Congestion Control Computer Networks Autumn 2000 John Kristoff


- Slides: 21

Congestion Control Computer Networks Autumn 2000 John Kristoff 1

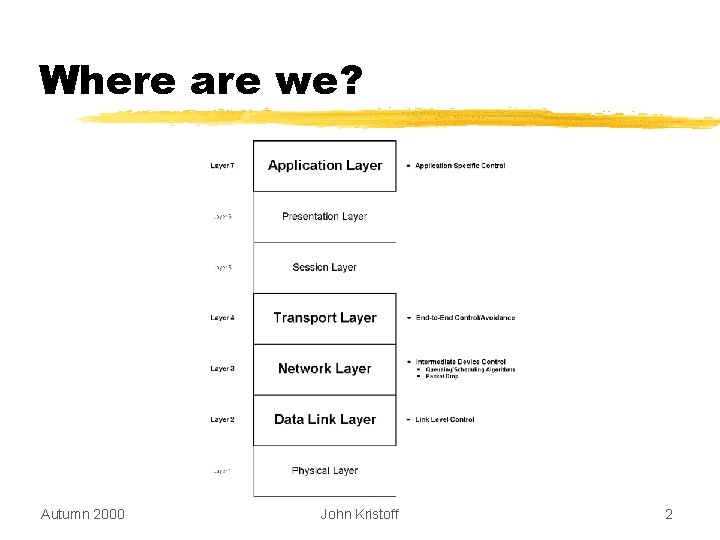
Where are we? Autumn 2000 John Kristoff 2

Recall Ñ Data Link Layer Ñ Link level specific transmission Ñ Network Layer Ñ End-to-End host addressing and routing Ñ Transport Layer Ñ End-to-End application multiplexing and message flow-control An expert: Sally Floyd <http: //www. aciri. org/floyd/> An expert: Van Jacobson Autumn 2000 John Kristoff 3

Note Flow control is a subset of congestion control. The former attempts to properly match the rate of the sender with that of the network and receiver. The later deals with the sustained overload of intermediate network elements such as internetwork routers. Autumn 2000 John Kristoff 4

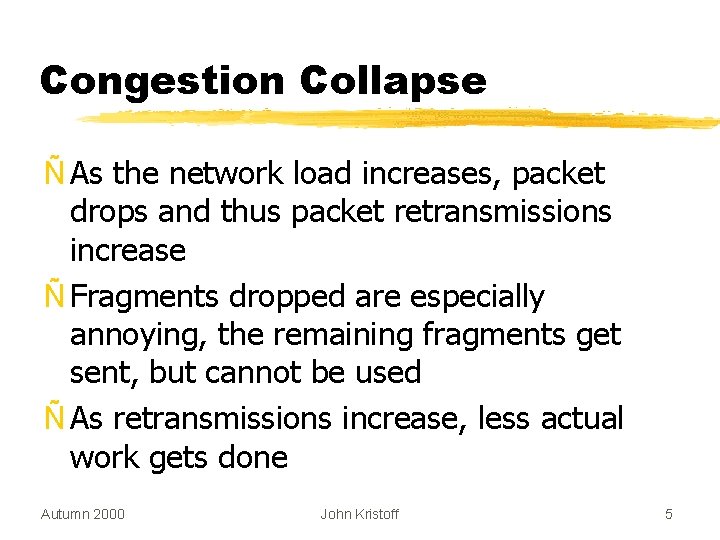
Congestion Collapse Ñ As the network load increases, packet drops and thus packet retransmissions increase Ñ Fragments dropped are especially annoying, the remaining fragments get sent, but cannot be used Ñ As retransmissions increase, less actual work gets done Autumn 2000 John Kristoff 5

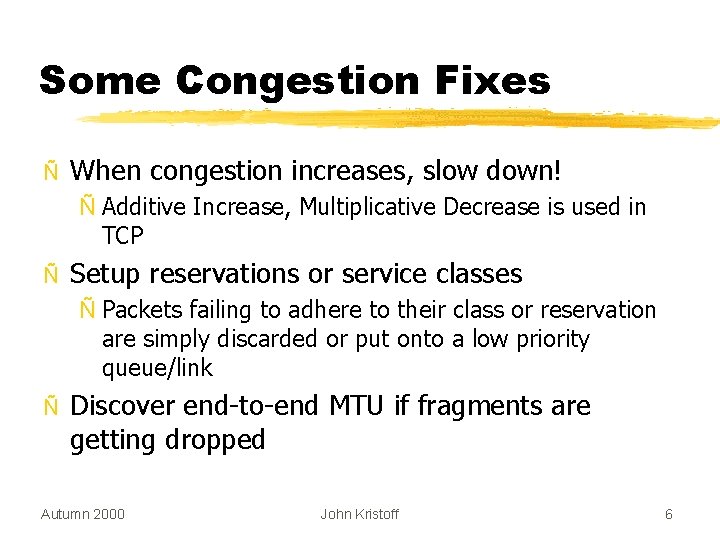
Some Congestion Fixes Ñ When congestion increases, slow down! Ñ Additive Increase, Multiplicative Decrease is used in TCP Ñ Setup reservations or service classes Ñ Packets failing to adhere to their class or reservation are simply discarded or put onto a low priority queue/link Ñ Discover end-to-end MTU if fragments are getting dropped Autumn 2000 John Kristoff 6

Fairness Ñ Equal share bandwidth to end stations Ñ Fair share based on application Ñ Fair share based on timeliness of data Ñ Fair share based on value of data Ñ Fair share based on price paid Ñ. . . and so on Autumn 2000 John Kristoff 7

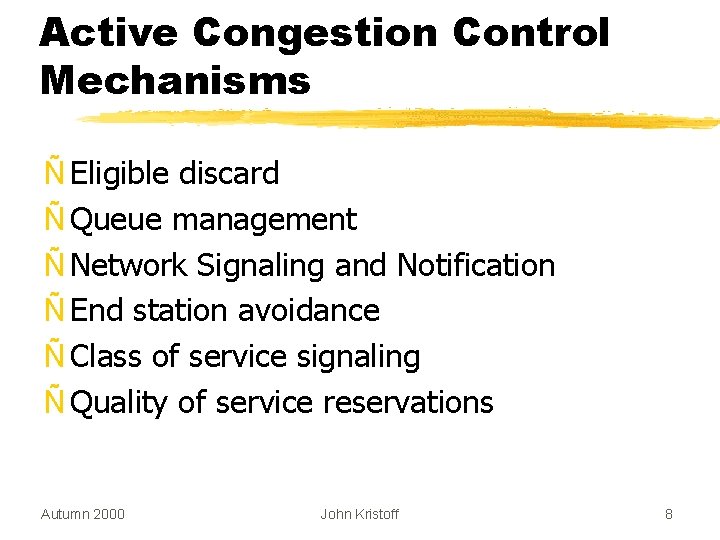
Active Congestion Control Mechanisms Ñ Eligible discard Ñ Queue management Ñ Network Signaling and Notification Ñ End station avoidance Ñ Class of service signaling Ñ Quality of service reservations Autumn 2000 John Kristoff 8

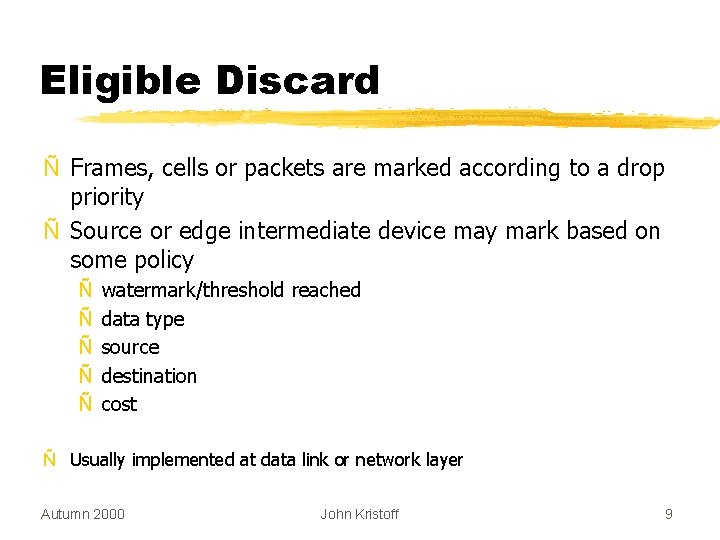
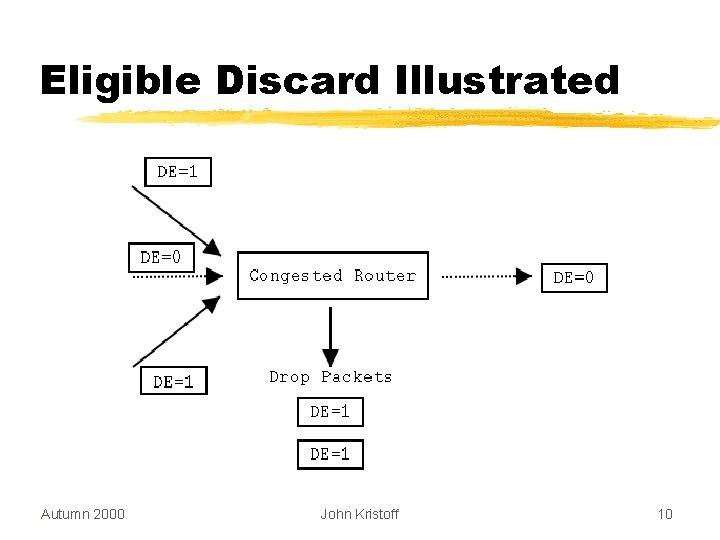
Eligible Discard Ñ Frames, cells or packets are marked according to a drop priority Ñ Source or edge intermediate device may mark based on some policy Ñ Ñ Ñ watermark/threshold reached data type source destination cost Ñ Usually implemented at data link or network layer Autumn 2000 John Kristoff 9

Eligible Discard Illustrated Autumn 2000 John Kristoff 10

Queue Management Ñ First in, first dropped (FIFO) Ñ Tail drop (LIFO) Ñ Leaky bucket Ñ Token bucket Ñ Random early detection (RED) Ñ Weighted Fair Queueing Ñ Usually implemented in intermediate devices such as routers and switches Autumn 2000 John Kristoff 11

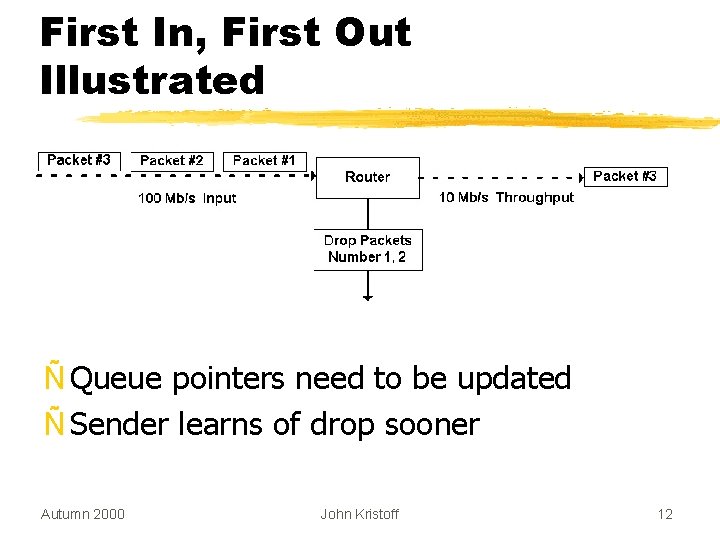
First In, First Out Illustrated Ñ Queue pointers need to be updated Ñ Sender learns of drop sooner Autumn 2000 John Kristoff 12

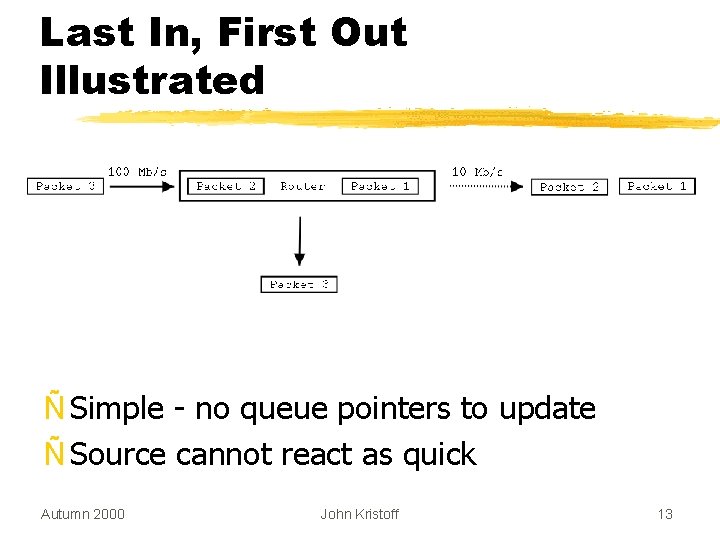
Last In, First Out Illustrated Ñ Simple - no queue pointers to update Ñ Source cannot react as quick Autumn 2000 John Kristoff 13

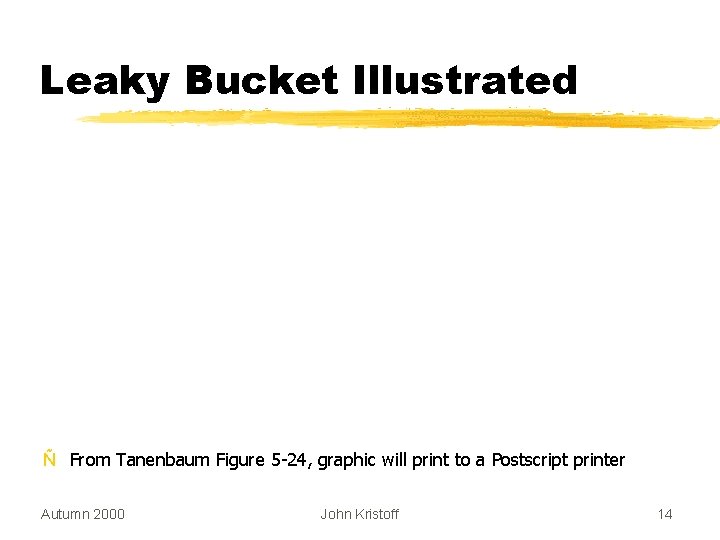
Leaky Bucket Illustrated Ñ From Tanenbaum Figure 5 -24, graphic will print to a Postscript printer Autumn 2000 John Kristoff 14

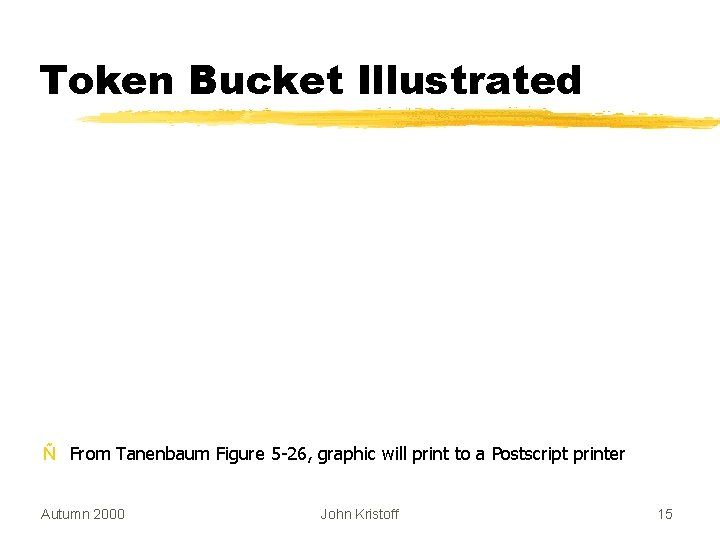
Token Bucket Illustrated Ñ From Tanenbaum Figure 5 -26, graphic will print to a Postscript printer Autumn 2000 John Kristoff 15

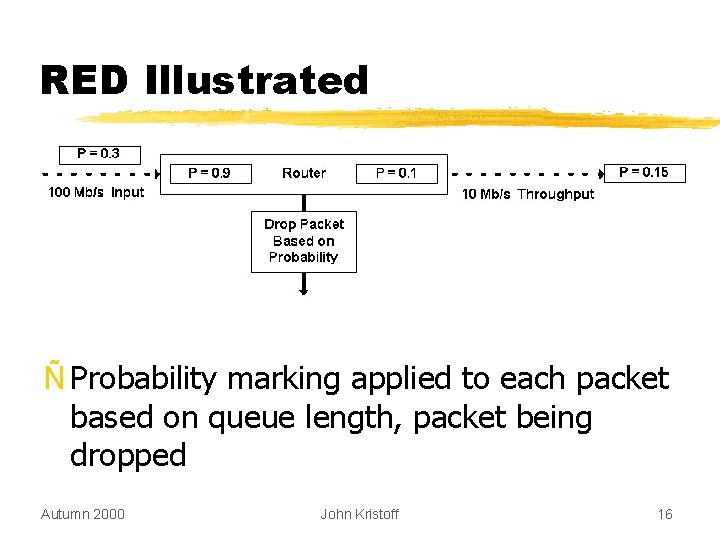
RED Illustrated Ñ Probability marking applied to each packet based on queue length, packet being dropped Autumn 2000 John Kristoff 16

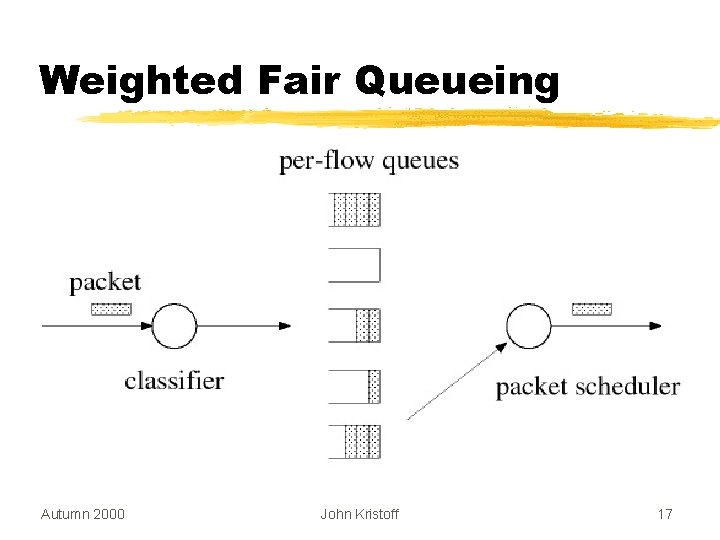
Weighted Fair Queueing Autumn 2000 John Kristoff 17

Network Signaling and Notification Ñ Also called choke packets Ñ In Frame Relay Ñ Forward Explicit Congestion Notification (FECN) Ñ Backward Explicit Congestion Notification (BECN) Ñ Bit in frame set Ñ Experimental Internet mechanism Ñ Explicit Congestion Notification (ECN) Ñ Bits set in packets to hosts Autumn 2000 John Kristoff 18

End Station Avoidance Ñ Also called end-to-end control Ñ TCP Ñ Slow start Ñ Congestion avoidance Ñ Fast Retransmit Ñ Fast Recovery Autumn 2000 John Kristoff 19

Class of Service Signaling Ñ Packets marked to a particular traffic class Ñ IEEE 802. 1 p Ñ Differentiated Services (Diff. Serv) Ñ Re-defines IP Type of Service (To. S) bit fields Ñ Asynchronous Transfer Mode Autumn 2000 John Kristoff 20

Quality of Service Reservations Ñ Resource Re. Ser. Vation Protocol Ñ Reserve resources in routers Ñ Requires stateful path Ñ Asynchronous Transfer Mode (ATM) Autumn 2000 John Kristoff 21