CS 3043 Social Implications Of Computing Class 8








































- Slides: 53

CS 3043 Social Implications Of Computing Class 8 Privacy Keith A. Pray Instructor socialimps. keithpray. net 10/29/2020 © 2013 Keith A. Pray 1

CS 3043 Social Implications Of Computing Overview 1. 2. 3. Privacy Assignment Students Present 10/29/2020 © 2013 Keith A. Pray 2

CS 3043 Social Implications Of Computing Survey Feedback n Class Slides ¨ Posted online in Power Point and Web Pages eg. n n Paper Grading ¨ n http: //socialimps. keithpray. net/documents/class-slides/07_Privacy/ I believe quality of feedback improving, Improving paper quality, Dropping Lowest Grade, Scaling, Re-Writes Class Discussion Majority of comments positive, for the rest: ¨ Respect everyone’s opinion and interests are important ¨ Participate more, Student Presentations ¨ n Assignment Explanations (Requests for broader and narrower topics) ¨ n n We’ll reserve more class time, Take simple view, Ask questions in class and email Quizzes (Equal number of likes and dis-likes) Top You Can Do’s Read early and more, Ask more questions, Start assignments earlier, Better research, Extra credit, Prepare questions for class, Participate © 2013 Keith A. Pray 10/29/2020 more ¨ 3

CS 3043 Social Implications Of Computing 10/29/2020 © 2013 Keith A. Pray 4

CS 3043 Social Implications Of Computing Quiz List two problems with using biometrics for identification. (1 point) 2. List two advantages of using biometrics for identification. (1 point) 3. Describe two tools people can use to protect their privacy on the Web. (1 point) 4. For Daniel Solove’s taxonomy of privacy give an example not listed in the book of 3 of the 4 categories. (3 points) Give example for all 4 for a bonus point. © 2013 Keith A. Pray 10/29/2020 1. 5

CS 3043 Social Implications Of Computing Overview 1. 2. 3. Privacy Assignment Students Present 10/29/2020 © 2013 Keith A. Pray 6

CS 3043 Social Implications Of Computing Assignment n One Page paper: ¨ Will eliminating anonymity make computers more secure? ¨ Sources could include legislation not covered in your text concerning computer related crimes. 10/29/2020 © 2013 Keith A. Pray 7

CS 3043 Social Implications Of Computing Overview 1. 2. 3. Privacy Assignment Students Present 10/29/2020 © 2013 Keith A. Pray 8

CS 3043 Social Implications Of Computing Jeremy Ridoré Is The Government Watching Me? n With the devices we carry on us everyday, how easy it is for the government to “snoop” on us? http: //www. att. com/wireless/iphone/assets/iphone-big. jpg, http: //nexus 404. com/Blog/wpcontent/uploads 2/2008/07/bic-disposable-cell-phone. jpg, http: //www. aim. org/wp-content/uploads/2012/12/tivo. jpg, http: //png-2. findicons. com/files/icons/1773/free/256/laptop_grey. png 10/29/2020 © 2013 Keith A. Pray 9

CS 3043 Social Implications Of Computing Jeremy Ridoré Can They Really Do That? Movie In Movie Real Life? Transformer Hacked phone camera Yes. The s 3 for live feed. Fin. Fisher Trojan. Enemy of The State Bird’s eye view Yes. Spy tracking with satellite. Satellites. Bad Boys 2 Planted numerous wire tapping bugs to listen in on the Cuban drug cartel boss. Yes. Warrantless wiretapping cases have been a continuous issue in court. http: //www. filmofilia. com/wp-content/uploads/2010/12/transformers 3_poster. jpg, http: //upload. wikimedia. org/wikipedia/en/thumb/7/75/Enemy_of_the_State. jpg/220 px -Enemy_of_the_State. jpg, http: //www. englishmoviez. com/wpcontent/uploads/2012/03/bad_boys_2. jpg 10/29/2020 © 2013 Keith A. Pray 10

CS 3043 Social Implications Of Computing Jeremy Ridoré How Private Is Your room? n Multiple laptops in a college dorm room ¨ n Tap into laptop microphone ¨ n At more of a risk 2006, Google planned to spy on internet users with PC microphone to create advertisement profiles Ti. Vo http: //www. aim. org/wp-content/uploads/2012/12/tivo. jpg , http: //www. soundprofessionals. com/mas_assets/full/SP-USB-LAPTOPMICROPHONE. jpg 10/29/2020 © 2013 Keith A. Pray 11

CS 3043 Social Implications Of Computing Jeremy Ridoré Cell Phone: Best Friend and Worst Enemy n How many i. Phone/i. Pad users? Month after i. Phone release a technology group in Russia released the results of their attempts to reverse engineer the i. Phone ¨ Antisec found a file called NCFTA_i. OS_devices_intel. csv, which is a list of the 12, 367, 232 Apple i. OS devices and related personal details ¨ http: //www. att. com/wireless/iphone/assets/iphone-big. jpg, http: //images. apple. com/ipad/compare/images/compare_hero_ipad_retina. jpg 10/29/2020 © 2013 Keith A. Pray 12

CS 3043 Social Implications Of Computing Jeremy Ridoré Cell Phone: Best Friend and Worst Enemy n Foot. Path Technology Tracking System ¨ n Was used Black Friday 2011 in 2 shopping malls Drug Enforcement Agency tracked marijuana courier, Melvin Skinner, disposable cell phone as he moved his cargo from Arizona to Tennessee http: //nexus 404. com/Blog/wp-content/uploads 2/2008/07/bic-disposable-cell-phone. jpg 10/29/2020 © 2013 Keith A. Pray 13

CS 3043 Social Implications Of Computing Jeremy Ridoré Why Can They Do This? n “Law enforcement can get months’ worth of this information, without you ever knowing – and often without a warrant from a judge. ” 1 ¨ n Breaking the 4 th amendment. Law on privacy and technology is outdated. [1] http: //www. aclu. org/government-location-tracking-cell-phones-gps-devices-andlicense-plate-readers, http: //images. sodahead. com/polls/003450689/3931694857_6 a 01053596 fb 28970 c 01116 8 c 9 e 35 e 970 c_pi_xlarge. jpeg 10/29/2020 © 2013 Keith A. Pray 14

CS 3043 Social Implications Of Computing Jeremy Ridoré Summary n n n Government is watching! Your computer has ears! If you have an i. Phone, the FBI is watching you! The Government can get any information they want, without letting you know. If you’re trafficking drugs, don’t bring your phone! 10/29/2020 © 2013 Keith A. Pray 15

CS 3043 Social Implications Of Computing Jeremy Ridoré Sources n n n n http: //www. cultofmac. com/132782/if-you-thought-carrier-iq-scandal -was-bad-wait-till-you-see-latest-wikileaks/ http: //www. spybusters. com/government_taps. html http: //rt. com/usa/supreme-fisa-wiretap-aclu-599/ http: //www. aclu. org/blog/national-security/warrantless-wiretappingwins-again http: //www. theregister. co. uk/2006/09/03/google_eavesdropping_sof tware/ http: //www. aclu. org/government-location-tracking-cell-phones-gpsdevices-and-license-plate-readers All accessed April 2, 2013 10/29/2020 © 2013 Keith A. Pray 16

CS 3043 Social Implications Of Computing Jeremy Ridoré Sources n n n http: //www. motherjones. com/mojo/2012/08/court-warrant-cellphone-gpsdata http: //endoftheamericandream. com/archives/cell-phones-are-trackingdevices-that-governments-police-big-corporations-and-stalkers-can-use-toeasily-track-your-movements http: //www. infosecurity-magazine. com/view/27972/hackers-claim-fbi-istracking-iphone-users/ http: //www. theblaze. com/stories/2012/10/11/apple-allows-tracking-ofiphone-users-again-and-buries-opt-out-function/ http: //www. prisonplanet. com/articles/july 2007/200707 iphonesurveillance. h tm All accessed April 2, 2013 10/29/2020 © 2013 Keith A. Pray 17

CS 3043 Social Implications Of Computing Neil Pomerleau The Panoptic Effect n Consequence of surveillance ¨ n We unintentionally adjust our behavior when we believe we are being watched. Named for Jeremy Bentham’s “Panopticon” [1] Bentham, Jeremy, The Panopticon Writings (Verso, 1995), 29 -95 10/29/2020 © 2012 Keith A. Pray 18

CS 3043 Social Implications Of Computing Neil Pomerleau The “Panopticon” Prison Image: http: //www. digitalcrossrhodes. com/wp-content/uploads/2009/09/Presidio-modelo 2. JPG (April 4, 2013) 10/29/2020 © 2012 Keith A. Pray 19

CS 3043 Social Implications Of Computing Neil Pomerleau Facebook as a Panopticon n Observation is unverifiable ¨ n Possible to observe many others at once ¨ n Is someone looking at my profile? News feed shows activity of many users User behavior is adjusted ¨ We present a crafted version of ourselves [1] Jian Rui, Michael A. Stefanone, Strategic Self-Presentation Online, http: //www. sciencedirect. com/science/article/pii/ S 0747563212002257 (April 4, 2013) 10/29/2020 © 2012 Keith A. Pray 20

CS 3043 Social Implications Of Computing Neil Pomerleau MPAA/RIAA as Panopticons n Observation is unverifiable ¨ n Possible to observe many others at once ¨ n Are they monitoring my illegal torrent download? One anti-piracy node can connect to many peers User behavior is adjusted ¨ Perhaps I shouldn’t try pirating that movie? 10/29/2020 © 2012 Keith A. Pray 21

CS 3043 Social Implications Of Computing Neil Pomerleau Video Surveillance n The Ultimate Panopticon ¨ n n n Don’t even need a watchman! Many people can be monitored We believe we’re being watched Our behavior is controlled Image: http: //www. howtovanish. com/images/surveillance-cameras. jpg (April 4, 2013) 10/29/2020 © 2012 Keith A. Pray 22

CS 3043 Social Implications Of Computing Neil Pomerleau Ever Seen These? Left Image: http: //www. mysecuritysign. com/img/lg/K/Video-Camera-Security-Sign-K-1099. gif (April 4, 2013) Center Image: http: //www. techcctv. com/21458. jpg (April 4, 2013) Right Image: http: //www. flatvision. co. uk/blog/wp-content/uploads/Flatvision-FES-Pro-22 W-PVM-in-Mamas-Papas. Liverpool-ONE-007. jpg (April 4, 2013) 10/29/2020 © 2012 Keith A. Pray 23

CS 3043 Social Implications Of Computing Neil Pomerleau Changes in Behavior n Crime Reduction CCTV cameras reduced risk of vandalism, etc. [1] ¨ Traffic cameras slow down drivers [2] ¨ n Police Oversight ¨ Fewer complaints about police behavior [3] [1] CCTV puts off vandals, Coventry Evening Telegraph (September 7, 2006) [2] Greg Wendt, Fixed cameras slow traffic (Herald, August 15, 2002), 14 [3] Heather Mac. Donald, Cameras put Oakland police on best behavior (Oakland Tribune, November 11, 2004), 1 10/29/2020 © 2012 Keith A. Pray 24

CS 3043 Social Implications Of Computing Neil Pomerleau Discussion n Other examples of Panopticons? Ever experienced the “Panoptic effect”? Is video surveillance ethical? 10/29/2020 © 2012 Keith A. Pray 25

CS 3043 Social Implications Of Computing Kexin Shi Privacy and the Government of China has a whole sophisticated census system. n The privacy law is not fully established in China. n Summary n 4/5/13 © 2013 Keith A. Pray 26

CS 3043 Social Implications Of Computing Kexin Shi Antique http: //www. 96 hq. com/news/21458. html 4/5/13 © 2013 Keith A. Pray 27

CS 3043 Social Implications Of Computing Kexin Shi Census n Western Han Dynasty q q q 202 – 9 BC Emperor Ping of Han South County to book 12, 366, 470 families 57, 671, 401 people http: //www. 521 yy. com/lisi/html/%E 6%B 1%89%E 5%B 9%B 3%E 5%B 8%9 D. htm 4/5/13 © 2013 Keith A. Pray 28

CS 3043 Social Implications Of Computing Kexin Shi Census n n n Population Agriculture Pollution Source Research and Development Economy Basic Units ¨ Industry ¨ Service Industry ¨ 10/29/2020 © 2013 Keith A. Pray 29

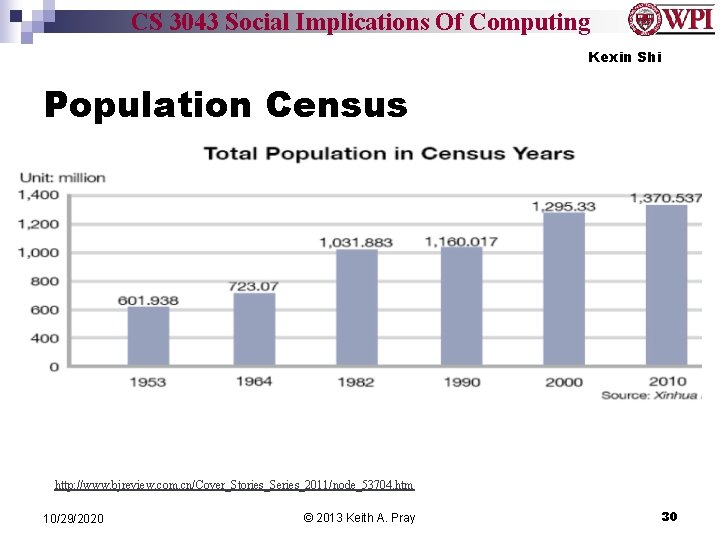
CS 3043 Social Implications Of Computing Kexin Shi Population Census http: //www. bjreview. com. cn/Cover_Stories_Series_2011/node_53704. htm 10/29/2020 © 2013 Keith A. Pray 30

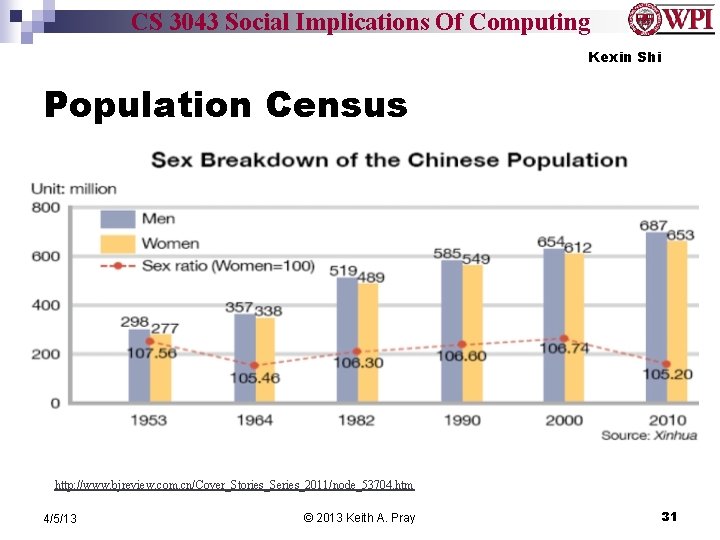
CS 3043 Social Implications Of Computing Kexin Shi Population Census http: //www. bjreview. com. cn/Cover_Stories_Series_2011/node_53704. htm 4/5/13 © 2013 Keith A. Pray 31

CS 3043 Social Implications Of Computing Kexin Shi Laws n n Constitution of the People’s Republic of China General Principles of the Civil Law of the People’s Republic of China None of them has mentioned about privacy. Why? 4/5/13 © 2013 Keith A. Pray 32

CS 3043 Social Implications Of Computing Kexin Shi Reason n Broad vs. Abstract http: //baike. baidu. com/picview/49910/0/43 e 6 c 733 c 0781 c 78 ac 4 b 5 f 0 d. html#albumindex=0&picindex=0 4/5/13 © 2013 Keith A. Pray 33

CS 3043 Social Implications Of Computing Kexin Shi Regulation n Computer Information Network and Internet Security, Protection and Management Regulations q “No unit or individual may, in violation of these regulations, use the Internet to violate the freedom and privacy of network users. ” 10/29/2020 © 2013 Keith A. Pray 34

CS 3043 Social Implications Of Computing Kexin Shi Regulation n Implementation Rules for Provisional Regulations of the Administration of International Networking of Computer Information in China q “Distributing malicious information, giving out information in other people’s names and violating others’ privacy through networks are forbidden. ” 4/5/13 © 2013 Keith A. Pray 35

CS 3043 Social Implications Of Computing Kexin Shi Regulation n Administration of Internet Electronic Messaging Services Provisions q Electronic Messaging Service providers shall maintain the confidentiality of the personal information concerning the online subscribers and may not disclose the same to third parties without the subscribers' consent, unless the law provides otherwise. 4/5/13 © 2013 Keith A. Pray 36

CS 3043 Social Implications Of Computing Kexin Shi Summary n n Regulation ≠ Law The unified concept of privacy has not fully formed, so the legislation, judiciary, and law enforcement need to find the balance to achieve the constant improvement of the privacy protection laws. 4/5/13 © 2013 Keith A. Pray 37

CS 3043 Social Implications Of Computing Kexin Shi Sources n n n http: //www. 96 hq. com/news/21458. html, July 1, 2011 Bielenstein, Hans. (1986). "Wang Mang, the Restoration of the Han Dynasty, and Later Han, " in The Cambridge History of China: Volume I: the Ch'in and Han Empires, 221 B. C. – A. D. 220. Edited by Denis Twitchett and Michael Loewe. Cambridge: Cambridge University Press. http: //www. 521 yy. com/lisi/html/%E 6%B 1%89%E 5%B 9%B 3%E 5%B 8%9 D. htm http: //www. stats. gov. cn/tjgb/rdpcgb/, October 25, 2012 http: //www. bjreview. com. cn/Cover_Stories_Series_2011/node_53704. htm http: //english. people. com. cn/constitution. html, December 4, 1982 http: //en. chinacourt. org/public/detail. php? id=2696, April 12, 1986 http: //baike. baidu. com/picview/49910/0/43 e 6 c 733 c 0781 c 78 ac 4 b 5 f 0 d. html#albumindex=0&picindex =0 http: //wenku. baidu. com/view/b 645 c 9956 bec 0975 f 465 e 20 d. html, August 11, 2011 http: //wenku. baidu. com/view/8 bf 6 e 4 f 904 a 1 b 0717 fd 5 dd 27. html, October 26, 2012 http: //www. rrting. com/res/sentence/law/provisional. htm http: //yy. china-b. com/hyfl/520622_5. html, May 4, 2008 4/5/13 © 2013 Keith A. Pray 38

CS 3043 Social Implications Of Computing Class 8 The End Keith A. Pray Instructor socialimps. keithpray. net 10/29/2020 © 2013 Keith A. Pray 39

CS 3043 Social Implications Of Computing My Reading Notes (4 th Edition) 5. 1 -5. 7 n n n n n pp. 221 Funny caption “…finishes Googling you” considering last chapter was on IP. pp. 222 Backwards: “You violate someone’s privacy when you treat him or her as a means to an end. ” pp. 224 “Taking away…privacy…moral capital…no means to develop personal relationships” 1984? pp. 224 ex-spouses only rate higher than potential rivals/enemies? pp. 233 Kantian should try considering non-secret monitoring as Rule Utilitarian did for a fair comparison. pp. 233 Last sentence, the nanny would not quit, the nanny would just not take the job in the first place. pp. 238 Calling in sick to go to ski resort not best example for arguing to protect privacy. pp. 238 How “new” is RFID? pp. 239 Is scanning for medical condition chip implants standard practice? pp. 240 Is Biometrics overkill for switching between different web browser profiles? pp. 240 Does spyware have to communicate over an internet connection? pp. 241 Shouldn’t credit card issuers take “reasonable steps” even without a fraud alert? pp. 241 Year of the Family Education Rights and Privacy Act? pp. 242 Video Privacy, why not cover all media? Any previous attempts to enact such a law before Bork? pp. 243 Genetic Information Nondiscrimination Act of 2008, when did Gattaca come out? pp. 245 What was the result of claims against H&R Block? pp. 246 NCIC privacy violations, how do first 2 bullets apply? pp. 247 One. DOJ, did they finish constructing it yet? pp. 249 filing a tax return is voluntary, awesome! 10/29/2020 © 2013 Keith A. Pray 40

CS 3043 Social Implications Of Computing My Reading Notes (4 th Edition) 5. 8 -5. 11 n n n n pp. 256 Did Vo. IP etc. modify systems so they could be “wiretapped” ? pp. 259 Does 191 out of 361 seem like a good conviction rate? How does this compare to other crimes? pp. 260 “…a few innocent bystanders…” 47% Upper bound from previous pp. more than a few. pp. 267 Identity theft = Misuse of another’s identity. How does one correctly use another’s identity? pp. 271 How does 4 follow from statement? Fallacy? pp. 273 Is the premise in 2 nd paragraph a fallacy? pp. 276 Will decryption times change given distributed computing, bot networks, quantum computers, etc. ? pp. 281 Was it decided people do not have a natural right to privacy? 10/29/2020 © 2013 Keith A. Pray 41

CS 3043 Social Implications Of Computing A Privacy Quote n “The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized. ” ¨ -- Fourth Amendment to the US Constitution 10/29/2020 © 2013 Keith A. Pray 42

CS 3043 Social Implications Of Computing Privacy n n Why do people want it? Keep private from whom? Is there any benefit in not having this stuff private? Who wants to know? 10/29/2020 © 2013 Keith A. Pray 43

CS 3043 Social Implications Of Computing Privacy n n Lots of things people would like to keep secret. Lots of people and organizations who would like to find out. Lots of things that could be done with the information. Correlations can be important. ¨ Beyond secrecy. 10/29/2020 © 2013 Keith A. Pray 44

CS 3043 Social Implications Of Computing Privacy n Expectations of privacy are: Cultural ¨ Philosophical ¨ Political ¨ Personal ¨ n Who has the right to know? 10/29/2020 © 2013 Keith A. Pray 45

CS 3043 Social Implications Of Computing Government n n What kinds of info should a government legitimately have about its citizens or others? What kinds of info should a government not have? What good things (for society) could a government do with info? What bad things could a government do? 10/29/2020 © 2013 Keith A. Pray 46

CS 3043 Social Implications Of Computing What Safeguards Are There? n In US: Census ¨ Taxes ¨ Federal n Local n Search warrants ¨ Wiretaps ¨ Inter-agency sharing ¨ 10/29/2020 © 2013 Keith A. Pray 47

CS 3043 Social Implications Of Computing Other Factors n n n Police: outstanding warrants Combos: child support /driver’s license Immigration Public health Security of Information 10/29/2020 © 2013 Keith A. Pray 48

CS 3043 Social Implications Of Computing Other Factors II n n n n Surveillance Freedom of association Anonymity? Newsgroups, email, snail mail, posters & flyers, ads. Criminal background Sexual harassment Discrimination Gun registration 10/29/2020 © 2013 Keith A. Pray 49

CS 3043 Social Implications Of Computing Companies n n What kinds of info should a company legitimately have about its customers, employees, or others? What kinds of info should a company not have? What good things (for society) could a company do with info? What bad things could a company do? 10/29/2020 © 2013 Keith A. Pray 50

CS 3043 Social Implications Of Computing Safeguards n Privacy policies ¨ n n Special for children Sharing within / between companies Right to correct / comment Privacy in the workplace Surveillance of employees & customers 10/29/2020 © 2013 Keith A. Pray 51

CS 3043 Social Implications Of Computing Other Business Things n n Bankruptcy Fraud 10/29/2020 © 2013 Keith A. Pray 52

CS 3043 Social Implications Of Computing Technology n n Overall computer security Encryption 10/29/2020 © 2013 Keith A. Pray 53