A Guide to IT Technical Support 9 th




























- Slides: 50

A+ Guide to IT Technical Support, 9 th Edition Chapter 17 Windows Resources on a Network

Objectives • Support some client-server applications • Share and secure files and folders on a network • Support cloud computing services on a network A+ Guide to IT Technical Support, 9 th Edition 2 © Cengage Learning 2017

Supporting Client/Server Applications • Client/Server applications expected to support: – Internet Explorer – Remote Desktop – Other remote applications • Also need to know how to use Group Policy to configure Quality of Service (Qo. S) – Also how to link a data source through a network to database applications A+ Guide to IT Technical Support, 9 th Edition 3 © Cengage Learning 2017

Network Servers • List of popular client-server resources: – – – – Mail server File server Print server DHCP server DNS server Proxy server Authentication server Web server A+ Guide to IT Technical Support, 9 th Edition 4 © Cengage Learning 2017

Internet Explorer • Most popular client/server applications are a browser and web server • Internet Explorer (IE) version 11: latest version at this writing – Windows 10 features new Microsoft Edge browser • Easy to upgrade by using Windows Update • Tips when using IE window: – To show the menu bar, press the Alt key – HTTP Secure – look for https and a padlock icon – If you have problems with IE 11, you can disable it A+ Guide to IT Technical Support, 9 th Edition 5 © Cengage Learning 2017

Internet Explorer • Use the Internet Options box to manage IE settings – Click Tools icon and click Internet Options • Internet Options box has several tabs with different configuration options and settings • General Tab – Change the home page or add a second home page – Protect your identity and surfing records – Check Delete browsing history on exit if you want your history cleared each time you close IE – Manage IE cache A+ Guide to IT Technical Support, 9 th Edition 6 © Cengage Learning 2017

Internet Explorer • Security Tab – Set security level (medium-high is the default level) • Prompts before downloading content • Does not download Active. X controls that are not signed by Microsoft (virus can sometimes hide in an Active. X control) – To customize security settings, click Custom level A+ Guide to IT Technical Support, 9 th Edition 7 © Cengage Learning 2017

Internet Explorer • Privacy Tab and Content Tab – Use Privacy Tab to block cookies that might invade your privacy or steal identity – Content tab contains settings for Family Safety, certificates used by web sites, and how Auto. Complete and Feeds are handled A+ Guide to IT Technical Support, 9 th Edition 8 © Cengage Learning 2017

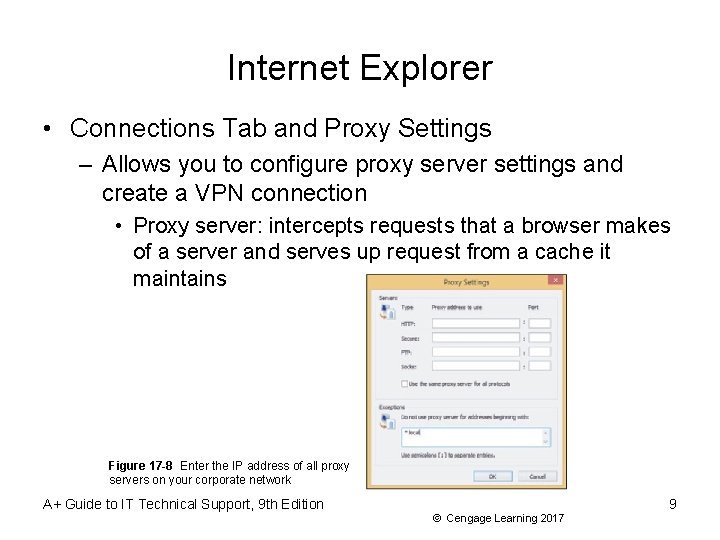
Internet Explorer • Connections Tab and Proxy Settings – Allows you to configure proxy server settings and create a VPN connection • Proxy server: intercepts requests that a browser makes of a server and serves up request from a cache it maintains Figure 17 -8 Enter the IP address of all proxy servers on your corporate network A+ Guide to IT Technical Support, 9 th Edition 9 © Cengage Learning 2017

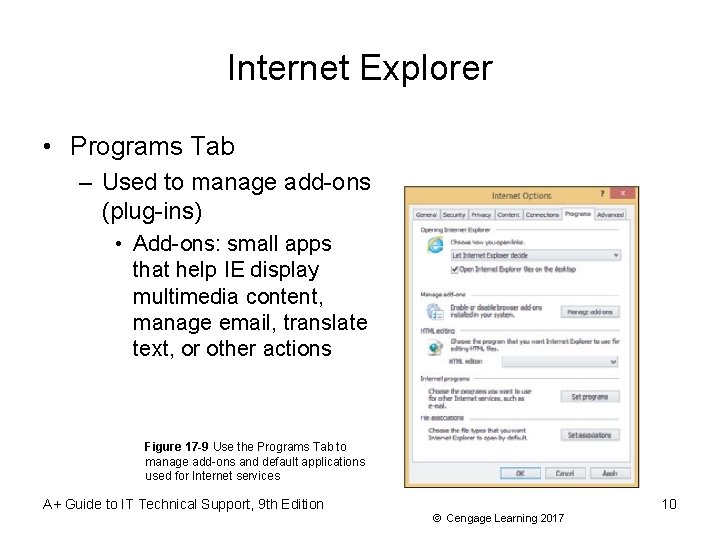
Internet Explorer • Programs Tab – Used to manage add-ons (plug-ins) • Add-ons: small apps that help IE display multimedia content, manage email, translate text, or other actions Figure 17 -9 Use the Programs Tab to manage add-ons and default applications used for Internet services A+ Guide to IT Technical Support, 9 th Edition 10 © Cengage Learning 2017

Internet Explorer • Advanced Tab – Contains several miscellaneous settings used to control Internet Explorer – One setting is useful when IE is giving problems • If you suspect problems are caused by wrong settings, click Reset to return IE to all default settings A+ Guide to IT Technical Support, 9 th Edition 11 © Cengage Learning 2017

Remote Desktop Connection (RDC) • Remote Desktop gives a user access to a Windows desktop from anywhere on the Internet • To use Remote Desktop, the computer you want to remotely access (the server) must be running business or professional editions of Windows 8/7/Vista – Computer accessing can be running any version of Windows • Computers set to serve up Remote Desktop are not as secure – You can use software that does not require opening ports for a more secure solution A+ Guide to IT Technical Support, 9 th Edition © Cengage Learning 2017 12

Remote Assistance • Remote Assistance – a user on the server computer can remain signed in during the remote session, retains control of the session, and can see the screen – Helpful when troubleshooting problems – User who needs help send an invitation by email or chat to connect to their computer using Remote Assistance A+ Guide to IT Technical Support, 9 th Edition 13 © Cengage Learning 2017

Remote Assistance • Ways to initiate a Remote Assistance session: – User saves an invitation file and send file to technician – User can send an automated email through the Remote Assistance app – User can use Easy Connect, which is the easiest method to start Remote Assistance connection • Both computers must support Easy Connect – Technician can initiate a session • Follow steps outlined in text to see how to initiate a Remote Assistance connection using Easy Connect A+ Guide to IT Technical Support, 9 th Edition 14 © Cengage Learning 2017

Remote Assistance • Things you can do during a Remote Assistance session: – – – Chat Request control Pause Disconnect or Stop sharing Log activity in a log file Change expiration of invitations A+ Guide to IT Technical Support, 9 th Edition 15 © Cengage Learning 2017

Remote Assistance • If you have problems making the connection: – Windows Firewall on the user’s computer might be blocking Remote Assistance • Verify Remote Assistance is checked as an exception to blocked apps in Windows Firewall window – If outside the user’s local network, the hardware firewall protecting her network might be blocking Remote Assistance • Verify that port forwarding is enabled for Remote Assistance A+ Guide to IT Technical Support, 9 th Edition 16 © Cengage Learning 2017

Use Group Policy to Improve Qo. S Applications • Group Policy (gpedit. msc) – Used to control what users can do and how the system can be used – Only available in Windows professional and business editions – Works by: • Making entries in registry • Applying scripts to Windows startup, shutdown, and logon processes • Affecting security settings A+ Guide to IT Technical Support, 9 th Edition 17 © Cengage Learning 2017

Use Group Policy to Improve Qo. S Applications • Group Policy (cont’d) – Can be applied to computer or user • Computer policies are applied just before logon screen • User policies are applied after login – To use Group Policy to set the Qo. S level for an application follow steps outlined in the text – To get the most out of Qo. S, configure each router and computer on the network to use Qo. S A+ Guide to IT Technical Support, 9 th Edition 18 © Cengage Learning 2017

Use Group Policy to Improve Qo. S Applications • Important options when creating a policy: – Priority level is determined by a DSCP (Differentiated Service Code Point) value – Outbound traffic can be throttled to limit the bandwidth assigned an application – The policy can apply to all applications or a specific program – You can specify the source IP address and/or destination IP address – You can select the protocol (TCP or UDP) and port numbers for the policy A+ Guide to IT Technical Support, 9 th Edition 19 © Cengage Learning 2017

ODBC Data Sources • Open Database Connectivity (ODBC) – technology used to create the data source – Which provides access to the database and includes the drivers required to interface between Access and the data – Drivers for Microsoft SQL Server must be installed on the local computer – Use the ODBC Data Sources tool in the Administrative Tools group of Control Panel to configure the data source A+ Guide to IT Technical Support, 9 th Edition 20 © Cengage Learning 2017

Controlling Access to Folders and Files • Managing shared resources is accomplished by: – Assigning rights to user accounts – Assigning permissions to folders and files A+ Guide to IT Technical Support, 9 th Edition 21 © Cengage Learning 2017

Classify User Accounts and User Groups • Principle of least privilege: An approach where computer users are assigned the minimum rights required to do their job • Rights or privileges are established when you first create a user account (based on account type) – Rights can later be changed by changing the user groups to which the account belongs • User accounts are created from the Control Panel or by using the Computer Management console A+ Guide to IT Technical Support, 9 th Edition 22 © Cengage Learning 2017

Classify User Accounts and User Groups • Type of User Account – Administrator account: has complete access to the system and can make changes that affect the security of the system and other users – Standard user account: can use software and hardware and make some system changes but cannot make changes that affect the security of the system or other users A+ Guide to IT Technical Support, 9 th Edition 23 © Cengage Learning 2017

Classify User Accounts and User Groups Figure 17 -29 Create a new user A+ Guide to IT Technical Support, 9 th Edition 24 © Cengage Learning 2017

Classify User Accounts and User Groups • Built-in User Groups – Administrators and Users groups – Guests group • Has limited rights and is given a temporary profile that is deleted when user logs off – Backup Operators group • Can back up and restore files on the system regardless of its access permission to files – Power Users group • Windows XP group that can read from and write to parts of the system, install apps, and perform limited administrator tasks A+ Guide to IT Technical Support, 9 th Edition 25 © Cengage Learning 2017

Classify User Accounts and User Groups • Windows might automatically assign one of these built-in user groups to an account: – Authenticated Users group: includes all user accounts except the Guest account – Everyone group: includes the Authenticated Users group as well as the Guest account – Anonymous users: users who have not been authenticated on a remote computer A+ Guide to IT Technical Support, 9 th Edition 26 © Cengage Learning 2017

Classify User Accounts and User Groups • Customized User Groups – Use Management Console in business and professional editions of Windows to create custom user groups – Easier to assign permissions to user groups rather than to individual accounts • User groups work well when several users need the same permissions • Create a user group and then assign permission to the user group A+ Guide to IT Technical Support, 9 th Edition 27 © Cengage Learning 2017

Methods to Assign Permissions To Folders and Files • Three general strategies for managing shared folder and files in Windows – Homegroup sharing: use when all users on a network require the same access to all resources – Workgroup sharing: offers better security than a homegroup – Domain controlling: if computer belongs to a domain, all security is managed by the network administrator for the entire network A+ Guide to IT Technical Support, 9 th Edition 28 © Cengage Learning 2017

Methods to Assign Permissions To Folders and Files • Tips on which folder to use to hold shared data: – Private data for individual users • C: Users folder for that user – Data for all users to share • C: UsersPublic folder – For best security, create a folder not in either of the above folders and assign permissions to that folder and its subfolders • Allow all users access or only certain users or user groups A+ Guide to IT Technical Support, 9 th Edition 29 © Cengage Learning 2017

Methods to Assign Permissions To Folders and Files • Using workgroup sharing, Windows offers two methods to share a folder – Share permissions: grant permissions only to network users and not to local users • Apply to a folder and its contents, not to individual files – NTFS permissions: apply to local users and network users • Apply to both folders and individual files • Work on NTFS volumes only A+ Guide to IT Technical Support, 9 th Edition 30 © Cengage Learning 2017

Methods to Assign Permissions To Folders and Files • Tips when implementing permissions: – If both share and NTFS permission are used, the most restrictive permission applies – If NTFS permissions are conflicting the more liberal permission applies – Permission propagation: when permissions are passed from parent to child – Inherited permissions: permissions attained from a parent object – When you move or copy an object to a folder, the object takes on permissions of that folder A+ Guide to IT Technical Support, 9 th Edition 31 © Cengage Learning 2017

How to Share Folders and Files • User and Group Information with the gpresult Command – Use the gpresult command to pull a list of all the groups a user belongs to – Information can be helpful when troubleshooting user group issues or Group Policy problems – Enter the command gpresult/scope user/username /r to retrieve information on a user other than the one signed in A+ Guide to IT Technical Support, 9 th Edition 32 © Cengage Learning 2017

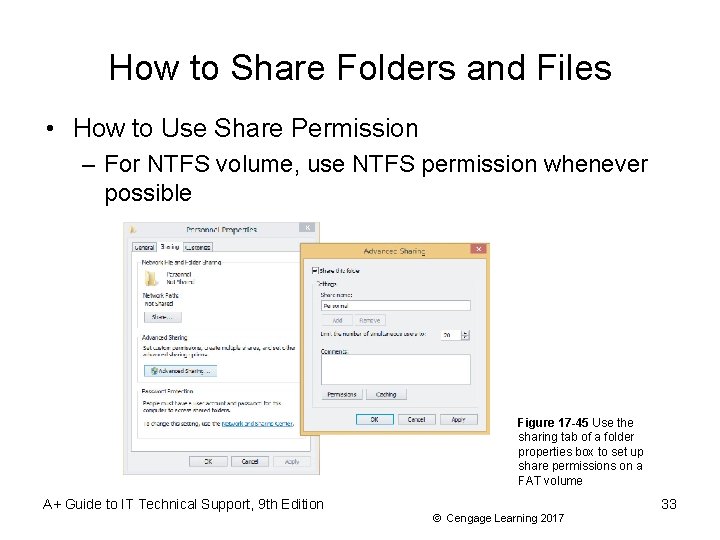
How to Share Folders and Files • How to Use Share Permission – For NTFS volume, use NTFS permission whenever possible Figure 17 -45 Use the sharing tab of a folder properties box to set up share permissions on a FAT volume A+ Guide to IT Technical Support, 9 th Edition 33 © Cengage Learning 2017

Support and Troubleshoot Shared Folders and Files • Few tips about managing shared folders and files: – Use advanced permissions settings if you need further control of a user or group • Click Advanced on the Security tab of a folder’s Properties box – Manage permissions using parent folder • Subfolders inherit permissions of the parent folder – Check the effective permissions • To know for sure which permissions are in effect, see Effective Permissions tab of Advanced Security Settings box A+ Guide to IT Technical Support, 9 th Edition 34 © Cengage Learning 2017

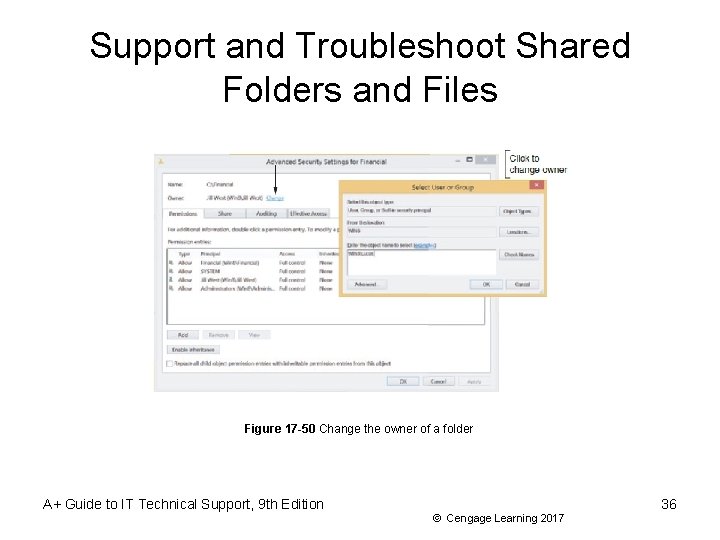
Support and Troubleshoot Shared Folders and Files • Few tips about managing shared folders and files: (cont’d) – Take ownership of a folder • Owner of a folder always has full permissions – Use only one workgroup • Performance improves when they are all in the same workgroup – Require passwords for all user accounts – Use a mapped network drive A+ Guide to IT Technical Support, 9 th Edition 35 © Cengage Learning 2017

Support and Troubleshoot Shared Folders and Files Figure 17 -50 Change the owner of a folder A+ Guide to IT Technical Support, 9 th Edition 36 © Cengage Learning 2017

How to Map a Network Drive or Network Printer • A network share is one of the most powerful and versatile methods of communicating over a network – Makes one computer (the client) appear to have a new hard drive, such a drive E, that is really hard drive space on another host computer – Called mapping a drive • Network File System (NFS) makes it possible for files on the network to be accessed as easily as if they are stored on the local computer A+ Guide to IT Technical Support, 9 th Edition 37 © Cengage Learning 2017

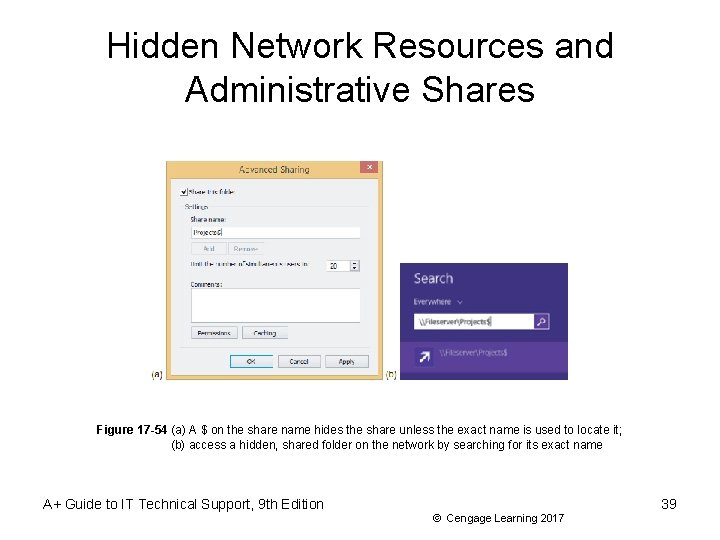
Hidden Network Resources and Administrative Shares • To protect confidential data from users on the network: – Disable File and Printer Sharing – Hide a shared folder • If you want to share a folder, but don’t want others to see it add a $ to the end of the folder name • Those that want to access the hidden folder must enter the complete path to the folder (including $) in search box A+ Guide to IT Technical Support, 9 th Edition 38 © Cengage Learning 2017

Hidden Network Resources and Administrative Shares Figure 17 -54 (a) A $ on the share name hides the share unless the exact name is used to locate it; (b) access a hidden, shared folder on the network by searching for its exact name A+ Guide to IT Technical Support, 9 th Edition 39 © Cengage Learning 2017

Hidden Network Resources and Administrative Shares • Local shares: folders and files on a computer that are shared with others using local user accounts • Administrative shares: folders that are shared by default that administrator accounts at the domain level can access – Two types of administrative shares: • The %systemroot% folder • Any volume or drive • Don’t share the /Windows folder or an entire drive – Don’t want system files and folders exposed A+ Guide to IT Technical Support, 9 th Edition 40 © Cengage Learning 2017

Cloud Computing • Cloud computing – when a third-party service or vendor makes computer resources available to its customers over the Internet • Can provide many other types of resources: – – – Applications Network services Websites Database servers Specialized developer applications Entire operating systems A+ Guide to IT Technical Support, 9 th Edition 41 © Cengage Learning 2017

Cloud Computing • All cloud computing service models incorporate the following elements: – – – Service at any time Elastic services and storage Support for multiple client platforms Resource pooling and consolidation Measured service A+ Guide to IT Technical Support, 9 th Edition 42 © Cengage Learning 2017

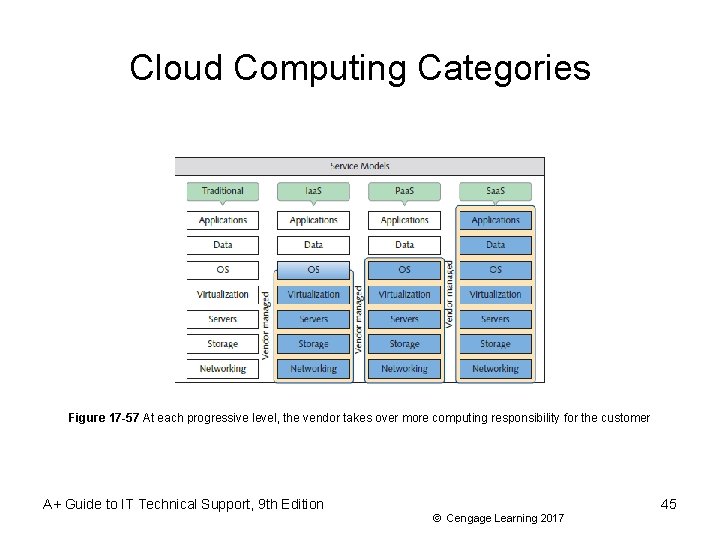
Cloud Computing Categories • Cloud computing service models are categorized by the types of services they provide: – Iaa. S (Infrastructure as a Service) – customer rents hardware, including servers, storage, and networking – Paa. S (Platform as a Service) – customer rents hardware, operating systems, and some applications that might support other applications installed – Saa. S (Software as a Service) – customers rent hardware, operating systems, and applications specific to the customer’s needs • Applications are provided through an online user interface A+ Guide to IT Technical Support, 9 th Edition 43 © Cengage Learning 2017

Cloud Computing Categories • Cloud computing service models are categorized by the types of services they provide (cont’d): – Xaa. S (Anything as a Service or Everything as a Service) – the “X” represents an unknown • Cloud can provide any combination of functions • Another Saa. S implementation that doesn’t fit the official definition of Saa. S is rentable software or software by subscription – Many companies are moving toward this subscription model A+ Guide to IT Technical Support, 9 th Edition 44 © Cengage Learning 2017

Cloud Computing Categories Figure 17 -57 At each progressive level, the vendor takes over more computing responsibility for the customer A+ Guide to IT Technical Support, 9 th Edition 45 © Cengage Learning 2017

Deployment Models for Cloud Computing • Cloud computing deployment models: – Public cloud – services are provided over the Internet to the general public – Private cloud – services are established on an organization’s own servers • Or established virtually for a single organization’s private use – Community cloud – services are shared between multiple organizations, but not available publicly – Hybrid cloud – a combination of public, private, and community clouds used by same organization A+ Guide to IT Technical Support, 9 th Edition 46 © Cengage Learning 2017

Chapter Summary • A client computer contacts a server to request information or to perform a task • The Internet Options dialog box is used to manage many Internet Explorer settings • Remote Desktop gives you access to your Windows desktop from anywhere on the Internet • A policy can be set using Group Policy to improve Quality of Service (Qo. S) for an application • Open Database Connectivity (OBDC) can create a data source, which provides a remote database and its drivers to a client computer A+ Guide to IT Technical Support, 9 th Edition 47 © Cengage Learning 2017

Chapter Summary • Controlling access to folders and files on a network is done by assigning rights to user accounts and assigning permissions to files and folders • Apply the principle of least privilege when assigning rights to users • Customized user groups that you create make it easier to manage rights to multiple user accounts • Three ways to share files and folders on the network are to use homegroup sharing, workgroup sharing, and domain controllers A+ Guide to IT Technical Support, 9 th Edition 48 © Cengage Learning 2017

Chapter Summary • A mapped network drive makes it easier for users to access drives and folders on the network • Peer-to-peer networks use local shares, and a Windows domain supports administrative shares • Cloud computing is providing computing resources over the Internet to customers • Cloud computing service models, including Iaa. S, Paa. S, Saa. S, and Xaa. S, are categorized by the types of services they provide A+ Guide to IT Technical Support, 9 th Edition 49 © Cengage Learning 2017

Chapter Summary • A public cloud service is available to the public, and a private cloud service is kept on an organization’s own servers or made available by a vendor only for a single organization’s private use A+ Guide to IT Technical Support, 9 th Edition 50 © Cengage Learning 2017