Get a WIF of this An introduction to






















- Slides: 27

Get a WIF of this! An introduction to Identity with WIF & AD FS 2. 0

About Todd Anderson Principal Consultant, CAthreads. net Expertise in WF 4, App. Fabric & WIF Co-Developed App. Fabric Training Kit for MS & ISV Starter Kit Email me: Todd@CAthreads. NET

About Zoiner Tejada President Tejada. NET Software Consultant Author, Trainer & Speaker Microsoft Influencer & CSD Advisor 10+ years experience Architecture SIG CS Degree Stanford University Email me: Zoiner. Tejada@Tejada. NET. com

Windows Identity Foundation �This presentation will focus on how WIF: �Can be used with websites as well as web services. �Makes life much easier for the developer. �Opens up possibilities that normally have been prohibitively complex. �Now to introduce the participants of this presentation:

The Ultimate Surfboard. . . The WIFboard �WIF (Windows Identity Foundation)– �It’s not just about Federation, it’s about outsourcing security decisions �Designed to integrate with ASP. NET and WCF applications.

The Surf Spot Relying Party (RP) �Replying parties are your applications: �Web Sites � WIF is used with a passive client, the browser. �Web Services � WIF is used in an Active manner.

The Kahuna STS / Identity Provider �Kahuna is the Hawaiian term for Authority �The same goes for a Security Token Service. �A Security Token Service is an authority on providing identity for the relying party. � An STS is generally a web service. �The Surf Spot expects to know how to talk with the Kahuna. �Various standards at play to achieve this.

The Shaka Security Tokens �Security Tokens contain claims. �These claims are information the RP needs to know about the user. For permission to surf at the spot, the surfer must go to that spot’s Kahuna and ask for a shaka, then present this shaka to the surf spot.

The Surfer (user) �In order to have authorization to surf at a surf spot (RP), the surfer must get shakas from the Kahuna (STS) and present them. �Some surf spots require a closer look at the shakas (security token claims) from the Kahuna. This surfer’s claim indicates he’s ridden ten foot barrels! He can surf here.

The Surf Mobile Fed. Util. exe �Fed. Util. exe is a configuration wizard that’s run against your application (RP) �It tells the surf spot to trust the Kahuna �To use Fed. Util. exe in Visual Studio �Right-click your website or web service �select "Add STS Reference. . . “ � Provide information about � The location of your RP � What STS to use � Certificate settings

Demo �Create a claims enabled web site that utilizes a simple STS �Create a claims enabled web service that utilizes a simple STS

All you need to go surf �A standards compliant Kahuna (STS) �A surf spot (RP) �The Surf Mobile (Fed. Util. exe) �A trusty WIFboard

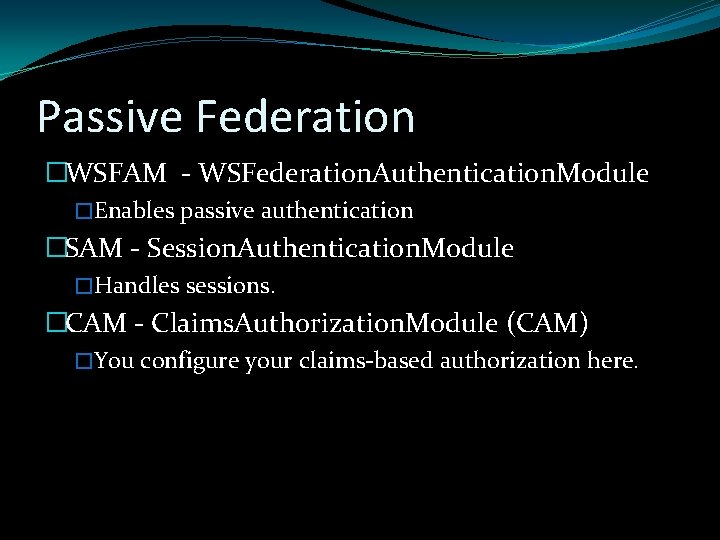
Passive Federation �WSFAM - WSFederation. Authentication. Module �Enables passive authentication �SAM - Session. Authentication. Module �Handles sessions. �CAM - Claims. Authorization. Module (CAM) �You configure your claims-based authorization here.

DEMO �Converting a membership/role provider based website to a claims based one

Federating identity �How would a surf spot trust the authority of Kahunas from other islands? �When your RP wants to authorize users from multiple IP-STSs, you use an FP-STS as an intermediary between the IP-STSs and your RP.

Federation Provider �A Federation Provider is also an STS, but it passes thru or transforms claims �The FP-STS accepts the tokens from the IP-STSs and if necessary, can transform the claims in these tokens before providing them to the RP.

Where is my Kahuna Home Realm Discovery (HRD) �When there is more than one Kahuna for a user to authenticate at. . �Upon arriving at the RP, you need to be redirected to the correct IP-STS for authentication. �Two approaches � Indicate which Kahuna via URL � Have user pick from list

Delegation �Without WIF, it is similar to needing a different surfboard for each condition you may encounter. �Trusted Subsystem is a security risk � When Johnny Utah logs into the web application, he is actually using Brodiliah’s admin account to be able to access the backend data. � With some clever tricks, Johnny could be able to gain access to information he’s not supposed to be able to reach. �The solution? Keep passing the original users credentials with delegation, tacking on other claims as needed downstream.

Federating Non-Claims Aware Apps �Claims to Windows Token Service (C 2 WTS) �C 2 WTS enables use of legacy or 3 rd party systems that rely on Windows Integrated Authorization and cannot be migrated to using claims. �Claims presented are converted to an impersonated Windows identity on the local box and the target application works as before. � e. g. , SQL Server

A Real-Life Big Kahuna let’s look at AD FS 2. 0. . .

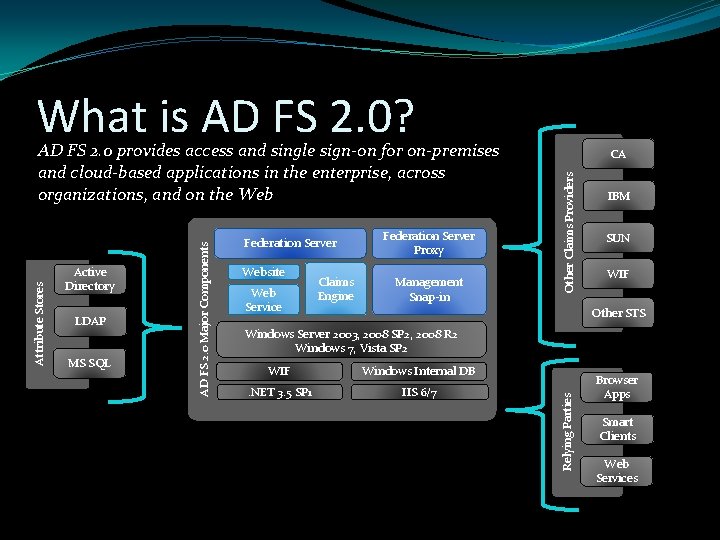
What is AD FS 2. 0? LDAP MS SQL Website Web Service Claims Engine Federation Server Proxy Management Snap-in Other Claims Providers Federation Server CA IBM SUN WIF Other STS Windows Server 2003, 2008 SP 2, 2008 R 2 Windows 7, Vista SP 2 WIF Windows Internal DB . NET 3. 5 SP 1 IIS 6/7 Relying Parties Active Directory AD FS 2. 0 Major Components Attribute Stores AD FS 2. 0 provides access and single sign-on for on-premises and cloud-based applications in the enterprise, across organizations, and on the Web Browser Apps Smart Clients Web Services

ADFS 2. 0 Benefits �Benefits of SSO � reduce administrative overhead � reduce security vulnerabilities as a result of lost or stolen passwords � improve user productivity �Intra-Enterprise: � provide SSO for all your web sites and applications �Pan-Enterprise: � provide SSO experiences for your users to access apps in other organizations � provide SSO experience for users from external organizations to access your apps �Easily externalize authentication & authorization � Rich claims rules processing engine � Management & Configuration Tools

Why even consider AD FS 2. 0? �Building a production-ready STS is hard. �The Visual Studio STS templates are just starters for trivial dev scenarios. �Lot's of config to manage, UI's to present in real world STS!

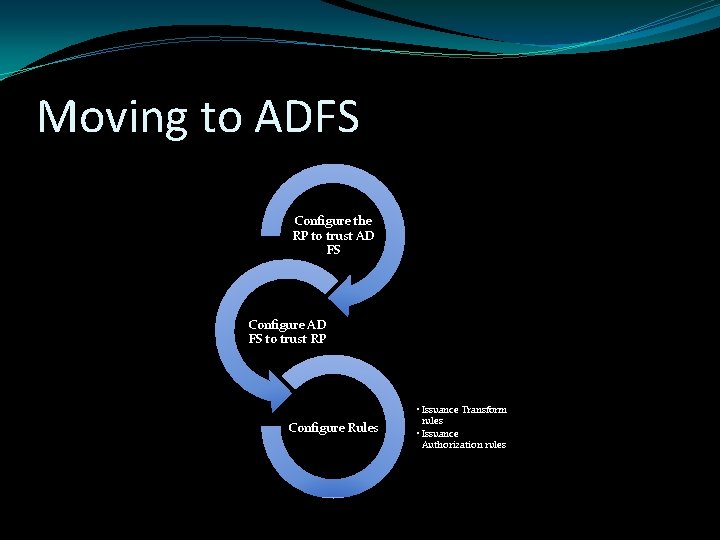
Moving to ADFS Configure the RP to trust AD FS Configure AD FS to trust RP Configure Rules • Issuance Transform rules • Issuance Authorization rules

DEMO �Migrating from a development STS to AD FS 2. 0

Other Scenarios Delegation Federating with another Claims Provider Leveraging Attribute Stores other than Active Directory

Useful Links �Blog: http: //The. Workflow. Element. com �WIF Dev Center - http: //msdn. microsoft. com/enus/security/aa 570351. aspx �For WIF SDK LABS link to Online STS (AD FS 2) � https: //ip-sts-01. federatedidentity. net/federationmetadata/200706/federationmetadata. xml � There's a few links floating around that are wrong. . . this is the correct one. �C 2 WTS - http: //msdn. microsoft. com/enus/library/ee 517278. aspx �ADFS How to Guides - http: //technet. microsoft. com/enus/library/dd 727938(WS. 10). aspx ( ) �Self-STS - http: //code. msdn. microsoft. com/Self. STS
 Get on get off
Get on get off Songs with poetic techniques
Songs with poetic techniques Get up get moving quiz
Get up get moving quiz Get up get moving quiz
Get up get moving quiz Get up get moving quiz
Get up get moving quiz Selection pseudocode example
Selection pseudocode example Get focused get results
Get focused get results Get up get moving quiz
Get up get moving quiz Introduction paragraph format
Introduction paragraph format What is the theoretical yield
What is the theoretical yield Who or what decides what you get
Who or what decides what you get Get the label
Get the label Sharpen the saw
Sharpen the saw Well if shelby were more serious about her studies
Well if shelby were more serious about her studies How to.find volume
How to.find volume How to get the selling price
How to get the selling price How to get percentage error
How to get percentage error Stuttering job interview
Stuttering job interview What is theoretical yeild
What is theoretical yeild Conditional past perfect
Conditional past perfect Karakia mo te taonga
Karakia mo te taonga Shortest path to get food
Shortest path to get food Passive with get + past participle
Passive with get + past participle Lets get a lock for this thing cartoon
Lets get a lock for this thing cartoon Speed & distance formula
Speed & distance formula Past simple of leave
Past simple of leave Calcular geb y get
Calcular geb y get Calcular geb y get
Calcular geb y get