Your Digital Footprint What is a footprint and









































- Slides: 55

Your Digital Footprint

What is a footprint, and why does it matter?

What is a footprint, and why does it matter? A recent study by Career. Builder shows that 43% of employers are looking at the social media profiles of applicants prior to making decisions about hiring, and 51% of employers have come across something on social media that has caused them to not hire an applicant.

What is a footprint, and why does it matter? The internet appears to be a place where you can be uninhibited and express yourself freely, without consequence. However, each action you have online leaves a traceable footprint that can be viewed by a wide, public, audience. This digital footprint can never be fully erased, and can have either positive or negative effects on the future of an individual. Everything posted online should reflect the best version of yourself.

Discussion Questions Can you tell what a person is truly like just based on their online persona? How does the online image of a person reflect on their individual character? What guidelines should a person consider before posting, sharing, or commenting online?

Your online image

Your online image Information shared online can build a positive or negative image for an individual. Everything you post can be shared in a split second by others taking a screenshot or clicking share. Your digital footprint is often the first impression you will make with others. What do you want it to say?

Discussion Questions Do you present yourself differently online than offline? Why or why not? What is similar and what is different about your online and offline selves? If you had to walk around with a sign around your neck with your most recent online post, would you be proud? What are the risks from creating an online persona that is different from an offline persona? What are the benefits? What are the reasons people may act differently online than offline?

College and Career Implications

College and Career Implications A 2014 survey by Kaplan Test Prep suggests that 35% of admissions officers have visited an applicant’s social media page, and 16% have found something online that negatively influenced an applicant’s chances of admission. A 2015 Kaplan survey shows the number already rising to 40% of college admissions officers visiting an applicant’s social media page to learn more about them. Staff. com shares how 3 out of 4 (75%) hiring managers check social media even when not provided by the applicant and 1 in 3 candidates are rejected because of something found on a social profile.

College and Career Implications College admissions officers are viewing social media to learn about applicants. Information shared online can build a positive or negative image for an individual. Everything you post can be shared in a split second by others taking a screenshot or clicking share.


Discussion Questions Should colleges or employers make decisions about admissions based on information found on social media? Why or why not?

Privacy Matters

Privacy Matters A privacy policy is a legal notice providing information about how a website visitor's personal information will be used. Privacy policies should be available on all websites you share personal information with. You should always take the time to read through privacy policies.

6 Steps to Staying Safe on Social Media 1. Clean It Up – Before blocking all your pages, consider cleaning it up. A positive social media presence is a good thing. 2. Privacy Settings: Who Can See You? – Privacy policies could include disclaimers that give the website the freedom to use the material you post. 3. How to Share Safely – Make sure to change your privacy settings from public to private if you do not want your information being accessed freely. Facebook, for example, will only allow individuals to view your personal information if you are their friend. This prevents strangers from accessing your personal information. Remember to always read site privacy policies to make sure your information stays safe and secure.

6 Steps to Staying Safe on Social Media 4. What Location Settings Mean - Certain apps ask to use your location. For GPS navigation and weather apps, it makes sense to use your exact location. When it comes to social media or photography apps, you should NEVER use your exact location. This will prevent other people from knowing your exact location or when you’re away from home. Only posting a photo of a vacation or at an event after you’ve returned home to prevent strangers from knowing your location at the time you are there.

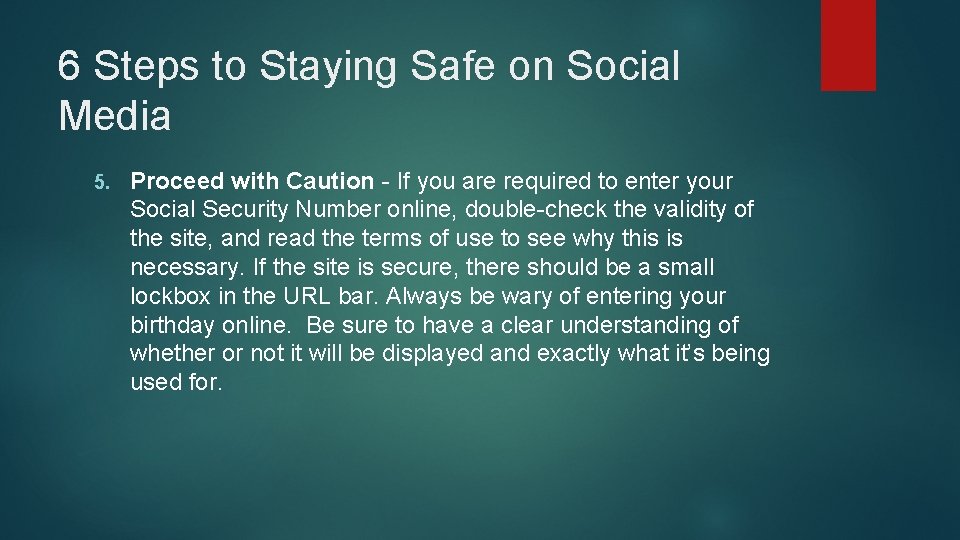
6 Steps to Staying Safe on Social Media 5. Proceed with Caution - If you are required to enter your Social Security Number online, double-check the validity of the site, and read the terms of use to see why this is necessary. If the site is secure, there should be a small lockbox in the URL bar. Always be wary of entering your birthday online. Be sure to have a clear understanding of whether or not it will be displayed and exactly what it’s being used for.

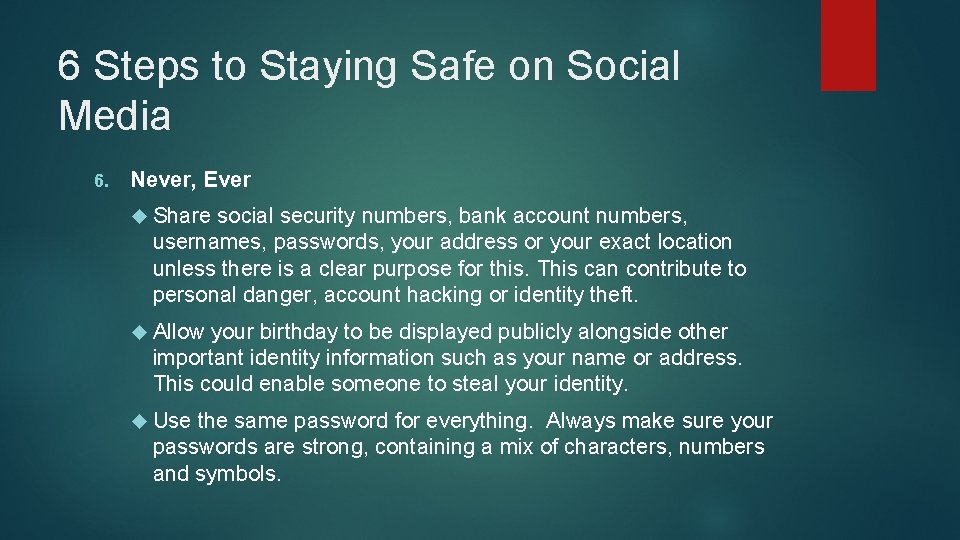
6 Steps to Staying Safe on Social Media 6. Never, Ever Share social security numbers, bank account numbers, usernames, passwords, your address or your exact location unless there is a clear purpose for this. This can contribute to personal danger, account hacking or identity theft. Allow your birthday to be displayed publicly alongside other important identity information such as your name or address. This could enable someone to steal your identity. Use the same password for everything. Always make sure your passwords are strong, containing a mix of characters, numbers and symbols.

Sharing Safely

What do these quotes mean in the context of your life, both digitally and non-digitally. “A picture is worth a thousand words. ” “It takes many good deeds to build a good reputation, and only one bad one to lose it. ” - Benjamin Franklin “The question isn’t ‘What do we want to know about people? ’ It’s ‘What do people want to tell about themselves? ’” - Mark Zuckerberg

Sharing Safely 57% of 18 -35 -year-olds think people share too much about their personal thoughts and experiences, and nearly that many feel technology is robbing them of their privacy Nearly 40% of internet users between the ages of 18 -35 have regretted posting personal information about themselves, and 35% have regretted posting personal information about a friend or family member.

Sharing Safely The internet appears to be a place where you can be uninhibited and express yourself freely, without consequence. However, each action you have online leaves a traceable footprint that can be viewed by a wide, public, audience. This digital footprint can never be fully erased, and can have either positive or negative effects on the future of an individual. Everything posted online should reflect the best version of yourself.

Discussion Questions What are the risks of oversharing online? What protections should you take before sharing personal information on social media?

Scams and Risks

Scams and Risks Internet scams are often targeted towards inexperienced and trusting groups of people, which includes teenagers and senior citizens. Scams can include contests, offers for grants/scholarships, information farming, false advertisements, fake money transfers, etc. The bottomline is, if something sounds too good to be true, it probably is.

Scams and Risks Identity thieves look for “clean” Social Security numbers that haven’t yet been used to get credit. They target teens and kids, who often have Social Security numbers that have no credit history yet.

Scams and Risks Identity thieves might sell or use these numbers, which would allow someone else to get a credit card or loan and build up debt under your name. Being a victim of identity theft can ruin your financial future and your ability to obtain loans and make purchases. It can take months, even years, to recover your identity if it’s stolen.

Scams and Risks Beware of Phishing: when people send you phony emails, pop-up messages, social media messages, texts, calls, or links to fake websites in order to hook you into giving out your personal and financial information.

Discussion Questions What kinds of personal information identity thieves might look for? How do you think identity thieves might try to get your information? What can you do to avoid falling for online scams?

Identifying High Quality Sites

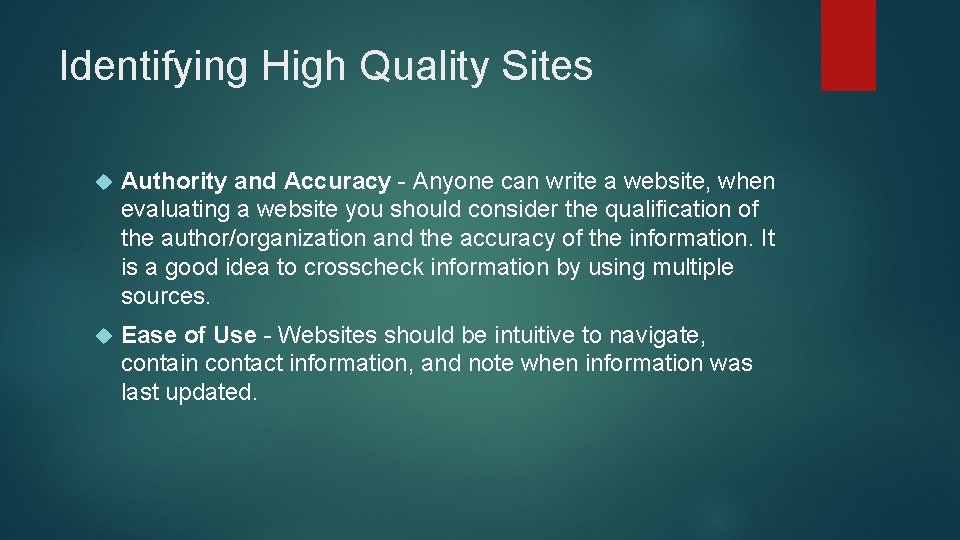
Identifying High Quality Sites Authority and Accuracy - Anyone can write a website, when evaluating a website you should consider the qualification of the author/organization and the accuracy of the information. It is a good idea to crosscheck information by using multiple sources. Ease of Use - Websites should be intuitive to navigate, contain contact information, and note when information was last updated.

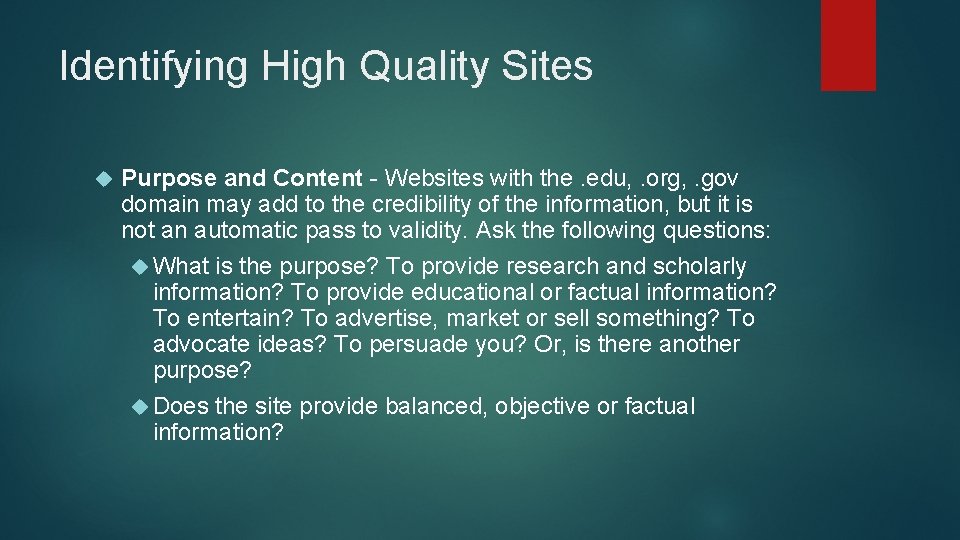
Identifying High Quality Sites Purpose and Content - Websites with the. edu, . org, . gov domain may add to the credibility of the information, but it is not an automatic pass to validity. Ask the following questions: What is the purpose? To provide research and scholarly information? To provide educational or factual information? To entertain? To advertise, market or sell something? To advocate ideas? To persuade you? Or, is there another purpose? Does the site provide balanced, objective or factual information?

Discussion Questions Why is considering website validity important? What are the risks of not evaluating a website before using it for research? for general knowledge? How can you ensure that the information you are using is valid?

Copyright and Fair Use

Key Definitions Copyright: the exclusive legal right, given to an originator or an assignee to print, publish, perform, film, or record literary, artistic, or musical material, and to authorize others to do the same. Fair Use: the doctrine that brief excerpts of copyrighted material may, under certain circumstances, be quoted verbatim for purposes such as criticism, news reporting, teaching, and research, without the need for permission from or payment to the copyright holder.

Key Definitions Public Domain: the state of belonging or being available to the public as a whole, and therefore not subject to copyright. Examples: the copyright has expired the copyright owner failed to follow copyright renewal laws the copyright owner deliberately places it in the public domain, known as “dedication” copyright law does not protect this type of work Plagiarism: the practice of taking someone else's work or ideas and passing them off as one's own.

Discussion Questions Have you ever used creative work you found online – for example, a photo or a poem – for personal use? When you use creative work you find online, what considerations do you make about who made it, if any? What are the ways you can be respectful of people’s creative work?

Are You Always Protected by the First Amendment?

Are You Always Protected by the First Amendment? After his wife left him, petitioner Anthony Douglas Elonis, under the pseudonym “Tone Dougie, ” used the social networking Web site Facebook to post self-styled rap lyrics containing graphically violent language and imagery concerning his wife, co-workers, a kindergarten class, and state and federal law enforcement. These posts were often interspersed with disclaimers that the lyrics were “fictitious” and not intended to depict real persons, and with statements that Elonis was exercising his First Amendment rights. Many who knew him saw his posts as threatening, however, including his boss, who fired him for threatening co-workers, and his wife, who sought and was granted a state court protection-from-abuse order against him. When Elonis’s former employer informed the Federal Bureau of Investigation of the posts, the agency began monitoring Elonis’s Face- book activity and eventually arrested him.

Are You Always Protected by the First Amendment? He was charged with five counts of violating 18 U. S. C. § 875(c), which makes it a federal crime to transmit in interstate commerce “any communication containing any threat. . . to injure the person of another. ” At trial, Elonis requested a jury instruction that the Government was required to prove that he intended to communicate a “true threat. ” Instead, the District Court told the jury that Elonis could be found guilty if a reasonable person would foresee that his statements would be interpreted as a threat. Elonis was convicted on four of the five counts and renewed his jury instruction challenge on appeal. The Third Circuit affirmed, holding that Section 875(c) requires only the intent to communicate words that the defendant understands, and that a reasonable person would view as a threat.

Discussion Questions Do you feel the First Amendment rights of Elonis were violated? To what extent do you believe the First Amendment rights of individuals should be protected online?

Cyber-Bullying

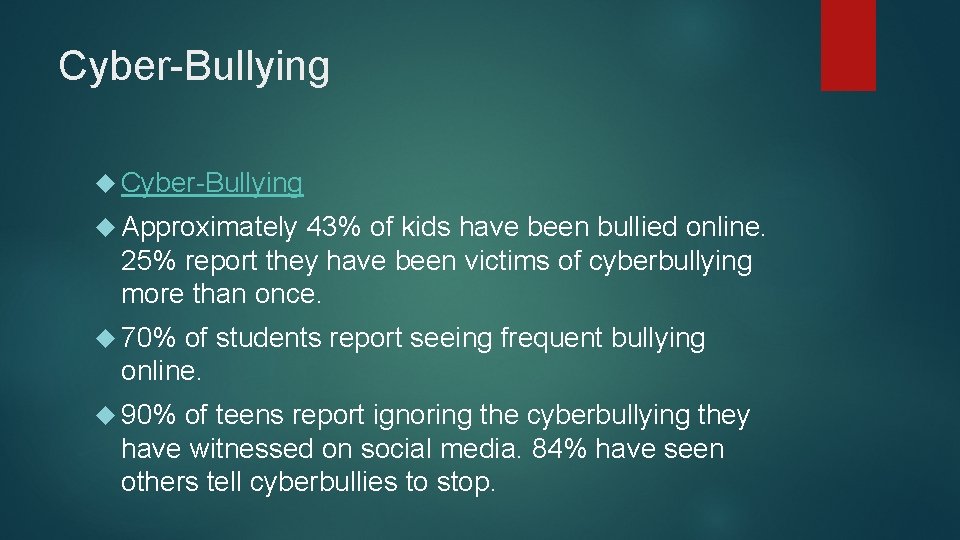
Cyber-Bullying “Cyberbullying” is defined as a young person tormenting, threatening, harassing, or embarrassing another young person using the Internet or other technologies, like cell phones. The psychological and emotional outcomes of cyberbullying are similar to those of real-life bullying.

Cyber-Bullying Approximately 43% of kids have been bullied online. 25% report they have been victims of cyberbullying more than once. 70% of students report seeing frequent bullying online. 90% of teens report ignoring the cyberbullying they have witnessed on social media. 84% have seen others tell cyberbullies to stop.

Cyber-Bullying Only 1 in 10 victims will inform a parent or trusted adult of their abuse online. Girls are about twice as likely as boys to be victims and perpetrators of cyberbullying. Bullying victims are 2 to 9 times more likely to consider committing suicide. About 75% of students admit they have visited a website bashing another student.

Discussion Questions What moral obligations do we have to report cyberbullying? What legal obligations do we have to report cyberbullying? What policies exist in our school/district regarding cyberbullying?

Sexting

What is Sexting? Sexting is sending, receiving, or forwarding sexual photos or sexually suggestive messages through text message, email, or electronic means. Sexting is when someone shares sexual, naked or semi-naked images or videos of themselves or others, or sends sexually explicit messages.

Why is Sexting Dangerous? Sexting can ruin a child's reputation and cause serious emotional and psychological problems. Once a photo is electronically uploaded, it's forever out of your control. An angry ex boyfriend or ex girlfriend can post it publicly for all to see, which could have long-term consequences.

Is Sexting Against the Law? Sexting You is prohibited under child pornography laws. could be arrested and convicted of child pornography trafficking for sending and/or receiving sexually-oriented text messages regardless of how unintentional and innocent the sexting may have been.

What are the Risks of Sexting? No control of images and how they are shared. When images are stored or shared online they become public. Some people may think that images and videos only last a few seconds on social media and then they're deleted, but they can still be saved or copied by others. This means that photos or videos which a young person may have shared privately could still be end up being shared between adults they don't know.

What are the Risks of Sexting? Blackmail - An offender may threaten to share the pictures with the child's family and friends unless the child sends money or more images. Bullying - If images are shared with their peers or in school, the child may be bullied. Unwanted attention - Images posted online can attract the attention of sex offenders, who know how to search for, collect and modify images. Emotional distress - Children can feel embarrassed and humiliated. If they're very distressed this could lead to suicide or self-harm.

Discussion Questions Do you think sexting should be against the law? Can you name at least three consequences that could happen if someone sexted? In the moment-when asked to, or asking someone to sext-why might someone ignore these consequences? Are there worries, pressures, or other considerations that come into play?

Discussion Questions What would it take to make someone think twice before sexting? Why should someone think twice before asking someone to, or sending, a sext? Is it ever okay to sext? Is it okay to pressure others to sext?
 How can your digital footprint affect you in the future
How can your digital footprint affect you in the future Understanding your digital footprint
Understanding your digital footprint Whats a digital footprint
Whats a digital footprint Whats a digital footprint
Whats a digital footprint Digital footprint calculator
Digital footprint calculator Digital footprint impact
Digital footprint impact Jonathan franzen digital footprint
Jonathan franzen digital footprint Digital footprint presentation
Digital footprint presentation Digital footprint game
Digital footprint game Give us your hungry your tired your poor
Give us your hungry your tired your poor Digital markets and digital goods
Digital markets and digital goods Ecological footprint ap human geography example
Ecological footprint ap human geography example Islandwood ecological footprint
Islandwood ecological footprint Ecological footprint map
Ecological footprint map Ecological footprint components
Ecological footprint components Iso 14067
Iso 14067 Overshoot definition apes
Overshoot definition apes Water footprint beer
Water footprint beer Ecological footprint worksheet
Ecological footprint worksheet Calculating ecological footprint involves consideration of
Calculating ecological footprint involves consideration of Whats an ecological footprint
Whats an ecological footprint Water footprint network
Water footprint network Ecological footprint game
Ecological footprint game Water art concepts
Water art concepts Water footprint turkey
Water footprint turkey Trillion dollar footprint answers
Trillion dollar footprint answers Sustrax
Sustrax Footprint
Footprint It footprint
It footprint Pjm footprint
Pjm footprint Unity footprint
Unity footprint Actual self and ideal self similarities
Actual self and ideal self similarities Pengertian warga digital
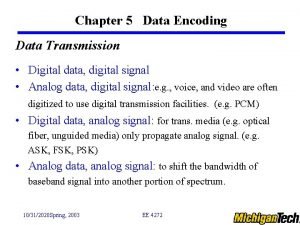
Pengertian warga digital Digital data digital signals
Digital data digital signals Digital data transmission
Digital data transmission E-commerce: digital markets, digital goods
E-commerce: digital markets, digital goods Signal encoding techniques in data communication
Signal encoding techniques in data communication Rdi board
Rdi board E-commerce digital markets digital goods
E-commerce digital markets digital goods Your conscious awareness of your own name and self identity
Your conscious awareness of your own name and self identity My wish for you is that life becomes
My wish for you is that life becomes Introduction to information technology: your digital world
Introduction to information technology: your digital world Introduction to information technology: your digital world
Introduction to information technology: your digital world Accept your loneliness you are your only friend
Accept your loneliness you are your only friend Stop blaming your parents for your problems
Stop blaming your parents for your problems What side is your heart on
What side is your heart on A poem is a little path
A poem is a little path How to introduce your friend to your teacher
How to introduce your friend to your teacher Wear your heart on your sleeve idiom meaning
Wear your heart on your sleeve idiom meaning Write your responses in your notebook
Write your responses in your notebook In your notebook define the following terms
In your notebook define the following terms Enagic comp plan
Enagic comp plan Show me your ways o lord teach me your paths
Show me your ways o lord teach me your paths Loss of forward vision
Loss of forward vision Write an article for your school magazine
Write an article for your school magazine Where your treasure is there your heart will be also
Where your treasure is there your heart will be also