Computer Networks and the Internet Sorin Adam Matei





























- Slides: 63

Computer Networks and the Internet Sorin Adam Matei Purdue University Covers multiple lectures 1

Introduction Our goal: l l get context, overview, “feel” of networking approach: l descriptive l use Internet as example Overview: l l l l what’s the Internet what’s a protocol? network edge network core access net, physical media Internet/ISP structure/net neutrality history 2

Roadmap 1. 1 What is the Internet? Internet Structure & Internet Providers 1. 2 Internet Protocols 1. 3 History 1. 4 Network edge/core packet switching E 2 E net neutrality 3

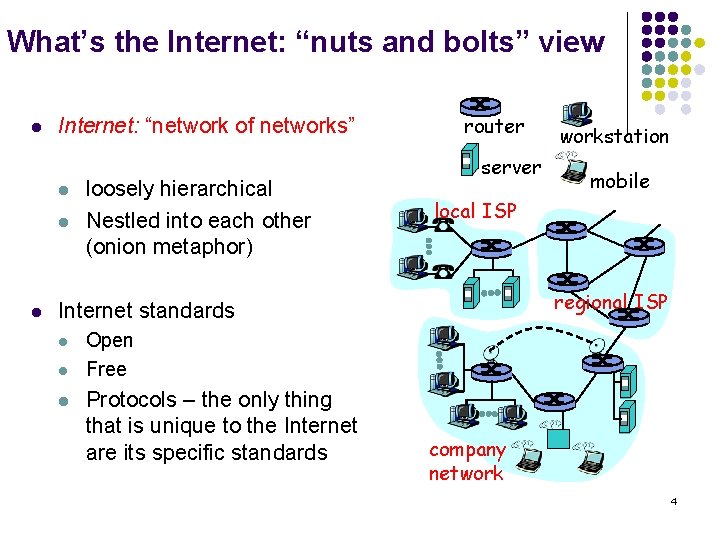
What’s the Internet: “nuts and bolts” view l Internet: “network of networks” l loosely hierarchical Nestled into each other (onion metaphor) router server l l mobile local ISP regional ISP Internet standards l workstation Open Free Protocols – the only thing that is unique to the Internet are its specific standards company network 4

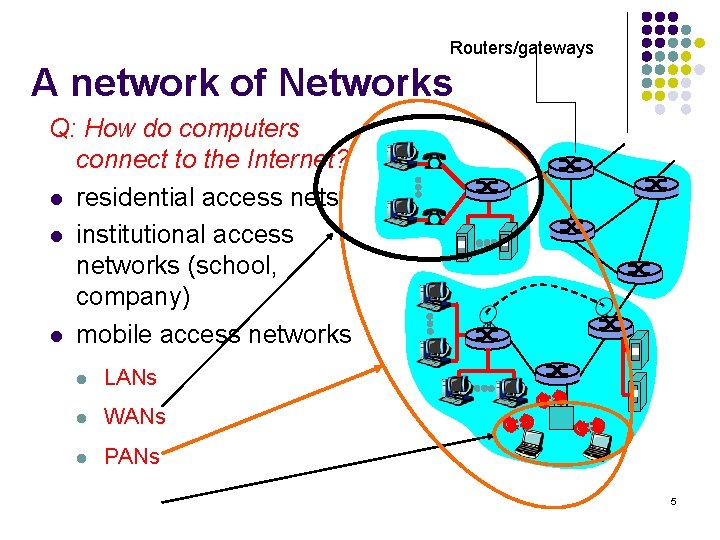
Routers/gateways A network of Networks Q: How do computers connect to the Internet? l residential access nets l institutional access networks (school, company) l mobile access networks l LANs l WANs l PANs 5

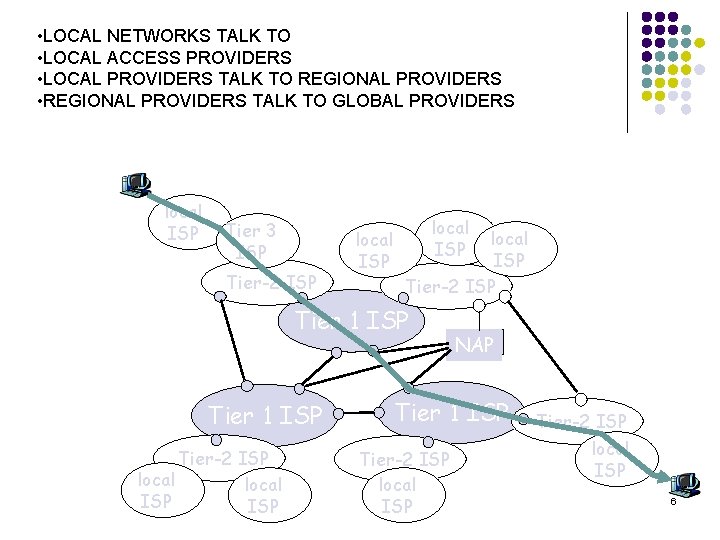
• LOCAL NETWORKS TALK TO • LOCAL ACCESS PROVIDERS • LOCAL PROVIDERS TALK TO REGIONAL PROVIDERS • REGIONAL PROVIDERS TALK TO GLOBAL PROVIDERS local ISP Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local ISP NAP Tier 1 ISP Tier-2 ISP local ISP 6

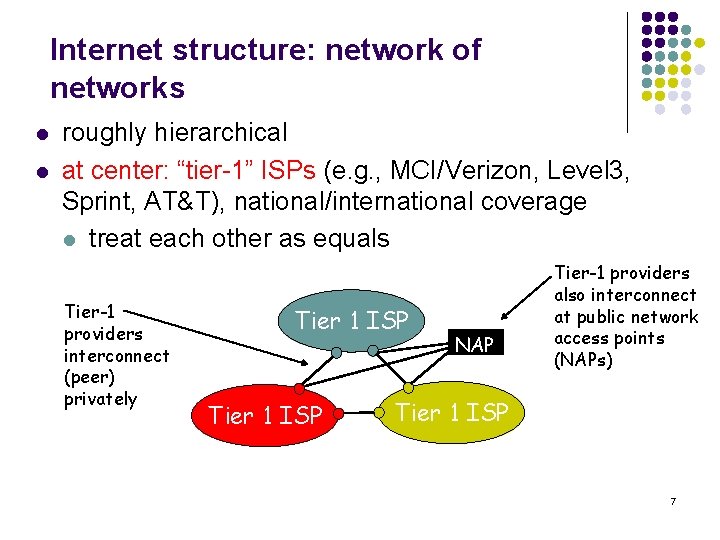
Internet structure: network of networks l l roughly hierarchical at center: “tier-1” ISPs (e. g. , MCI/Verizon, Level 3, Sprint, AT&T), national/international coverage l treat each other as equals Tier-1 providers interconnect (peer) privately Tier 1 ISP NAP Tier-1 providers also interconnect at public network access points (NAPs) Tier 1 ISP 7

Tier-1 ISP: e. g. , Sprint US backbone network 8

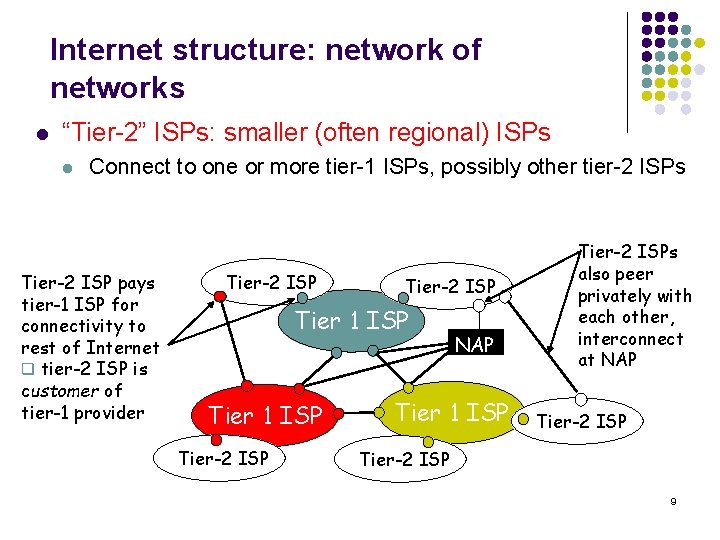
Internet structure: network of networks l “Tier-2” ISPs: smaller (often regional) ISPs l Connect to one or more tier-1 ISPs, possibly other tier-2 ISPs Tier-2 ISP pays tier-1 ISP for connectivity to rest of Internet q tier-2 ISP is customer of tier-1 provider Tier-2 ISP Tier 1 ISP Tier-2 ISP NAP Tier 1 ISP Tier-2 ISPs also peer privately with each other, interconnect at NAP Tier-2 ISP 9

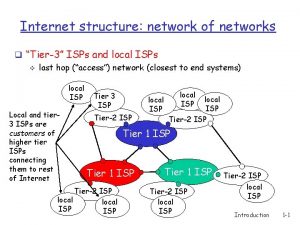
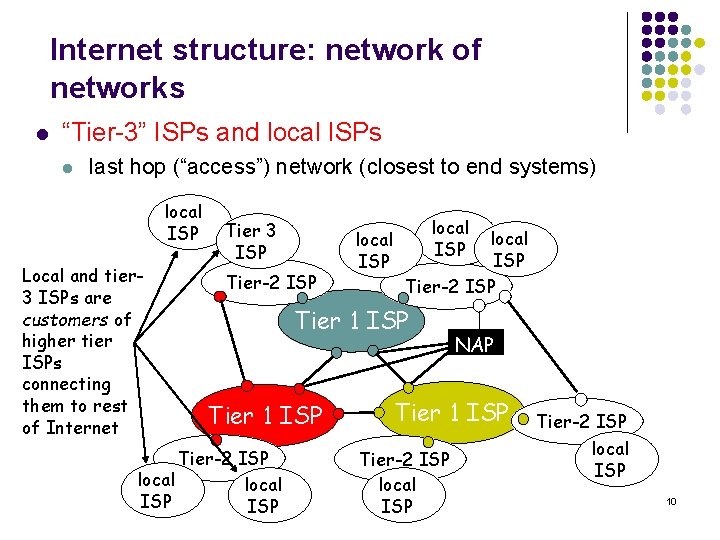
Internet structure: network of networks l “Tier-3” ISPs and local ISPs l last hop (“access”) network (closest to end systems) local ISP Local and tier 3 ISPs are customers of higher tier ISPs connecting them to rest of Internet Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local ISP NAP Tier 1 ISP Tier-2 ISP local ISP 10

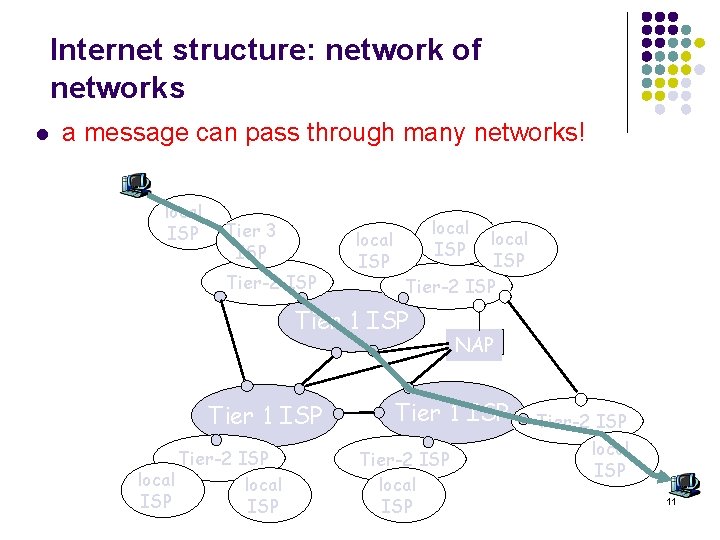
Internet structure: network of networks l a message can pass through many networks! local ISP Tier 3 ISP Tier-2 ISP local ISP Tier-2 ISP Tier 1 ISP Tier-2 ISP local ISP NAP Tier 1 ISP Tier-2 ISP local ISP 11

Roadmap 1. 1 What is the Internet? Internet Structure & Internet Providers 1. 2 Internet Protocols 1. 3 History 1. 4 Network edge/core packet switching E 2 E net neutrality 12

Protocols l Connect computers that do not speak the same language l l Not embedded in a particular operating system Are simple sets of instructions Are the Internet’s “operating system” Without them the Internet would not exist 13

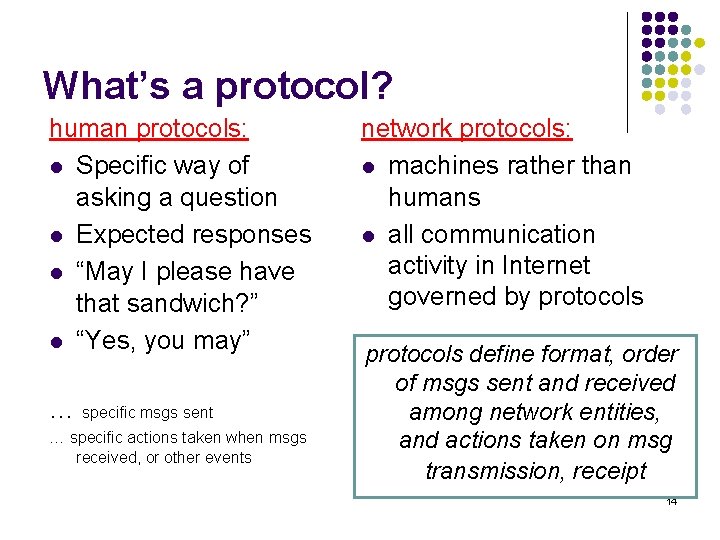
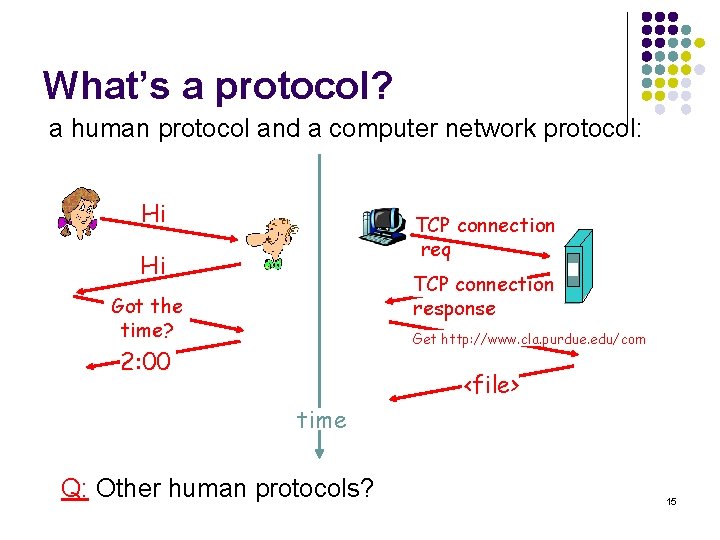
What’s a protocol? human protocols: l Specific way of asking a question l Expected responses l “May I please have that sandwich? ” l “Yes, you may” … specific msgs sent … specific actions taken when msgs received, or other events network protocols: l machines rather than humans l all communication activity in Internet governed by protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt 14

What’s a protocol? a human protocol and a computer network protocol: Hi TCP connection req Hi TCP connection response Got the time? Get http: //www. cla. purdue. edu/com 2: 00 <file> time Q: Other human protocols? 15

Packet switching core internet principle l l l Send and email or l It’s like a highway request a video or l Break down the webpage shipment into individual Messages/videos/files are “trucks”, do not send the broken down into small whole train down, might pieces get bogged down… Each piece is sent l http: //www. pbs. org/opb/nerds 2. 0. 1/geek_glossar independently of all y/packet_switching_flash. html others on the shortest l Baran, Kleinrock path available at the time Roberts, Cerf… 16

The Internet is a higway system, while old telephones were railroads l Telephones: a line, when used by two people is "busy" - the entire bandwidth is taken by the conversation l Like a railroad track that is kept closed between any two stations until the train passes l Internet: a line is filled with bits of information from multiple messages, racing one past another, l like a road network, cars (packets, bits) can run side by side on the same road until they occupy all the available space 17

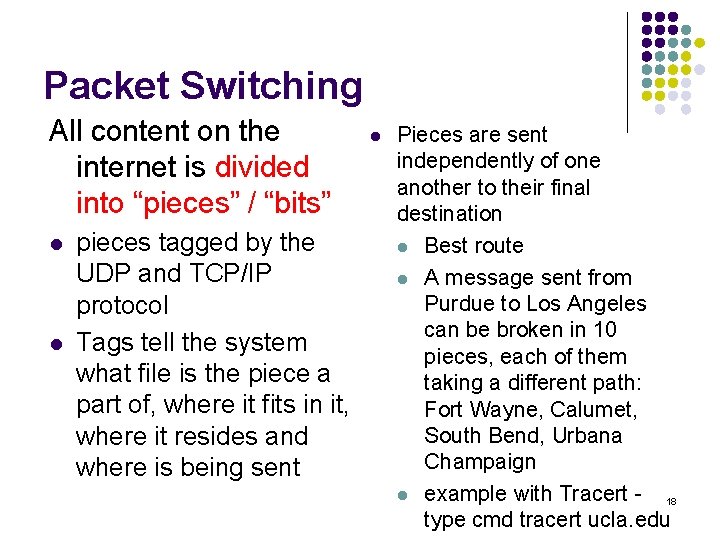
Packet Switching All content on the internet is divided into “pieces” / “bits” l l pieces tagged by the UDP and TCP/IP protocol Tags tell the system what file is the piece a part of, where it fits in it, where it resides and where is being sent l Pieces are sent independently of one another to their final destination l Best route l A message sent from Purdue to Los Angeles can be broken in 10 pieces, each of them taking a different path: Fort Wayne, Calumet, South Bend, Urbana Champaign l example with Tracert - 18 type cmd tracert ucla. edu

Three Important Protocols l l UDP (Used Datagram), TCP (Transport Protocol), IP (Internet Protocol) set of rules (protocols) used to send data in the form of message units (packets) between computers over the Internet. UDP - basic unitizing of information into packets (bits) - used for some simple transfers, cannot take care of call backs IP takes care of handling the actual delivery of the data, TCP creates a connection and takes care of keeping track of the individual units of data (called packets) that a message is divided into for efficient routing through the Internet and understandably reassembled at the other end. If a packet is lost, TCP makes sure that the receiver calls back for it. 19

What do UDP, TCP, IP do when you call a webpage ? When an HTML file is sent to you from a Web server, the protocols divide the file into one or more packets, numbers the packets, and then forwards them individually to the destination IP address. Although each packet has the same destination IP address, it may get routed differently through the network. Visualization of path taken by the North Korean Press Agency site to reach to West Lafayette (via http: //www. monitis. com/traceroute/index. jsp? url=kcna. kp&test. Id=20396 10) - Click to visualize At the other end (the client program in your computer), TCP/IP/UDP programs reassemble the individual packets and waits until they have 20 arrived to forward them to you as a single file.

IP addresses l l l All physical computers have an IP address (198. 324. 9. 009) – see syllabus resources Domain names (addresses matei. org, veffort. us, purdue. edu) are assigned to an IP address (reside on a physical computer), but there could be several domains assigned to a single computer with a unique IP address Domain names should be bought, there are no automatic domain names They are in the format purdue. edu, name. tld The computer you use to access the web has an IP address as well… 21

More protocols l The Internet uses a set of protocols, stacked on top of each other l l l Ethernet (hardware) TCP/IP (addressing; essential; packet switching) FTP (file transfer) HTTP (file and link connectivity) VOIP (voice of the internet, not one, but several) RTSP (radio/voice protocol used for streaming audio) 22

Tracert, whois, visual path l l l PC Start > type cmd Type tracert matei. org Mac Terminal – traceroute matei. org 23

Roadmap 1. 1 What is the Internet? Internet Structure & Internet Providers 1. 2 Internet Protocols 1. 3 History 1. 4 Network edge/core packet switching E 2 E net neutrality 24

Why should we know anything about Internet history? l l l Internet technologies (protocols, connections) born over time - We had Internet connections before the public knew about it (@20 years) No definite goal from the very beginning - goals emerged First Internet-like network 1969 - experimental, scientific collaboration Internet as we know it - 1980 Made to be be efficient and flexible, open to innovation = as long as use was limited and distributed Various protocols invented by various people for various reasons: l Example - The invention of the web by a British physicist 25 in Switzerland to share physics papers

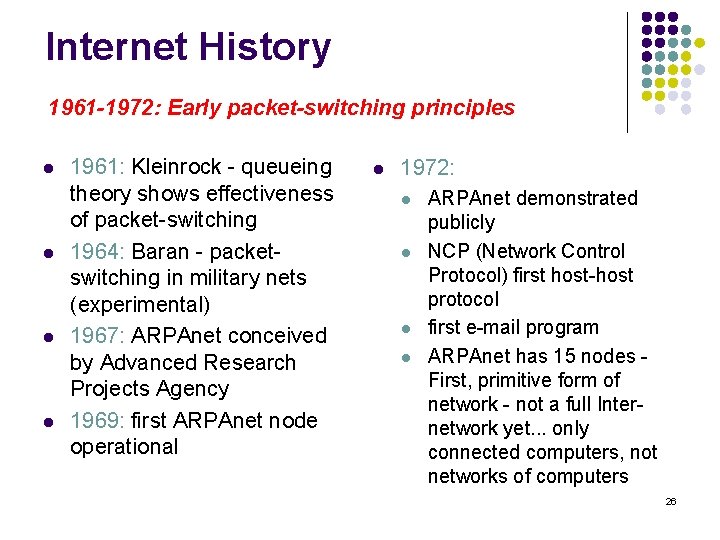
Internet History 1961 -1972: Early packet-switching principles l l 1961: Kleinrock - queueing theory shows effectiveness of packet-switching 1964: Baran - packetswitching in military nets (experimental) 1967: ARPAnet conceived by Advanced Research Projects Agency 1969: first ARPAnet node operational l 1972: l l ARPAnet demonstrated publicly NCP (Network Control Protocol) first host-host protocol first e-mail program ARPAnet has 15 nodes - First, primitive form of network - not a full Internetwork yet. . . only connected computers, not networks of computers 26

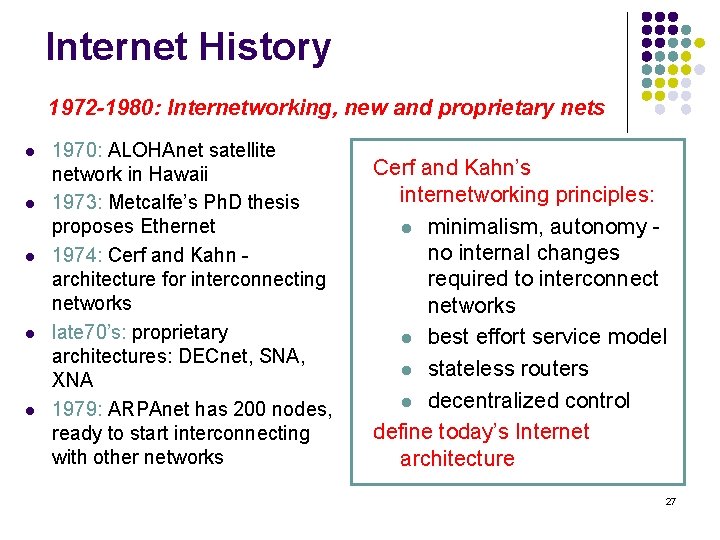
Internet History 1972 -1980: Internetworking, new and proprietary nets l l l 1970: ALOHAnet satellite network in Hawaii 1973: Metcalfe’s Ph. D thesis proposes Ethernet 1974: Cerf and Kahn - architecture for interconnecting networks late 70’s: proprietary architectures: DECnet, SNA, XNA 1979: ARPAnet has 200 nodes, ready to start interconnecting with other networks Cerf and Kahn’s internetworking principles: l minimalism, autonomy - no internal changes required to interconnect networks l best effort service model l stateless routers l decentralized control define today’s Internet architecture 27

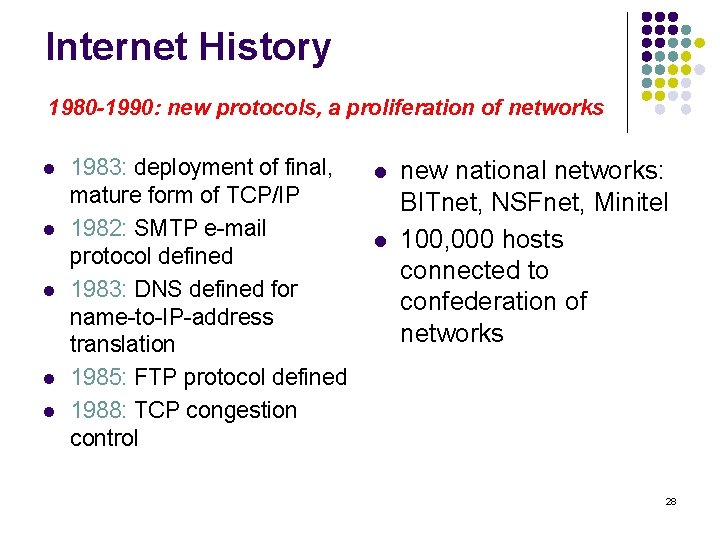
Internet History 1980 -1990: new protocols, a proliferation of networks l l l 1983: deployment of final, mature form of TCP/IP 1982: SMTP e-mail protocol defined 1983: DNS defined for name-to-IP-address translation 1985: FTP protocol defined 1988: TCP congestion control l l new national networks: BITnet, NSFnet, Minitel 100, 000 hosts connected to confederation of networks 28

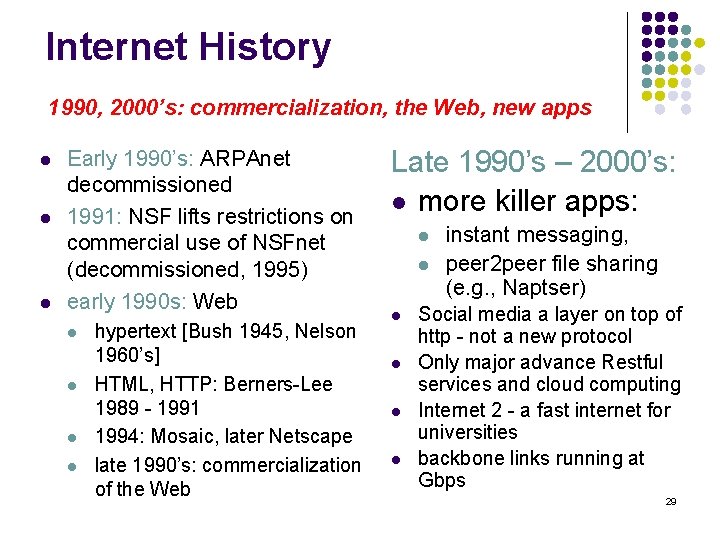
Internet History 1990, 2000’s: commercialization, the Web, new apps l l l Early 1990’s: ARPAnet decommissioned 1991: NSF lifts restrictions on commercial use of NSFnet (decommissioned, 1995) early 1990 s: Web l l hypertext [Bush 1945, Nelson 1960’s] HTML, HTTP: Berners-Lee 1989 - 1991 1994: Mosaic, later Netscape late 1990’s: commercialization of the Web Late 1990’s – 2000’s: l more killer apps: l l l instant messaging, peer 2 peer file sharing (e. g. , Naptser) Social media a layer on top of http - not a new protocol Only major advance Restful services and cloud computing Internet 2 - a fast internet for universities backbone links running at Gbps 29

Roadmap 1. 1 What is the Internet? Internet Structure & Internet Providers 1. 2 Internet Protocols 1. 3 History 1. 4 Network edge/core frompacket switching to E 2 E net neutrality and the dark side of e 2 e and of the Internet 30

E 2 E - a design philosophy l l l A way to describe at the conceptual level how things work A way to describe how Internet technologies should work together A way to emphasize the role of some Internet technologies at the expense of others A way to discuss about Internet virtues (and vices) A handy explanation for why the Internet is good at certain things and not at other things A way to understand what/who is responsible for the fact that the Internet is inherently: l open, unreliable, privacy averse, vulnerable to attacks 31

Packet switching versus circuit switching (old telephone style) Is packet switching a “slam dunk winner? ” l l l Packet switching: divide message in small bits, send by most efficient route at the moment l Great for bursty data (email, IM, web pages) l resource sharing (access You. Tube) l simpler, no call setup, very flexible, you can add new protocols Excessive congestion: packet delay and loss l new protocols needed for reliable data transfer, congestion control - none available yet and frowned upon by FCC (net neutrality) Q: How to provide telephone-like behavior? l bandwidth guarantees needed for audio/video apps l still not completely solved… and there is a big IF this type of network can finally deliver l Problem? Edge to Edge architecture. . 32

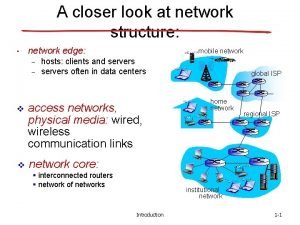
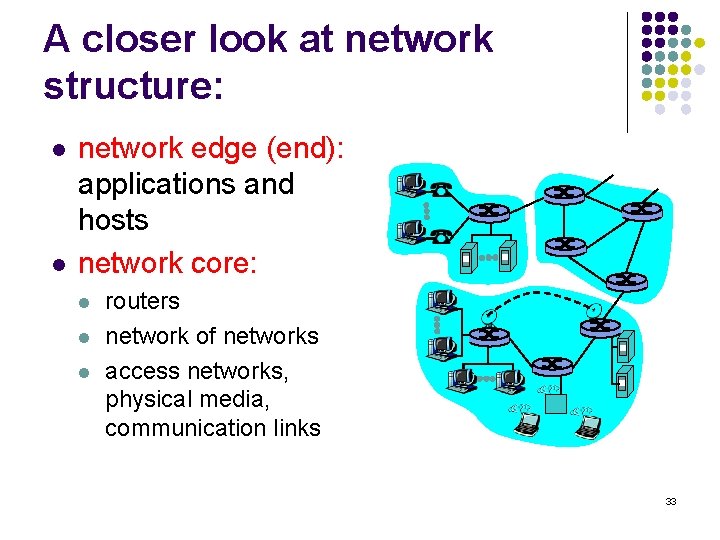
A closer look at network structure: l l network edge (end): applications and hosts network core: l l l routers network of networks access networks, physical media, communication links 33

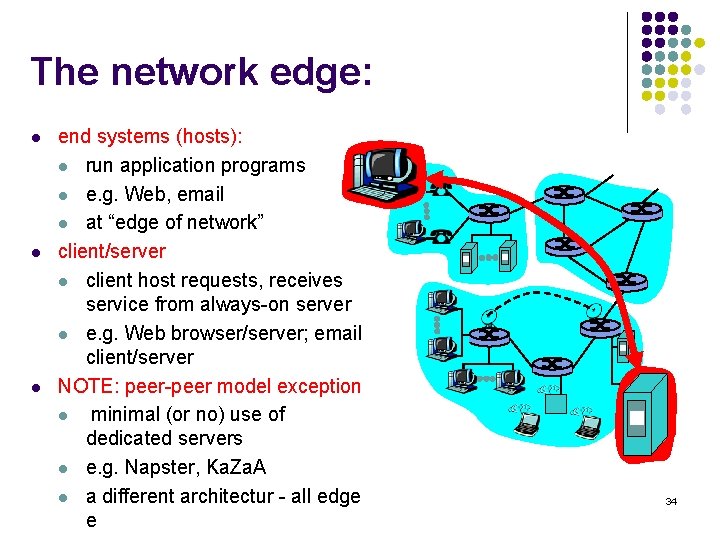
The network edge: l l l end systems (hosts): l run application programs l e. g. Web, email l at “edge of network” client/server l client host requests, receives service from always-on server l e. g. Web browser/server; email client/server NOTE: peer-peer model exception l minimal (or no) use of dedicated servers l e. g. Napster, Ka. Za. A l a different architectur - all edge e 34

The edge is l l l Where you are Your computer and the content delivery computers connected to you Where most applications run: l l l Web browsers Servers Media Players (Real Player) FTP programs Limewire or Edonkey 35

The network core l Is the network of routers and domain name servers that make the connections possible l l Responsible with directing and regulating Internet traffic Generally dumb, cannot filter or prioritize traffic l l l Because of E 2 E (edge to edg or END TO END or E@E e) principle Intelligence in a network should be at the edge Some of the trunk (core) wires and connections 36

Edge to Edge (END TO END or E 2 E) Principle l l l The Internet is designed to be smart at the edge (your local computer, servers, applications) Dumb at the core (routers, protocols) Facilitates flexibility and interconnectivity NOTE: Lessig prefers End to End, I prefer Edge, as being more descriptive

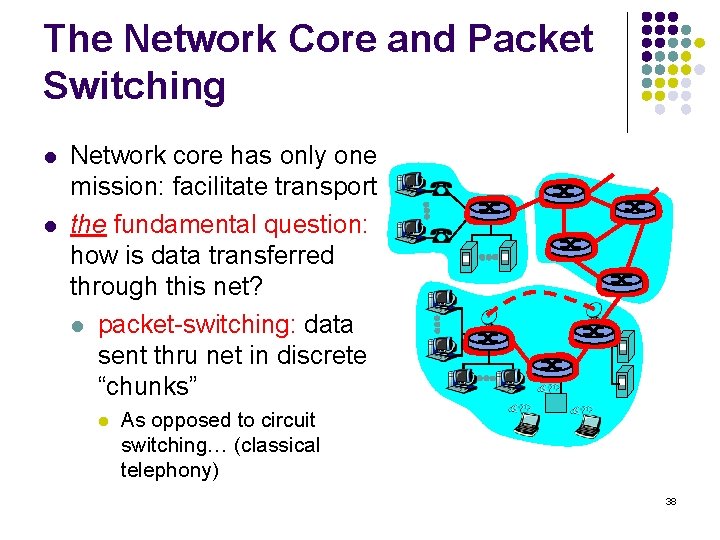
The Network Core and Packet Switching l l Network core has only one mission: facilitate transport the fundamental question: how is data transferred through this net? l packet-switching: data sent thru net in discrete “chunks” l As opposed to circuit switching… (classical telephony) 38

Packet Switching - a technology l Like the highway system l l l Each packet (car) gets on the highway at an entry point independently and arrives at destination the way it wants to Takes advantage of all routes available at a specific point Maximum use of available resources Difficult to schedule massive and simultaneous communication l NOTE: Circuit switching (telephone) like the railroad system-a line occupied for one conversation (Train) at the time Because packets are treated equally and protocols used to manipulate them are simple -> foster simplicity and helps adding new components to the network 39

Net neutrality - a policy l The basic protocol TCP/IP is designed to treat all packets the same l l l The Internet is in fact constructed with a weak core, dumb core l l l Dispatch them all at the same speed and same priority TCP is neutral as to its content It is an “E 2 E” network – edge to edge All information is to be treated as simply and sent as fast as possible to destination Net neutrality=all content should be treated the same, no prioritizing, no censorship 40

Net neutrality exception l l Does not apply to wireless Internet traffic Why? l l Wireless companies paid for the spectrum and invested significant amounts of money in infrastructure – they need to recoup their costs and should not be forced to open their networks to their competitors (contested Facetime vs ATT) Does not apply to China or IRAN l l China & Iran are fact is actively messing up with the protocols Create “smart” routers to censor searches 41

End to End (edge to edge) or E 2 E a design philosophy l l l Facilitates connectivity of various computer systems and networks Fosters innovation (Lessig - innovation commons and Zittrain - generative web ) l Innovation commons=you can add any application, web browser, service that is in compliance with the simple rules of TCP/IP, HTTP, FTP, VOIP, etc l The Internet should be treated as a kind of commons - this fosters innovation l The protocols belong to no one, can be hacked Created democratically, via RFCs l Requests for proposals l Protocols are not proprietary, are open and non-profit 42

Net neutrality is not only about prioritizing traffic, is also about coding l l l HTML code Open this page and Right click > View Source l Each graphic element described by tags (instructions) Used to create-recreate pages Browsers build pages from tags the way orchestras play scores The method for encoding the music (Score) is part of the http protocol Some tried to “improve” it creating code that only works in some browsers (Microsoft) 43

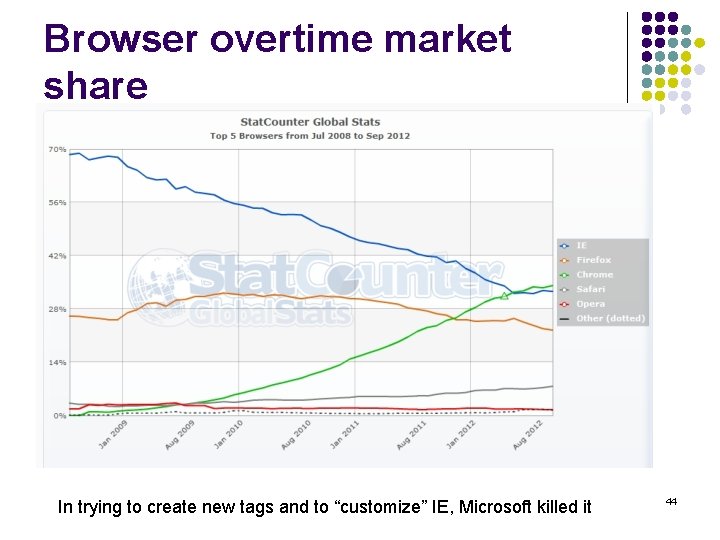
Browser overtime market share In trying to create new tags and to “customize” IE, Microsoft killed it 44

You can do better than mess up with IE and html tags…. l l l You can extend the smarts at the edges Leave html alone, create programs that use things as they are Create programs to create new types of presentations and mount them on servers l l l 3 D visualizations Interactive notifications (status updates) Mashups (Google maps and Youtube) Applications (Google docs) Use the “generative” capabilities of the web 45

What is the “generative” web? l A web that allows content creators to: l Make edges smart l l l Create applications in the “cloud” (google docs, foursquare) GW allows sending and receiving code and data along the same paths Example: a webpage is made of l l l HTML CSS Scripts (javascript)- enhance utility-the code part of the page 46

Generative web builds on and extends the PC model l The web follows the model of the PC: l l l Universal computing Programmable Extendable PCs allow third parties to write new applications This is how PCs get infected with viruses BTW 47

Generative web and e 2 e l It is the e 2 e principle that makes the web generative in two ways l l You can create new protocols (voip, etc) - Lessig You can create edge-smart apps – Twitter, Facebook, Google Docs etc… l l Most important Makes the web extensible by allowing you to write new services 48

What is the opposite of the generative web/network? l A proprietary network l l l Example: Compuserve – old network All smarts in the core Edge dumb You cannot send code alongside data Thin/dumb clients You need to login and all content is controlled 49

The end of the generative web? l Some of the greatest successes of the generative web can be its downfall: l l l The generative web allows not only “good” innovations, but also “bad” ones Viruses and worms take advantage of the generative nature of the web, especially its proclivity to allow code to use the same paths as data Facebook, a good innovation can turned against it creator, becoming a walled garden (that’s why Zittrain thinks that the future of the Internet is bleak) 50

Worms as examples of bad products of the generative web l l l A worm is a computer program It is automatically downloaded and it installs on your computer when you visit a webpage It takes advantage of the “Generative” hooks provided by the web and PCs l Ability to install and run programs in a browser or on an OS 51

Generative = Unsafe l l l A generative web cannot be 100% safe/secure A generative web is by definition open, thus liable to exploitation The generative web is like our society: l l l Freedom of expression and to carry weapons One of the countries with the highest incarceration rates and non-conformity in all aspects of life Many like it that way, since they believe that the costs are worth the benefits 52

Conficker l l Ukrainian (? ) worm Software that self-replicates and sends itself from computer to computer through the Internet Creates a zombie bot net (6 million? ) Illustrates that the generative properties of the web can also create bad things l l l Encrypted communication Calls periodically 50, 000 domain names, one of which is controlled by the hackers to upgrade itself Has not done anything bad - YET 53

Why need to know about Conficker? l l l Open web is exploited for nefarious projects Conficker bot net is produced/supported by the generative web Illustrates the Generative Dilemma: openness = vulnerability 54

Solutions for downside aspects of Internet architecture l Dedicated networks? l Two Internets? l l l Already exists, interuniversity, Internet 2 - but limited use by academia Abandon net neutrality? Create smart networks? Infinite bandwidth? l l l Put so much bandwidth in the ground (fiber optic) such that it does not matter how much data you throw at it Does not deal with security vulnerability Folow Iran and China? Create great firewall? Allow Facebook, Google, Apple to create walled gardens? 55

SOPA and Internet neutrality l STOP ONLINE PIRACY act l l deny pirate sites financial services deny user access by rerouting domain name conversions (DNS diversion) delist from Google prevent paypal, visa, master card, etc. from dealing with them l When DNS requests are redirected you basically mess up with net neutrality. . . Internet is interfered with 56

Weaknesses of E 2 E and of net neutrality l Cannot handle well abuse l l l Cannot support filters Most of the email traffic is spam (80 -90%) Security is weak (cannot implement encryption or filters for spam and viruses at the core of the network) Malware and worms (Conficker) become a new major threat Cannot guarantee specific speed or bandwidth l l You cannot privilege video over email You cannot reserve an entire pipeline for a gigantic 57 burst of data (Superbowl example)

Test you knowledge l Try to answer the questions on the next slides 58

Generative web l Definition l What does it do 59

Bot net l Definition l What does it do? 60

Compuserve, AOL, BITNET l Examples of. . l How did they work 61

Net neutrality l Definition l What does it do? 62

Summary Covered a “ton” of material! l Internet overview l what’s a protocol? l network edge, core, access network l packet-switching versus circuitswitching l Information commons l IP address, Domain l E 2 E and its downside Generative web and its drawbacks l history l You now have: l context, overview, “feel” of networking l next, how does Web 2. 0 work 63
 Sorin adam matei
Sorin adam matei Virtual circuit network uses
Virtual circuit network uses Basestore iptv
Basestore iptv Computer networks and internets with internet applications
Computer networks and internets with internet applications Internet transport protocol in computer networks
Internet transport protocol in computer networks Sorin mitran
Sorin mitran Sorin cismas
Sorin cismas Sorin peste
Sorin peste Labcecil
Labcecil Sorin mitrea
Sorin mitrea Primordial prevention
Primordial prevention Romania
Romania Adriana bazgan
Adriana bazgan Dan sorin duke
Dan sorin duke Omnilogic romania
Omnilogic romania Notre dame sorin society
Notre dame sorin society Simbolul nucului
Simbolul nucului Adam adam facebook
Adam adam facebook Matei zaharia
Matei zaharia Matei purice
Matei purice Matei zaharia
Matei zaharia Dispozitie eutimica
Dispozitie eutimica Liceul matei basarab craiova
Liceul matei basarab craiova Colegiul tehnic matei corvin hunedoara
Colegiul tehnic matei corvin hunedoara Dr cristina matei
Dr cristina matei Matei 28 19
Matei 28 19 Grupeaza dupa modelul de la exercitiul 1
Grupeaza dupa modelul de la exercitiul 1 571r distribution center
571r distribution center Matei zaharia spark
Matei zaharia spark Matei purice
Matei purice Matei 22
Matei 22 Matei purice
Matei purice Internet structure network of networks
Internet structure network of networks Internet structure network of networks
Internet structure network of networks The internet is a combination of networks glued together by
The internet is a combination of networks glued together by Interconnected networks internet
Interconnected networks internet Integrated and differentiated services in computer networks
Integrated and differentiated services in computer networks Error detection in computer networks
Error detection in computer networks Byte stuffing and bit stuffing
Byte stuffing and bit stuffing What is bit and byte stuffing? explain with example.
What is bit and byte stuffing? explain with example. Reverse arp
Reverse arp Analogue and digital transmission in computer networks
Analogue and digital transmission in computer networks Web and http in computer networks
Web and http in computer networks Hamming distance in computer network
Hamming distance in computer network Protocols and standards in computer networks
Protocols and standards in computer networks Crc example
Crc example Computer networks and internets
Computer networks and internets What is internet
What is internet Crc in computer networks
Crc in computer networks Crc in computer networks
Crc in computer networks Traffic management in computer networks
Traffic management in computer networks Tpdu in computer networks
Tpdu in computer networks What is optimality principle in computer networks
What is optimality principle in computer networks Snmp ports
Snmp ports What is optimality principle in computer networks
What is optimality principle in computer networks Uses of computer network in business application
Uses of computer network in business application Definition of computer
Definition of computer Intro dns
Intro dns Icmp in computer networks
Icmp in computer networks Framing in computer network
Framing in computer network Dns in computer networks
Dns in computer networks Data communication and networking assignment questions
Data communication and networking assignment questions Network vs distributed system
Network vs distributed system Routing algorithms in computer networks
Routing algorithms in computer networks