Secure Computation Jonathan Katz Professor Computer Science UMD









![Notable improvements • Protocol level – OT extension [IKNP 03] – Better garbling (free-XOR Notable improvements • Protocol level – OT extension [IKNP 03] – Better garbling (free-XOR](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-20.jpg)
![Client Key tool: ORAM Server (writes also supported) ORAM read, i 12 D[i 21] Client Key tool: ORAM Server (writes also supported) ORAM read, i 12 D[i 21]](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-27.jpg)
![Conceptually… Client (x) [st]st [ORAM state] “Trusted 3 rd party” Server (D) [st] [ORAM Conceptually… Client (x) [st]st [ORAM state] “Trusted 3 rd party” Server (D) [st] [ORAM](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-30.jpg)
![Conceptually… Client (x) [st] [d’] [d] st = x d= while (1) { (inst, Conceptually… Client (x) [st] [d’] [d] st = x d= while (1) { (inst,](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-31.jpg)
![A secure protocol! Client (x) [st] [d’] st = x d= while (1) { A secure protocol! Client (x) [st] [d’] st = x d= while (1) {](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-32.jpg)


![Conceptually… MIPS CPU [PC] [regs’] [regs] P 2 (y) ORAM P 1 (x) x Conceptually… MIPS CPU [PC] [regs’] [regs] P 2 (y) ORAM P 1 (x) x](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-38.jpg)




- Slides: 45

Secure Computation Jonathan Katz Professor, Computer Science, UMD Director, Maryland Cybersecurity Center

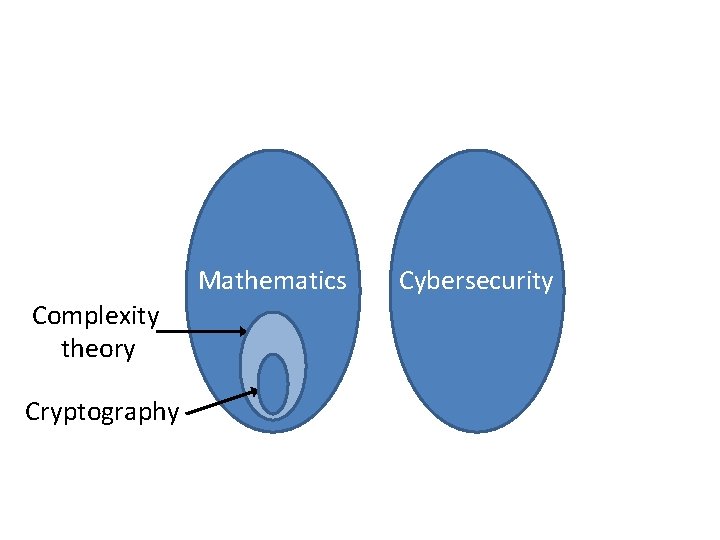
Mathematics Complexity theory Cryptography Cybersecurity

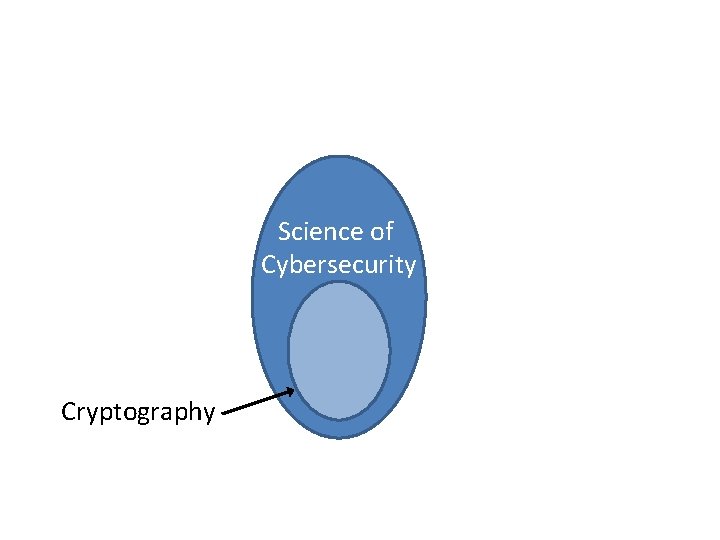
Science of Cybersecurity Cryptography

Importance of cryptography • Cryptography is a key component in many (all? ) security solutions • The cryptographic approach provides a way to move beyond the “design-break-patch” cycle • Define (even informally) what you want to achieve • State your assumptions explicitly • Prove that your construction achieves your goal • Cryptography is a nucleus for cybersecurity research – Foundations for a “secure networked world” … with end-to -end formal guarantees

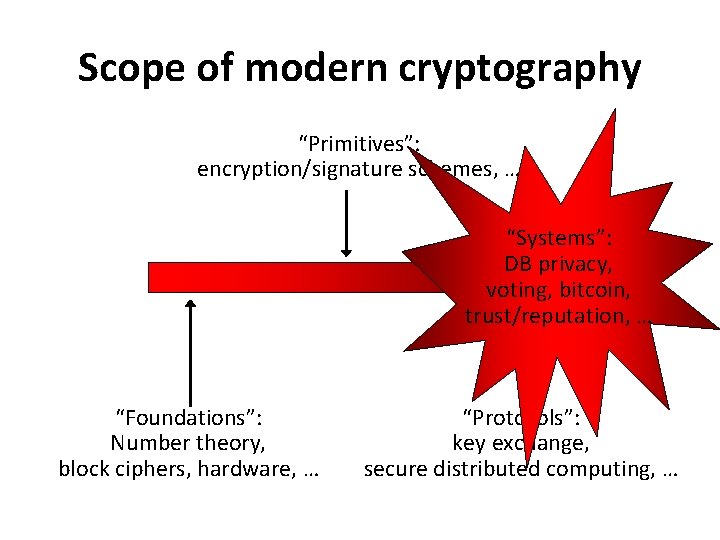
Scope of modern cryptography “Primitives”: encryption/signature schemes, … “Systems”: DB privacy, voting, bitcoin, trust/reputation, … “Foundations”: Number theory, block ciphers, hardware, … “Protocols”: key exchange, secure distributed computing, …

Secure computation

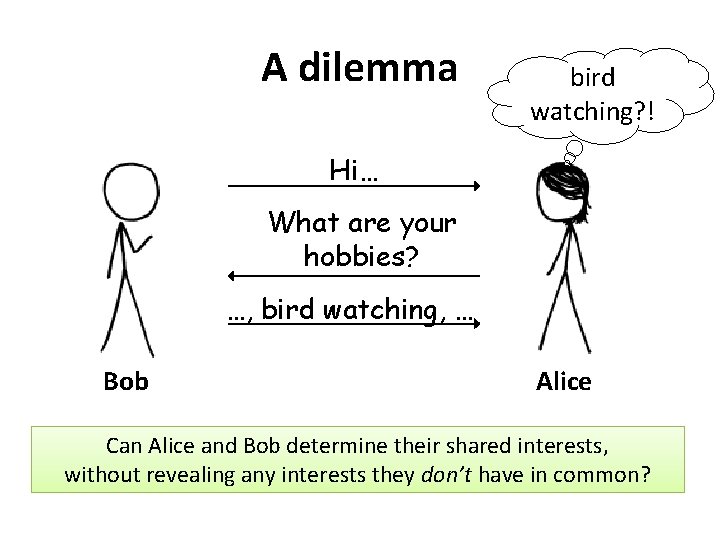
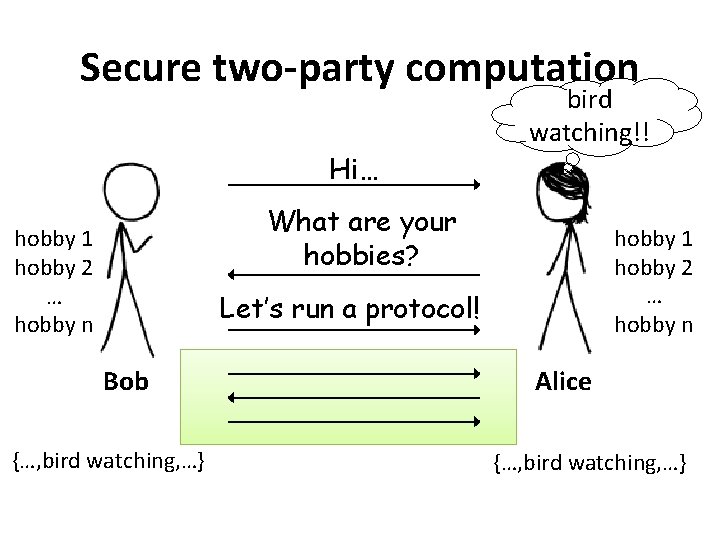
A dilemma bird watching? ! Hi… What are your hobbies? …, bird watching, … Bob Alice Can Alice and Bob determine their shared interests, without revealing any interests they don’t have in common?

Secure two-party computation Hi… bird watching!! What are your hobbies? hobby 1 hobby 2 … hobby n Let’s run a protocol! Bob {…, bird watching, …} Alice {…, bird watching, …}

Secure two-party computation Are any passengers on the no-fly list? Person 1 Person 2 … Person n Passenger 1 Passenger 2 … Passenger n

Natural question I • How can these parties (who don’t trust each other) “securely” perform the computation? – While preserving secrecy of their inputs (to the extent possible) – While ensuring correctness of outputs • Techniques/ideas from crypto, programming languages, distributed computing

Natural question II • Why are these questions important? • Candidate application domains – [Do. D/IC] Secure search, cloud storage – [OFR, Treasury] More transparency, better regulation – Industry interest

How can parties securely compute f ?

A protocol is secure if it emulates the use of a trusted party In particular, this implies: • The computed results are correct • Parties’ inputs remain private (except for what is implied by the outputs) • Parties’ inputs are chosen independently • And more…

Threat models • Semi-honest (honest-but-curious) adversaries – Adversary follows the protocol faithfully, but tries to learn information from the protocol execution – A reasonable threat model in some settings • Trusted parties under legal/policy constraints • Software attestation, auditing, etc. • Malicious adversaries – May behave arbitrarily; still cannot violate security guarantees

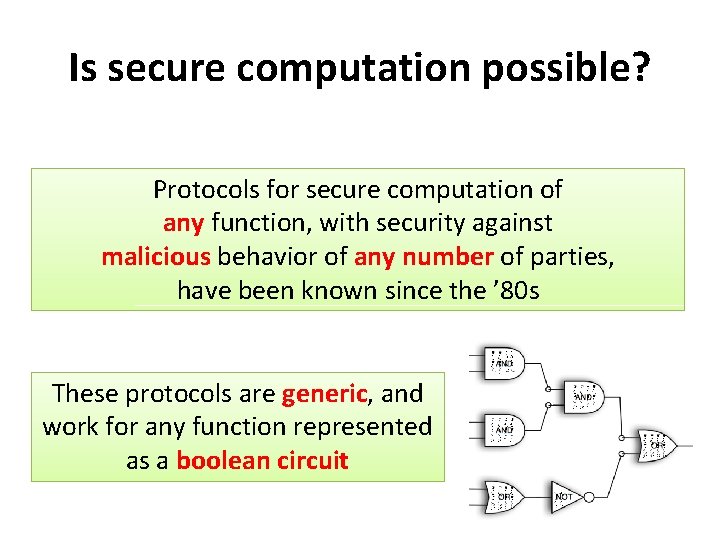
Is secure computation possible? Protocols for secure computation of any function, with security against malicious behavior of any number of parties, have been known since the ’ 80 s These protocols are generic, and work for any function represented as a boolean circuit

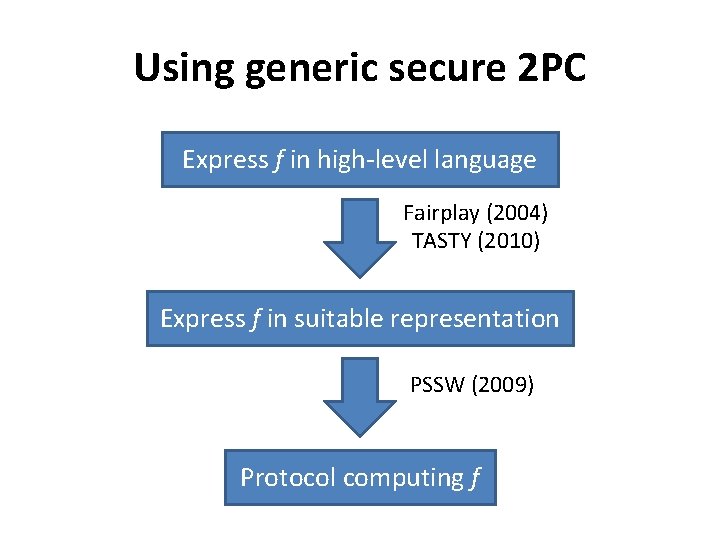
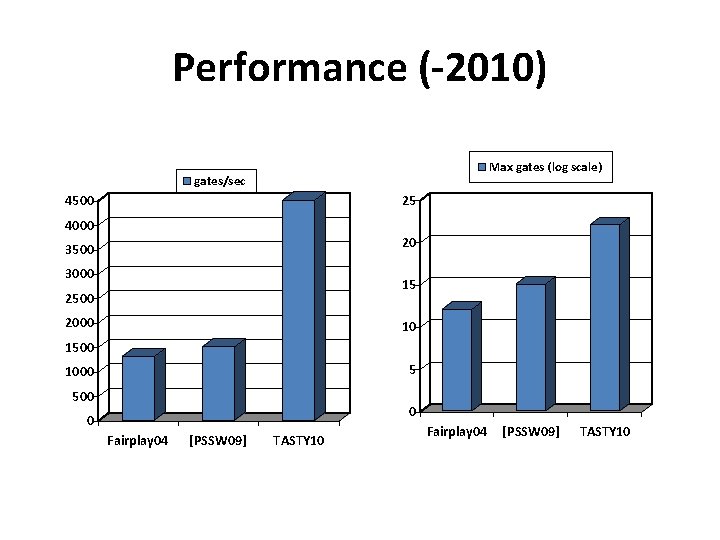
Using generic secure 2 PC Express f in high-level language Fairplay (2004) TASTY (2010) Express f in suitable representation PSSW (2009) Protocol computing f

Is secure computation practical? • The general perception in the ’ 80 s/’ 90 s was that garbled circuits were hopelessly inefficient – Need to express f as a boolean circuit – Circuits get big quickly! (>230 gates) – Symmetric-key operations linear in the circuit size – Public-key operations linear in the input length

Performance (-2010) Max gates (log scale) gates/sec 4500 25 4000 20 3500 3000 15 2500 2000 10 1500 5 1000 500 0 0 Fairplay 04 [PSSW 09] TASTY 10

Using generic secure 2 PC Express f in high-level language Express f in suitable representation Efficient implementation Protocol computing f optimizations Better crypto primitives
![Notable improvements Protocol level OT extension IKNP 03 Better garbling freeXOR Notable improvements • Protocol level – OT extension [IKNP 03] – Better garbling (free-XOR](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-20.jpg)
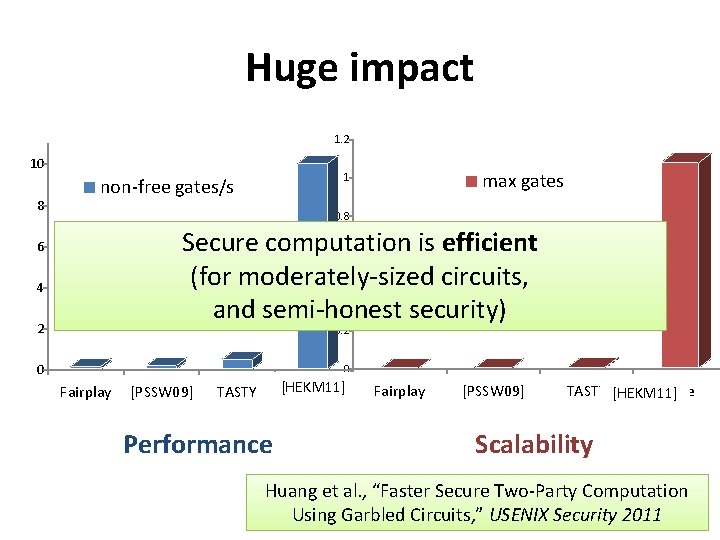
Notable improvements • Protocol level – OT extension [IKNP 03] – Better garbling (free-XOR [KS 08], row reduction [PSSW 09], half gates [ZRE 15]) – Cut-and-choose [LP 07, LP 11, HKE 14, L 14, …], new models [MF 06, HKE 12], amortization [LR 14, H+14] • Implementation level [HEKM 11] – “Pipelining” – Reducing number of wires/gates – Optimized circuit libraries

Huge impact 1. 2 10 8 max gates 1 non-free gates/s 0. 8 Secure computation is efficient 0. 6 (for moderately-sized circuits, 0. 4 and semi-honest security) 6 4 2 0 0 Fairplay [PSSW 09] [HEKM 11] Here TASTY Performance Fairplay [PSSW 09] TASTY [HEKM 11] Here Scalability Huang et al. , “Faster Secure Two-Party Computation Using Garbled Circuits, ” USENIX Security 2011

Using generic secure 2 PC Express f in high-level Expressiveness? language Support for low-level optimizations? Compile-time optimizations? Type checking? Choice of representation Express f in suitable representation Which representation? Which protocol? Efficient implementation Protocol computing f optimizations Better crypto primitives

Recent results • Secure 2 PC in the RAM model* – Represent f as a RAM program rather than as a boolean circuit • Better compilers/programming languages for secure 2 PC (in the RAM model)** – Allow programmers to code as usual • Secure 2 PC of native MIPS code*** – Language-agnostic * Gordon et al. , ACM CCCS 2012 ** Liu et al. , IEEE S&P 2014 *** Gordon et al. , in submission

Why the RAM model? • Efficiency – Running time for a RAM program can be much better than the circuit size (e. g. , binary search) • Sublinear-time computation for “big data”? – The circuit for any non-trivial function must have size at least linear in the input length – In fact, linear complexity is inherent for secure computation of any non-trivial function • This is not true for amortized complexity!

Why the RAM model? • Better alignment with how programmers think about algorithms and write their code – What is the complexity of sorting? – Dynamic memory accesses (e. g. , count[a[i]]++; ) – General-purpose computation on a von Neumann architecture • Input-dependent running time

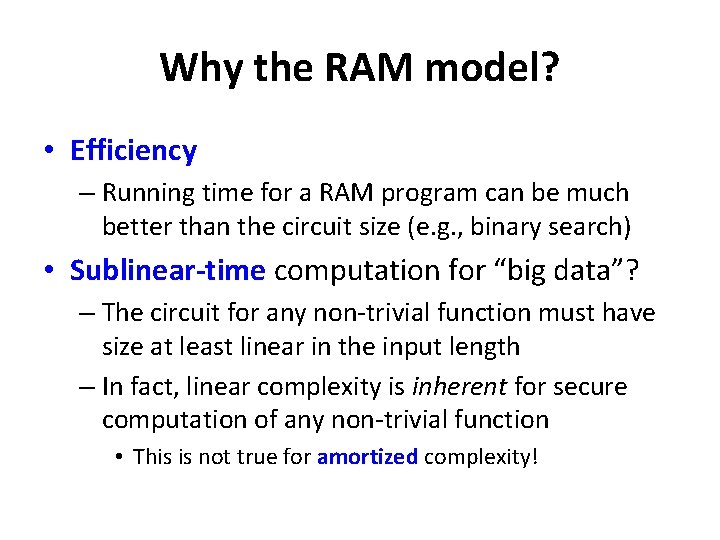
Key tool: ORAM Client Server • Allows oblivious access to stored data, with polylog overhead [GO 96, …, S+11, S+13, …] D: ORAM state
![Client Key tool ORAM Server writes also supported ORAM read i 12 Di 21 Client Key tool: ORAM Server (writes also supported) ORAM read, i 12 D[i 21]](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-27.jpg)
Client Key tool: ORAM Server (writes also supported) ORAM read, i 12 D[i 21] ORAM state Security: accessed positions are independent of i 1, i 2, …

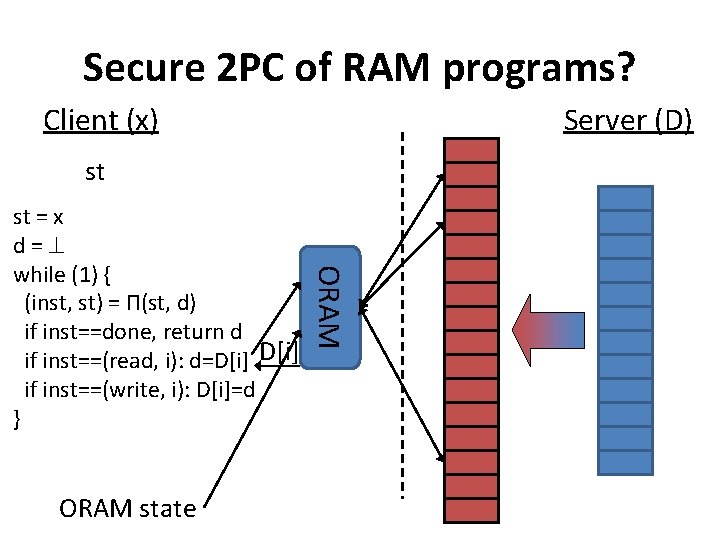
Secure 2 PC of RAM programs? Client (x) Server (D) st ORAM state ORAM st = x d= while (1) { (inst, st) = Π(st, d) if inst==done, return d if inst==(read, i): d=D[i] if inst==(write, i): D[i]=d }

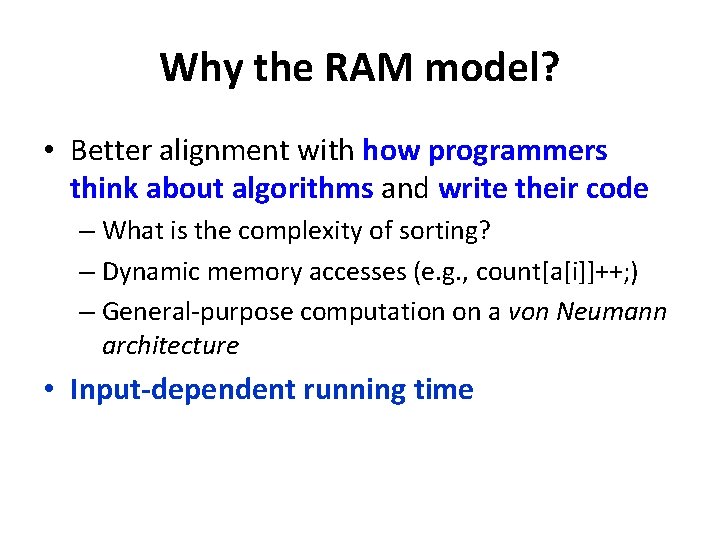
Problems? • If server initializes the ORAM itself, access patterns are no longer oblivious to the server! • No security against the client! – Client learns st – Client learns ORAM state – Client learns intermediate results of the ORAM computation
![Conceptually Client x stst ORAM state Trusted 3 rd party Server D st ORAM Conceptually… Client (x) [st]st [ORAM state] “Trusted 3 rd party” Server (D) [st] [ORAM](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-30.jpg)
Conceptually… Client (x) [st]st [ORAM state] “Trusted 3 rd party” Server (D) [st] [ORAM state]
![Conceptually Client x st d d st x d while 1 inst Conceptually… Client (x) [st] [d’] [d] st = x d= while (1) { (inst,](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-31.jpg)
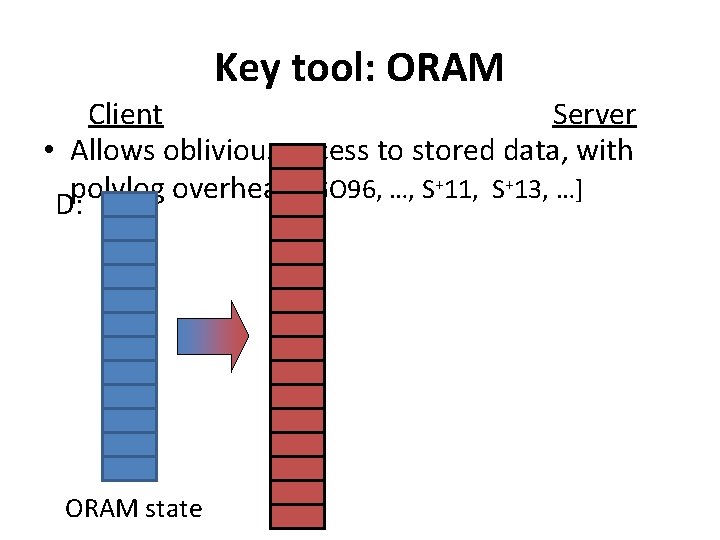
Conceptually… Client (x) [st] [d’] [d] st = x d= while (1) { (inst, st) = Π(st, d) if inst==done, return d if inst==(read, i): d=D[i] Repeatif inst==(write, until inst = done, then i): D[i]=d reconstruct final output } Server (D) [st] [d’] [d] ORAM [ORAM state]
![A secure protocol Client x st d st x d while 1 A secure protocol! Client (x) [st] [d’] st = x d= while (1) {](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-32.jpg)
A secure protocol! Client (x) [st] [d’] st = x d= while (1) { (inst, st) = Π(st, d) if inst==done, return d if inst==(read, i): d=D[i] if inst==(write, i): D[i]=d } Server (D) [st] [d’] ORAM [ORAM state]

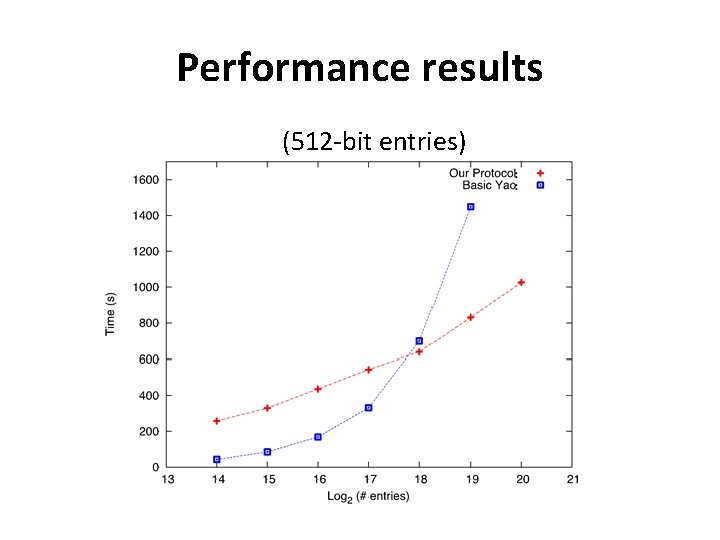
Have we gained anything? • After the initialization, all circuits computed have small size, independent of |D| • Amortized complexity: – Say original computation requires T steps for memory of size S Þ ORAM protocol needs O(T polylog S) lookups Þ O(T polylog S) secure-computation sub-protocols on small circuits of size polylog S Þ If T is sublinear, sublinear complexity overall!

Performance results (512 -bit entries)

Limitations • Programmers still limited to using a fixed (toy? ) language to express their programs • No support for legacy code • Although programs can be made instruction oblivious, doing so increases the number of instructions executed – Existing compilers for secure computation are not as good as gcc…

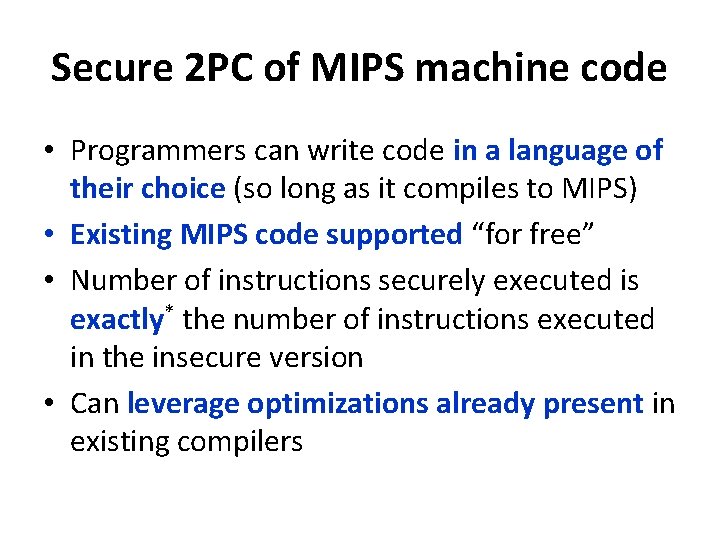
Secure 2 PC of MIPS machine code • Programmers can write code in a language of their choice (so long as it compiles to MIPS) • Existing MIPS code supported “for free” • Number of instructions securely executed is exactly* the number of instructions executed in the insecure version • Can leverage optimizations already present in existing compilers

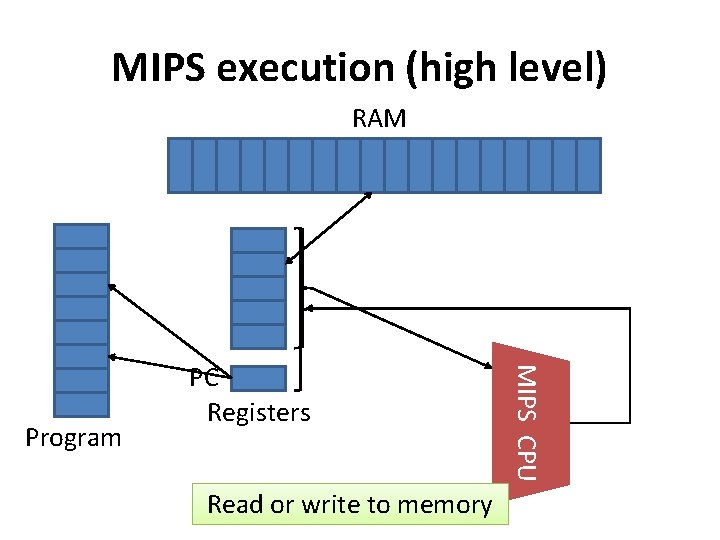
MIPS execution (high level) RAM Read Fetch Execute ornext write instruction to memory MIPS CPU Program PC Registers
![Conceptually MIPS CPU PC regs regs P 2 y ORAM P 1 x x Conceptually… MIPS CPU [PC] [regs’] [regs] P 2 (y) ORAM P 1 (x) x](https://slidetodoc.com/presentation_image/ca15e00a5dd8a9c12a6312574e109a36/image-38.jpg)
Conceptually… MIPS CPU [PC] [regs’] [regs] P 2 (y) ORAM P 1 (x) x y [PC] [regs’] [regs]

Why are these questions important?

Do. D • IARPA: secure database search – Now being piloted by NCTC • DARPA: fully homomorphic encryption (PROCEED); private search (BRANDEIS) • Air Force: detecting potential satellite collisions

OFR (US Dept. of the Treasury) • Looking at using secure computation and differential privacy for facilitating data sharing – Among regulators – Between firms – With researchers and the public • Obtain the benefits of transparency, while complying with policy regulations and reducing concerns about confidentiality Flood et al. , “Cryptography and the Economics of Supervisory Information: Balancing Transparency and Confidentiality, ” Financial Stability Conference 2013

Industry • Partisia – Danish sugar-beet auction (2008 -present) – Wireless-spectrum auctions • Sharemind – Statistical analysis of financial data • Sepior, Dyadic – Threshold AES decryption

Conclusions • Tremendous advances in theory and practice of secure 2 PC in past few years • Real-world deployment is already here! – Will continue to grow in importance and impact

Acknowledgments • Research supported by – NSF (“TC: Large: Collaborative Research: Practical Secure Computation: Techniques, Tools, and Applications”) – DARPA (“Toward Practical Cryptographic Protocols for Secure Information Sharing”) – ARL-ITA (“Secure Information Flow in Hybrid Coalition Networks”) Papers and code available at http: //www. cs. umd. edu/~jkatz/papers. html

Questions?