Health Information Privacy Security LIS 4785 Introduction to

























- Slides: 35

Health Information Privacy & Security LIS 4785 Introduction to Health Informatics Fall 2015, Week 10 -1 Instructor: Dr. Sanghee Oh

Incoming Course Schedule • Week 10 (10/27, 10/29) – Health information privacy & security; Telehealth; mhealth • Week 11 (11/3, 11/5) – Project Application Template Demo; Consumer health informatics • Week 12 (11/10, 11/12) – No classes; Self study; Group meetings • Week 13 (11/17, 11/19) – Topic reviews; Midterm exam 2 (11/19) • Week 14 (11/24, 11/26) Thanksgiving Holidays – No classes • Week 15 (12/1, 12/3) – Final Presentations • Week 16 (12/8, 12/10) – No classes; Final report submission

Show and Tell

HEALTH INFORMATION PRIVACY & SECURITY

Health Insurance Portability and Accountability Act (HIPAA)

History HIPAA Health Insurance Portability and Accountability Act (1996) HITECH American Recovery and Reinvestment Act - Health Information Technology for Economic and Clinical Health (2009) Meaningful Use Guidelines for EHR (2010)

Health Insurance Portability and Accountability Act (1996) (HIPPA) • Before HIPPA, there was no universally recognized security standard or basic mandates for Protected Health Information (PHI) • The goal of HIPAA was to ___________ while enabling healthcare organizations to pursue initiatives that further innovation and patient care. • However, enforcement was very limited. HIPAA Health Insurance Portability and Accountability Act (1996)

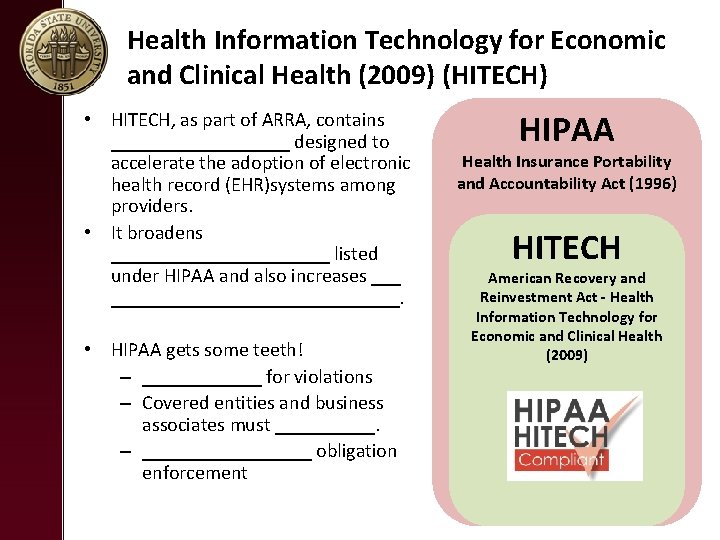
Health Information Technology for Economic and Clinical Health (2009) (HITECH) • HITECH, as part of ARRA, contains _________ designed to accelerate the adoption of electronic health record (EHR)systems among providers. • It broadens ___________ listed under HIPAA and also increases ________________. • HIPAA gets some teeth! – ______ for violations – Covered entities and business associates must _____. – _________ obligation enforcement HIPAA Health Insurance Portability and Accountability Act (1996) HITECH American Recovery and Reinvestment Act - Health Information Technology for Economic and Clinical Health (2009)

Health Information Technology for Economic and Clinical Health (2009) (HITECH) • CMS’s Meaningful Use incentives program provides incentive payouts to eligible professionals, hospitals, and CHAs (Community Health Alliances) that meet criteria for efficient and patient‐centered use of EHR. • The program provides incentives to further __________ set fourth in HITECH and HIPAA, including conducting a risk analysis. HIPAA Health Insurance Portability and Accountability Act (1996) HITECH American Recovery and Reinvestment Act - Health Information Technology for Economic and Clinical Health (2009) Meaningful Use Guidelines for EHR (2010)

The Health Insurance Portability and Accountability Act of 1996 (HIPAA) • The primary goal of HIPPA is _________ and ____________.

Electronic Health Records: Privacy and Security https: //www. youtube. com/watch? v=SMUFa 5 am. PKs

What Information Must Be Protected?

__________________ • HIPAA protects an individual’s health information and his/her demographic information. This is called “_______________” or “PHI”. • Information meets the definition of PHI if, even without the patient’s name, if you look at certain information and ______________ then it is PHI. • The PHI can relate to __________ physical or mental health of the individual. PHI describes a disease, diagnosis, procedure, prognosis, or condition of the individual and can exist in _______ – files, voice mail, email, fax, or verbal communications. These rules apply ______ you view, use, and share PHI. • •

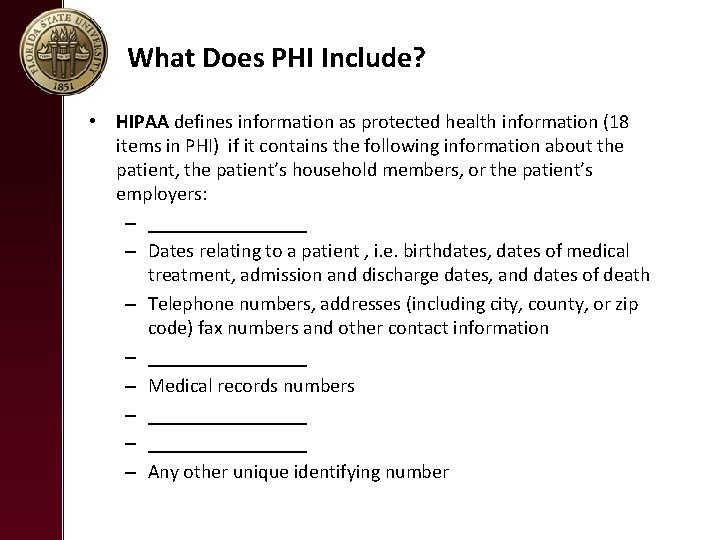
What Does PHI Include? • HIPAA defines information as protected health information (18 items in PHI) if it contains the following information about the patient, the patient’s household members, or the patient’s employers: – ________ – Dates relating to a patient , i. e. birthdates, dates of medical treatment, admission and discharge dates, and dates of death – Telephone numbers, addresses (including city, county, or zip code) fax numbers and other contact information – ________ – Medical records numbers – ________________ – Any other unique identifying number

HIPAA Rules • If you’re a covered entity (a health care plan, a health care clearinghouse or a health care provider that electronically transmits medical information), then you must comply with: – ________, which regulates the use and disclosure of Protected Health Information (PHI) held by covered entities, and protects individuals’ rights to understand control how their health information is used. – ________, which complements the Privacy Rule and deals specifically with Electronic Protected Health Information (e. PHI). It states that covered entities must ensure the confidentiality, integrity and availability of all e. PHI they create, receive, maintain or transmit. – ________, which relates to the standardization of electronic transactions. – ________, which states that all HIPAA covered healthcare providers using electronic communications must use a unique ten‐digit identification number National Provider Identifier (NPI). – ________, which establishes procedures for compliance and investigations, and sets civil money penalties for violations of the HIPAA AS Rules

HIPAA PRIVACY RULE

HIPAA Privacy Rule

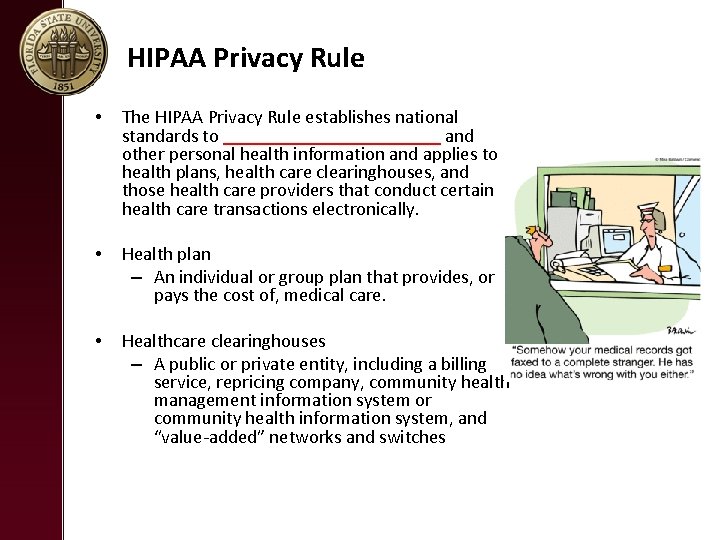
HIPAA Privacy Rule • The HIPAA Privacy Rule establishes national standards to ____________ and other personal health information and applies to health plans, health care clearinghouses, and those health care providers that conduct certain health care transactions electronically. • Health plan – An individual or group plan that provides, or pays the cost of, medical care. • Healthcare clearinghouses – A public or private entity, including a billing service, repricing company, community health management information system or community health information system, and “value‐added” networks and switches

HIPAA Privacy Rule • The HIPAA Privacy Rule establishes a set of national standards for the ________ of individually identifiable health information – often called ___________– by covered entities, as well as standards for providing individuals’ with health information privacy rights and helping individuals understand control how their health information is used.

A PATIENT’S RIGHTS • HIPAA stipulates the following patient’s right under its privacy rule: – Patients have a right to receive a __________ of any health care provider health clearing house, or health plan. – Patients have a right to ________ and ________of their PHI (paper or electronic formats). – Patients have a right to request ________ to information, that changes be made to correct errors in their records or to add information that ha been omitted. – Patients have a right to request ________ of PHI uses and disclosures. – Patients have a right to request that you give ________ to their PHI. – Patients have a right to request ________. – Patients have a right to ________.

Notice of Privacy Practices • Describes to patients how their protected health information may be ________ • Details ________in regards to their PHI and how to exercise these rights • Details ________of covered entity to protect PHI

Notice of Privacy Practices (NPP) for PHI • The NPP allows PHI to be used and disclosed for purposes of TPO (_______________, and ________) • Examples – The patient’s referring physician calls and asks for a copy of the patient’s recent exam at a healthcare setting. – A patient’s insurance company calls and requests a copy of the patient’s medical record for a specific service date – The Quality Improvement office calls and asks for a copy of an Operative Report • TPO includes teaching, medical staff/peer review, legal, auditing, quality reviews, customer service, business management, and releases mandated by law.

Minimum Necessary • Minimum Necessary applies: – When using or disclosing PHI or when requesting PHI from another covered entity or business associate, a covered entity or business associate must make reasonable efforts to _____________________ to accomplish the intended purpose of the use, disclosure, or request.

HIPAA Snippets: Social Media Compliance https: //www. youtube. com/watch? v=n 6 WMGg 26 lj. A

Use of Social Media • An example guideline regarding use of social media at the UCSF Healthcare Facility. – Do not share on social media any patient information acquired through your work, even if the information is public. – Information obtained from your patient/provider relationship is confidential. – Posting patient information without authorization is a violation of the patient’s right to privacy and confidentiality. – Even if you think you’ve de‐identified the information, it still might be identifiable to others. • NOTE: De‐identification of PHI requires removal of all 18 PHI • identifiers, which includes “Any other unique identifying number, code, or characteristic” (e. g. , photo of a wound; description of a patient’s condition)

HIPAA SECURITY RULE

HIPAA Security Rule • The HIPAA Security Rule establishes national standards to protect individuals’ ________________ that is created, received, used, or maintained by a HIPPA covered entity. e-PHI

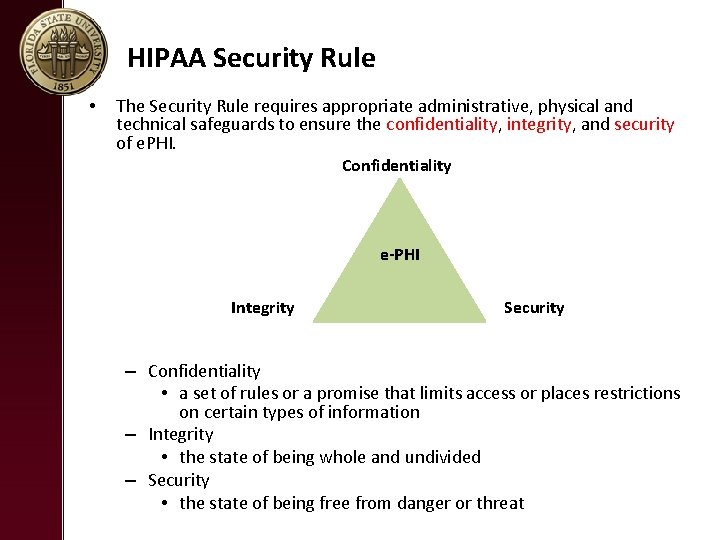
HIPAA Security Rule • The Security Rule requires appropriate administrative, physical and technical safeguards to ensure the _______________, and ________ of e. PHI.

HIPAA Security Rule • The Security Rule requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of e. PHI. Confidentiality e-PHI Integrity Security – Confidentiality • a set of rules or a promise that limits access or places restrictions on certain types of information – Integrity • the state of being whole and undivided – Security • the state of being free from danger or threat

Security of e. PHI • Good security standards follow the “ 90/10” Rule: – 10% of security safeguards are ________ – 90% of security safeguards rely on ________ to adhere to good practices

HIPAA VIOLATIONS

HIPAA Violations Bring More Than Minimal Fines https: //www. youtube. com/watch? v=U 0‐FQQet. Ez. Y

A Breach of Unsecured PHI • A breach is, generally, an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of PHI such that the use or disclosure poses a significant risk of financial, reputational, or other harm to the affected individual. • The Breach Notification Rule requires covered providers to promptly notify individuals and the Secretary of the HHS (Department of Health and Human Services) of the loss, theft, or certain other impermissible uses or disclosures of unsecured PHI. Health care providers must also promptly notify the Secretary of HHS if there is any breach of unsecured protected health information if the breach affects 500 or more individuals, and notify the media if the breach affects more than 500 individuals of a State or jurisdiction. •

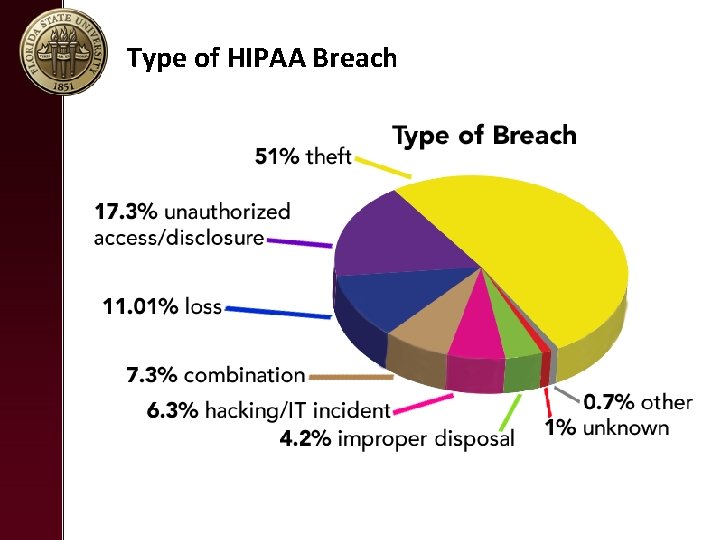
Type of HIPAA Breach

Penalties • Failure to comply with the HIPAA Rules can result in civil and criminal penalties ($100 per violations to millions). • Civil Penalties – The U. S. Department of Health and Human Services (HHS)’ Office for Civil Rights (OCR) is responsible for administering and enforcing the HIPAA Privacy and Security Rules and conducts associated complaint investigations, compliance reviews, and audits. OCR may impose fines on covered providers for failure to comply with the HIPAA Rules. – State Attorneys General may also enforce provisions of the HIPAA Rules. • Criminal Penalties – The U. S. Department of Justice (DOJ) may enforce criminal penalties for HIPAA violations.
 Gb4785
Gb4785 Privacy awareness and hipaa privacy training cvs answers
Privacy awareness and hipaa privacy training cvs answers Private securty
Private securty Azure security privacy compliance and trust
Azure security privacy compliance and trust Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Chapter 9 privacy security and ethics
Chapter 9 privacy security and ethics Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Cyberextortionist definition
Cyberextortionist definition Visa international security model
Visa international security model Cnss model
Cnss model Australian privacy principles
Australian privacy principles Issues surrounding information privacy
Issues surrounding information privacy Revealing information while preserving privacy
Revealing information while preserving privacy Introduction to information security chapter 2
Introduction to information security chapter 2 10 difference between health education and health promotion
10 difference between health education and health promotion How to remove personnel in lis
How to remove personnel in lis Lis de veracruz
Lis de veracruz Je lis des syllabes
Je lis des syllabes Křivka lis
Křivka lis Lis de veracruz arte ciencia luz
Lis de veracruz arte ciencia luz La lengua de las mariposas donde ver
La lengua de las mariposas donde ver Ntu lis
Ntu lis Lis his system
Lis his system Land-l are recursive enumerable then lis
Land-l are recursive enumerable then lis Hydraulický lis výpočet
Hydraulický lis výpočet Lis deped forgot password
Lis deped forgot password Lis bosy
Lis bosy Lis ampath
Lis ampath Lehrplaninformationssystem bayern
Lehrplaninformationssystem bayern Lis lewis structure
Lis lewis structure Hệ thống thông tin trong logistics
Hệ thống thông tin trong logistics Celula hepatocito
Celula hepatocito Lis tussyadiah
Lis tussyadiah Whats lis pendens
Whats lis pendens Je lis, je comprends segpa
Je lis, je comprends segpa