Identity management Tuomas Aura CSEC 3400 Information security
















- Slides: 30

Identity management Tuomas Aura CSE-C 3400 Information security Aalto University, autumn 2014

Outline 1. 2. 3. 4. 5. 6. Single sign-on SAML and Shibboleth Open. Id OAuth (Corporate IAM) Strong identity 2

Single sign-on (SSO) § Users have too many user accounts – Cannot remember the passwords – Service access slow and inconvenient – Forgotten, unmanaged accounts are a security risk Need for an SSO solution § SSO types: – Pseudo-SSO: separate authentication to each service; client software manages the credentials and hides the login from user – Proxy-based SSO: pseudo-SSO implemented in a proxy; proxy in the network manages user credentials and hides the login details from the client – True SSO: user authenticates to a separate authentication service, which asserts user identity to other services – Federated SSO: authentication between administrative domains § Main problem with SSO systems: there’re so many of them 3

SAML AND SHIBBOLETH 4

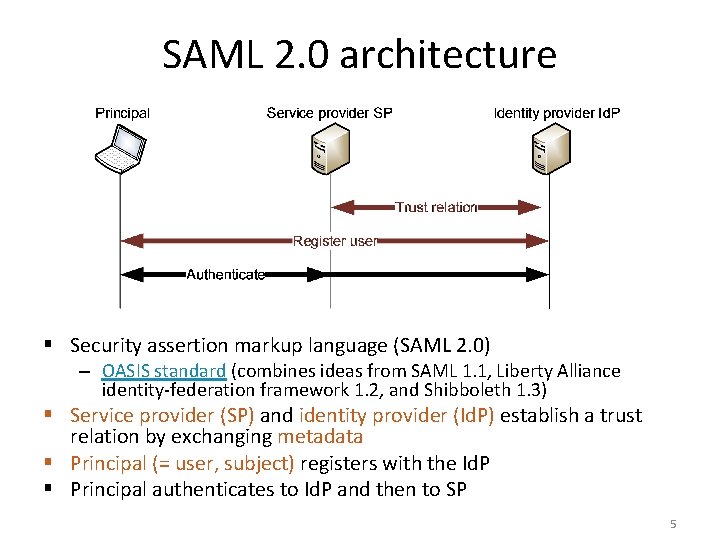
SAML 2. 0 architecture § Security assertion markup language (SAML 2. 0) – OASIS standard (combines ideas from SAML 1. 1, Liberty Alliance identity-federation framework 1. 2, and Shibboleth 1. 3) § Service provider (SP) and identity provider (Id. P) establish a trust relation by exchanging metadata § Principal (= user, subject) registers with the Id. P § Principal authenticates to Id. P and then to SP 5

SAML § SAML is a complex family of protocols: – Assertions are statements by Id. P about a principal, written in XML – Protocols define message flows for requesting assertions – Bindings define how protocol messages are transported over HTTP, SOAP etc. – Profiles define useful combinations of assertions, protocols and bindings – Metadata defines trust relations § SAML is based on contractual relations – Metadata must be first exchanged between Id. P and SP – Federation may set rules for its member Id. Ps and SPs – User cannot decide which id to use where § Typical profile: SAML web browser SSO profile 6

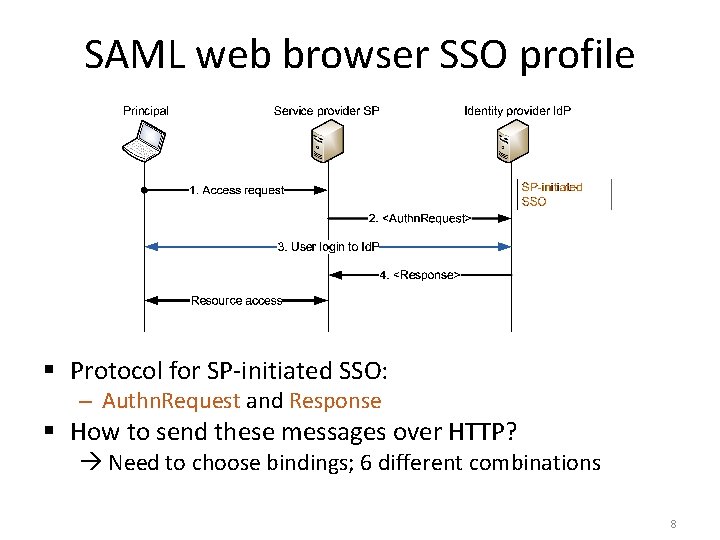
SAML web browser SSO profile § Id. P-initiated or SP-initiated SSO: – User first logs into the Id. P, or first connects to SP § Bindings to HTTP messages – Redirect: message from SP to Id. P is sent in GET URL via browser, with help of HTTP redirection – POST: message between SP and Id. P is sent in HTTP form via browser, submitted by user click or script – Artifact: reference to message is sent in GET URL via browser, with the help of HTTP redirection, and the actual message is retrieved directly from the sender § SOAP binding is not used in this profile 7

SAML web browser SSO profile § Protocol for SP-initiated SSO: – Authn. Request and Response § How to send these messages over HTTP? Need to choose bindings; 6 different combinations 8

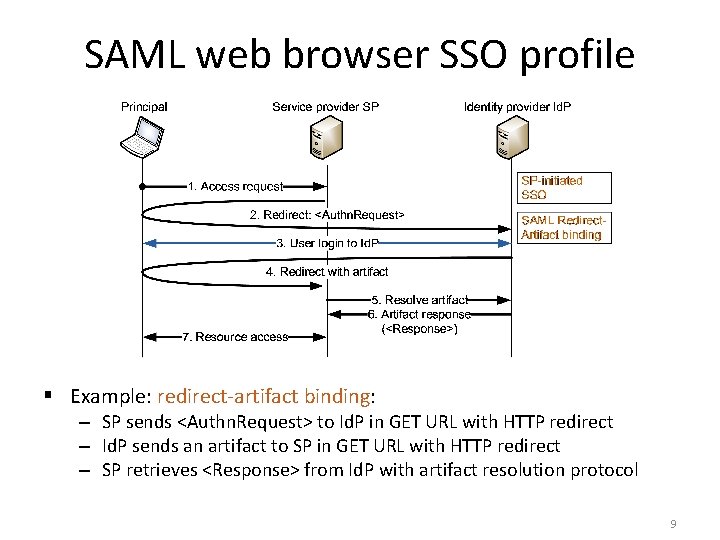
SAML web browser SSO profile § Example: redirect-artifact binding: – SP sends <Authn. Request> to Id. P in GET URL with HTTP redirect – Id. P sends an artifact to SP in GET URL with HTTP redirect – SP retrieves <Response> from Id. P with artifact resolution protocol 9

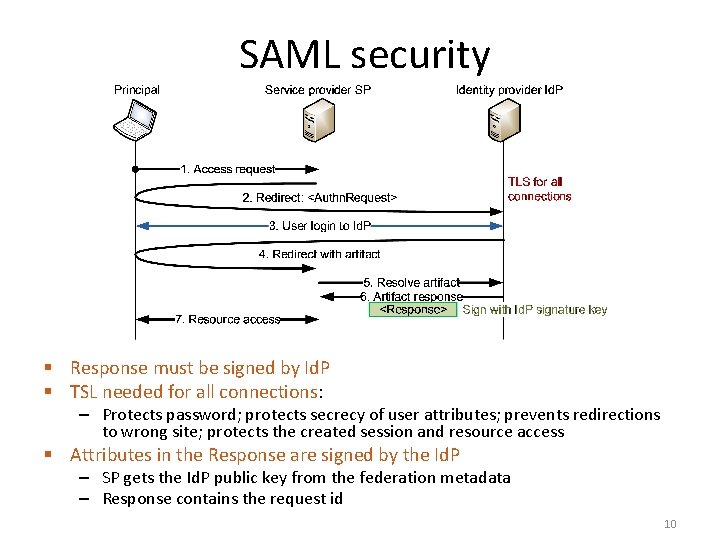
SAML security § Response must be signed by Id. P § TSL needed for all connections: – Protects password; protects secrecy of user attributes; prevents redirections to wrong site; protects the created session and resource access § Attributes in the Response are signed by the Id. P – SP gets the Id. P public key from the federation metadata – Response contains the request id 10

Shibboleth 2 § Open-source implementation of SAML 2. 0 for web SSO (wiki) – Developed by the Internet 2 project § Used mainly in research and educational institutions; many other commercial and open-source SAML implementation exist § If SP supports multiple Id. Ps, SP-initiated authentication goes via the where are you from (WAYF) page – One more step of redirection for the Authn. Request § Federation is a group of Id. Ps and SPs that – – share metadata in one signed file agree on an attribute schema agree on CA for TLS have a service agreement that sets out rules for the federation e. g. Haka federation 11

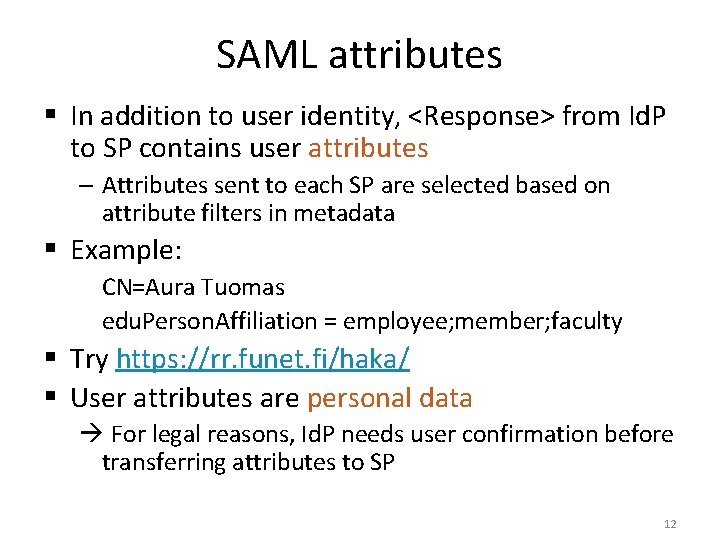
SAML attributes § In addition to user identity, <Response> from Id. P to SP contains user attributes – Attributes sent to each SP are selected based on attribute filters in metadata § Example: CN=Aura Tuomas edu. Person. Affiliation = employee; member; faculty § Try https: //rr. funet. fi/haka/ § User attributes are personal data For legal reasons, Id. P needs user confirmation before transferring attributes to SP 12

Sessions in Shibboleth § Shibboleth implements two kinds of sessions: – Id. P session between browser and the Id. P (Id. P cookies) user only needs to type in password once – SP session between browser and each SP (SP cookies) § Additional application sessions: – Web middleware incl. PHP, JSP and ASP. NET implements sessions using cookies, URL or web form) – Applications may set their own cookies § No single logout – Logging out of SP does not usually log the user out of the Id. P can log back to SP without password – Logging out of Id. P does not log the user out of SPs – Logging out of one SO does not log the user out of other SPs § Application sessions complicate the situation further Shibboleth logout behavior is hard to understand 13

OPENID 14

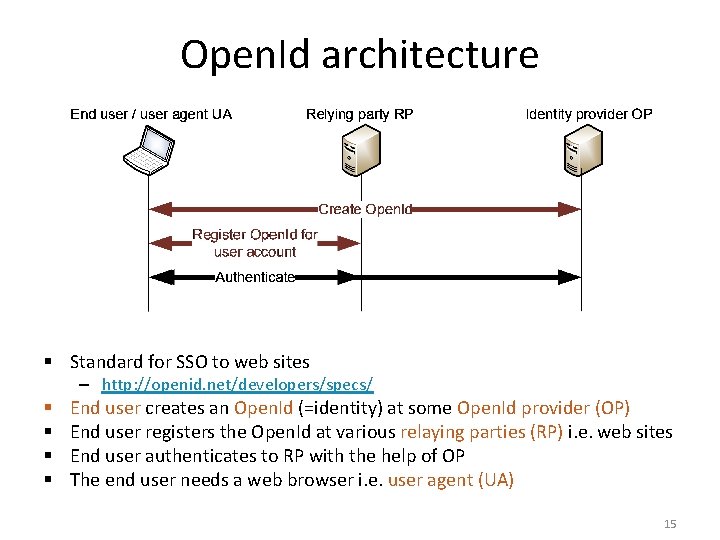
Open. Id architecture § Standard for SSO to web sites – http: //openid. net/developers/specs/ § § End user creates an Open. Id (=identity) at some Open. Id provider (OP) End user registers the Open. Id at various relaying parties (RP) i. e. web sites End user authenticates to RP with the help of OP The end user needs a web browser i. e. user agent (UA) 15

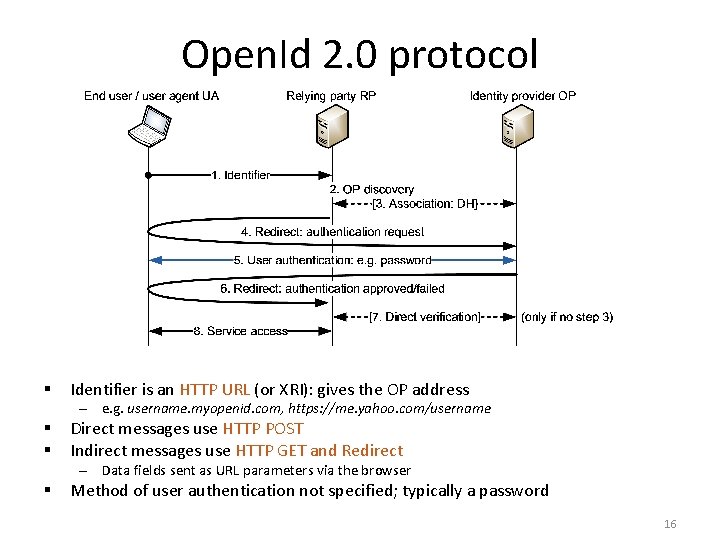
Open. Id 2. 0 protocol § Identifier is an HTTP URL (or XRI): gives the OP address – e. g. username. myopenid. com, https: //me. yahoo. com/username § § Direct messages use HTTP POST Indirect messages use HTTP GET and Redirect – Data fields sent as URL parameters via the browser § Method of user authentication not specified; typically a password 16

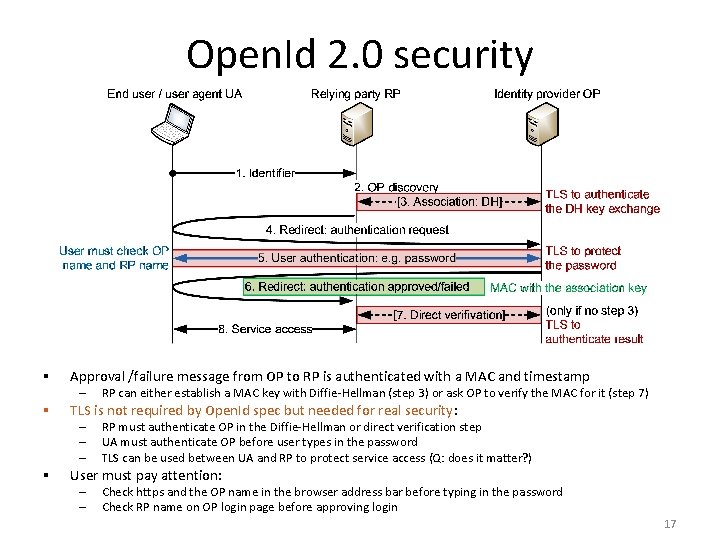
Open. Id 2. 0 security § Approval /failure message from OP to RP is authenticated with a MAC and timestamp – § TLS is not required by Open. Id spec but needed for real security: – – – § RP can either establish a MAC key with Diffie-Hellman (step 3) or ask OP to verify the MAC for it (step 7) RP must authenticate OP in the Diffie-Hellman or direct verification step UA must authenticate OP before user types in the password TLS can be used between UA and RP to protect service access (Q: does it matter? ) User must pay attention: – – Check https and the OP name in the browser address bar before typing in the password Check RP name on OP login page before approving login 17

Open. Id notes § What does “open” mean? – – Anyone can become an identity provider User can choose any identity provider Services accept the identity chosen by the user Works on any web browser without proprietary software § In practice, not always so open: – RP policy may determine which OPs are accepted – OP policy may determine which RPs are accepted § For privacy, user-provided id may just point to OP without user id – e. g. https: //www. google. com/accounts/o 8/id § Open. Id specification is poorly written – Assumes the reader knows previous versions – Uses XRI, Yadis and XRDS: very complex and incomplete specifications § Security not obvious from the specification: – Focus on implementation, not on secure protocol design – Vague security claims especially when used without TLS 18

OAUTH 2. 0 19

OAuth 2. 0 § OAuth was designed for authorization (i. e. delegation) – Allow an external web site or app to access a service on the user’s behalf – Password sharing not required, and access can be revoked § Examples: – Authorize an external web site or app to update your Facebook profile or page – Authorize continuous integration tool to monitor a Git. Hub repository § Standardized by IETF (RFC 6749, RFC 6750) – Many implementation options cause interoperability issues – OAuth 2. 0 security is based only on TLS (Oath 1. 0 used client signatures) 20

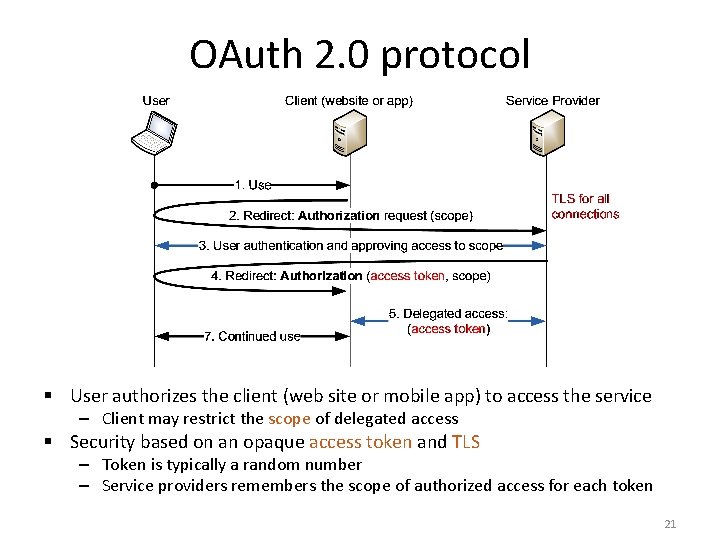
OAuth 2. 0 protocol § User authorizes the client (web site or mobile app) to access the service – Client may restrict the scope of delegated access § Security based on an opaque access token and TLS – Token is typically a random number – Service providers remembers the scope of authorized access for each token 21

OAuth for authentication? § The message flow in OAuth looks like Open. Id or SAML tempting to use the same protocol for authentication – User would prove its identity by delegating access to a (dummy) resource associated with the user account § In principle, this is a bad idea: – OAuth access token enables client to access a resource on the service provider – The client in OAuth does not know or care who gives it the token, as long as the token works for accessing SP – The protocol does not prevent the client from sharing the token with others Malicious client can impersonate its users to other clients § Businesses have made proprietary extensions to make OAuth work for authentication as well 22

STRONG IDENTITY 26

Strong authentication § Goal: authentication equivalent to verifying national identity card or passport § Why is it needed? – Initial id check when registering new users, e. g. students enrolling to university – Required by law for access to government services and personal information – Increasing trust in commercial online transactions — but this has long since been solved in other ways § Why not use Open. Id or SAML? – Open. Id allows user to choose identifier no secure link to a real person – SAML works internally in organizations and between organizations that have a contract not for new, open online services 27

Finnish electronic identity card § Finnish identity cards (HST-kortti) have a smartcard chip with three key pairs – Signature, encryption and authentication keys – http: //www. fineid. fi/ § Keys are certified by the national population register (VRK) § Has not gained popularity; few people have an id card; even fewer ever use it for electronic authentication – Why? 28

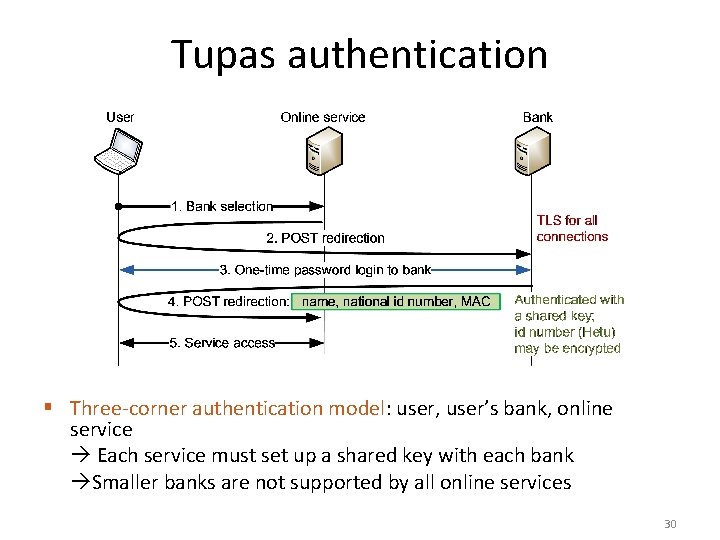
Tupas authentication § Tupas uses bank accounts for strong authentication – Defined by Federation of Finnish Financial Services http: //www. fkl. fi/teemasivut/sahkoinen_asiointi/tupas/ – Developed from online the payment system (commonly used in Finland for online purchases) – User authentication with one-time passwords § Advantage: everyone has a bank account, and banks are required to know the identity of their customers no cost for identity proofing § Example: https: //password. aalto. fi/ 29

Tupas authentication § Three-corner authentication model: user, user’s bank, online service Each service must set up a shared key with each bank Smaller banks are not supported by all online services 30

Mobile signature § Mobile phone operators install a signature key on the SIM – ETSI standard, developed from earlier “business SIM” – No direct access from phone to signature key; signatures are requested via the operator’s mobile signature service provider (MSSP) § Advantages: everyone has a SIM card, and operators have 24/7 service for revocation § Four-corner authentication model: – Mobile operators have contracts with each other – Each service and user only needs to have a contract with one operator § Deployment and adoption has been slow – Requires identity proofing i. e. checking if the subject identity before issuing the certificate (now done with Tupas in Finland) – Operators want a fee for every transaction low number of transactions may not be a viable business 31

Reading material § Online: – Open. Id 2. 0, http: //openid. net/developers/specs/ – SAML 2. 0 Technical Overview, http: //www. oasisopen. org/committees/download. php/27819/sstcsaml-tech-overview-2. 0 -cd-02. pdf – OAuth specification http: //tools. ietf. org/html/rfc 6749 32

Exercises § How much security does Open. Id exactly give if TLS is not used? § Learn about XRI name space and XRI discovery. If XRI is used as the user identifier in Open. Id, how is the user supposed to authenticate the OP before typing in the password? § How much difference does it make to security and privacy if the userprovided id points to the OP without identifying the user, and the user identity is entered only at the OP site? § Look at the Haka federation metadata for Shibboleth 2. How does this create trust between an Id. P and SP? What ways are there to limit the trust? § Can you capture the Authn. Request and Response messages when logging into Noppa? Which bindings are used? § Why exactly is TLS needed at each stage in SAML/Shibboleth authentication, or is it? § Compare the logout (and re-login) behavior of Noppa, Oodi and nelliportaali. fi. Which sessions get deleted, when and how? § Despite similarities in the protocols, Open. Id, SAML, Oauth, and Tupas have different goals and make different assumptions about the relations between entities. What differences are there? 33