http www svamindia com Official Title of ISO



















- Slides: 30

http: //www. svamindia. com/ Official Title of ISO 27001: 2013 "Information technology— Security techniques — Information security management systems — Requirements". An Awareness Training on ISO 27001: 2013 11/22/2020

What is Information Security The protection of information against unauthorized disclosure, transfer, modification, or destruction, whether accidental or intentional Information Assets • Asset is something that has “value to the organization” • Information assets of an organization can be: • • business data E-mail data Employee information Research records Price lists Tender documents Spoken in conversations over the telephone – – – Data stored on computers Transmitted across networks Printed out Written on a paper, sent by fax Stored on disks Held on microfilm Organization must determine which assets can materially affect the delivery of product/service by their absence or degradation Information Security Management relates to all types of information, be it paper-based, electronic or other. It determines how information is processed, stored, transferred, archived and destroyed. A secure information is one which ensures Confidentiality, Integrity, and Availability. It is all about protecting information assets from potential security breaches. 11/22/2020

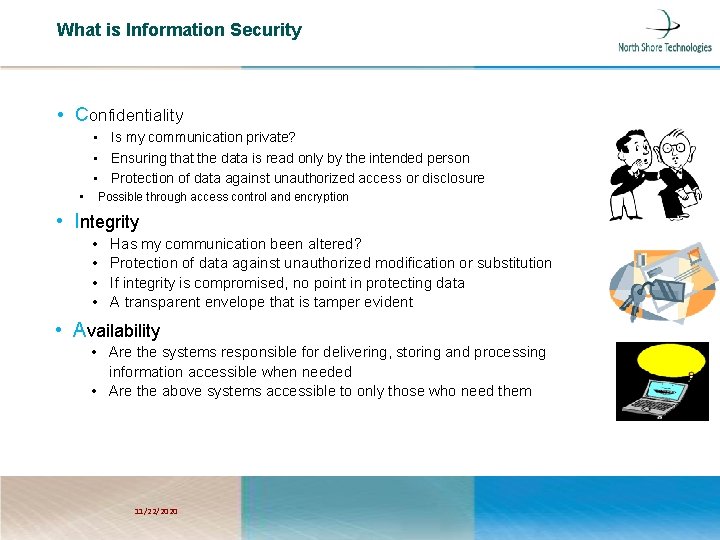
What is Information Security • Confidentiality • Is my communication private? • Ensuring that the data is read only by the intended person • Protection of data against unauthorized access or disclosure • Possible through access control and encryption • Integrity • • Has my communication been altered? Protection of data against unauthorized modification or substitution If integrity is compromised, no point in protecting data A transparent envelope that is tamper evident • Availability • Are the systems responsible for delivering, storing and processing information accessible when needed • Are the above systems accessible to only those who need them 11/22/2020

Need for ISMS Management Concerns • • Security Measures/Controls Market reputation Business continuity Disaster recovery Business loss Loss of confidential data Loss of customer confidence Legal liability Cost of security • • • Technical Procedural Physical Logical Personnel Management All these can be addressed effectively and efficiently only by establishing a proper Information Security Management System (ISMS) 11/22/2020 4

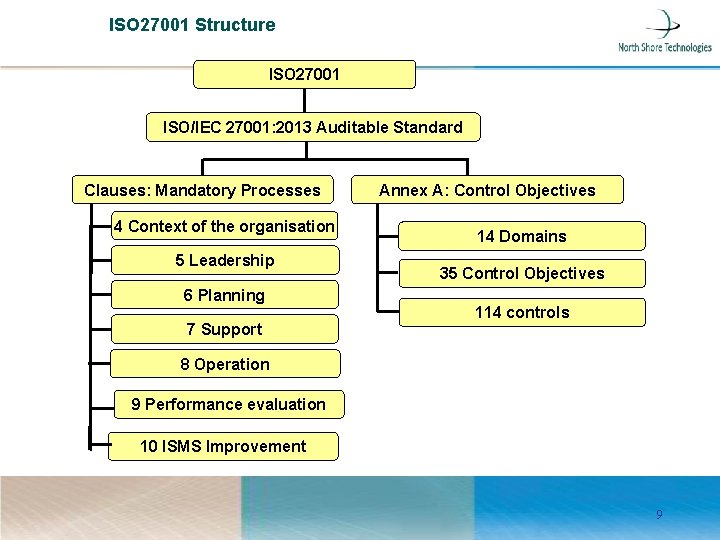
Comparing ISO 27001: 2005 to ISO 27001: 2013 ISO 27001: 2005 Structure The specification is spread across 5 clauses, which approach the ISMS from a managerial perspective. 4. Information security management system 5. Management responsibility 6. Internal ISMS audits 7. Management review of the ISMS 8. ISMS improvement 11/22/2020 ISO 27001: 2013 Structure The specification is spread across 7 clauses, which do not have to be followed in the order they are listed. 4. Context of the organization 5. Leadership 6. Planning 7. Support 8. Operation 9. Performance evaluation 10. Improvement

Comparing ISO 27001: 2005 to ISO 27001: 2013 ISO 27001: 2005 ISO 27001: 2013 Process The standard clearly states that it follows the PDCA (Plan-Do-Check-Act) model The standard does not specify any particular process model. The standard requires that a process of continual improvement is used Governance and management Senior management plays a major role. Management roles are described as ‘management’ and ‘top management’, removing reference to the board. Management and board engagement is high but the separation between board and management is not clear. The organization is that part of the business that falls within the scope, and not necessarily the legal entity. The board initiates the ISMS; management oversees the implementation of the ISMS 11/22/2020

Comparing ISO 27001: 2005 to ISO 27001: 2013 ISO 27001: 2005 ISO 27001: 2013 Risk assessments The definition of risk is the “combination of the probability of an event and its consequences”. The definition of risk is the “effect of uncertainty on objectives”, which may be positive or negative. The organization identifies risks against assets. Baseline controls based on regulatory, business and contractual obligations may be identified and implemented before the risk assessment is conducted. The asset owner determines how to treat the risk, accepting residual risk. Controls are drawn from Annex A is not exhaustive, so additional controls can be drawn from other sources. The Statement of Applicability records whether a control from Annex A is selected and why. The organization identifies risks to the organization's information the assessment does not have to be asset-based. The risk owner determines how to treat the risk, accepting residual risk. Controls are drawn from any source or control Set Selected controls are compared to those in Annex A. The Statement of Applicability records whether a control from Annex A is selected and why 11/22/2020

Comparing ISO 27001: 2005 to ISO 27001: 2013 ISO 27001: 2005 ISO 27001: 2013 Controls Annex A contains 133 controls across 11 control categories. Annex A contains 114 controls across 14 control categories Controls from other sources are used to ‘plug gaps’ not covered by Annex A controls Controls (from any source) are identified before referring to Annex A Documentation The standard recognizes two forms: documents and records. The standard makes no distinction between documents and records. Documents include policies, procedures, process diagrams, etc. Documents and records are subject to the same control requirements. Records track work completed, audit schedules, etc. 11/22/2020

ISO 27001 Structure ISO 27001 ISO/IEC 27001: 2013 Auditable Standard Clauses: Mandatory Processes 4 Context of the organisation 5 Leadership 6 Planning 7 Support Annex A: Control Objectives 14 Domains 35 Control Objectives 114 controls 8 Operation 9 Performance evaluation 10 ISMS Improvement 9

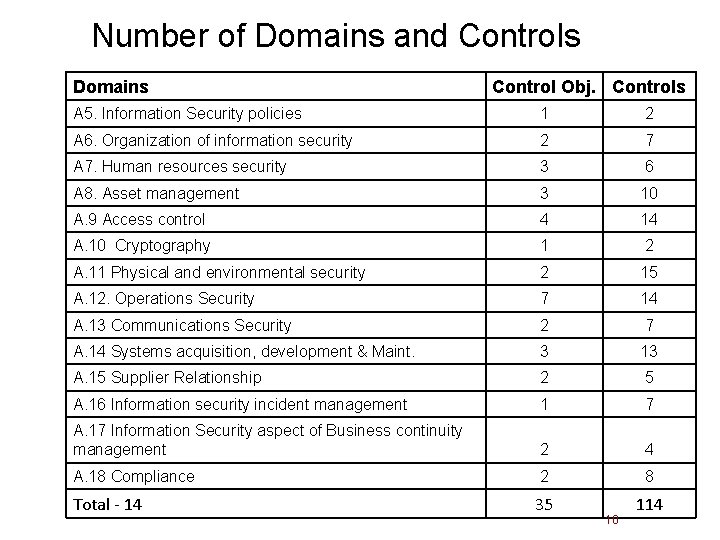
Number of Domains and Controls Domains Control Obj. Controls A 5. Information Security policies 1 2 A 6. Organization of information security 2 7 A 7. Human resources security 3 6 A 8. Asset management 3 10 A. 9 Access control 4 14 A. 10 Cryptography 1 2 A. 11 Physical and environmental security 2 15 A. 12. Operations Security 7 14 A. 13 Communications Security 2 7 A. 14 Systems acquisition, development & Maint. 3 13 A. 15 Supplier Relationship 2 5 A. 16 Information security incident management 1 7 A. 17 Information Security aspect of Business continuity management 2 4 A. 18 Compliance 2 8 Total - 14 35 114 10

ISO 27001 Main Clauses • Clause 4: Context of the organization • Understanding the organization and its context • Understanding the needs and expectation of interested parties. • Determining the scope of the information security management system • Information security management system • Clause 5: Leadership • Leadership and Commitment • Policy • Organization, roles, responsibilities and authorties • Clause 6: Planning • Action to address Risk and Opportunities • Information security objectives and Planning to achieve them • Clause 7: Support • Resource • Competence • Awareness • Communication • Documented Information 11/22/2020 11

ISO 27001 Main Clauses • Clause 8: Operation • Operation planning and control • Information security Risk assessment • Information security Risk Treatment • Clause 9: Performance evaluation • Monitoring, measurement, analysis and evaluation • Internal Audit • Management Review • Clause 10: Improvement • Non conformity and corrective action • Continual improvement 11/22/2020 12

ISMS Scope The Information Security Management Systems covering all business functions and processes associated with information assets to provide customers, employees and business partners benefits and services in the organization. 11/22/2020 13

Quality Policy & Business Objectives Quality & Security Policy : NST is committed to maintain high quality standards in delivering timely and cost effective solutions to our customers by continual improvement of our processes, instilling quality consciousness amongst all employees and recognizing the confidentiality, integrity and availability of information assets to relevant stakeholders including our customers. Business Objectives Key Objective 1: Provide high quality services to our clients. Key Objective 2: Continuous focus on employee satisfaction and competency development so as to reduce and stabilize employee attrition. Key Objective 3: Continual improvement of services to our internal & external customers. Key Objective 4: To secure its information assets and of its customers, NST shall deploy procedures to maintain confidentiality, integrity and availability of all information assets. Key Objective 5: To have year on year revenue increase while maintaining profitability.

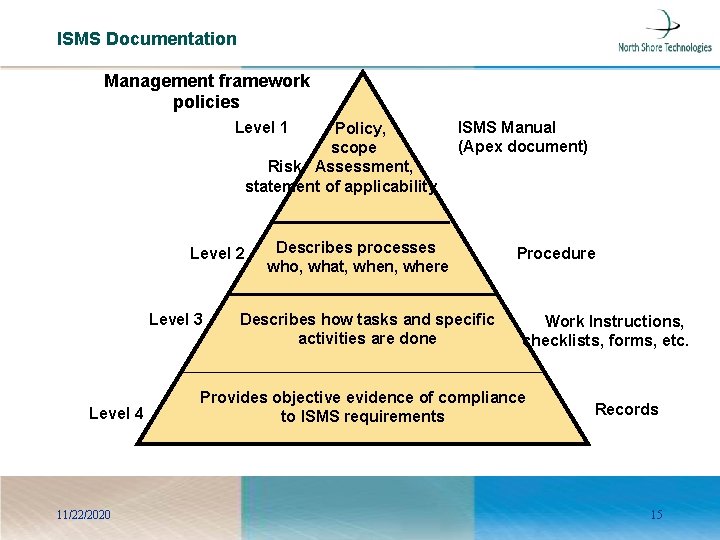
ISMS Documentation Management framework policies Level 1 Policy, scope Risk Assessment, statement of applicability Level 2 Level 3 Level 4 11/22/2020 ISMS Manual (Apex document) Describes processes who, what, when, where Describes how tasks and specific activities are done Procedure Work Instructions, checklists, forms, etc. Provides objective evidence of compliance to ISMS requirements Records 15

Risk Assessment and Management • Risk Assessment • • Identify all Stakeholders Identify Business Process Identify Operation Process Identify Assets Identify Risk on the basis of all Stakeholders Identify Threats and Vulnerabilities Evaluate Probability and Impact Calculate Risk Value • Risk treatment • • Mitigate/Reduce risk Avoid risk Transfer risk Accept risk • Risk Management • Mitigate the risk by appropriate controls • Evaluate controls periodically 11/22/2020 16

ISO 27001: 2013 Main Clauses-10 • Clause 4: Context of the Organization • Clause 5: Leadership • Clause 6: Planning • Clause 7: Support • Clause 8: Operation • Clause 9: Performance Evaluation • Clause 10: Improvement • Clause 11: Domain, Control Objective & Controls There are 14 domains 35 control objectives and 114 detail controls

Structure of ISO 27001: 2013 Controls 14 Domains comprising 35 Control Objectives and 114 Controls A. 5 Information security policies – controls on how the policies are written and reviewed A. 6 Organization of information security – controls on how the responsibilities are assigned; also includes the controls for mobile devices and teleworking A. 7 Human resources security – controls prior to employment, during, and after the employment A. 8 Asset management – controls related to inventory of assets and acceptable use, also for information classification and media handling A. 9 Access control – controls for Access control policy, user access management, system and application access control, and user Responsibilities A. 10 Cryptography – controls related to encryption and key management A. 11 Physical and environmental security – controls defining secure areas, entry controls, protection against threats, equipment security, secure disposal, clear desk and clear screen policy, etc. A. 12 Operational security – lots of controls related to management of IT production: change management, capacity management, malware, backup, logging, monitoring, installation, vulnerabilities, etc. A. 13 Communications security – controls related to network security, segregation, Network services, transfer of information, messaging, etc.

Structure of ISO 27001: 2013 Controls A. 14 System acquisition, development and maintenance – controls defining security requirements and security in development and support processes A. 15 Supplier relationships – controls on what to include in agreements, and how to monitor the suppliers A. 16 Information security incident management – controls for reporting events and weaknesses, defining responsibilities, response procedures, and collection of evidence A. 17 Information security aspects of business continuity management – controls requiring the planning of business continuity, procedures, verification and reviewing, and IT redundancy A. 18 Compliance – controls requiring the identification of applicable laws and regulations, intellectual property protection, personal data protection, and reviews of information security 19

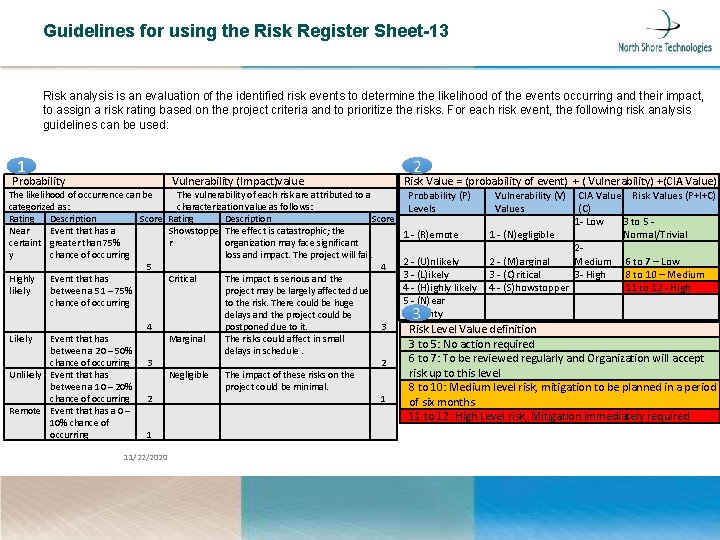
Guidelines for using the Risk Register Sheet-13 Risk analysis is an evaluation of the identified risk events to determine the likelihood of the events occurring and their impact, to assign a risk rating based on the project criteria and to prioritize the risks. For each risk event, the following risk analysis guidelines can be used: 1 Probability Vulnerability (Impact)value The likelihood of occurrence can be The vulnerability of each risk are attributed to a categorized as: characterization value as follows: Rating Description Score Rating Description Score Near Event that has a Showstoppe The effect is catastrophic; the certaint greater than 75% r organization may face significant y chance of occurring loss and impact. The project will fail. 5 4 Highly Event that has Critical The impact is serious and the likely between a 51 – 75% project may be largely affected due chance of occurring to the risk. There could be huge delays and the project could be 4 postponed due to it. 3 Likely Event that has Marginal The risks could affect in small between a 20 – 50% delays in schedule. chance of occurring 3 2 Unlikely Event that has Negligible The impact of these risks on the between a 10 – 20% project could be minimal. chance of occurring 2 1 Remote Event that has a 0 – 10% chance of occurring 1 11/22/2020 2 Risk Value = (probability of event) + ( Vulnerability) +(CIA Value) Probability (P) Levels Vulnerability (V) CIA Value Risk Values (P+I+C) Values (C) 1 - Low 3 to 5 - 1 - (R)emote 1 - (N)egligible Normal/Trivial 2 - 2 - (U)nlikely 2 - (M)arginal Medium 6 to 7 – Low 3 - High 3 - (L)ikely 3 - (C)ritical 8 to 10 – Medium 4 - (H)ighly likely 4 - (S)howstopper 11 to 12 - High 5 - (N)ear certainty 3 Risk Level Value definition 3 to 5: No action required 6 to 7: To be reviewed regularly and Organization will accept risk up to this level 8 to 10: Medium level risk, mitigation to be planned in a period of six months 11 to 12: High Level risk, Mitigation immediately required

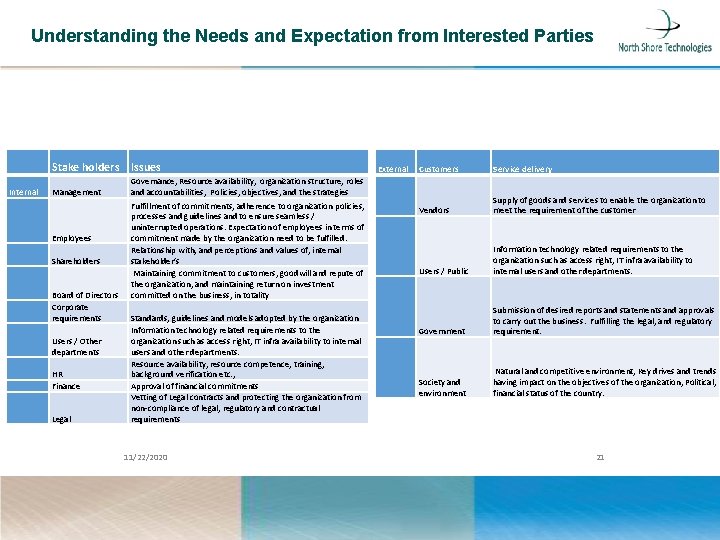
Understanding the Needs and Expectation from Interested Parties Internal Stake holders Issues Management Employees Shareholders Board of Directors Corporate requirements Users / Other departments HR Finance Legal Governance, Resource availability, organization structure, roles and accountabilities, Policies, objectives, and the strategies Fulfillment of commitments, adherence to organization policies, processes and guidelines and to ensure seamless / uninterrupted operations. Expectation of employees in terms of commitment made by the organization need to be fulfilled. Relationship with, and perceptions and values of, internal stakeholder’s Maintaining commitment to customers, goodwill and repute of the organization, and maintaining return on investment committed on the business, in totality Standards, guidelines and models adopted by the organization Information technology related requirements to the organization such as access right, IT infra availability to internal users and other departments. Resource availability, resource competence, training, background verification etc. , Approval of financial commitments Vetting of Legal contracts and protecting the organization from non-compliance of legal, regulatory and contractual requirements 11/22/2020 External Customers Service delivery Vendors Supply of goods and services to enable the organization to meet the requirement of the customer Users / Public Information technology related requirements to the organization such as access right, IT infra availability to internal users and other departments. Government Submission of desired reports and statements and approvals to carry out the business. Fulfilling the legal, and regulatory requirement. Society and environment Natural and competitive environment, Key drives and trends having impact on the objectives of the organization, Political, financial status of the country. 21

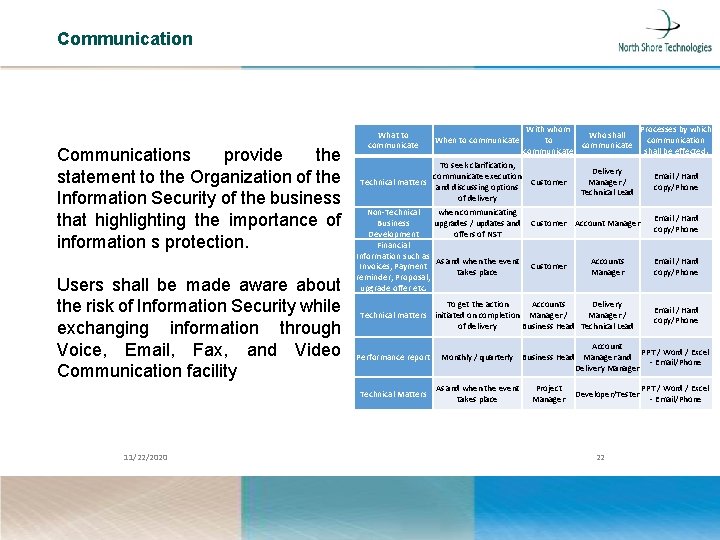
Communications provide the statement to the Organization of the Information Security of the business that highlighting the importance of information s protection. Users shall be made aware about the risk of Information Security while exchanging information through Voice, Email, Fax, and Video Communication facility What to communicate With whom Processes by which Who shall to communication communicate shall be effected. To seek clarification, communicate execution Technical matters Customer and discussing options of delivery Delivery Manager / Technical Lead Non-Technical when communicating Business upgrades / updates and Customer Account Manager Development offers of NST Financial Information such as As and when the event Accounts Invoices, Payment Customer takes place Manager reminder, Proposal, upgrade offer etc. To get the action Accounts Delivery Technical matters initiated on completion Manager / of delivery Business Head Technical Lead Performance report Technical Matters 11/22/2020 When to communicate Email / Hard copy/Phone Account PPT / Word / Excel Monthly / quarterly Business Head Manager and - Email/Phone Delivery Manager As and when the event takes place Project Manager Developer/Tester 22 PPT / Word / Excel - Email/Phone

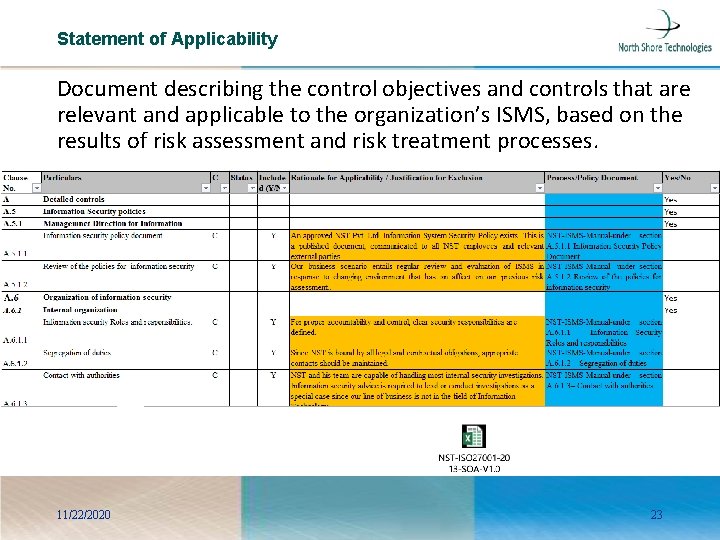
Statement of Applicability Document describing the control objectives and controls that are relevant and applicable to the organization’s ISMS, based on the results of risk assessment and risk treatment processes. 11/22/2020 23

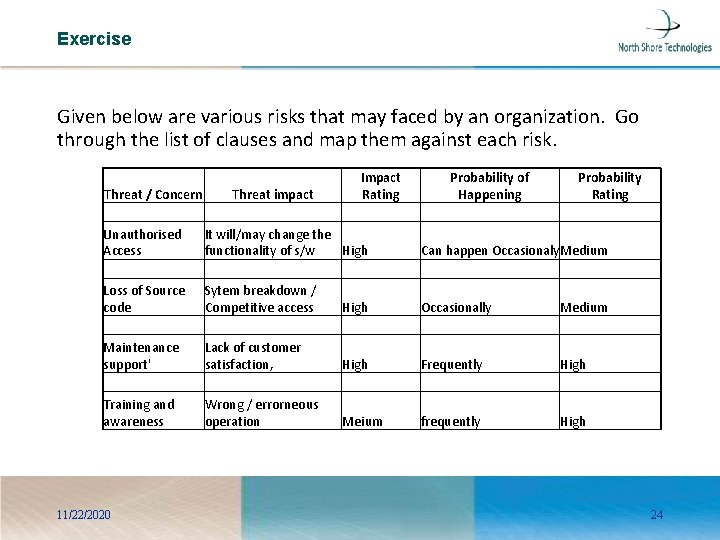
Exercise Given below are various risks that may faced by an organization. Go through the list of clauses and map them against each risk. Threat / Concern Impact Rating Threat impact Probability of Happening Probability Rating Unauthorised Access It will/may change the functionality of s/w High Can happen Occasionaly. Medium Loss of Source code Sytem breakdown / Competitive access High Occasionally Medium Maintenance support' Lack of customer satisfaction, High Frequently High Training and awareness Wrong / errorneous operation Meium frequently High 11/22/2020 24

Generic Changes from ISO 27001: 2005 standard • Puts more emphasis on measuring and evaluating how well an organization's ISMS is performing • New section on Outsourcing • Does not emphasize the Plan-Do-Check-Act cycle. • More attention is paid to the organizational context of information security. • Risk assessment has changed. • Management commitment requirements have a focus on “leadership” • Preventive action has been replaced with “actions to address, risks and opportunities” • SOA requirements are similar, with more clarity on the need to determine controls by the risk treatment process • Controls in Annex A have been modified to reflect changing threats, remove duplication and have a more logical grouping. • Stress on maintaining documented information, rather than information record • Greater emphasis is on setting objectives, monitoring performance and metric 25

Risk assessment and risk treatment • Risk management is the activities to make clear what kind of information security risks may occur, determine the risk treatment and manage the risks. • The activities to make the risks clear are referred to as "risk assessment". • Identify the risk owners • The actions taken for the risks, which are made clear, are referred to as "risk treatment". • Avoiding: Withdrawal of business, etc. • Taking or increasing risk in order to pursue an opportunity: Additional investment, etc. • Changing the likelihood of risks: Performing preventive measures, etc. • Removing the risk sources: Performing preventive measures, etc. • Changing the consequences of risks: Preparing the actions taken for the possible situations, etc. • Sharing the risks with another parties: Insuring the risks, etc. • Retaining the risk as they are: Accepting the risks upon recognition • This is the same as the "management judgment" conventionally conducted by Management.

New controls 14. 2. 1 Secure development policy – rules for development of software and information systems 14. 2. 5 Secure system engineering principles – principles for system engineering 14. 2. 6 Secure development environment – establishing and protecting development environment 14. 2. 8 System security testing – tests of security functionality 16. 1. 4 Assessment of and decision on information security events – this is part of incident management 17. 2. 1 Availability of information processing facilities – achieving redundancy 27

Conceptual changes New/Updated Concepts Explanation Context of the organization The environment in which the organization operates Issues, risks and opportunities Replaces preventive action Interested parties Replaces stakeholders Leadership Requirements specific to top management Communication There are explicit requirements for both internal and external communications Information security objectives are now to be set at relevant functions and levels Risk assessment Identification of assets, threats and vulnerabilities is no longer a prerequisite for the identification of information security risks. (6. 1. 2 d) – Now emphasis is on impact and Probability Risk owner Replaces asset owner Risk treatment plan The effectiveness of the risk treatment plan is now regarded as being more important than the effectiveness of controls Controls Now determined during the process of risk treatment. Documented information Replaces documents and records Performance evaluation Covers the measurement of ISMS and risk treatment plan effectiveness Continual improvement Methodologies other than Plan-Do-Check-Act (PDCA) may be used 28

List of controls removed from ISO 27001: 2005 A. 06. 01. 1 Management commitment to information security A. 06. 01. 2 Information security coordination A. 06. 01. 4 Authorization process for information processing facilities A. 06. 02. 1 Identification of risks related to external parties A. 06. 02. 2 Addressing security when dealing with customers A. 10. 02. 1 Service delivery A. 10. 04. 2: Controls against Mobile code A. 10. 07. 4 Security of system documentation A. 10. 08. 5 Business Information Systems A. 10. 09. 3 Publicly available information A. 10. 2 Monitoring system use A. 10. 4 Administrator and operator logs A. 10. 5 Fault logging A. 11. 04. 2 User authentication for external connections A. 11. 04. 3 Equipment identification in networks A. 11. 04. 4 Remote Diagnostic and configuration port A. 11. 04. 6 Network Connection control A. 11. 04. 7 Network routing control A. 11. 05. 2 User identification and authentication A. 11. 05. 5 Session time-out A. 11. 05. 6 Limitation of connection time A. 11. 06. 2 Sensitive system isolation A. 12. 02. 1: Input data validation A. 12. 02. 2 Control of internal processing A. 12. 02. 3 Message integrity A. 12. 02. 4 Output data validation A. 12. 05. 4 Information leakage A. 14. 01. 1 Including information security in the business continuity management process A. 14. 01. 3 Developing and implementing continuity plans including formation security. A. 14. 01. 4 Business continuity planning framework A. 15. 01. 5 Prevention of misuse of information processing facilities 64

Click to edit Master title style Thank you
 Iso 9000 iso 9001 iso 9002 iso 9003 iso 9004
Iso 9000 iso 9001 iso 9002 iso 9003 iso 9004 Bài thơ mẹ đi làm từ sáng sớm
Bài thơ mẹ đi làm từ sáng sớm Cơm
Cơm Daffodil drug
Daffodil drug Title title
Title title Prefatory part of report
Prefatory part of report Iso27k toolkit
Iso27k toolkit Iso 9001 iso 14001 ohsas 18001 comparison
Iso 9001 iso 14001 ohsas 18001 comparison Proyeccion primer angulo
Proyeccion primer angulo Iso 9000 iso 22000
Iso 9000 iso 22000 Iso 8583 to iso 20022 mapping
Iso 8583 to iso 20022 mapping Siat.ung.ac.id
Siat.ung.ac.id Http //mbs.meb.gov.tr/ http //www.alantercihleri.com
Http //mbs.meb.gov.tr/ http //www.alantercihleri.com Internet official protocol standards
Internet official protocol standards 88 official constellations
88 official constellations New zealand official languages english
New zealand official languages english Non official compendia
Non official compendia Microsoft official academic course microsoft excel 2016
Microsoft official academic course microsoft excel 2016 Ffa colors are
Ffa colors are Ffa dresscode
Ffa dresscode Microsoft official academic course
Microsoft official academic course Filip simovic teretana
Filip simovic teretana Microsoft official academic course microsoft word 2016
Microsoft official academic course microsoft word 2016 How does antony show himself to be ruthless in this scene
How does antony show himself to be ruthless in this scene Crista lopes
Crista lopes The official nordstrom organization chart puts the
The official nordstrom organization chart puts the Official statistics from mobile phone data
Official statistics from mobile phone data Electronic official personnel file
Electronic official personnel file Big data official statistics
Big data official statistics What are the official ffa colors? *
What are the official ffa colors? * Laos official language
Laos official language