Risk Assessment The Cornerstone of Information Security Gerhard
















- Slides: 19

Risk Assessment – The Cornerstone of Information Security Gerhard Steinke, Ph. D, CISSP Seattle Pacific University gsteinke@spu. edu INTERNATIONAL CYBER SECURITY AND POLICING CONFERENCE AUGUST 22 -23, 2014 Kochi, India

Alternate Titles: Risk Assessment The Cornerstone of your Information Security and Risk Management Planning How do you know what controls you have? How do you know if your controls are working? Additional Benefits/Applications for your Risk Assessment


Security Risks n n n Business/Strategic ¨ Risks that impact the mission/brand/image of the organization Financial ¨ Risks that cause a measurable financial impact. Operational ¨ Risks that impact productivity and carry an opportunity cost. ¨ Risk that information and information systems are compromised 4

Assess Risk. Each organization should: 1. Identify reasonably foreseeable internal and external threats that could result in unauthorized disclosure, misuse, alteration, or destruction of personal information or information systems; 2. Assess the likelihood and potential damage of these threats, taking into consideration the sensitivity of personal information; and 3. Assess the sufficiency of policies, procedures, information systems, and other arrangements in place to control risks. From: Guidelines for Safeguarding Member Information - Appendix A 12 CFR 748

1. Identify reasonably foreseeable internal and external threats… Rogue Insiders Software Bugs Corporate Spies Script Kiddies Password Crackers vulnerabilities Web Defacements Network “Sneak Denial of Service War Drivers er. Net”Trojans Backdoors Worms Employee Error Buffer Overflows “Blended Viruses Threats” 6

How to Organize the Threats / Vulnerabilities n Perhaps by Assets ¨ Hardware ¨ Software ¨ Data ¨ Supplies ¨ Physical plant ¨ Funds ¨ Goodwill ¨ People and skills n Perhaps by Threat Category ¨ Accidents, Errors ¨ Physical ¨ Authorization ¨ Authentication ¨ Network Configuration ¨ Server Configuration ¨ Malware ¨ Perimeter ¨ Remote Access ¨ Security Administration 7

Threats n n n n n n n T 01 T 02 T 03 T 04 T 05 T 06 T 07 T 08 T 09 T 10 T 11 T 12 T 13 T 14 T 15 T 16 T 17 T 18 T 19 T 20 T 21 T 22 T 23 T 24 T 25 (from NIST FIPS PUB 65) Access (Unauthorized to System - logical) Access (Unauthorized to Area - physical) Airborne Particles (Dust) Air Conditioning Failure Application Program Change (Unauthorized) Bomb Threat Chemical Spill Civil Disturbance Communications Failure Data Alteration (Error) Data Alteration (Deliberate) Data Destruction (Error) Data Destruction (Deliberate) Data Disclosure (Unauthorized) Disgruntled Employee Earthquakes Errors (All Types) Electro-Magnetic Interference Emanations Detection Explosion (Internal) Fire, Catastrophic Fire, Major Fire, Minor Floods/Water Damage Fraud/Embezzlement n n n n n n n T 26 T 27 T 28 T 29 T 30 T 31 T 32 T 33 T 34 T 35 T 36 T 37 T 38 T 39 T 40 T 41 T 42 T 43 T 44 T 45 T 46 T 47 T 48 T 49 T 50 Hardware Failure/Malfunction Hurricanes Injury/Illness (Personal) Lightning Storm Liquid Leaking (Any) Loss of Data/Software Marking of Data/Media Improperly Misuse of Computer/Resource Nuclear Mishap Operating System Penetration/Alteration Operator Error Power Fluctuation (Brown/Transients) Power Loss Programming Error/Bug Sabotage Static Electricity Storms (Snow/Ice/Wind) System Software Alteration Terrorist Actions Theft (Data/Hardware/Software) Tornado Tsunami (Pacific area only) Vandalism Virus/Worm (Computer) Volcanic Eruption 8

Vulnerabilities n n n Physical V 01 Susceptible to unauthorized building access V 02 Computer Room susceptible to unauthorized access V 03 Media Library susceptible to unauthorized access V 04 Inadequate visitor control procedures (and 36 more) n n n n Administrative V 41 Lack of management support for security V 42 No separation of duties policy V 43 Inadequate/no computer security plan policy V 44 Inadequate/no computer security awareness training plan V 45 No ADP Security Officer and assistant assigned in writing V 46 Inadequate/no backup plan V 47 Inadequate/no emergency action plan (and 7 more) n n n n Personnel V 56 Inadequate personnel screening V 57 Personnel not adequately trained in job Software V 62 Inadequate/missing audit trail capability V 63 Audit trail log not reviewed weekly V 64 Inadequate control over application/program changes Communications V 87 Inadequate communications system V 88 Lack of encryption V 89 Potential for disruptions Hardware V 92 Lack of hardware inventory V 93 Inadequate monitoring of maintenance personnel V 94 No preventive maintenance program 9

2. Assess the Likelihood and Potential Damage… H, M, L n Quantitative vs. Qualitative n External reports and consultants n

Likelihood and Impact / Potential Damage n Quantitative Probability of event occurring ¨ Assigning real numbers to costs of safeguards and damage ¨ By quantifying the risk, we can justify the benefit of spending money to implement controls ¨ n Qualitative Judging an organization’s risk to threats ¨ Based on judgment, intuition, and experience ¨ Ranks the seriousness of the threats for the sensitivity of the assets ¨ 11

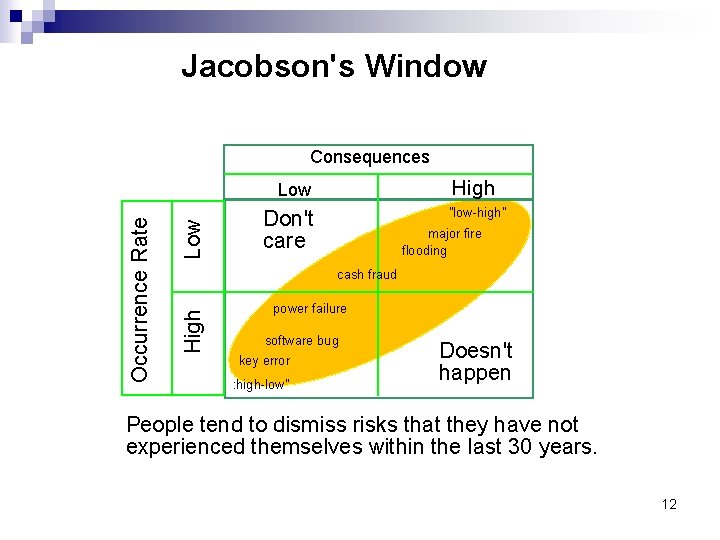
Jacobson's Window Consequences High Low "low-high" Don't care major fire flooding cash fraud High Occurrence Rate Low power failure software bug key error : high-low" Doesn't happen People tend to dismiss risks that they have not experienced themselves within the last 30 years. 12

3. Assess the sufficiency of policies, procedures, information systems, and other arrangements in place to control risks… n Controls / Countermeasure ¨ n Any process, procedure, product, feature or function that will restrict/block access, deter, or lower the occurrence of a threat/vulnerability within the specified environment Test the controls Who tests? ¨ How frequently? ¨ n Are the controls effective?

Controls / Safeguards n Cryptographic controls n Data base access controls n Secure protocols n Data base reliability controls n Program development controls n Data base inference controls n n Program execution environment controls n Multilevel security for operating systems, data, and data bases Operating system protection features n Personal computer controls Identification n Authentication n Network access controls n Secure operating system design and implementation n Network integrity controls n Controls on telecommunications media n Physical controls n Security in Computing, C. Pfleeger 14

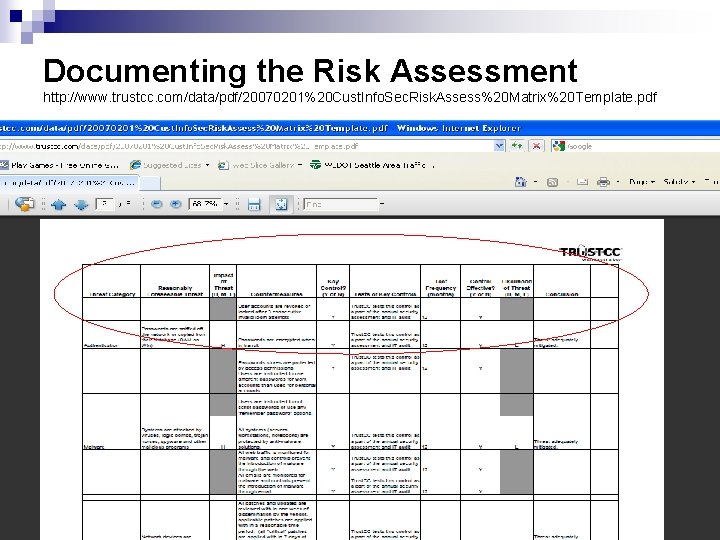
Documenting the Risk Assessment http: //www. trustcc. com/data/pdf/20070201%20 Cust. Info. Sec. Risk. Assess%20 Matrix%20 Template. pdf

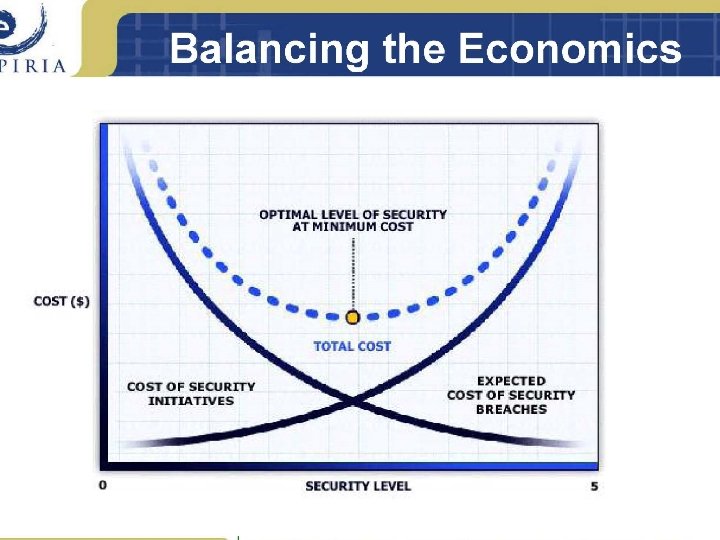
After the Risk Assessment - Now what? n n n Examine controls – are they working? Where do we need more/different controls? What about cost of controls? Evaluate alternatives, effectiveness, costs of countermeasures Indicate where to most effectively use your limited resources Look at ROI… 16

17

Further Benefits of Risk Analysis n n Improved awareness by customers, users and management Documentation of assets, their vulnerabilities and controls Provides an accountable basis for security reviews, penetration testing Provides accountable justification for expenditure on controls and countermeasures 18

 Is a cornerstone in the protection of information assets
Is a cornerstone in the protection of information assets Market risk assessment
Market risk assessment Security private
Security private Visa international security model in information security
Visa international security model in information security Nstissc security model
Nstissc security model Rais toxicity
Rais toxicity Cornerstone bible institute
Cornerstone bible institute The chief cornerstone high school
The chief cornerstone high school Christ alone cornerstone weak made strong
Christ alone cornerstone weak made strong Define chief cornerstone
Define chief cornerstone Cornerstone big data
Cornerstone big data Cornerstone employer
Cornerstone employer Scintilla charter academy uniforms
Scintilla charter academy uniforms Identify the cornerstones of the wellness movement
Identify the cornerstones of the wellness movement Cornerstone
Cornerstone Lesson 1 american free enterprise capitalism answers
Lesson 1 american free enterprise capitalism answers Cornerstone congregational church
Cornerstone congregational church Change management crm
Change management crm Walter gerhard
Walter gerhard Lutz sperling
Lutz sperling


































