DITTO A SYSTEM FOR OPPORTUNISTIC CACHING IN MULTIHOP


![HIERARCHICAL CACHING [WEB CACHING TECHNIQUE] Takes advantage of the similarity and locality of workload. HIERARCHICAL CACHING [WEB CACHING TECHNIQUE] Takes advantage of the similarity and locality of workload.](https://slidetodoc.com/presentation_image/6a89e39cbc461bf743a2fc6f8ef2063f/image-6.jpg)






- Slides: 28

DITTO - A SYSTEM FOR OPPORTUNISTIC CACHING IN MULTIHOP MESH NETWORKS

CONTENTS • • • Introduction to WMN Throughput issues in WMN Related Work Challenges and Opportunities Ditto Design Chunk Based Transfers – Ditto Proxy – Sniffer – • • Evaluation Limitations 2

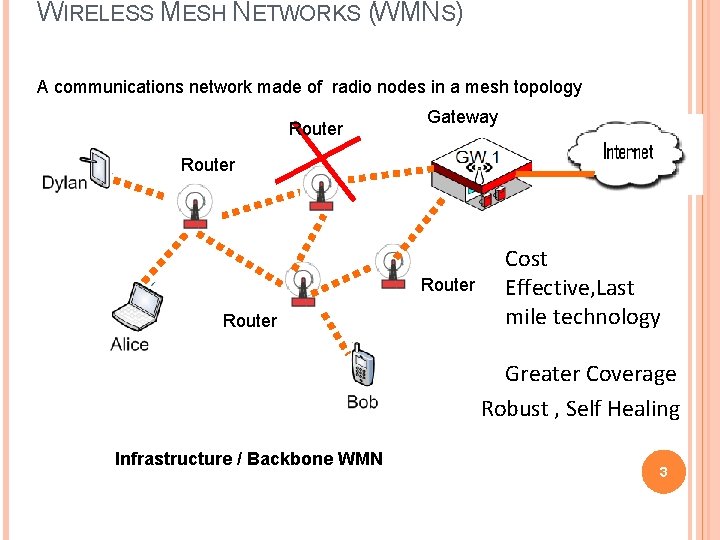
WIRELESS MESH NETWORKS (WMNS) A communications network made of radio nodes in a mesh topology Router Gateway Router Cost Effective, Last mile technology Greater Coverage Robust , Self Healing Infrastructure / Backbone WMN 3

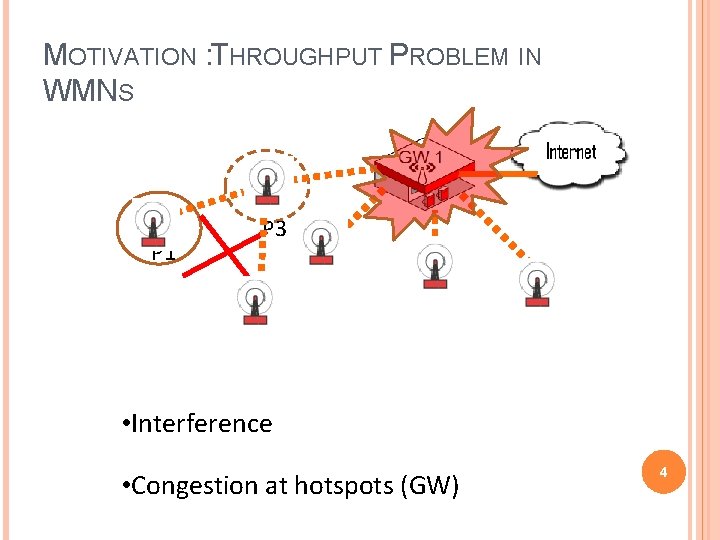
MOTIVATION : THROUGHPUT PROBLEM IN WMNS P 1 P 3 • Interference • Congestion at hotspots (GW) 4

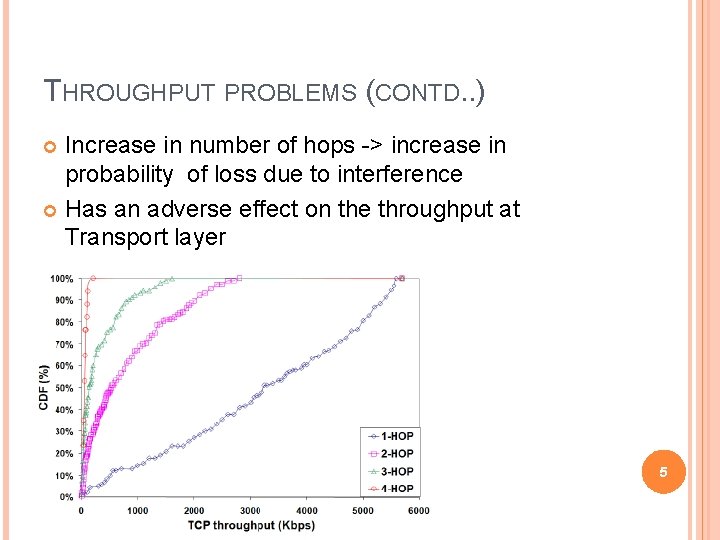
THROUGHPUT PROBLEMS (CONTD. . ) Increase in number of hops -> increase in probability of loss due to interference Has an adverse effect on the throughput at Transport layer 5
![HIERARCHICAL CACHING WEB CACHING TECHNIQUE Takes advantage of the similarity and locality of workload HIERARCHICAL CACHING [WEB CACHING TECHNIQUE] Takes advantage of the similarity and locality of workload.](https://slidetodoc.com/presentation_image/6a89e39cbc461bf743a2fc6f8ef2063f/image-6.jpg)
HIERARCHICAL CACHING [WEB CACHING TECHNIQUE] Takes advantage of the similarity and locality of workload. Ser ver National Cache Regional Cache Institutional Cache Bottom(Local Cache) Disadvantages 1) Application specific 2) Need to cache the whole files. 6

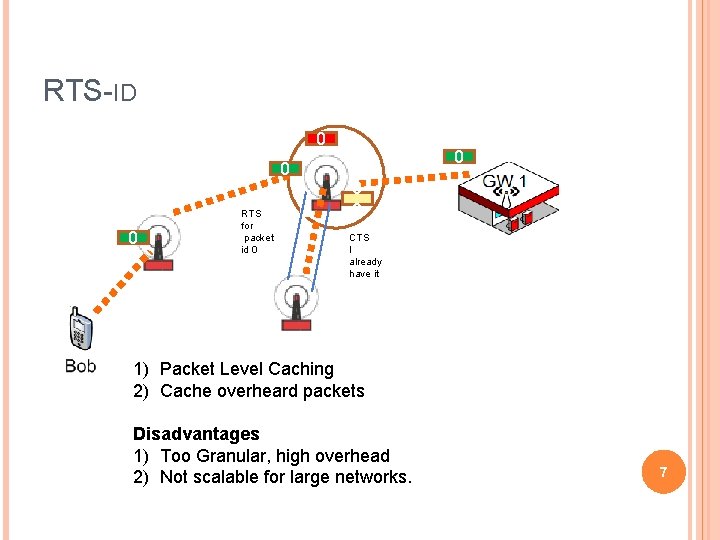
RTS-ID 0 0 0 RTS for packet id 0 0 CTS I already have it 1) Packet Level Caching 2) Cache overheard packets Disadvantages 1) Too Granular, high overhead 2) Not scalable for large networks. 7

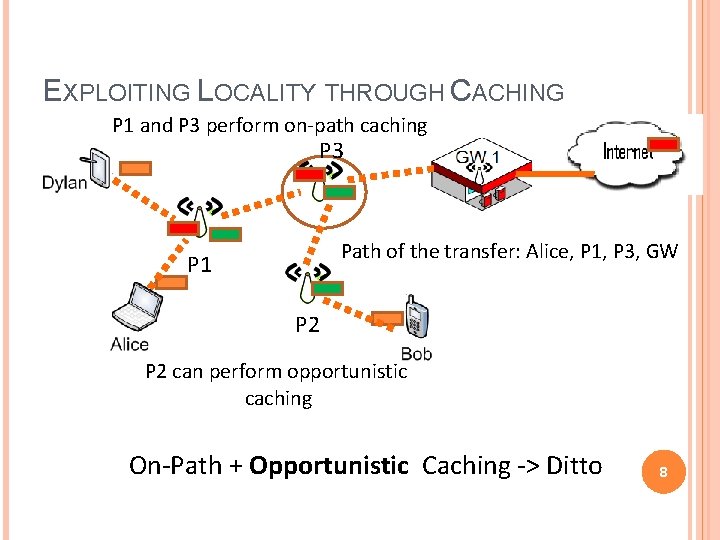
EXPLOITING LOCALITY THROUGH CACHING P 1 and P 3 perform on-path caching P 3 Path of the transfer: Alice, P 1, P 3, GW P 1 P 2 can perform opportunistic caching On-Path + Opportunistic Caching -> Ditto 8

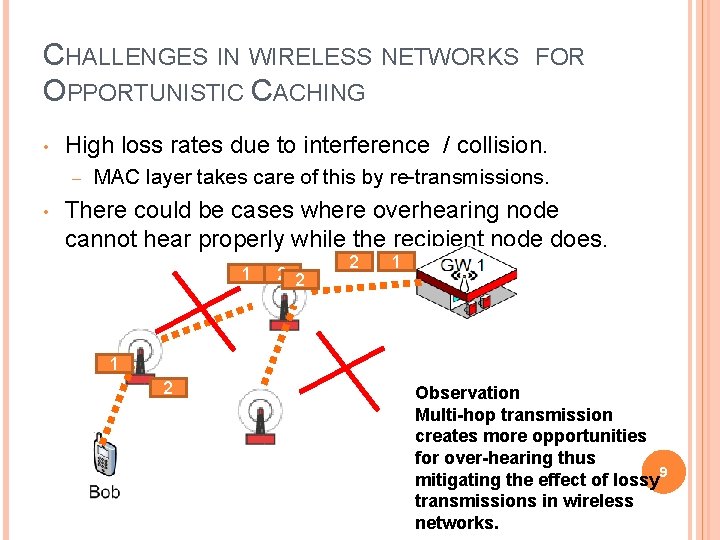
CHALLENGES IN WIRELESS NETWORKS OPPORTUNISTIC CACHING • High loss rates due to interference / collision. – • FOR MAC layer takes care of this by re-transmissions. There could be cases where overhearing node cannot hear properly while the recipient node does. 1 12 2 2 1 1 2 Observation Multi-hop transmission creates more opportunities for over-hearing thus mitigating the effect of lossy 9 transmissions in wireless networks.

DITTO : KEY POINTS Based on Opportunistic caching and exploits the broadcast nature of wireless networks. “Chunk based” caching Application independent. Exploits re-transmissions for advantage. 10

FILE TRANSFER MECHANISM IN DITTO Ditto uses “Data Oriented Transfer” Factors needed to be considered while devising an efficient file transfer mechanism: 1) Packet level caching is too granular. Incurs a lot of overhead for re-assembly. 2) File-level caching is also not efficient as overhearing a complete file is less probable. Solution: Divide file into smaller units called “Chunks”[8 – 32 kb] Use chunks as data transfer units. Use the hash value of contents to identify the chunk. 11

ADVANTAGES OF DOT Fairly good probability of overhearing, easy to Reassemble Application independent : uses Rabin fingerprinting to mark boundary regions for splitting files into chunks. Increases the probability of finding identical chunks in similar files. Self verifying mechanism as chunks are named using the hash value of their contents. 12

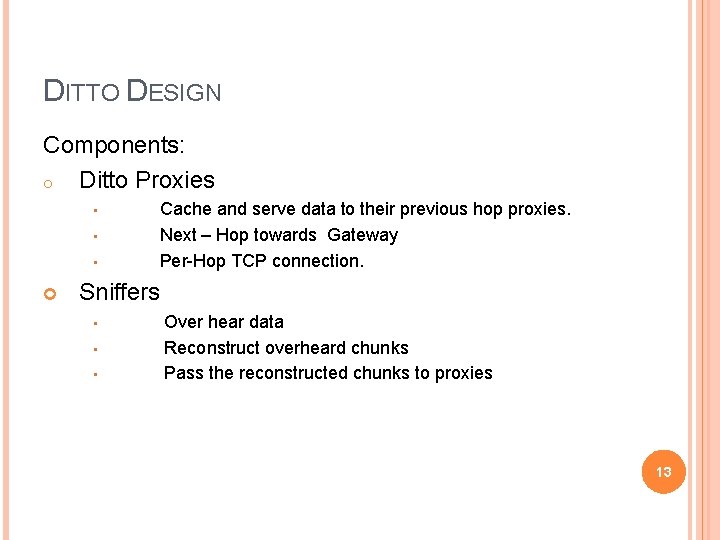
DITTO DESIGN Components: o Ditto Proxies • • • Cache and serve data to their previous hop proxies. Next – Hop towards Gateway Per-Hop TCP connection. Sniffers • • • Over hear data Reconstruct overheard chunks Pass the reconstructed chunks to proxies 13

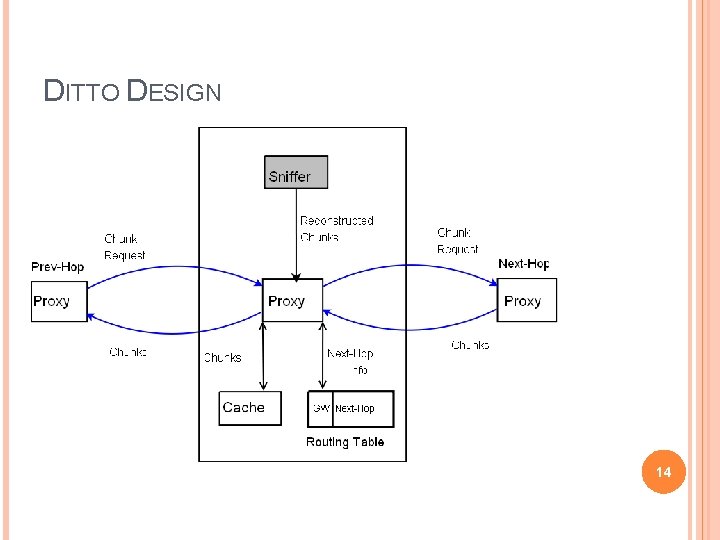
DITTO DESIGN 14

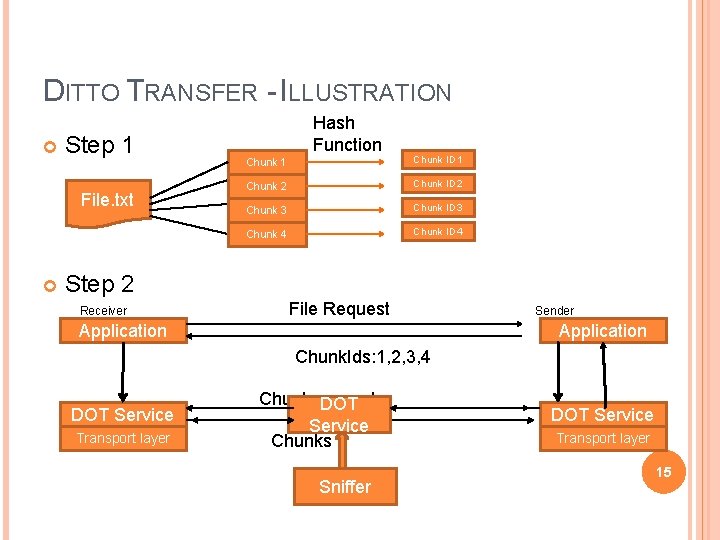
DITTO TRANSFER - ILLUSTRATION Step 1 File. txt Hash Function Chunk 1 Chunk ID 1 Chunk 2 Chunk ID 2 Chunk 3 Chunk ID 3 Chunk 4 Chunk ID 4 Step 2 Receiver File Request Application Sender Application Chunk. Ids: 1, 2, 3, 4 DOT Service Transport layer Chunk request DOT Service Chunks Sniffer DOT Service Transport layer 15

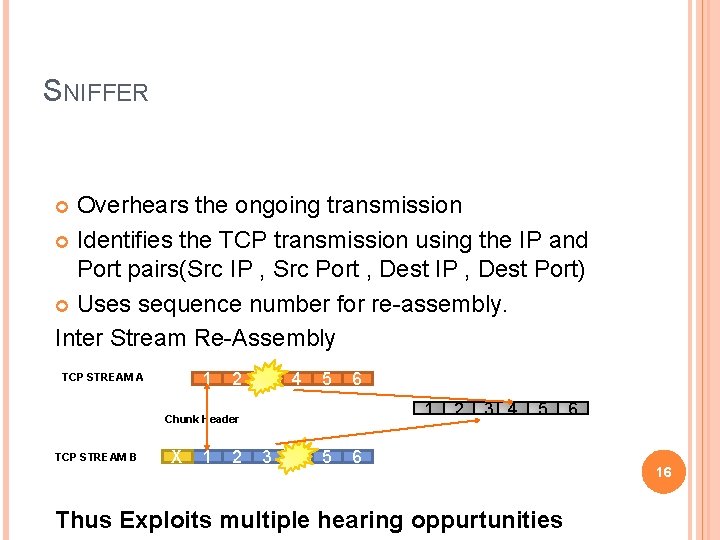
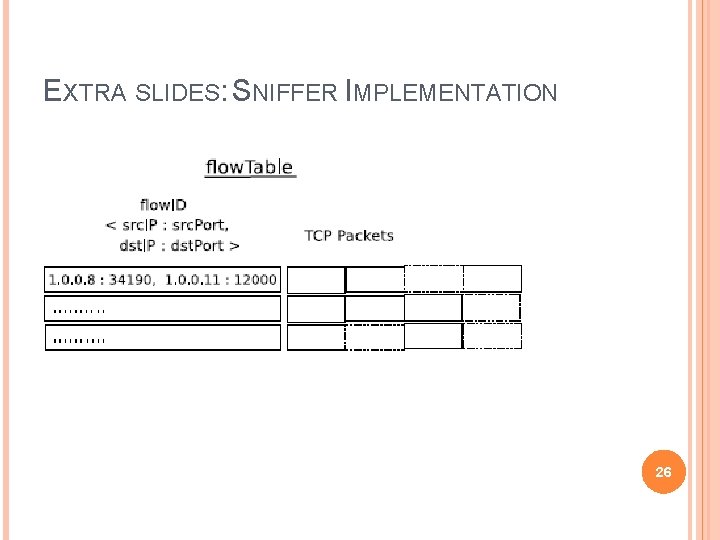
SNIFFER Overhears the ongoing transmission Identifies the TCP transmission using the IP and Port pairs(Src IP , Src Port , Dest IP , Dest Port) Uses sequence number for re-assembly. Inter Stream Re-Assembly 1 TCP STREAM A 2 4 5 6 1 Chunk Header TCP STREAM B X 1 2 3 5 2 3 4 5 6 Thus Exploits multiple hearing oppurtunities 6 16

EMULAB WIRELESS TESTBED Gate way 17

EXPERIMENTAL SETUP Wireless Network used : 802. 11 b File Sizes : 1 - 5 MB Chunk Sizes – 8 KB, 16 KB, 32 KB 18

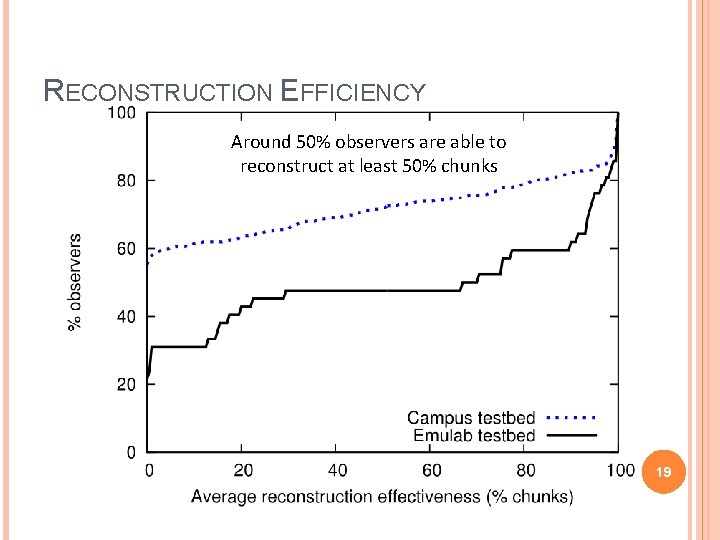
RECONSTRUCTION EFFICIENCY Around 50% observers are able to reconstruct at least 50% chunks 19

THROUGHPUT EVALUATION Leaf Nodes request the same file from the gateway � e. g: software update on all nodes Different request patterns: Sequential, staggered � Random order of receivers � Schemes � Ditto’s comparison with On-Path and E 2 E 20

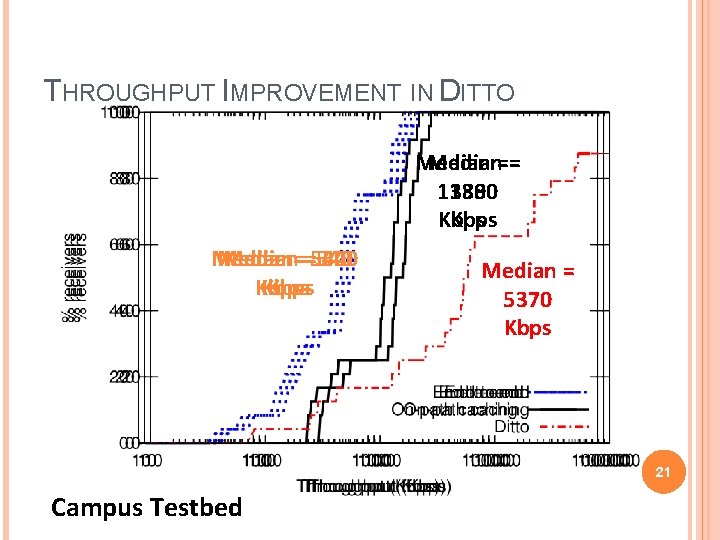
THROUGHPUT IMPROVEMENT IN DITTO Median== 1380 Kbps Median===540 Median 540 Kbps Median = 5370 Kbps 21 Campus Testbed

RESULTS (CONTD) Effect Of Chunk Size - As noted earlier , smaller chunk size implies better reconstruction efficiency. - Results show that with 8 Kb chunk size 20 % of observers were able to reconstruct 80% of chunks. With 32 Kb chunk size , this reduces to 60 %. Effect of Inter Stream Re-assembly 10 % improvement over without inter-stream reassembly. 22

EVALUATION RESULTS / CONCLUSION Hotspot formation near gateways avoided as nodes near gateway have high overhearing effectiveness. A choice 8 -32 KB of chunk size gives a good reconstruction efficiency. Significant throughput improvement – up to 7 X compared to On Path and 10 X compared to no caching At points where-ever inter stream assembly by overhearing was possible there was an improvement of 10% in reconstruction efficiency 23

LIMITATIONS OF THE APPROACH Ditto requires that a TCP connection between each proxy , if there are multiple Transport layer timeouts it would severely affect the performance. (It is quite possible in a wireless environment). While fetching a file , a lookup is made at each proxy which results in considerable delay if there are many proxies on the path [especially if the file chunks are not present in any of the proxies]. The method is not energy efficient , overhearing results in a lot of energy wastage. If Encapsulated packets are used as in secure tunnels, it would be complex to perform inter stream re-assembly (as all packets are addressed to the same destination – which is the secure gateway). 24
Th nk You Q? 25

EXTRA SLIDES: SNIFFER IMPLEMENTATION 26

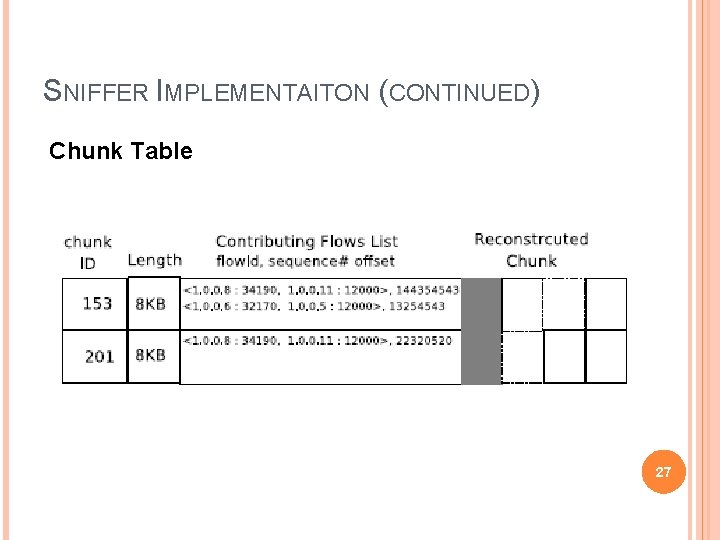
SNIFFER IMPLEMENTAITON (CONTINUED) Chunk Table 27

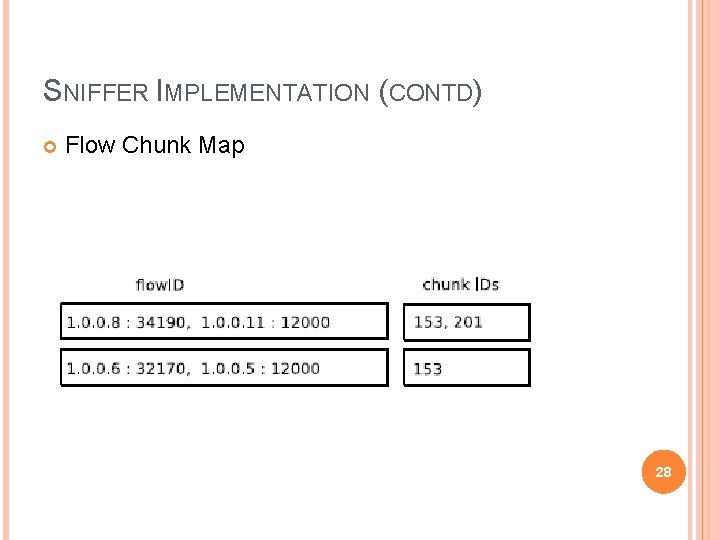
SNIFFER IMPLEMENTATION (CONTD) Flow Chunk Map 28