Virtual Private Networks VPN Crypto Party London Tuesday



























- Slides: 45

Virtual Private Networks (VPN) Crypto. Party London Tuesday 18 th December 2018 @Crypto. Party. LDN https: //cryptoparty. in/london @Spy. Blog

Threat Model • What are you trying to protect ? Assume: – IP address privacy – Internet Connection Location privacy – Protection from Man-In-The-Middle Attacks especially on Public “Free” Wi. Fi internet connections – Free speech in censored internet environments – Ability to access streaming content you have paid for in license restricted regions or countries

Threat Model • Who are you trying to protect yourself from ? – – – – – UK and Foreign Intelligence Agencies UK and Foreign Law Enforcement Organised Criminal Gangs Terrorists Opportunistic thieves Corporate mercenary spies Stalkers Political factions and opponents Hacktivists Advertisers

Threat Model • How likely that they target you ? – High risk of general Mass Surveillance sweeps by the State or by powerful advertisers / Face. Book / Google – your data may come to haunt you in the future e. g. Tf. L Tube Wi. Fi tracking – Medium risk of Watering Hole attacks i. e. everyone at a particular Wi. Fi enabled café to grab banking details, but not aimed at you personally – Low risk of a stalker aiming specifically at you

Threat Model • How Risky is their activity to you ? – State level attackers - low immediate risk if you are just part a Mass Surveillance sweep. Higher risk of “guilt by association” after pattern analysis – High risk of exposure of confidential meetings / informants by State and Advertising Surveillance – Medium to high (financial) risk if caught up by Watering Hole attack by criminals – High to very high personal safety risk from a stalker who is tracking your location

Individuals at high risk • Journalists and Confidential Sources / Whistleblowers • Political activists • Public figures attracting social media, harassment women in general, but also in certain tech niches e. g. Bit. Coin pioneers – Jameson Lopp @lopp uses a VPN all the time, just to hide his Home Address (life was put at risk by SWATing - false report to armed police)

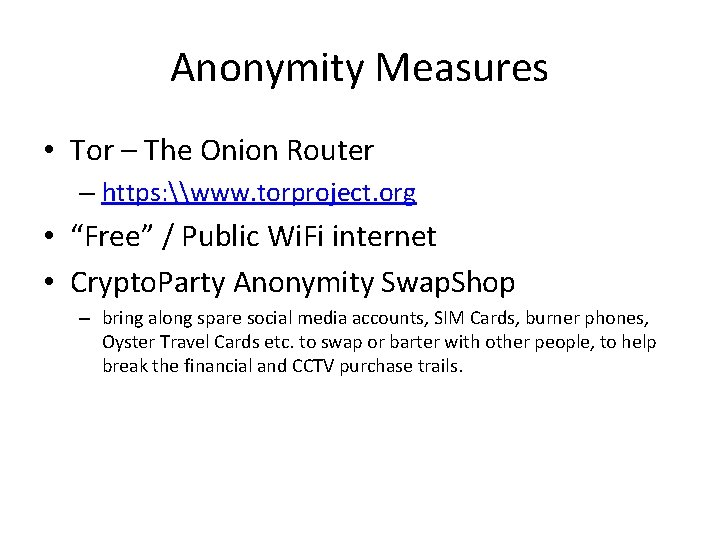
Anonymity Measures • Tor – The Onion Router – https: \www. torproject. org • “Free” / Public Wi. Fi internet • Crypto. Party Anonymity Swap. Shop – bring along spare social media accounts, SIM Cards, burner phones, Oyster Travel Cards etc. to swap or barter with other people, to help break the financial and CCTV purchase trails.

Secrecy Countermeasures • Encryption – using mathematically strong Cryptographic algorithms and well tested Key generation and storage software / hardware • Steganography – hiding or obscuring exactly what you are doing without raising suspicions triggering closer examination

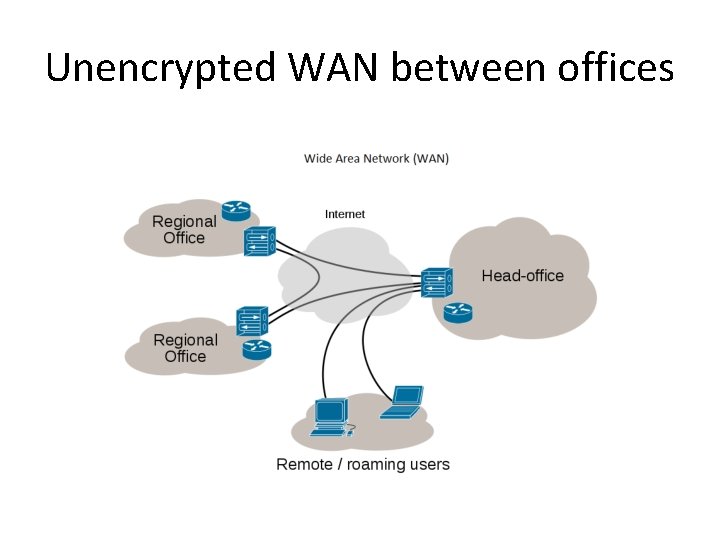
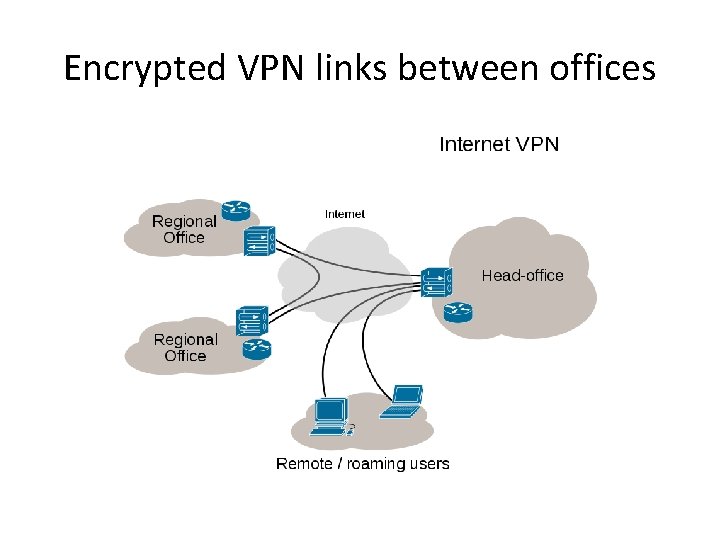
What is a VPN ? • Usually a Point To Point Encrypted Tunnel created by software to work on top of an existing Internet Connection passing through the Internet hardware infrastructure as seamlessly as possible. • Developed originally for, and widely used by Companies and Government departments with multiple regional office locations, linked by a shared (non-private) communications infrastructure e. g. the Internet

Unencrypted WAN between offices

Encrypted VPN links between offices

VPN performance • A Local Area Network at Home or at Work runs at e. g. 1 Gigabit per second (1000 Megabits per second – both downlink and uplink speed) • Wide Area Network links e. g. Wi. Fi hotspots run at e. g. 10 to 150 Megabits per second (also equally fast downlink and uplink) • Internet gateway links are usually asymmetrical only 2 to 60 Megabits per second downlink, often no more than 16 to 20 Megabits per second uplink

VPN performance • Encryption adds an overhead e. g. 10 to 20% slower / less throughput per second. • Big file transfers will take a bit longer via an encrypted VPN, but unless you are running e. g. a Web Server or Peer to Peer server sharing music or movies etc. then you won’t notice this on a typical PC or laptop or Smart. Phone

Choosing a VPN service • “Free” VPN are exactly what you should expect, • No guarantee of Performance or Privacy, • Claims about “No logs” not always true – may effectively be logged indirectly by their upstream Internet Service Provider, who will comply with legal warrants & often informal requests from Law Enforcement regardless • Free” VPN App are usually funded by Adverts, so the Advertising networks will log your usage • Some “Free” VPN Apps aimed at authoritarian countries actually have malware / deliberate backdoors • Avoid

Choosing a VPN service • There are dozens of VPN service providers, none of them are perfect and it will take several days to review them all in detail. • Decide if anti-censorship or copyright enforcement evasion is most important to you. – Commercial VPN with Points of Presence in suitable *foreign* countries – typically cost £ 5 to £ 10 per month i. e. as much as a low end Home internet connection

Choosing a VPN service • Choose the right VPN protocol on offer • Ignore Point To Point Tunnelling Protocol (PPTP) – although commonly offered by VPN suppliers and built in to current and old versions of Microsoft Windows etc. , the Cryptography is weak by modern standards • Ignore IPSEC even though this is built in to modern operating systems – it needs Corporate levels of skilled IT staff support, or closed source VPN clients e. g. from Cisco, Juniper etc. and is less commonly offered by VPN suppliers

Choosing a VPN service • Choose a VPN supplier offering the Open. VPN protocol • https: //en. wikipedia. org/wiki/Open. VPN • Well regarded VPN suppliers include – https: //www. expressvpn. com/ – https: //www. privateinternetaccess. com/ – https: //nordvpn. com

Proton VPN • https: //protonvpn. com/ • Set up by the well regarded free & commercial Encrypted Email provider set up by CERN scientists in Geneva , Switzerland. – Switzerland has strong privacy laws, *not* a full member of #5 EYES, but obviously some cooperation on terrorism & crime, less on tax evasion

Proton VPN • • • Has VPN clients for most platforms – Windows, Apple Mac, Linux, Android and i. OS Reasonably large number of Points of Presence in foreign countries as well as UK Paid for service handles Netflix etc. streaming from USA 1 device 3 country unlimited bandwith service for free as a subsidised loss leader (all VPN providers have some introductory discounts or offers) Offers some VPN then Tor servers Own private DNS servers Connection Kill Switch (if VPN connection breaks, stops leak of your real IP ) Requires a Registration Email Address (does not have to be Proton. Mail, but c. f. Anonymity Swapshop for setting up burner email accounts Payment via Credit Card (not the cheapest VPN)

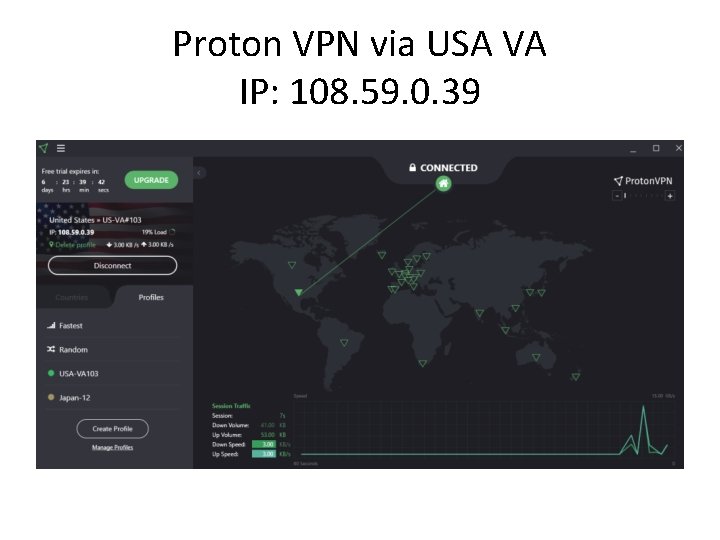
Proton VPN via USA VA IP: 108. 59. 0. 39

Proton VPN via Japan IP: 185. 242. 4. 206

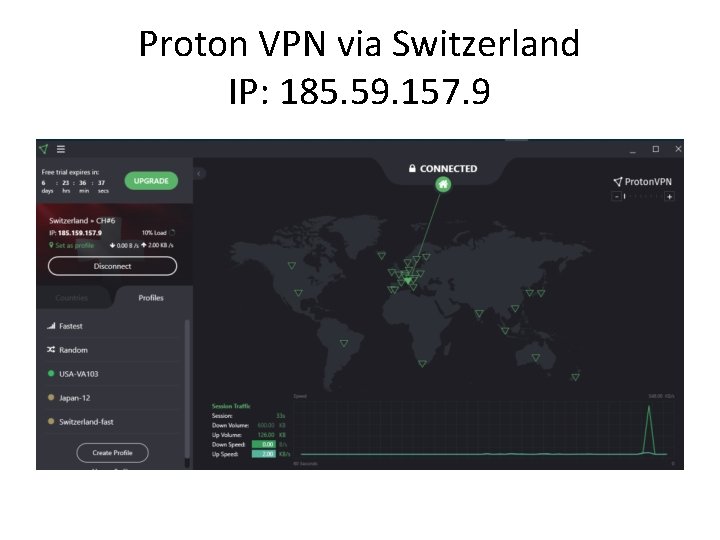
Proton VPN via Switzerland IP: 185. 59. 157. 9

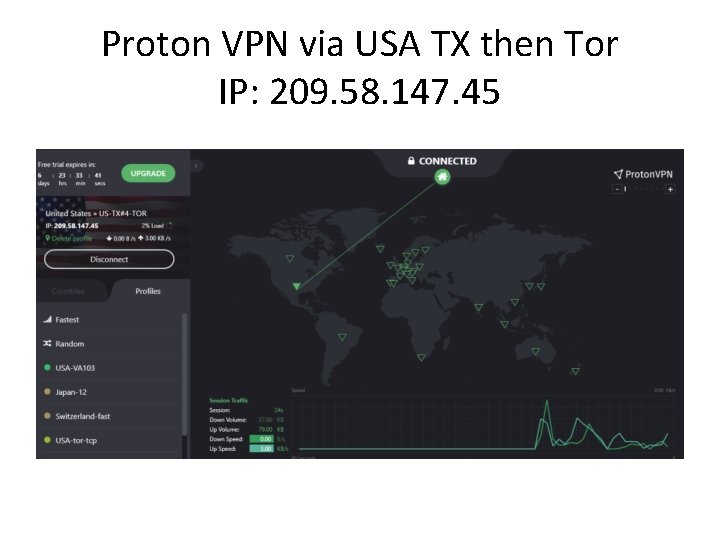
VPN then Tor • Proton VPN offer some of their servers which immediately hop onto the Tor privacy cloud, rather than exiting directly onto the public internet

Proton VPN via USA TX then Tor IP: 209. 58. 147. 45

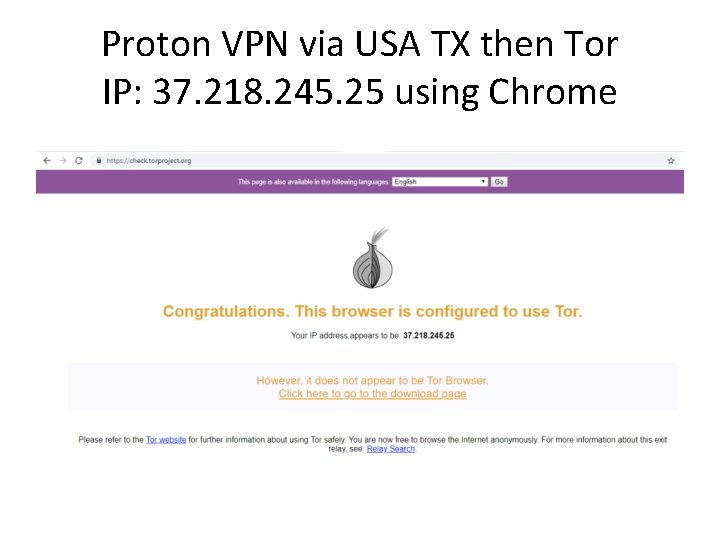
Proton VPN via USA TX then Tor IP: 37. 218. 245. 25 using Chrome

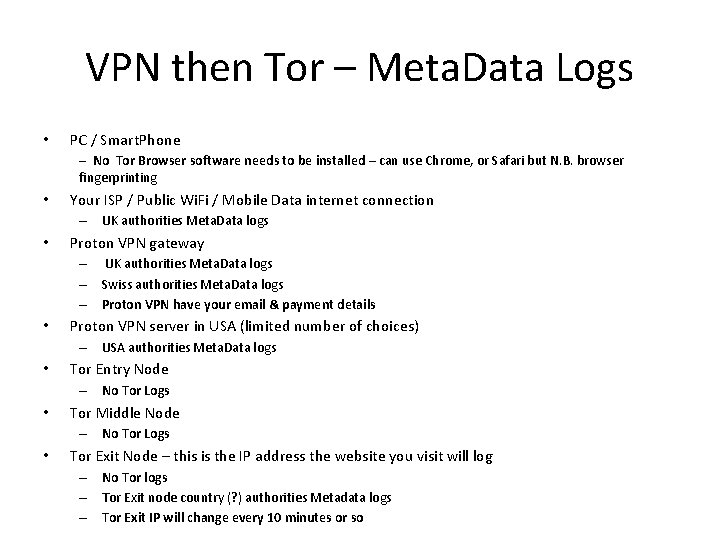
VPN then Tor – Meta. Data Logs • PC / Smart. Phone – No Tor Browser software needs to be installed – can use Chrome, or Safari but N. B. browser fingerprinting • Your ISP / Public Wi. Fi / Mobile Data internet connection – UK authorities Meta. Data logs • Proton VPN gateway – UK authorities Meta. Data logs – Swiss authorities Meta. Data logs – Proton VPN have your email & payment details • Proton VPN server in USA (limited number of choices) – USA authorities Meta. Data logs • Tor Entry Node – No Tor Logs • Tor Middle Node – No Tor Logs • Tor Exit Node – this is the IP address the website you visit will log – No Tor logs – Tor Exit node country (? ) authorities Metadata logs – Tor Exit IP will change every 10 minutes or so

VPN then Tor • Tor Browser looks exactly like it does when using Your ISP or public Wi. Fi connection

VPN Iceland then Tor Browser Bundle IP: 185. 159. 158. 58

VPN Iceland then Tor Browser Bundle IP: 51. 38. 69. 128

Tor Browser via VPN – Meta. Data Logs • PC / Smart. Phone – needs Tor Browser software installed – may be incriminating if seized • Your ISP / Public Wi. Fi / Mobile Data internet connection – UK authorities Meta. Data logs • Proton VPN gateway – UK authorities Meta. Data logs – Swiss authorities Meta. Data logs – Proton VPN have your email & payment details • Proton VPN server in Iceland (random pick) – Icelandic authorities Meta. Data logs • Tor Entry Node – No Tor Logs • Tor Middle Node – No Tor Logs • Tor Exit Node – this is the IP address the website you visit will log – No Tor logs – Tor Exit node country (? ) authorities Metadata logs – Tor Exit IP will change every 10 minutes or so

Tor then VPN • This is an advanced topic for which there is no time for today • It is possible to run Tor first and then connect to a VPN account, reducing any Meta. Data that the VPN service can reveal. • You can configure the SOCKS 5 proxy and the Tor Browser configuration file • Else use QUBES and Whonix virtual machines and a Tor only network gateway

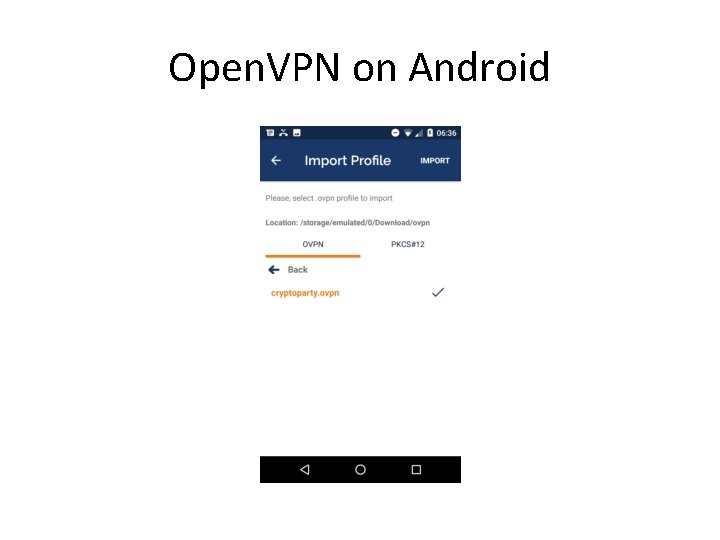
Open. VPN profiles and Smart. PHONES • Installing the Open. VPN App on Android from the Play. Store or on i. OS from the App Store is straightforward. • The hardest part of setting up a working VPN connection is sometimes simply getting the. ovpn configuration profiles imported into a Smart. Phone App

. ovpn profile

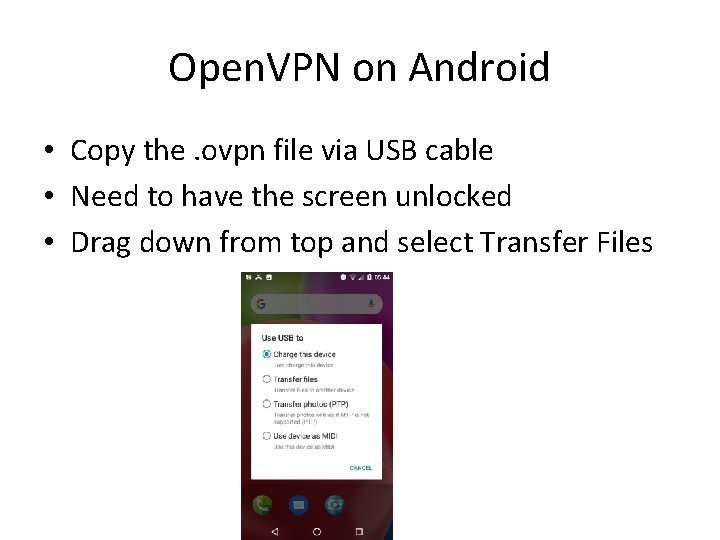
Open. VPN on Android • Copy the. ovpn file via USB cable • Need to have the screen unlocked • Drag down from top and select Transfer Files

Open. VPN on Android

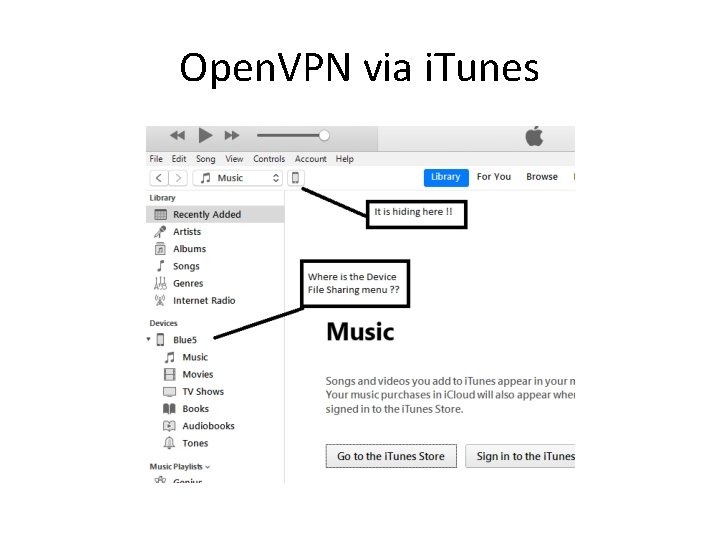
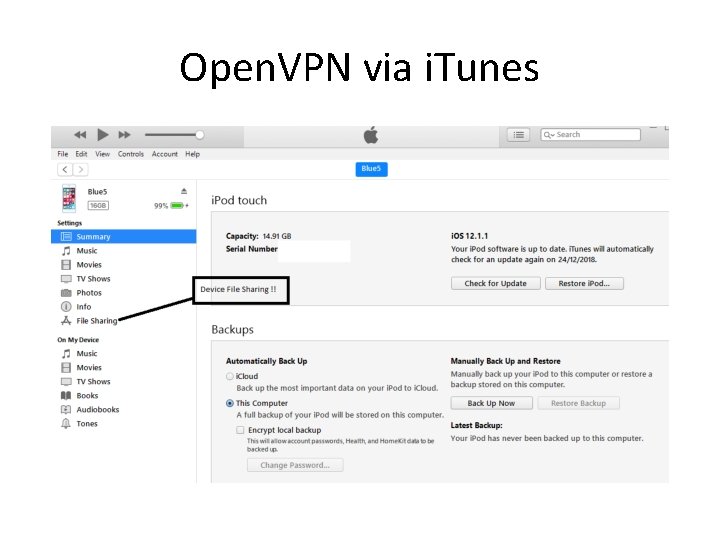
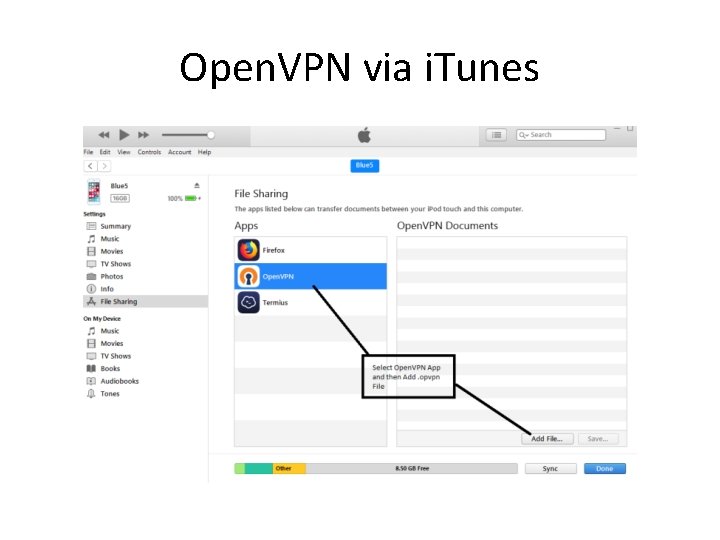
Open. VPN via i. Tunes • Plug in the USB / Lightning cable and or dongles & adapters • Latest i. OS requires Passphrase entry to enable USB interface • N. B. awful i. Tunes user interface hides away the Device File Sharing menu

Open. VPN via i. Tunes

Open. VPN via i. Tunes

Open. VPN via i. Tunes

Run your own Open. VPN server • A VPN service costs £ 60 to £ 200 a year • For that money you can run your own Open. VPN server using a Raspberry Pi and your Home / Office broadband internet connection, which you are not using when travelling or on public Wi. Fi etc. • Obviously a UK based home VPN server won’t help with censorship / copyright evasion, but will protect you from Man-In-the-Middle-Attacks • It also protects your Location privacy i. e. “always at home” to social media even when at a Crypto. Party or a protest etc.

Pi. VPN • http: //www. pivpn. io/ • Easy script to set up Open. VPN on latest Raspian and Debian 16

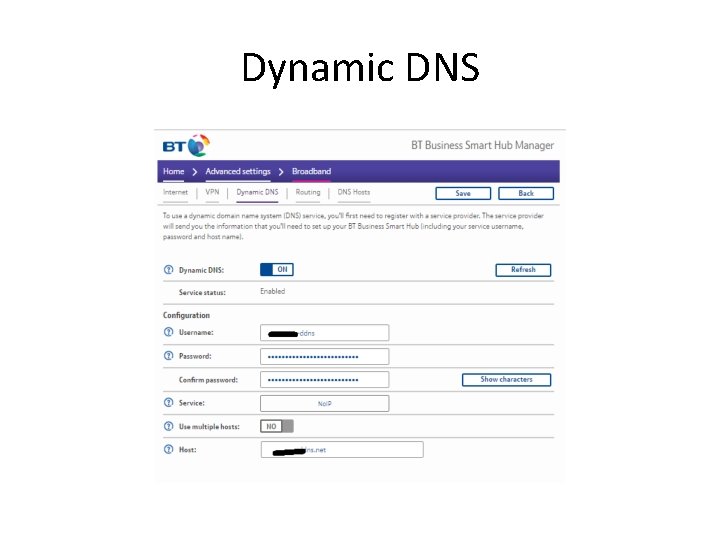
Dynamic DNS • https: //www. noip. com/ • Either download a background service application which updates e. g. cryptoparty. ddns. net with your Dynamic IP Address every 5 minutes, running on a machine on your Home / Office LAN • Or configure your e. g. BT Wi. Fi router with the DDNS credentials

Dynamic DNS

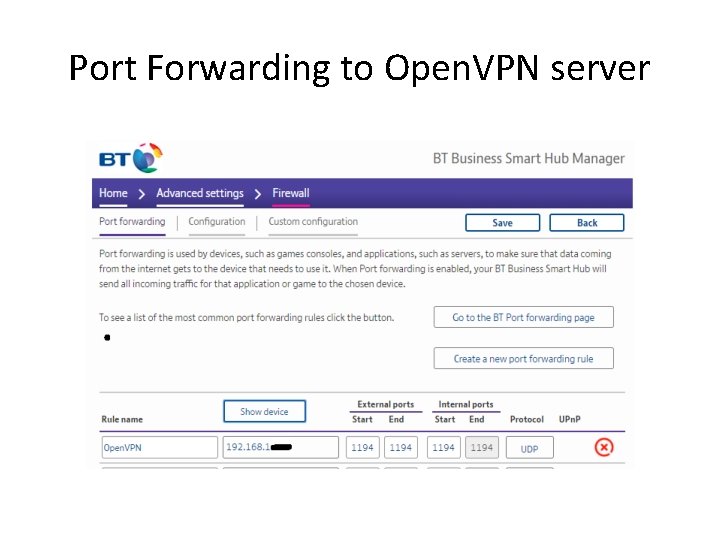
Port Forwarding to Open. VPN server

Tor Browser & Pi. VPN – Meta. Data Logs • PC / Smart. Phone – needs Tor Browser software installed – may be incriminating if seized • Your ISP / Public Wi. Fi / Mobile Data internet connection – UK authorities Meta. Data logs • Pi. VPN gateway – UK authorities Meta. Data logs – No VPN email or payment details – cheaper than annual VPN service – Location privacy – always appear “at home” to social media even when at a Crypto. Party • Tor Entry Node – No Tor Logs • Tor Middle Node – No Tor Logs • Tor Exit Node – this is the IP address the website you visit will log – No Tor logs – Tor Exit node country (? ) authorities Metadata logs – Tor Exit IP will change every 10 minutes or so
 Vc vs datagram
Vc vs datagram Crypto private key storage
Crypto private key storage Ipsec vs ssl vpn
Ipsec vs ssl vpn Ncsu vpn
Ncsu vpn Third party vs fourth party
Third party vs fourth party Backbone networks in computer networks
Backbone networks in computer networks Private industrial networks
Private industrial networks Crypto des
Crypto des Crypto des
Crypto des Sudoku crypto
Sudoku crypto Crypto des
Crypto des Window.crypto.subtle.generatekey
Window.crypto.subtle.generatekey Nandita beri
Nandita beri Propchain
Propchain My crypto world
My crypto world Ctf
Ctf Ecb electronic signature
Ecb electronic signature Ghsp crypto
Ghsp crypto Riga cripto
Riga cripto Santa crypto
Santa crypto Mmaps crypto
Mmaps crypto Short. term. crypto. predictions.
Short. term. crypto. predictions. Ryan patrick crypto
Ryan patrick crypto Pink slip cripto
Pink slip cripto Xec crypto projet
Xec crypto projet 16mod9
16mod9 Lmrst crypto
Lmrst crypto Crypto
Crypto Credit default swap crypto
Credit default swap crypto Abcd arabe crypto
Abcd arabe crypto Crypto
Crypto Safeastro crypto
Safeastro crypto Timelock crypto
Timelock crypto Nomads definition world history
Nomads definition world history Crypto
Crypto Fabriik crypto
Fabriik crypto Vpn protocols wiki
Vpn protocols wiki Virtual private network
Virtual private network Apa itu shared hosting
Apa itu shared hosting Has virtual functions and accessible non-virtual destructor
Has virtual functions and accessible non-virtual destructor Monday tuesday wednesday thursday friday calendar
Monday tuesday wednesday thursday friday calendar Tuesday please
Tuesday please Tuesdays with morrie first chapter
Tuesdays with morrie first chapter Tuesday morning prayers
Tuesday morning prayers Feathered friend by arthur c clarke
Feathered friend by arthur c clarke Tuesday morning prayers
Tuesday morning prayers