CCNA 2 v 3 1 Module 11 Access









- Slides: 33

CCNA 2 v 3. 1 Module 11 Access Control Lists (ACLs) © 2004 Cisco Systems, Inc. All rights reserved. 1

Objectives

Overview • ACLs enable management of traffic and secure access to and from a network. • Access Control Lists (ACLs) provides basic filtering capabilities based on – source and/or destination IP addresses – protocol types and port numbers • ACLs can be as simple as a single line intended to permit packets from a specific host, or they can be extremely complex sets of rules and conditions that can precisely define traffic and shape the performance of router processes

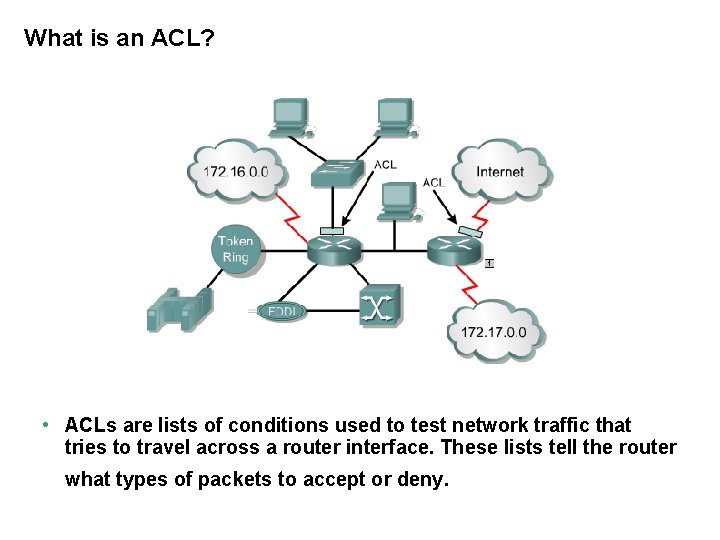
What is an ACL? • ACLs are lists of conditions used to test network traffic that tries to travel across a router interface. These lists tell the router what types of packets to accept or deny.

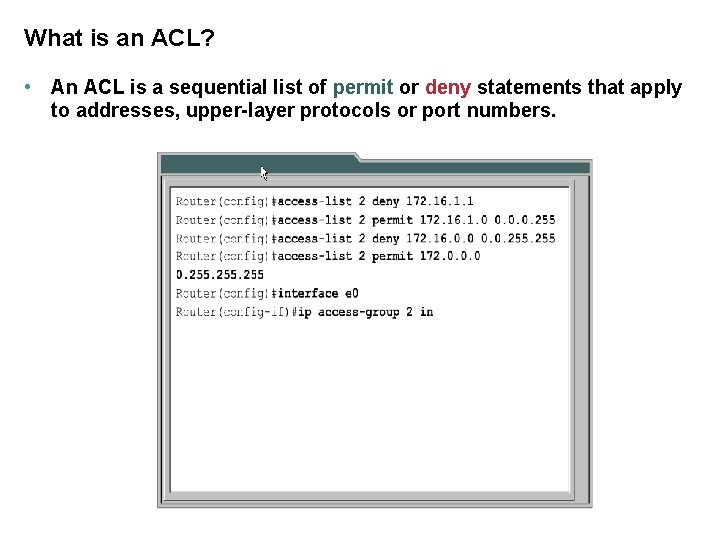
What is an ACL? • An ACL is a sequential list of permit or deny statements that apply to addresses, upper-layer protocols or port numbers.

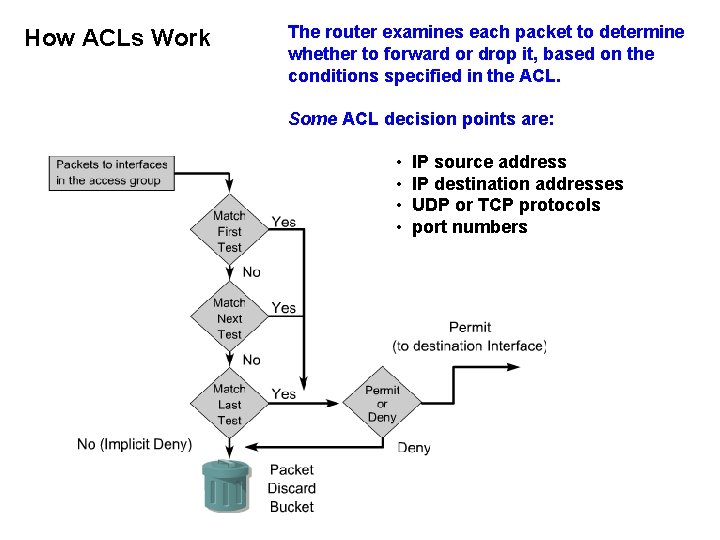
How ACLs Work The router examines each packet to determine whether to forward or drop it, based on the conditions specified in the ACL. Some ACL decision points are: • • IP source address IP destination addresses UDP or TCP protocols port numbers

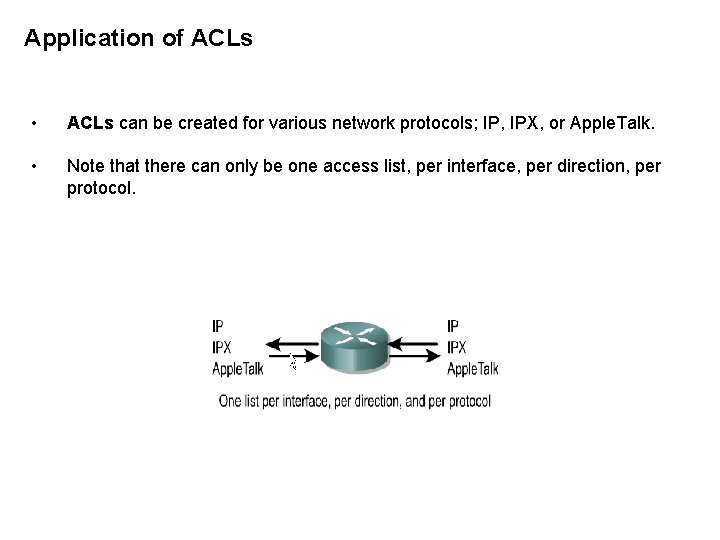
Application of ACLs • ACLs can be created for various network protocols; IP, IPX, or Apple. Talk. • Note that there can only be one access list, per interface, per direction, per protocol.

Execution of ACL Statements • ACL statements operate in sequential, logical order, from top to bottom. • If a condition is matched, the packet is permitted or denied and the rest of the ACL is not checked. • e. g. If a condition statement that permits all traffic is located at the top of the list, no statements added below that will ever be checked. Order important. • An implicit "deny any" statement is at end of list by default • However it is good practice

Why use ACLS? § performance Limit network traffic to increase network _______. § Provide traffic flow control by restricting the delivery of routing updates ________. § Security _____ - allow one host access but prevent another. § forwarded blocked Control which types of traffic are _____ or ____ by the router. § areas Ability to control which _______ a client can access. § types of files Restrict user access to only certain _______, (eg. Web pages). § all packets If ACLs are not configured, _____ passing through all parts the router will be allowed onto _____ of the network.

Updating Access Lists • If additional condition statements are needed in an access list, the entire • ACL must be deleted and recreated with the new condition statements Command no access-list-number

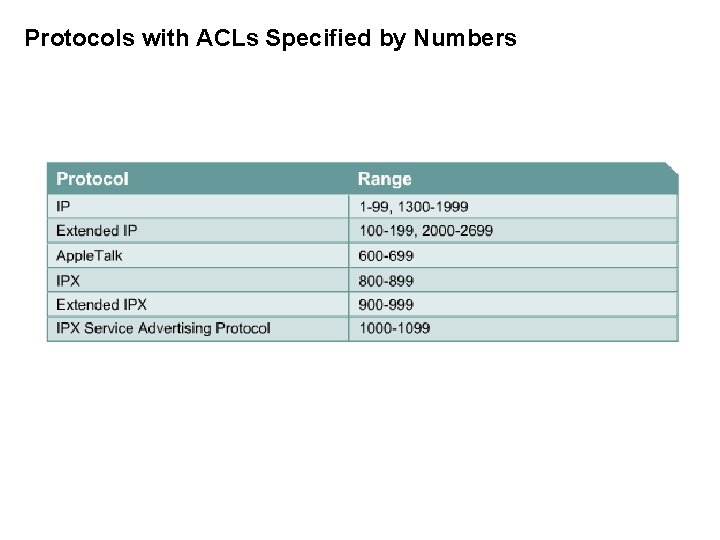
Protocols with ACLs Specified by Numbers

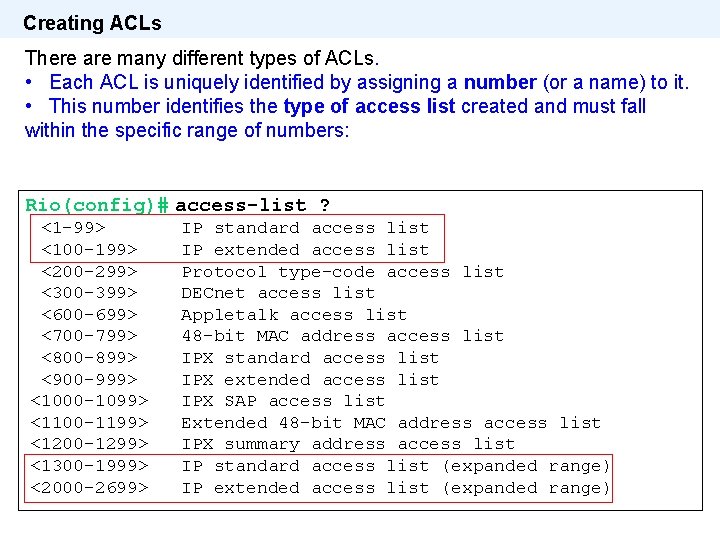
Creating ACLs There are many different types of ACLs. • Each ACL is uniquely identified by assigning a number (or a name) to it. • This number identifies the type of access list created and must fall within the specific range of numbers: Rio(config)# access-list ? <1 -99> <100 -199> <200 -299> <300 -399> <600 -699> <700 -799> <800 -899> <900 -999> <1000 -1099> <1100 -1199> <1200 -1299> <1300 -1999> <2000 -2699> IP standard access list IP extended access list Protocol type-code access list DECnet access list Appletalk access list 48 -bit MAC address access list IPX standard access list IPX extended access list IPX SAP access list Extended 48 -bit MAC address access list IPX summary address access list IP standard access list (expanded range) IP extended access list (expanded range)

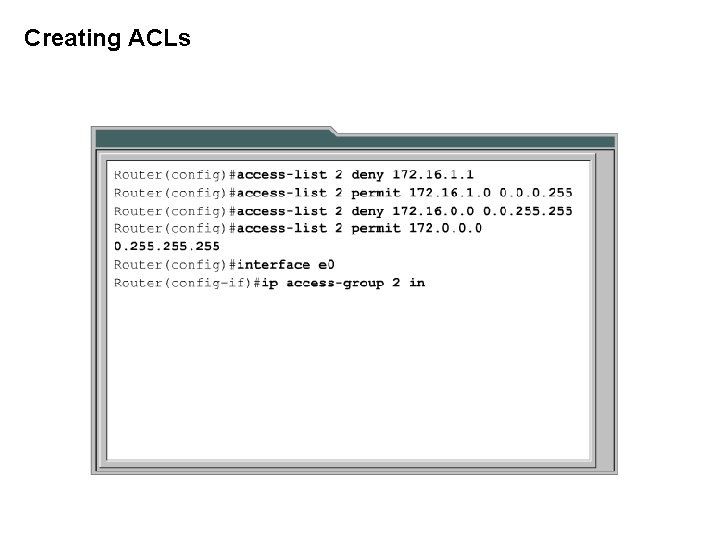
Creating ACLs

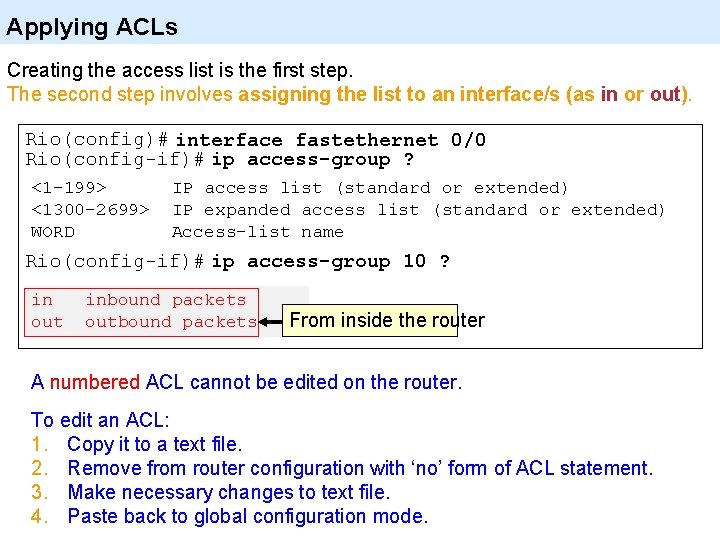
Applying ACLs Creating the access list is the first step. The second step involves assigning the list to an interface/s (as in or out). Rio(config)# interface fastethernet 0/0 Rio(config-if)# ip access-group ? <1 -199> <1300 -2699> WORD IP access list (standard or extended) IP expanded access list (standard or extended) Access-list name Rio(config-if)# ip access-group 10 ? in out inbound packets outbound packets From inside the router A numbered ACL cannot be edited on the router. To edit an ACL: 1. Copy it to a text file. 2. Remove from router configuration with ‘no’ form of ACL statement. 3. Make necessary changes to text file. 4. Paste back to global configuration mode.

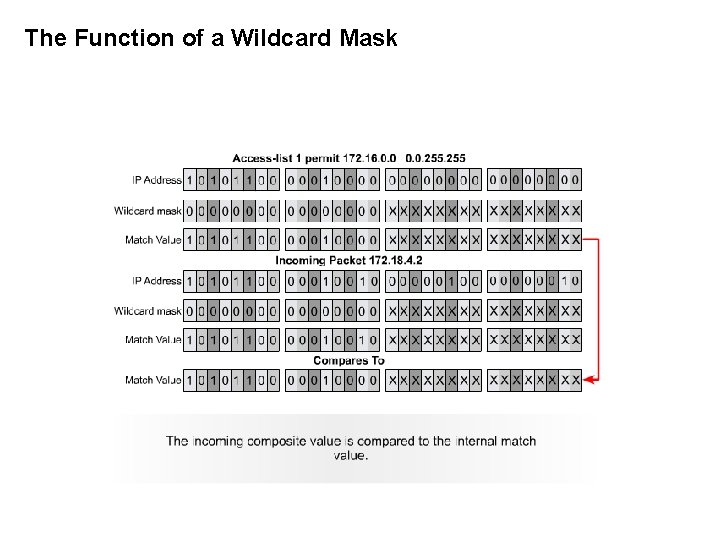
The Function of a Wildcard Mask

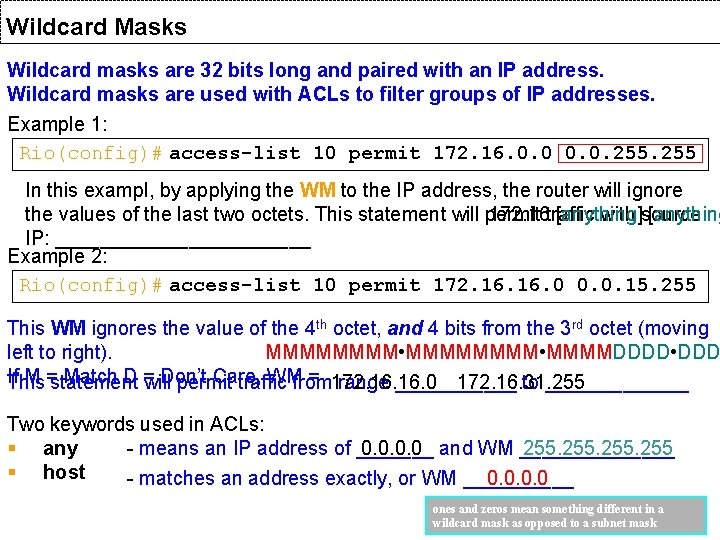
Wildcard Masks Wildcard masks are 32 bits long and paired with an IP address. Wildcard masks are used with ACLs to filter groups of IP addresses. Example 1: Rio(config)# access-list 10 permit 172. 16. 0. 0. 255 In this exampl, by applying the WM to the IP address, the router will ignore the values of the last two octets. This statement will permit traffic with source 172. 16. [anything]. [anything IP: ____________ Example 2: Rio(config)# access-list 10 permit 172. 16. 0 0. 0. 15. 255 This WM ignores the value of the 4 th octet, and 4 bits from the 3 rd octet (moving left to right). MMMMMMMM • MMMMDDDD • DDD If M = Match D = Don’t Care, WM = This statement will permit traffic from range ______ to _______ 172. 16. 0 172. 16. 31. 255 Two keywords used in ACLs: § any - means an IP address of _______ and WM _______ 0. 0 255 § host - matches an address exactly, or WM _____ 0. 0 ones and zeros mean something different in a wildcard mask as opposed to a subnet mask

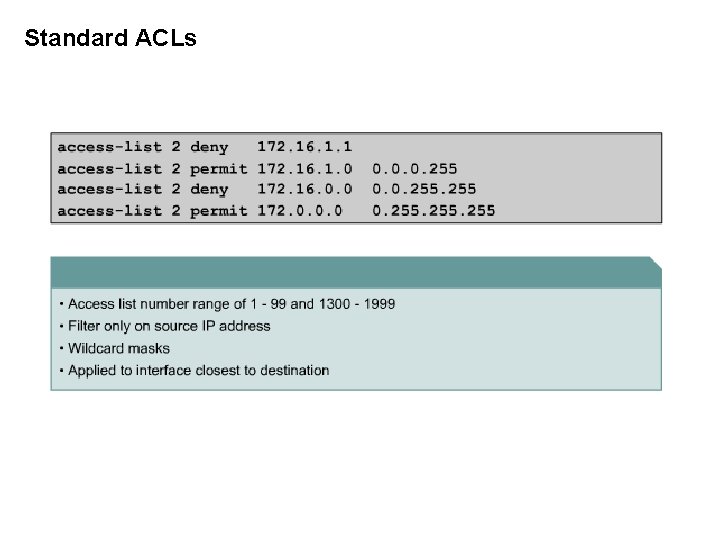
Standard ACLs

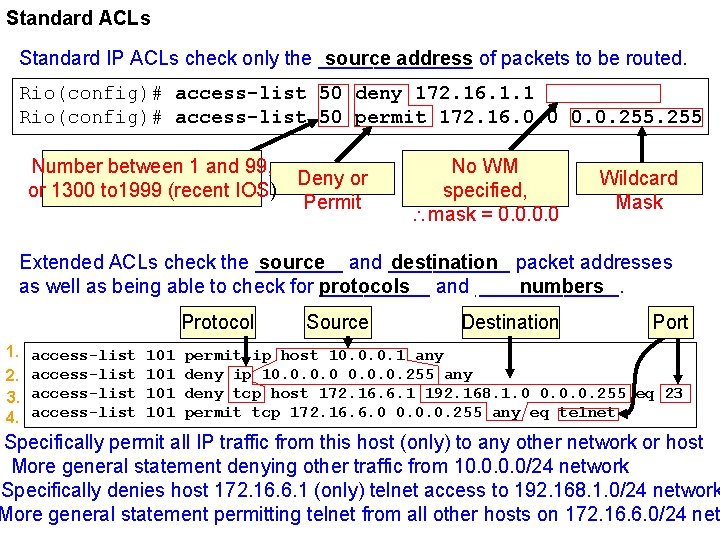
Standard ACLs Standard IP ACLs check only the _______ of packets to be routed. source address Rio(config)# access-list 50 deny 172. 16. 1. 1 Rio(config)# access-list 50 permit 172. 16. 0. 0. 255 Number between 1 and 99, or 1300 to 1999 (recent IOS) Deny or Permit Extended ACLs No WM specified, mask = 0. 0 Wildcard Mask Extended ACLs check the ____ and ______ packet addresses source destination as well as being able to check for _____ and _______. protocols port numbers Protocol 1. 2. 3. 4. access-list 101 101 Source Destination Port permit ip host 10. 0. 0. 1 any deny ip 10. 0. 255 any deny tcp host 172. 16. 6. 1 192. 168. 1. 0 0. 0. 0. 255 eq 23 permit tcp 172. 16. 6. 0 0. 0. 0. 255 any eq telnet Specifically permit all IP traffic from this host (only) to any other network or host More general statement denying other traffic from 10. 0/24 network Specifically denies host 172. 16. 6. 1 (only) telnet access to 192. 168. 1. 0/24 network More general statement permitting telnet from all other hosts on 172. 16. 6. 0/24 net

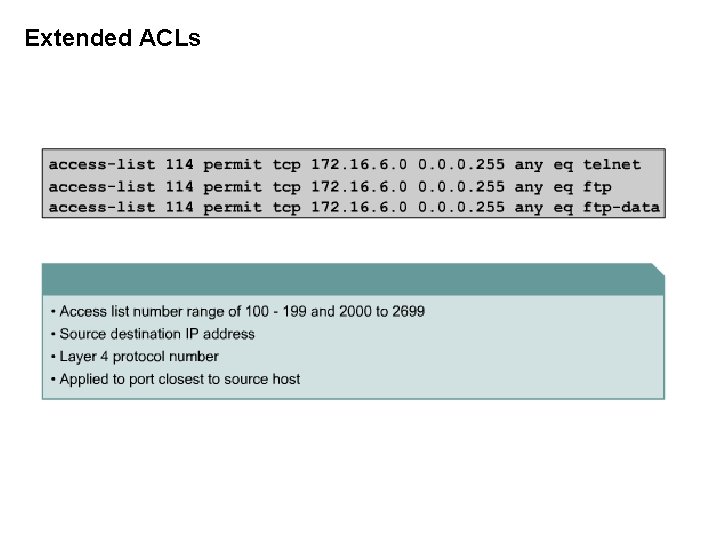
Extended ACLs

Named ACLs

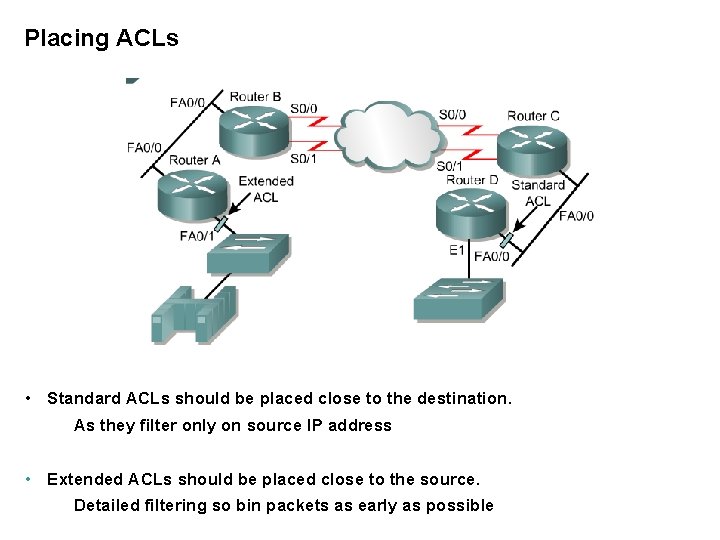
Placing ACLs • Standard ACLs should be placed close to the destination. As they filter only on source IP address • Extended ACLs should be placed close to the source. Detailed filtering so bin packets as early as possible

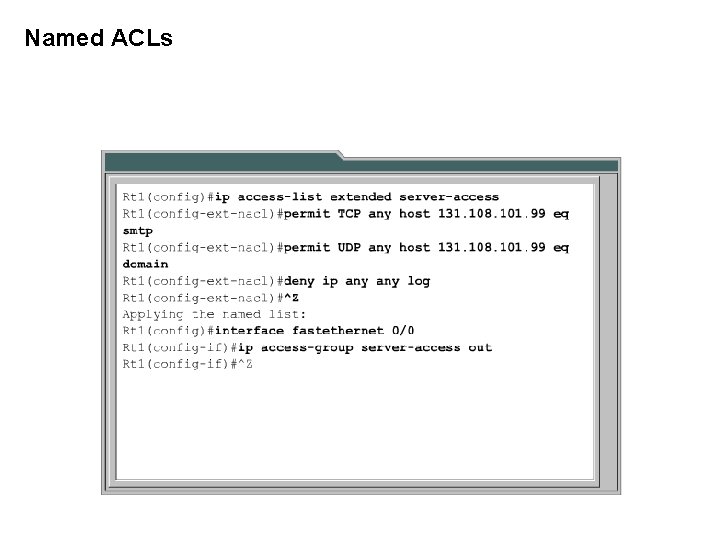
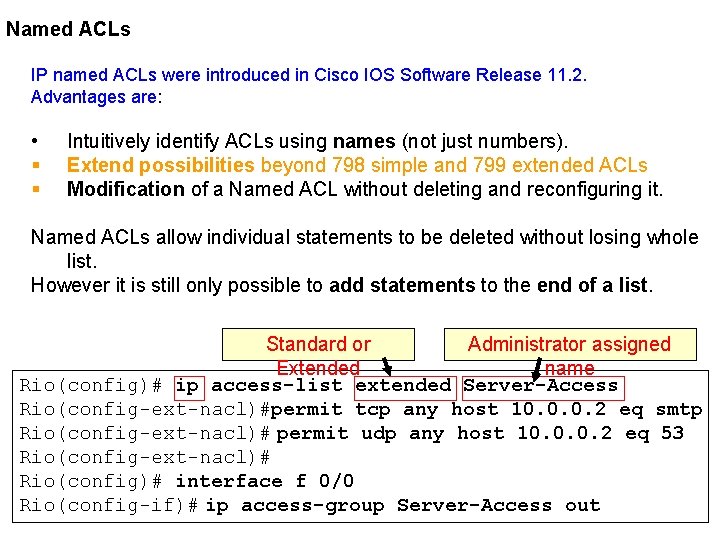
Named ACLs IP named ACLs were introduced in Cisco IOS Software Release 11. 2. Advantages are: • § § Intuitively identify ACLs using names (not just numbers). Extend possibilities beyond 798 simple and 799 extended ACLs Modification of a Named ACL without deleting and reconfiguring it. Named ACLs allow individual statements to be deleted without losing whole list. However it is still only possible to add statements to the end of a list. Standard or Administrator assigned Extended name Rio(config)# ip access-list extended Server-Access Rio(config-ext-nacl)#permit tcp any host 10. 0. 0. 2 eq smtp Rio(config-ext-nacl)# permit udp any host 10. 0. 0. 2 eq 53 Rio(config-ext-nacl)# [Control + Z] Rio(config)# interface f 0/0 Rio(config-if)# ip access-group Server-Access out

Verifying ACLs • There are many show commands that will verify the content and placement of ACLs on the router. show ip interface show access-lists Show running-config

Verifying ACLs - show run

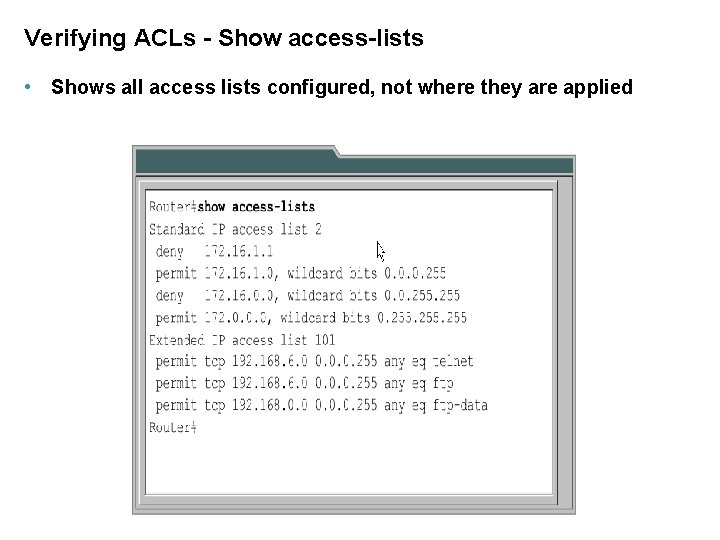
Verifying ACLs - Show access-lists • Shows all access lists configured, not where they are applied

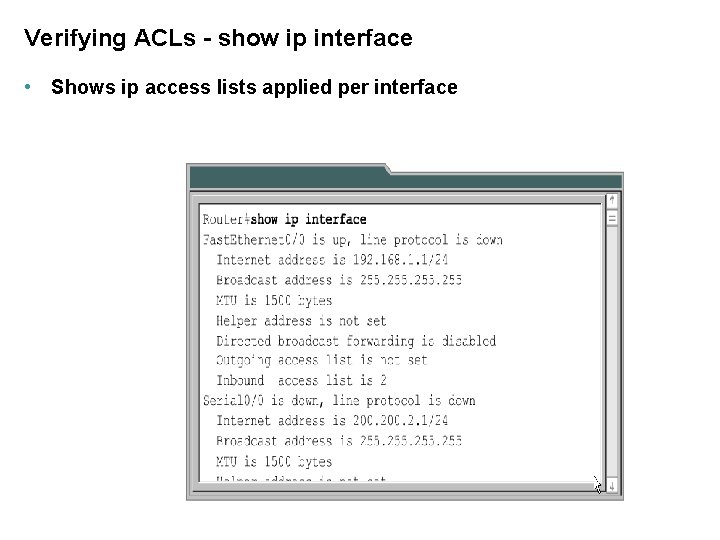
Verifying ACLs - show ip interface • Shows ip access lists applied per interface

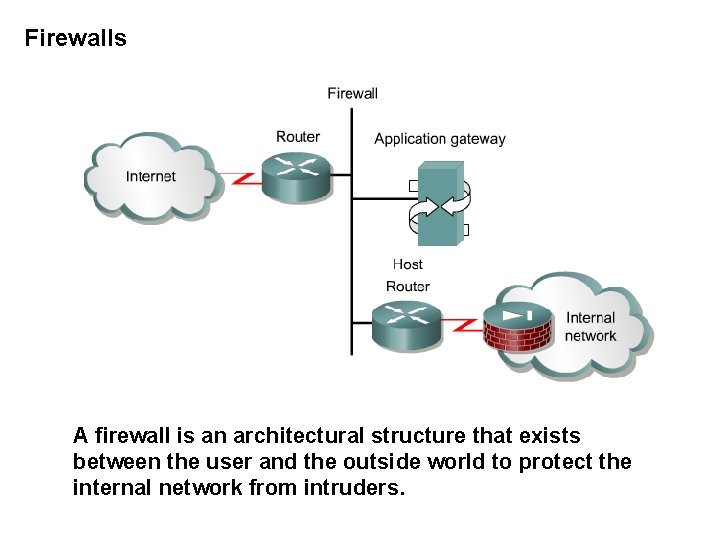
Firewalls A firewall is an architectural structure that exists between the user and the outside world to protect the internal network from intruders.

Firewalls • Use of ACLs in the firewall routers Control traffic entering or exiting a specific part of the internal network Provides basic security from the outside network into a more private area of the network Ex. If the only application that is permitted is mail, then configure ACL so that only mail packets can be allowed through the router. This protects the application gateway and avoids overwhelming it with packets that it would otherwise discard.

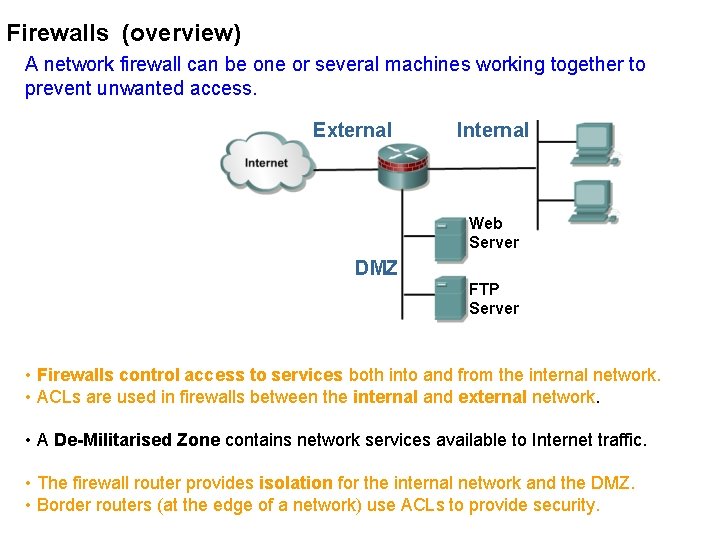
Firewalls (overview) A network firewall can be one or several machines working together to prevent unwanted access. External Internal Web Server DMZ FTP Server • Firewalls control access to services both into and from the internal network. • ACLs are used in firewalls between the internal and external network. • A De-Militarised Zone contains network services available to Internet traffic. • The firewall router provides isolation for the internal network and the DMZ. • Border routers (at the edge of a network) use ACLs to provide security.

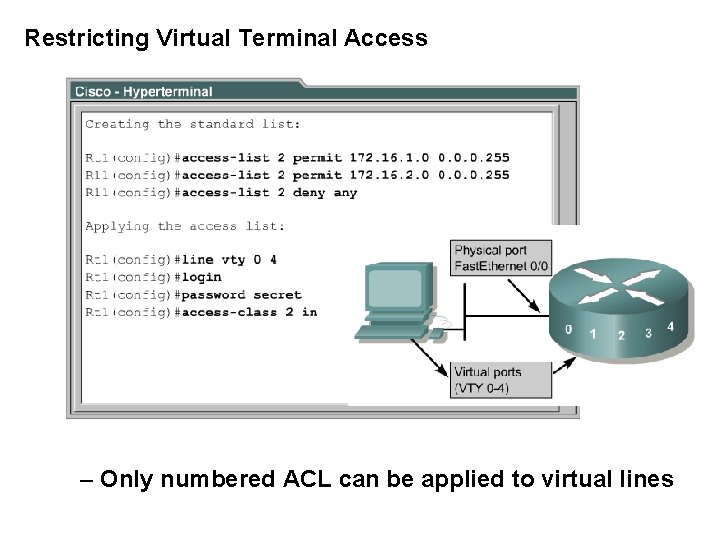
Restricting Virtual Terminal Access – Only numbered ACL can be applied to virtual lines

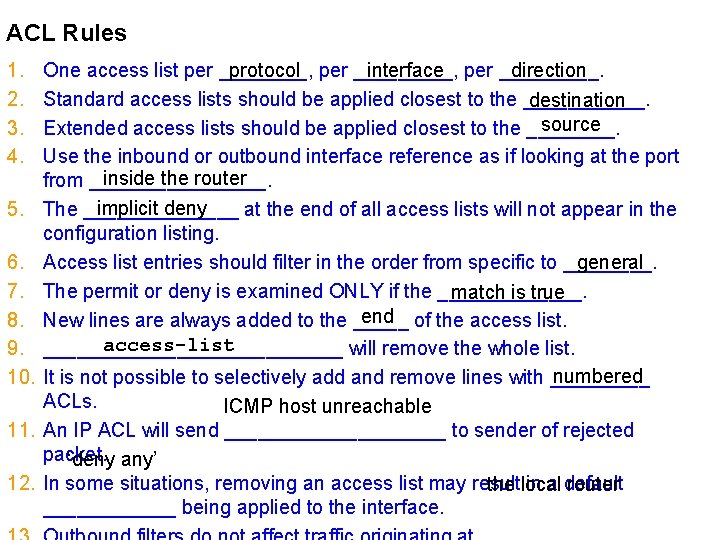
ACL Rules 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. protocol interface direction One access list per ________, per _____. Standard access lists should be applied closest to the ______. destination source Extended access lists should be applied closest to the ____. Use the inbound or outbound interface reference as if looking at the port inside the router from ________. implicit deny The _______ at the end of all access lists will not appear in the configuration listing. general Access list entries should filter in the order from specific to ____. The permit or deny is examined ONLY if the _______. match is true end New lines are always added to the _____ of the access list. no access-list [number] ______________ will remove the whole list. numbered It is not possible to selectively add and remove lines with _____ ACLs. ICMP host unreachable An IP ACL will send __________ to sender of rejected packet. ‘deny any’ In some situations, removing an access list may result in a default the local router ______ being applied to the interface.

ACL Summary • There should be one access list per protocol per direction. • Never work with an access list that is actively applied. • Standard access lists should be applied closest to the destination. • • Extended access lists should be applied closest to the source. A text editor should be used to create comments that outline the logic. Then fill in the statements that perform the logic. • • The inbound or outbound interface should be referenced as if looking at the port from inside the router. New lines are always added to the end of the access list. A no access-list x command will remove the whole list. It is not possible to selectively add and remove lines with numbered ACLs • Statements are processed sequentially from the top of the list to the bottom until a match is found. If no match is found then the packet is denied, and discarded. • An IP access list will send an ICMP host unreachable message to the sender of the rejected packet and will discard the packet in the bit bucket. • There is an implicit deny at the end of all access lists. This will not appear in the configuration listing. • • Access list entries should filter in the order from specific to general. Specific hosts should be denied first, and groups or general filters should come last. An access list should be removed carefully. If an access list that is applied to a production interface is removed, some versions of IOS will apply a default deny any to the interface and all traffic will be halted. • Outbound filters do not affect traffic that originates from the local router. • The match condition is examined first. The permit or deny is examined only if the match is true.

Summary