Awareness Training Series Management Awareness Training Dan Hadaway

























































































































- Slides: 182

Awareness Training Series Management Awareness Training Dan Hadaway CISA, CISM Managing Partner infotex

Objectives • What is IT Governance, and what does a typical IT Governance program look like? • What is the management team’s role in the IT Governance Program? • What is the ISO’s role? • What should the management team know to ensure proper IT Governance? • How can management help manage technology risk? infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

In this next section • We will become familiar with the “workshop portal” and this presentation. • We will hear credentials that can be used to log onto the workshop portal. • We will learn what is on the “workshop portal. ” infotex

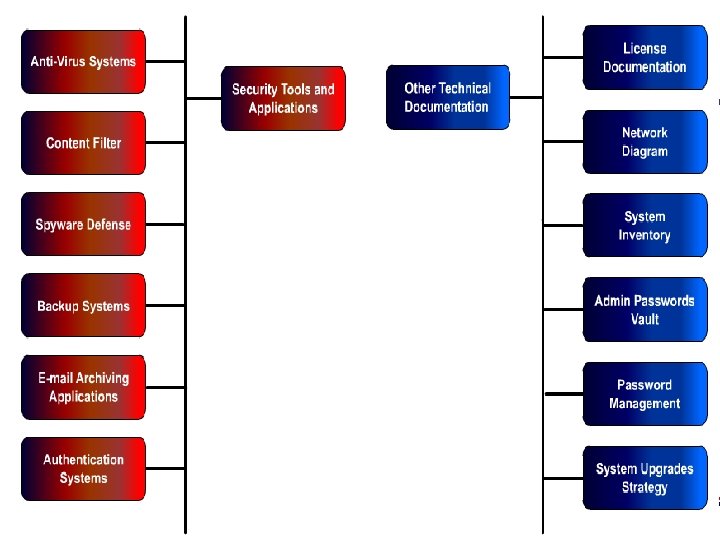
Available Tools. . . • • IT Audit Test Types The ISO Job Description Awareness Training Procedure Management Awareness Training Procedure • Governance Policy Development Chart infotex

Available Tools. . . • Management Guidelines for Social Media • User Guidelines for Social Media • Management Talking Points for Mobile Banking and Social Media infotex

Available Tools. . . • Wireless Banking Article (Top Five Risks) • Wireless Banking Article • Wireless Banking Risk Assessment • Wireless Banking Due Diligence Kit infotex

Our Credentials • Information Security – CISAs, CISMs, CISSPs – Developed my first AUP in 1988 – Updating our process annually – Been doing Annual UAT for banks since 2002 • GLBA, BSA, OFAC, FACTA, HIPAA • Assessments, IT Audits, Consulting • Managed Services (Network Monitoring) infotex

Nomenclature • Information Security Strategy • Information Security Program • IT Risk Management Program • IT Governance Program Essentially the same thing. infotex

IT Governance Program • Combines: – Serve Business Mission – Manage Technology Risk (information security) infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

In this next section • We will learn five basic tenets of IT Governance that all management team members should know. • We will learn why IT Governance is concerned with Risk Management • We will learn “the one control” and why this workshop is important. infotex

#1 infotex

#1: Serve the Mission Information Technology must be aligned with the Business Strategy of the bank! infotex

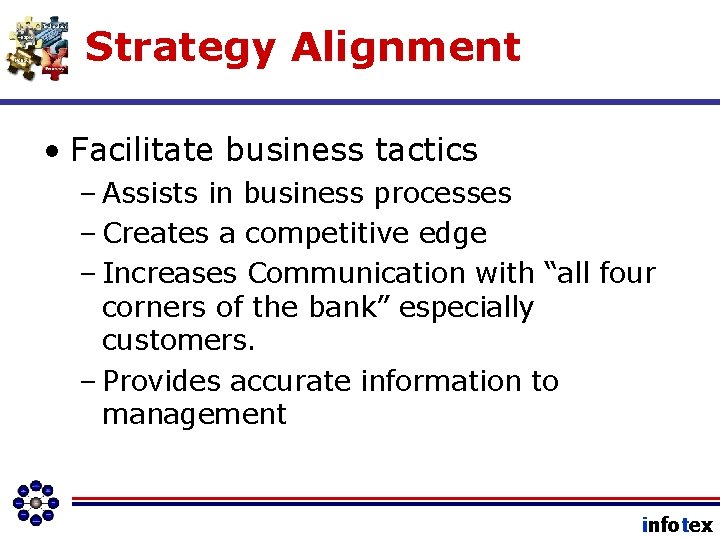
Strategy Alignment • Facilitate business tactics – Assists in business processes – Creates a competitive edge – Increases Communication with “all four corners of the bank” especially customers. – Provides accurate information to management infotex

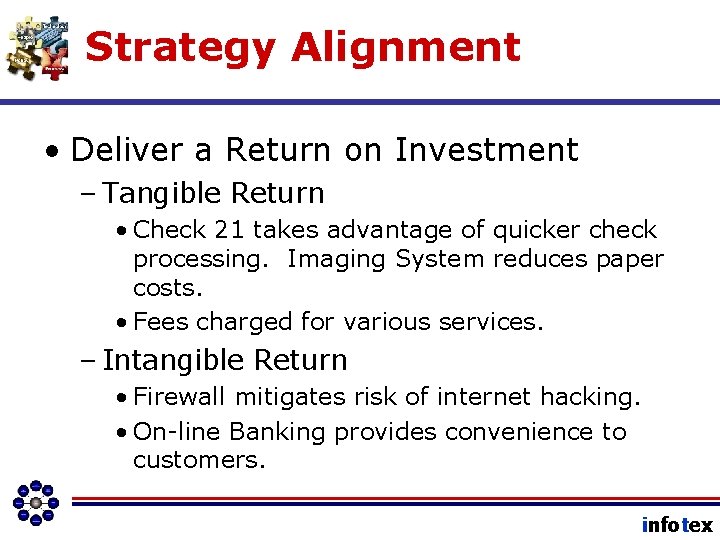
Strategy Alignment • Deliver a Return on Investment – Tangible Return • Check 21 takes advantage of quicker check processing. Imaging System reduces paper costs. • Fees charged for various services. – Intangible Return • Firewall mitigates risk of internet hacking. • On-line Banking provides convenience to customers. infotex

Management Role • Determine technologies that will best facilitate business tactics. • Determine appropriate time to deploy new technologies (Apply Pressure) infotex

Management Role • Search and Selection Process – Cost/Benefit Benefit/Risk When? ? ? – Risk Analysis – Requirements Definition – Request for Proposal infotex

Management Role • Negotiate Contracts (as per Vendor Management Procedure) • Implementation – From a user perspective – Return to risk analysis – Return to cost/benefit analysis – Return to features analysis • Ongoing Vendor Due Diligence (as per Vendor Management Procedure) infotex

When is the appropriate time? infotex

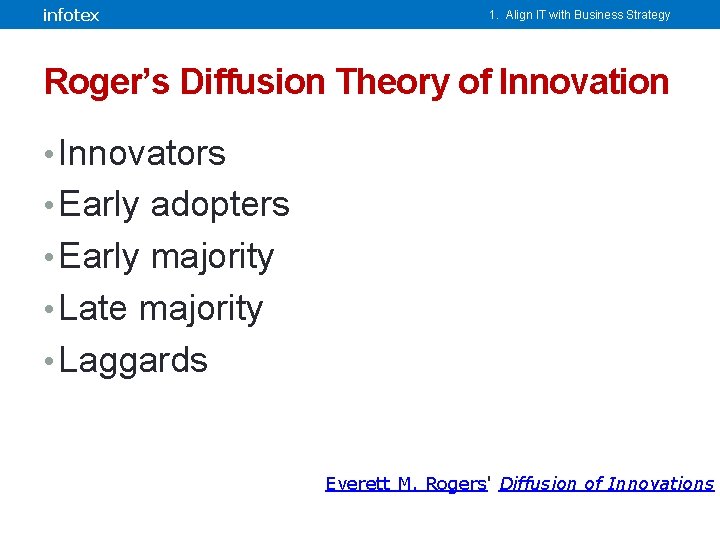
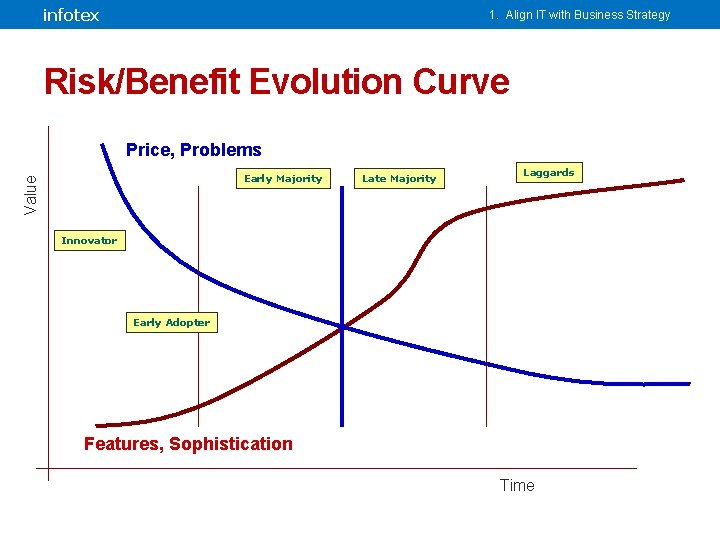
infotex 1. Align IT with Business Strategy Roger’s Diffusion Theory of Innovation • Innovators • Early adopters • Early majority • Late majority • Laggards Everett M. Rogers' Diffusion of Innovations

infotex 1. Align IT with Business Strategy Stages of Innovation • Knowledge • Persuasion • Decision • Implementation • Confirmation Risk Assessment? Security Controls Everett M. Rogers' Diffusion of Innovations

infotex 1. Align IT with Business Strategy Early Adopters in Banking • Physical Security • Information Security Dan’s Interpretation of Everett M. Rogers' Diffusion of Innovations

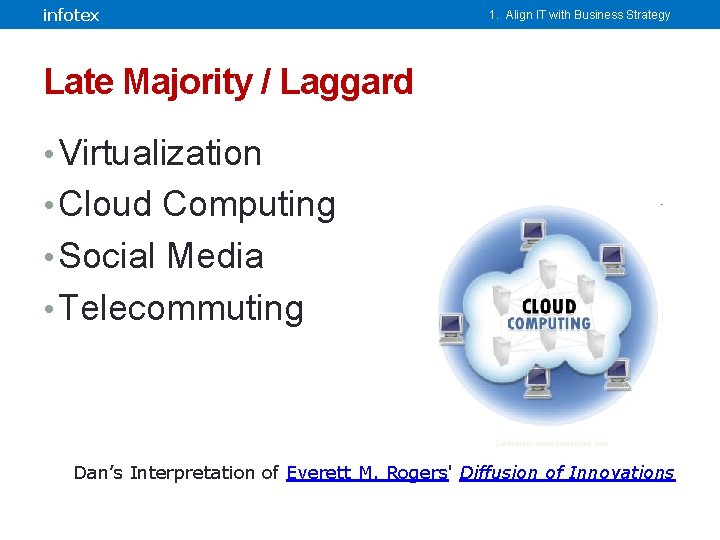
infotex 1. Align IT with Business Strategy Late Majority / Laggard • Virtualization • Cloud Computing • Social Media • Telecommuting Softwareforcloudcomputing. com Dan’s Interpretation of Everett M. Rogers' Diffusion of Innovations

infotex 1. Align IT with Business Strategy Risk/Benefit Evolution Curve Value Price, Problems Features, Sophistication Time

infotex 1. Align IT with Business Strategy Risk/Benefit Evolution Curve Value Price, Problems Features, Sophistication Time

infotex 1. Align IT with Business Strategy Risk/Benefit Evolution Curve Price, Problems Value Early Majority Late Majority Laggards Innovator Early Adopter Features, Sophistication Time

Digital Video Security • Innovators • Early adopters • Early majority • Late majority • Laggards 2012 infotex

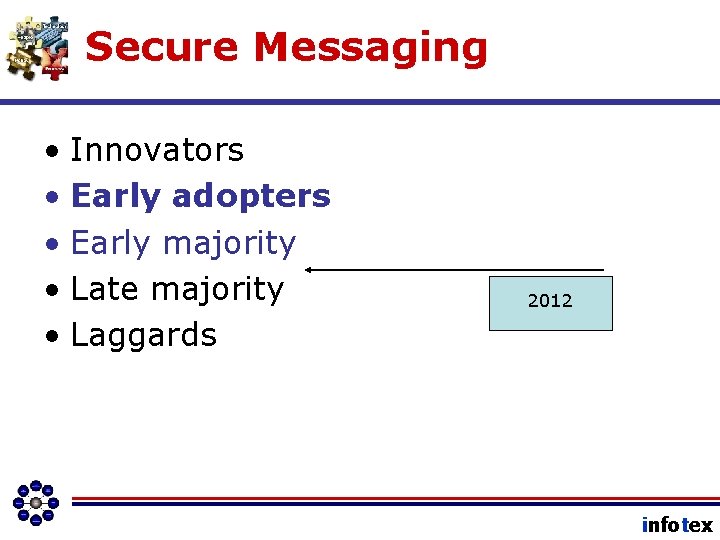
Secure Messaging • Innovators • Early adopters • Early majority • Late majority • Laggards 2012 infotex

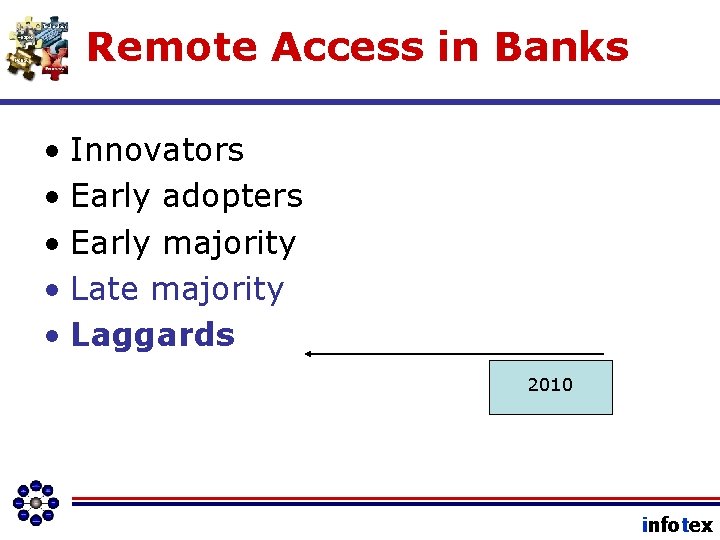
Remote Access in Banks • Innovators • Early adopters • Early majority • Late majority • Laggards 2010 infotex

Social Media in Banks • Innovators • Early adopters • Early majority • Late majority • Laggards 2011 infotex

Wireless Banking • Innovators • Early adopters • Early majority • Late majority • Laggards 2013 infotex

#2 infotex

#2: Manage the Risk Information, Technology, and Information Technology expose the bank to risk! infotex

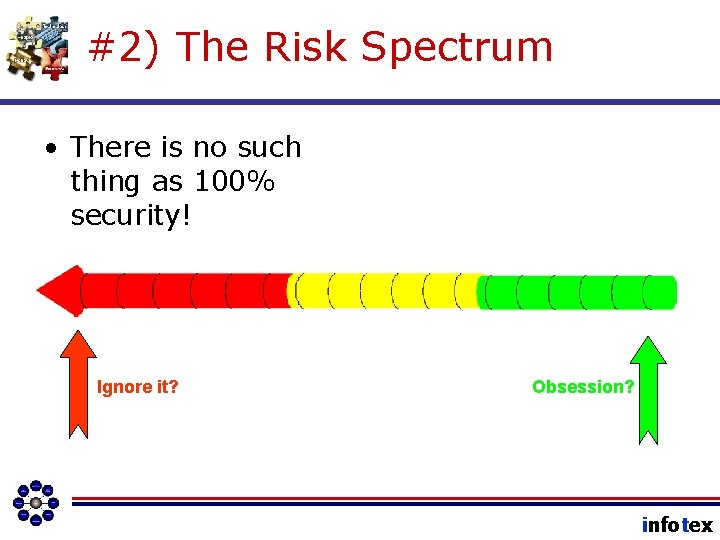
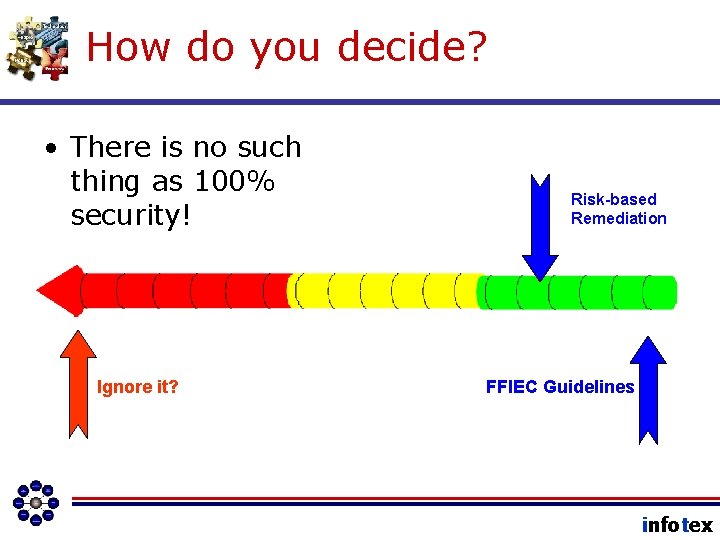
#2) The Risk Spectrum • There is no such thing as 100% security! Ignore it? Obsession? infotex

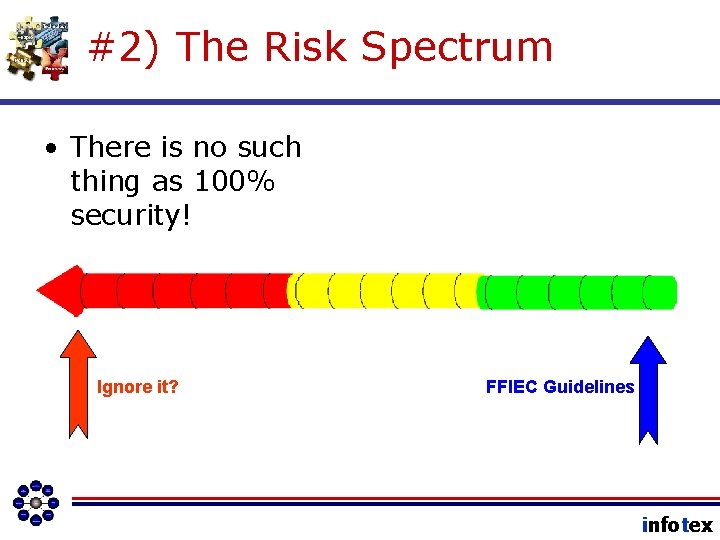
#2) The Risk Spectrum • There is no such thing as 100% security! Ignore it? FFIEC Guidelines infotex

How do you decide? • There is no such thing as 100% security! Ignore it? Risk-based Remediation FFIEC Guidelines infotex

Principle Number Two Information Security is about ACCEPTING RISK. infotex

#3 infotex

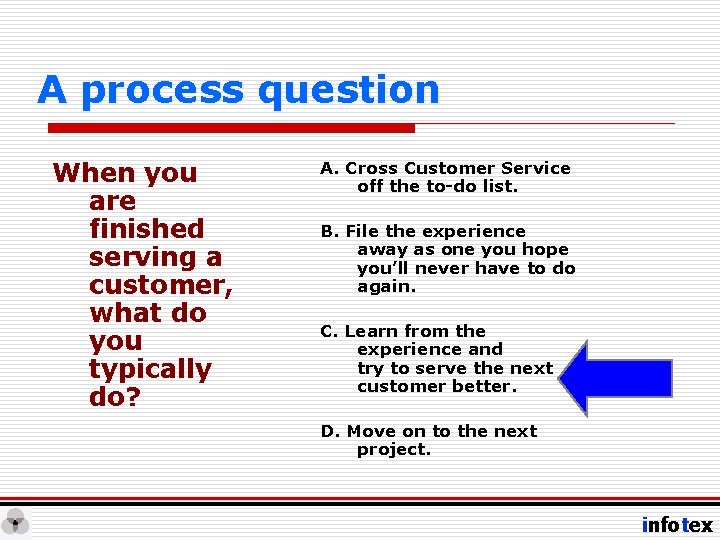
A process question When you are finished serving a customer, what do you typically do? A. Cross Customer Service off the to-do list. B. File the experience away as one you hope you’ll never have to do again. C. Learn from the experience and try to serve the next customer better. D. Move on to the next project. infotex

Fundamental #3 infotex

Which means. . . • No crossing it off the list. • No filing it away. • No wishing you never have to deal with it again. infotex

And means. . . • Its cyclical. • You learn from each cycle. • It is constantly improving (we hope). • It’s about managing risk and ensuring alignment with other business processes. infotex

And to improve. . • We must start by measuring. But remember that metrics are all relative. infotex

Fundamental #3 infotex

#4 infotex

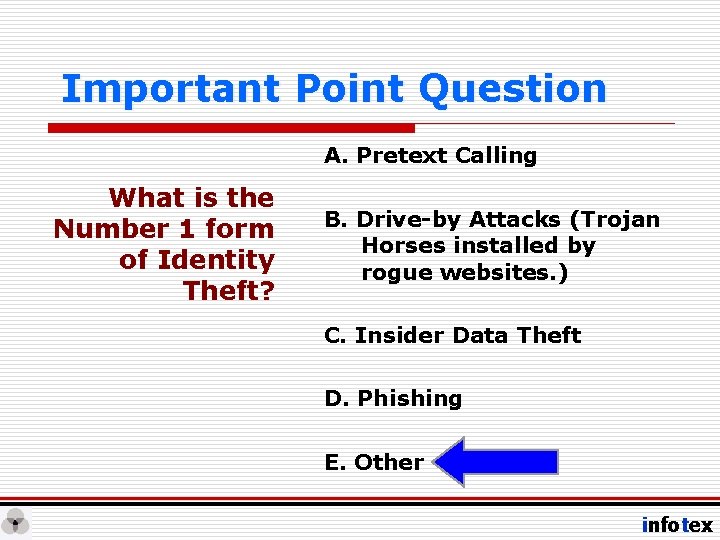
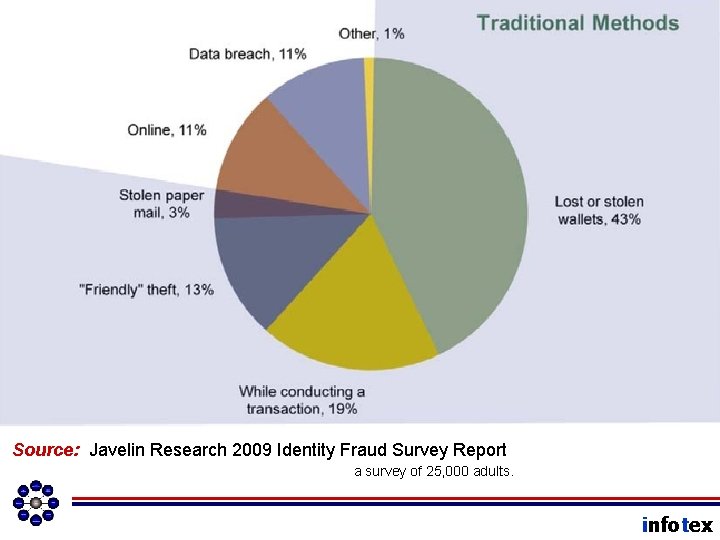
Important Point Question A. Pretext Calling What is the Number 1 form of Identity Theft? B. Drive-by Attacks (Trojan Horses installed by rogue websites. ) C. Insider Data Theft D. Phishing E. Other infotex

Source: Javelin Research 2009 Identity Fraud Survey Report a survey of 25, 000 adults. infotex

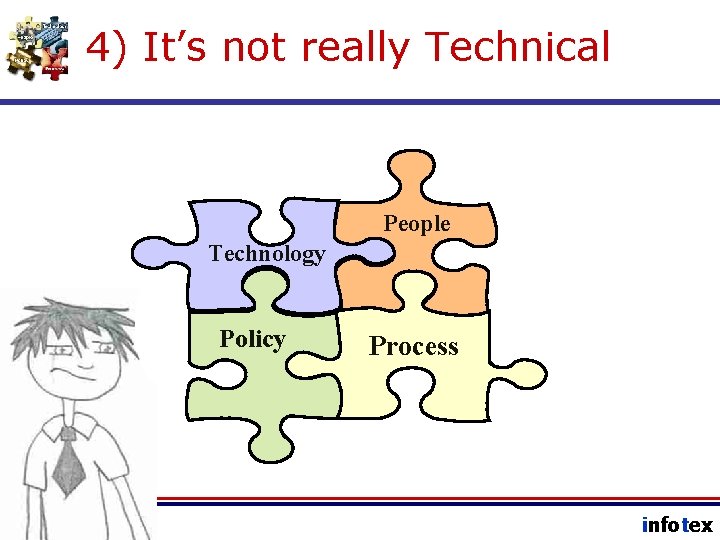
4) It’s not really Technical People Technology Policy Process infotex

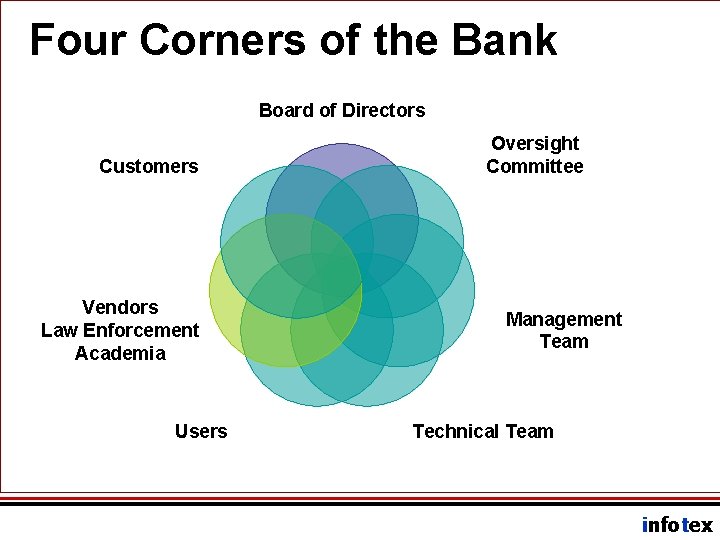
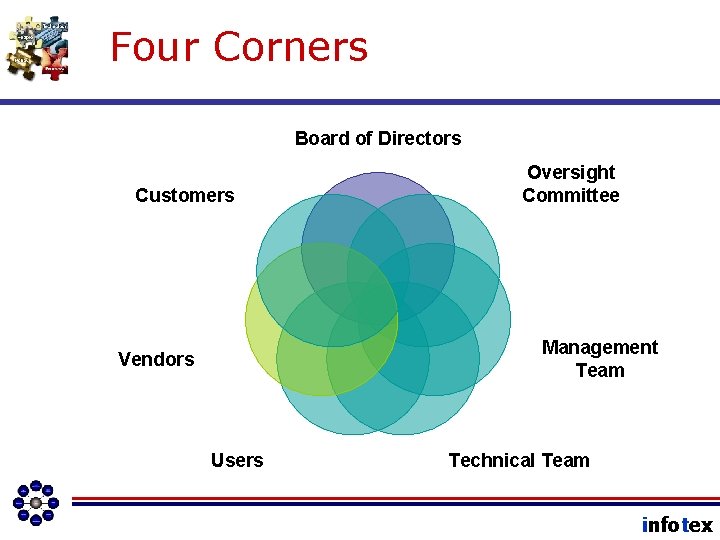
IT requires a Team Approach • Risk must be measured and managed using a multi-disciplinary approach. • Risk is mitigated by establishing controls in the form of policies, procedures, and tools. • Risk Management Controls involve “all four corners of the bank. ” infotex

Four Corners of the Bank infotex

Four Corners of the Bank Board of Directors Customers Vendors Law Enforcement Academia Users Oversight Committee Management Team Technical Team infotex

Information Security Officer • Measures, Manages, Reports Information Security Risk • Interacts with all four corners. • Facilitates development and continuous improvement of security controls. • Delivers an Annual Report directly to the board. infotex

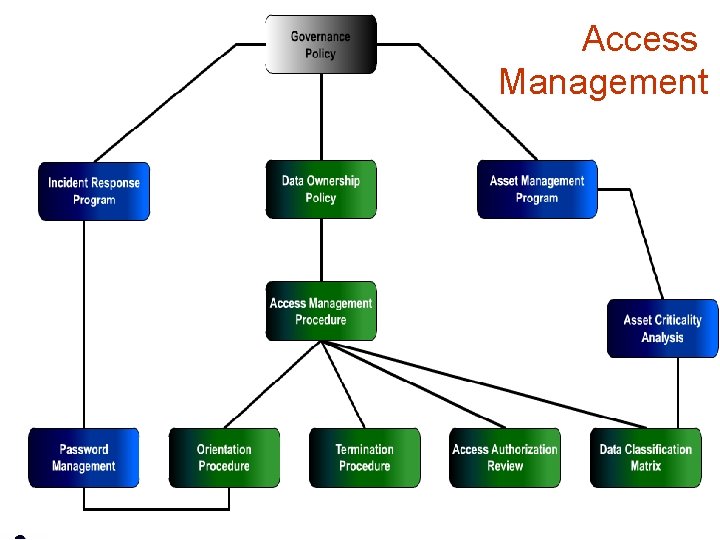
Information Security Officer • Works with Management to: – Measure and Control Risk – Develop and enforce Security Controls – Plan Response to Negative Incidents (Policy Violation, Security, Disaster) – Manage Vendor Risk – Authorize Access to IT Assets – Inventory and manage IT Assets – Escalate Risk Acceptance Decisions (to the Board of Directors) infotex

#5 infotex

infotex

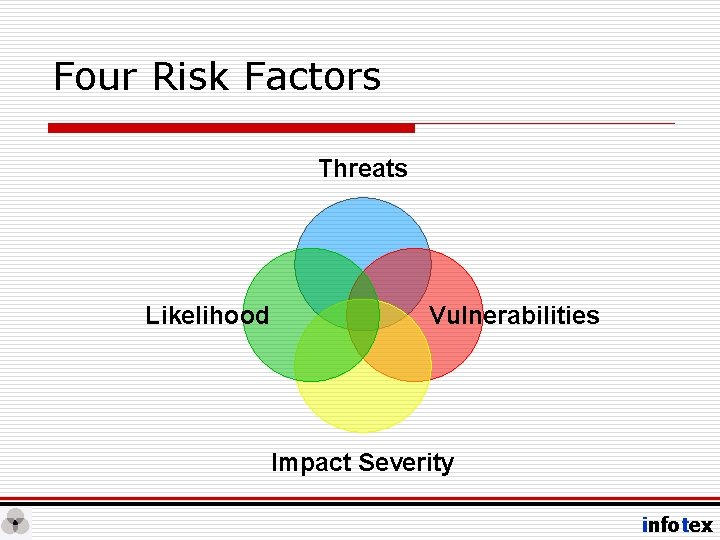
Four Risk Factors Threats Likelihood Vulnerabilities Impact Severity infotex

Threats • Terrorists • Hackers • Scammers / Conmen /Fraudsters / Thieves • Vandals • Technology Itself • Users / Vendors • Nosy Neighbors • Ex-Spouses infotex

We can’t take it lightly • Zeus • Software suite designed to help hackers attack banks. infotex

Marc Rogers, Purdue University infotex

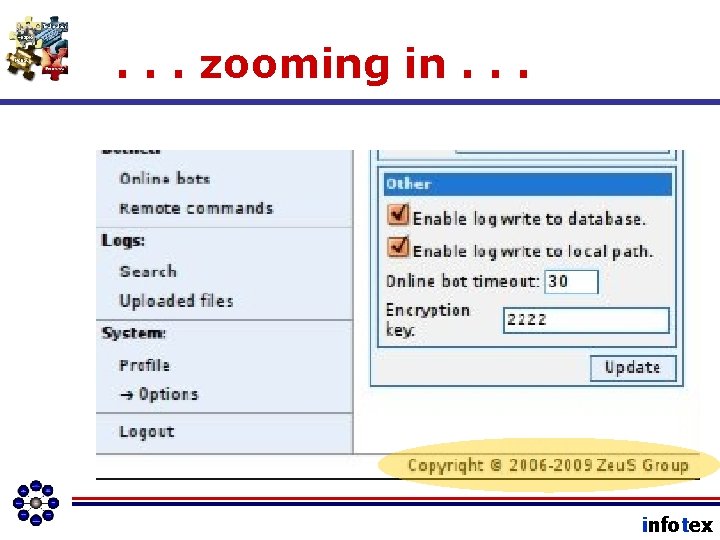
. . . zooming in. . . infotex

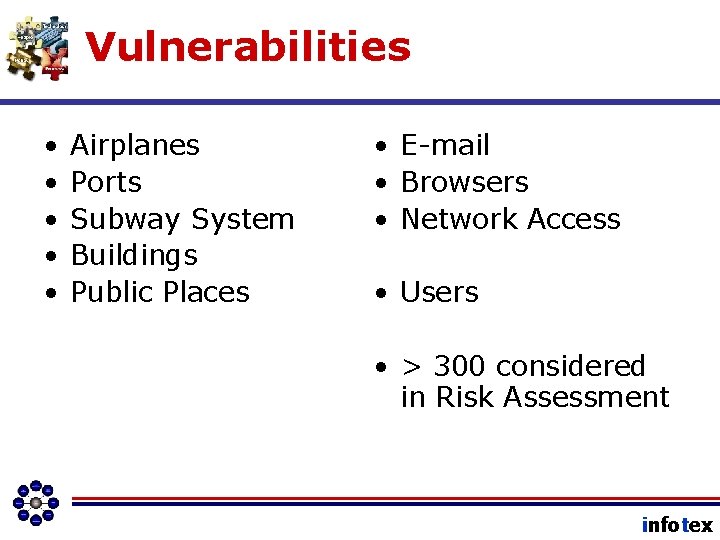
Vulnerabilities • • • Airplanes Ports Subway System Buildings Public Places • E-mail • Browsers • Network Access • Users • > 300 considered in Risk Assessment infotex

Impact Severity • Almost 3000 people • Financial System • Airlines • Convenience • Customers’ Identities • Horror Stories • Heartland Payment System ($7/card, 20, 000 cards) • Reputation infotex

Likelihood • It can happen on American Soil • Technology Itself Very High • Pretext Calling High • Phishing High • Hacking Medium • Physical Breach Low – Still happens though! infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

In this next section • We will learn about the Federal Financial Institution Examination Council (FFIEC) and it’s published “guidelines” for information technology, and why these guidelines become audit frameworks. • We will see a quick summary of “management responsibilities for IT. ” • We will review a “map” of the typical bank’s IT Governance Program • We will learn how the management team “plugs in” to the IT Governance Program. infotex

Types of Risk • Transaction Risk – Data Corruption Problems – Social Engineering – Customer Errors (Internet Banking) • Legal Risk – Obscene Jokes in E-mail – Privacy Violations – Unlicensed Software infotex

Types of Risk • Financial Risk – Early Adapter of Technology – Vendor Solvency – Cost of Security Breaches • Operational Risk – Virus Attacks – Denial of Service (Do. S) Attacks – Project Management Risk infotex

Types of Risk • Reputational Risk – Any Security Incident presents some reputational risk. – Poor Incident Response can turn a minor incident into a major incident. infotex

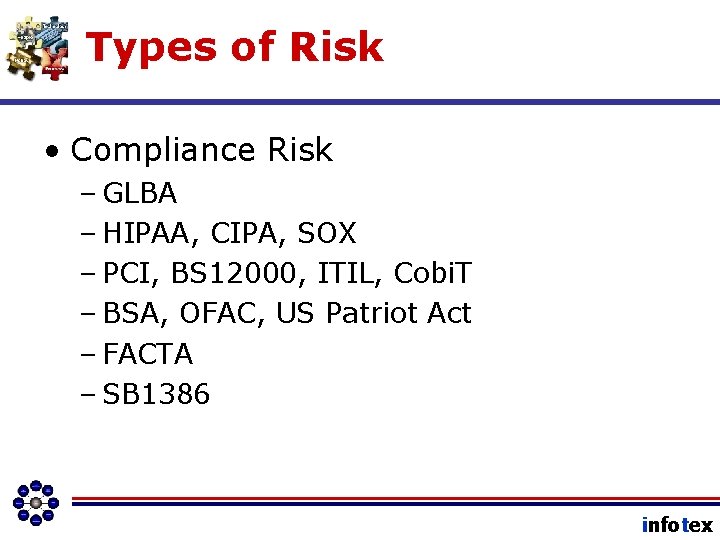
Types of Risk • Compliance Risk – GLBA – HIPAA, CIPA, SOX – PCI, BS 12000, ITIL, Cobi. T – BSA, OFAC, US Patriot Act – FACTA – SB 1386 infotex

Gramm Leach Bliley Act Specifically, Title V of the GLBA, called "Disclosure of Nonpublic Personal Information, " is intended to ensure security and confidentiality of customers' records and information, protect the integrity of such information, and protect against unauthorized access to such information. infotex

Thank goodness for the. . . infotex

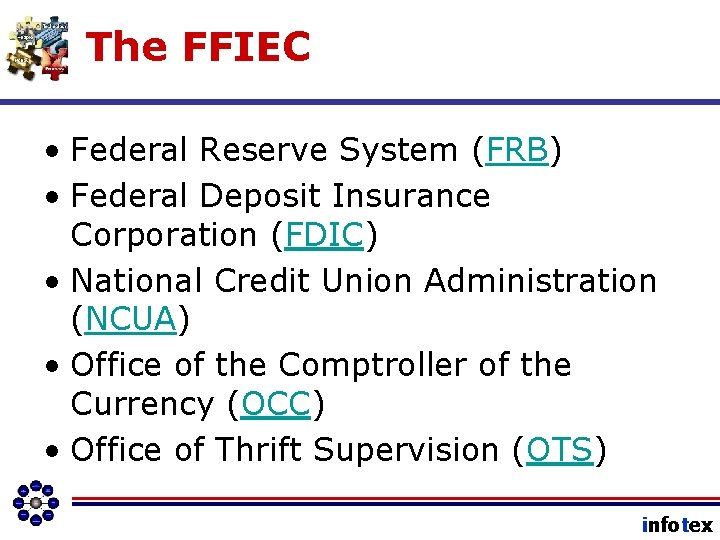
The FFIEC • Federal Reserve System (FRB) • Federal Deposit Insurance Corporation (FDIC) • National Credit Union Administration (NCUA) • Office of the Comptroller of the Currency (OCC) • Office of Thrift Supervision (OTS) infotex

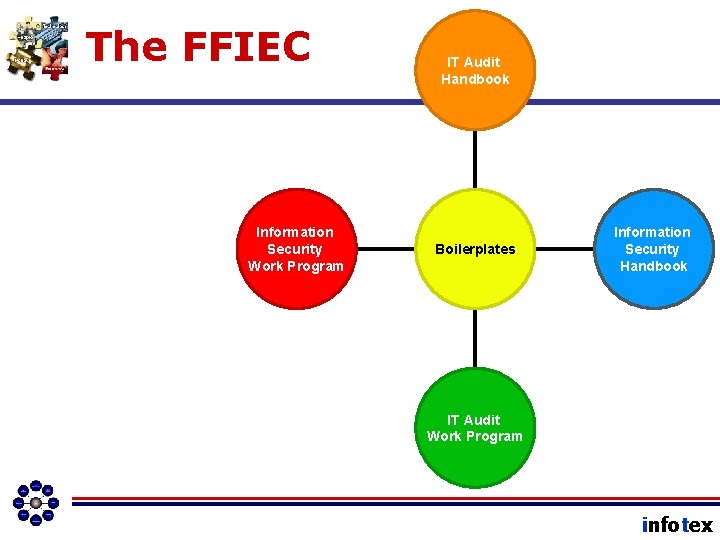
The FFIEC Information Security Work Program IT Audit Handbook Boilerplates Information Security Handbook IT Audit Work Program infotex

Awareness Training Series Management Responsibilities A quick summary infotex

Summary of Responsibilities • Understand how IT aligns with bank and department business strategy and work with IT to ensure appropriate alignment. • Know the IT Governance program, how it works, the ISO’s role, and your role in the various sub-programs. • Be familiar with technology risk that the bank faces. • Enforce technology controls. • Activate awareness of staff members. infotex

What does an IT Governance Program include? (according to FFIEC Guidelines) infotex

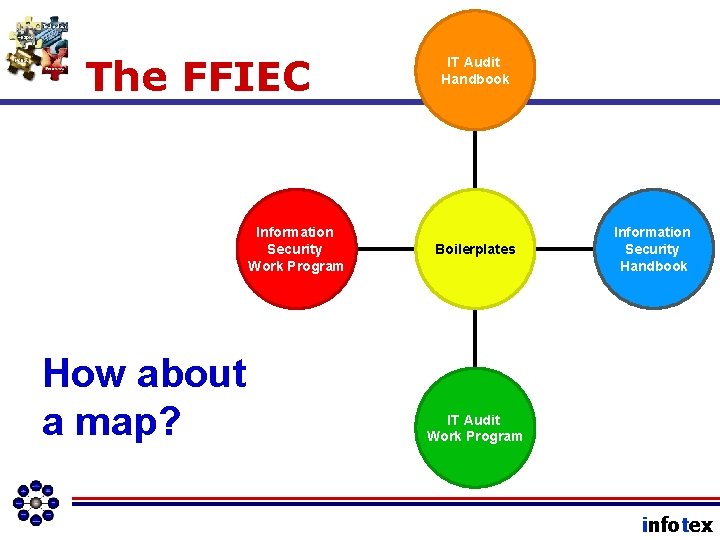
The FFIEC Information Security Work Program How about a map? IT Audit Handbook Boilerplates Information Security Handbook IT Audit Work Program infotex

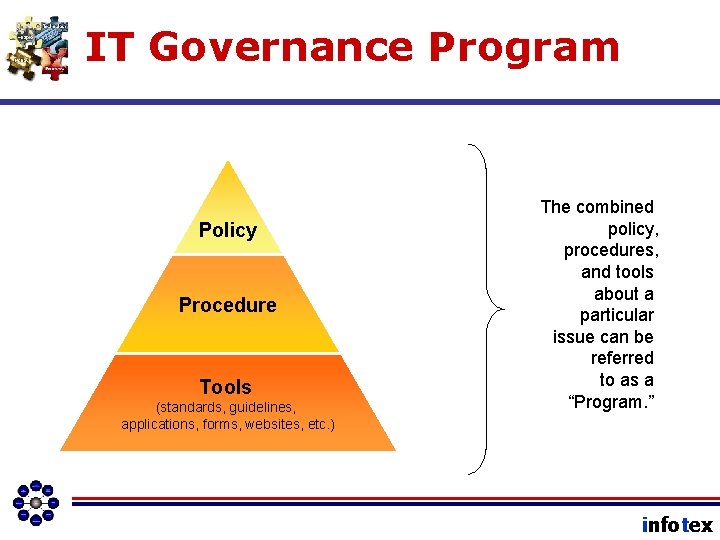
IT Governance Program Policy Procedure Tools (standards, guidelines, applications, forms, websites, etc. ) The combined policy, procedures, and tools about a particular issue can be referred to as a “Program. ” infotex

Authentication Example AUP Authentication Procedures A procedure enforces a board level policy using tools called for in the procedure. Passwords Out-of-Pocket Questions Visitor Authorization Process infotex

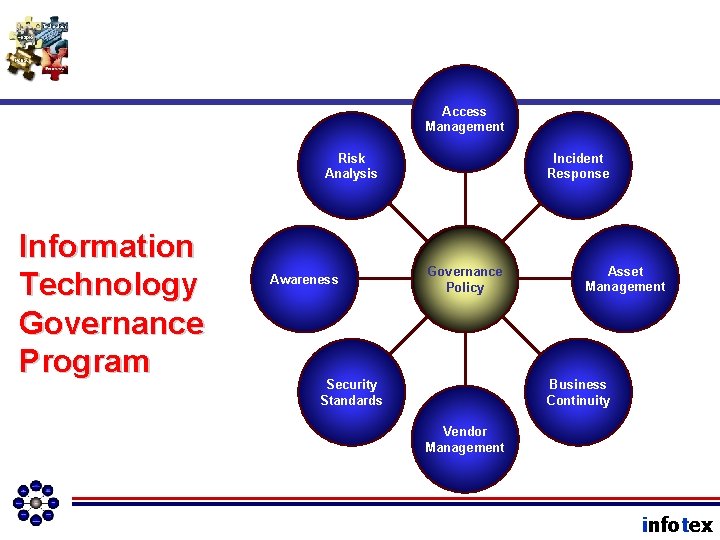
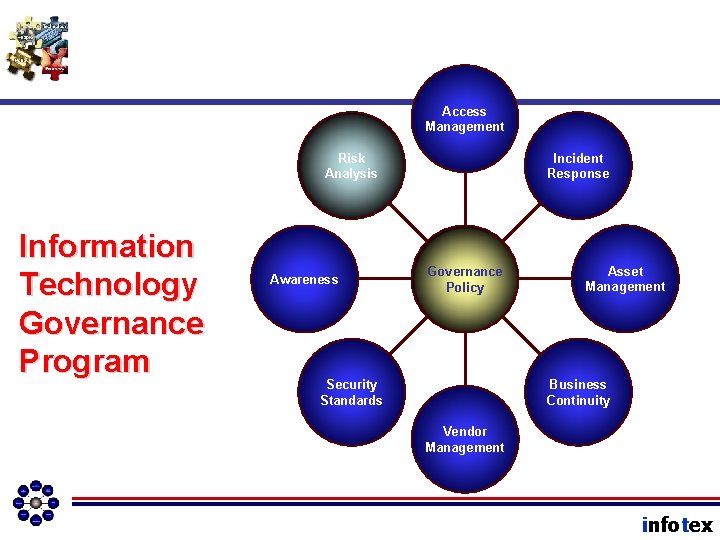
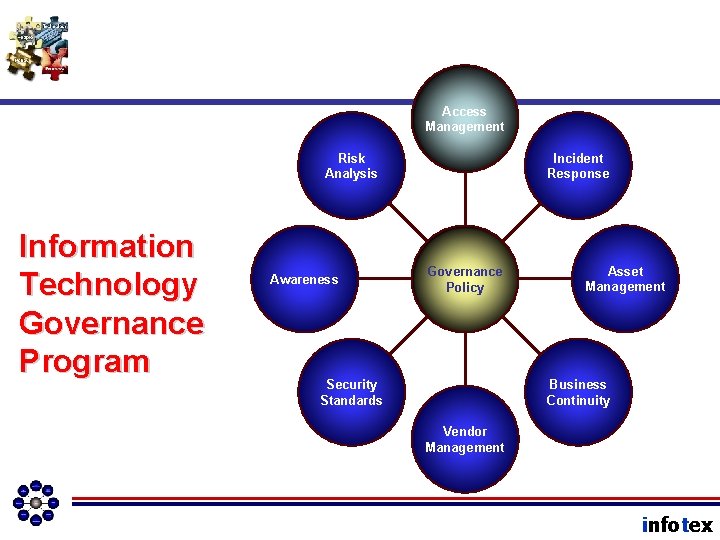
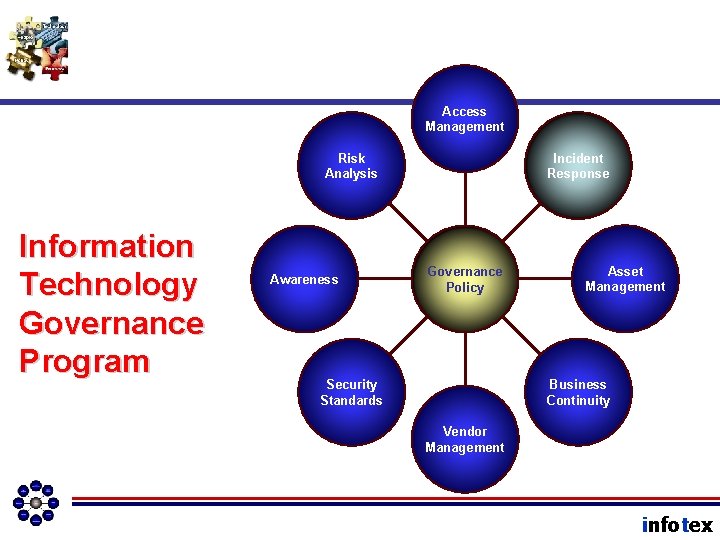
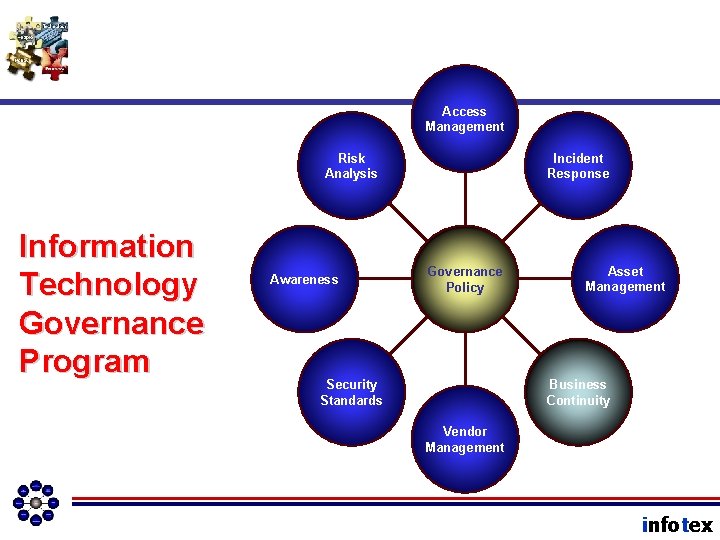
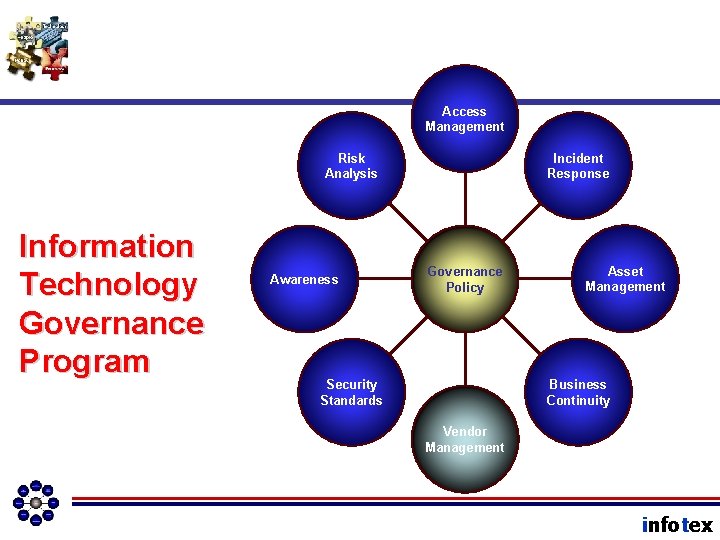
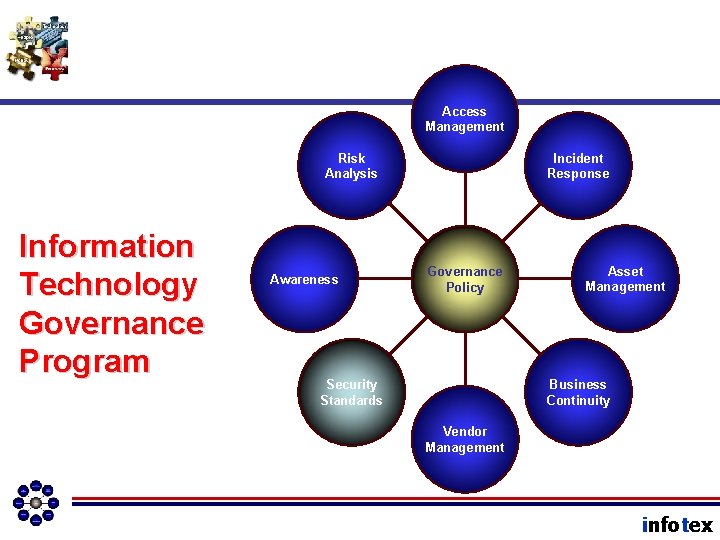
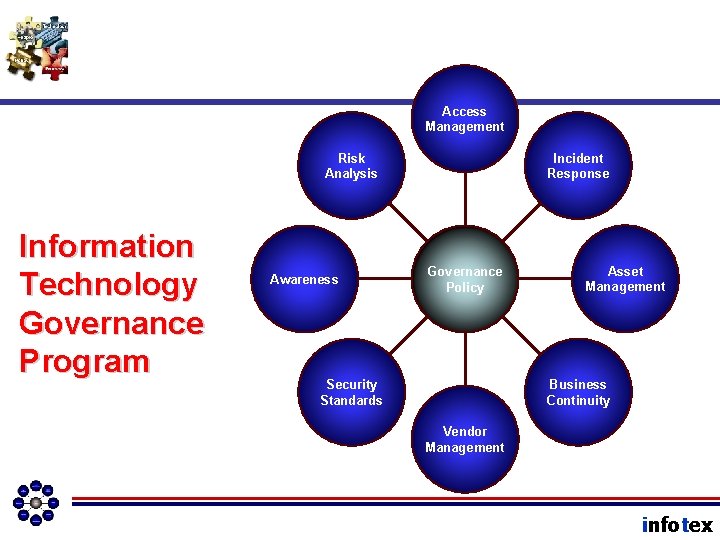
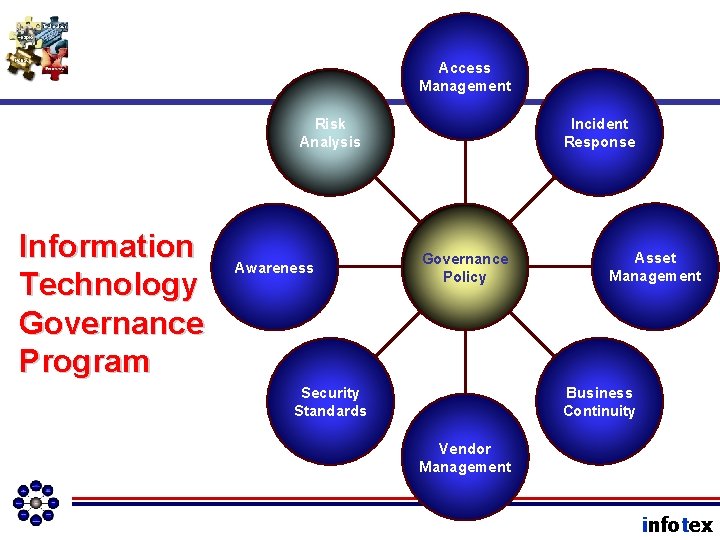
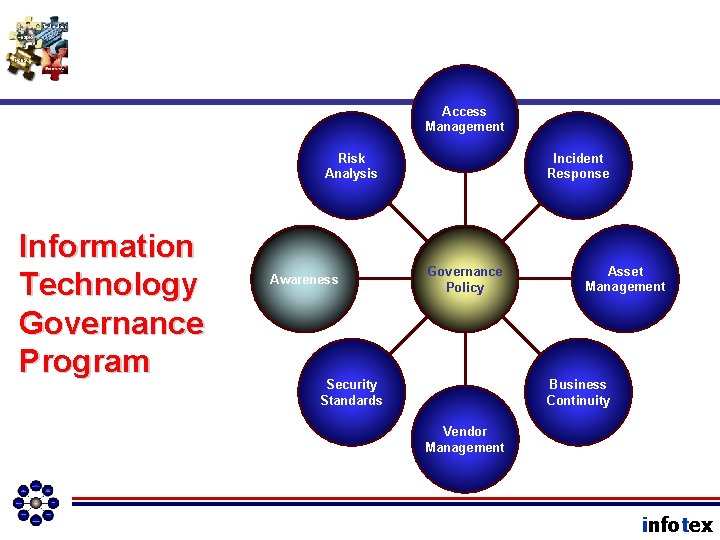
Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

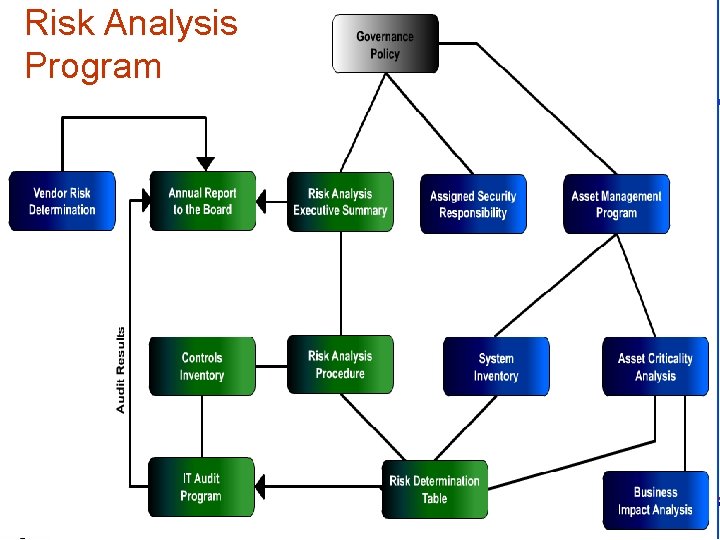
Risk Analysis Program infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

Access Management infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

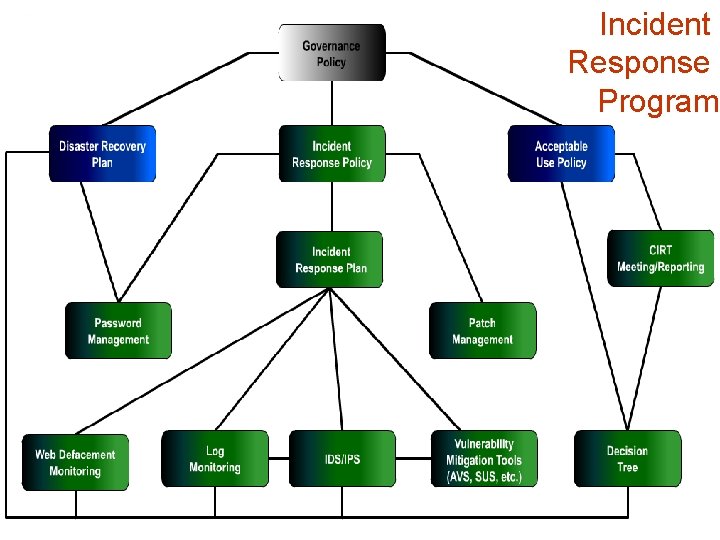
Incident Response Program infotex

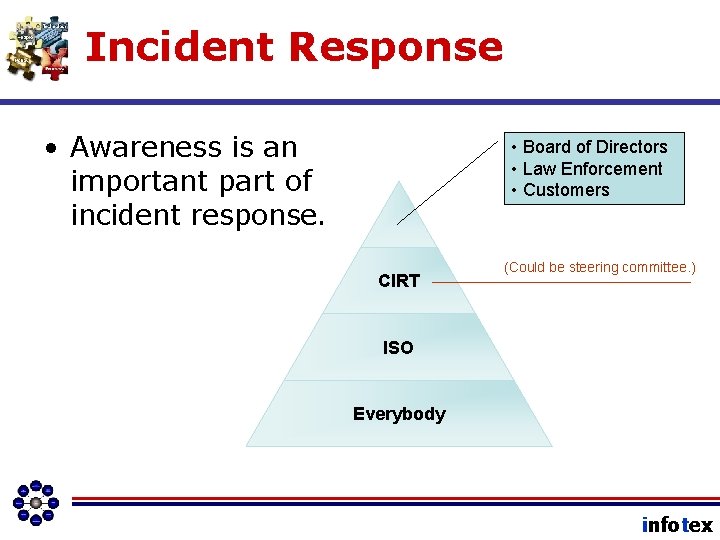
Incident Response • Awareness is an important part of incident response. • Board of Directors • Law Enforcement • Customers CIRT (Could be steering committee. ) ISO Everybody infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

Asset Management Program infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

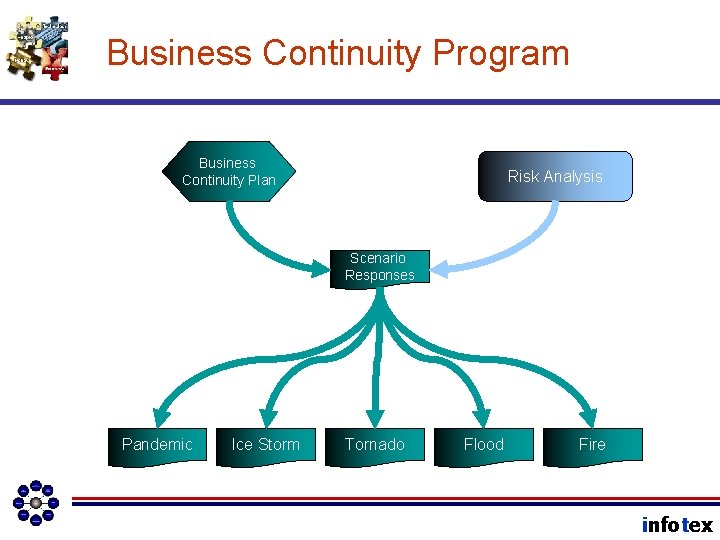
Business Continuity Program infotex

Business Continuity Program Business Continuity Plan Risk Analysis Scenario Responses Pandemic Ice Storm Tornado Flood Fire infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

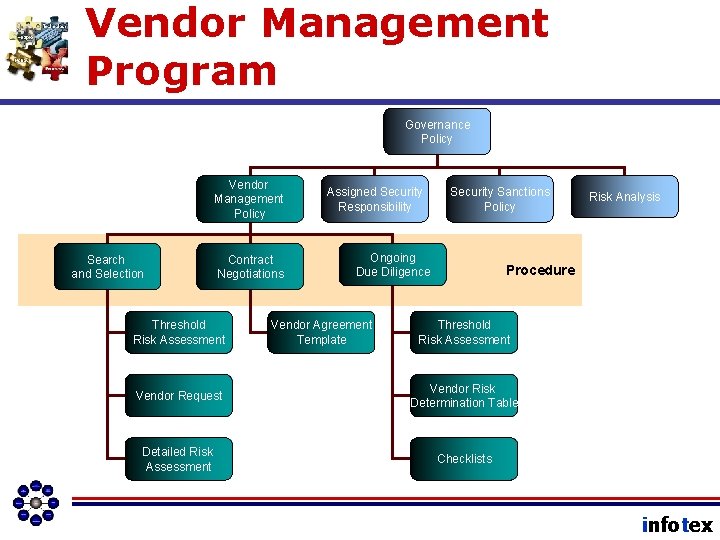
Vendor Management Program Governance Policy Vendor Management Policy Search and Selection Contract Negotiations Threshold Risk Assessment Assigned Security Responsibility Security Sanctions Policy Ongoing Due Diligence Vendor Agreement Template Risk Analysis Procedure Threshold Risk Assessment Vendor Request Vendor Risk Determination Table Detailed Risk Assessment Checklists infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

Security Standards infotex

Security Standards infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

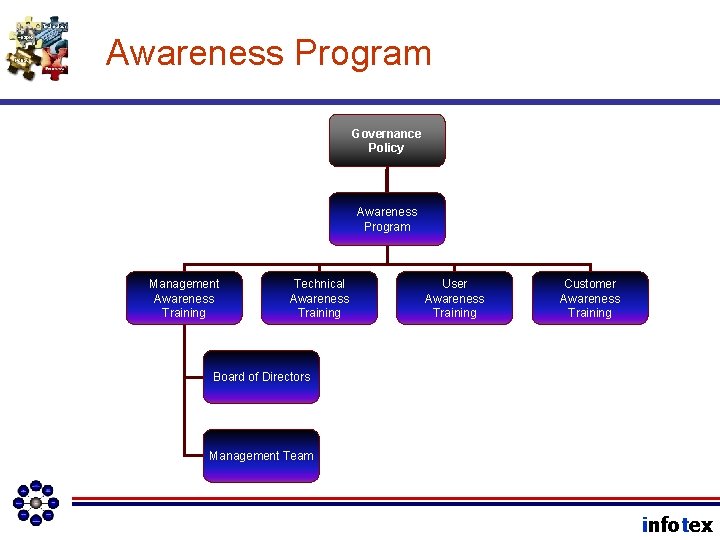
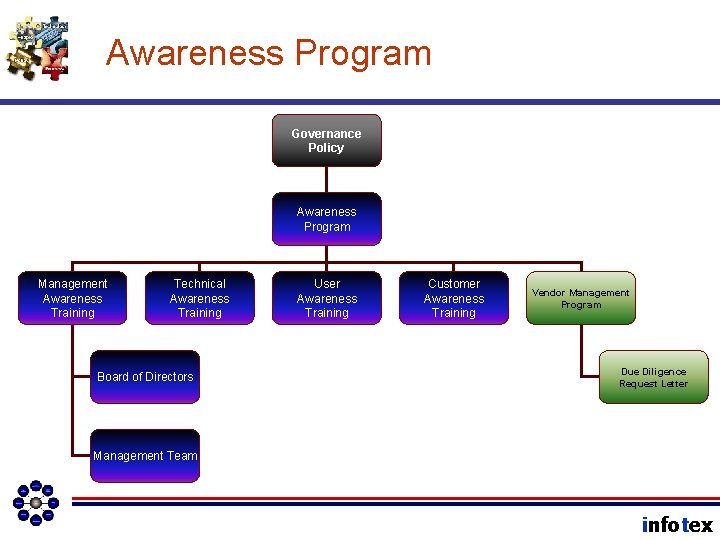
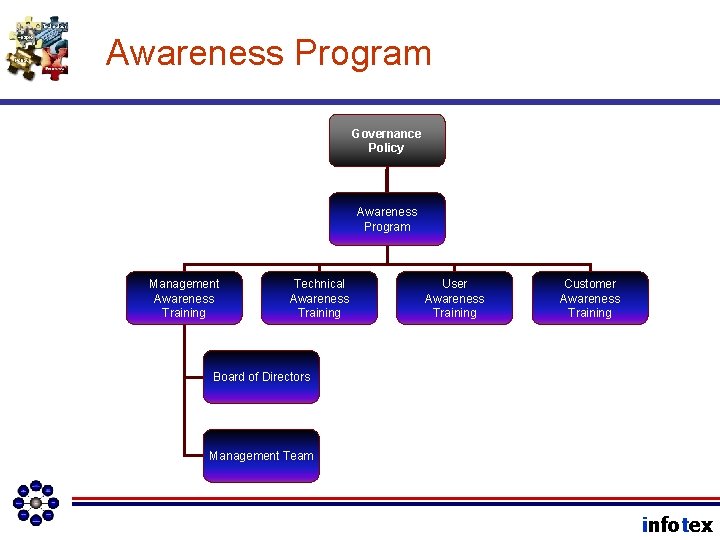
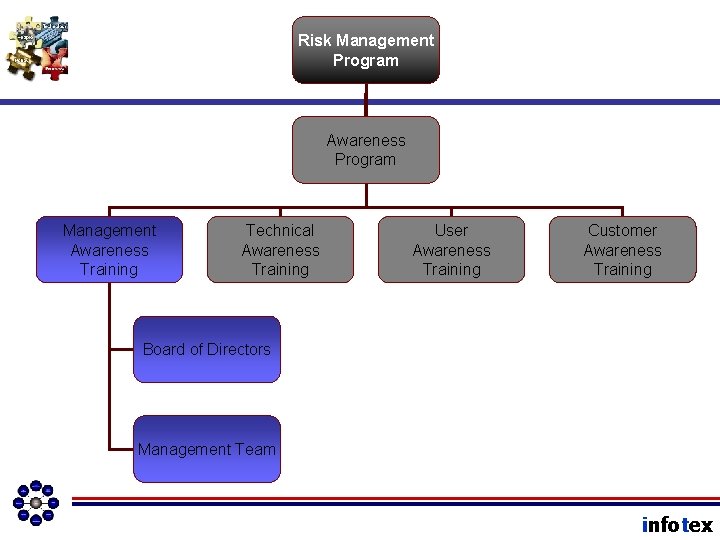
Awareness Program Governance Policy Awareness Program Management Awareness Training Technical Awareness Training User Awareness Training Customer Awareness Training Board of Directors Management Team infotex

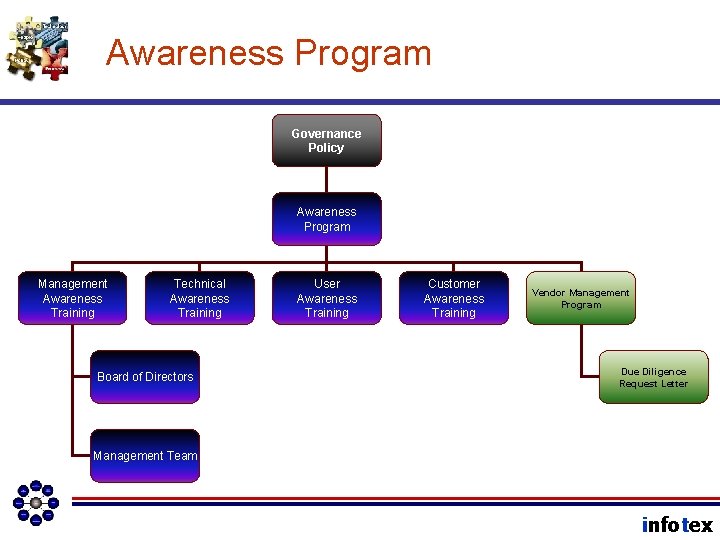
Awareness Program Governance Policy Awareness Program Management Awareness Training Technical Awareness Training Board of Directors User Awareness Training Customer Awareness Training Vendor Management Program Due Diligence Request Letter Management Team infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

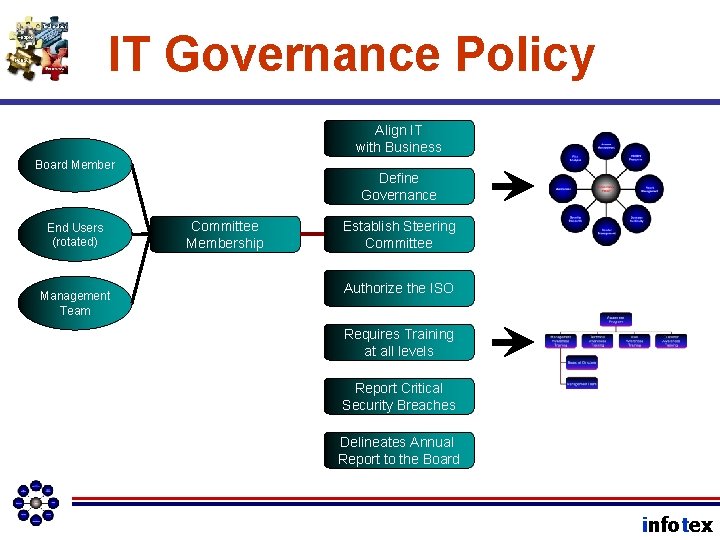
IT Governance Policy Align IT with Business Board Member End Users (rotated) Management Team Define Governance Committee Membership Establish Steering Committee Authorize the ISO Requires Training at all levels Report Critical Security Breaches Delineates Annual Report to the Board infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

In this next section • We will learn why a multidisciplinary approach to technology risk assessments is critical. • We will find out the types of threats that need to be considered in a risk assessment. • We will see a typical risk assessment process. infotex

Summary: Managers Should • Clearly support all aspects of the information security program; • Implement the information security program as approved by the board of directors; • Establish appropriate policies, procedures, and controls; • Participate in assessing the effect of security issues on the financial institution and its business lines and processes; infotex

Summary: Managers Should • Delineate clear lines of responsibility and accountability for information security risk management decisions; • Define risk measurement definitions and criteria; • Establish acceptable levels of information security risks; and • Oversee risk mitigation activities. infotex

That’s straight out of FFIEC guidelines (page 6, Information Security Handbook) infotex

Information Security Program Equals IT Governance Program infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

Risk Analysis Program infotex

Four Primary Risk Assessments Business Impact Analysis Asset Criticality Analysis Technology Risk Assessment Vendor Risk Determination infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2010/2011 • ISO Job Description & Interactions infotex

In this next section • We will learn the primary purposes of an IT Audit. • We will understand the need for riskbased auditing • We will learn the different types of audit tests. • We will be exposed to the need for good IT Audit metrics. infotex

The IT Audit infotex

Three Primary Purposes • Alignment with business mission • Appropriate risk management • Compliance with applicable law infotex

Alignment w/ Business Mission • Strategy Alignment • Facilitate Execution of Business Tactics • Demonstrate Return on Investment infotex

Risk Management Assurance • Test of Risk Assessment Process • Test of Management Awareness • Test of Declared Controls • Test of User Awareness • Escalate Risk Acceptance decisions to the Board of Directors infotex

Comply with the Law! • FFIEC Guidelines as the Framework • Cobi. T as Framework for SOX banks • State laws may introduce individual compliance framework needs (SB 1386 in California) infotex

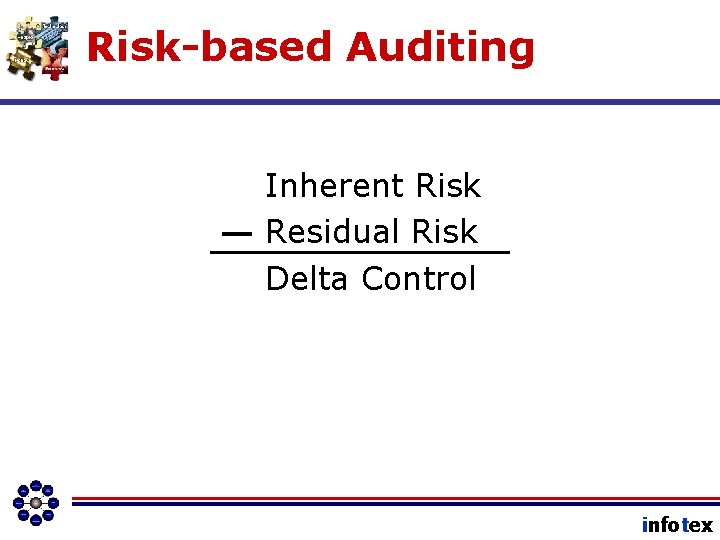
Risk-based Auditing • Ensures testing is appropriate • Delivers Value to Audit Process • Relies heavily on bank risk assessment infotex

Risk-based Auditing • Test the controls that protect the highest value assets. • Test the controls that protect the most likely targeted assets. • Test the controls that management has declared mitigate the MOST risk (highest delta control value). infotex

Risk-based Auditing Inherent Risk Residual Risk Delta Control infotex

Types of IT Audit Tests • Technical • Non-technical infotex

But first … • Capture-the-flag versus assessment infotex

Types of IT Audit Tests • IT Governance Review – – GLBA Compliance Policy and Procedure Review Testing of Non-technical Controls Involves interviewing “all four corners” of the bank infotex

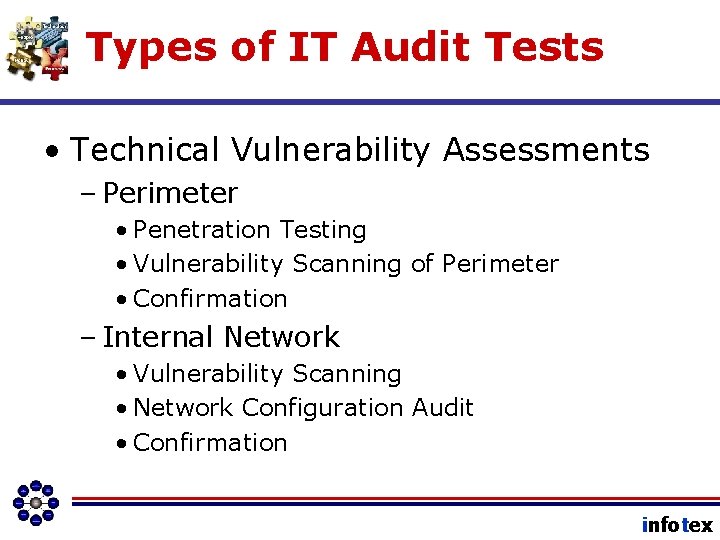
Types of IT Audit Tests • Technical Vulnerability Assessments – Perimeter • Penetration Testing • Vulnerability Scanning of Perimeter • Confirmation – Internal Network • Vulnerability Scanning • Network Configuration Audit • Confirmation infotex

Types of IT Audit Tests • Social Engineering Tests – Two purposes • Test Awareness • Test Incident Response – Spear Phishing – Pretext Calling – Password File Analysis – Orchestrated Attacks infotex

IT Physical Security • Physical Breach Tests • Walk-through’s • Dumpster Diving – Trash-can Diving • Physical Security Checklists infotex

Checklist Tests • IT Governance • Physical Security • Network Configuration Audits Be careful that findings are risk ranked. infotex

Risk Metrics • Should be based on likelihood and impact • Some auditors will also factor in ease of remediation • You should be interested in residual risk, anticipated residual risk, and risk reduction (or “delta control”) infotex

Risk Metrics • Comparing risk from one year to the next, or from one bank to the next, is difficult • What’s important is knowing that the management team understands the metrics and the risk infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

In this next section • We will learn the primary purposes of the annual Vendor Due Diligence Review. infotex

Vendor Management Program Governance Policy Vendor Management Policy Search and Selection Contract Negotiations Threshold Risk Assessment Assigned Security Responsibility Security Sanctions Policy Ongoing Due Diligence Vendor Agreement Template Risk Analysis Procedure Threshold Risk Assessment Vendor Request Vendor Risk Determination Table Detailed Risk Assessment Checklists infotex

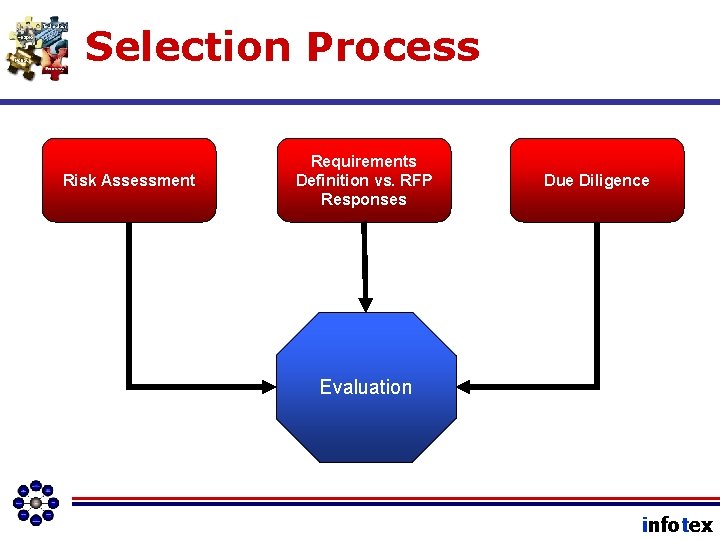
Selection Process Risk Assessment Requirements Definition vs. RFP Responses Due Diligence Evaluation infotex

Vendor Due Diligence Checklist • Makes the annual review go so much better! • . . . at least after the first one. infotex

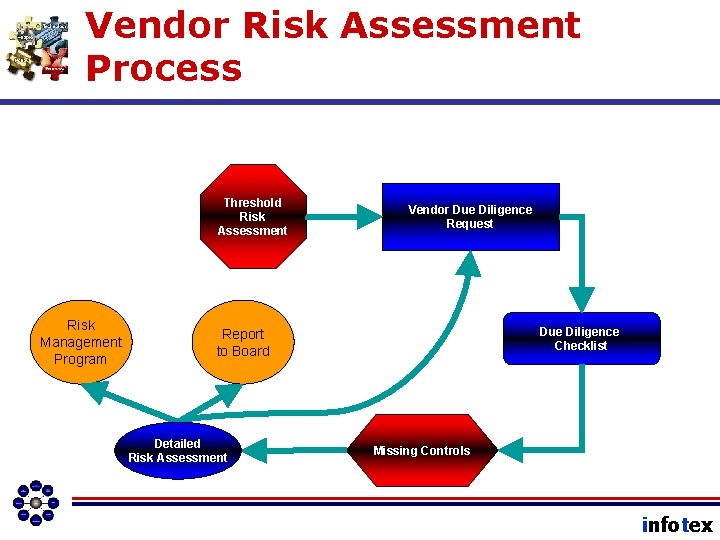
Vendor Risk Assessment Process Threshold Risk Assessment Risk Management Program Vendor Due Diligence Request Due Diligence Checklist Report to Board Detailed Risk Assessment Missing Controls infotex

Outputs of Annual Review ØMissing controls and anticipated safeguards should input into the IT Risk Assessment. infotex

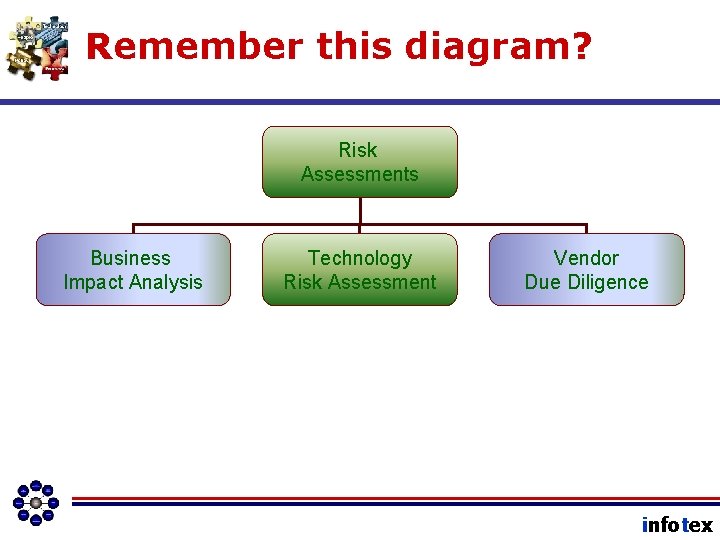
Remember this diagram? Risk Assessments Business Impact Analysis Technology Risk Assessment Vendor Due Diligence infotex

Remember this diagram? Risk Assessments Business Impact Analysis Technology Risk Assessment Vendor Due Diligence This (and missing vendor controls) is where Vendor Due Diligence plugs into the overall Risk Assessment Process. infotex

Outputs of Annual Review ØMissing controls and anticipated safeguards should input into the IT Risk Assessment. ØThey will be deployed as per risk severity in a reasonable period of time. infotex

Outputs of Annual Review ØFinally, risk acceptance decisions should be escalated to the board of directors by the ISO in the Annual Report. infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

In this next section • We will learn some of the fundamental responsibilities of the Information Security Officer. • We will see how the ISO interacts with various areas of the bank. • We will understand how we can utilize the ISO to better manage our own technology risk. infotex

Access Management Risk Analysis Information Technology Governance Program Awareness Incident Response Governance Policy Asset Management Business Continuity Security Standards Vendor Management infotex

Awareness Program Governance Policy Awareness Program Management Awareness Training Technical Awareness Training Board of Directors User Awareness Training Customer Awareness Training Vendor Management Program Due Diligence Request Letter Management Team infotex

Awareness Program Governance Policy Awareness Program Management Awareness Training Technical Awareness Training User Awareness Training Customer Awareness Training Board of Directors Management Team infotex

Risk Management Program Awareness Program Management Awareness Training Technical Awareness Training User Awareness Training Customer Awareness Training Board of Directors Management Team infotex

BAT Tools • Board Awareness Training (video webcast is available) • Annual Report – Risk Analysis Executive Summary – Vendor Due Diligence Results – Summary of Critical Security Breaches – Strategy • Policy Approval Process infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

New Risks in 2011/2012 • Targeted Malware attacks (Zeus, Russian Business Network, Chinese, and spin-offs) • Social Media Usage (by employees AND the bank) • Mobile Banking Deployment infotex

Orchestrated Attacks • Usually combining: – Malware from drive-by attack sites – Phishing – Pretext Calling • Assets Attacked: – Customer credentials – ACH – On-line Banking infotex

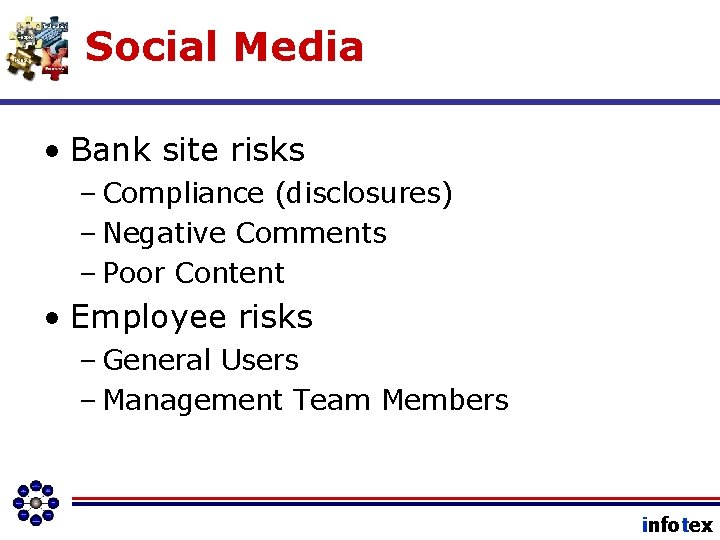
Social Media • Bank site risks – Compliance (disclosures) – Negative Comments – Poor Content • Employee risks – General Users – Management Team Members infotex

Horse Before the Cart: Top 5 Mobile Banking Risks infotex Wireless Banking Risks 1. 2. 3. 4. 5. Late Majority Adoption Tepid Adoption Security Risk Compliance Risk Strategic Risk infotex

Today’s Agenda • Management Awareness Resources • Five Tenets of IT Governance • The IT Governance Program – The Risk Assessment – Information Technology Audits – Vendor Due Diligence – Awareness Training • New Risks for 2011/2012 • The 2011 Audit Results infotex

In this next section • We will learn some of the fundamental responsibilities of the Information Security Officer. • We will see how the ISO interacts with various areas of the bank. • We will understand how we can utilize the ISO to better manage our own technology risk. infotex

ISO Job Description • The single point of contact. . . liaison. . . for all matters involving Information Security (and often IT Governance as a whole. ) • The “inside consultant” on IT Security Matters. • The person who teaches us how to manage technology risk. infotex

ISO Teams • Steering Committee: Member • Technical Staff: Member • CIRT: Team Leader • Risk Assessment: Team Leader • Vendor Management: Team Leader • Business Continuity Plan: sometimes the BCP coordinator, often not. infotex

What the ISO does. . . • Writes policies and procedures. • Filters vulnerability news down to what the bank needs to know. • Writes agendas and reports for various meetings. • Activates awareness through reminders, tests, and training. infotex

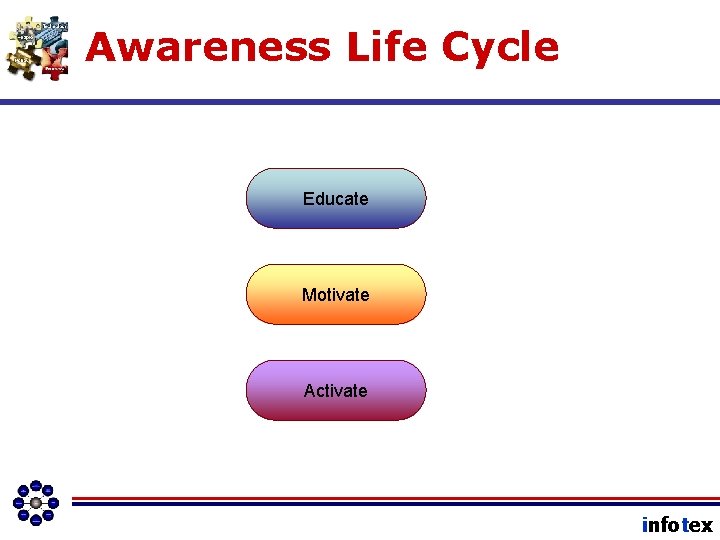
ISO Job Description • Maintain the IT Governance Program • Ensure through measurement and testing that the controls in the IT Governance Program are adequate and are being enforced. • Escalate Risk Acceptance Decisions to the Board • Educate, Motivate, and Activate Awareness. infotex

Awareness Life Cycle Educate Motivate Activate infotex

Four Corners Board of Directors Customers Oversight Committee Management Team Vendors Users Technical Team infotex

Board Level • Educate • Annual Report, Awareness Training • Motivate • Risk Analysis, VDD Results, Audit Findings • Activate • Policy Approval, Strategy, Budget infotex

Management Team • Educate • Motivate • Activate • Annual Awareness Training, Applicable Policies and Procedures (see distribution list) • Annual Report to the Board, Audit Results • Risk Analysis, Vendor Due Diligence infotex

Technical Team • Educate • Motivate • Activate • IT Audit Program, Security Standards, Policies and Procedures, Comprehension Testing, BCP Testing Plan • Auditing, Monitoring, Testing, Vulnerability Assessments • Vulnerability Reports, Conferences, CPE infotex

Users • Educate • Motivate • Activate • Acceptable Use Policy • Annual Awareness Training, Comprehension Tests • Social Engineering Tests, Exercises, Reminders infotex

Customers • Educate • Motivate • Activate • Flyers, Knowledgeable Employees • Annual Awareness Training • Stuffers, Web Site Announcements infotex

Vendors • Educate • Motivate • Activate • Due Diligence Request Letter, Phone Call • Contract Negotiations, Due Diligence Request Letter, AP New Vendor Form • Ongoing discussion emphasizing security. A call when something doesn’t seem right. infotex

On the Portal. . . • Information Security Officer Job Description infotex

How should we summarize? infotex

Interactions infotex

ISO must interact with: • Board of Directors – Annual Report to the Board – Risk Acceptance Decisions – Policy Approval infotex

ISO must interact with: • Oversight Committee – Internal Auditing – Monitoring – Audit Reports – Vulnerability Assessments infotex

ISO must interact with: • Management Team – Risk Analysis – Training – Vendor Due Diligence – Access Authorization Review – Budget – Incident Response infotex

ISO Must Interact With: • The you-wouldn’t-expect interactions – Human Resources • Policy Development and Enforcement • Incident Response Team • Risk Assessment • Orientation – Marketing • Customer Awareness Training • Public Presence Security Controls • Use of Social Media infotex

ISO must interact with: • Technical Team – Security Standards – Incident Response – Vulnerability Assessments – Audits – Network Monitoring infotex

ISO must interact with: • Users (all employees) – Acceptable Use Policy – Annual Awareness Training – Policy Enforcement – Security Reminders and Notices – Testing – Incident Response – Answering Questions infotex

ISO must interact with: • Vendors – Vendor Risk Analysis – Vendor Due Diligence Requirements – Risk Acceptance infotex

ISO must interact with: • Customers – Customer Awareness Training – Incident Response infotex

Thank you! Don’t forget the Evaluations! infotex

The Workshop Portal • List of boilerplates and related websites. • Electronic Version of Documents, Articles, and Boilerplates for your use. – mat 2009. infotex. com (all lower case) – Your user name. . . mat 2009 (all lower case) – Th 3!b@#1 is the password. • Portal is classified “internal use. ” infotex
 Privacy awareness and hipaa awareness training cvs
Privacy awareness and hipaa awareness training cvs Environmental management system awareness training
Environmental management system awareness training Dynamic risk assessment
Dynamic risk assessment Maclaurin series vs taylor series
Maclaurin series vs taylor series Heisenberg 1925 paper
Heisenberg 1925 paper Maclaurin series vs taylor series
Maclaurin series vs taylor series Taylor frederick
Taylor frederick P series server
P series server Feedback amplifier
Feedback amplifier Series aiding and series opposing
Series aiding and series opposing Arithmetic sum formula
Arithmetic sum formula Iso 9001 presentation
Iso 9001 presentation Security training and threat awareness
Security training and threat awareness Cjis level 4 certification
Cjis level 4 certification Sexual abuse quiz
Sexual abuse quiz Ppe awareness training
Ppe awareness training Ppe awareness training
Ppe awareness training Iatf 16949 awareness training
Iatf 16949 awareness training Iso 9001:2015 management review meeting presentation ppt
Iso 9001:2015 management review meeting presentation ppt Iso 14001 2015 awareness training
Iso 14001 2015 awareness training Insider threat awareness training
Insider threat awareness training Security education training and awareness seta
Security education training and awareness seta Mold awareness training
Mold awareness training Chemical security awareness training
Chemical security awareness training Dysphagia care training
Dysphagia care training Vibration awareness training
Vibration awareness training Ergonomics awareness training for supervisors
Ergonomics awareness training for supervisors Ergonomics awareness training for supervisors
Ergonomics awareness training for supervisors Sfar 73 awareness training
Sfar 73 awareness training Mold awareness training
Mold awareness training Insider threat awareness
Insider threat awareness Esd awareness training
Esd awareness training Webroot cyber security training
Webroot cyber security training Lgbt awareness training
Lgbt awareness training Find ergonomics awareness training
Find ergonomics awareness training Rf safety awareness training answers
Rf safety awareness training answers Bloodborne pathogens awareness training
Bloodborne pathogens awareness training Phonological awareness training program
Phonological awareness training program Child protection awareness training
Child protection awareness training Counterfeit material awareness training
Counterfeit material awareness training Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Ehs awareness training
Ehs awareness training Sfcu medford ny
Sfcu medford ny Uc cyber security awareness training answers
Uc cyber security awareness training answers The safest ladder to use around electricity
The safest ladder to use around electricity Cda security awareness training
Cda security awareness training Cultural awareness training presentation
Cultural awareness training presentation Asbestos awareness training wa
Asbestos awareness training wa Perbedaan on the job training dan off the job training
Perbedaan on the job training dan off the job training Perbedaan consciousness dan awareness
Perbedaan consciousness dan awareness Pyramid levels of management
Pyramid levels of management Top management middle management first line management
Top management middle management first line management Top management and middle management
Top management and middle management Analisis time series dan forecasting data keuangan
Analisis time series dan forecasting data keuangan Training is expensive without training it is more expensive
Training is expensive without training it is more expensive Aggression replacement training facilitator training
Aggression replacement training facilitator training Te&o army
Te&o army Time management training materials
Time management training materials Rqm 110
Rqm 110 Masterclassmanagement
Masterclassmanagement Customer relationship management training ppt
Customer relationship management training ppt Application lifecycle management training
Application lifecycle management training Absence management training
Absence management training Self management and recovery training
Self management and recovery training Problem management expert is responsible for
Problem management expert is responsible for Institute of secretariat training and management
Institute of secretariat training and management Total management and training
Total management and training Dynamic tag management
Dynamic tag management Sampoorna school
Sampoorna school Methods of training in human resource management
Methods of training in human resource management Nara records management training
Nara records management training Flighthub check in
Flighthub check in What does palms stand for in conflict resolution
What does palms stand for in conflict resolution Call centre management training
Call centre management training Metadata management training
Metadata management training Navy stress management training
Navy stress management training Inventory management training ppt
Inventory management training ppt Green world group hyderabad
Green world group hyderabad Csr radar
Csr radar Change management training materials
Change management training materials Iaea gsr part 2
Iaea gsr part 2 Atlweather
Atlweather Command financial management system training
Command financial management system training Why is self-awareness important
Why is self-awareness important Trauma awareness and treatment center utah
Trauma awareness and treatment center utah Metalinguistic awareness
Metalinguistic awareness Metalinguistic awareness
Metalinguistic awareness Lesson eleven consumer awareness
Lesson eleven consumer awareness Lesson eleven consumer awareness
Lesson eleven consumer awareness Kpis de awareness
Kpis de awareness Elaine bromiley case
Elaine bromiley case Self awareness is having a clear perception of
Self awareness is having a clear perception of Substitute phonemes
Substitute phonemes Intentional communication
Intentional communication Phonological awareness continuum chart
Phonological awareness continuum chart Phonemic awareness definition
Phonemic awareness definition Prephonemic stage
Prephonemic stage Arctic domain awareness center
Arctic domain awareness center Objective for mental health awareness
Objective for mental health awareness Mental health awareness poem
Mental health awareness poem Medical ultrasound awareness month
Medical ultrasound awareness month Awareness exploration expansion commitment dissolution
Awareness exploration expansion commitment dissolution Shared situational awareness jesip
Shared situational awareness jesip 3 zones of space and awareness dementia
3 zones of space and awareness dementia Internal audit awareness presentation
Internal audit awareness presentation Integrated awareness
Integrated awareness Potential insider threat indicators cyber awareness
Potential insider threat indicators cyber awareness Non obvious relationship awareness
Non obvious relationship awareness Raise awareness of or for grammar
Raise awareness of or for grammar Pa-psfa-hazardous materials awareness
Pa-psfa-hazardous materials awareness Ammonia awareness safety program
Ammonia awareness safety program Test your awareness whodunnit answers
Test your awareness whodunnit answers Environment definition
Environment definition Language awareness readings for college writers
Language awareness readings for college writers 10 points on self-awareness
10 points on self-awareness Dyslexia awareness week 2020
Dyslexia awareness week 2020 Dwarfism awareness перевод
Dwarfism awareness перевод Cyber awareness meting
Cyber awareness meting Security awareness game
Security awareness game Advantages of current awareness services
Advantages of current awareness services Current awareness platform
Current awareness platform Awareness of sin
Awareness of sin Constant integrated awareness
Constant integrated awareness Direct inner awareness example
Direct inner awareness example Advertising communication models
Advertising communication models Circle of sexuality
Circle of sexuality Four common marketing tactics are:
Four common marketing tactics are: Self-awareness examples
Self-awareness examples Self awareness continuum
Self awareness continuum Security awareness screensavers
Security awareness screensavers Our awareness of ourselves and our environment.
Our awareness of ourselves and our environment. Celf 5 percentile ranks
Celf 5 percentile ranks Cultural awareness questions
Cultural awareness questions Your conscious awareness of your own name and self identity
Your conscious awareness of your own name and self identity Dimension of self awareness
Dimension of self awareness Question maker face asl
Question maker face asl Awareness raising tv spot
Awareness raising tv spot Language flashcards
Language flashcards Johari window arena
Johari window arena Introduction to mental health awareness presentation
Introduction to mental health awareness presentation Awareness exploration expansion commitment dissolution
Awareness exploration expansion commitment dissolution Ptit safe driving and awareness course
Ptit safe driving and awareness course Staircase that represents cultural competence
Staircase that represents cultural competence Iso27001 staff awareness
Iso27001 staff awareness Lesson 5 freedom of the human person answer key
Lesson 5 freedom of the human person answer key Drink area
Drink area Consumer awareness conclusion
Consumer awareness conclusion Highland substance awareness toolkit
Highland substance awareness toolkit Charity awareness monitor
Charity awareness monitor Gestalt cycle of awareness interruptions
Gestalt cycle of awareness interruptions Awareness requires totally focusing attention on the task.
Awareness requires totally focusing attention on the task. Change curve+awareness+understanding+acceptance+commitment
Change curve+awareness+understanding+acceptance+commitment Awareness of ourselves and our environment is:
Awareness of ourselves and our environment is: Tadra is an acronym for the state of georgia
Tadra is an acronym for the state of georgia Elsmar.com
Elsmar.com Sutherland phonological awareness test
Sutherland phonological awareness test Sound word wall
Sound word wall Center for spiseforstyrrelser herning
Center for spiseforstyrrelser herning 13 malaysian patient safety goals
13 malaysian patient safety goals Outdoor ethics awareness award
Outdoor ethics awareness award Printer security awareness
Printer security awareness What is internet awareness
What is internet awareness Total set awareness set consideration set
Total set awareness set consideration set Self awareness project
Self awareness project Information technology workshop
Information technology workshop Idph allergen awareness
Idph allergen awareness Phonemic awareness ppt
Phonemic awareness ppt Hosa health education portfolio examples
Hosa health education portfolio examples When a driver's awareness and focus drift from
When a driver's awareness and focus drift from Phonemic awareness
Phonemic awareness Sensitive line self awareness
Sensitive line self awareness Awareness of ourselves and our environment is
Awareness of ourselves and our environment is Awareness of ourselves and our environment is:
Awareness of ourselves and our environment is: Vigilance awareness week presentation
Vigilance awareness week presentation Awareness creativity and communication
Awareness creativity and communication What does cultural awareness mean
What does cultural awareness mean Social justice awareness
Social justice awareness Situational awareness construction
Situational awareness construction Self confidence and self awareness eyfs
Self confidence and self awareness eyfs Robbery prevention training
Robbery prevention training Robbery awareness
Robbery awareness Environmental awareness presentation
Environmental awareness presentation Security awareness program
Security awareness program