APPLICATION LAYER FTP DNS HTTP SMTP WWW Presented




















- Slides: 56

APPLICATION LAYER: FTP, DNS, HTTP, SMTP, WWW Presented By: Ghouse Taj Khan Prasanjit Behera Gouri shankar Shetty Abhilasa Moharana Biswanath Mahapatra

OBJECTIVE: § § § Define the application layer as the source and destination of data for communication across networks. Explain the role of protocols in supporting communication between server and client processes. Describe the features, operation, and use of wellknown TCP/IP application layer services (HTTP, DNS, SMTP).

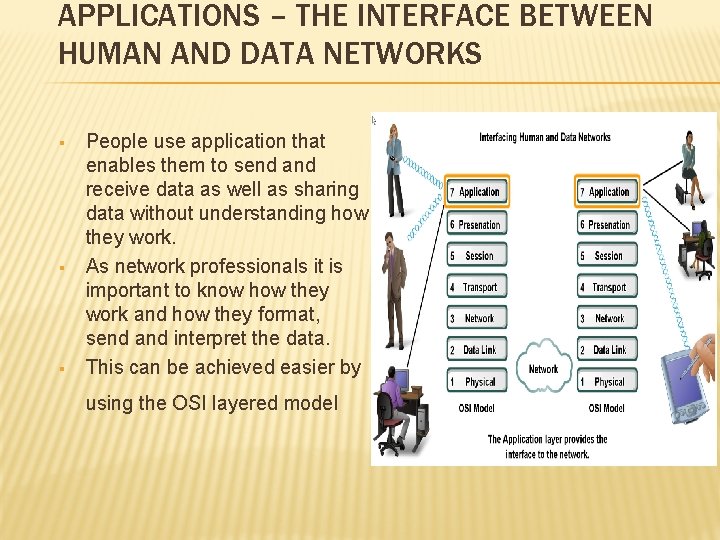
APPLICATIONS – THE INTERFACE BETWEEN HUMAN AND DATA NETWORKS § § § People use application that enables them to send and receive data as well as sharing data without understanding how they work. As network professionals it is important to know how they work and how they format, send and interpret the data. This can be achieved easier by using the OSI layered model

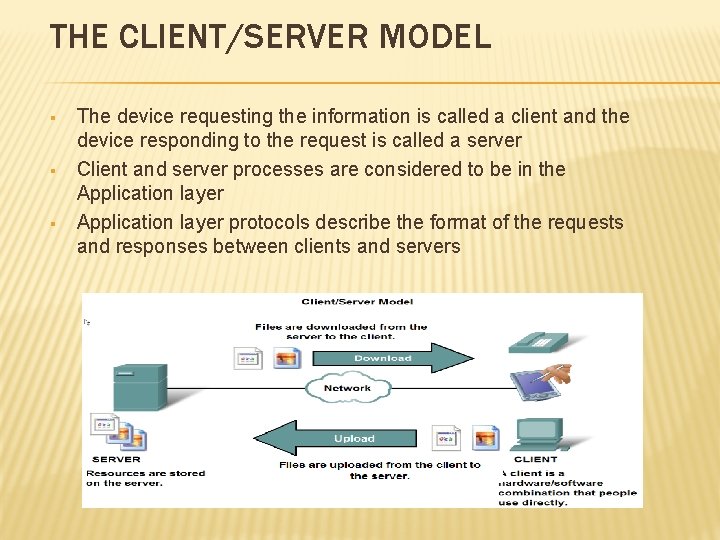
THE CLIENT/SERVER MODEL § § § The device requesting the information is called a client and the device responding to the request is called a server Client and server processes are considered to be in the Application layer protocols describe the format of the requests and responses between clients and servers

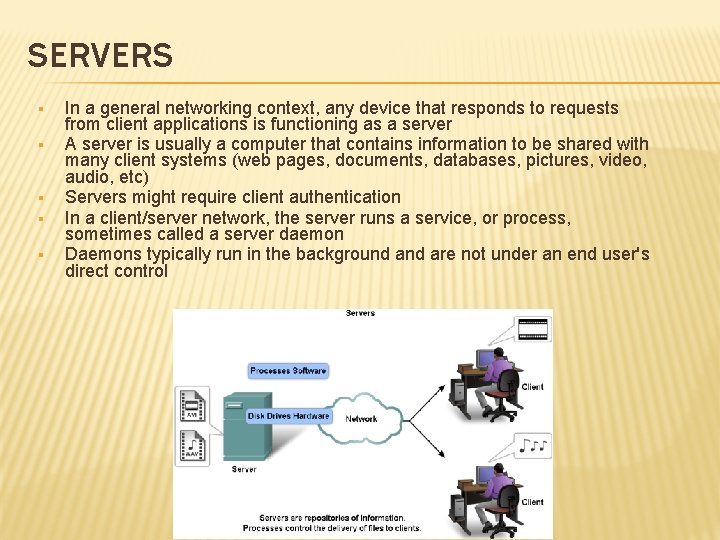
SERVERS § § § In a general networking context, any device that responds to requests from client applications is functioning as a server A server is usually a computer that contains information to be shared with many client systems (web pages, documents, databases, pictures, video, audio, etc) Servers might require client authentication In a client/server network, the server runs a service, or process, sometimes called a server daemon Daemons typically run in the background are not under an end user's direct control

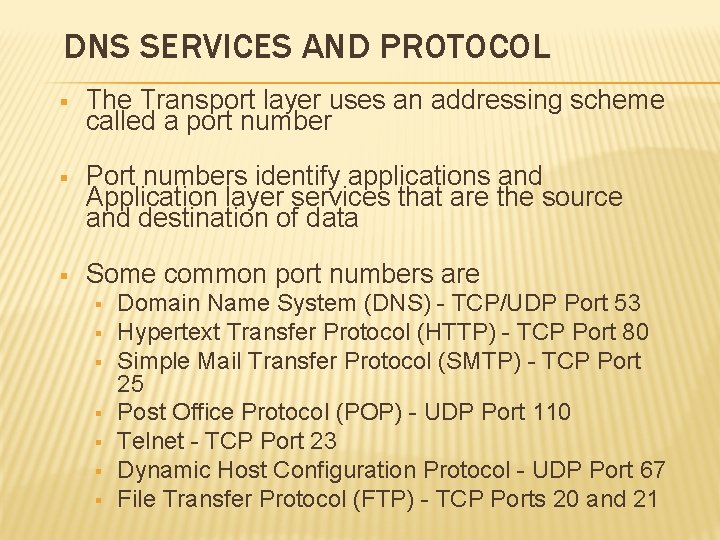
APPLICATION LAYER SERVICES AND PROTOCOLS § § A single application may employ multiple Application layer services (one request for a web page may, in fact, amount to dozens of individual requests) A server might receive multiple client requests at the same time. The Application layer processes and services rely on support from lower layer functions to successfully manage the multiple conversations

DNS SERVICES AND PROTOCOL § The Transport layer uses an addressing scheme called a port number § Port numbers identify applications and Application layer services that are the source and destination of data § Some common port numbers are § § § § Domain Name System (DNS) - TCP/UDP Port 53 Hypertext Transfer Protocol (HTTP) - TCP Port 80 Simple Mail Transfer Protocol (SMTP) - TCP Port 25 Post Office Protocol (POP) - UDP Port 110 Telnet - TCP Port 23 Dynamic Host Configuration Protocol - UDP Port 67 File Transfer Protocol (FTP) - TCP Ports 20 and 21

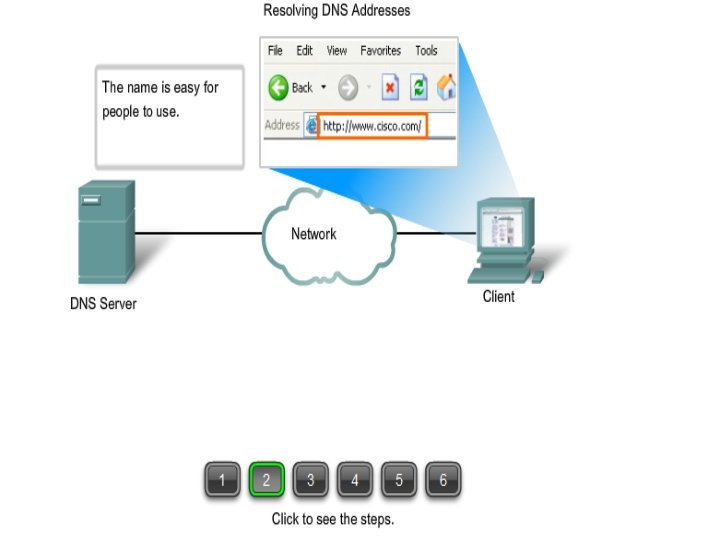
DNS SERVICES AND PROTOCOL § § Host file concept: When internet was small, mapping was done by host file. It had only 2 columns: -1)name 2)Address § § Today , However, it is impossible to have single host file to relate every address with a name. § Because it would be too large. § To over come this problem Domain Name System(DNS) is used.

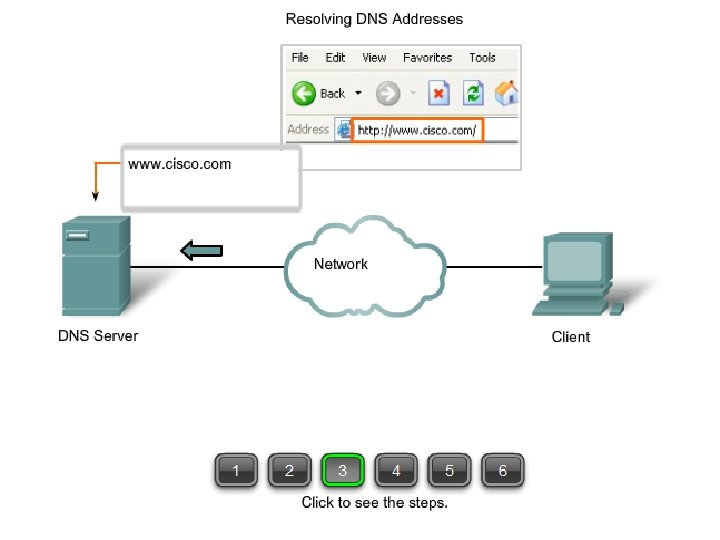
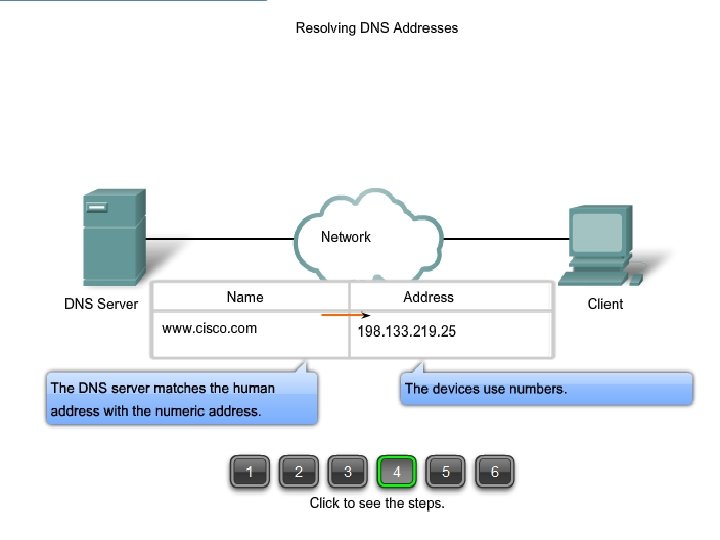
DNS: § Each device on a network is identified by an IP address § On the Internet it is difficult to remember all the IP addresses so domain names are created. § The Domain Name System (DNS) was created for domain name to address resolution. § DNS uses a distributed set of servers to resolve the names associated with these numbered addresses. The DNS protocol defines an automated service that matches resource names with the required numeric network address § §







NAME SPACE CONCEPT: A name space that maps each address to a unique name can be organised in two ways: 1)flat 2)Hierarchical § In flat, it consists of sequence of character without structure. § The main disadvantage is , it cannot be used in large systems like internet. § Because it is difficult to avoid ambiguity and duplication. § But in hierarchical name space, a name is divided in to several parts like : nature , name &departments of an organisation. § To have an hierachical name space domain name space is used.

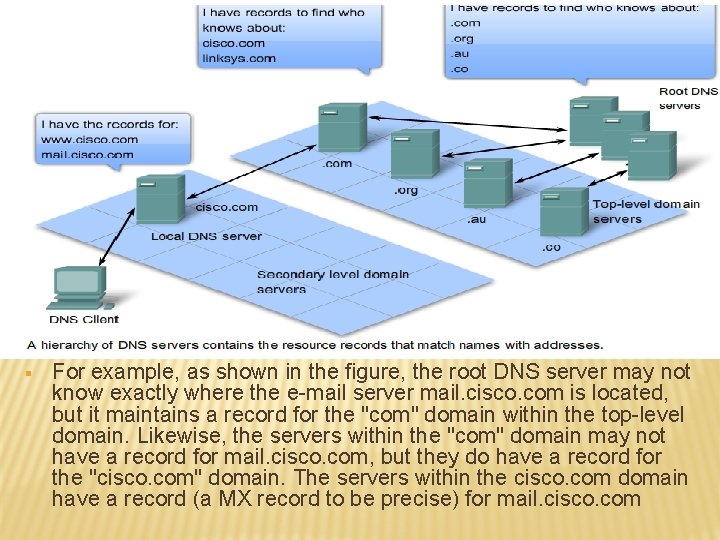
CONTD… § The Domain Name System uses a hierarchical system to create a name database to provide name resolution. The hierarchy looks like an inverted tree with the root at the top and branches below. § At the top of the hierarchy, the root servers maintain records about how to reach the top-level domain servers, which in turn have records that point to the secondary level domain servers and so on. The different top-level domains represent either the type of organization or the country of origin. Examples of top-level domains are: . au - Australia . co - Colombia . com - a business or industry . jp - Japan . org - a non-profit organization •

CONTD… § For example, as shown in the figure, the root DNS server may not know exactly where the e-mail server mail. cisco. com is located, but it maintains a record for the "com" domain within the top-level domain. Likewise, the servers within the "com" domain may not have a record for mail. cisco. com, but they do have a record for the "cisco. com" domain. The servers within the cisco. com domain have a record (a MX record to be precise) for mail. cisco. com

RESOLUTION: Mapping a name to an address or an address to a name is called name address resolution. Resolver § When a client wants to connect with a particular server. at that time resolver identifies the client , and checks whether it belongs to the respective server or not.

DNS MESSAGES: DNS has two types of messages: 1)query 2)Respon se §

CACHING: � When a server receives a query from the client which does not belong to its domain, then it search it’s data base to find the server ip address. � This process consumes a lot of time. � So for the reduction of that time DNS uses caching concept.

TYPES OF RECORDS: Two types of records used in DNS: 1)Question 2)Resource � � A question record is used by the client to get the information from the server. this contains domain name � The server database consists of resource records. it s also the information returned from server to client.

DDNS: � When DNS was designed no one predicted that their would be so many address changes. � These types of changes needs a manual updating. � The size of today’s internet dosen’t allow for this kind of manual updating. � So by using DDNS , we can update DNS master file dynamically.

ENCAPSULATION: § DNS can use either UDP or TCP. § In both cases the well known port used by the server is port 53 § UDP is used when the size of the response message is less than 512 bytes. § If the size of the message exceed that limit then TCP connection is used.

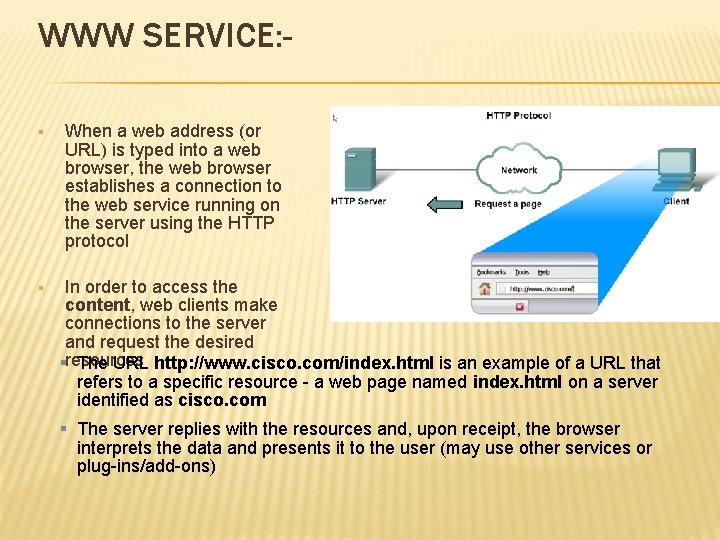
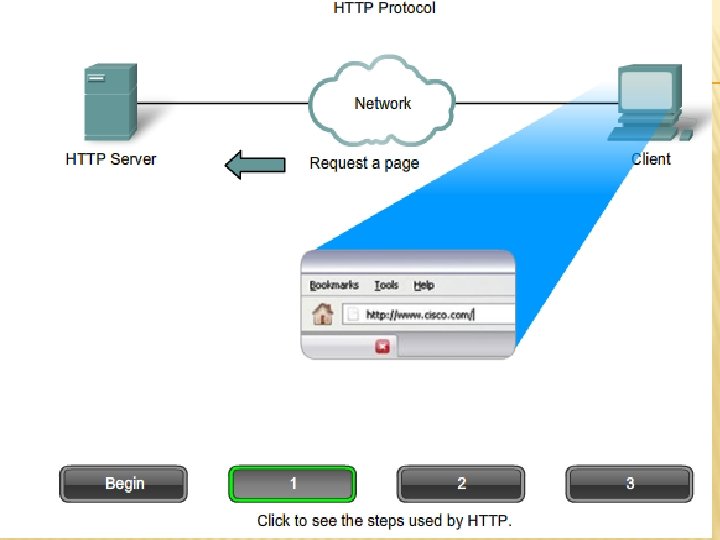
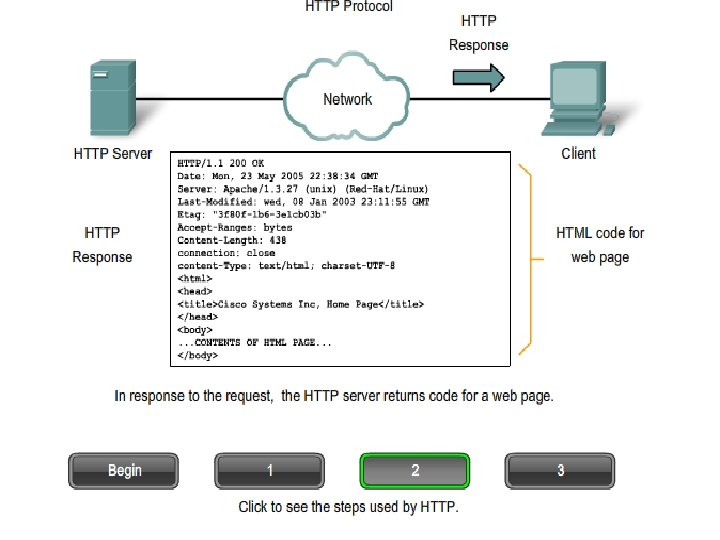
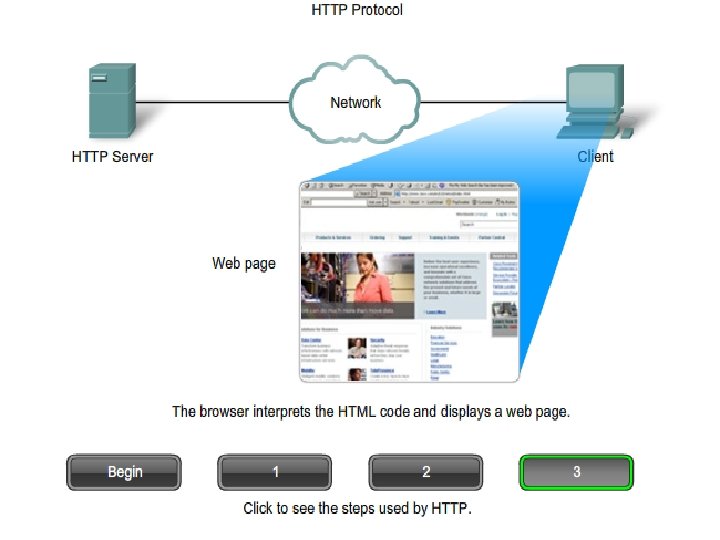
WWW SERVICE: § § When a web address (or URL) is typed into a web browser, the web browser establishes a connection to the web service running on the server using the HTTP protocol In order to access the content, web clients make connections to the server and request the desired §resources The URL http: //www. cisco. com/index. html is an example of a URL that refers to a specific resource - a web page named index. html on a server identified as cisco. com § The server replies with the resources and, upon receipt, the browser interprets the data and presents it to the user (may use other services or plug-ins/add-ons)

URL § It stands for uniform resource locater. § A client wants to access a web page needs the address. § To facilitate this documents distributed throughout the world. § URL is a standard for specifying any kind of information on the internet. § It definds 4 things: protocol, host port , &path.

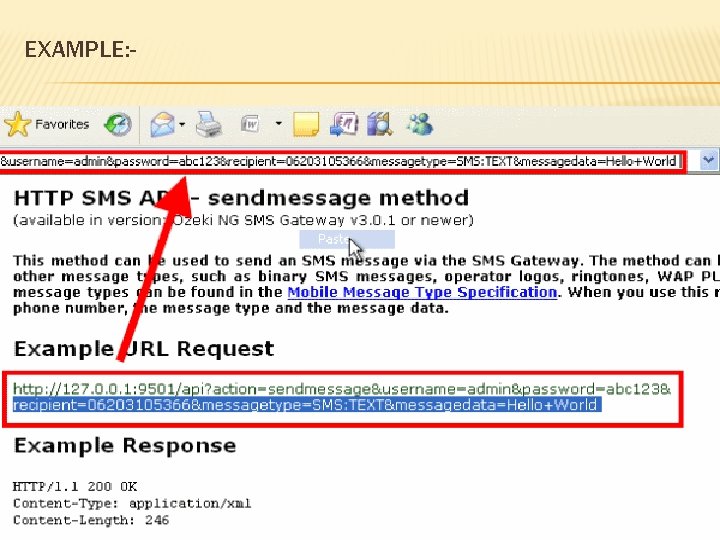
EXAMPLE: -

COOKIES: � A cookie is usually a small piece of data sent from a website and stored in a user's web browser while a user is browsing a website. � When the user browses the same website in the future, the data stored in the cookie can be retrieved by the website to notify the website of the user's previous activity. � Cookies were designed to be a reliable mechanism for websites to remember the state of the website or activity the user had taken in the past.

WEB DOCUMENT: The document in www can be grouped in to three categories: 1)Static 2)Dynamic 3)Active � � Static documents are fixed-content documents that are created and stored in a server. � Dynamic document created by a web server when ever a browser request the document. � For many applications, we need a program or script to be run at the client side these are called Active document.

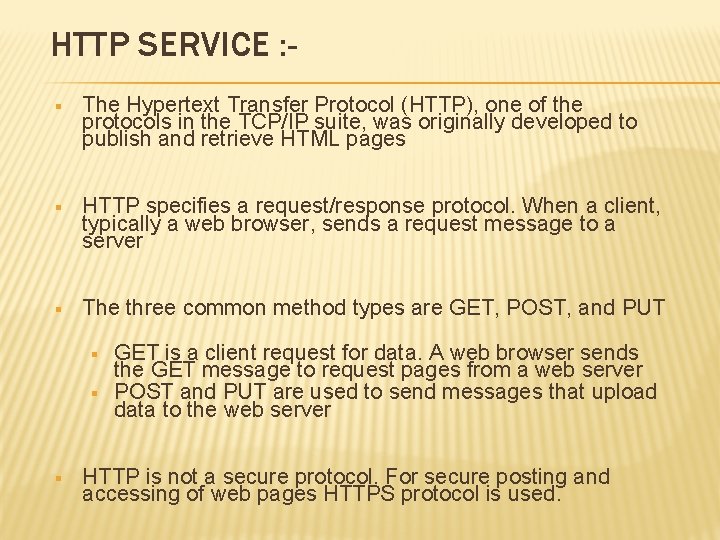
HTTP SERVICE : § The Hypertext Transfer Protocol (HTTP), one of the protocols in the TCP/IP suite, was originally developed to publish and retrieve HTML pages § HTTP specifies a request/response protocol. When a client, typically a web browser, sends a request message to a server § The three common method types are GET, POST, and PUT § § § GET is a client request for data. A web browser sends the GET message to request pages from a web server POST and PUT are used to send messages that upload data to the web server HTTP is not a secure protocol. For secure posting and accessing of web pages HTTPS protocol is used.


7



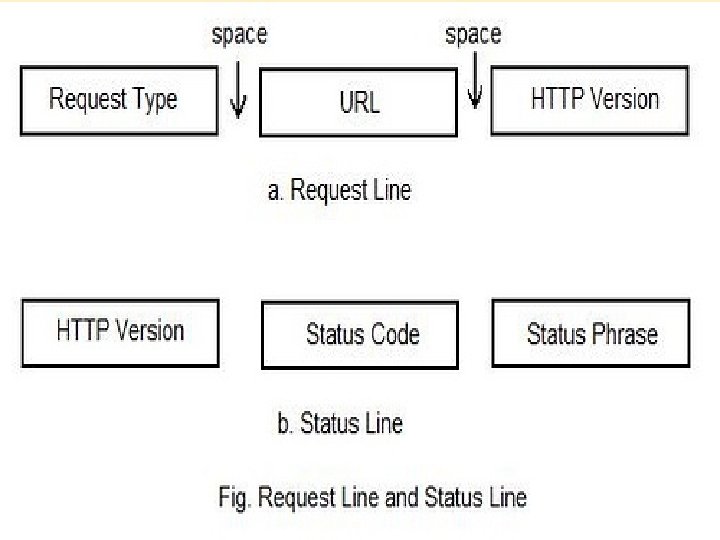
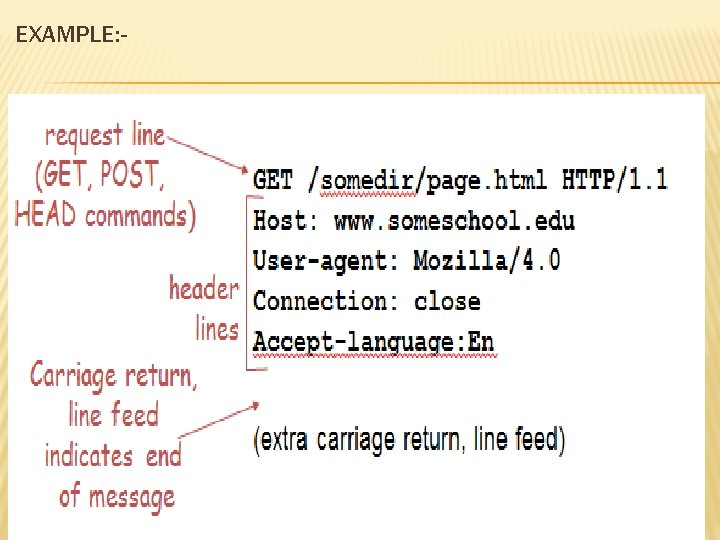
REQUEST AND RESPONSE MESSAGE Request message � Request line � Header � A blank line � Body Response message � Status line � Header � A blank line � Body

CONTD… � The first line in request message is called request line. � The header exchanges additional information between the client and the server. � A blank line used to separate the header, request line from body. � The body can be present in a request and response message , It contains the document to be sent or received.


EXAMPLE: -

CONTD…. � Request type : - It is the field used in request message. It is categorized in to methods. � URL we discussed. � Version: - current version of HTTP is 1. 1 � Status code: - it is used in response message. This field is consists of three digits. � The range of the digit is 100 -500. � Status phase: - This field is explains the status code in text form.

HEADER: A header line belongs to four categories: 1)general header 2)request header 3)response header 4)entity header � General header gives general information about message. can be present in both request and response message. � � Request header specifies the client’s configuration. � Response header specifies the server configuration and special information about the request. � Entity header gives information about the body of the document.

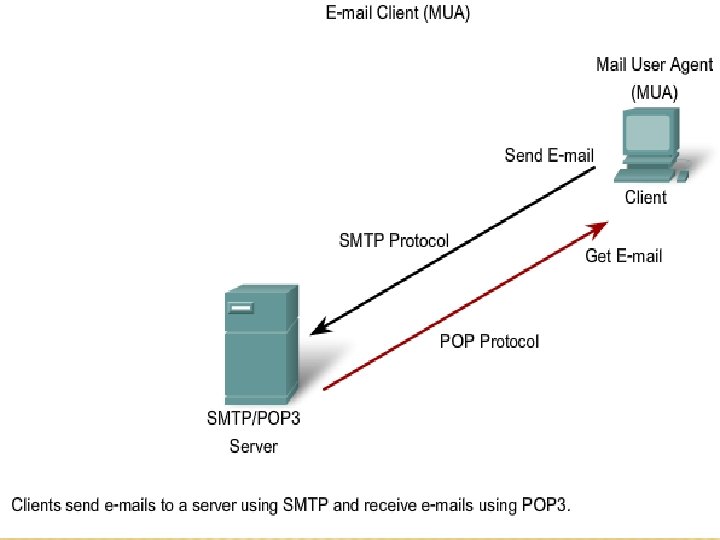
EMAIL SERVICES AND SMTP/POP PROTOCOLS: § e-mail requires several applications and services. § Two example Application layer protocols are Post Office Protocol (POP) and Simple Mail Transfer Protocol (SMTP), § In order to receive e-mail messages from an e-mail server, the e-mail client can use POP. § Sending e-mail from either a client or a server uses message formats and command strings defined by the SMTP protocol.


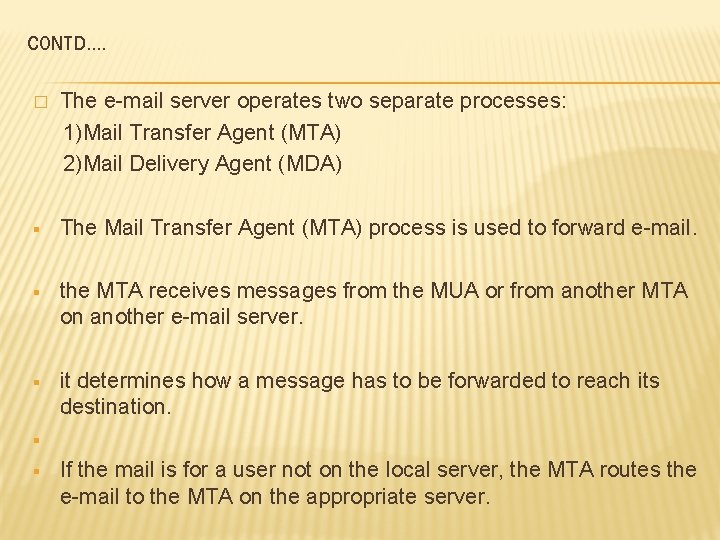
CONTD…. The e-mail server operates two separate processes: 1)Mail Transfer Agent (MTA) 2)Mail Delivery Agent (MDA) � § The Mail Transfer Agent (MTA) process is used to forward e-mail. § the MTA receives messages from the MUA or from another MTA on another e-mail server. § it determines how a message has to be forwarded to reach its destination. If the mail is for a user not on the local server, the MTA routes the e-mail to the MTA on the appropriate server. § §


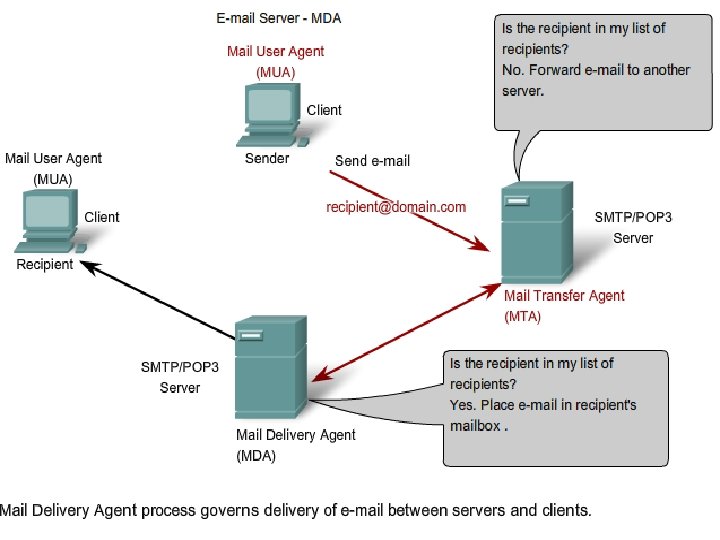
CONTD… § we see that the Mail Delivery Agent (MDA) accepts a piece of email from a Mail Transfer Agent (MTA) and performs the actual delivery. § The MDA receives all the inbound mail from the MTA and places it into the appropriate users' mailboxes. § The MDA can also resolve final delivery issues, such as virus scanning, spam filtering, and return-receipt handling. § Most e-mail communications use the MUA, MTA, and MDA applications. However, there are other alternatives for e-mail delivery.

CONTD… § The SMTP protocol message format uses a rigid set of commands and replies. § These commands support the procedures used in SMTP, such as session initiation, mail transaction, forwarding mail, verifying mailbox names, expanding mailing lists, and the opening and closing exchanges. Some of the commands specified in the SMTP protocol are: § HELO - identifies the SMTP client process to the SMTP server process § EHLO - Is a newer version of HELO, which includes services extensions § MAIL FROM - Identifies the sender § RCPT TO - Identifies the recipient § DATA - Identifies the body of the message

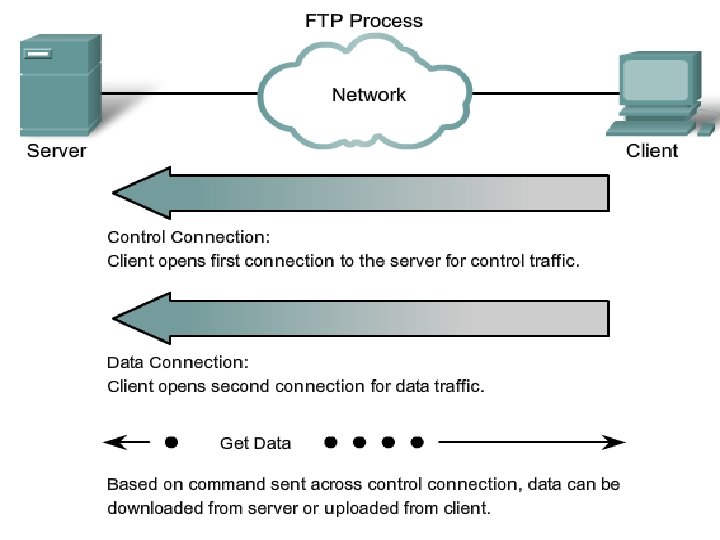
FILE TRANSFER PROTOCOL(FTP): § The File Transfer Protocol (FTP) is another commonly used Application layer protocol. § FTP was developed to allow for file transfers between a client and a server. § FTP uses 2 well known TCP ports: port 21 is used for the control connection, and port 20 is used for the data connection. § The file transfer can happen in either direction. The client can download (pull) a file from the server or, the client can upload (push) a file to the server.

COND… � The message can be retrived with an e-mail client POP or IMAP(Internet Mail access Protocol). � IMAP is similar to POP 3 but supports some additional feature. � For eg: -with IMAP 4 you can search through your e-mail message for keywords while the message are still on mail server

KEY GOALS FOR IMAP : � Be fully compatible with internet message standards. � Allows message access and management from more than one computer. � Provide support for online , offline, disconnect access mode. � Support for concurrent access to shared mailboxes.

CONTD… § To successfully transfer files, FTP requires two connections between the client and the server: one for commands and replies, the other for the actual file transfer. § The client establishes the first connection to the server on TCP port 21. This connection is used for control traffic, consisting of client commands and server replies. § The client establishes the second connection to the server over TCP port 20. This connection is for the actual file transfer and is created every time there is a file transferred.


ANONYMOUS FTP: § Generally , to use FTP user needs a password on the remote server. § Some sites have a set of files available for public access , to enable Anonymous FTP. § To access these files a user doesn’t need to have an user id or password. § Instead the user can use “Anonymous” as the user name and “guest” as the password

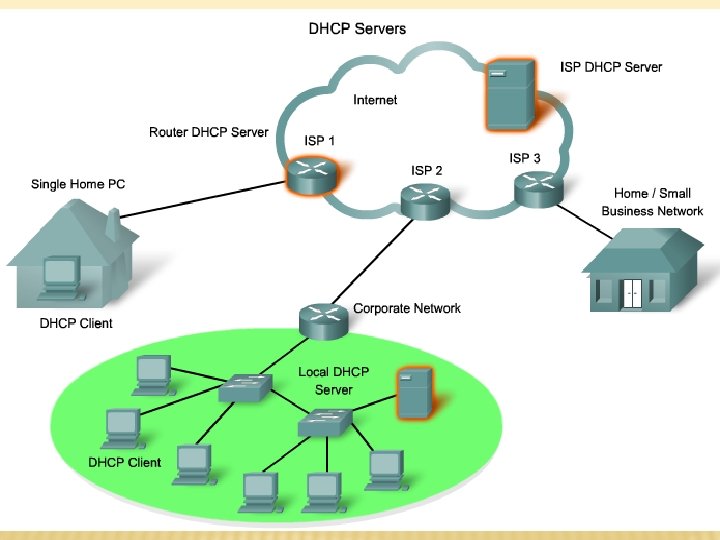
DYNAMIC HOST CONTROL PROTOCOL(DHCP): § The Dynamic Host Configuration Protocol (DHCP) service enables devices on a network to obtain IP addresses and other information from a DHCP server. § This service automates the assignment of IP addresses, subnet masks, gateway and other IP networking parameters. § On larger local networks, or where the user population changes frequently, DHCP is preferred. § The host can obtain an IP address once the hardware connection is made, either via a wired or wireless LAN. E. g: -


Thank you
