disclosing party may use to support its claims or defenses. 11 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Discovery of ESI that is “Not Reasonably Accessible” Rule 26(b)(2)(B) n Under Rule 26(b) a responding party should produce ESI that is relevant, not privileged and reasonably accessible n Rule 26(b)(2)(B) provides that a party need not provide discovery of ESI from sources that the party identifies as not reasonably accessible because of undue burden or cost n Initially, the producing party makes the call on what reasonably accessible ESI it will produce 12 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Reasonably Accessible ESI n No hard rule, but will be ultimately determined on a case-by-case basis. n “Accessible information is electronically-stored information that is easily retrievable in the ordinary course of business without undue cost and burden. ” State Trial Court Guidelines, 1. B. n “ESI is reasonably accessible when it is stored in a readily usable format that “does not need to be restored or otherwise manipulated to be usable. ” Quinby v. West. LB, 2006 WL 2597900 at *7 (S. D. N. Y. , September 2006 (quoting Zubulake v. USB Warburg, LLC, 217 F. R. D. 309, 320 (S. D. N. Y. 2003) (Zubulake I)) 13 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Not Reasonably Accessible ESI n Although a decision on whether ESI is not reasonably accessible is made on a case-by-case basis, the Advisory Committee to the Rules identified the following as potential sources of ESI that is not readily accessible: n Back up tapes intended for disaster recovery purposes that are not indexed, organized or susceptible to electronic searching; n Legacy data from obsolete systems that is unintelligible on current systems; n “deleted data that remains in fragmented form but would require forensics specialists for reconstruction; or n Databases designed to create information only in certain ways not easily amenable to production. n Backup tapes were considered not reasonably accessible in Zubulake v. USB Warburg, LLC 217 F. R. D. 309 (S. D. N. Y. 2003) (Zubulake III), 14 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Challenging a Claim that ESI is Not Reasonably Accessible n The Rules include a two-step procedure when dealing with ESI that is not reasonably accessible: n n On motion to compel discovery (Rule 37) by requesting party or for a protective order (Rule 26(c)) by producing party, the party from whom the information is sought must show that the information not reasonably accessible because of undue burden or cost If that showing is made, the court may nonetheless order discovery from such sources if the requesting party shows good cause 15 January 9, 2007 Adler Info. Sec & Privacy Group LLC

“Good Cause” n Even if a source of ESI is not reasonably accessible, the requesting party may still obtain discovery by showing good cause by balancing the costs and potential benefits, looking at: (1) (2) (3) (4) (5) (6) January 9, 2007 the specificity of the discovery request; the quantity of information available from other and more easily accessed sources; the failure to produce relevant information that seems likely to have existed but is no longer available on more easily accessed sources; the likelihood of finding relevant, responsive information that cannot be obtained from other, more easily accessed sources; predictions as to the importance and usefulness of the further information; and the importance of the issues at stake in the litigation; 16 and the parties' resources. Adler Info. Sec & Privacy Group LLC

Options Available to Court: General Bases for Denial n Even with the showing of good cause, the court may deny discovery if it determines: n n n The discovery sought is unreasonably cumulative or duplicative or is otherwise obtainable from another source that is more convenient, less burdensome, or less expensive; The party seeking discovery has had ample opportunity by discovery in the action to obtain the information sought; or The burden or expense of the proposed discovery outweighs its likely benefit, taking into account the needs of the case, the amount in controversy, the parties’ resources, the importance of the issues at stake in the litigation, and the importance of the proposed discovery in resolving issues. 17 January 9, 2007 Adler Info. Sec & Privacy Group LLC

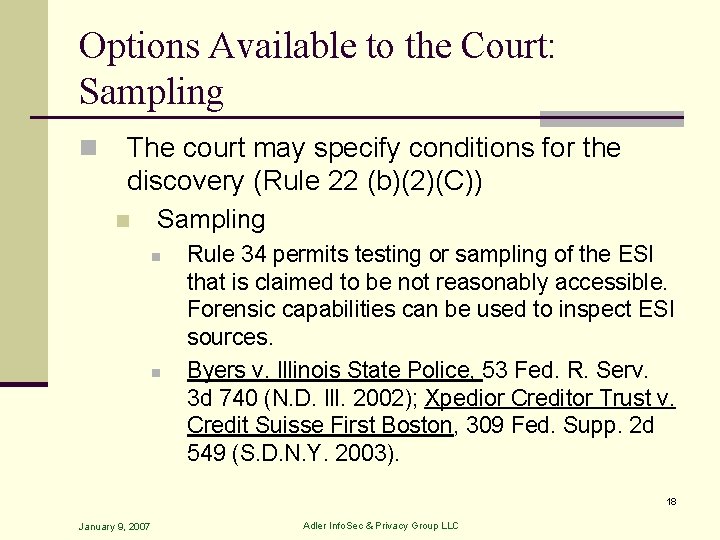
Options Available to the Court: Sampling n The court may specify conditions for the discovery (Rule 22 (b)(2)(C)) n Sampling n n Rule 34 permits testing or sampling of the ESI that is claimed to be not reasonably accessible. Forensic capabilities can be used to inspect ESI sources. Byers v. Illinois State Police, 53 Fed. R. Serv. 3 d 740 (N. D. Ill. 2002); Xpedior Creditor Trust v. Credit Suisse First Boston, 309 Fed. Supp. 2 d 549 (S. D. N. Y. 2003). 18 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Options Available to the Court: Cost Shifting n There is a presumption that the responding party must bear the expense of complying with discovery requests. Oppenheimer Fund, Inc. v. Saunders, 437 U. S. 340, 358 (1978). n A court may issue an order protecting the responding party from undue burden or expense by “conditioning discovery on the requesting party’s payment of the cost of discovery. ” Oppenheimer Fund, Inc. v. Saunders, 437 U. S. 340, 358 (1978); Zubulake v. USB Warburg LLC, 216 F. R. D. 280, 283 (S. D. N. Y. 2003) (Zubulake III) n The order may be granted only on a motion for a protective order brought by the responding party and only for good cause shown. Rule 26(c) n The responding party has the burden of proof on a motion for cost-shifting. Quinby v. West. LB, 2006 WL 2597900 at *7 (S. D. N. Y. , September 2006) (quoting Zubulake v. UBS Warburg LLC, 216 F. R. D. 280, 283 (S. D. N. Y. 2003) (Zubulake III)) 19 January 9, 2007 Adler Info. Sec & Privacy Group LLC

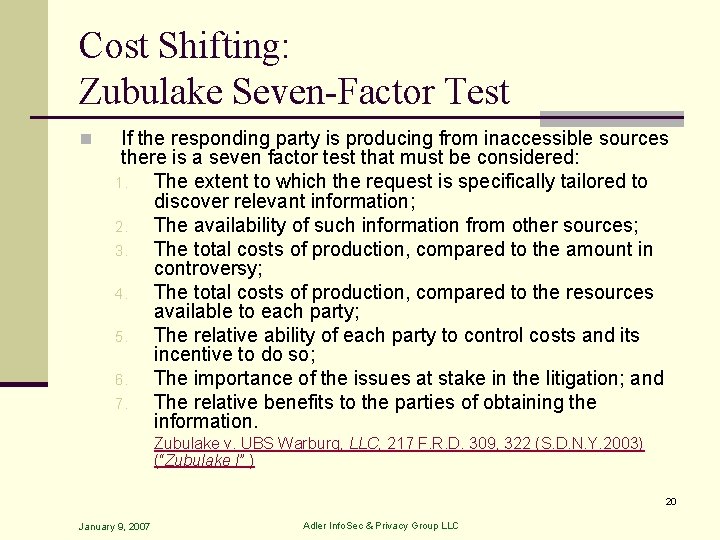
Cost Shifting: Zubulake Seven-Factor Test n If the responding party is producing from inaccessible sources there is a seven factor test that must be considered: 1. The extent to which the request is specifically tailored to discover relevant information; 2. The availability of such information from other sources; 3. The total costs of production, compared to the amount in controversy; 4. The total costs of production, compared to the resources available to each party; 5. The relative ability of each party to control costs and its incentive to do so; 6. The importance of the issues at stake in the litigation; and 7. The relative benefits to the parties of obtaining the information. Zubulake v. UBS Warburg, LLC, 217 F. R. D. 309, 322 (S. D. N. Y. 2003) (“Zubulake I” ) 20 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Production of ESI: Rule 34 n Rule 34(a) Adds ESI as a category subject to production in addition to “documents. ” n Rule 34(b) adds procedures for requesting and objecting to the form for producing information and provides default forms of production. 21 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Production: Rule 34(a) n Production requests covers documents and ESI: n Including writings drawings, graphs, charts, photographs, sound recordings, images and other data or data compilations stored in any medium from which the information can be obtained. 22 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Form or Forms of ESI Production: Rule 34(b) The form or form of the ESI can be agreed in the initial meeting described in Rule 26(f). If the parties do not reach agreement, Rule 34(b) provides a default procedure for production of ESI. n n n n A request may specify the form or forms of the ESI to be produced. Responding party may object (in writing within 30 days after the request is served) to the requested form or forms of the ESI, stating the reasons for objection. If a request does not specify the form or forms for producing ESI, a responding party must produce the ESI in a form or forms in which it is ordinarily maintained or in a form or forms that is readily usable. If an objection is not received or no form is specified, the responding party must identify the form it has chosen in its Rule 34 response. If the form or forms are disputed: n n January 9, 2007 The requesting party then can move to compel production in a different form; or The producing party may seek a protective order. Adler Info. Sec & Privacy Group LLC 23

Sampling, Inspections, Tests n Amended Rule 34(a)(1) provides that parties may request an opportunity to inspect, copy, test or sample ESI sought. n Burden and intrusiveness can be addressed under Rules 26(b)(2) and 26(c). Issues of privacy, security, trade secrets, etc. n Does not include a routine right of access to a party’s information system, although access may be justified in some instances. n 24 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Privilege and other Limits on Discoverability n Attorney-Client Privilege n Work Product Doctrine (Trial Preparation) n Trade Secrets and Proprietary Information n Copyright and License Restrictions 25 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Privilege and ESI: Rule 26(b)(5) n Guarding against privilege waiver is more difficult when discovery of ESI is sought. n n The volume of the available information is enormous. The forms in which ESI is stored make review and determination more difficult, expensive and timeconsuming and less likely to detect all privileged information. Inadvertent production and waiver may occur. The failure to screen out even one privileged item may result in an argument that there has been a waiver as to all other privileged materials related to the same subject matter. 26 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Procedure: Asserting Party n A party asserting a claim of privileged must give notice to the receiving party: In writing, unless circumstances preclude it (e. g. , during deposition); n Specifically identifying the information and stating the basis for the claim; and n Detailed enough to enable the receiving party and the court to understand the claim basis and whether waiver has occurred. n 27 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Procedure: Receiving Party n After receiving notice, each party that received the information must promptly return, sequester, or destroy the information, and: n n May not use or disclose the information pending resolution of the privilege claim; and Must retrieve all information disclosed to third parties prior to receiving notice. n The receiving party may present to the court questions whether the information is privileged or protection has been waived. n The party must provide the court and producing parties notice and serve all parties. 28 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Interrogatories: Rule 33(d) n Permits analysis of records, including ESI, to answer interrogatories when the cost is roughly the same for both parties n Cost analysis will be key: n Do costs include overhead costs of maintaining the necessary hardware and software and training personnel to use them? n May not be a good option considering potential business disruption, security compromise and privilege issues involved in having opponent access the system. n Better answer may be to produce the ESI 29 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Discovery of ESI from Non-Parties through Subpoena: Rule 45 n Applies to entities that operate computer networks for persons in litigation (e. g. , ISPs, ASPs, employers, schools). n These non-parties are increasingly being asked to respond to subpoenas for ESI about a party’s computer use. n The amended Rule adds ESI and requires non-parties to face the same questions of preservation, cost, privilege, accessibility and form of production as parties. n Upon receipt of the subpoena, the non party to discuss with the requesting party about the scope of the request, protective measures and costs. n Court will relieve nonparties from “substantial costs” rather than “undue burden” which is a lower threshold 30 January 9, 2007 Adler Info. Sec & Privacy Group LLC

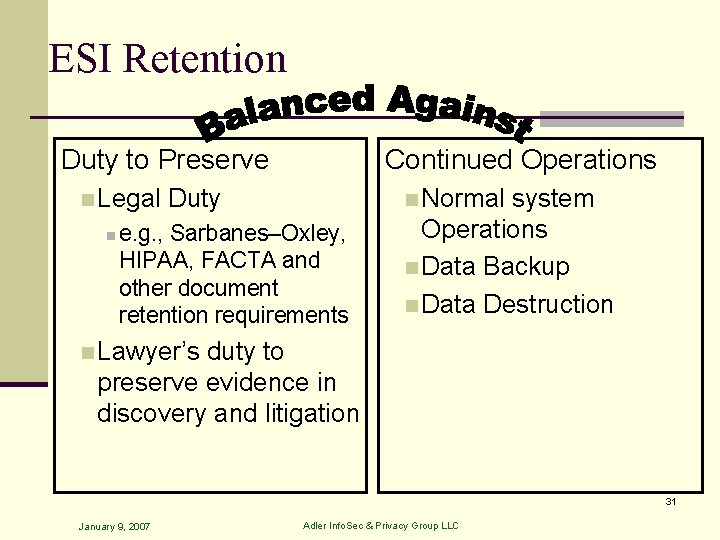
ESI Retention Duty to Preserve n Legal n Continued Operations Duty n Normal e. g. , Sarbanes–Oxley, HIPAA, FACTA and other document retention requirements system Operations n Data Backup n Data Destruction n Lawyer’s duty to preserve evidence in discovery and litigation 31 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Duty to Preserve n Duty attaches when a person knows or reasonably anticipates litigation involving identifiable parties and identifiable facts. n Encompasses potential evidence related to identifiable facts, which may shift as litigation proceeds. Stevenson v. Union Pac. R. R. , 354 F. 3 d 739 (8 th Cir. 2004) n Exists independent of any preservation demand letter, or court order. Wigington v. Ellis, 2003 WL 22439865 (N. D. Ill. 2003) (Wigington I); Treppel v. Biovail Corp. , 233 F. R. D. 363 (S. D. N. Y 2006). n The fact that ESI is not reasonably accessible does not relieve a party from its duty to preserve the information if potentially relevant. Zubulake v. UBS Warburg LLC, 220 F. R. D. 212 (S. D. N. Y. 2003) (“Zubulake IV”) 32 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Failure to Preserve: Sanctions for Spoliation n Duty to monitor preservation falls on inside and outside counsel. n Potential sanctions will vary on intent and behavior of producing party (bad faith, gross negligence, negligence) and degree of prejudice to the requesting party caused by spoliation. Possible sanctions include: n n n Fines; Adverse inference jury instruction; Striking of a pleading or defense; Dismissal or default; and Costs for supplemental discovery. 33 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Right to Destroy n Courts have acknowledged that organizations have the right to destroy - whether or not it is consciously deleted - electronic information that does not meet the internal criteria of information or records requiring retention. n “‘Document retention policies, ’ which are created in part to keep certain information from getting into the hands of others, including the Government, are common in business …. It is, of course, not wrongful for a manager to instruct his employees to comply with a valid document retention policy under ordinary circumstances’ Arthur Andersen, LLP v. United States, 125 S. Ct. 2129, 2135 (2005). 34 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Safe Harbor: Rule 37(f) n The court will not impose sanctions parties who fail to produce ESI that was lost as a result of routine, good faith operation of an electronic information system, absent exceptional circumstances. Rule 37(f) n Good faith destruction of potentially relevant ESI will be difficult to establish when there is a claim pending or has received a credible threat of a claim. n A Committee Note to Rule 37 (f) states: “Good Faith in the routine operation of an information system may involve a party’s intervention to modify or suspend certain features of that routine operation to prevent the loss of information if that information is subject to a preservation obligation. 35 January 9, 2007 Adler Info. Sec & Privacy Group LLC

ESI Production – Responding Party n Identifying ESI. n Locating ESI on media and information systems using staten n n of-the-art applications and forensic capabilities. Retrieving ESI using specialized computer hardware and software and computer forensics methods. Preserving ESI and providing notices to personnel and placing holds on destruction of the information. In this phase document retention procedures for preserving ESI are invoked. Analyzing ESI to determine which is relevant and responsive. Sorting through ESI and removing privileged electronic information and records from the production set and prepare logs in compliance with applicable law. Producing ESI to the opposing party in an accessible or agreed to form. 36 January 9, 2007 Adler Info. Sec & Privacy Group LLC

ESI Retention Risks n Spoliation and Sanction Risks. Because of retention duties, a party persuade the court that those documents that no longer exist were purged pursuant to a policy and were not willfully destroyed or spoliated. n Cost of Retrieval Risk. Knowing where information is stored or if it has been destroyed pursuant to document retention policies will avoid the high costs associated with e-discovery fishing expeditions. n Inability to Defend Risk. The loss of critical evidence potentially leads to the inability to properly defend a claim. 37 January 9, 2007 Adler Info. Sec & Privacy Group LLC

ESI Retention Program n Compliance and Auditing Plan n Create or Amend Policy on ESI Retention and Destruction n Indexing and Document Naming System n Attorney-Client Privilege Procedures n Litigation Hold Procedures n Employee Training n Post-Implementation Compliance and Auditing 38 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Hindrance or Opportunity? n An ESI Management Program contains many of the elements found in security and privacy programs. n Removal of sensitive ESI on a regular basis will enhance an organization’s privacy and security. 39 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Examples of Overlap of elements of ESI, Security and Privacy Programs n n Data classification Map data flow Identify systems Evaluate IT function in creation, receipt transmission and processing of data n n n System Backup Access rights Third party contracts Roles and responsibilities Management of email n Procedures for storage of confidential, restricted access electronic records n Formal technology standards (ISO 17799, ISO 15489) n Auditing and review function January 9, 2007 Adler Info. Sec & Privacy Group LLC 40

ESI Retention n Review Written vs. Actual ESI Retention Practices Creation n Use n Disposal n n Are electronic records being kept as required by law and internal procedures? n Are electronic records being managed over their entire lifecycle? 41 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Litigation/Investigations n Procedures, roles and responsibilities for identifying and retrieving ESI. n Does offsite storage of ESI exist? If so, is it indexed or stored in a manner that adequately identifies them? n Litigation Hold n n n What is the process for determining when a claim arises? Responsibility for determining necessity for litigation hold? n How is it authorized and communicated? n Scope? n What is the time frame? Where are suspended electronic records kept? How is the end of the litigation hold communicated, carried out and monitored? What are the procedures for disposal of electronic records after a case closes? 42 January 9, 2007 Adler Info. Sec & Privacy Group LLC

Contact Information M. Peter Adler Info. Sec & Privacy Group LLC 2103 Windsor Road Alexandria, VA 22307 Telephone: (202) 251 -7600 Facsimile: (703) 997. 5633 Email: adler@adleripg. com 43 January 9, 2007 Adler Info. Sec & Privacy Group LLC