Chapter 11 CCNA 2 Chapter 11 Access Control











- Slides: 54

Chapter 11 CCNA 2 Chapter 11 Access Control Lists : Creating ACLs, using Wildcard Mask Bits, Standard and Extended ACLs Page 1

Chapter 11 ACL – Access Control Lists ACLs are instructions that are applied to router’s interfaces. The ACLs tell what kind of packets to accept or deny. Acceptance / denial can be based on: • source address • destination address • port number ACLs are configured at the router to control access to a network or subnet. ACLs must be defined separately for each protocol; one for IP, one for IPX; one for Apple. Talk, etc. Some times they are called packet filters. Page 2

Chapter 11 Reasons to create ACLs • limit network traffic, hence increase network performance i. e. packets can be processed before other traffic • provide traffic flow - limit traffic through the network • provide for security • decide which traffic is blocked and forwarded Page 3

Chapter 11 Cisco IOS checks the packet and Upper - layer headers for • destination address • source address • protocol • port number The ACL statements are checked in sequential order and when there is a match, no more checks are made. If there are no matches, then the packet is discarded. IF additional statements are needed for an ACL, one must delete the ACL statements and re-create a new ACL. (If additional statements are added at the end, then one does not have to delete the ACL statements. ) Page 4

Chapter 11 When a packet enters an interface 1) checks if there are ACLs If there are, then tests against the conditions. If pass, then 2) checks the packet against the routing tables Then the destination interface 1) checks for ACLs If there are, then test against the conditions. If pass, then 2) sent out the interface Page 5

Chapter 11 ACL statements operate in logical, sequential order. When there is a match, the rest of the conditions are not checked. If all the ACL statements are not matched, then there is implicit deny any. access-list 10 { permit | deny } { test conditions } access-list 10 { permit | deny } { test conditions } access-list 10 deny any Page 6

Chapter 11 Two types of IP ACL : • standard - has access list value of 1 - 99 • extended - has access list value of 100 - 199 Must be in global configuration mode. Router (config) # Steps in creating ACLs: 1) create the ACL (in global configuration mode) 2) apply the ACL to an interface ACLs can be written to filter: • inbound traffic, or • outbound traffic Page 7

Where to place ACLs Chapter 11 Standard ACLs are placed as close as possible to the destination. Extended ACLs are placed as close as possible to the source. Page 8

Chapter 11 Create: Router(config)# access-list <ACL number> { permit | deny } { test conditions } Router(config)# access-list 1 permit { test conditions } Router(config)# access-list 50 deny { test conditions } Apply: At an interface: Router(config)# int E 0 Router(config-if)# { protocol } access-group <ACL number> [in | out] Out is the default if not mentioned Router(config-if)# ip access-group 1 Router(config-if)# ip access-group 50 To delete all ACL statements of an access-list Router(config)# no access-list <ACL number> Router(config)# no access-list 50 Page 9

Chapter 11 A wildcard mask is matched with an IP address or protocol address. It is a 32 bit mask divided into 4 octets, each containing 8 bits. A 0 in the mask means to check the bit. A 1 in the mask means ignore the bit. Page 10

Abbreviations Chapter 11 To permit any address: 0. 0 255 Address wildcard mask Use the abbreviation any Router(config)# access-list 1 permit 0. 0 255 Router(config)# access-list 1 permit any Page 11

Abbreviations Chapter 11 To match all the bits of IP address: EX: 172. 30. 16. 29 0. 0 Router(config)# access-list 1 permit host 172. 30. 16. 29 Page 12

Standard ACLs Chapter 11 Criteria: • block all traffic from a network • allow all traffic from a network • deny entire protocol suits Standard ACLs only check the source address. Router(config)# access-list <ACL number> { deny | permit } source [ source wildcard] [log] Page 13

Standard ACLs Chapter 11 What does this statement perform: access-list 33 permit 172. 16. 0. 0. 255 log Permits all traffic from 172. 16. 0. 0 and sends messages to the console every time the access list is hit. Page 14

Standard ACLs Chapter 11 What does this statement perform: access-list 44 deny 172. 16. 13. 7 0. 0 log Denies traffic from host 172. 16. 13. 7 and sends messages to the console every time the access list is hit. Page 15

Standard ACLs Chapter 11 What does this statement perform: access-list 55 deny 172. 16. 64. 0 0. 0. 0. 255 Denies all traffic from network 172. 16. 64. 0 Page 16

Standard ACLs Chapter 11 The log command: Prints messages to the console: includes the ACL number, whether the packet was permitted or denied, the source address, and the number of packets. The message is generated for the first packet that matches, and then at fiveminute intervals, including the number of packets permitted or denied in the prior five-minute interval. Use for debugging. Not used for live networks. Page 17

Standard ACLs Chapter 11 Example of applying the access-list (note: it is at the interface): Router(config-if)# ip access-group 33 in Router(config-if)# ip access-group 44 out Router(config-if)# ip access-group 44 Page 18

Standard ACLs Chapter 11 To monitor IP access list: (at the EXEC mode) show access-list Displays all access lists and their parameters configured on the router. (Does not show which interface the list is set on. ) show access-list <ACL number> Shows only the parameters for the access list <ACL number>. (Does not show the interface the list is set on. ) show ip access-list Shows only the IP access lists configured on the router show ip interface Shows which interfaces have access lists set. show running-config Shows the access lists and which interfaces have access lists set Page 19

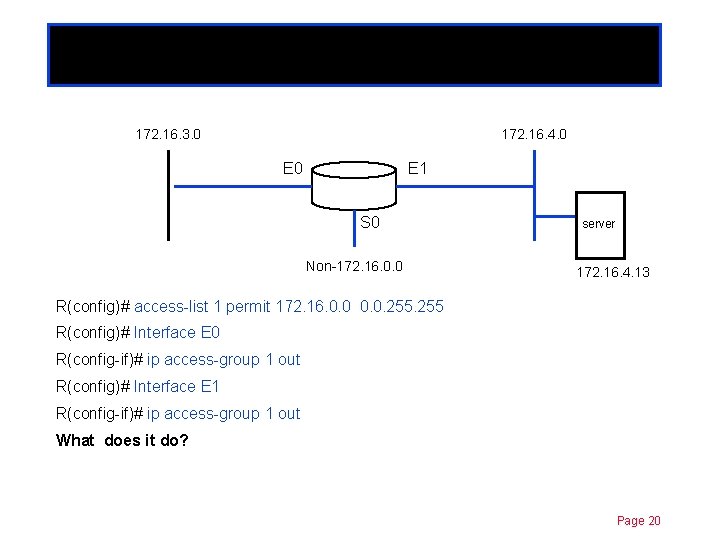
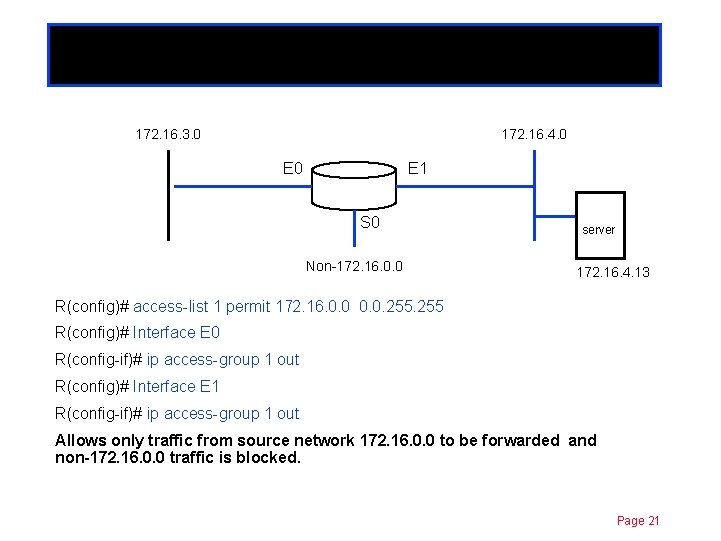
Standard ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 server 172. 16. 4. 13 R(config)# access-list 1 permit 172. 16. 0. 0. 255 R(config)# Interface E 0 R(config-if)# ip access-group 1 out R(config)# Interface E 1 R(config-if)# ip access-group 1 out What does it do? Page 20

Standard ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 server 172. 16. 4. 13 R(config)# access-list 1 permit 172. 16. 0. 0. 255 R(config)# Interface E 0 R(config-if)# ip access-group 1 out R(config)# Interface E 1 R(config-if)# ip access-group 1 out Allows only traffic from source network 172. 16. 0. 0 to be forwarded and non-172. 16. 0. 0 traffic is blocked. Page 21

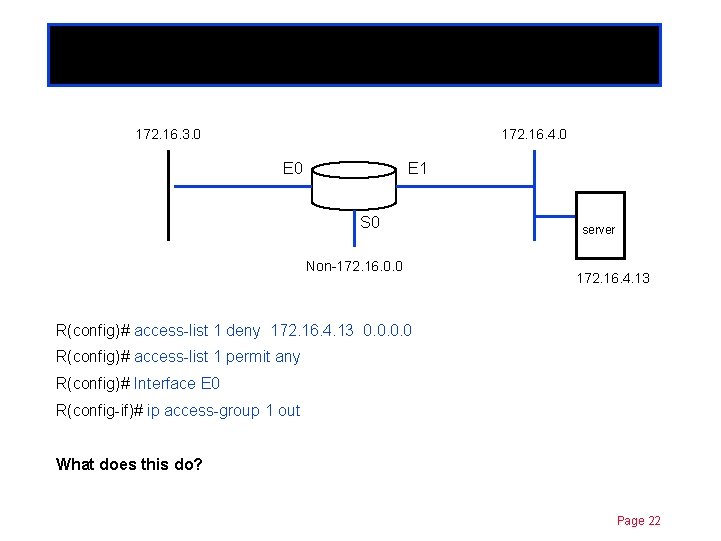
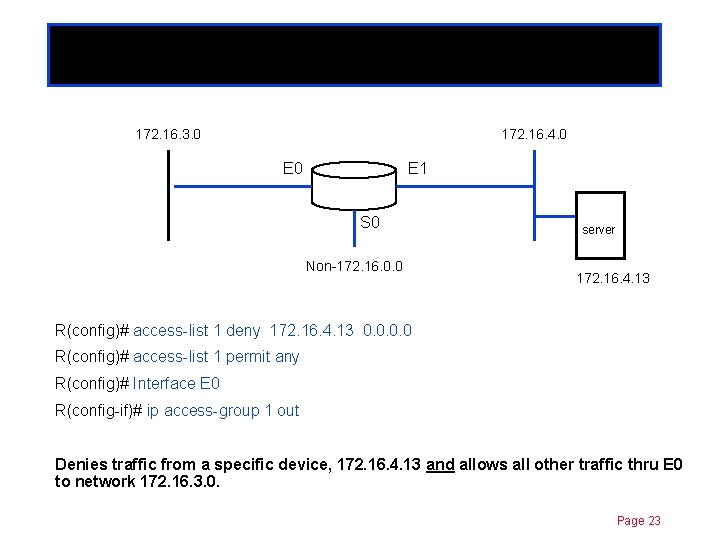
Standard ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 server 172. 16. 4. 13 R(config)# access-list 1 deny 172. 16. 4. 13 0. 0 R(config)# access-list 1 permit any R(config)# Interface E 0 R(config-if)# ip access-group 1 out What does this do? Page 22

Standard ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 server 172. 16. 4. 13 R(config)# access-list 1 deny 172. 16. 4. 13 0. 0 R(config)# access-list 1 permit any R(config)# Interface E 0 R(config-if)# ip access-group 1 out Denies traffic from a specific device, 172. 16. 4. 13 and allows all other traffic thru E 0 to network 172. 16. 3. 0. Page 23

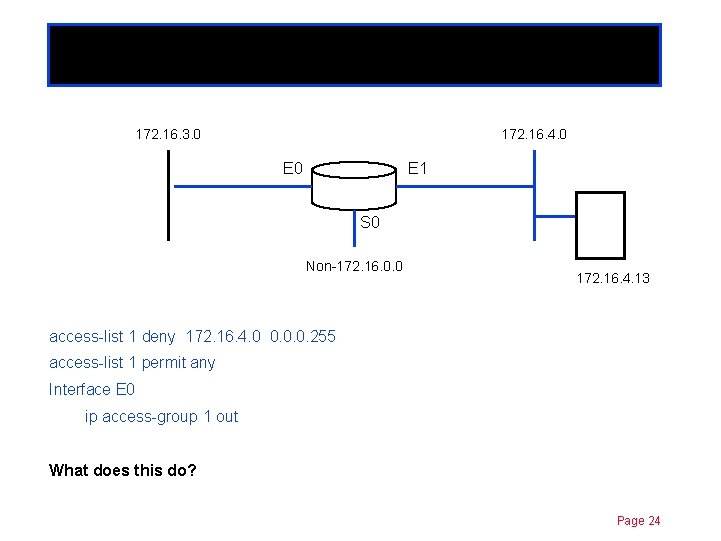
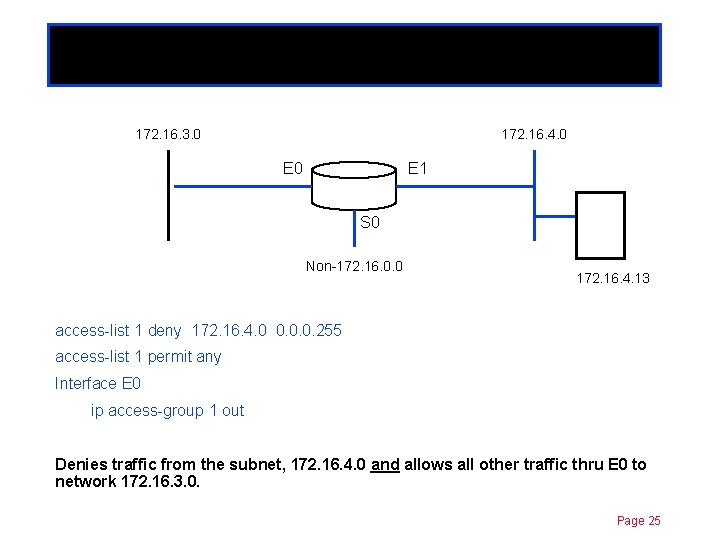
Standard ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 172. 16. 4. 13 access-list 1 deny 172. 16. 4. 0 0. 0. 0. 255 access-list 1 permit any Interface E 0 ip access-group 1 out What does this do? Page 24

Standard ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 172. 16. 4. 13 access-list 1 deny 172. 16. 4. 0 0. 0. 0. 255 access-list 1 permit any Interface E 0 ip access-group 1 out Denies traffic from the subnet, 172. 16. 4. 0 and allows all other traffic thru E 0 to network 172. 16. 3. 0. Page 25

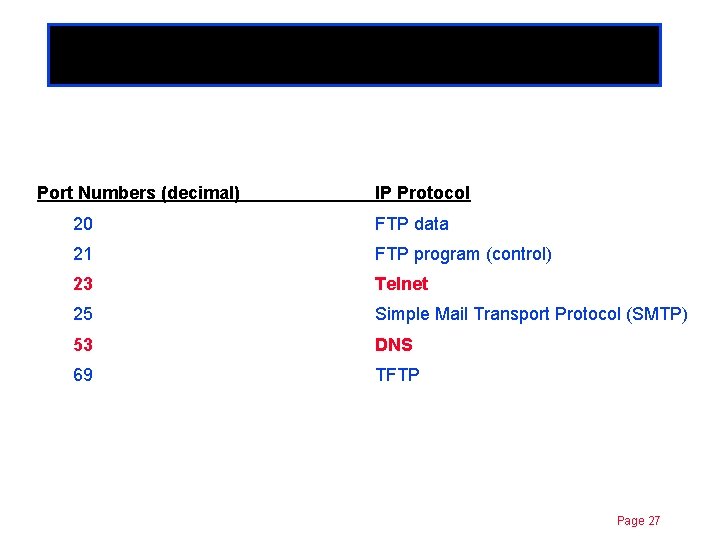
Extended ACLs Chapter 11 Criteria: • check for both source and destination packet addresses • check for specific protocol • check for specific port numbers • permit or denied pings / telnets / FTP, etc. • for IP, the ACL values range between 100 - 199 Page 26

Extended ACLs Port Numbers (decimal) Chapter 11 IP Protocol 20 FTP data 21 FTP program (control) 23 Telnet 25 Simple Mail Transport Protocol (SMTP) 53 DNS 69 TFTP Page 27

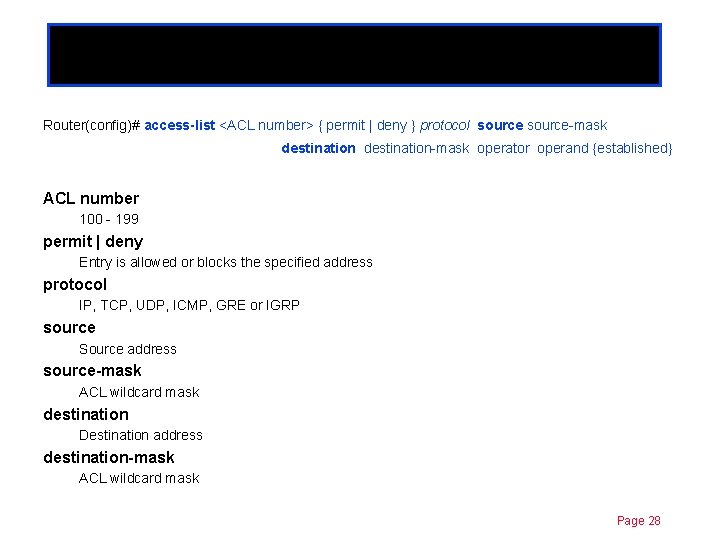
Extended ACLs Chapter 11 Router(config)# access-list <ACL number> { permit | deny } protocol source-mask destination-mask operator operand {established} ACL number 100 - 199 permit | deny Entry is allowed or blocks the specified address protocol IP, TCP, UDP, ICMP, GRE or IGRP source Source address source-mask ACL wildcard mask destination Destination address destination-mask ACL wildcard mask Page 28

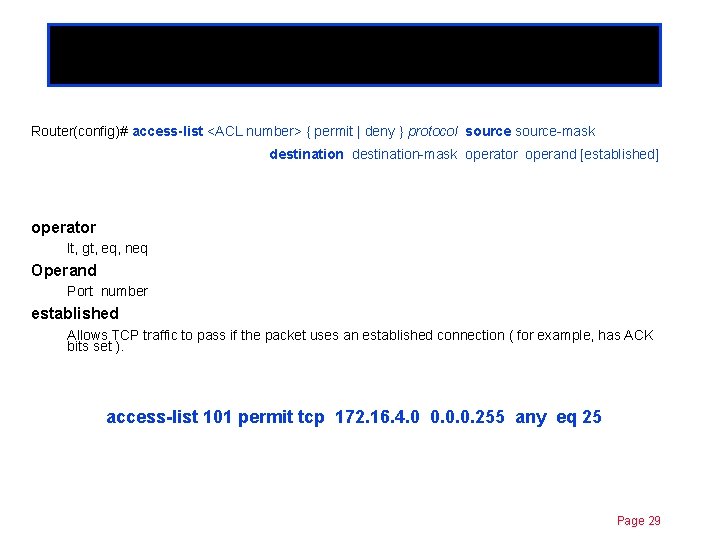
Extended ACLs Chapter 11 Router(config)# access-list <ACL number> { permit | deny } protocol source-mask destination-mask operator operand [established] operator lt, gt, eq, neq Operand Port number established Allows TCP traffic to pass if the packet uses an established connection ( for example, has ACK bits set ). access-list 101 permit tcp 172. 16. 4. 0 0. 0. 0. 255 any eq 25 Page 29

Extended ACLs Chapter 11 Assign the ACL to an interface: Router(config-if)# ip access-group <ACL number> { in | out } NOTE: out is the default (though with the present IOS, you have to put out). Router(config)# int E 0 Router(config-if)# ip access-group 101 in Page 30

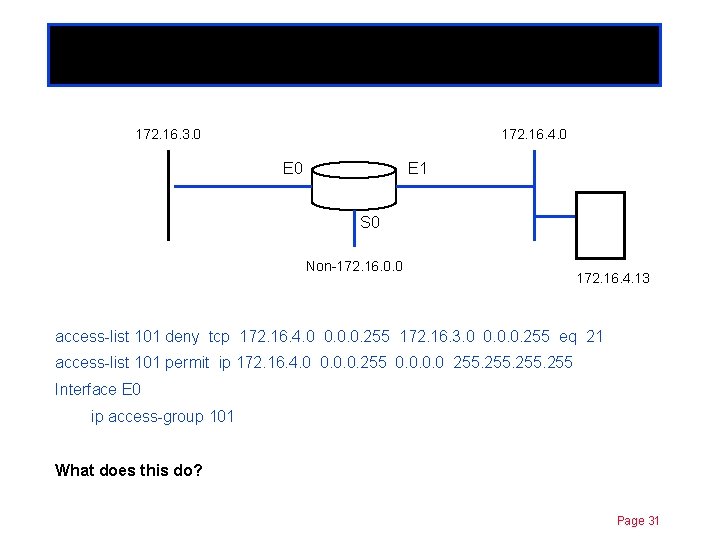
Extended ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 172. 16. 4. 13 access-list 101 deny tcp 172. 16. 4. 0 0. 0. 0. 255 172. 16. 3. 0 0. 0. 0. 255 eq 21 access-list 101 permit ip 172. 16. 4. 0 0. 0. 0. 255 0. 0 255 Interface E 0 ip access-group 101 What does this do? Page 31

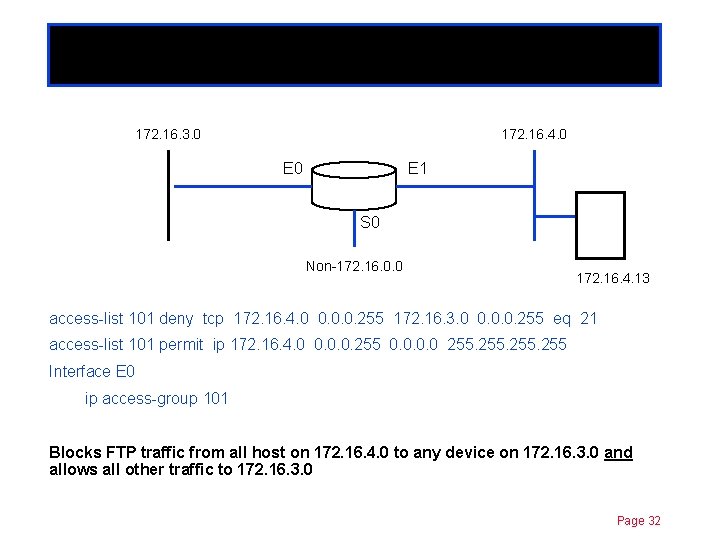
Extended ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 172. 16. 4. 13 access-list 101 deny tcp 172. 16. 4. 0 0. 0. 0. 255 172. 16. 3. 0 0. 0. 0. 255 eq 21 access-list 101 permit ip 172. 16. 4. 0 0. 0. 0. 255 0. 0 255 Interface E 0 ip access-group 101 Blocks FTP traffic from all host on 172. 16. 4. 0 to any device on 172. 16. 3. 0 and allows all other traffic to 172. 16. 3. 0 Page 32

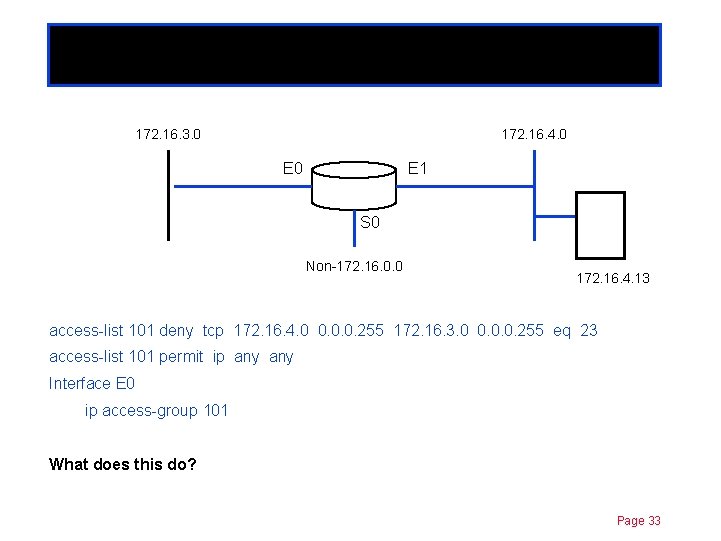
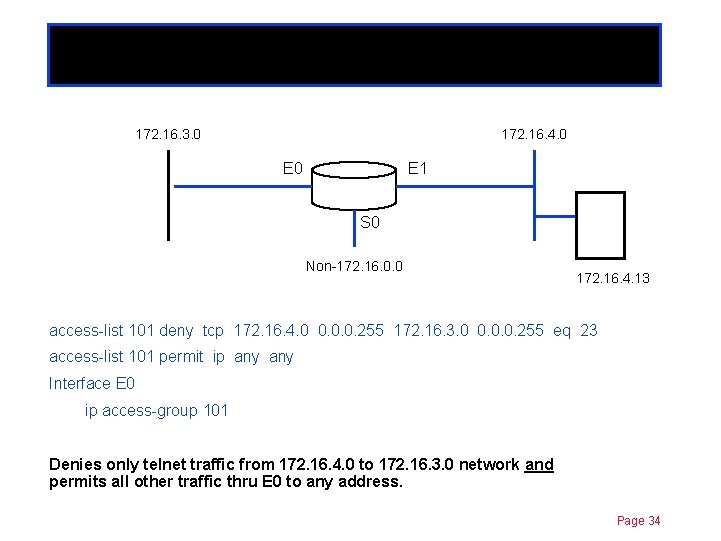
Extended ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 172. 16. 4. 13 access-list 101 deny tcp 172. 16. 4. 0 0. 0. 0. 255 172. 16. 3. 0 0. 0. 0. 255 eq 23 access-list 101 permit ip any Interface E 0 ip access-group 101 What does this do? Page 33

Extended ACLs 172. 16. 3. 0 Chapter 11 172. 16. 4. 0 E 1 S 0 Non-172. 16. 0. 0 172. 16. 4. 13 access-list 101 deny tcp 172. 16. 4. 0 0. 0. 0. 255 172. 16. 3. 0 0. 0. 0. 255 eq 23 access-list 101 permit ip any Interface E 0 ip access-group 101 Denies only telnet traffic from 172. 16. 4. 0 to 172. 16. 3. 0 network and permits all other traffic thru E 0 to any address. Page 34

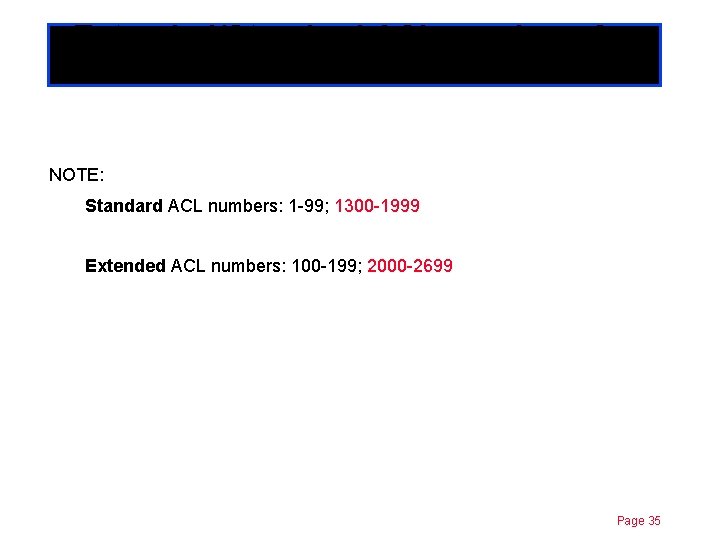
Extended/Standard ACL numbers Chapterfor 11 IP NOTE: Standard ACL numbers: 1 -99; 1300 -1999 Extended ACL numbers: 100 -199; 2000 -2699 Page 35

Chapter 11 Extended/Standard ACL One can not add ACL statements to the access-list (except at the end of the list). The access list must be deleted first, and then rewritten. That is why it is a good idea to first write your access-list in text (using Notepad), and then transfer it to your router. Outbound filters do not affect traffic originating from the local router! Page 36

Chapter 11 Configuring Named ACLs NOTE: • named ACLs are not compatible with Cisco IOS release prior to Release 11. 2 • cannot use the same name for multiple ACLs. Ex. Can’t specify a standard ACL named XYZ and an extended ACL with same name. • can be used both for standard and extended • use an alphanumeric string instead of the ACL number (1 - 199 ) • use Named ACLs to intuitively identify ACLs using an alphanumeric name • use Named ACLs when having more than 99 standard and 100 extended ACLs to be configured in a router for a given protocol Page 37

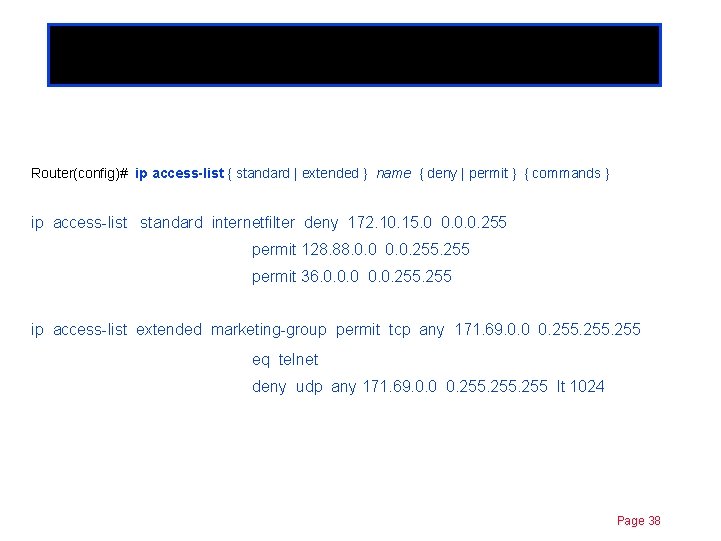
Chapter 11 Configuring Named ACLs Router(config)# ip access-list { standard | extended } name { deny | permit } { commands } ip access-list standard internetfilter deny 172. 10. 15. 0 0. 0. 0. 255 permit 128. 88. 0. 0. 255 permit 36. 0. 0. 0. 255 ip access-list extended marketing-group permit tcp any 171. 69. 0. 0 0. 255 eq telnet deny udp any 171. 69. 0. 0 0. 255 lt 1024 Page 38

Named ACL Chapter 11 A named ACL will allow the deletion of statements, but will only allow for the statements to be inserted a the end of the list. Page 39

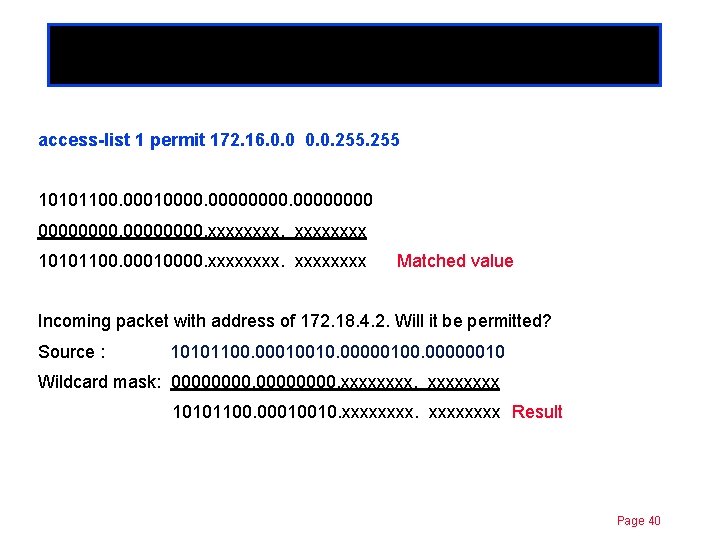
More Details Chapter 11 access-list 1 permit 172. 16. 0. 0. 255 10101100. 000100000000. xxxx 10101100. 00010000. xxxxxxxx Matched value Incoming packet with address of 172. 18. 4. 2. Will it be permitted? Source : 10101100. 00010010. 00000100. 00000010 Wildcard mask: 00000000. xxxx 10101100. 00010010. xxxxxxxx Result Page 40

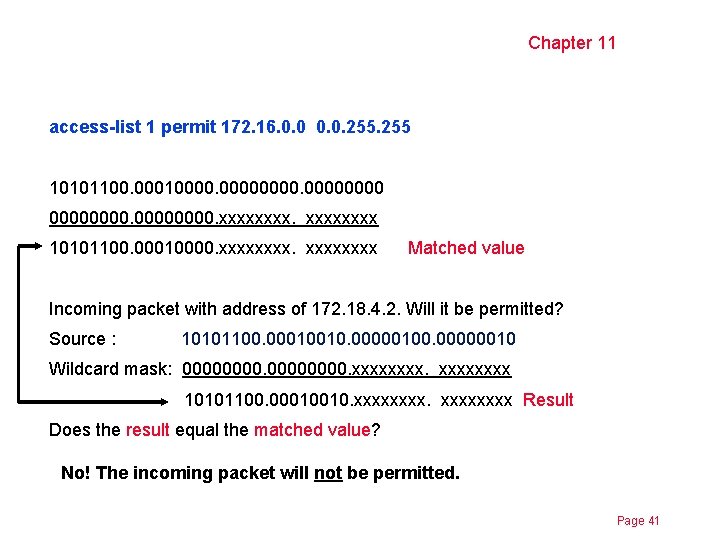
Chapter 11 access-list 1 permit 172. 16. 0. 0. 255 10101100. 000100000000. xxxx 10101100. 00010000. xxxxxxxx Matched value Incoming packet with address of 172. 18. 4. 2. Will it be permitted? Source : 10101100. 00010010. 00000100. 00000010 Wildcard mask: 00000000. xxxx 10101100. 00010010. xxxxxxxx Result Does the result equal the matched value? No! The incoming packet will not be permitted. Page 41

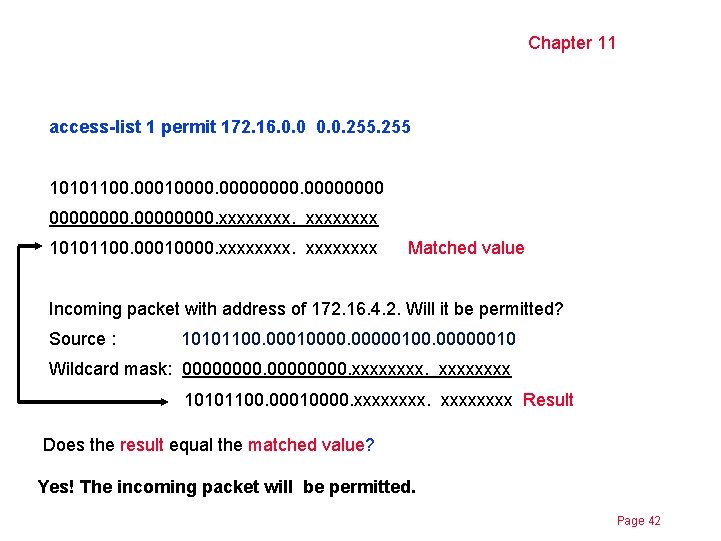
Chapter 11 access-list 1 permit 172. 16. 0. 0. 255 10101100. 000100000000. xxxx 10101100. 00010000. xxxxxxxx Matched value Incoming packet with address of 172. 16. 4. 2. Will it be permitted? Source : 10101100. 000100000100. 00000010 Wildcard mask: 00000000. xxxx 10101100. 00010000. xxxxxxxx Result Does the result equal the matched value? Yes! The incoming packet will be permitted. Page 42

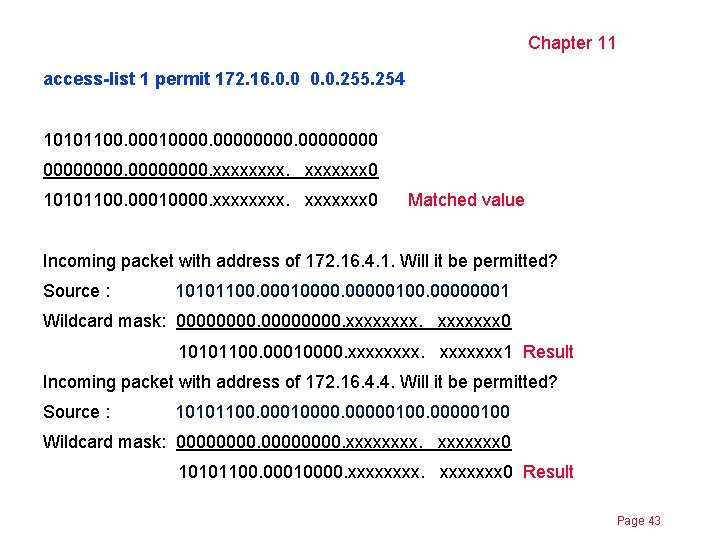
Chapter 11 access-list 1 permit 172. 16. 0. 0. 255. 254 10101100. 000100000000. xxxxxxx 0 10101100. 00010000. xxxxxxx 0 Matched value Incoming packet with address of 172. 16. 4. 1. Will it be permitted? Source : 10101100. 000100000100. 00000001 Wildcard mask: 00000000. xxxxxxx 0 10101100. 00010000. xxxxxxx 1 Result Incoming packet with address of 172. 16. 4. 4. Will it be permitted? Source : 10101100. 000100000100 Wildcard mask: 00000000. xxxxxxx 0 10101100. 00010000. xxxxxxx 0 Result Page 43

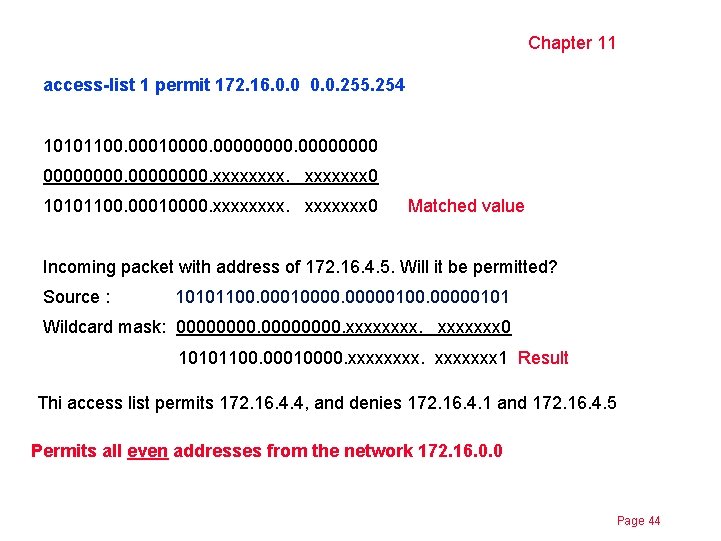
Chapter 11 access-list 1 permit 172. 16. 0. 0. 255. 254 10101100. 000100000000. xxxxxxx 0 10101100. 00010000. xxxxxxx 0 Matched value Incoming packet with address of 172. 16. 4. 5. Will it be permitted? Source : 10101100. 000100000101 Wildcard mask: 00000000. xxxxxxx 0 10101100. 00010000. xxxxxxx 1 Result Thi access list permits 172. 16. 4. 4, and denies 172. 16. 4. 1 and 172. 16. 4. 5 Permits all even addresses from the network 172. 16. 0. 0 Page 44

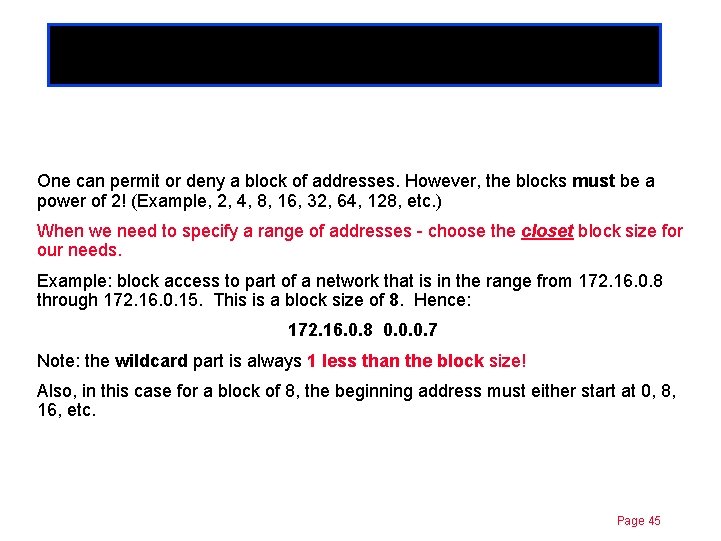
Chapter 11 Permit/Deny blocks of addresses One can permit or deny a block of addresses. However, the blocks must be a power of 2! (Example, 2, 4, 8, 16, 32, 64, 128, etc. ) When we need to specify a range of addresses - choose the closet block size for our needs. Example: block access to part of a network that is in the range from 172. 16. 0. 8 through 172. 16. 0. 15. This is a block size of 8. Hence: 172. 16. 0. 8 0. 0. 0. 7 Note: the wildcard part is always 1 less than the block size! Also, in this case for a block of 8, the beginning address must either start at 0, 8, 16, etc. Page 45

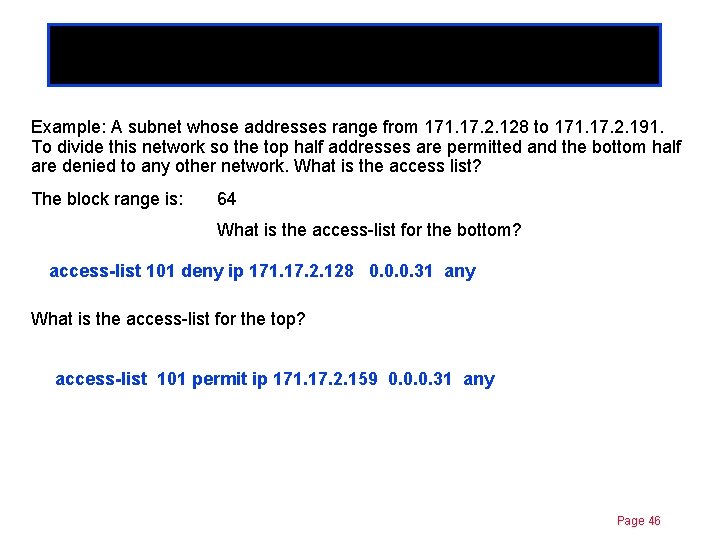
Chapter 11 Permit/Deny blocks of addresses Example: A subnet whose addresses range from 171. 17. 2. 128 to 171. 17. 2. 191. To divide this network so the top half addresses are permitted and the bottom half are denied to any other network. What is the access list? The block range is: 64 What is the access-list for the bottom? access-list 101 deny ip 171. 17. 2. 128 0. 0. 0. 31 any What is the access-list for the top? access-list 101 permit ip 171. 17. 2. 159 0. 0. 0. 31 any Page 46

Chapter 11 Permit/Deny blocks of addresses What does this do? access-list 10 deny 172. 16. 64. 0 0. 0. 63. 255 Denies a block of 64 subnetworks starting at 172. 16. 64. 0 Page 47

Virtual Terminal ACL Chapter 11 To block access through the vty ports in order to control telnet sessions into the router. Write the ACL as usual but use access-class to apply it. Example: Router(config t)# access-list 1 permit 172. 16. 1. 0 0. 0. 0. 255 Router(config t)# line vty 0 4 Router(config-line)# login Router(config-line)# password cisco Router(config-line)# access-class 1 in Note: only numbered access lists can be applied to virtual lines! Page 48

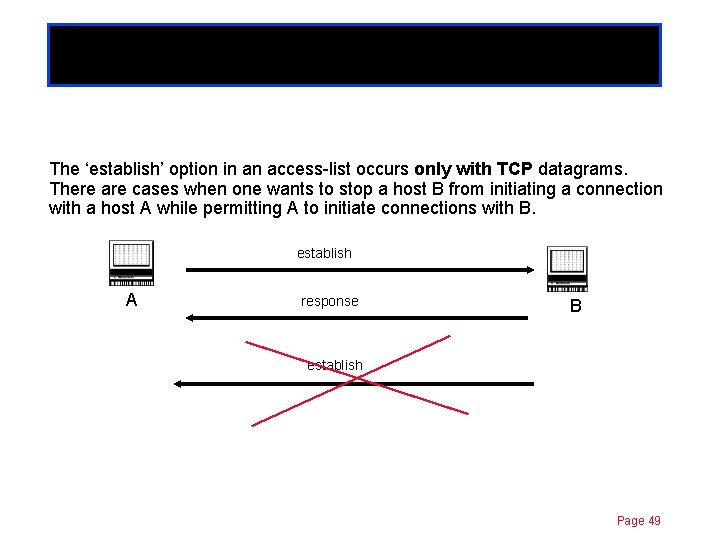
Established option Chapter 11 The ‘establish’ option in an access-list occurs only with TCP datagrams. There are cases when one wants to stop a host B from initiating a connection with a host A while permitting A to initiate connections with B. establish A response B establish Page 49

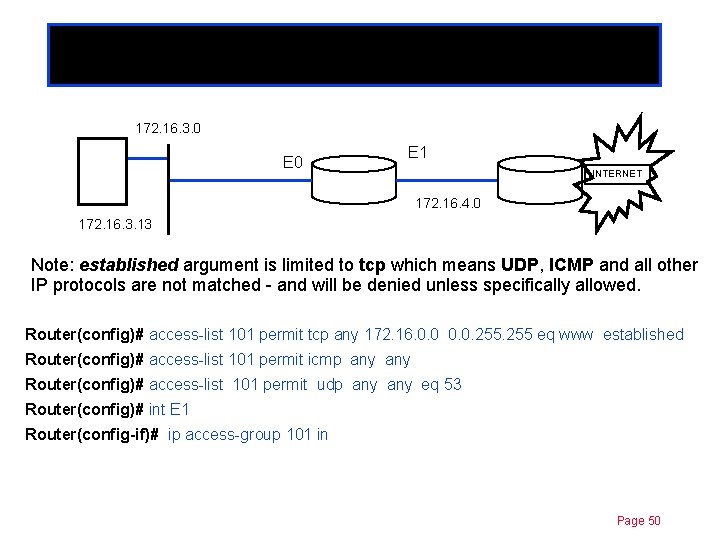
Established option Chapter 11 172. 16. 3. 0 E 1 INTERNET 172. 16. 4. 0 172. 16. 3. 13 Note: established argument is limited to tcp which means UDP, ICMP and all other IP protocols are not matched - and will be denied unless specifically allowed. Router(config)# access-list 101 permit tcp any 172. 16. 0. 0. 255 eq www established Router(config)# access-list 101 permit icmp any Router(config)# access-list 101 permit udp any eq 53 Router(config)# int E 1 Router(config-if)# ip access-group 101 in Page 50

Where to place ACLs? Chapter 11 Cisco’s definition: Standard ACL Put the ACL as near the destination as possible. • one might not have access to all the routers Extended ACL Put the ACL as close as possible to the source of the traffic denied. Page 51

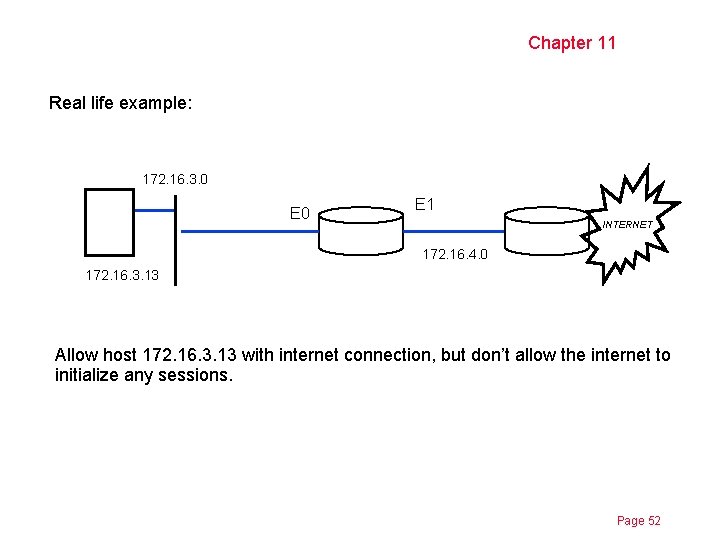
Chapter 11 Real life example: 172. 16. 3. 0 E 1 INTERNET 172. 16. 4. 0 172. 16. 3. 13 Allow host 172. 16. 3. 13 with internet connection, but don’t allow the internet to initialize any sessions. Page 52

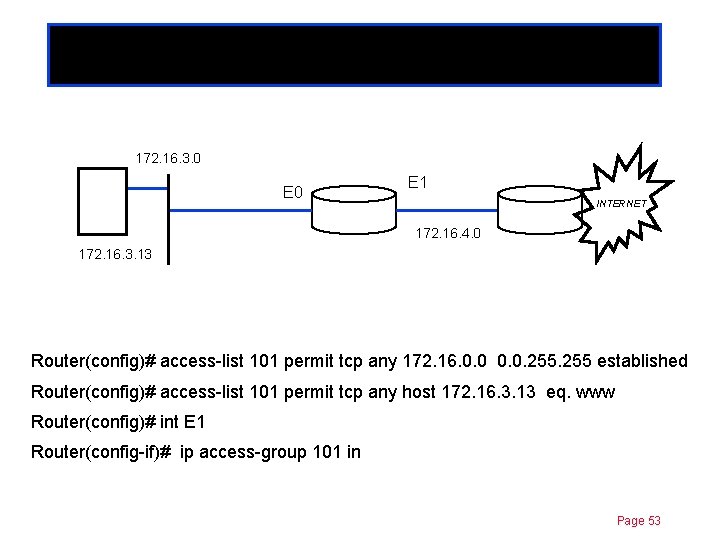
Established option Chapter 11 172. 16. 3. 0 E 1 INTERNET 172. 16. 4. 0 172. 16. 3. 13 Router(config)# access-list 101 permit tcp any 172. 16. 0. 0. 255 established Router(config)# access-list 101 permit tcp any host 172. 16. 3. 13 eq. www Router(config)# int E 1 Router(config-if)# ip access-group 101 in Page 53

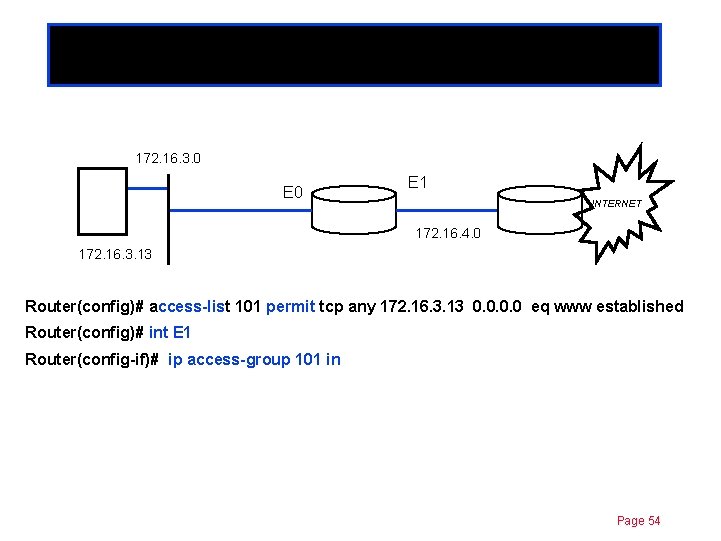
Established option Chapter 11 172. 16. 3. 0 E 1 INTERNET 172. 16. 4. 0 172. 16. 3. 13 Router(config)# access-list 101 permit tcp any 172. 16. 3. 13 0. 0 eq www established Router(config)# int E 1 Router(config-if)# ip access-group 101 in Page 54