CMSC 414 Computer and Network Security Jonathan Katz









































- Slides: 45

CMSC 414 Computer and Network Security Jonathan Katz

Course Organization

Administrative ¨ Me ¨ TA ¨ Contact information, office hours, listed on course webpage

Course webpage http: //www. cs. umd. edu/~jkatz/security/f 09 ¨ Syllabus – Subject to change… – Assigned readings and videos • Will try to post by Friday for the following week • Read in advance and come prepared to discuss – Additional (optional) readings ¨ Homeworks distributed from the course webpage ¨ Check frequently for announcements

Class readings ¨ Material posted on the course webpage is fair game for the exams, even if not covered in class ¨ Material covered in class is fair game for the exams, even if not listed on the webpage

Textbook ¨ No required text ¨ Several good texts out there – Will list on the course webpage ¨ Will supplement lectures with other readings (distributed on class webpage)

Course requirements ¨ Homeworks – 3 -5 programming assignments – Possibly 1 -2 written assignments ¨ I expect students have access to a computer/laptop capable of running a hypervisor – VM player for Windows/linux (free download) – VMware Fusion for MACs ($49. 99 for academic license), other free options may be available – Occasional in-class exercises

Labs (tentative) ¨ Crypto ¨ Building a secure protocol ¨ Buffer overflow ¨ Web security

Piazza http: //piazza. com ¨ For your benefit ¨ Questions about lecture/readings ¨ Homework questions ¨ News items – I encourage you to post links to news of interest!

Class participation ¨ Please!

Syllabus (tentative)

Syllabus I ¨ Introduction… – A broad perspective on security ¨ Cryptography – The basics (take CMSC 456 or read my book for more) • If you took 456 with me, you can skip – Cryptography is not the whole solution… – …but it is an important part of the solution – Along the way, we will see why cryptography can’t solve all security problems

Syllabus II ¨ Network security I – Identity, PKI – Authentication and key exchange protocols – Password and biometric authentication – Anonymity and pseudonymity – Privacy

Syllabus II ¨ System security – General principles – Security policies – Access control – OS security – “Trusted computing” ¨ Programming language security – Buffer overflows, input validation errors – Viruses/worms – Web security

Syllabus IV ¨ Privacy/anonymity – Database security – Anonymous communication – Privacy in social networks ¨ Network security in the real world – Some real-world protocols (IPSec/SSL) – Security of network infrastructure (routing, DNS, TCP/IP, DDos attacks, …)

Overview

Introduction and overview ¨ What is computer/network security? Why is it important? ¨ Course philosophy and goals ¨ A broad perspective on “computer security”

Computer security is important… ¨ Several high-profile hacks in past years – Number of vulnerabilities/attacks increasing ¨ Cyberwarfare ¨ Increasing gov’t and academic interest ¨ Just read the news…

Cybercrime ¨ e. g. , botnets ¨ Washington Post, “Invasion of the Computer Snatchers” (2006): – – High-school dropout Breaks into 2000 computers in 6 hours (while sleeping) $6, 800 per month; 2 minutes of work per day $2 B industry (annual)

Thoughts ¨ Why is the problem so difficult? ¨ What can be done about it?

“Security” ¨ Most of computer science is concerned with achieving desired behavior ¨ Security is concerned with preventing undesired behavior – Different way of thinking! – An enemy/opponent/hacker/adversary who is actively and maliciously trying to circumvent any protective measures you put in place

One illustration of the difference ¨ Software testing determines whether a given program implements a desired functionality – Test I/O characteristics – Q/A ¨ How do you test whether a program does not allow for undesired functionality? – Penetration testing helps, but only up to a point

Why is computer security so hard? ¨ Computer networks are “systems of systems” – Your system may be secure, then the environment changes ¨ Too many things dependent on a small number of systems ¨ Society is unwilling to trade off features for security ¨ Ease of attacks – – Cheap Distributed, automated Anonymous Insider threats ¨ Security not built in from the beginning ¨ Humans in the loop… ¨ Computers ubiquitous…

Computers are everywhere… ¨ …and can always be attacked ¨ Electronic banking, social networks, e-voting ¨ i. Pods, i. Phones, PDAs, RFID transponders ¨ Automobiles ¨ Appliances, TVs ¨ (Implantable) medical devices ¨ Cameras, picture frames(!) – See http: //www. securityfocus. com/news/11499

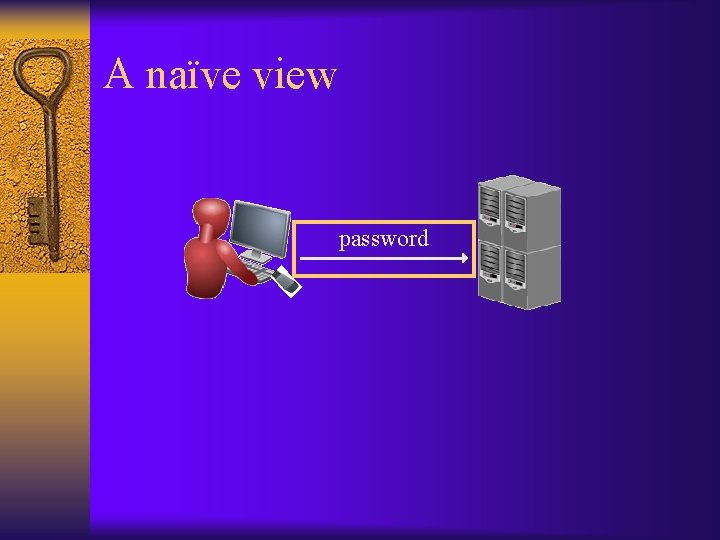
A naïve view password

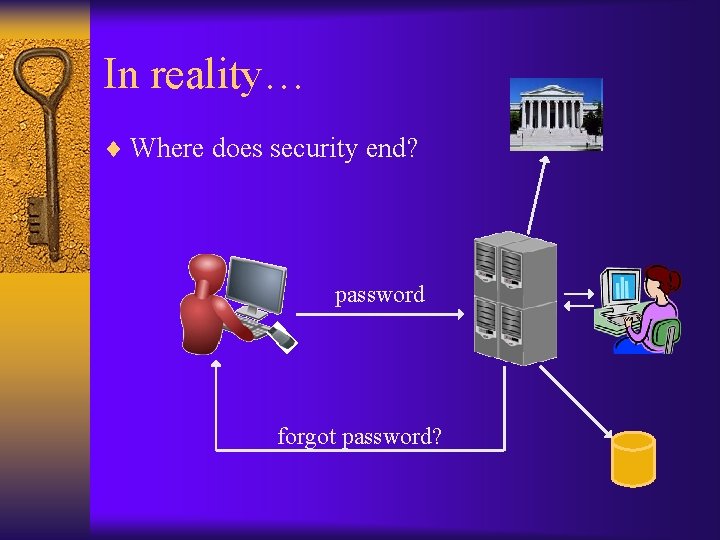
In reality… ¨ Where does security end? password forgot password?

One good attack ¨ Use public records to figure out someone’s password, or to get it from tech support – E. g. , hacked email account of Sarah Palin ¨ The password-recovery mechanism is part of the system! – The password-recovery mechanism may be the most vulnerable point to attack

Computer security is not just about computers ¨ What is “the system”? ¨ Physical security ¨ Social engineering – Bribes for passwords – Phishing ¨ “External” means of getting information – Legal records, trash cans ¨ User education… ¨ Security is a process, not a product…(!)

Security is interdisciplinary ¨ Draws on all areas of CS – Theory (especially cryptography) – Networking – Programming languages/compilers – Operating systems – Databases – AI/learning theory – Computer architecture / hardware – HCI, psychology

Security mindset ¨ Learn to think with a “security mindset” in general – What is “the system”? – How could this system be attacked? • What is the weakest point of attack? – How could this system be defended? • What threats am I trying to address? • How effective will a given countermeasure be? • What is the trade-off between security, cost, and usability?

An example: airline security ¨ Ask: what is the cost (economic and otherwise) of current airline security? ¨ Ask: do existing rules (e. g. , banning liquids) make sense? ¨ Ask: are the tradeoffs worth it? – (Why do we not apply the same rules to train travel? ) – (Would spending money elsewhere be more effective? ) ¨ Ask: how would you get on a plane if you were on the no-fly list? – (I will not give you the answer – you can find it online) – This is a thought experiment only!

Computer security is not just about “security” ¨ Prevention… ¨ Detection, response, audit – How do you know when you are being attacked? – How quickly can you stop the attack? – Attribution: can you identify the attacker(s)? – Can you prevent the attack from recurring? ¨ Recovery – Can be much more important than prevention ¨ Economics, insurance, risk management… ¨ Security is a process, not a product…

A naïve view ¨ Achieve “absolute” security

In reality… ¨ Absolute security is easy to achieve! – How…? ¨ Absolute security is impossible to achieve! – Why…? ¨ Good security is about risk management

Security as a trade-off ¨ The goal is not (usually) “to make the system as secure as possible”… ¨ …but instead, “to make the system as secure as possible within certain constraints” (cost, usability, convenience) – Military vs. personal networks ¨ Must understand the existing constraints – E. g. , passwords…

Cost-benefit analysis ¨ Important to evaluate what level of security is necessary/appropriate – Cost of mounting a particular attack vs. value of attack to an adversary – Cost of damages from an attack vs. cost of defending against the attack – Likelihood of a particular attack ¨ Sometimes the best security is to make sure you are not the easiest target for an attacker…

“More” security not always better ¨ “No point in putting a higher post in the ground when the enemy can go around it” ¨ Need to identify the weakest link – Security of a system is only as good as the security at its weakest point… ¨ Security is not a “magic bullet” ¨ Security is a process, not a product

Summary ¨ “The system” is not just a computer or a network ¨ Prevention is not the only goal – Cost-benefit analysis – Detection, response, recovery ¨ Nevertheless…in this course, we will focus on computer security, and primarily on prevention – If you want to be a security expert, you need to keep the rest in mind

Philosophy of this course ¨ We are not going to be able to cover everything – We are not going to be able to even mention everything ¨ Main goals – A sampling of many different aspects of security – The security “mindset” – Become familiar with basic acronyms (RSA, SSL, PGP, etc. ), and “buzzwords” (phishing, …) – Become an educated security consumer – Try to keep it interesting with real-world examples and “hacking” projects

Course goals ¨ You will not be a security expert after this class (after this class, you should realize why it would be dangerous to think you are) ¨ But you should have a better appreciation of the threats, and how to address some of them

“Trusting trust”

“Trusting trust” ¨ Consider a compiler that embeds a trapdoor into anything it compiles ¨ How to catch? – Read source code? (What if replaced? ) – Re-compiler? ¨ What if the compiler embeds the trojan code whenever it compiles a compiler? – (That’s nasty…)

¨ Change compiler source S compiler(S) { if (match(S, "login-pattern")) { compile (login-backdoor) return } if (match(S, "compiler-pattern")) { compile (compiler-backdoor) return }. . /* compile as usual */ }

“Trusting trust” ¨ Whom do you trust? ¨ Does one really need to be this paranoid? ? – Probably not – Sometimes, yes ¨ Shows that security is complex…and essentially impossible ¨ Comes back to risk/benefit trade-off

Assigned readings ¨ Thompson’s article ¨ “Inside the Twisted Mind of the Security Professional” ¨ “We are All Security Customers” ¨ “Information Security and Externalities” ¨ Chapter 1 of “Security Engineering”