Chapter 30 Private Networks Virtual Private Networks and

















- Slides: 39

Chapter 30 Private Networks, Virtual Private Networks, and Network Address Translation

Outline o o o PRIVATE NETWORKS VIRTUAL PRIVATE NETWORKS (VPN) NETWORK ADDRESS RESOLUTION (NAT)

30. 1 PRIVATE NETWORKS The Mc. Graw-Hill Companies, Inc. , 2000

Private Networks o o Designed to be used inside an organization Intranet n n o A private network (LAN) that uses the TCP/IP protocol suite However, access to the private network is limited only to the users inside the organization Extranet n The same as an intranet with one major difference o n Some resources may be accessed by specific groups of uses outside the organization under the control of the network administrators For example, a university can allow distance learning students access to the computer lab after passwords have been checked

Addressing o A private network has its IP address by the following three methods n The network can apply for a set of addresses from the Internet authorities and use them without being connected to the Internet o o n Advantage: easy when the organization decides to be connected to the network Disadvantage: the address space is wasted The network can use any set of addresses without registering with the Internet authorities o The network can use any set of addresses without registering with the Internet authorities n n Because the network is isolated, the address do not have to be unique Drawback: users might mistakenly confuse the address as part of the global network

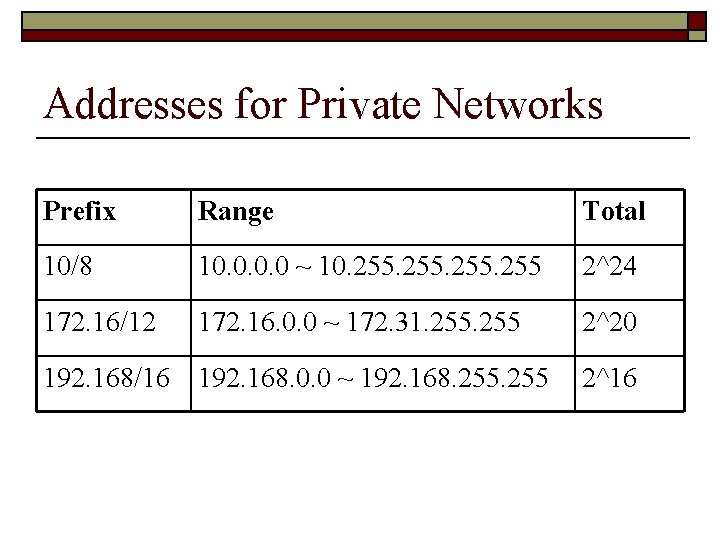
Addressing (Cont. ) n The internet authorities have reserved three sets of addresses to overcome the problems in previous two strategies o o Without permission from the Internet authorities Everybody knows that these reserved addresses are for private networks Unique inside the organization, but not unique globally No router will forward a packet that has one of these address as the destination address

Addresses for Private Networks Prefix Range Total 10/8 10. 0 ~ 10. 255 2^24 172. 16/12 172. 16. 0. 0 ~ 172. 31. 255 2^20 192. 168/16 192. 168. 0. 0 ~ 192. 168. 255 2^16

30. 2 VIRTUAL PRIVATE NETWORKS (VPN) The Mc. Graw-Hill Companies, Inc. , 2000

Virtual Private Networks (VPN) o Use the global Internet for both intra- and inter-organization communication n o But require privacy in their intra-organization communication How to achieving Privacy n Three strategies: private networks, hybrid networks, and virtual private networks

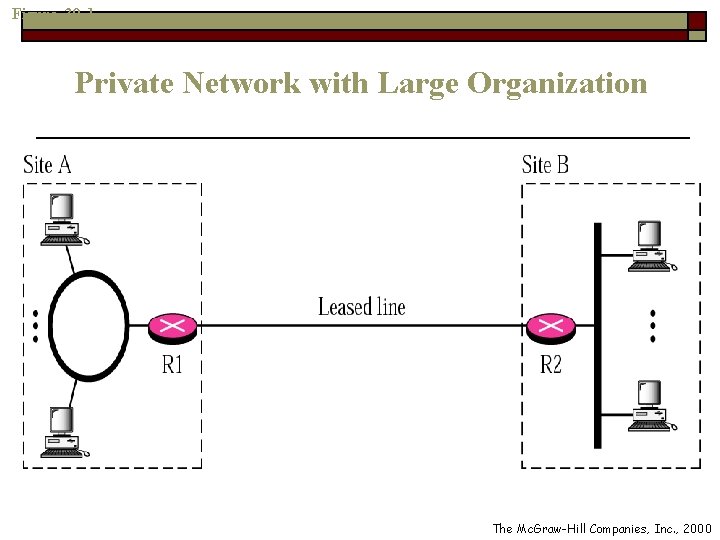
Private Networks o o An organization that needs privacy when routing information inside the organization can use a private network Small organization with one single site n n o Can use an isolated LAN Data in the organization is totally remain inside the organization, secure from outsiders Large organization with several sites n n The LANs at different site can be connected using routers and leased lines Thus, network is made out of private LANs and private WANs

Figure 30 -1 Private Network with Large Organization The Mc. Graw-Hill Companies, Inc. , 2000

Private Networks (Cont. ) o Thus, the organization has created a private internet that is totally isolated from the global Internet o There is no need for the organization to apply for IP addresses with the Internet authorities n Because the internet is private, duplication of addresses by another organization in the global Internet is not a problem

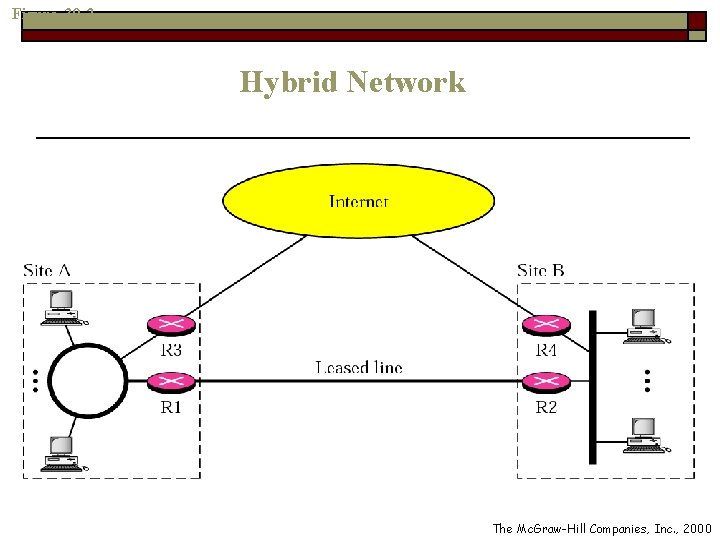
Hybrid Network o o However, above scenario does not allow the organizations to be connected to the global Internet Solution: hybrid network n Allow a organization to have its own private internet o n Intraorganization data is routed through private network And allow to access to the global Internet o Interorganization data is routed through global Internet

Figure 30 -2 Hybrid Network The Mc. Graw-Hill Companies, Inc. , 2000

Virtual Private Networks o Both private and hybrid networks have a major drawback: cost n n o o Private wide area networks are expensive To connect several sites, an organization needs several leased lines Goal: use the global Internet for both private and public communication Solution: virtual private network (VPN)

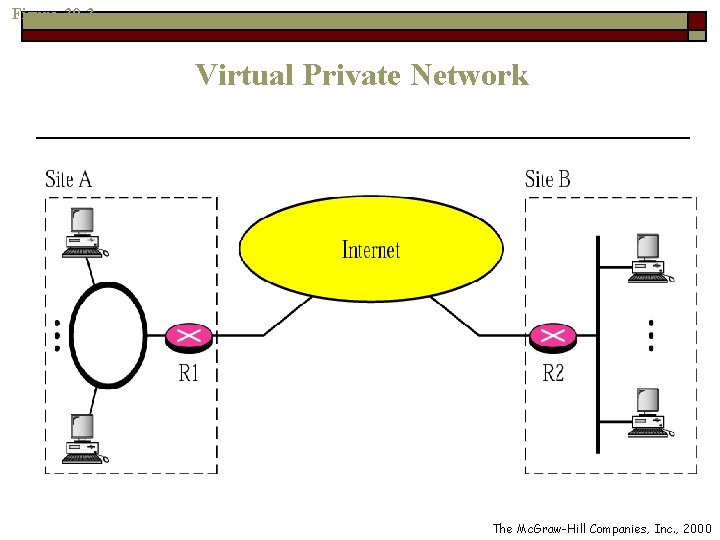
Virtual Private Networks (Cont. ) o VPN creates a network that is private but virtual n Private: it guarantees privacy inside an organization n Virtual: it does not use real private WANs o The network is physically public but virtually private

Figure 30 -3 Virtual Private Network The Mc. Graw-Hill Companies, Inc. , 2000

VPN Technology o VPN uses two simultaneous technologies to guarantee privacy for an organization n IPSec n Tunneling

IPSec o Discussed in Chapter 29 o A virtual private network can use either AH or ESP for authentication and privacy

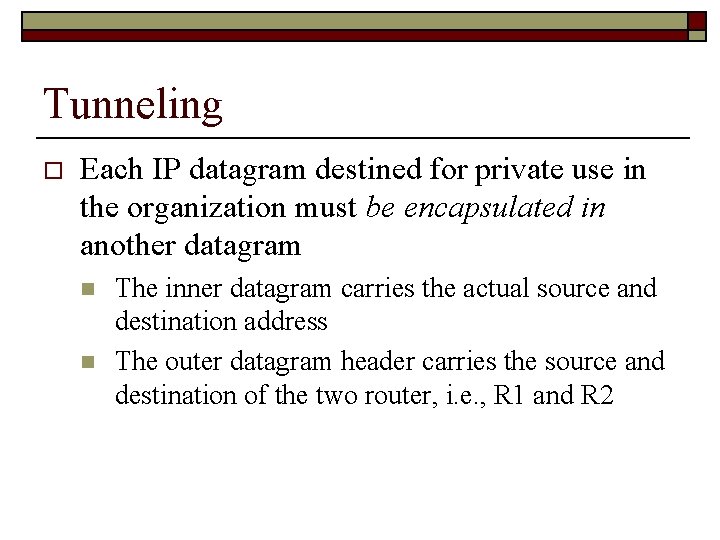
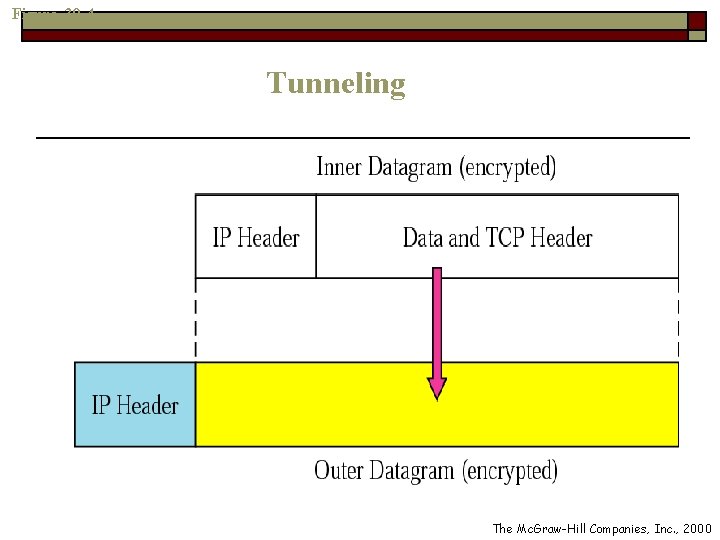
Tunneling o Each IP datagram destined for private use in the organization must be encapsulated in another datagram n n The inner datagram carries the actual source and destination address The outer datagram header carries the source and destination of the two router, i. e. , R 1 and R 2

Figure 30 -4 Tunneling The Mc. Graw-Hill Companies, Inc. , 2000

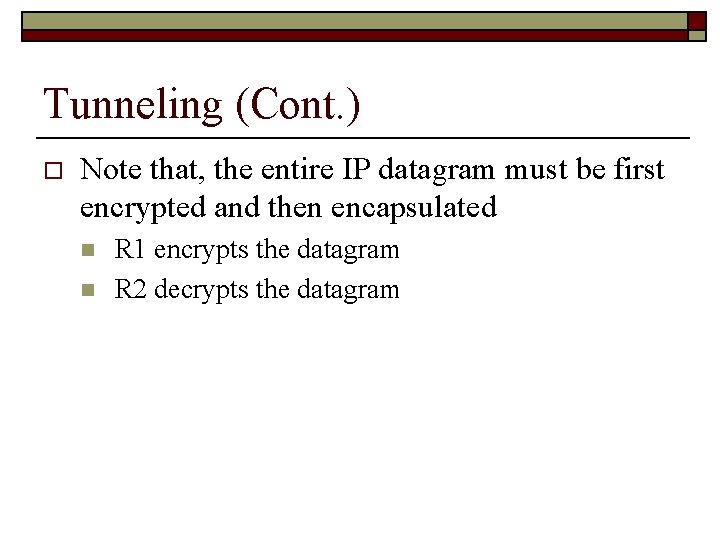
Tunneling (Cont. ) o Note that, the entire IP datagram must be first encrypted and then encapsulated n n R 1 encrypts the datagram R 2 decrypts the datagram

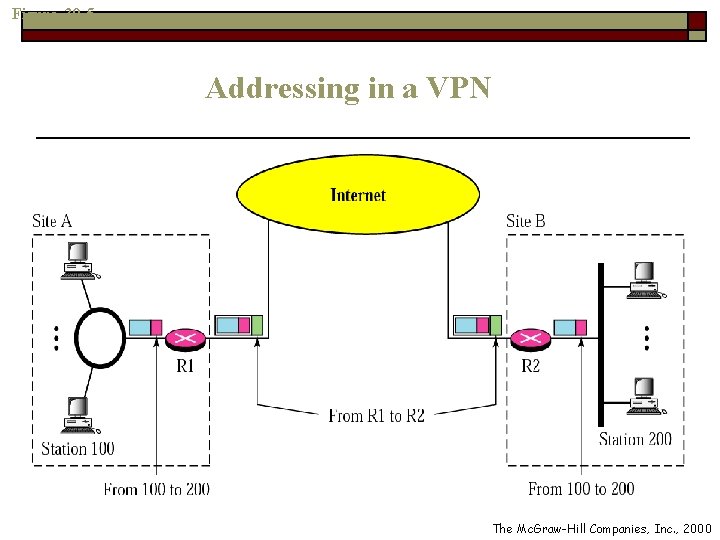
Figure 30 -5 Addressing in a VPN The Mc. Graw-Hill Companies, Inc. , 2000

30. 3 NETWORK ADDRESS TRANSLATION (NAT) The Mc. Graw-Hill Companies, Inc. , 2000

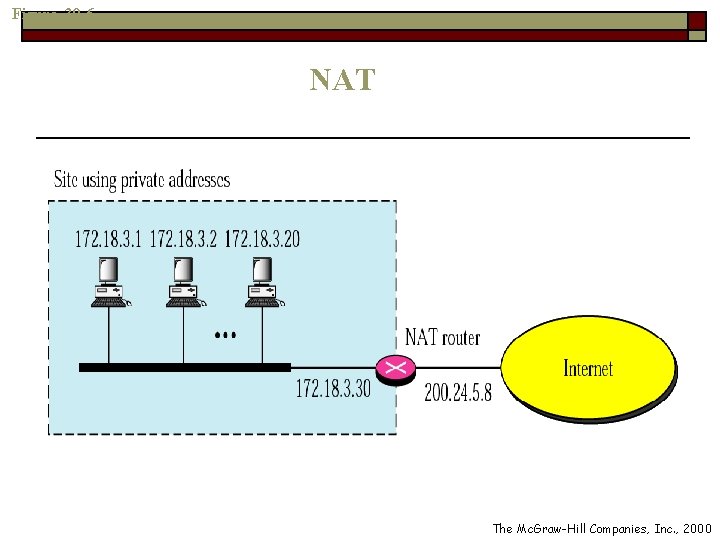
Network Address Translation (NAT) o Allow n n o A set of private addresses for internal communication A set of (at least one) global Internet addresses for communication with another site From the next slide n n The private network uses private addresses The NAT router uses one private address and one global address o The rest of the internet sees only the NAT router with the address 200. 24. 5. 8

Figure 30 -6 NAT The Mc. Graw-Hill Companies, Inc. , 2000

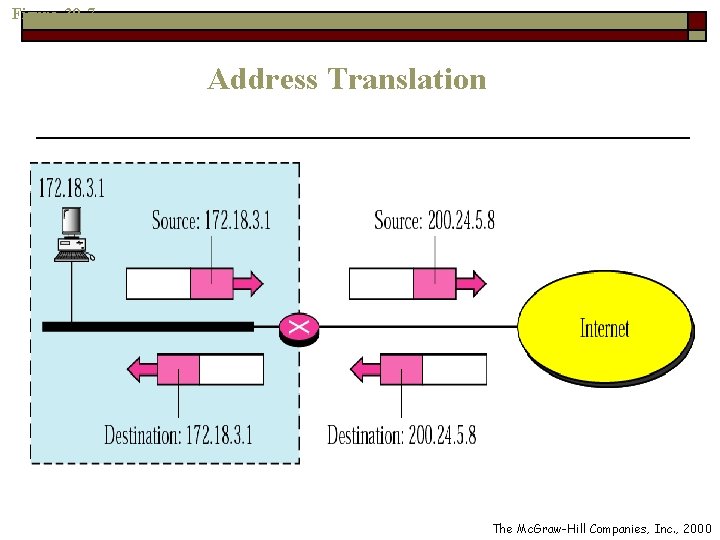
Address Translation o NAT n Replaces the source address of all outgoing packets with the global NAT address n Replace the destination address of all incoming packets with the appropriate private address

Figure 30 -7 Address Translation The Mc. Graw-Hill Companies, Inc. , 2000

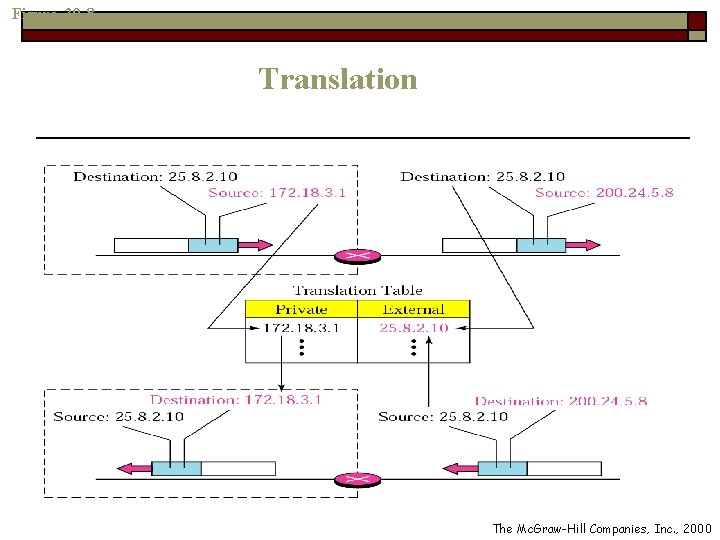
Translation Table o Used by the NAT to drive the destination address for a packet coming from the Internet o Three cases n n n Using one IP address Using a Pool of IP addresses Using Both IP addresses and Port numbers

Using One IP Address o The translation table has only two columns n n o The private address The external address (destination address of the packet) When the router translates the source address of the outgoing packet n It also make note of the destination address, where the packet is going

Figure 30 -8 Translation The Mc. Graw-Hill Companies, Inc. , 2000

Using One IP Address (Cont. ) o Communication must always be initiated by the private network o Thus, a private network cannot run a server program for clients outside of its network if it is using NAT technology

Using a Pool of IP Addresses o Using only one global address allows only one private-network host to access the same external host Solution: using a pool of IP addresses o For example, if the NAT can use four address o n Four private-network hosts can communicate with the same external host at the same time

Using a Pool of IP Addresses (Cont. ) o Drawbacks n n n No more than four connections can be made to the same destination No private-network host can access two external server program (e. g. , HTTP and TELNET) at the same time Two private-network hosts cannot access the same external server program at the same time

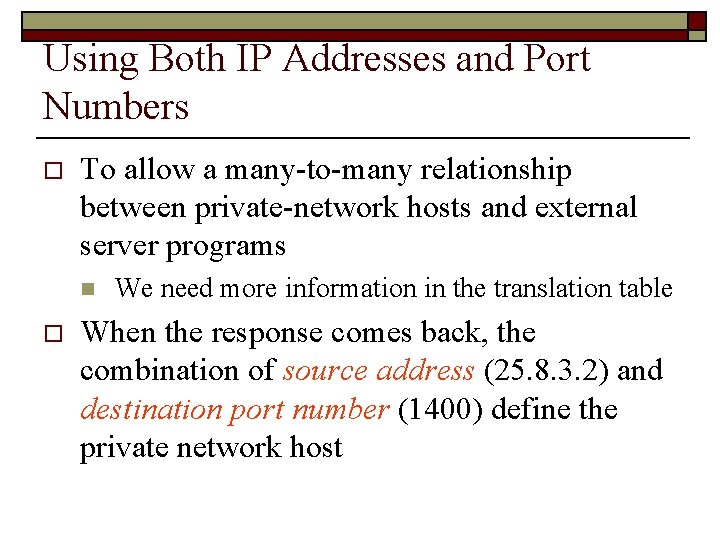
Using Both IP Addresses and Port Numbers o To allow a many-to-many relationship between private-network hosts and external server programs n o We need more information in the translation table When the response comes back, the combination of source address (25. 8. 3. 2) and destination port number (1400) define the private network host

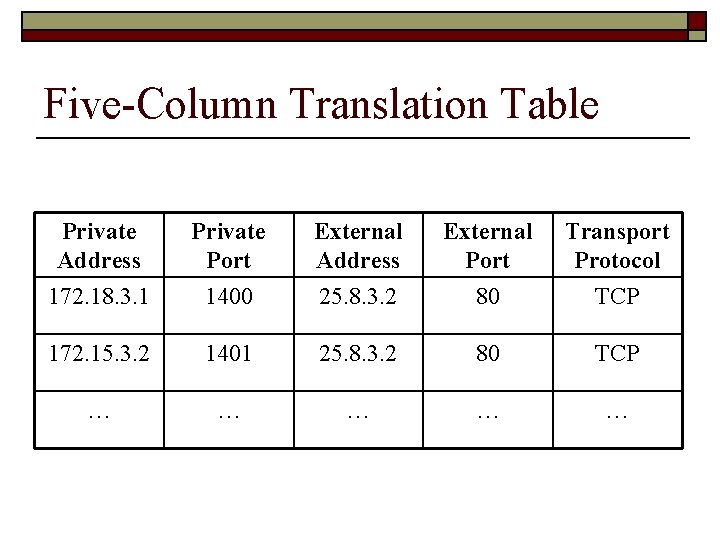
Five-Column Translation Table Private Address Private Port External Address External Port Transport Protocol 172. 18. 3. 1 1400 25. 8. 3. 2 80 TCP 172. 15. 3. 2 1401 25. 8. 3. 2 80 TCP … … …

Using Both IP Addresses and Port Numbers o Thus, for this translation to work, the temporary port number (1400 and 1401) must be unique

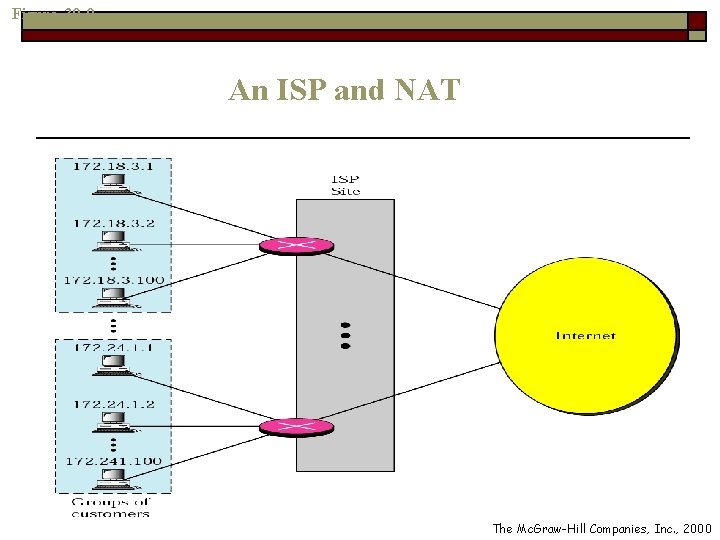
NAT and ISP o o An ISP the serves dial-up customers can use NAT technology to conserve address For example, an ISP is granted 1000 addresses n n But has 100, 000 customers The ISP can divide the customers into 1000 groups o Each group is a private network

Figure 30 -9 An ISP and NAT The Mc. Graw-Hill Companies, Inc. , 2000