THURSDAY MARCH 27 2014 AUSTIN TEXAS The Texas





























- Slides: 42

THURSDAY, MARCH 27, 2014 | AUSTIN, TEXAS The Texas Cybersecurity Framework and Information Security Plans

The Texas Framework and Agency Security Plans Agenda Texas Cybersecurity Framework Agency Security Plans Examples Questions Open Discussion 3. 27. 2014 2

The Texas Framework and Agency Security Plans Agenda Texas Cybersecurity Framework Agency Security Plans Examples Questions Open Discussion 3. 27. 2014 3

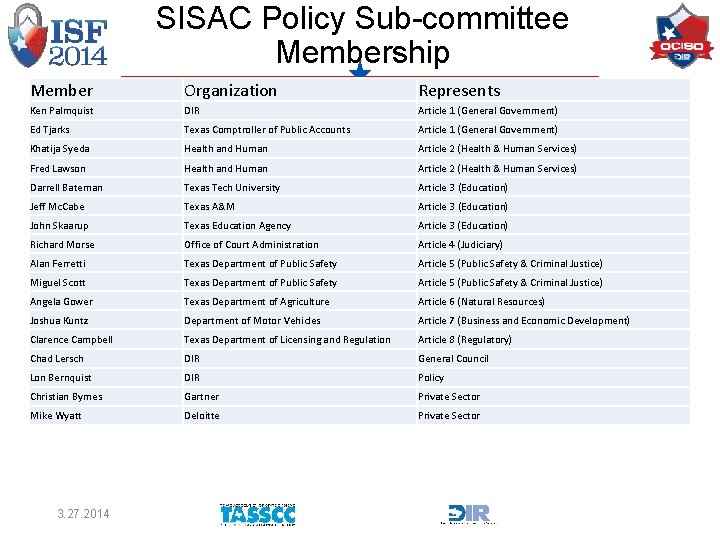
SISAC Policy Sub-committee Membership Member Organization Represents Ken Palmquist DIR Article 1 (General Government) Ed Tjarks Texas Comptroller of Public Accounts Article 1 (General Government) Khatija Syeda Health and Human Article 2 (Health & Human Services) Fred Lawson Health and Human Article 2 (Health & Human Services) Darrell Bateman Texas Tech University Article 3 (Education) Jeff Mc. Cabe Texas A&M Article 3 (Education) John Skaarup Texas Education Agency Article 3 (Education) Richard Morse Office of Court Administration Article 4 (Judiciary) Alan Ferretti Texas Department of Public Safety Article 5 (Public Safety & Criminal Justice) Miguel Scott Texas Department of Public Safety Article 5 (Public Safety & Criminal Justice) Angela Gower Texas Department of Agriculture Article 6 (Natural Resources) Joshua Kuntz Department of Motor Vehicles Article 7 (Business and Economic Development) Clarence Campbell Texas Department of Licensing and Regulation Article 8 (Regulatory) Chad Lersch DIR General Council Lon Bernquist DIR Policy Christian Byrnes Gartner Private Sector Mike Wyatt Deloitte Private Sector 3. 27. 2014

Statewide Security Program Overview Operations Identify Protect Detect Respond Recover Texas Cybersecurity Framework TAC 202 Control Catalog Plan & Strategy Vendor Services Alignment Agency Security Plan Template Risk Mgmt Security Services Direct Elected Services Cooperative Contract Procurement Offerings Managed Services Education & Awareness Security Officer Training 3. 27. 2014 Agency Personnel Awareness Public Awareness 5

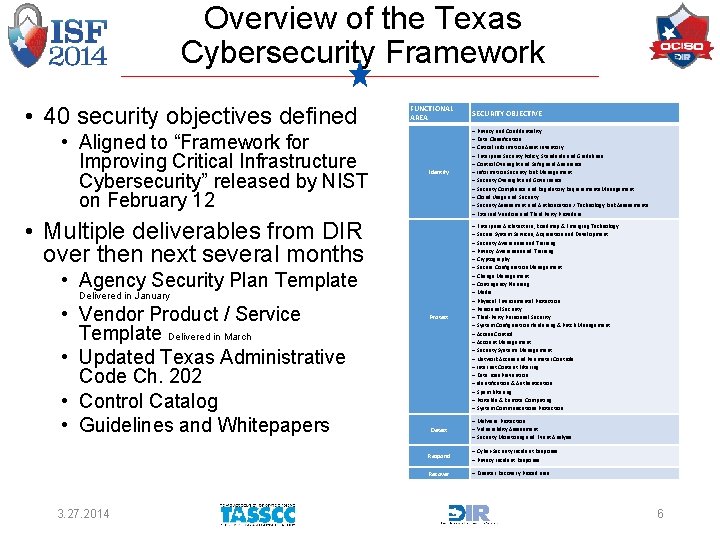
Overview of the Texas Cybersecurity Framework • 40 security objectives defined • Aligned to “Framework for Improving Critical Infrastructure Cybersecurity” released by NIST on February 12 FUNCTIONAL AREA Identify – Privacy and Confidentiality – Data Classification – Critical Information Asset Inventory – Enterprise Security Policy, Standards and Guidelines – Control Oversight and Safeguard Assurance – Information Security Risk Management – Security Oversight and Governance – Security Compliance and Regulatory Requirements Management – Cloud Usage and Security – Security Assessment and Authorization / Technology Risk Assessments – External Vendors and Third Party Providers Protect – Enterprise Architecture, Roadmap & Emerging Technology – Secure System Services, Acquisition and Development – Security Awareness and Training – Privacy Awareness and Training – Cryptography – Secure Configuration Management – Change Management – Contingency Planning – Media – Physical Environmental Protection – Personnel Security – Third-Party Personnel Security – System Configuration Hardening & Patch Management – Access Control – Account Management – Security Systems Management – Network Access and Perimeter Controls – Internet Content Filtering – Data Loss Prevention – Identification & Authentication – Spam Filtering – Portable & Remote Computing – System Communications Protection Detect – Malware Protection – Vulnerability Assessment – Security Monitoring and Event Analysis • Multiple deliverables from DIR over then next several months • Agency Security Plan Template Delivered in January • Vendor Product / Service Template Delivered in March • Updated Texas Administrative Code Ch. 202 • Control Catalog • Guidelines and Whitepapers 3. 27. 2014 SECURITY OBJECTIVE Respond – Cyber-Security Incident Response – Privacy Incident Response Recover – Disaster Recovery Procedures 6

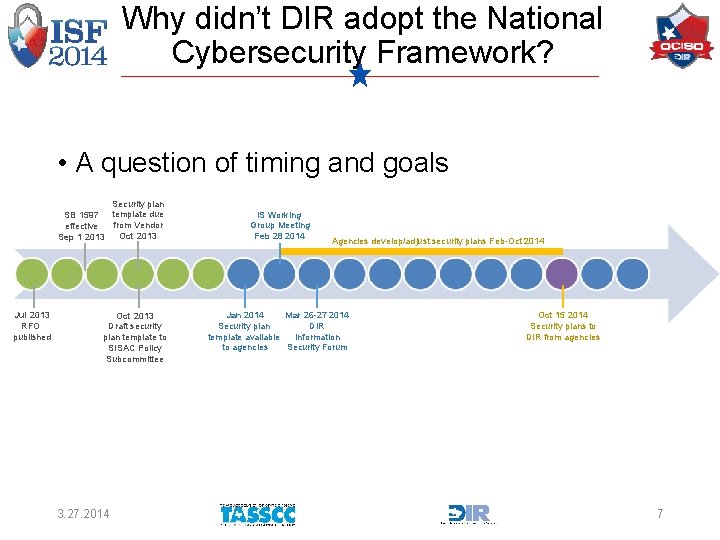
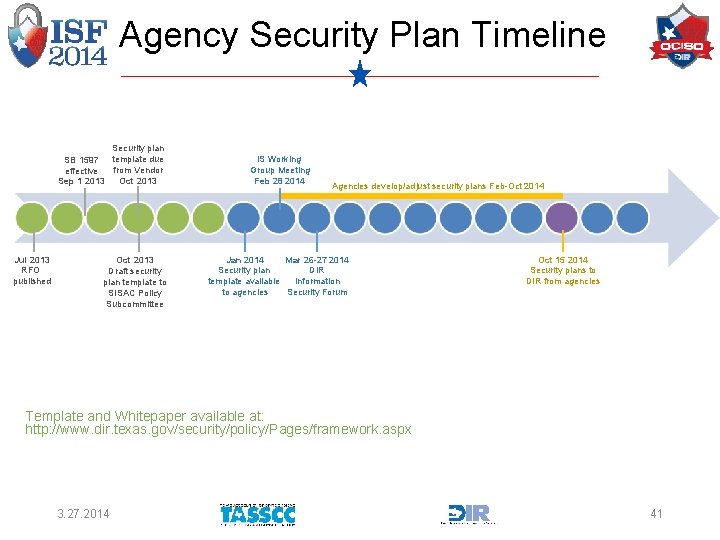
Why didn’t DIR adopt the National Cybersecurity Framework? • A question of timing and goals Security plan SB 1597 template due from Vendor effective Oct 2013 Sep 1 2013 Jul 2013 RFO published Oct 2013 Draft security plan template to SISAC Policy Subcommittee 3. 27. 2014 IS Working Group Meeting Feb 28 2014 Agencies develop/adjust security plans Feb-Oct 2014 Jan 2014 Mar 26 -27 2014 Security plan DIR template available Information to agencies Security Forum Oct 15 2014 Security plans to DIR from agencies 7

Why didn’t DIR adopt the National Cybersecurity Framework? • A question of timing and goals • The framework “shell game” Texas Framework National Framework NIST 800 -53 SANS Top 20 Controls Functional Areas / Control Family 5 5 18 20 Controls / Objectives 40 22 243 184 Sub Category 3. 27. 2014 98 8

Why didn’t DIR adopt the National Cybersecurity Framework? • A question of timing and goals • The framework “shell game” • The long-term solution lends itself to adaption to any framework or compliance regime 3. 27. 2014 9

The Texas Framework and Agency Security Plans Agenda Texas Cybersecurity Framework Agency Security Plans Examples Questions Open Discussion 3. 27. 2014 10

Security Plan Template • Available on the DIR website in the Texas Cybersecurity Framework section 3. 27. 2014 11

Agency Security Plans • Responsive to SB 1134 (Ellis) and SB 1597 (Zaffirini) • Objective-based • Provides a uniform understanding of agency security program maturity MATURITY LEVEL DIR DESCRIPTION KEYWORDS 0 There is no evidence of the organization meeting the objective. None, Nonexistent 1 The organization has an ad hoc, inconsistent, or reactive approach to meeting the objective. Ad-hoc, Initial 2 The organization has a consistent overall approach to meeting the objective, but it is still mostly reactive and undocumented. The organization does not routinely measure or enforce policy compliance. Managed, Consistent, Repeatable 3 The organization has a documented, detailed approach to meeting the objective, and regularly measures its compliance. Compliant, Defined 4 The organization uses an established risk management framework to measure and evaluate risk and integrate improvements beyond the requirements of applicable regulations. Risk-Based, Managed 5 The organization has refined its standards and practices focusing on ways to improve its capabilities in the most efficient and costeffective manner. Efficient, Optimized, Economized 3. 27. 2014 12

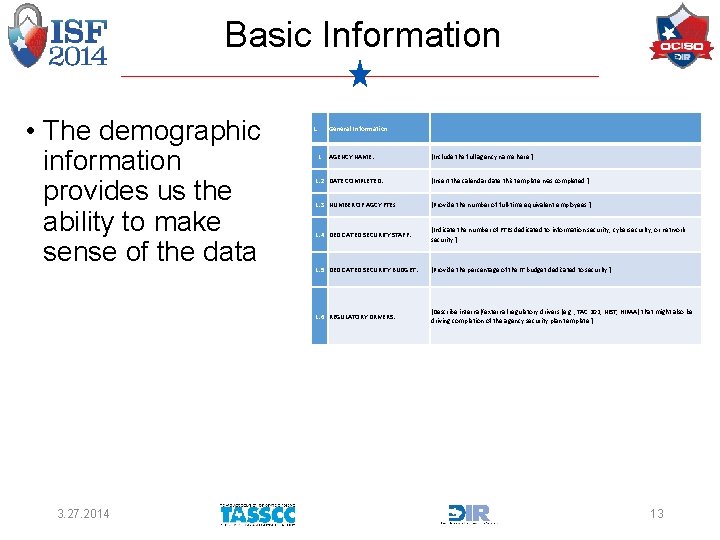
Basic Information • The demographic information provides us the ability to make sense of the data 3. 27. 2014 1. 1 General Information AGENCY NAME: [Include the full agency name here. ] 1. 2 DATE COMPLETED: [Insert the calendar date this template was completed. ] 1. 3 NUMBER OF AGCY FTEs [Provide the number of full-time equivalent employees. ] 1. 4 DEDICATED SECURITY STAFF: [Indicate the number of FTEs dedicated to information security, cybersecurity, or network security. ] 1. 5 DEDICATED SECURITY BUDGET: [Provide the percentage of the IT budget dedicated to security. ] 1. 6 REGULATORY DRIVERS: [Describe internal/external regulatory drivers (e. g. , TAC 202, NIST, HIPAA) that might also be driving completion of the agency security plan template. ] 13

Control activities • Agencies are asked to provide the controls they have in place for each security objective 3. 27. 2014 FUNCTIONAL AREA SECURITY OBJECTIVE NIST FRAMEWORK RELEVANT CONTROL ACTIVITIES IN PLACE MAPPING Protect Security PR. AT-1 Awareness and Training Agency Policy states that “All employees are required to complete annual computer-based security awareness training as assigned by the Information Security Officer (ISO). ” The Agency makes use of SANS Secure The Human computer-based awareness training provided by DIR. As of 12/31/2013, 50 percent of agency staff have completed the modules assigned. The Agency is launching formal Information Security Awareness Project that incorporates an internal website, instructor-led classes, and a division-by-division assessment of training focus and needs. It is expected that this program will be fully implemented in FY 2014. In the past, the Agency has also purchased posters and mouse pads with a security message in order to keep the concept of information security in front of our employees 14

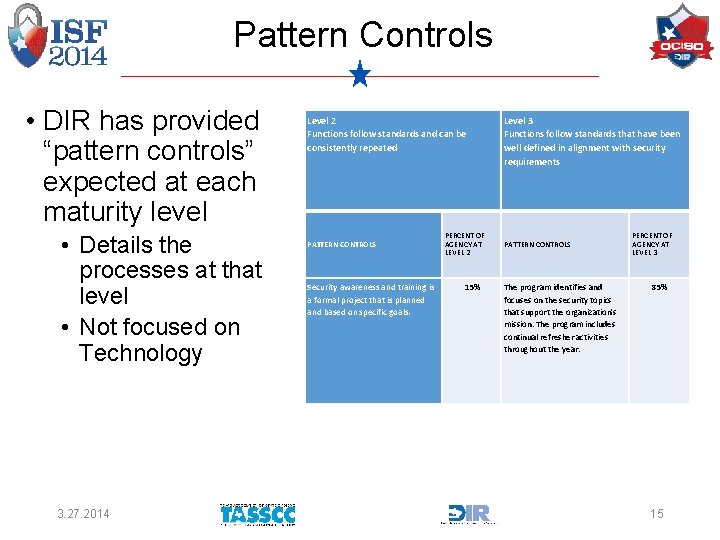
Pattern Controls • DIR has provided “pattern controls” expected at each maturity level • Details the processes at that level • Not focused on Technology 3. 27. 2014 Level 2 Functions follow standards and can be consistently repeated PATTERN CONTROLS Security awareness and training is a formal project that is planned and based on specific goals. PERCENT OF AGENCY AT LEVEL 2 15% Level 3 Functions follow standards that have been well defined in alignment with security requirements PATTERN CONTROLS The program identifies and focuses on the security topics that support the organization's mission. The program includes continual refresher activities throughout the year. PERCENT OF AGENCY AT LEVEL 3 85% 15

Effectiveness • Agencies at level 4 are asked to detail how they measure effectiveness Level 4 Functions are monitored and measured with oversight and assurance. PATTERN CONTROLS The organization provides regular and ongoing role-based training and awareness that are designed to address top risks identified by the organization in its assessments. The organization measures employee completion and comprehension rates and adjusts its approach to improve those rates. 3. 27. 2014 PERCENT OF AGENCY AT LEVEL 4 20% HOW IS EFFECTIVENESS OF THE CONTROL MEASURED? Periodic testing of the agency personnel demonstrates that the awareness training provided has resulted in behavior changes that overall has resulted in fewer incidents related to successful phishing attacks and malware infections. 16

Efficiency • Similarly, at level 5, agencies are asked to detail how they measure efficiency of controls Level 5 Functions have a high level of efficiency and integration with IT or business processes PATTERN CONTROLS Employee participation and comprehension rates in training applicable to their jobs is near 100 percent, and the organization's security-training program has been recognized by peers as an industry leader. PERCENT OF AGENCY AT LEVEL HOW IS EFFICIENCY OF CONTROL MEASURED? 5 10% The overall cost of the training provided to agency personnel is approximately $5 per employee per year, for material that is presented to the employee at least on a monthly basis. The $5 per employee per year extrapolates to approximately $1, 200 per year total, which is approximately 1 percent of the total security budget. While 1 percent of total security budget could be increased, the amount of time required of each employee has reached an acceptable amount for the agency. 3. 27. 2014 17

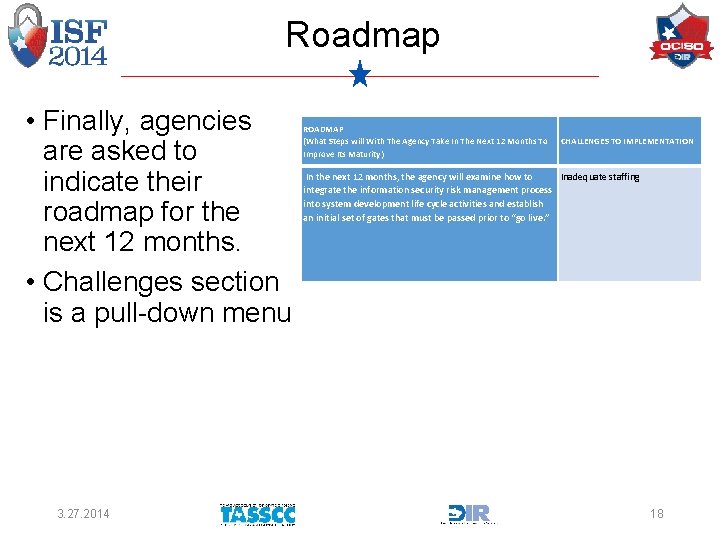
Roadmap • Finally, agencies are asked to indicate their roadmap for the next 12 months. • Challenges section is a pull-down menu 3. 27. 2014 ROADMAP (What Steps will With The Agency Take In The Next 12 Months To Improve Its Maturity) CHALLENGES TO IMPLEMENTATION In the next 12 months, the agency will examine how to Inadequate staffing integrate the information security risk management process into system development life cycle activities and establish an initial set of gates that must be passed prior to “go live. ” 18

The Texas Framework and Agency Security Plans Agenda Texas Cybersecurity Framework Agency Security Plans Examples Questions Open Discussion 3. 27. 2014 19

Example 1: Security Awareness and Training Control Objective • Define, prepare, deliver, and facilitate an ongoing awareness campaign utilizing a wide variety of mediums and delivery mechanisms to effectively and constantly educate the organization on security related information, threats, and technology risks. • Assume agency is at a maturity level 3 for example 1 The program identifies and focuses on the security topics that support the organization's mission. The program includes continual refresher activities throughout the year. 3. 27. 2014 20

Example 1: Security Awareness and Training Control Activity Security awareness training consists of Power. Point presentations with testing, that are taken on an annual basis by all staff. 3. 27. 2014 21

Example 1: Security Awareness and Training Control Activity Security awareness training consists of Power. Point presentations with testing, that are taken on an annual basis by all staff. 3. 27. 2014 Security awareness training consists of agency developed Power. Point presentations delivered across our agency intranet. Each staff member must also pass an accompanying with testing for each module, with at least 80% correct. , that are taken on an annual basis by all staff. The agency has a goal of 100% of staff trained within the first 6 months of employment. 22

Example 1: Security Awareness and Training Roadmap The agency has allocated funds for improving training programs. 3. 27. 2014 23

Example 1: Security Awareness and Training Roadmap The agency has allocated funds for improving training programs. 3. 27. 2014 The agency has met its goal of 100% of staff trained within the first 6 months of employment, but tracking has been a manual process. The agency has allocated funds to build a training management system, which will programmatically track compliance with for improving training programs requirements. 24

Example 2: Access Control Objective • Processes used to ensure access to applications, servers, databases, and network devices in the environment is limited to authorized personnel. Access is to be limited to authorized users, processes acting on behalf of authorized users, or authorized devices. Authorized users are further limited to the types of transactions and functions that they are permitted to exercise. Session limits, lockout features for failed login attempts, account expirations and disabling unused accounts are controls that provide access control. • Assume agency is at a level 4 and 5 for example 2 • Pattern Controls 4. Role-based access controls are implemented and the principle of "least privilege" is employed. Roles are defined for system access. Individual users are assigned permissions based on roles, no individual permissions are granted. Two factor authentication mechanisms are employed for systems identified as high risk by a documented risk management process. 5. Onboarding: Access to systems is granted based on role-based controls in a documented and auditable manner. Off boarding: A defined and auditable process is in place to revoke all access permissions within 2 hours of a separation activity. 3. 27. 2014 25

Example 2: Access Control Activity The organization is in the process of implementing an IAM system to ensure that access levels are rolebased and that no shared accounts exist. Two factor authentication is in the process of being deployed for high risk systems. 3. 27. 2014 26

Example 2: Access Control Activity The organization is in the process of implementing an IAM system to ensure that access levels are rolebased and that no shared accounts exist. Two factor authentication is in the process of being deployed for high risk systems. 3. 27. 2014 The organization is in the process of implementing an IAM system to ensure that access levels are rolebased and that no shared accounts exist. The system is expected to be fully deployed by Q 4 of FY 14. Two factor authentication is in the process of being deployed for high risk systems which contain PII, customer data or are critical to delivering the agency mission. 27

Example 2: Access Control Effectiveness Annual audits 3. 27. 2014 28

Example 2: Access Control Effectiveness Annual audits 3. 27. 2014 The agency’s internal audit team reviews access control exceptions reports for compliance with agency policy Aannually. Audits The agency has a goal of disabling non-current accounts within 12 hours. The agency has established a 99% effectiveness rate as a goal for all access control measures. 29

Example 2: Access Control Efficiency Annual audits 3. 27. 2014 30

Example 2: Access Control Efficiency Annual audits 3. 27. 2014 Annual audits The agency’s business owners review access control process and procedures to ensure that information owners are clearly identified and that access to business critical functions is not delayed for new employees. 31

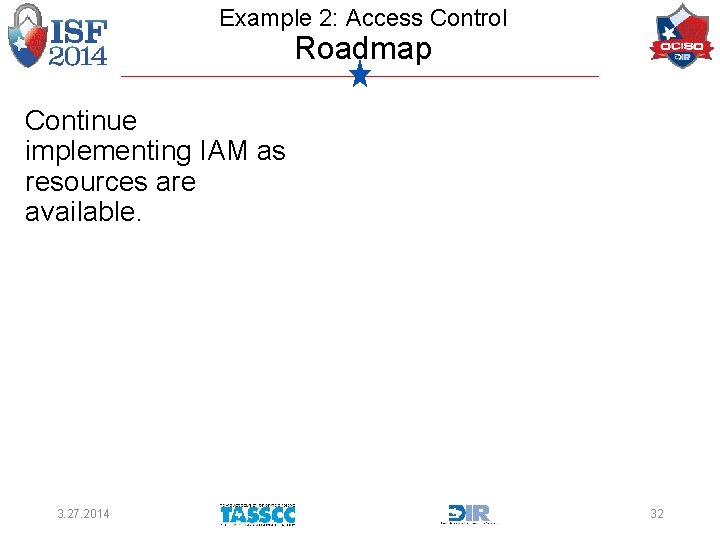
Example 2: Access Control Roadmap Continue implementing IAM as resources are available. 3. 27. 2014 32

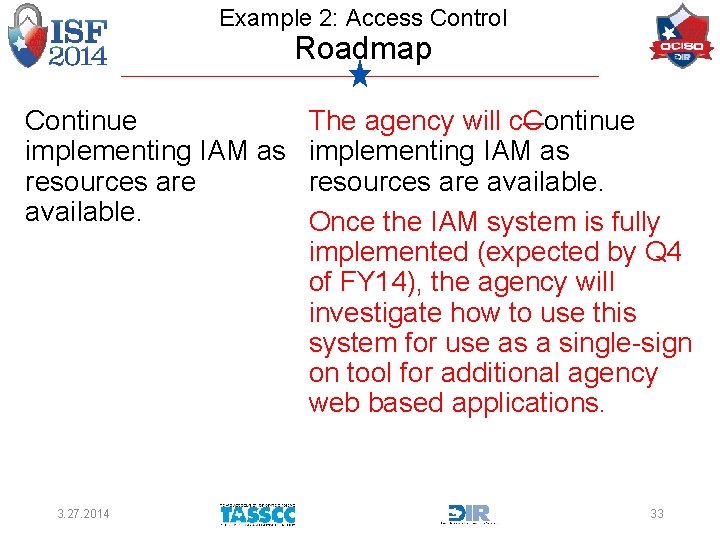
Example 2: Access Control Roadmap Continue implementing IAM as resources are available. 3. 27. 2014 The agency will c. Continue implementing IAM as resources are available. Once the IAM system is fully implemented (expected by Q 4 of FY 14), the agency will investigate how to use this system for use as a single-sign on tool for additional agency web based applications. 33

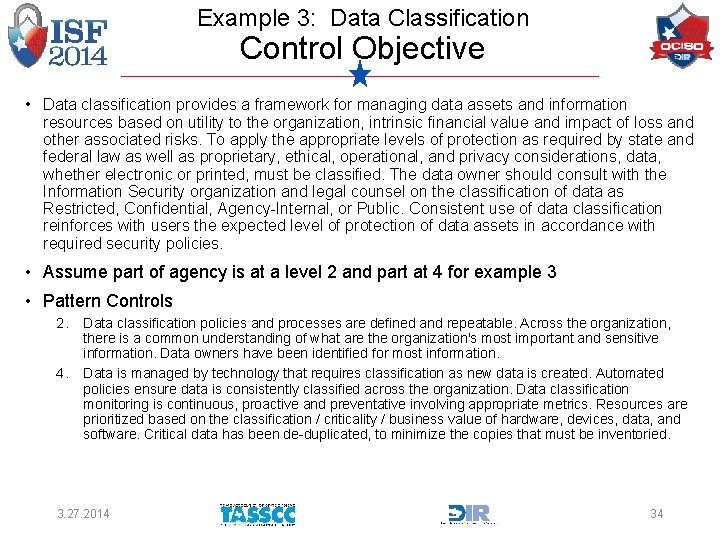
Example 3: Data Classification Control Objective • Data classification provides a framework for managing data assets and information resources based on utility to the organization, intrinsic financial value and impact of loss and other associated risks. To apply the appropriate levels of protection as required by state and federal law as well as proprietary, ethical, operational, and privacy considerations, data, whether electronic or printed, must be classified. The data owner should consult with the Information Security organization and legal counsel on the classification of data as Restricted, Confidential, Agency-Internal, or Public. Consistent use of data classification reinforces with users the expected level of protection of data assets in accordance with required security policies. • Assume part of agency is at a level 2 and part at 4 for example 3 • Pattern Controls 2. 4. Data classification policies and processes are defined and repeatable. Across the organization, there is a common understanding of what are the organization's most important and sensitive information. Data owners have been identified for most information. Data is managed by technology that requires classification as new data is created. Automated policies ensure data is consistently classified across the organization. Data classification monitoring is continuous, proactive and preventative involving appropriate metrics. Resources are prioritized based on the classification / criticality / business value of hardware, devices, data, and software. Critical data has been de-duplicated, to minimize the copies that must be inventoried. 3. 27. 2014 34

Example 3: Data Classification Roadmap Improve compliance with the data classification plan. 3. 27. 2014 35

Example 3: Data Classification Roadmap Improve compliance with the data classification plan. 3. 27. 2014 The agency has spent time and resources ensuring that PII and customer data is properly classified for business critical systems. Over the next 12 months, the agency will expand the scope of its data classification project to ensure that all program areas Improve complyiance with the data classification plan. 36

The Texas Framework and Agency Security Plans Agenda Texas Cybersecurity Framework Agency Security Plans Examples Questions Open Discussion 3. 27. 2014 37

What is DIR going to do with the data? • SB 1134 tells DIR to develop a framework • SB 1597 does not indicate what DIR is expected to do with agency security plans received • We will analyze the data for outliers • What can we do to help agencies with lower maturity? • We learn from agencies with higher maturity? 3. 27. 2014 38

What can agencies do with the data? • Appropriations • Focus resources • Build a common lexicon • Provide visibility during transitions 3. 27. 2014 39

How should large organizations structure their response? • Framework is flexible enough for multiple scenarios • Single ISO for entity • Entity with multiple divisions • Large entities with multiple IT groups and funding sources 3. 27. 2014 40

Agency Security Plan Timeline Security plan SB 1597 template due from Vendor effective Oct 2013 Sep 1 2013 Jul 2013 RFO published Oct 2013 Draft security plan template to SISAC Policy Subcommittee IS Working Group Meeting Feb 28 2014 Agencies develop/adjust security plans Feb-Oct 2014 Jan 2014 Mar 26 -27 2014 Security plan DIR template available Information to agencies Security Forum Oct 15 2014 Security plans to DIR from agencies Template and Whitepaper available at: http: //www. dir. texas. gov/security/policy/Pages/framework. aspx 3. 27. 2014 41

The Texas Framework and Agency Security Plans Agenda Texas Cybersecurity Framework Agency Security Plans Examples Questions Open Discussion 3. 27. 2014 42
 Poland national anthem lyrics
Poland national anthem lyrics Terrence dickson bristol
Terrence dickson bristol Rbfcu headquarters
Rbfcu headquarters Phishing austin texas
Phishing austin texas Thursday bellwork
Thursday bellwork Thursday
Thursday What s your favourite subject
What s your favourite subject Monday tuesday wednesday thursday friday calendar
Monday tuesday wednesday thursday friday calendar Thursday bell ringer
Thursday bell ringer This coming thursday
This coming thursday Dua for thursday
Dua for thursday 997ni1xcmkw -site:youtube.com
997ni1xcmkw -site:youtube.com Senior g friendship thursday
Senior g friendship thursday Thursday bellringer
Thursday bellringer Sunday monday tuesday wednesday
Sunday monday tuesday wednesday British easter traditions
British easter traditions Th adjectives for thursday
Th adjectives for thursday St paul's church wibsey
St paul's church wibsey Thursday prayer images
Thursday prayer images Why did the yazoo land fraud occur?
Why did the yazoo land fraud occur? Act 2 romeo and juliet timeline
Act 2 romeo and juliet timeline How's the weather answer
How's the weather answer Welcome thursday
Welcome thursday Welcome thursday
Welcome thursday Monday tuesday wednesday thursday friday saturday sunday
Monday tuesday wednesday thursday friday saturday sunday Which festival celebrates christs rising from death
Which festival celebrates christs rising from death Thursday morning prayer
Thursday morning prayer Holy thursday poem
Holy thursday poem Welcome thursday
Welcome thursday Wednesday evening prayer
Wednesday evening prayer Have a terrific thursday
Have a terrific thursday Black thursday
Black thursday Eugene kelly colgate
Eugene kelly colgate Thoughtful thursday morning message
Thoughtful thursday morning message Thursday question of the day
Thursday question of the day Arvolan karjapiha
Arvolan karjapiha Blessed holy thursday
Blessed holy thursday Monday tuesday wednesday saturday
Monday tuesday wednesday saturday Thursday420
Thursday420 Thursday bell ringers
Thursday bell ringers Thế nào là số nguyên tố
Thế nào là số nguyên tố Thiếu nhi thế giới liên hoan
Thiếu nhi thế giới liên hoan Fecboak
Fecboak