Access control models and policies Tuomas Aura CSEC


















- Slides: 31

Access control models and policies Tuomas Aura CSE-C 3400 Information security Aalto University, autumn 2014

Outline 1. 2. 3. 4. 5. Access control Discretionary AC Mandatory AC Other AC models Role-based AC Models and terminology for thinking about security policies 2

ACCESS CONTROL 3

Access control (AC) § Subjects request actions on objects – Alice wants to read a file – Bob wants to update account balance – Process wants to open a socket § AC = authentication + authorization – authentication = verifying the identity of the subject – authorization = checking that the subject has the right to perform the requested action on the subject 4

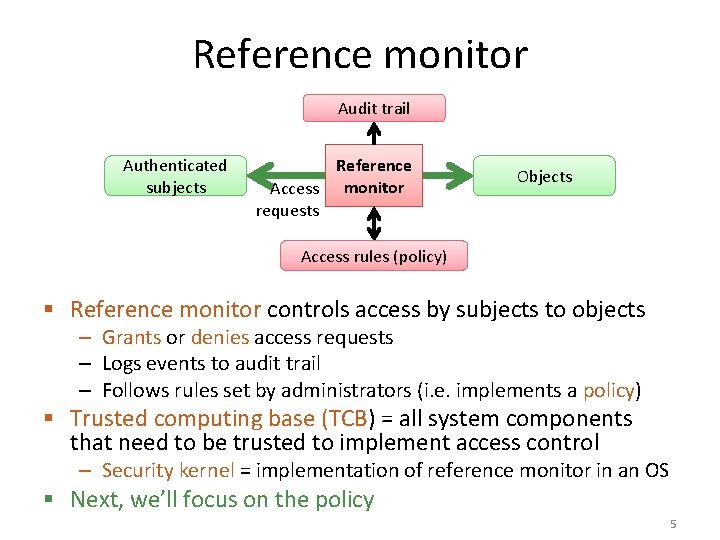
Reference monitor Audit trail Authenticated subjects Reference Access monitor requests Objects Access rules (policy) § Reference monitor controls access by subjects to objects – Grants or denies access requests – Logs events to audit trail – Follows rules set by administrators (i. e. implements a policy) § Trusted computing base (TCB) = all system components that need to be trusted to implement access control – Security kernel = implementation of reference monitor in an OS § Next, we’ll focus on the policy 5

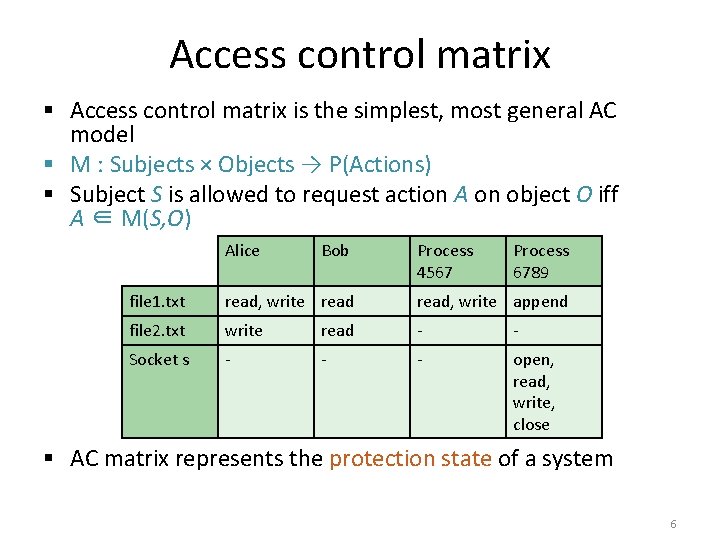
Access control matrix § Access control matrix is the simplest, most general AC model § M : Subjects × Objects → P(Actions) § Subject S is allowed to request action A on object O iff A ∈ M(S, O) Alice Bob Process 4567 Process 6789 file 1. txt read, write append file 2. txt write read - - Socket s - - - open, read, write, close § AC matrix represents the protection state of a system 6

DISCRETIONARY ACCESS CONTROL 8

Discretionary access control (DAC) § Data owners, usually users, set access rights § Subjects are trusted to make decisions about sharing access rights – Users decide who is allowed to access their files – User or process that can read a secret file can also share it e. g. by email § Also called identity-based AC: rights are assigned to users § Typical in commercial and consumer systems § There may be a policy against sharing and access may be audited, but the policy is not enforced technically § Examples of DAC outside computers: – Person with a key can open the door to others; door keys can be shared and copied – Tell your friend a secret on the condition that he does not tell it to anyone else 9

Access control list (ACL) § ACL = list of the access rights associated with an object § ACLs are another way to represent the AC matrix: one row of the matrix is stored for each object – file 1. txt ACL: Alice: { read, write }; Bob: { read }; Process 4567: { read, write }; Process 6789: { append }. – file 2. txt ACL: Alice: { write }; Bob: { read }. – Socket s ACL: Process 6789: { open, read, write, close }. § ACL examples: – Key-card locks, table reservations, visitor registration in military and police headquarters – Windows file system, Confluence wiki page Many old applications restrictions 10

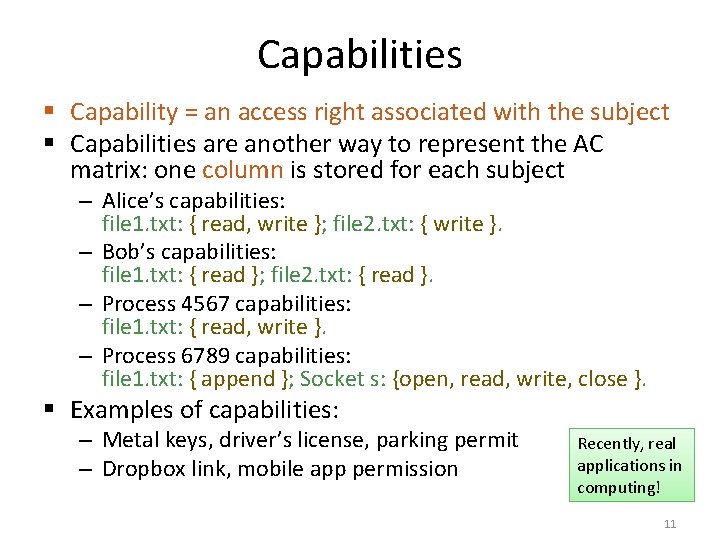
Capabilities § Capability = an access right associated with the subject § Capabilities are another way to represent the AC matrix: one column is stored for each subject – Alice’s capabilities: file 1. txt: { read, write }; file 2. txt: { write }. – Bob’s capabilities: file 1. txt: { read }; file 2. txt: { read }. – Process 4567 capabilities: file 1. txt: { read, write }. – Process 6789 capabilities: file 1. txt: { append }; Socket s: {open, read, write, close }. § Examples of capabilities: – Metal keys, driver’s license, parking permit – Dropbox link, mobile app permission Recently, real applications in computing! 11

MANDATORY ACCESS CONTROL 12

Mandatory access control (MAC) § Access rights are based on rules (i. e. policy) set by administration § The AC policy is enforced and cannot be changed by users § Subjects cannot leak access rights to others – User can read a secret file but cannot copy, print or email; file viewer application prevents cut-and-paste and screen shots – One process can access the Internet, another write files to the disk, neither is allowed to do both § MAC is also called rule-based AC § MAC originates from military policies – Intelligence officer may not be allowed to read his own reports – Officer can read a secret document but cannot take a copy out of the room – Officer who has had contact with foreign agents may lose access to classified information 13

Mandatory access control (MAC) § MAC has some uses in commercial systems – DRM: Alice can play the music she has purchased, but cannot share it – Malware isolation: Host firewall may block potential spyware from making outbound connections to prevent information leaks § Examples of MAC-like policies outside computers: – Biometric authentication prevents sharing of capabilities, e. g. photo on driver’s license or signature on credit card – Admit-one event tickets: UV stamps, shredding bracelets – In UK, jurors must not read newspapers or watch TV about the case so that they are not influenced by them 14

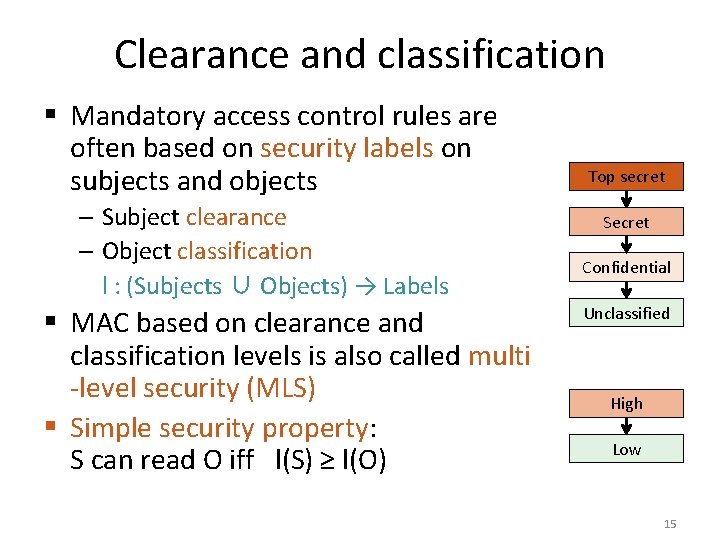
Clearance and classification § Mandatory access control rules are often based on security labels on subjects and objects – Subject clearance – Object classification l : (Subjects ∪ Objects) → Labels § MAC based on clearance and classification levels is also called multi -level security (MLS) § Simple security property: S can read O iff l(S) ≥ l(O) Top secret Secret Confidential Unclassified High Low 15

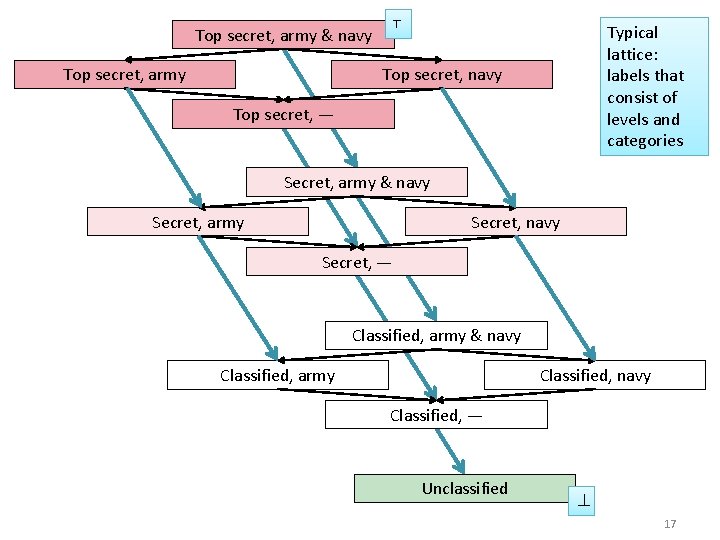
Top secret, army & navy Top secret, army ⊤ Typical lattice: labels that consist of levels and categories Top secret, navy Top secret, — Secret, army & navy Secret, army Secret, navy Secret, — Classified, army & navy Classified, army Classified, navy Classified, — Unclassified ⊥ 17

Bell-La. Padula model § Bell-La. Padula (BLP) is a MAC policy for protecting secrets – Military security model for computers; military is mostly concerned with protecting secrets – Observation: the simple security property is not sufficient to prevent secrets from leaking § Bell-La. Padula rules: Simple security property: S can read O iff l(S) ≥ l(O) *-property: S can write O iff l(O) ≥ l(S) § Also called: no read up, no write down 20

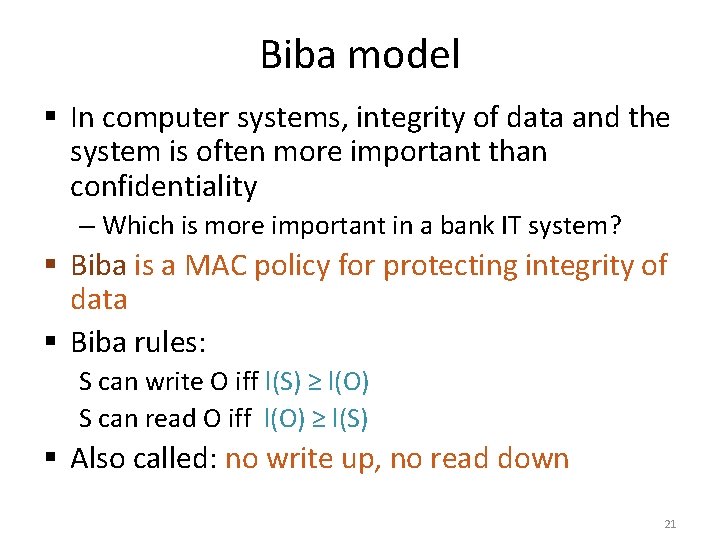
Biba model § In computer systems, integrity of data and the system is often more important than confidentiality – Which is more important in a bank IT system? § Biba is a MAC policy for protecting integrity of data § Biba rules: S can write O iff l(S) ≥ l(O) S can read O iff l(O) ≥ l(S) § Also called: no write up, no read down 21

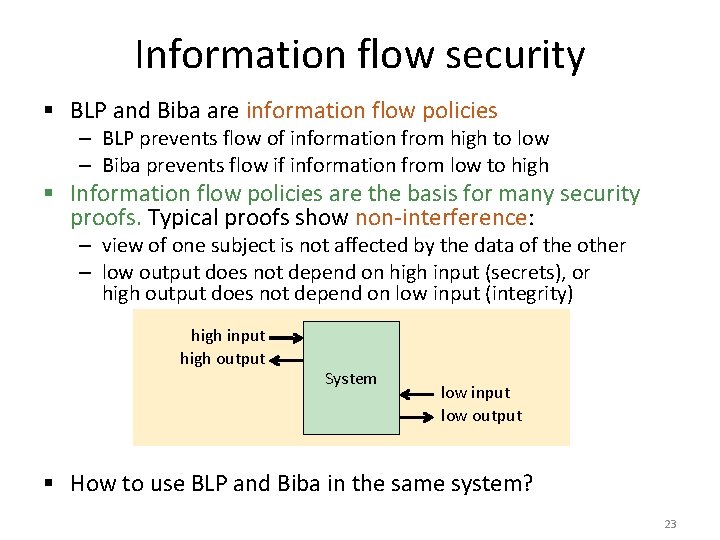
Information flow security § BLP and Biba are information flow policies – BLP prevents flow of information from high to low – Biba prevents flow if information from low to high § Information flow policies are the basis for many security proofs. Typical proofs show non-interference: – view of one subject is not affected by the data of the other – low output does not depend on high input (secrets), or high output does not depend on low input (integrity) high input high output System low input low output § How to use BLP and Biba in the same system? 23

High water mark, low water mark § How to classify an object that is created combining low and high information? High water mark policy for secrecy: always set the classification of output to the highest input Low water mark policy for integrity: always set the classification of output to the lowest input § Problem: – Over time, all documents will become top secret with the lowest integrity level § Even people can lose their clearance e. g. if they come to contact with a foreign agent 24

Upgrading and downgrading § Upgrading, downgrading: – In practice, security levels need to be changed by humans – E. g. downgrading documents for publication – E. g. upgrading intelligence reports that aggregate a lot of lowlevel data § Declassification = downgrading to unclassified level § Documents may need to be sanitized i. e. redacted before downgrading – E. g. removing personal names from military documents before publication § Sanitization may be difficult – E. g. US military painting black box over text in PDF; AOL publishing anonymized web search data – High subjects can use covert channels to leak data intentionally, e. g. hide data in photos ! 25

OTHER ACCESS CONTROL MODELS 26

Chinese Wall model § Conflicts of interest are common in business: – Consulting company, investment bank, or law office may be advising competing clients and must keep their information separate – The clients are assigned to different employees who do not speak to each other § To avoid conflicts of interest, the access control policy must take into account the information previously accessed by the subject § Chinese Wall model: – If subject S has previously accessed an object O 1 and the objects O 1 and O 2 are in a conflict of interest, then S may not access O 2 – Idea: subject can fall to different sides of the wall and cannot change sides later 28

Separation of duty § Chinese Wall is an example of separation of duty § Other separation of duty policies: – Expense claim requires two signatures: the claimant and an authorized approver, e. g. department manager; one person cannot act in both roles for the same expense claim – Auditors are often required to be from outside the company – Some safes have two locks, and the keys are given to two different persons – Lecturers issue grades to students but only study office staff can enter them into the study register § Unlike BLP and Biba, separation of duty policies are stateful, i. e. they need a memory of past events ! 29

ROLE-BASED ACCESS CONTROL 30

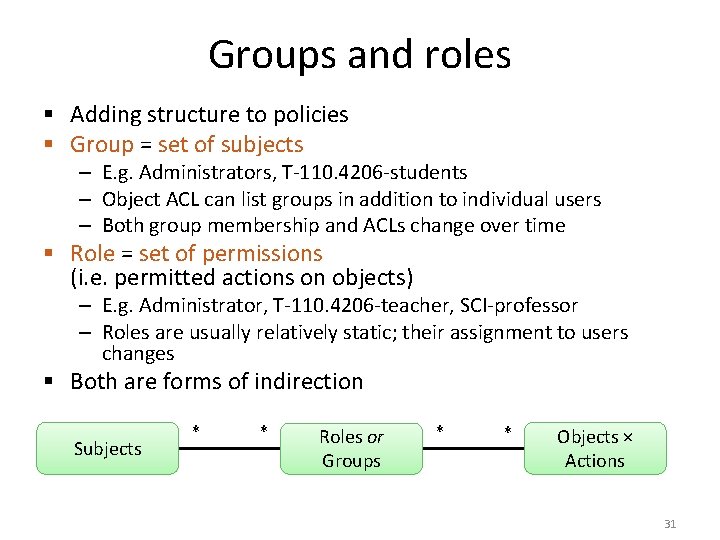
Groups and roles § Adding structure to policies § Group = set of subjects – E. g. Administrators, T-110. 4206 -students – Object ACL can list groups in addition to individual users – Both group membership and ACLs change over time § Role = set of permissions (i. e. permitted actions on objects) – E. g. Administrator, T-110. 4206 -teacher, SCI-professor – Roles are usually relatively static; their assignment to users changes § Both are forms of indirection Subjects * * Roles or Groups * * Objects × Actions 31

Role-based access control (RBAC) § NIST standard § Modeling high-level roles in an organization – E. g. Doctor, Nurse, Student, Lecturer, Course-assistant – Roles defined once; changed infrequently § Roles may be parameterized – E. g. Treating-doctor of patient S. Smith, Lecturer of T-110. 4206, Student of T-110. 4206 § Roles may form a hierarchy with rights inheritance – E. g. Lecturer and Teaching-assistant are Teaching-staff § Roles are assigned to users for longer term but activated on demand for each session § Constraints on role assignment and simultaneous activation can implement separation of duty 32

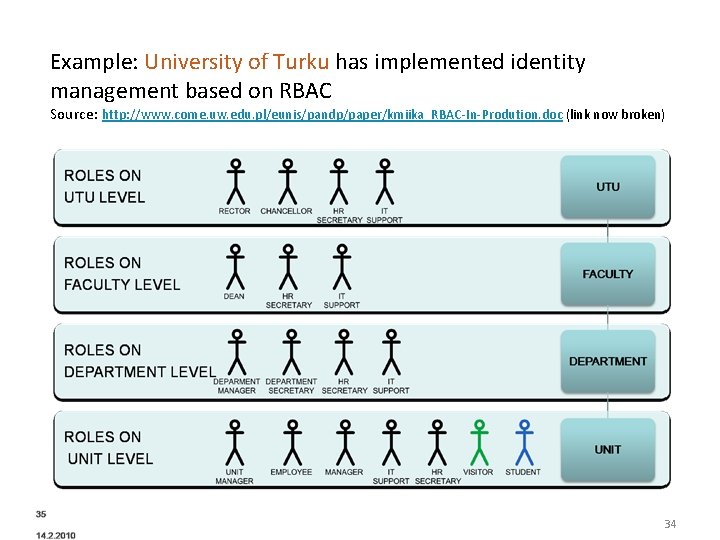
Example: University of Turku has implemented identity management based on RBAC Source: http: //www. come. uw. edu. pl/eunis/pandp/paper/kmiika_RBAC-In-Prodution. doc (link now broken) 34

Principals § Principal is a concept used in many AC systems § Subjects act on behalf of principals – Process (subject) executes as a specific user (principal) – User activating a different role becomes a different principal (principal = user in a role) – User acting as administrator or normal user are different principals § Access rights are often assigned to principals, not directly to subjects (indirection) § One subject may act on behalf of several principals simultaneously or at different times § Each principal should belong only to one user 35

Still other access control models § Originator-controlled AC (ORCON) – Creator of data retains control over access to it § Attribute-based AC – Access control is based in subject attributes (properties) instead of subject identity – AC = attribute verification + authorization – E. g. need to be 18 to buy tobacco; need to be an Aalto student to access course material – Enables anonymous access § Double-blinded review for scientific journals § Location or context-based AC § Many other AC models have been proposed 36

Reading material § Dieter Gollmann: Computer Security, 2 nd ed. , chapters 4, 8, 9; 3 rd ed. chapters 5– 6 § Edward Amoroso: Fundamentals of Computer Security Technology, chapters 6 -13 § Ross Anderson: Security Engineering, 2 nd ed. , chapter 8 38

Exercises § What are the subjects, object and actions in Noppa? § Can you think of security mechanisms outside computers which would need MAC but actually implement DAC? § What security labels and MAC policy would be suitable for Noppa? § Give examples of systems that require confidentiality or integrity but not both. § Which AC model and what kind of security labels could be used to describe virtual machine isolation? What label would be hypervisor or VM monitor get? § Could you define different confidentiality labels and integrity labels and then use both Bell-La. Padula and Biba policies in the same system? Give an example. § Define RBAC roles that could be used in the implementations of Noppa. § To what extent can your RBAC policy (above) be implemented with groups? § Consider separation-of-duty policies implemented in RBAC. How can conflicts be resolved if they arises after the role assignment? (E. g. a family new relation is between employees creates a conflict of interest. ) § What kind of access control is there (or could be) in social networks? § To what extent can access control prevent spam (email or other)? 39