DDOS attacks in an IPv 6 World Tom














- Slides: 42

DDOS attacks in an IPv 6 World Tom Paseka HKNOG 1. 0 September 2014

Who are we? 2

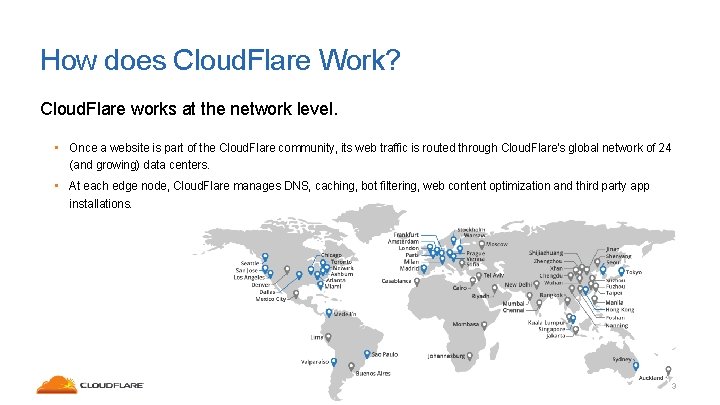
How does Cloud. Flare Work? Cloud. Flare works at the network level. • Once a website is part of the Cloud. Flare community, its web traffic is routed through Cloud. Flare’s global network of 24 (and growing) data centers. • At each edge node, Cloud. Flare manages DNS, caching, bot filtering, web content optimization and third party app installations. 3

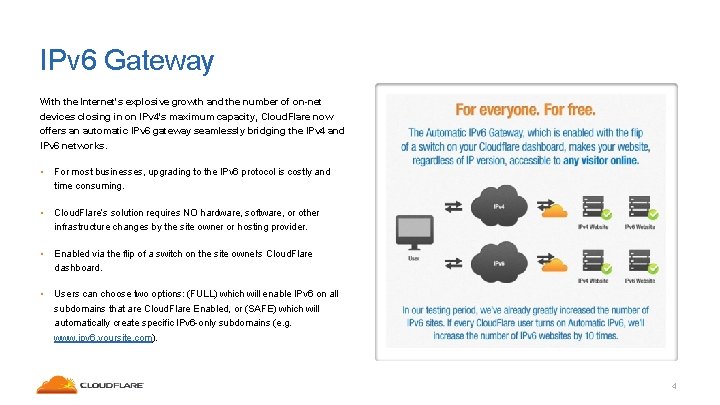
IPv 6 Gateway With the Internet's explosive growth and the number of on-net devices closing in on IPv 4's maximum capacity, Cloud. Flare now offers an automatic IPv 6 gateway seamlessly bridging the IPv 4 and IPv 6 networks. • For most businesses, upgrading to the IPv 6 protocol is costly and time consuming. • Cloud. Flare’s solution requires NO hardware, software, or other infrastructure changes by the site owner or hosting provider. • Enabled via the flip of a switch on the site owner’s Cloud. Flare dashboard. • Users can choose two options: (FULL) which will enable IPv 6 on all subdomains that are Cloud. Flare Enabled, or (SAFE) which will automatically create specific IPv 6 -only subdomains (e. g. www. ipv 6. yoursite. com). 4

DDo. S Overview

DDo. S Overview • Purpose of a DDo. S is to overwhelm an internet resource, to take it offline • This can be: • Volumetric (eg. High Gbps, High PPS or SYN Flooding). To overwhelm infrastructure to the website / resource. SYN floods overwhelm the • Application based (eg. Excessive HTTP POST or search) To overwhelm the application or server. • A website suddenly becoming very popular can also be like a DDOS

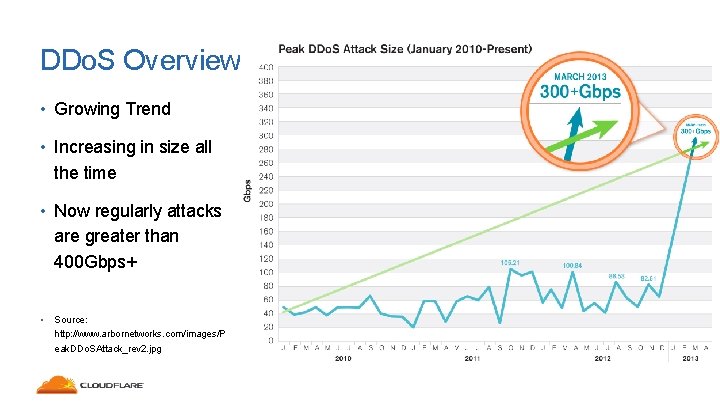
DDo. S Overview • Growing Trend • Increasing in size all the time • Now regularly attacks are greater than 400 Gbps+ • Source: http: //www. arbornetworks. com/images/P eak. DDo. SAttack_rev 2. jpg

DDo. S Overview • Large scale DDo. S is a common occurrence. • Used for exploitation, even for relatively low amounts (US$500 and below). • Online services available for purchase of DDo. S • Known as ‘Booters’ • Large purpose is to kick competitors off online-games so they forfeit the game • Free trails are often available for ‘Booters’ too!

So, what’s this got to do with IPv 6?

So, what’s this got to do with IPv 6? Nothing?

So, what’s this got to do with IPv 6? Or maybe a lot?

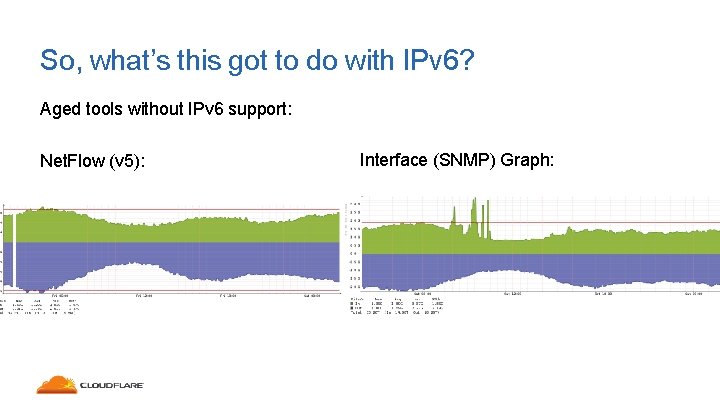
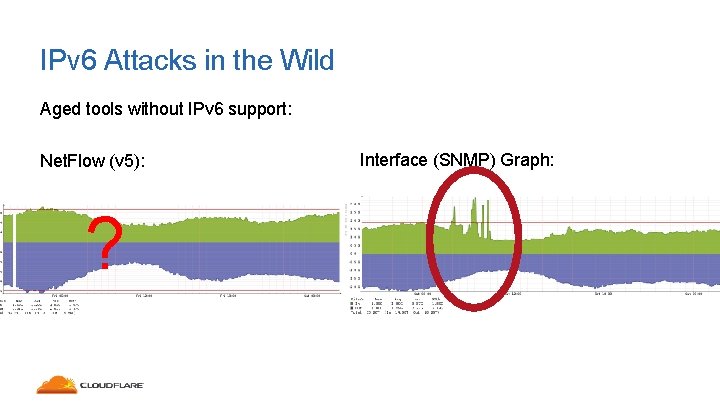
So, what’s this got to do with IPv 6? Aged tools without IPv 6 support: Net. Flow (v 5): Interface (SNMP) Graph:

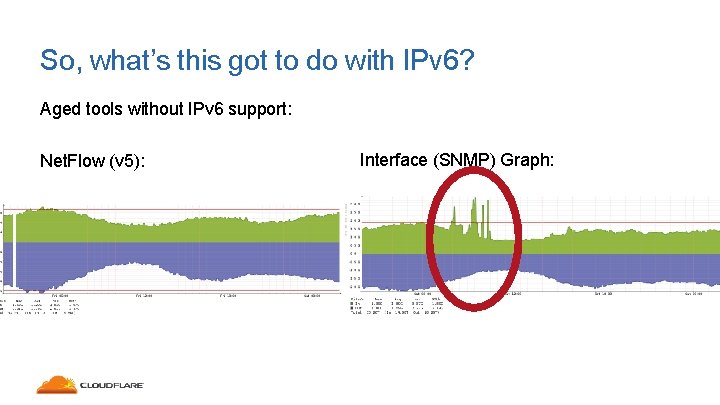
So, what’s this got to do with IPv 6? Aged tools without IPv 6 support: Net. Flow (v 5): Interface (SNMP) Graph:

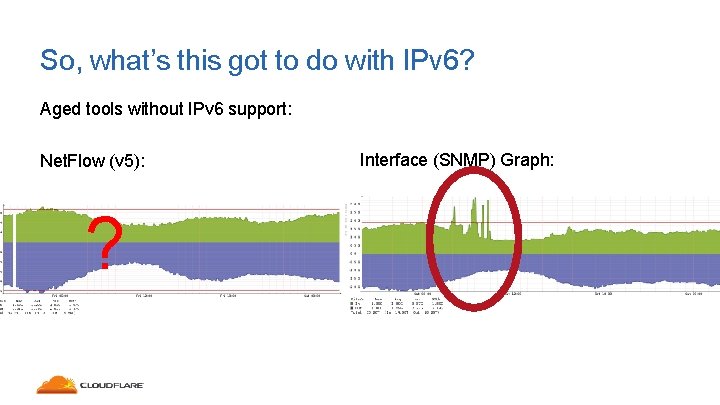
So, what’s this got to do with IPv 6? Aged tools without IPv 6 support: Net. Flow (v 5): ? Interface (SNMP) Graph:

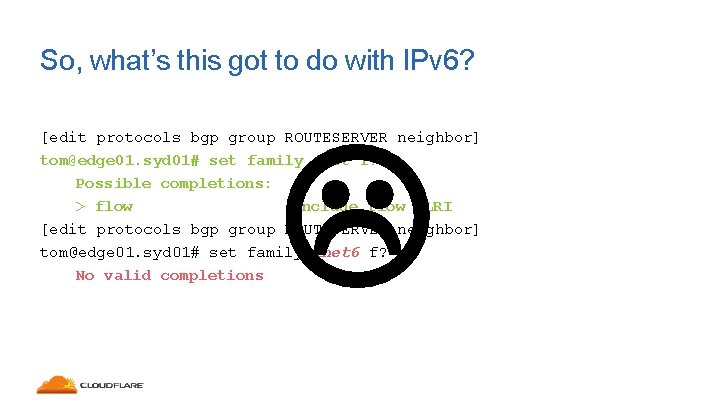
So, what’s this got to do with IPv 6? [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet f? Possible completions: > flow Include flow NLRI [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet 6 f? No valid completions

So, what’s this got to do with IPv 6? [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet f? Possible completions: > flow Include flow NLRI [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet 6 f? No valid completions

So, what’s this got to do with IPv 6? [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet f? Possible completions: > flow Include flow NLRI [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet 6 f? No valid completions

So, what’s this got to do with IPv 6? [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet f? Possible completions: > flow Include flow NLRI [edit protocols bgp group ROUTESERVER neighbor] tom@edge 01. syd 01# set family inet 6 f? No valid completions

So, what’s this got to do with IPv 6? • Without supporting systems, many things may be impeded: • Ability to identify attacks: No Net. Flow data? • Ability to filter the attacks: IP Tables support? (ip 6 tables) IP ACL / Access-lists BGP Flow. Spec Remotely Triggered Black Holing

So, what’s this got to do with IPv 6? • So, is this IPv 6’s fault? • Looking at the vendors in the room. • Why is any product released without FULL IPv 6 support today.

So, what’s this got to do with IPv 6? • A lot of IPv 6 deployments feel like “best effort” • Best effort doesn’t cut it under big attacks and with security • We all still have a long way to come.

IPv 6 Attacks in the Wild

IPv 6 Attacks in the Wild • For the most part, in our experience, they’re the same as IPv 4 based attacks. • Typically, attack scope is smaller, due to much smaller number of IPv 6 hosts on the internet • Not true for all attacks

IPv 6 Attacks in the Wild • DNS cache-busted query attacks. • Not only a IPv 6 attack, but interesting because of how it came in over IPv 6. • Botnet bots, query through their normal configured recursors, using random strings which aren’t cachable

IPv 6 Attacks in the Wild Queries look like this: ebepexklyfaxmloh. www. popvote. hk ktylstudkr. www. popvote. hk ohunarajmbkrej. www. popvote. hk wwtdheilzcv. www. popvote. hk zktvvotoyrewaku. www. popvote. hk ……. khyhavsnijslyb. www. popvote. hk gchjpexychflvfv. api-token. popvote. hk ruqnpvp. api-token. popvote. hk fapzefvgowzonss. api-token. popvote. hk mcvhothfketpgre. api-token. popvote. hk

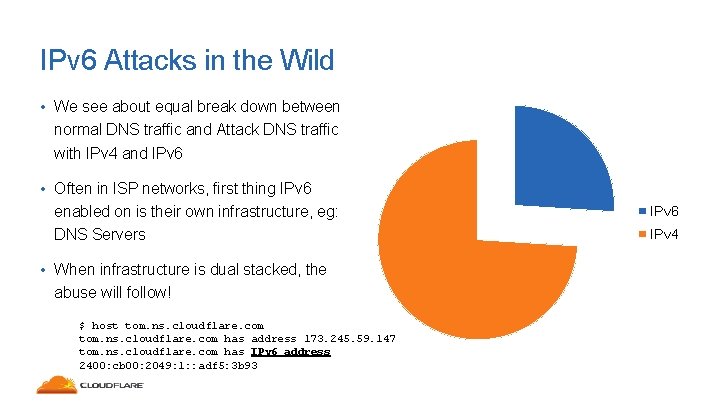
IPv 6 Attacks in the Wild • We see about equal break down between normal DNS traffic and Attack DNS traffic with IPv 4 and IPv 6 • Often in ISP networks, first thing IPv 6 enabled on is their own infrastructure, eg: DNS Servers • When infrastructure is dual stacked, the abuse will follow! $ host tom. ns. cloudflare. com has address 173. 245. 59. 147 tom. ns. cloudflare. com has IPv 6 address 2400: cb 00: 2049: 1: : adf 5: 3 b 93 IPv 6 IPv 4

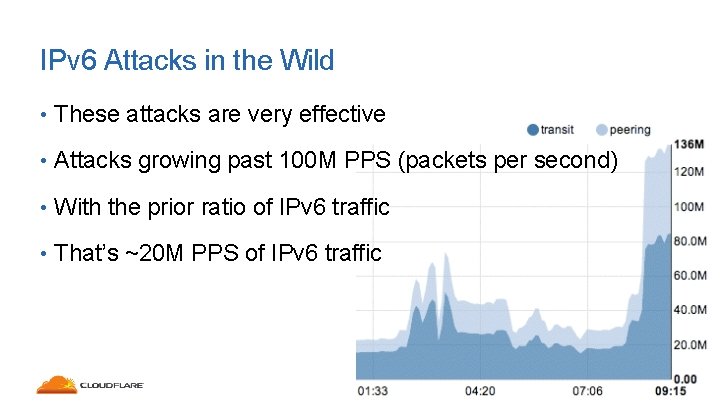
IPv 6 Attacks in the Wild • These attacks are very effective • Attacks growing past 100 M PPS (packets per second) • With the prior ratio of IPv 6 traffic • That’s ~20 M PPS of IPv 6 traffic

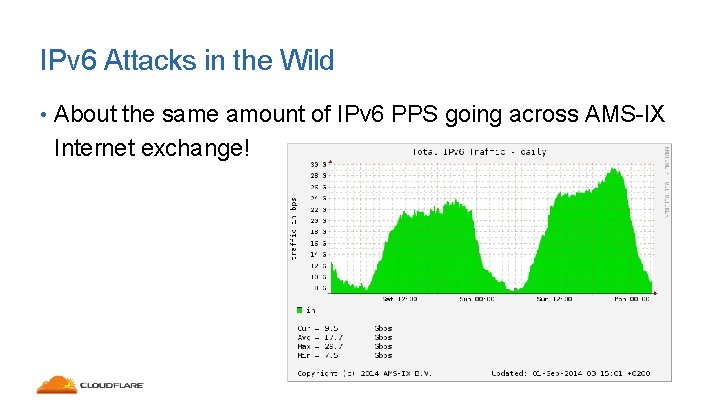
IPv 6 Attacks in the Wild • About the same amount of IPv 6 PPS going across AMS-IX Internet exchange!

IPv 6 Attacks in the Wild • IPv 6 SYN Floods (and other flooding based attacks) • Botnet send commands/attacks to direct traffic towards a hostname, eg: example. com $ host example. com has address 93. 184. 216. 119 example. com has IPv 6 address 2606: 2800: 220: 6 d: 26 bf: 1447: 1097: aa 7

IPv 6 Attacks in the Wild • Botnet master may not be intentional to send traffic towards IPv 6 hosts • But bots inside the botnet see the AAAA and send traffic that way • IPv 6 preferred selection.

IPv 6 Attacks in the Wild Aged tools without IPv 6 support: Net. Flow (v 5): ? Interface (SNMP) Graph:

IPv 6 Attacks in the Wild Is all of this interesting?

IPv 6 Attacks in the Wild • Show’s IPv 6 adoption is growing, not just in users networks, but other parts of the internet. • Expands scope of where IPv 6 attacks can come in • Helps change the IPv 4 only mindset

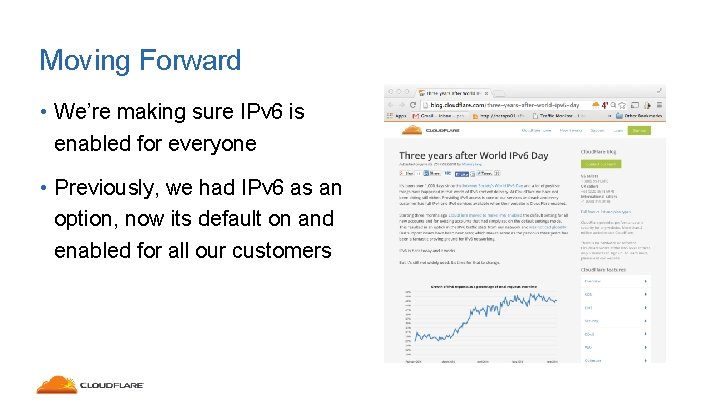
Moving Forward

Moving Forward

Moving Forward • We’re making sure IPv 6 is enabled for everyone • Previously, we had IPv 6 as an option, now its default on and enabled for all our customers

Moving Forward

Moving Forward • This is just the tip of the iceberg • Nothing over IPv 6 has been that unique yet • Most attacks are still directed at an IP (IPv 4) Address • Most sophisticated are still IPv 4 only • Who knows what is coming next?

Moving Forward • Unless we can see what’s happening now • We can’t know what to expect going forward • Except that if you’re not prepared with the same principles in IPv 4 security, IPv 6 will byte you. • Once you’ve reached equality in IPv 4 and IPv 6, the issues of IPv 4 v. IPv 6 in attacks is moot.

Questions?

Thank You!
