CCNA DISCOVERY 1 MODULE 7 WIRELESS TECHNOLOGIES 1






















































































- Slides: 100

CCNA DISCOVERY 1 • MODULE 7 – WIRELESS TECHNOLOGIES

1. What do wireless technologies use to carry information between devices? • Electromagnetic waves

2. What are the most common wave lengths used for public wireless communication? • Infrared (IR) • Radio Frequency (RF)

3. Which wavelength is relatively low energy and cannot penetrate through walls or other obstacles? • IR

4. Which wavelength has the greatest range? • RF

5. What ranges can be used with very few restrictions? • 900 MHz, 2. 4 GHZ, 5 GHz

6. What are the ranges with the fewest restrictions called? • Industrial, Scientific, and Medical (ISM)

7. What has made Bluetooth technology the preferred method for connection computer peripherals? • One-to-many communications

7. 1. 1. 4 Activity

8. What is one of the main advantages of wireless technology? • The ability to provide anytime, anywhere connectivity

9. What is a hotspot? • The implementation of wireless in public locations

10. What are the benefits of wireless LAN technology? • • • Mobility Scalability Flexibility cost savings reduce installation time reliability in harsh environments

11. What are the limitations of wireless LAN technology? • Interference • network and data security • technology

12. What two techniques have been developed to help secure wireless transmissions? • Encryption and authentication

13. What are three major categories of wireless networks? • WPAN – Wireless Personal Area Network • WLAN – Wireless Local Area Network • WWAN – Wireless Wide Area Network

14. What is the smallest wireless network, which is used to connect various peripheral devices? • WPAN

15. What does an access point do? • Provides a connection between wireless hosts and hosts on an Ethernet wired network

16. What technologies does the WWAN use? • Code Division Multiple Access (CDMA) or Global System for Mobile Communications (GSM)

17. What is a good example of a WWAN? • Cell phone network

7. 1. 3. 3 Activity

18. What do wireless standards ensure? • Specify the RF spectrum used, data rates, and how the information is transmitted

19. What is the main organization responsible for the creation of wireless technical standards? • IEEE

20. What IEEE standard governs the WLAN environment? • 802. 11

21. What are the current standards for the WLAN environment? • 802. 11 a, 802. 11 b, 802. 11 g, 802. 11 n

22. What organization is responsible for testing wireless LAN devices from different manufacturers? • WI-FI Alliance

23. What does the Wi-Fi logo on a device mean? • The equipment meets standards and should interoperate with other devices of the same standard

24. Complete the Common IEEE WLAN Standards Chart

25. What is a STA? • A wireless client/station

26. What do antennas do? • increase output signal strength from a wireless device • receives wireless signals from other devices

27. What is an increase in signal strength from an antenna known as? • gain

28. How are antenna classified? • According to the way they radiate the signal

29. What is the difference between a directional antenna and an omni-directional antenna? • Directional antenna concentrate signal strength in one direction; omni-directional emit equally in all directions

30. Which antenna type can achieve greater transmission distances? • directional

7. 2. 2. 3 Activity

31. How do you ensure that wireless components connect to the appropriate WLAN? • SSID – Service Set Identifier

32. What is a case-sensitive, alpha-numeric string that can be up to 32 characters? • SSID

33. What is the SSID used for? • To tell wireless devices which LAN they belong to and with which other devices they can communicate

34. What are the two basic forms of WLAN installations? • Ad hoc • Infrastructure mode

35. What is the simplest form of a wireless network? • Ad-hoc

36. How is an ad-hoc network created? • Connecting two or more wireless clients together in a peer-to-peer network

37. What is the mode of wireless communication most often used in the home and business environment? • Infrastructure

38. What controls all communications and ensures that all STAs have equal access to the media on infrastructure mode? • Access Point

39. What is the area covered by a single access point known as? • Basic Service Set (BSS)

40. What is the smallest building block of a WLAN? • BSS

41. What is an Extended Service Set (ESS)? • Multiple access points in separate BSS

42. In order to allow movement between the cells without the loss of signal, how much must BSS’s overlap? • 10%

7. 2. 3. 4 Activity

43. How are the conversations between sender and receiver controlled? • Through channels

44. What does Wireless technology use to avoid collisions? • CSMA/CA – Carrier Sense Multiple access with Collision Avoidance

45. What is a CTS (Clear to Send)? • A message indicating that the device may transmit on the channel

46. What is an ACK (acknowledgement)? • A transmission control character that confirms a transmitted message was received uncorrupted or without errors or that the receiving station is ready to accept transmissions

47. Who receives the ACK? • All devices within the BSS

7. 2. 4. 3 Activity

48. When should basic configuration tasks be conducted? • Before the access point is connected to a live network

49. What does the type of mode enabled on the access point depend on? • The type of host connecting to it

50. What happens if you select mixed mode? • Network performance will decrease

51. What must adjacent BSSs use in order to optimize throughput? • Non-overlapping channels

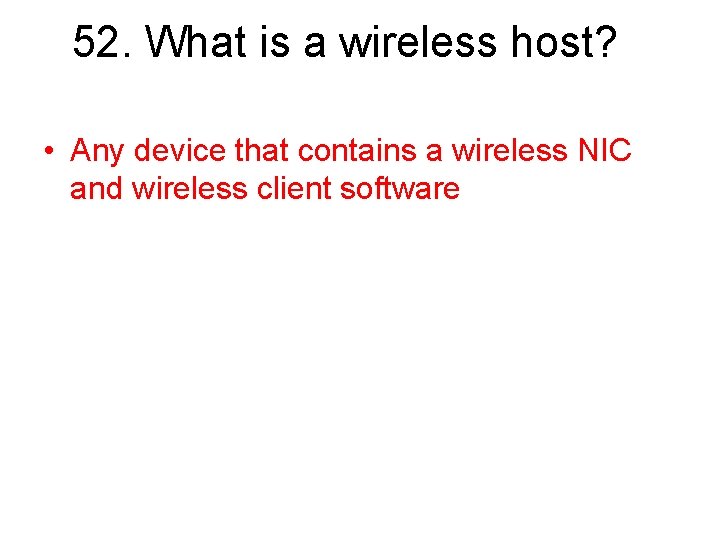
52. What is a wireless host? • Any device that contains a wireless NIC and wireless client software

53. What is basic management software that can control most wireless client configurations? • Windows XP wireless client software

54. What are some of the features available with standalone wireless utility software? • Link information, profiles, site survey

55. Is it possible for wireless utility software and Windows XP client software to manage the wireless connection at the same time • YES or NO

56. What feature displays the current signal strength and quality of the wireless signal? • Link information

57. What is one of the most common tests for verifying successful data transmission? • Ping

58. What does a successful ping tell you? • Data transmission is possible

59. What is one of the primary benefits of wireless networking? • Ease and convenience of connecting devices

60. What is one easy way to gain entry to a wireless network? • Through the network name or SSID

61. How can you make the network non-public? • Turn off the SSID broadcast feature

62. Why should you change the default settings? • So that attackers cannot identify and infiltrate the network

63. What is one way to limit access to your wireless network? • Control exactly which devices can gain access to your network

64. What is MAC address filtering? • Using the MAC address to identify which devices are allowed to connect to the wireless network

65. What happens if the MAC address is not located in the database? • The device will not be allowed to connect to or communicate across the wireless network

66. What is authentication? • The process of permitting entry to a network based on a set of credentials

67. What is the most common form of authentication? • The use of a username and password

68. What are three types of wireless authentication methods? • open authentication • PSK • EAP

69. What is open authentication? • All clients are able to associate

70. What is PSK (pre-shared key) authentication? • One-way authentication both the access point and client must be configured with the same key or secret word

71. What is EAP (Extensible Authentication Protocol)? • Two-way authentication as well as user authentication

72. If MAC address filtering and authentication are enabled, which occurs first? • authentication

73. What is encryption? • The process of transferring data so that even if it is intercepted, it is unusable

74. What is WEP (Wired Equivalency Protocol)? • An advanced security feature that encrypts network traffic as it travels through the air

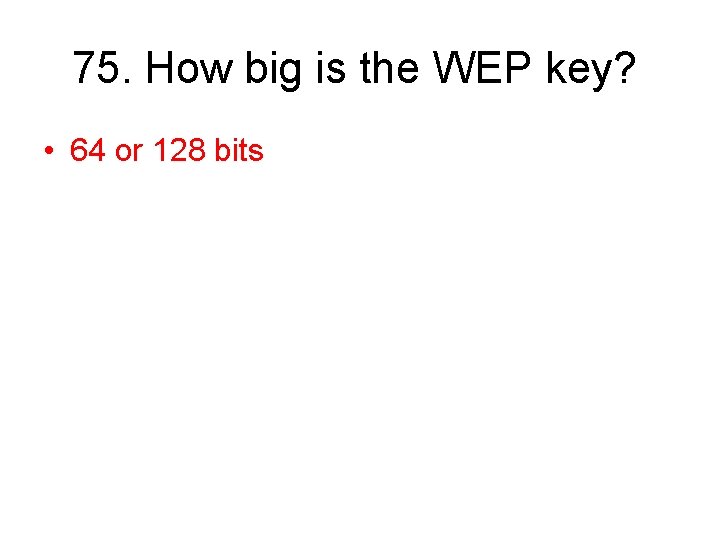
75. How big is the WEP key? • 64 or 128 bits

76. What is a passphrase? • An easy way to remember the word or phrase to automatically generate a key

77. How is WPA (Wi-Fi Protected Access) different than WEP? • WPA generates a new, dynamic key each time a client establishes a connection with the access point

78. Why is WPA considered more secure than WEP? • It is more difficult to crack

7. 3. 4. 3 Activity

79. What is traffic filtering? • Blocks undesirable traffic from entering or leaving the wireless network

80. What things should be included when planning a network installation? • • the type of wireless standard to be used the most efficient layout of devices an installation and security plan a strategy for backing up and updating the firmware for the wireless device

81. What are the most common factors to consider when determining which WLAN standards to use? • Bandwidth requirements, coverage areas, existing implementation, and cost

82. What is the best way to learn end- user requirements? • Ask questions

83. Which wireless standard supports a larger BBS? • 802. 11 b/g/n

84. What is a benefit of a larger BBS? • Less equipment and a lower cost of implementation

85. What is Total Cost of Ownership (TCO)? • The purchase of the equipment as well as installation and support costs

86. What are some of the more basic security measures? • change default values for the SSID • disable broadcast SSID • configure MAC address filtering

87. What are the two ways to restore factory defaults? • select restore factory defaults from appropriate menu • press and hold the reset button for 30 seconds

7. 4. 3. 2 Activity

88. Where is the operating system on most integrated routers stored? • In firmware

89. If the update process is interrupted before completion, what happens to the drive? • It may become inoperable

90. What is the process of updating firmware on an integrated router? • determine the version of the currently installed firmware • download the updated version of the firmware • select firmware upgrade feature in GUI

7. 4. 4. 2 Activity
