LM 5 DataOriented Wireless Network IT 48336833 Dr











- Slides: 56

LM 5. Data-Oriented Wireless Network IT 4833/6833 Dr. Lei Li Note: The content of this slides are adapted from the material provided by Dr. Edward Jung and Dr. Yang Ming

Road Map Introduction Network Security Wireless Network Wireless Security Special Topic Intro. to Network Security Protocols Voice-Oriented Network Traditional Wireless Network Mobile Security & Cryptography Security & Layered Architecture Data-Oriented Network Wireless LAN Wireless Ad Hoc Network 2

Learning Objectives �After this chapter, student will be able to: �Describe how WLAN is different from LAN and WAN �Define a typical 802. 11 network and describe different standards within 802. 11 �Explain the connection setup process in 802. 11 �Define MANET and describe its main characteristics �Explain the routing and address allocation in MANET �Describe Bluetooth technology 3

INTRODUCTION • • • One of the fastest-growing technologies The demand is increasing everywhere Wireless LANs can be found on everywhere

WLAN Characteristics • • WAN: AMPS, GSM, UMTS; 802. 11 vs. 3 G/4 G cellphone network connectivity; WLAN vs. LAN • Setting up WLANs is much easier than setting up LANs; • Packet loss experienced in WLANs is much more than that in wired LANs. 802. 11 standard is that it operates in the unlicensed frequency spectrum.

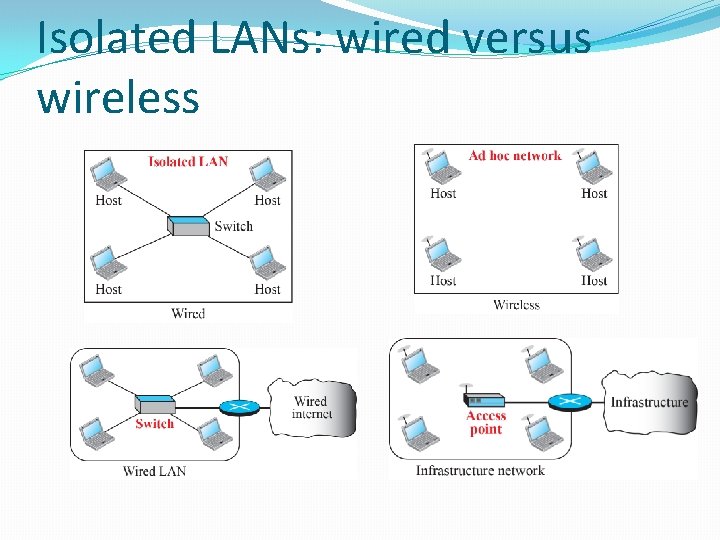
Isolated LANs: wired versus wireless

IEEE 802. 11 Wireless LAN � 802. 11 a � 5 -6 GHz range � up to 54 Mbps � 802. 11 b � 2. 4 -5 GHz unlicensed spectrum � up to 11 Mbps � direct sequence spread spectrum (DSSS) in physical layer � all hosts use same chipping code � 802. 11 g � 2. 4 -5 GHz range � up to 54 Mbps � 802. 11 n: multiple antennas � 2. 4 -5 GHz range � up to 200 Mbps 7

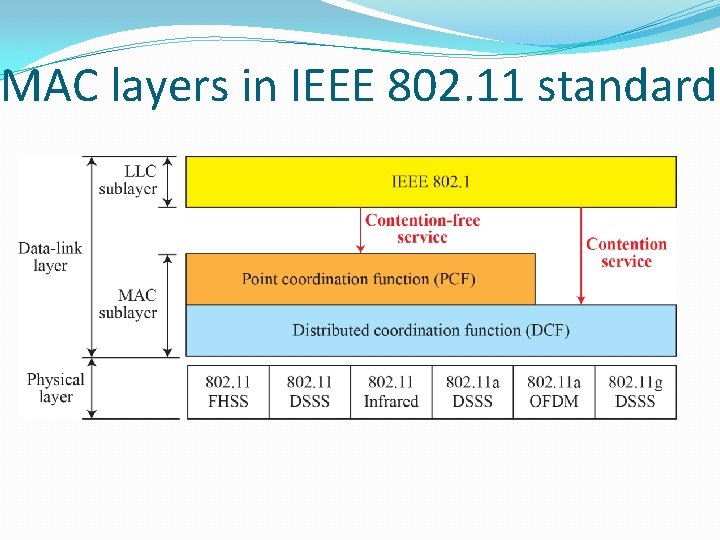
WLANs �IEEE 802. 11 WLAN standards : defines Layer 1 and 2 specification 802. 11 in the OSI 8

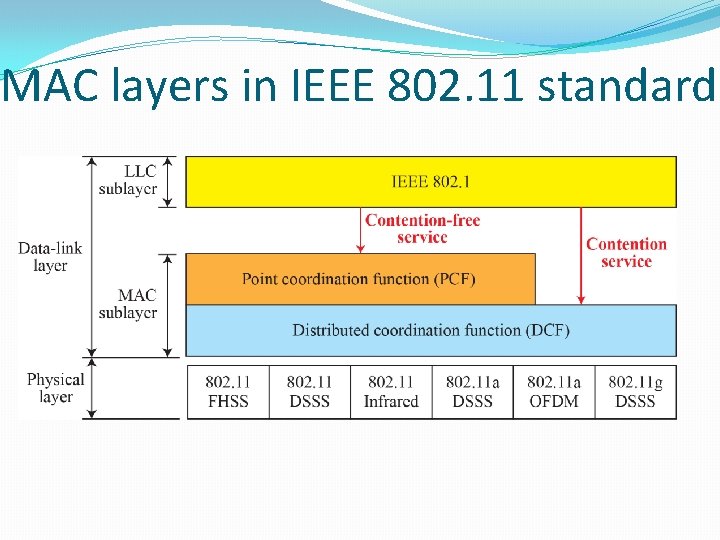
MAC layers in IEEE 802. 11 standard

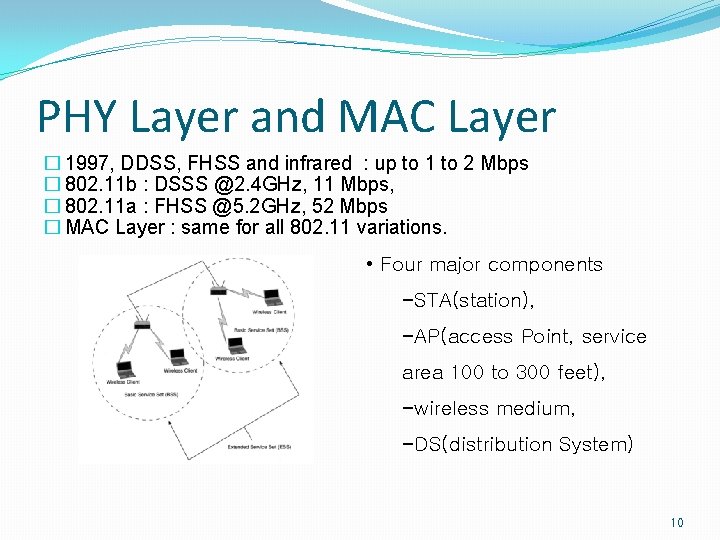
PHY Layer and MAC Layer � 1997, DDSS, FHSS and infrared : up to 1 to 2 Mbps � 802. 11 b : DSSS @2. 4 GHz, 11 Mbps, � 802. 11 a : FHSS @5. 2 GHz, 52 Mbps � MAC Layer : same for all 802. 11 variations. • Four major components −STA(station), −AP(access Point, service area 100 to 300 feet), −wireless medium, −DS(distribution System) 10

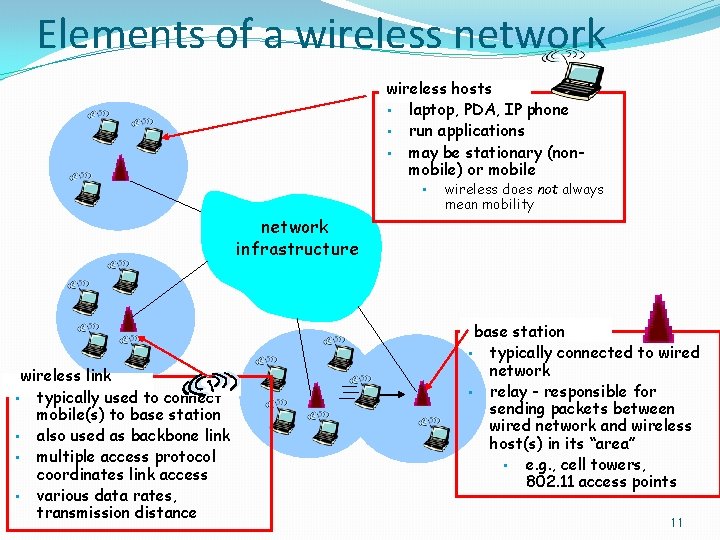
Elements of a wireless network wireless hosts • laptop, PDA, IP phone • run applications • may be stationary (nonmobile) or mobile • wireless does not always mean mobility network infrastructure wireless link • typically used to connect mobile(s) to base station • also used as backbone link • multiple access protocol coordinates link access • various data rates, transmission distance base station • typically connected to wired network • relay - responsible for sending packets between wired network and wireless host(s) in its “area” • e. g. , cell towers, 802. 11 access points 11

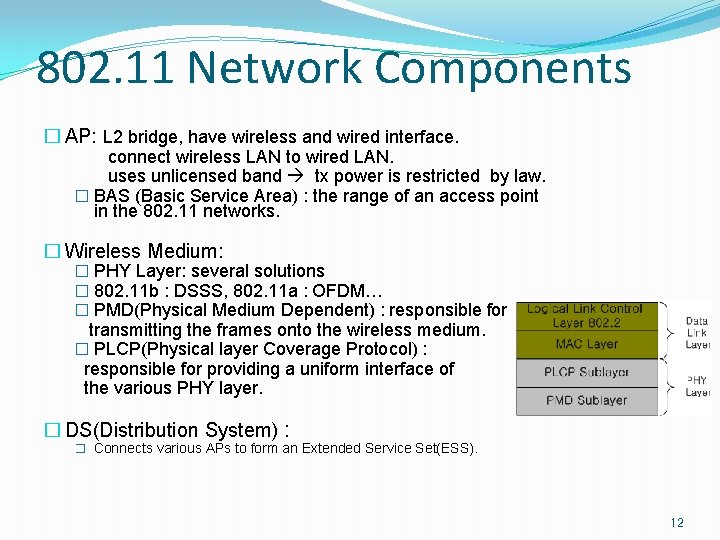
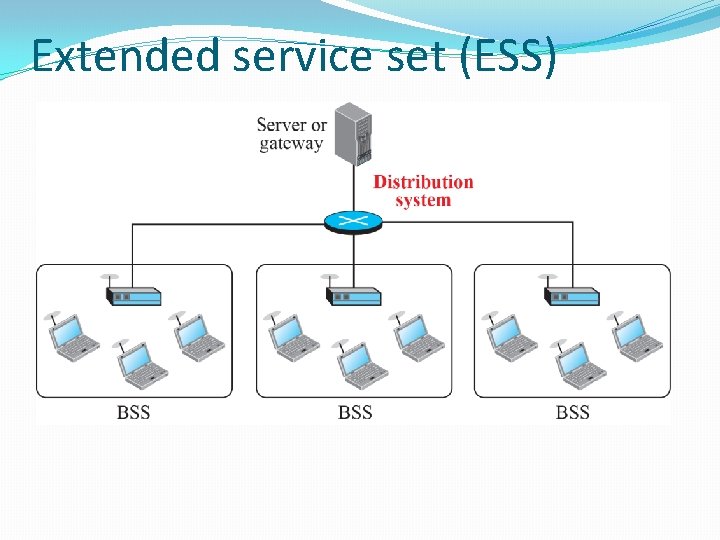
802. 11 Network Components � AP: L 2 bridge, have wireless and wired interface. connect wireless LAN to wired LAN. uses unlicensed band tx power is restricted by law. � BAS (Basic Service Area) : the range of an access point in the 802. 11 networks. � Wireless Medium: � PHY Layer: several solutions � 802. 11 b : DSSS, 802. 11 a : OFDM… � PMD(Physical Medium Dependent) : responsible for transmitting the frames onto the wireless medium. � PLCP(Physical layer Coverage Protocol) : responsible for providing a uniform interface of the various PHY layer. � DS(Distribution System) : � Connects various APs to form an Extended Service Set(ESS). 12

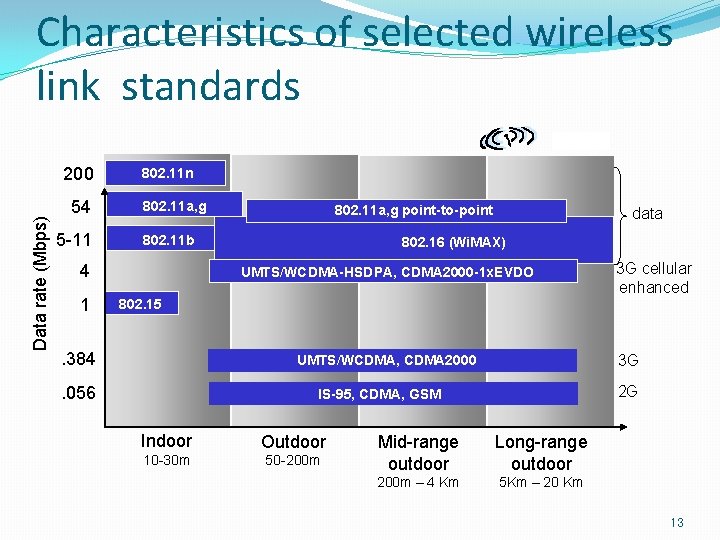
Characteristics of selected wireless link standards Data rate (Mbps) 200 54 5 -11 802. 11 n 802. 11 a, g 802. 11 b 4 1 802. 11 a, g point-to-point data 802. 16 (Wi. MAX) UMTS/WCDMA-HSDPA, CDMA 2000 -1 x. EVDO 3 G cellular enhanced 802. 15 . 384 3 G UMTS/WCDMA, CDMA 2000 . 056 2 G IS-95, CDMA, GSM Indoor Outdoor 10 -30 m 50 -200 m Mid-range outdoor Long-range outdoor 200 m – 4 Km 5 Km – 20 Km 13

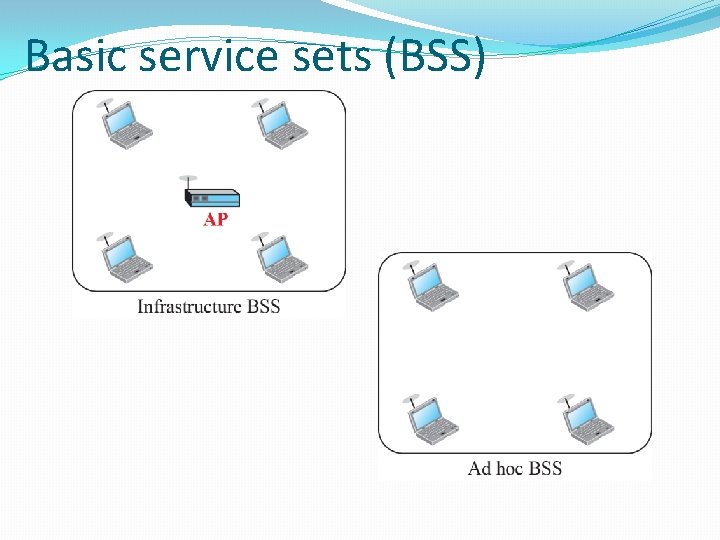
Basic service sets (BSS)

Extended service set (ESS)

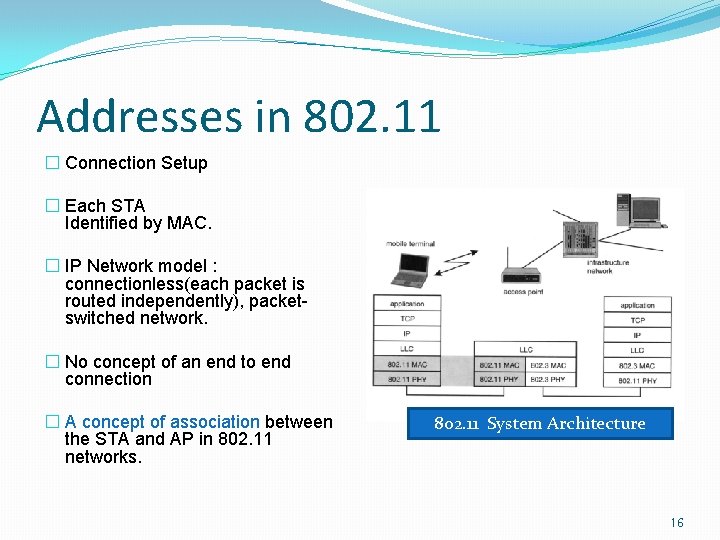
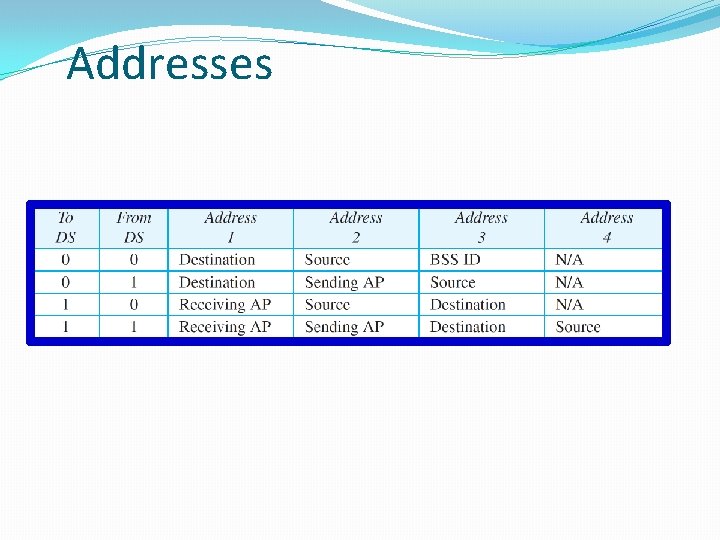
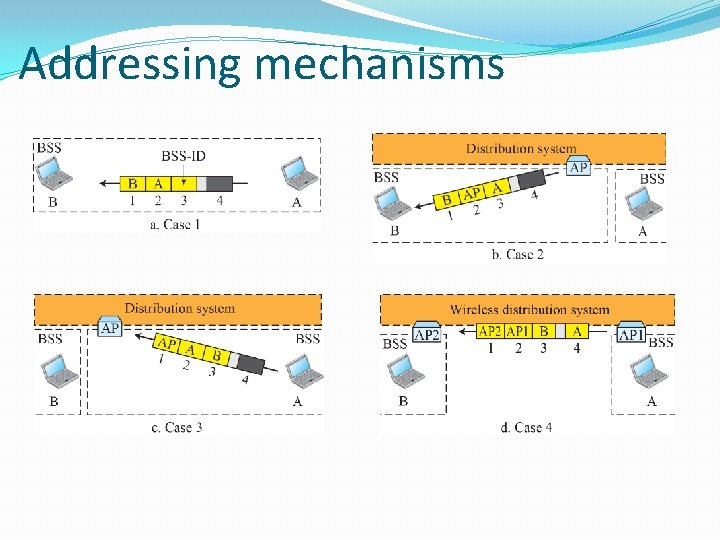
Addresses in 802. 11 � Connection Setup � Each STA Identified by MAC. � IP Network model : connectionless(each packet is routed independently), packetswitched network. � No concept of an end to end connection � A concept of association between the STA and AP in 802. 11 networks. 802. 11 System Architecture 16

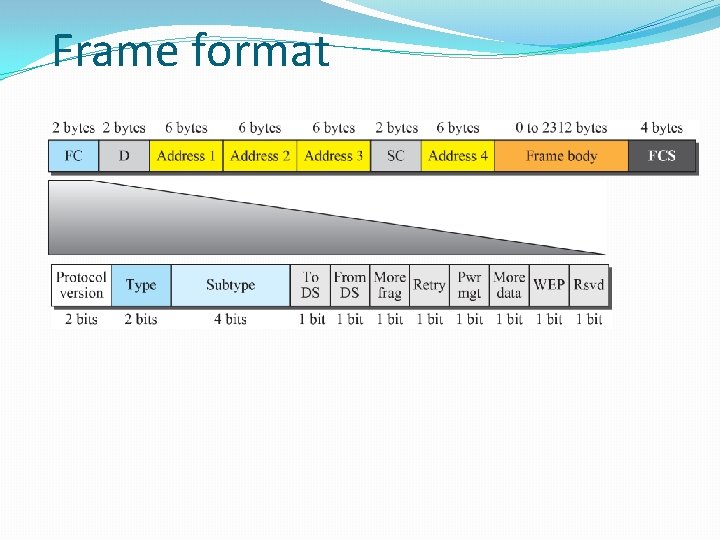
Frame format

Addresses

Addressing mechanisms

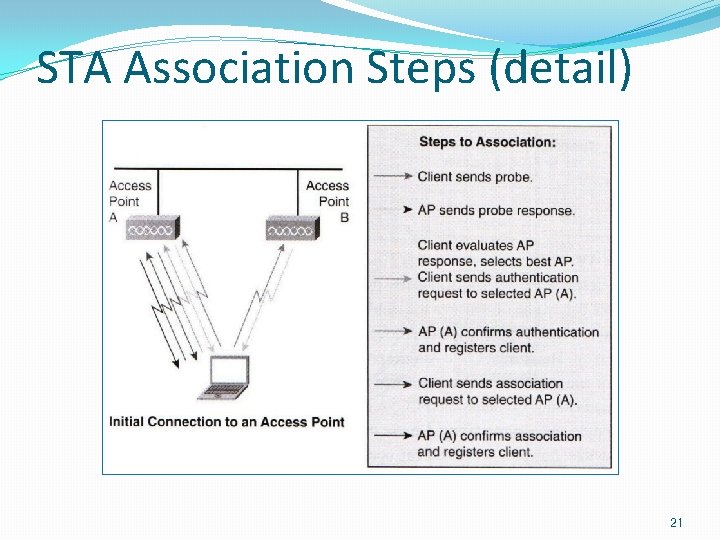
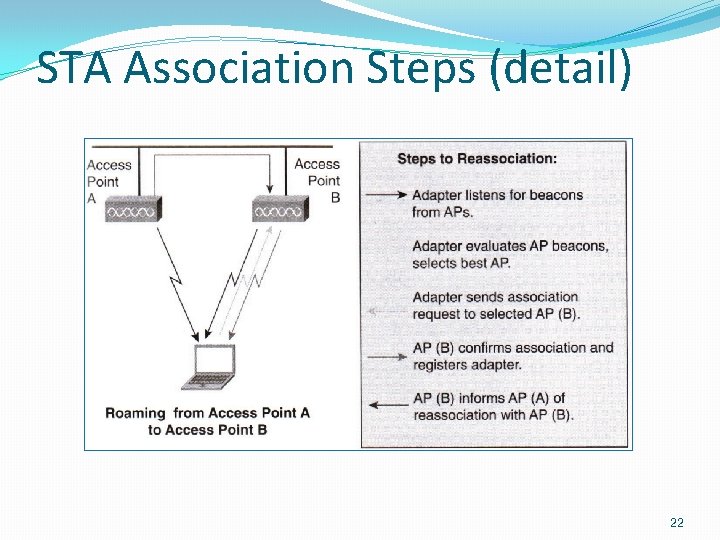
STA Association Steps 1. STA AP : Probe Request {…, Service Set ID, …} 2. AP STA : Probe Response. �Authenticate at this moment : correct SSID, registered MAC, authentication protocol. �Authentication TWNs: aim to establish end-to-end Authentication. � 802. 11: Data link layer authentication � OSA(open system authentication), SKA(shared Key Authentication) 3. STA AP : association request {. . , capability and rate info, …} 4. AP STA : association response {accept or accept} � Association: establish a logical connection btw the STA and the AP. � Now DS know in which AP the STA is. 20

STA Association Steps (detail) 21

STA Association Steps (detail) 22

MAC layers in IEEE 802. 11 standard

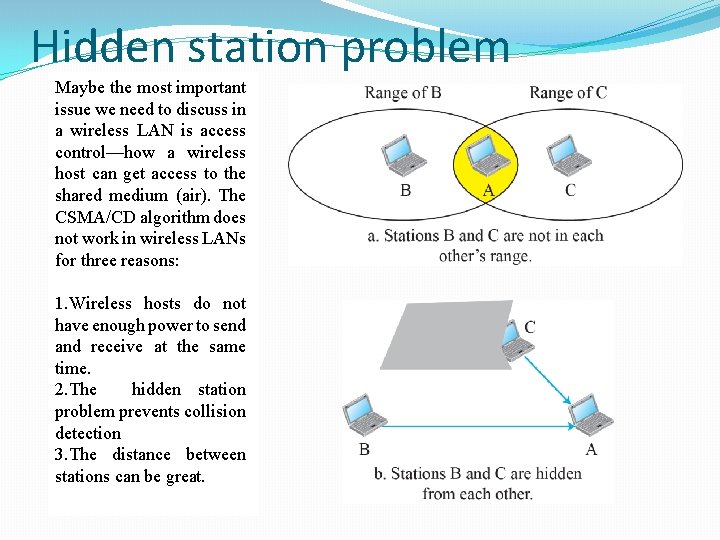
Hidden station problem Maybe the most important issue we need to discuss in a wireless LAN is access control—how a wireless host can get access to the shared medium (air). The CSMA/CD algorithm does not work in wireless LANs for three reasons: 1. Wireless hosts do not have enough power to send and receive at the same time. 2. The hidden station problem prevents collision detection 3. The distance between stations can be great.

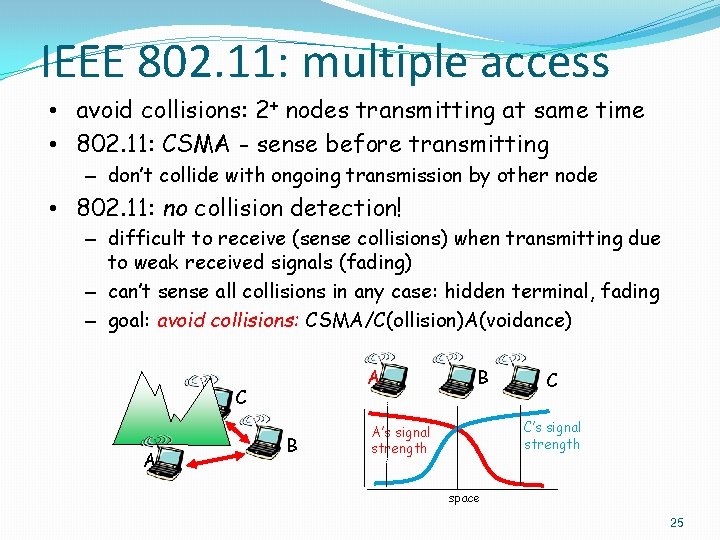
IEEE 802. 11: multiple access • avoid collisions: 2+ nodes transmitting at same time • 802. 11: CSMA - sense before transmitting – don’t collide with ongoing transmission by other node • 802. 11: no collision detection! – difficult to receive (sense collisions) when transmitting due to weak received signals (fading) – can’t sense all collisions in any case: hidden terminal, fading – goal: avoid collisions: CSMA/C(ollision)A(voidance) A C A B B C C’s signal strength A’s signal strength space 25

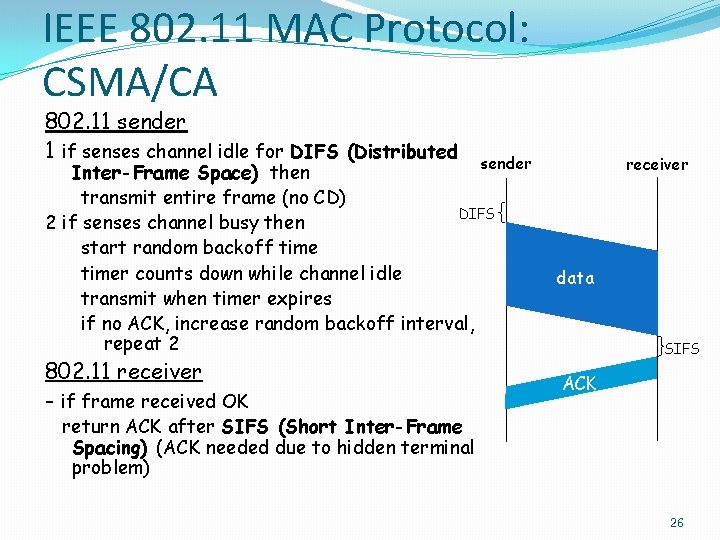
IEEE 802. 11 MAC Protocol: CSMA/CA 802. 11 sender 1 if senses channel idle for DIFS (Distributed sender Inter-Frame Space) then transmit entire frame (no CD) DIFS 2 if senses channel busy then start random backoff timer counts down while channel idle transmit when timer expires if no ACK, increase random backoff interval, repeat 2 802. 11 receiver - if frame received OK receiver data SIFS ACK return ACK after SIFS (Short Inter-Frame Spacing) (ACK needed due to hidden terminal problem) 26

Avoiding collisions (more) idea: allow sender to “reserve” channel rather than random access of data frames: avoid collisions of long data frames • sender first transmits small request-to-send (RTS) packets to BS using CSMA – RTSs may still collide with each other (but they’re short) • BS broadcasts clear-to-send (CTS) in response to RTS • CTS heard by all nodes – sender transmits data frame – other stations defer transmissions avoid data frame collisions completely using small reservation packets! 27

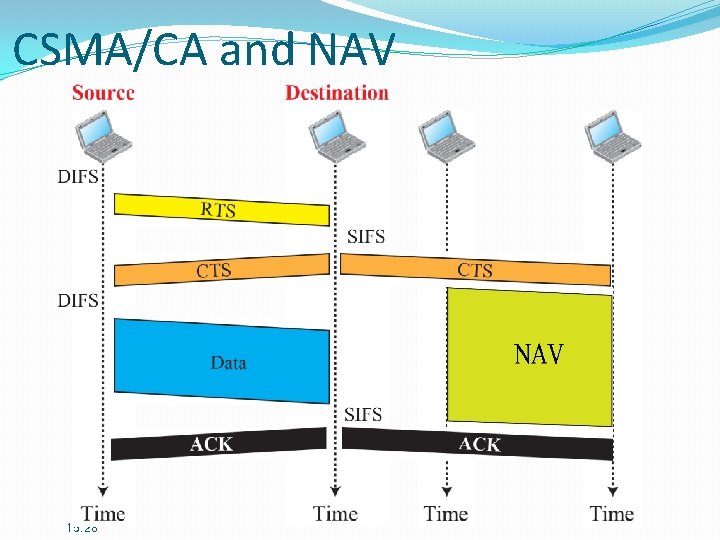
CSMA/CA and NAV 15. 28

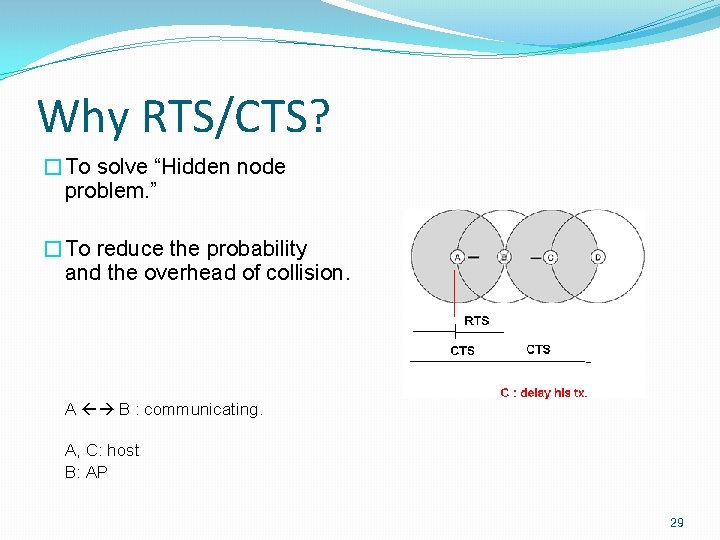
Why RTS/CTS? �To solve “Hidden node problem. ” �To reduce the probability and the overhead of collision. A B : communicating. A, C: host B: AP 29

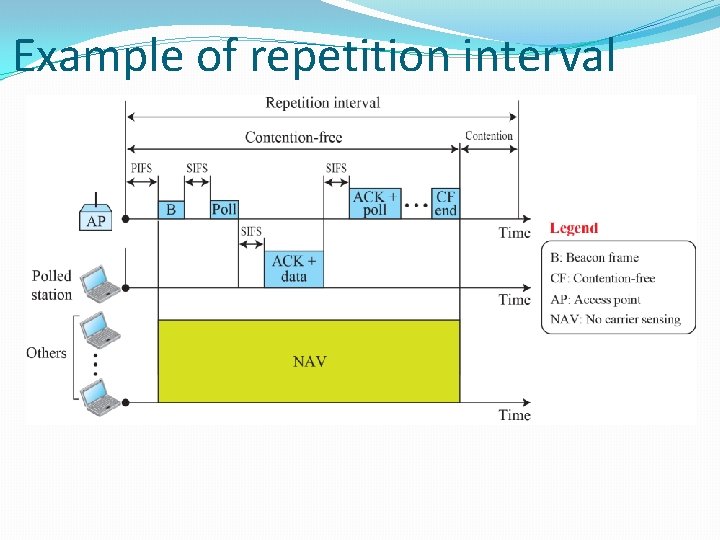
Example of repetition interval

MANET • • • MANET does not rely on any fixed infrastructure to establish communication: instead, wireless nodes co-operate among themselves to establish communication. MANETs are especially attractive for use by the military, emergency service providers and commercial applications where user density is too sparse or too temporary to justify the deployment of any infrastructure.

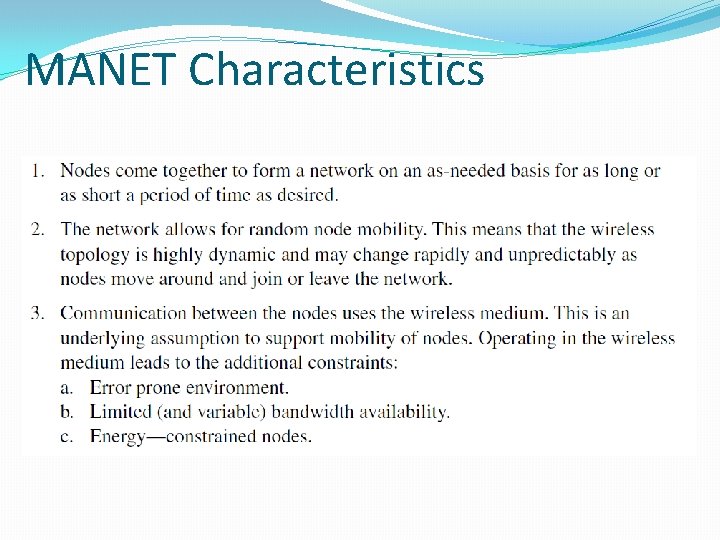
MANET Characteristics

MANET Characteristics 15. 33

MAC for MANET 15. 34

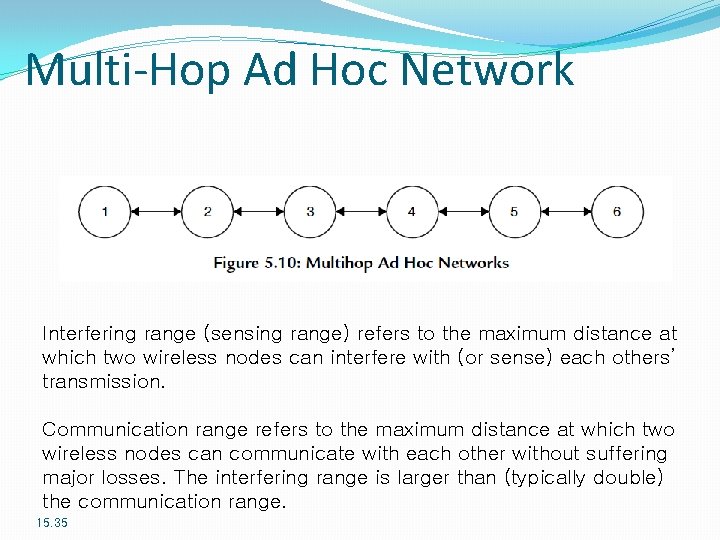
Multi-Hop Ad Hoc Network Interfering range (sensing range) refers to the maximum distance at which two wireless nodes can interfere with (or sense) each others’ transmission. Communication range refers to the maximum distance at which two wireless nodes can communicate with each other without suffering major losses. The interfering range is larger than (typically double) the communication range. 15. 35

Routing in MANET In MANETs however, because of the very nature of the network, we do not have access to a fixed infrastructure: the end-users (and therefore the routers themselves) are mobile. So, not only do the routes change dynamically but the routers themselves may disappear altogether (when they leave the network). It is this dynamic nature of the network that makes routing extremely complicated in MANETs. Analogy: Post Office; What if the end user is mobile? What if even the post office is mobile? 15. 36

Routing in MANET

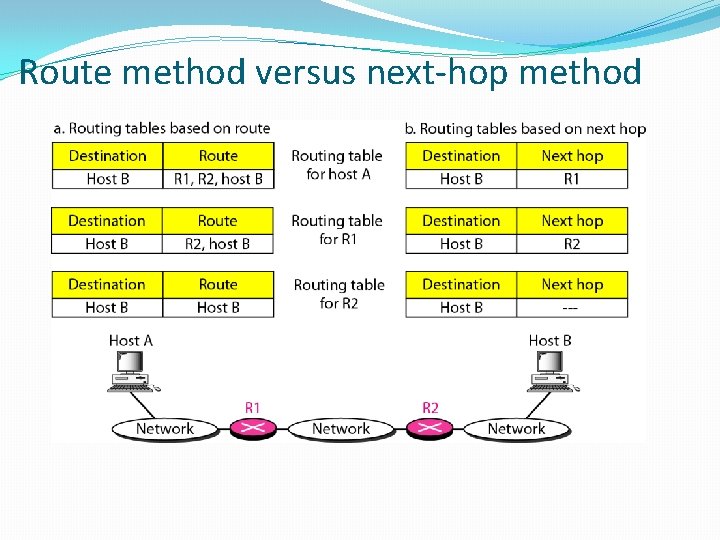
Route method versus next-hop method

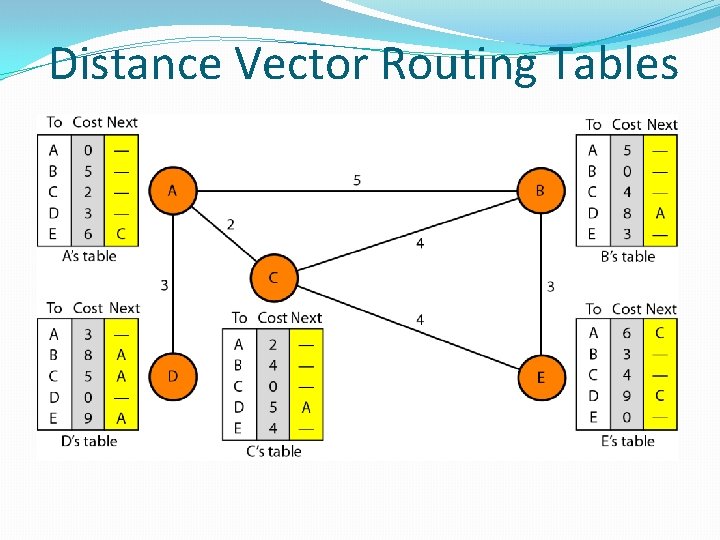
Distance Vector Routing Tables

Initialization of Tables

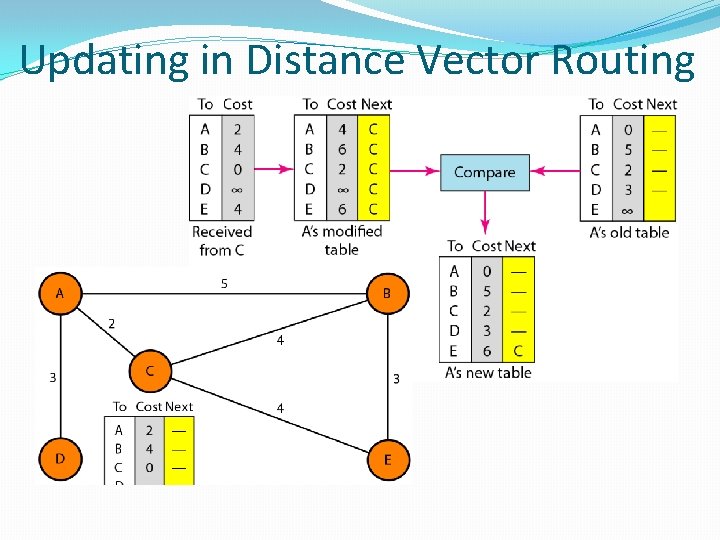
Updating in Distance Vector Routing

Proactive Routing Protocols • • • Aim to maintain routes to all nodes in the network (even if they are not needed). In other words, these protocols practically aim to map the network. This is achieved by the routers (nodes) in the network periodically exchanging routing updates. These updates are then used to maintain up-to-date routing tables in each of the routers (nodes). Whenever a node wishes to transmit a packet, it looks up its routing table and transmits to the appropriate next hop. Advantage: very low latencies. Problem: require a lot of overhead (in terms of processing power, bandwidth and so on) for maintaining routes which may never be used. Examples: Dynamic Destination Sequenced Distance Vector Routing (DSDV) protocol and Optimized Link State Routing (OLSR) protocol.

Reactive Routing Protocols • • • Reactive routing protocols, on the other hand, work on an ondemand basis where the route to the destination is discovered if and when needed. This reduces the overhead of proactive protocols but increases the latency in packet transmission time, since the route discovery mechanism has to complete before the transmission of the first packet can begin. It is also possible that in the time that it takes to determine the route to the destination, the route becomes invalid (due to a node moving out of the network). Examples: Dynamic Source Routing (DSR) protocol and Ad Hoc Ondemand Distance Vector (AODV) routing protocol.

Hybrid Routing Protocols D= 2 H

Hybrid Routing Protocols • • • Work by combining the proactive and the reactive approaches to optimize performance. Such protocols create a hierarchical network by grouping nodes in close proximity into clusters (a Tier 1 network). Each cluster has a cluster-head which acts as the gateway (default router) for all other nodes. The cluster-heads of different clusters then communicate with each other, thus forming a Tier 2 network. The hybrid approach uses a reactive routing approach at the Tier 1 network (inside the cluster) and a pro-active routing approach at the Tier 2 network (between clusters). This optimizes performance because “minor” node mobility changes routes frequently inside a cluster but the inter-cluster routes are affected only if the nodes travel a large distance. Hybrid protocols are therefore extremely effective in scenarios where nodes move frequently but within a small geographical region.

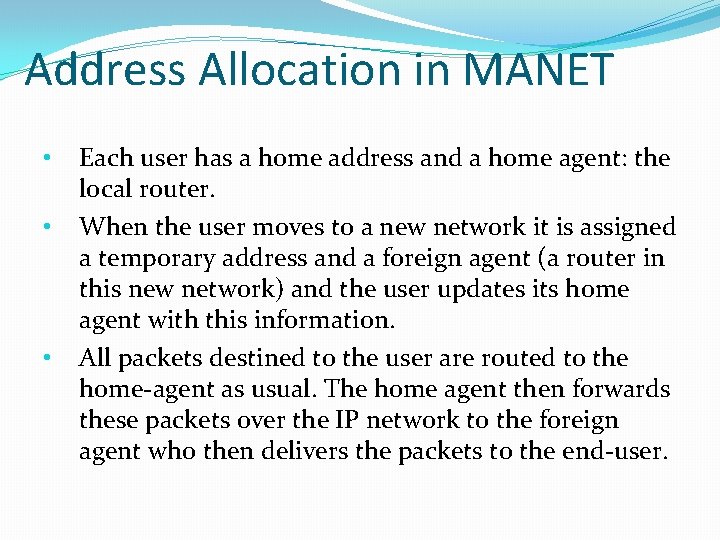
Address Allocation in MANET • • • Each user has a home address and a home agent: the local router. When the user moves to a new network it is assigned a temporary address and a foreign agent (a router in this new network) and the user updates its home agent with this information. All packets destined to the user are routed to the home-agent as usual. The home agent then forwards these packets over the IP network to the foreign agent who then delivers the packets to the end-user.

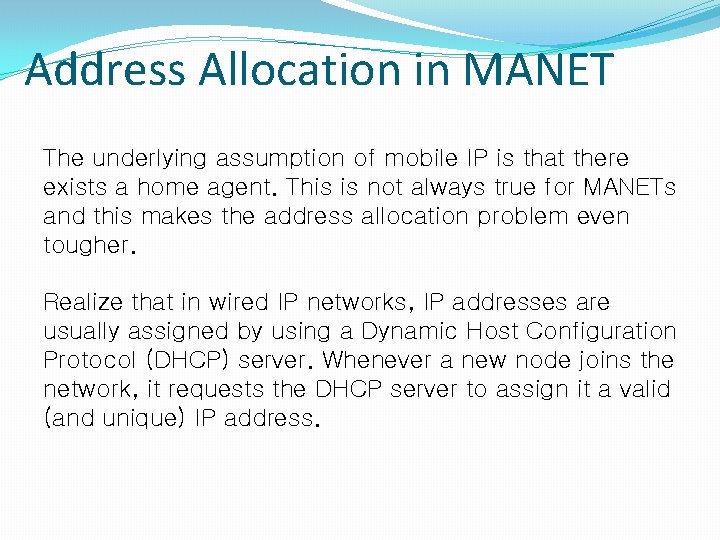
Address Allocation in MANET The underlying assumption of mobile IP is that there exists a home agent. This is not always true for MANETs and this makes the address allocation problem even tougher. Realize that in wired IP networks, IP addresses are usually assigned by using a Dynamic Host Configuration Protocol (DHCP) server. Whenever a new node joins the network, it requests the DHCP server to assign it a valid (and unique) IP address.

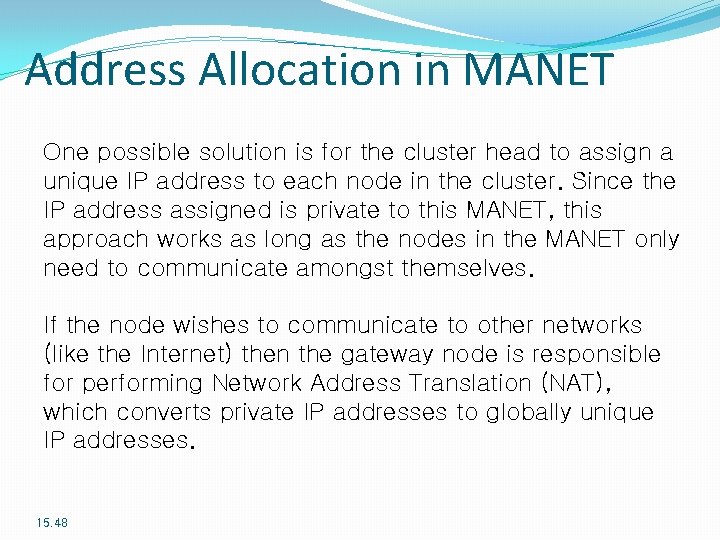
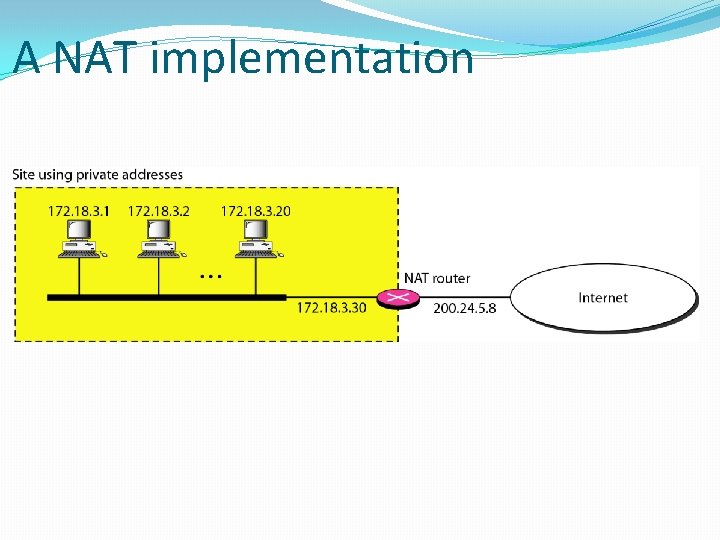
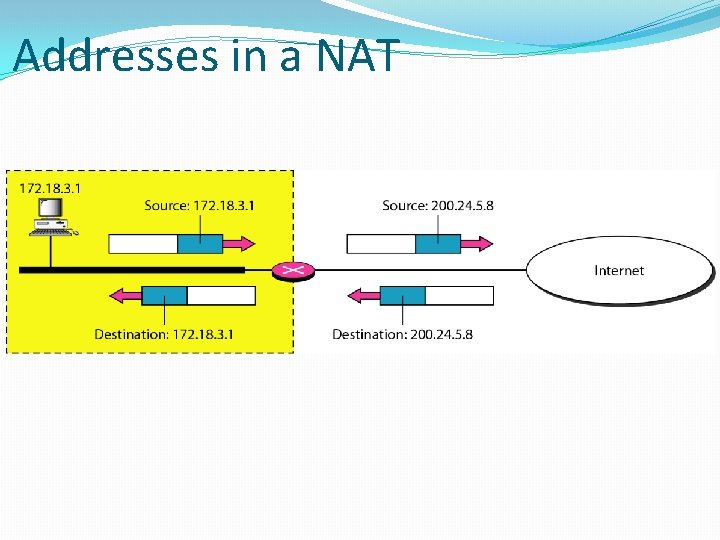
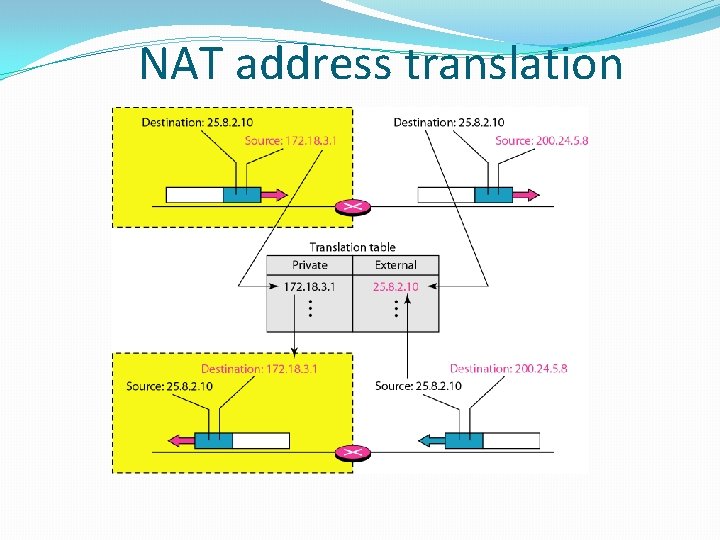
Address Allocation in MANET One possible solution is for the cluster head to assign a unique IP address to each node in the cluster. Since the IP address assigned is private to this MANET, this approach works as long as the nodes in the MANET only need to communicate amongst themselves. If the node wishes to communicate to other networks (like the Internet) then the gateway node is responsible for performing Network Address Translation (NAT), which converts private IP addresses to globally unique IP addresses. 15. 48

A NAT implementation

Addresses in a NAT

NAT address translation

Address Allocation in MANET If the node wishes to communicate to other networks (like the Internet) then the gateway node is responsible for performing Network Address Translation (NAT), which converts private IP addresses to globally unique IP addresses. However, this approach works only if the network uses a hierarchical routing approach and each cluster has appointed a cluster head. In a flat topology MANET where there is no cluster head, each node which joins the network chooses an IP address at random and then performs a Duplicate Address Detection (DAD) process to ensure that the IP 15. 52

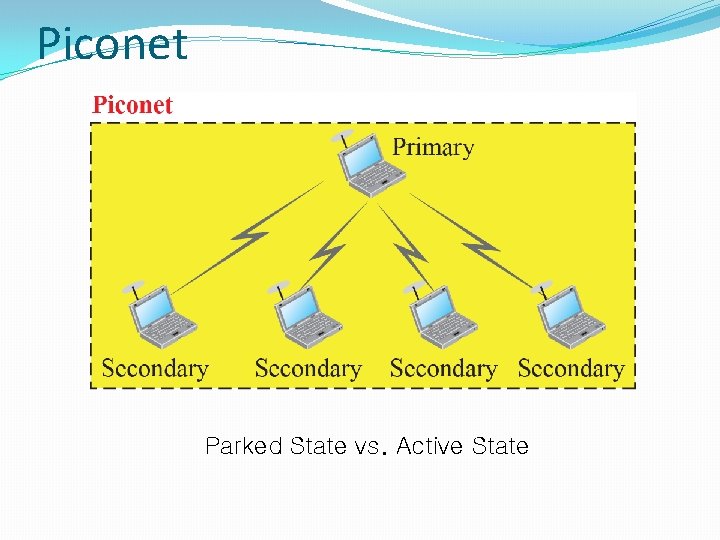
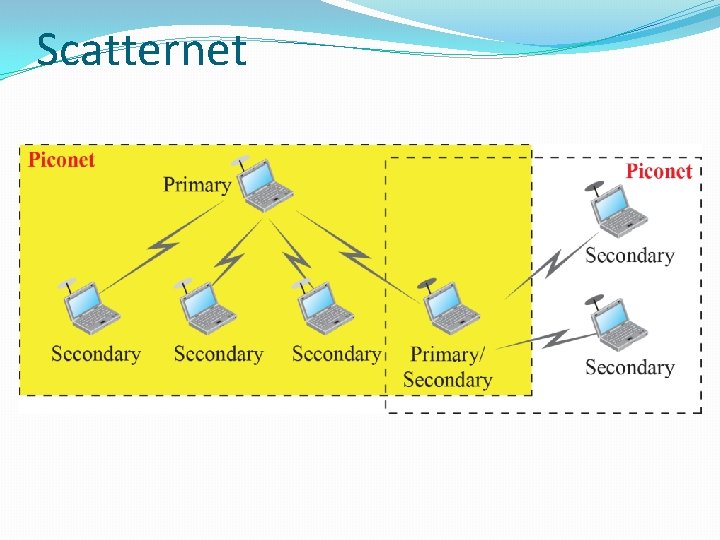
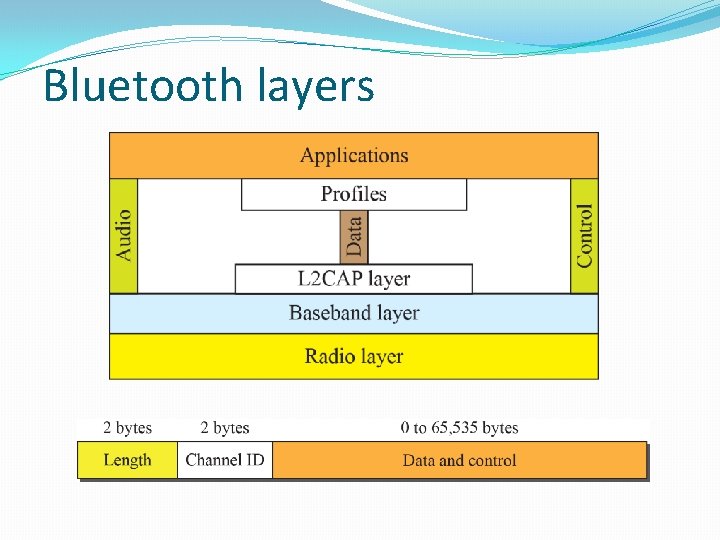
BLUETOOTH Bluetooth is a wireless LAN technology designed to connect devices of different functions when they are at a short distance from each other. A Bluetooth LAN is an ad hoc network. The devices, sometimes called gadgets, find each other and make a network called a piconet.

Piconet Parked State vs. Active State

Scatternet

Bluetooth layers