Transport Layer Computer Networks Spring 2000 John Kristoff





- Slides: 34

Transport Layer Computer Networks Spring 2000 John Kristoff 1

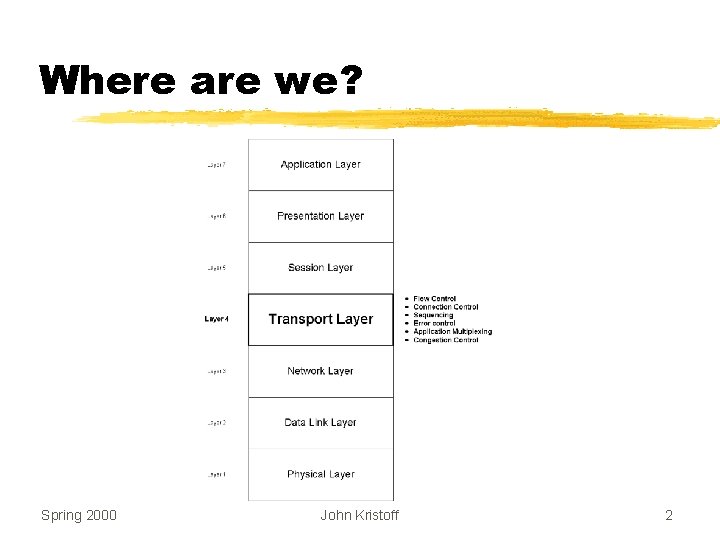
Where are we? Spring 2000 John Kristoff 2

Recall z. Network Layer y. Provides host-to-host communication y. Source and destination addresses are computers y. Machine-to-machine networking Spring 2000 John Kristoff 3

Transport Protocols z Provide application-to-application communication z Need extended addressing mechanism to identify applications z Called end-to-end z Optionally provide: x. Reliability x. Flow Control x. Congestion Control Spring 2000 John Kristoff 4

Example Transport Layer: Transmission Control Protocol (TCP) z Standardized by IETF as RFC 793 z Most popular layer 4 protocol z Connection-oriented protocol z Conceptually between applications and IP z Full-duplex operation z Byte-stream interface z Of utmost importance for this class! z The book: TCP/IP Illustrated, Volume I - W. R. Stevens Spring 2000 John Kristoff 5

TCP Feature Summary Provides a completely reliable (no data duplication or loss), connection-oriented, full-duplex stream transport service that allows two application programs to form a connection, send data in either direction and then terminate the connection. Spring 2000 John Kristoff 6

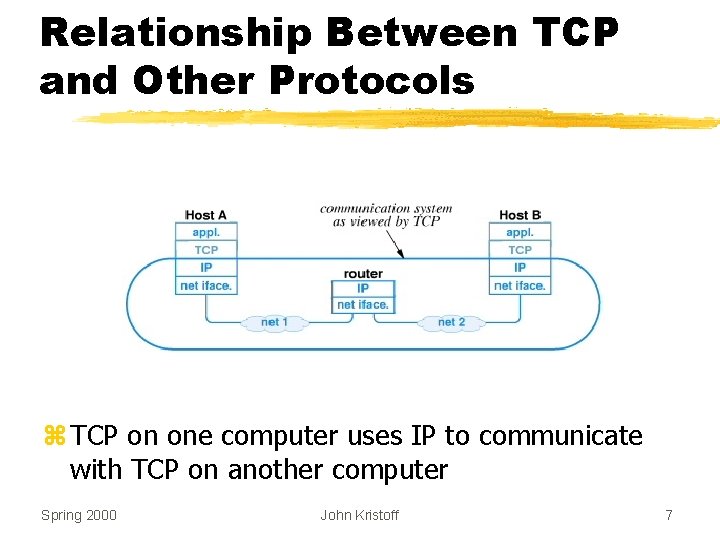
Relationship Between TCP and Other Protocols z TCP on one computer uses IP to communicate with TCP on another computer Spring 2000 John Kristoff 7

Apparent Contradiction z. IP offers best-effort (unreliable) delivery z. TCP uses IP z. TCP provides completely reliable transfer z. How is this possible? Spring 2000 John Kristoff 8

Achieving Reliability z. Reliable connection setup z. Reliable data transmission z. Reliable connection shutdown Spring 2000 John Kristoff 9

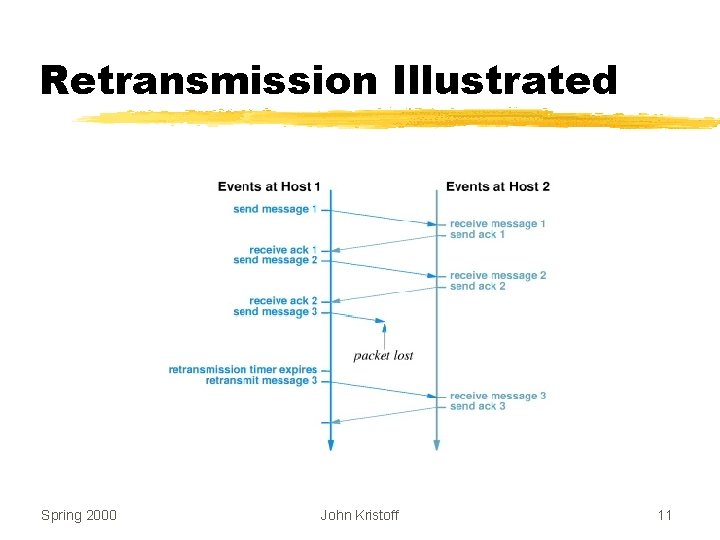
Reliable Data Transmission z. Positive Acknowledgement y. Receiver returns short message when data arrives y. Call an acknowledgement z. Retransmission y. Sender starts timer whenever message is transmitted y. If timer expires before acknowledgement arrives, sender retransmits message Spring 2000 John Kristoff 10

Retransmission Illustrated Spring 2000 John Kristoff 11

How Long Should TCP Wait Before Retransmitting? z. Time for acknowledgement to arrive depends on y. Distance to destination y. Current traffic conditions z. Multiple connections can be open simultaneously z. Traffic conditions change rapidly Spring 2000 John Kristoff 12

Important Point The delay required for data to reach a destination and an acknowledgement to return depends on traffic in the internet as well as the distance to the destination. Since it allows multiple application programs to communicate with multiple destinations concurrently, TCP must handle a variety of delays that can change rapidly. Spring 2000 John Kristoff 13

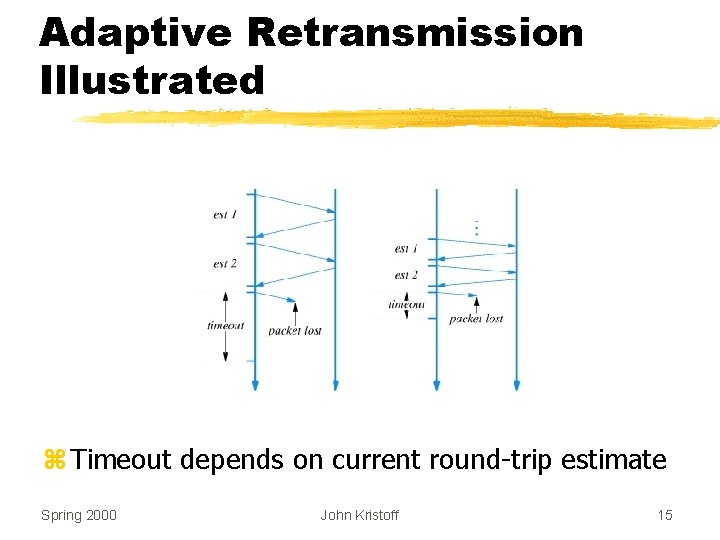
Solving the Retransmission Problem z. Keep estimate of round trip time on each connection z. Use current estimate to set retransmission timer z. Known as adaptive retransmission z. Key to TCP’s success Spring 2000 John Kristoff 14

Adaptive Retransmission Illustrated z Timeout depends on current round-trip estimate Spring 2000 John Kristoff 15

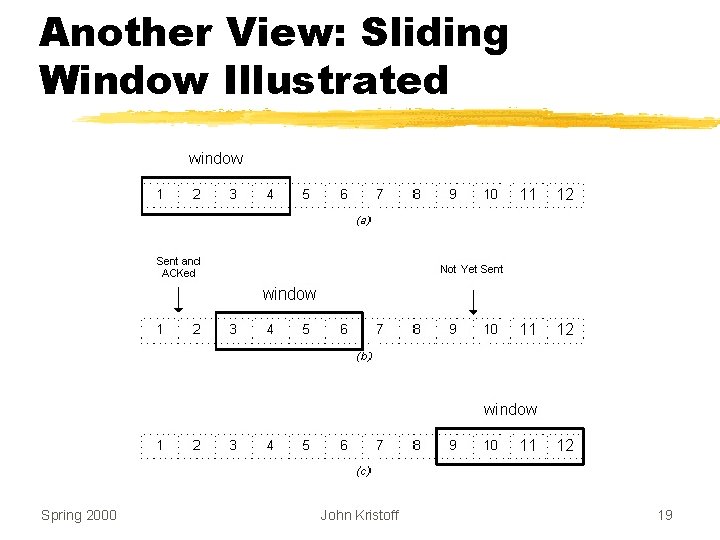
TCP Flow Control z. Receiver y. Advertises available buffer space y. Called the window z. Sender y. Can send up to entire window before ACK arrives z. Also called a sliding window protocol Spring 2000 John Kristoff 16

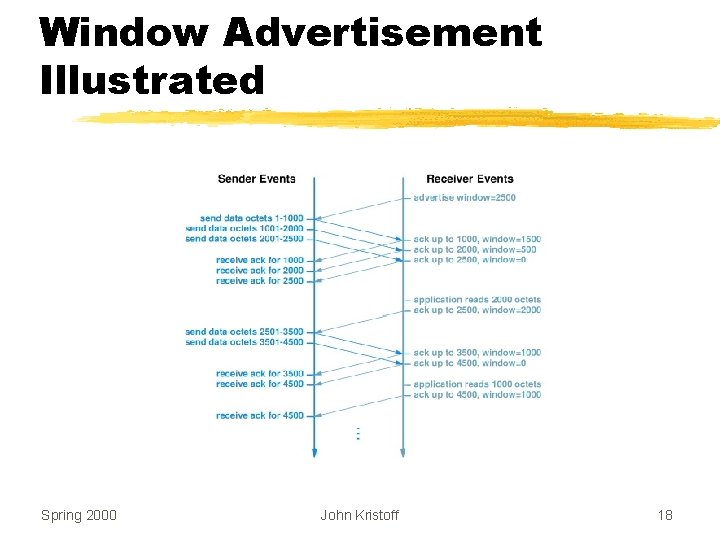
Window Advertisement z. Each acknowledgement carries new window information y. Call window advertisement y. Can be zero (called closed window) z. Interpretation: I have received up through X and can take Y more octets Spring 2000 John Kristoff 17

Window Advertisement Illustrated Spring 2000 John Kristoff 18

Another View: Sliding Window Illustrated Spring 2000 John Kristoff 19

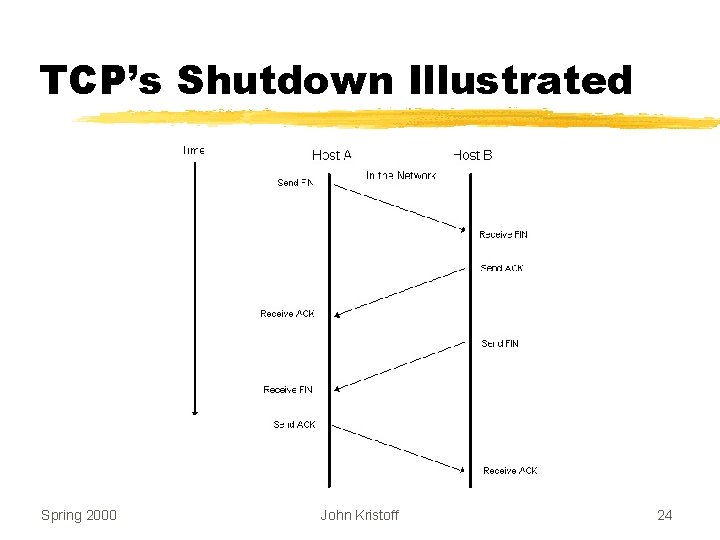
Startup and Shutdown z. Connection Startup y. Must be reliable z. Connection Shutdown y. Must be graceful z. Difficult Spring 2000 John Kristoff 20

Why Startup/Shutdown is Difficult z. Segments can be ylost yduplicated ydelayed ydelivered out of order yeither side can crash yeither side can reboot z. Need to avoid duplicate shutdown “message” from affecting later connection Spring 2000 John Kristoff 21

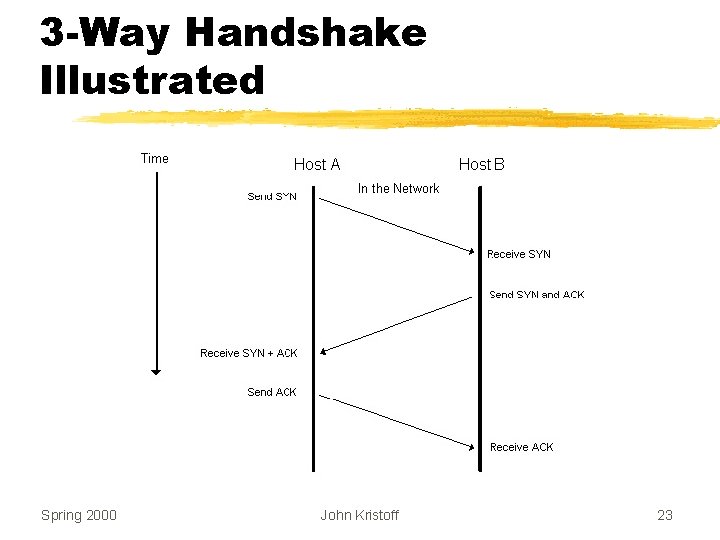
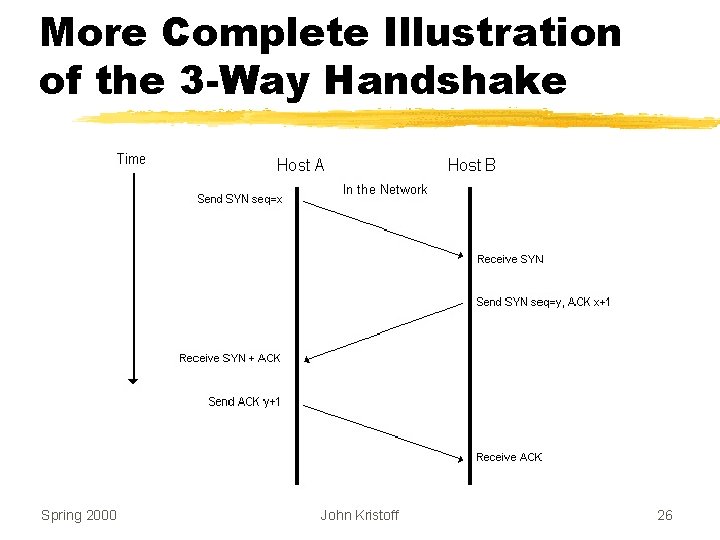
TCP’s Startup Solution z. Use three-message exchange z. Known as the 3 -way handshake z. Necessary and sufficient for unambiguous, reliable startup z. SYN messages used for connection establishment Spring 2000 John Kristoff 22

3 -Way Handshake Illustrated Spring 2000 John Kristoff 23

TCP’s Shutdown Illustrated Spring 2000 John Kristoff 24

Byte Stream Sequencing z Segments are labeled with a sequence number z Protects from out-of-order delivery z 32 -bit number z Limited size of byte stream? z Initial Sequence Numbers (ISNs) must be exchanged at TCP connection establishment Spring 2000 John Kristoff 25

More Complete Illustration of the 3 -Way Handshake Spring 2000 John Kristoff 26

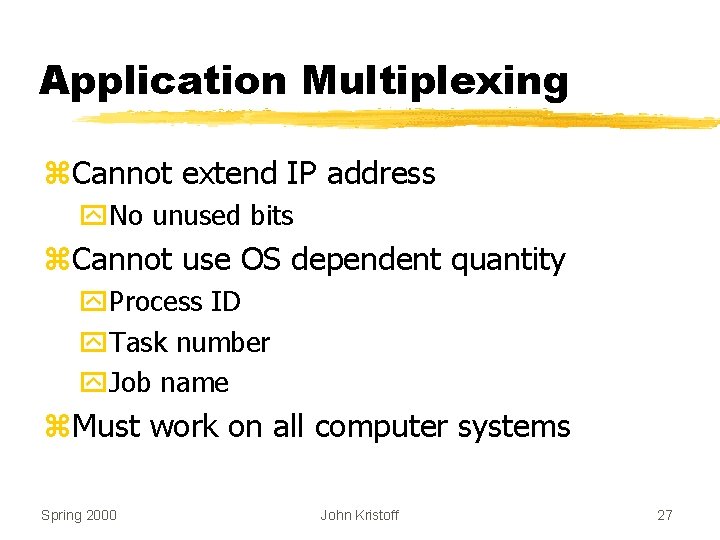
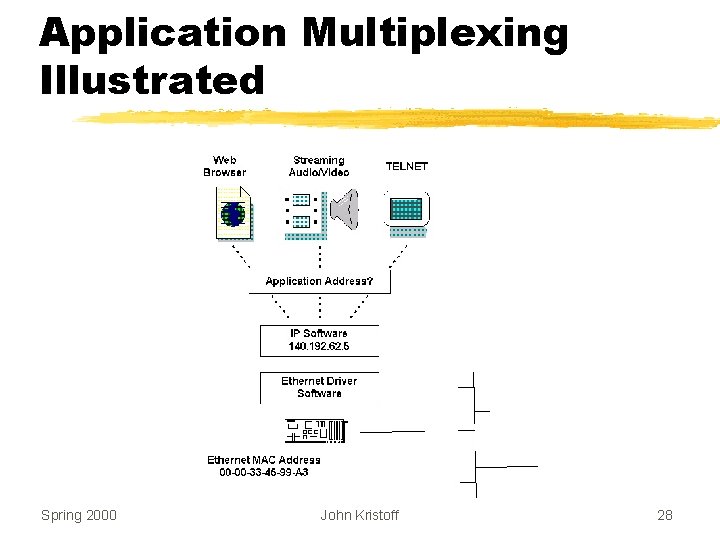
Application Multiplexing z. Cannot extend IP address y. No unused bits z. Cannot use OS dependent quantity y. Process ID y. Task number y. Job name z. Must work on all computer systems Spring 2000 John Kristoff 27

Application Multiplexing Illustrated Spring 2000 John Kristoff 28

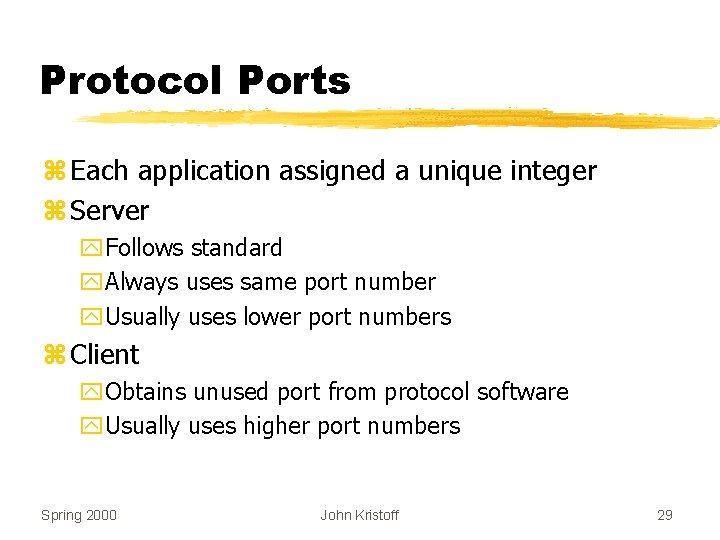
Protocol Ports z Each application assigned a unique integer z Server y. Follows standard y. Always uses same port number y. Usually uses lower port numbers z Client y. Obtains unused port from protocol software y. Usually uses higher port numbers Spring 2000 John Kristoff 29

Protocol Port Example z Web server application is assigned port 80 z Web client application obtains port 32938 z TCP segment sent from client to server has ysource port number 32938 ydestination port number 80 z When web server responds, TCP segment has ysource port number 80 ydestination port number 32938 Spring 2000 John Kristoff 30

Standard Protocol Ports z See http: //www. iana. org for standard protocol port assignments z See /etc/services in UNIX systems and winntsystem 32driversetcservices in Windows NT Spring 2000 John Kristoff 31

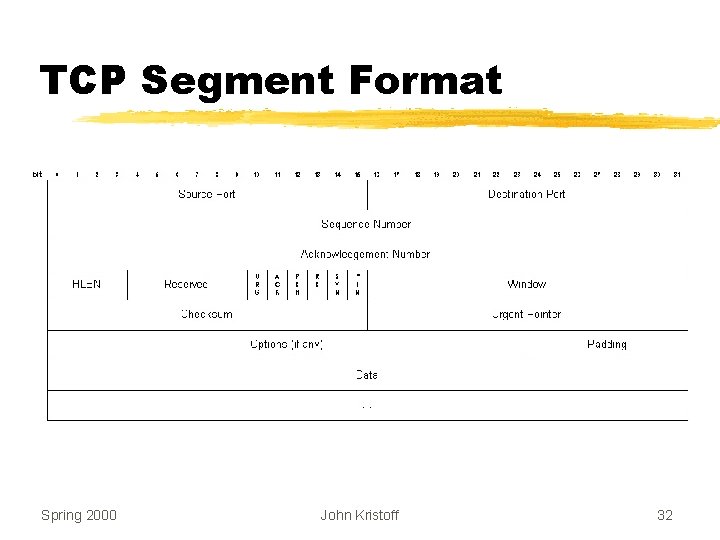
TCP Segment Format Spring 2000 John Kristoff 32

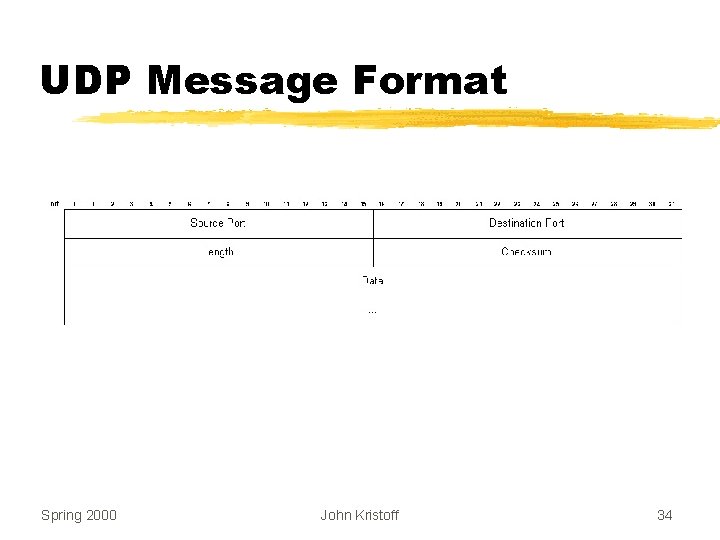
Example Transport Layer: User Datagram Protocol (UDP) z. Unreliable message delivery z. Connectionless protocol z. No flow control (no window) z. No error recovery (no ACKs) z. Provides application multiplexing z. Error detection optional (checksum field) Spring 2000 John Kristoff 33

UDP Message Format Spring 2000 John Kristoff 34