HIPAA awareness training and fear mongering Steve Allen



































































- Slides: 76

HIPAA awareness training and fear mongering Steve Allen Adams, MCS, COC, CPMA, CPC-I, PCS, FCS, COA Steve. adams@ingaugehsi. com 770 -709 -3598 Becauseyourpatientscomefirst.

www. thecodingeducator. com

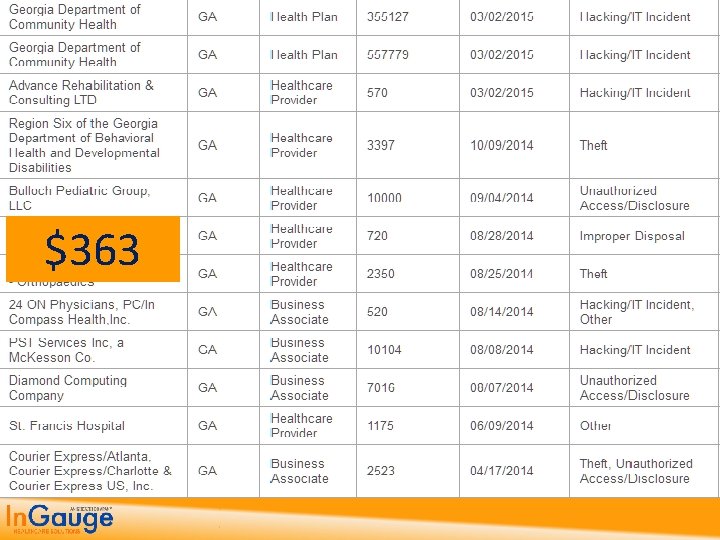
$363

Topics 1. The Findings and Penalties from Recent HIPAA Reviews 2. The Past, Present and Future of HIPAA 3. The HIPAA Privacy Rules and what they mean to you 4. Implementing the HIPAA Security Rule Standards 5. Getting up to date with HIPAA HITech Rules and Standards 6. How to get started on being HIPAA Compliant

1. Findings from Recent Government Reviews

4 Tiers of Penalties Tier A is for violations in which the offender didn’t realize he or she violated the Act and would have handled the matter differently. – $100 fine for each violation, and – $25, 000, maximum total imposed for the calendar year. Tier B is for violations due to reasonable cause, but not “willful neglect. ” – $1, 000 fine for each violation, and – $100, 000, maximum total imposed for the calendar year. Tier C is for violations due to willful neglect that the organization ultimately corrected. – $10, 000 fine for each violation, and – $250, 000, maximum total imposed for the calendar year. Tier D is for violations of willful neglect that the organization did not correct. – $50, 000 fine for each violation, and – $1, 500, 000, maximum total imposed for the calendar year.

Small Practice HIPAA Violations: 65% Security Rule 26% Privacy Rule 9% Breech Rule (HITech)

2. Past, Present and Future of HIPAA

HIPAA History & Update • The Health Insurance Portability and Accountability Act (HIPAA), also referred to as the Kennedy - Kassebaum, bill was passed by Congress in 1996 to provide consumers with: 1. greater access to health care insurance; 2. protect the privacy of health care data; and 3. promote more standardization and efficiency in the health care industry.

HIPAA is currently broken up into five (5) titles

HIPAA Titles • Title I – Health Care Access, Portability, and Renewability • Title II – Preventing Healthcare Fraud and Abuse, Administrative Simplification, Medical Liability Reform. • Title III – Tax Related Health Provisions • Title IV – Application and Enforcement of Group Health Plan Requirements • Title V – Revenue Offsets

Administrative Simplification Provisions that required HHS to adopt national standards for: 1. electronic health care transactions and code sets, 2. unique health identifiers (NPI), and 3. security. Congress recognized that advances in electronic technology could erode the privacy of health information. Consequently, they incorporated into HIPAA provisions that mandated the adoption of Federal privacy and security protections for individually identifiable health information. Next came the HITECH law in the ARRA.

“Privacy”, “Security” and “HITECH” aren’t in the name “HIPAA, ” but they present some of our biggest challenges today in Healthcare

What’s The Difference? • In general, the Privacy Rule covers protected health information (PHI) in all forms. The Privacy Rule sets the standards spelling out how you should control PHI. • The Security Rule only covers PHI in electronic form. The Security Rule defines the standards that you must implement to provide basic safeguards to protect EPHI. • The HITECH Act makes significant changes to all provisions of HIPAA (Breech rule) of which the Privacy Rule and Security Rule are a part.

Privacy Rule

Privacy Rule HHS published a final Privacy Rule in December 2000, which was later modified in 2002. This Rule set national standards for the protection of individually identifiable health information by three types of covered entities: 1. health plans, 2. health care clearinghouses, and 3. health care providers who conduct the standard health care transactions electronically. Compliance with the Privacy Rule was required as of April 14, 2003.

Security Rule Standards

Security Rule Standards HHS published a final Security Rule in 2003. This Rule sets national standards for protecting the 1. confidentiality, 2. integrity, and 3. availability of electronic protected health information. Compliance with the Security Rule was required as of April 20, 2005.

HITECH Act

HITECH Act The HITECH Act was enacted under Title XIII of the American Recovery and Reinvestment Act of 2009. It changes/updates both the privacy and security law as well as allowing for increased penalties for violations of both laws.

3. Privacy Rule is the one you are more familiar with for PHI (manual)

HIPAA Privacy Rule • The Privacy Rule covers all Protected Health Information(PHI) • This is information that can identify the patient to the health record • De-identified Information does not have to be protected by HIPAA • Privacy Rule is concerned with guarding the confidentiality of PHI in ALL formats; paper, oral or electronic.

Types of PHI • • Names • Address/Zip Codes • All Dates Telephone & Fax Numbers • • E-mail Addresses Social Security Numbers • Medical Record Numbers • Health Plan Numbers License Numbers Vehicle Identification Numbers Account Numbers Biometric Identifiers Full Face Photos Any Other Unique Identifying Number, Characteristic or Code

HIPAA Privacy Rule • The HIPAA Privacy Rule regulates the use and disclosure of Protected Health Information (PHI) held by "covered entities" (generally, health care clearinghouses, employer sponsored health plans, health insurers, and medical service providers that engage in certain transactions.

Types of PHI Disclosures 1. No Authorization Required to: – To disclose PHI to the patient – To use or disclose PHI for treatment, payment or healthcare operations – Certain disclosures required by law (for example, public health reporting of diseases, abuse/neglect cases, etc. ) 2. No Authorization Required - Must Offer Opportunity to Object: – Patient must be offered an opportunity to object before discussing PHI with a patient’s family or friends – Limited PHI (e. g. , patient’s hospital room/location number) is included in the “Hospital Directory” but patients must be offered “Opt Out” opportunity – Certain disclosures to clergy members 3. Authorization Is Required: – For Research (unless IRB approves a waiver of authorization) – To conduct certain fundraising activities – For marketing activities

HIPAA Privacy Rule • Any other disclosures of PHI (Protected Health Information) require the covered entity to obtain written authorization from the individual for the disclosure. • However, when a covered entity discloses any PHI, it must make a reasonable effort to disclose only the minimum necessary information required to achieve its purpose.

HIPAA Privacy Rule • What is the “minimum necessary” standard? The Privacy Rule generally requires covered entities to take reasonable steps to limit the use or disclosure of, and requests for, protected health information to the minimum necessary to accomplish the intended purpose

http: //www. hhs. gov/ocr/privacy/hipaa/understanding/summary/index. html 4. Security Rule is the most confusing and least clearly explained (manual)

Core Objective 15 Protect electronic health information created or maintained by the certified EHR technology through the implementation of appropriate technical capabilities. - 170. 302 (o)-(w) Conduct or review a security risk analysis per 45 CFR 164. 308 (a)(1) and implement security updates as necessary and correct identified security deficiencies as part of its risk management process

Security Rule • While the Privacy Rule pertains to all Protected Health Information (PHI) including paper and electronic, the Security Rule deals specifically with Electronic Protected Health Information (EPHI).

HIPAA Security Rule • Ensures that the business processes and technology used is not vulnerable to threats. • 18 standards and 44 implementation specifications broken down into: 1. Administrative Safeguards (9) 2. Physical Safeguards (4) 3. Technical Safeguards (5)

HIPAA Security Rule • Each Implementation Specification is either: Required or Addressable • Even if only Addressable the practice must write in a policy why the Implementation Specification is not needed. • All Required specifications must be implemented and included in a written policy and procedure.

Administrative Safeguards (9) policies and procedures designed to clearly show the entity will comply with the act www. hhs. gov/ocr/privacy/hipaa/administrative/securityrule/adminsafeguards. pdf

Administrative Standards 1. Security Management Process q q Risk Analysis - Required Risk Management - Required Sanction Policy - Required Information System Activity Review - Required 2. Assigned Security Responsibility q Identify the practices HIPAA Security Official – Required Identify the security official who is responsible for the development and implementation of the policies and procedures for the entity

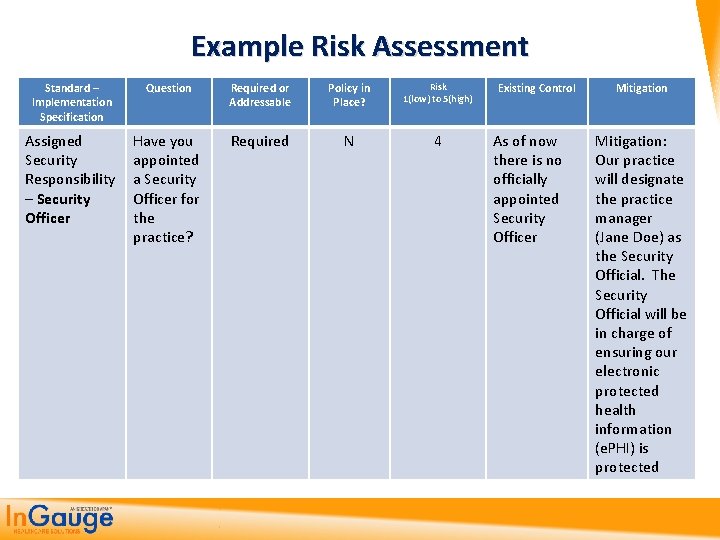
Example Risk Assessment Standard – Implementation Specification Question Required or Addressable Policy in Place? Risk 1(low) to 5(high) Assigned Security Responsibility – Security Officer Have you appointed a Security Officer for the practice? Required N 4 Existing Control As of now there is no officially appointed Security Officer Mitigation: Our practice will designate the practice manager (Jane Doe) as the Security Official. The Security Official will be in charge of ensuring our electronic protected health information (e. PHI) is protected

Now The Policy Administrative Safeguards Standard: Implementation Specification: Assigned Security Responsibility Security Officer(Required) Requirement: Identify the security officer who is responsible for developing and implementing the policies and procedures required by the HIPAA Security Rule for the protection of electronic protected health information. Policy: Our practice has designated a security officer who will be in charge of ensuring our electronic protected health information (e. PHI) is protected. Procedure: Our practice has designated the following individual as our HIPAA Security Officer: Jane Doe 1123 Nowhere Dr Beer Creek, WY 11111 (344) 333 -3333 The security officer may delegate tasks and responsibilities but is ultimately responsible for protecting the confidentiality of protected health information. Key responsibilities include: • Developing and implementing policies, procedures, and guidelines to direct and carry out the objectives of our security program, including policies and procedures that govern: • maintaining up to date inventory of software and hardware • ensuring the privacy and security of electronic health information, computer networks, servers, and wireless network • developing and implementing disaster recovery program • providing physical security • providing ongoing and initial HIPAA Security training • investigating, responding to, and remedying breaches and security incidents • supervising vendor personnel or business associates who perform technical maintenance and ensuring they have proper training regarding these policies and procedures as well as signing our Business Associate Agreement where applicable.

Administrative Standards 3. Workforce Security q Authorization/Supervision – Addressable q Workforce Clearance Procedures – Addressable q Termination Procedures - Addressable Implement procedures for terminating access to electronic protected health information when the employment of a workforce member ends… 4. Information Access Management q Isolating Healthcare clearinghouse functions – Required Third party must take responsibility as of HITECH act q Access Authorization - Required q Access Establishment and Modification - Addressable

Administrative Standards 5. Security Awareness and Training q q Security Reminders – Addressable Protection from Malicious software – Addressable Log-in monitoring – Addressable Password Management – Addressable Procedures for creating, changing, and safeguarding passwords 6. Security Incident Procedures q Response and Reporting – Required Your practice is required to respond and mitigate any harmful effects of security incidents All incidents must be logged and kept in a report

Administrative Standards 7. Contingency Plan q q q Data Backup Plan – Required Disaster Recovery Plan – Required Emergency Mode Operation Plan – Required Testing and Revision – Addressable Applications and Data Criticality Analysis – Addressable Establish (and implement as needed) policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure, and natural disaster) that damages systems that contain electronic protected health information. ” 8. Evaluation – q Periodic evaluation of practice levels of risk – Required At least annually

Administrative Standards 9. Business Associates Contract q Require all business associates to sign BAC - Required Have all business associates been identified? Business associates may include clearinghouses, medical billing services, vendors of hardware and software, external consultants, lawyers, transcription contractors, or others who have access to EPHI.

Physical Safeguards (4) controlling physical access to protect against inappropriate access to protected data www. hhs. gov/ocr/privacy/hipaa/administrative/securityrule/physsafeguards. pdf

Physical Safeguards 10. Facility Access Controls q Contingency Operations – Addressable Physical access to facility (part of Disaster Recovery) q Facility Security Plan – Addressable Physical facility safeguards (i. e. alarm system, sign in sheets, etc) q Access Control and Validation – Addressable Controls that validate a persons physical access q Maintenance Records – Addressable 11. Workstation Use – Required Proper usage of workstations documented 12. Workstation Security – Required Physical safeguards to restrict access to workstations from unauthorized users.

Physical Safeguards 13. Device and Media Controls q. Disposal – Required Media must be purged or destroyed congruent with NIST Guidelines for Media Sanitation. – don’t just throw away a hard drive… q. Media Re-Use – Required Media must be wiped clean before being re-used. - PC’s containing e. PHI cannot be re-used unless e. PHI has been removed. q. Accountability – Addressable q. Data Backup and Storage - Addressable

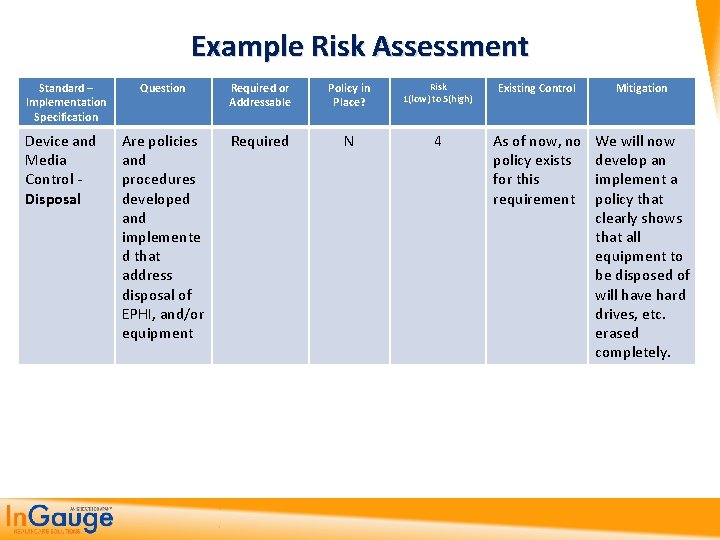
Example Risk Assessment Standard – Implementation Specification Device and Media Control - Disposal Question Required or Addressable Policy in Place? Risk 1(low) to 5(high) Existing Control Mitigation Are policies and procedures developed and implemente d that address disposal of EPHI, and/or equipment Required N 4 As of now, no policy exists for this requirement We will now develop an implement a policy that clearly shows that all equipment to be disposed of will have hard drives, etc. erased completely.

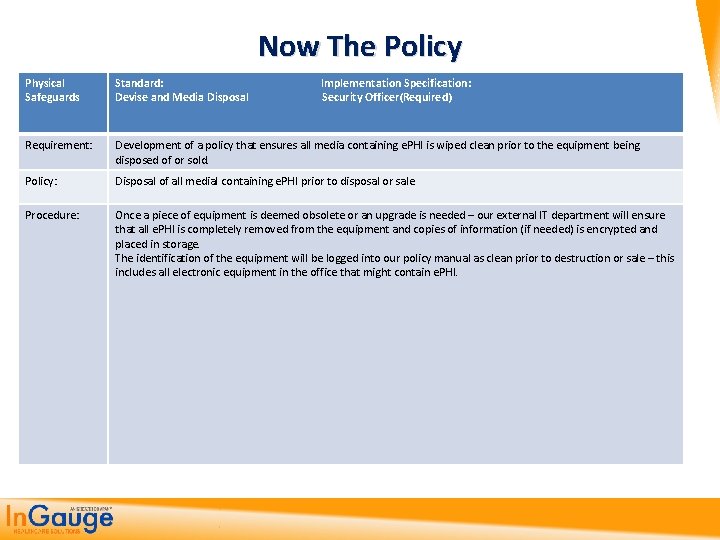
Now The Policy Physical Safeguards Standard: Implementation Specification: Devise and Media Disposal Security Officer(Required) Requirement: Development of a policy that ensures all media containing e. PHI is wiped clean prior to the equipment being disposed of or sold. Policy: Disposal of all medial containing e. PHI prior to disposal or sale Procedure: Once a piece of equipment is deemed obsolete or an upgrade is needed – our external IT department will ensure that all e. PHI is completely removed from the equipment and copies of information (if needed) is encrypted and placed in storage. The identification of the equipment will be logged into our policy manual as clean prior to destruction or sale – this includes all electronic equipment in the office that might contain e. PHI.

Technical Safeguards (5) controlling access to computer systems and enabling covered entities to protect communications containing PHI transmitted electronically over open networks from being intercepted by anyone other than the intended recipient. www. hhs. gov/ocr/privacy/hipaa/administrative/securityrule/techsafeguards. pdf

Technical Safeguards 14. Access Control q. Unique User Identification – Required q. Emergency Access Procedure - Required q. Automatic Log Off – Addressable q. Encryption and Decryption – Addressable e. PHI at rest or in a database must be encrypted 15. Audit Controls – Required Requires that mechanisms are in place that record and examine activity in information systems that contain e. PHI.

Technical Safeguards 16. Integrity Controls q Mechanism to Authenticate e. PHI – Addressable Ensure all e. PHI that is transmitted is not improperly modified without detection. (most competent EMR systems have audit trails that track which user did what) 17. Person/Entity Authentication – Required Procedures that verify a person or entity seeking access to e. PHI is who they claim to be. Requires password management and audit trails that enable practice to authenticate who is accessing , altering or transmitting e. PHI.

Example Risk Assessment Standard – Implementation Specification Technical Safeguards – Automatic Logoff Question Required or Addressable Does your Addressable current system have automatic logoff capability to ensure unauthorize d users do not have access Policy in Place? Risk 1(low) to 5(high) Existing Control N 3 None at this time Mitigation We will develop this policy

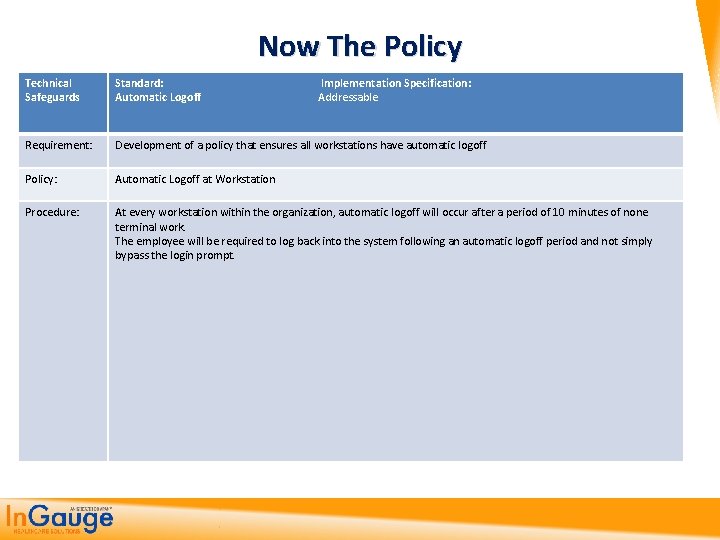
Now The Policy Technical Safeguards Standard: Implementation Specification: Automatic Logoff Addressable Requirement: Development of a policy that ensures all workstations have automatic logoff Policy: Automatic Logoff at Workstation Procedure: At every workstation within the organization, automatic logoff will occur after a period of 10 minutes of none terminal work. The employee will be required to log back into the system following an automatic logoff period and not simply bypass the login prompt.

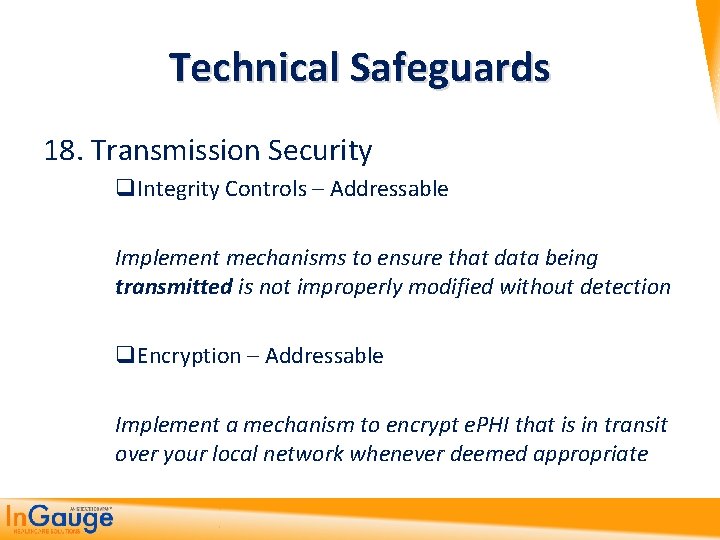
Technical Safeguards 18. Transmission Security q. Integrity Controls – Addressable Implement mechanisms to ensure that data being transmitted is not improperly modified without detection q. Encryption – Addressable Implement a mechanism to encrypt e. PHI that is in transit over your local network whenever deemed appropriate

Policies and Procedures Standard A covered entity must implement “reasonable and appropriate” policies and procedures to comply with the standards and implementation specifications.

5. HITECH Act Under HIPAA and ARRA

HITECH Act The 2009 American Recovery and Reinvestment Act (ARRA) includes a section called the Health Information Technology for Economic and Clinical Health (HITECH) Act. It essentially makes 15 changes that have placed a huge burden on small and large physician practices:

HITECH Act Objectives Enforcement is strengthened significantly 1. Penalties are increased in the new Civil Monetary Penalty (CMP) System 2. Enforcement is more proactive, more punitive and by more parties 3. Additional audit authority is now provided to HHS audit CEs and BAs Business Associates and others are fully and completely “in scope” 4. BAs are now statutorily obligated to comply with the relevant regulations. 5. Adds temporary breach notification requirements to vendors of personal health records Security Provisions are strengthened and clarified 6. Data protected is expanded beyond EPHI to include other personal information 7. More specific guidance on technical safeguards is provided by HHS annually 8. New data breach notification requirement

HITECH Act Objectives Privacy Provisions are strengthened and clarified 9. Individual right to request restrictions on use and disclosure of PHI is now mandatory 10. The definition of “minimum necessary” PHI to use/disclose is clarified 11. Disclosure accounting is strengthened - eliminates any exceptions from the disclosure accounting rules 12. Tightens restrictions on use of protected health information for marketing purposes 13. Requires clear and conspicuous opt-out opportunity for fund-raising communications 14. Consumers now have the right to receive an electronic copy of their PHI 15. Prohibits a CE or BA from receiving payment in exchange for any PHI

Business Associate Agreements Have to change these to now reflect the BA is responsible for losses of information or a breech and not you.

Business Associate Agreements

Breach Notifications

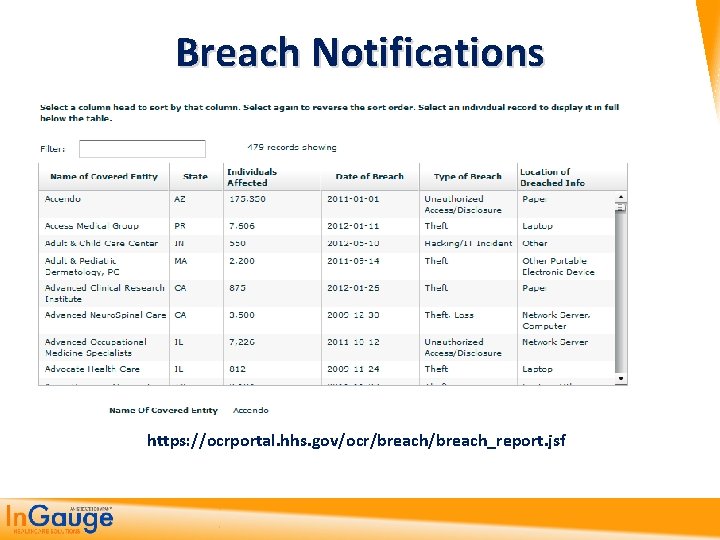
Breach Notifications • A data breach affecting more than 500 people must be reported immediately to the HHS, major media outlets and individuals affected by the breach. Also, the HHS secretary is required to post on an HHS website the list of covered entities that have reported breaches. • A data breach affecting fewer than 500 people must be reported to the HHS secretary on an annual basis and to the individuals affected by the breach. www. hhs. gov/ocr/privacy/hipaa/administrative/breachnotificationrule/breachtool. html

Breach Notifications https: //ocrportal. hhs. gov/ocr/breach_report. jsf

Encryption Requirements • The HITECH Act also requires the issuance of technical guidance on the technologies and methodologies “that render protected health information unusable, unreadable, or indecipherable to unauthorized individuals. ”

EHR Access • In the case where a provider has implemented an EHR system, the Act provides individuals with a right to obtain their PHI in an electronic format (i. e. e. PHI). An individual can also designate that a third party be the recipient of the e. PHI. The Act provides that only a fee equal to the labor cost can be charged for an electronic request.

Accounting of Disclosures • New rules for the accounting of disclosures of a patient's health information. It extends the current accounting for disclosure requirements to information that is used to carry out treatment, payment and health care operations when an organization is using an EHR. This new requirement also limits the timeframe for the accounting to three years instead of six as it currently stands.

If Nothing Else – Focus on These Common Errors

No Such Thing as 100% Security Covered Entities are just expected to follow the Security Rule standards; implement the proper policies, procedures, and technologies; and reasonably show the organization is making an effort to protect against common threats and vulnerabilities.

Common Employee/Management Related Issues q Sharing usernames and passwords Clear violation q Not logging out before leaving a workstation q Passwords that are too easy q Discussing clinical conditions within earshot of others q Not having patients sign the NOPP q Downloading garbage from the internet or talking about PHI on Facebook/Twitter

Common Employee/Management Related Issues q q q Not updating policies and procedures Lack of Business Associates Agreements No Business Continuity Plan (Disaster Recovery) Disgruntled employees Not reporting violations ALL VIOLATIONS SHOULD BE REPORTED IMMEDIATELY TO YOUR SUPERVISOR, HIGHER LEVEL MANAGER, OR COMPLIANCE OFFICER

Common Technical Related Issues Faxing Methods q Use a cover letter q Send only necessary PHI, no more q Use saved speed dial numbers for entities you dial most often, this helps prevent error q Never leave PHI sitting on fax machine or copier q Make sure machine DOES NOT save copies of received faxes q Do not fax if there are other “more secure” methods of delivering PHI

Common Technical Related Issues q Inadequate firewalls Cheap “home use” firewalls q Improperly configured firewalls Simply having a firewall doesn’t guarantee it is configured correctly q Lack of intrusion prevention q Untested backups q No anti-virus software (or expired) q Weak wireless encryption q Taking portable media off-site with no encryption

Common Technical Related Issues q Unencrypted Email Never send e. PHI over a non-encrypted internet account (i. e. Yahoo, Gmail) It is OK to send non-e. PHI over unsecure methods as long as e. PHI is de-identified. (Example: appointment reminder)

6. How To Get Started On Your Own

Getting this Done 1. Do it by yourself: http: //www. hhs. gov/ocr/privacy/hipaa/adminis trative/securityruleguidance. html 2. Buy a Guide http: //www. optumcoding. com/Product/19850/ 3. Hire an IT/HIPAA Consultant Brian Tuttle – contact CPA for more information

Topics 1. The Findings and Penalties from Recent HIPAA Reviews 2. The Past, Present and Future of HIPAA 3. The HIPAA Privacy Rules and what they mean to you 4. Implementing the HIPAA Security Rule Standards 5. Getting up to date with HIPAA HITech Rules and Standards 6. How to get started on being HIPAA Compliant

Questions

Contact Information Office: 770 -709 -3598 E-Fax: 770 -709 -3698 E-mail: steve. adams@ingaugehsi. com Facebook: facebook. com/kingofcoders Web: thecodingeducator. com
 Cvs privacy awareness and hipaa training answers
Cvs privacy awareness and hipaa training answers Hipaa privacy and security awareness training
Hipaa privacy and security awareness training In allen wipfeln spürest du
In allen wipfeln spürest du When should you promote hipaa awareness
When should you promote hipaa awareness What are the modifiers of human act
What are the modifiers of human act Steve jobs steve wozniak and ronald wayne
Steve jobs steve wozniak and ronald wayne Hipaa training georgia
Hipaa training georgia Air force hipaa training
Air force hipaa training Accountable hipaa training
Accountable hipaa training Hipaa training strategies
Hipaa training strategies Hipaa training for nurses
Hipaa training for nurses Security education and training programs
Security education and training programs Security training and threat awareness
Security training and threat awareness Iso 9001:2015 ppt
Iso 9001:2015 ppt The cjis security policy outlines the minimum requirements
The cjis security policy outlines the minimum requirements Sexual abuse quiz
Sexual abuse quiz Ppe awareness
Ppe awareness Ppe awareness training
Ppe awareness training Iatf 16949 awareness training
Iatf 16949 awareness training Iso 9001 awareness
Iso 9001 awareness Iso 14001 awareness training
Iso 14001 awareness training Insider threat training slides
Insider threat training slides Environmental management system awareness training
Environmental management system awareness training Risk management awareness training
Risk management awareness training Mold awareness training
Mold awareness training Chemical security awareness training
Chemical security awareness training Signs of dysphagia
Signs of dysphagia Vibration awareness training
Vibration awareness training Ergonomics awareness training for supervisors
Ergonomics awareness training for supervisors Ergonomics awareness training for supervisors
Ergonomics awareness training for supervisors Sfar 73
Sfar 73 Ppt-059
Ppt-059 Insider threat awareness training powerpoint
Insider threat awareness training powerpoint Esd awareness training
Esd awareness training Webroot security awareness training pricing
Webroot security awareness training pricing Lgbt awareness training
Lgbt awareness training Find ergonomics awareness training
Find ergonomics awareness training Rf safety awareness training answers
Rf safety awareness training answers Bloodborne pathogens awareness training
Bloodborne pathogens awareness training Phonological awareness training program
Phonological awareness training program Child protection awareness training
Child protection awareness training Counterfeit material awareness training
Counterfeit material awareness training Ehs awareness training
Ehs awareness training Check fraud training
Check fraud training Good computing practices
Good computing practices Electrical hazard awareness training
Electrical hazard awareness training Cda security awareness training
Cda security awareness training Cultural awareness training presentation
Cultural awareness training presentation Asbestos awareness training wa
Asbestos awareness training wa Patient portals and hipaa
Patient portals and hipaa Joint commission and hipaa compliance
Joint commission and hipaa compliance Steve brace training
Steve brace training Steve brace training
Steve brace training Hippa secure now
Hippa secure now Joint commission hipaa
Joint commission hipaa Hipaa pre-existing condition protections
Hipaa pre-existing condition protections Gillman hipaa progress note
Gillman hipaa progress note Evolution of hipaa
Evolution of hipaa Jira hipaa
Jira hipaa Hipaa security rule self assessment toolkit
Hipaa security rule self assessment toolkit Gillman hipaa progress note
Gillman hipaa progress note Uday ali pabrai
Uday ali pabrai Hipaa summit
Hipaa summit What does tpo stand for in hipaa
What does tpo stand for in hipaa Hipaa objectives
Hipaa objectives What is hipaa
What is hipaa What is hipaa
What is hipaa Ada hipaa compliance kit
Ada hipaa compliance kit Hippocratic oath
Hippocratic oath Hippa
Hippa Louisiana hipaa laws
Louisiana hipaa laws Hipaa summit
Hipaa summit Hipaa frequently asked questions
Hipaa frequently asked questions Hipaa breach notification decision tree
Hipaa breach notification decision tree Hipaa principles
Hipaa principles Ferpa violation
Ferpa violation Gremote.geisinger
Gremote.geisinger