TCPIP TCPIP Protocol Suite 1 Physical layer Datalink













- Slides: 47

TCP/IP

TCP/IP Protocol Suite (1) Physical layer Data-link layer –PPP, ARP, RARP Network layer – IP, ICMP, IGMP, Boot. P Transport layer _ TCP, UDP, RTP Application layer – http, smtp, ftp

TCP/IP Protocol Suite (2) Point-to-Point Protocol (PPP): a link layer protocol used in the Internet Address Resolution Protocol (ARP): IP address Ethernet address Reverse Address Resolution Protocol (RARP): Ethernet address IP address Bootstrap Protocol (BOOTP): function is similar to RARP, but using UDP messages, and was extended to DHCP (Dynamic Host Configuration Protocol)

TCP/IP Protocol Suite (3) Internet Control Message Protocol (ICMP) : monitor or test the Internet Group Management Protocol (IGMP) : manage the membership of IP multicast groups Real-time Transport Protocol (RTP): provides end-to-end network transport functions suitable for applications transmitting real-time data

TCP/IP Protocol Suite (4) http: Hyper. Text Transfer Protocol smtp: Simple Mail Transfer Protocol ftp: File Transfer Protocol

Internet Protocol (IP) Addressing Routing Fragmentation and Reassembly Quality of Service Multiplexing and Demultiplexing

Addressing Need unique identifier for every host in the Internet (analogous to postal address) IP addresses are 32 bits long Hierarchical addressing scheme Conceptually … n IPaddress =(Network. Address, Host. Address)

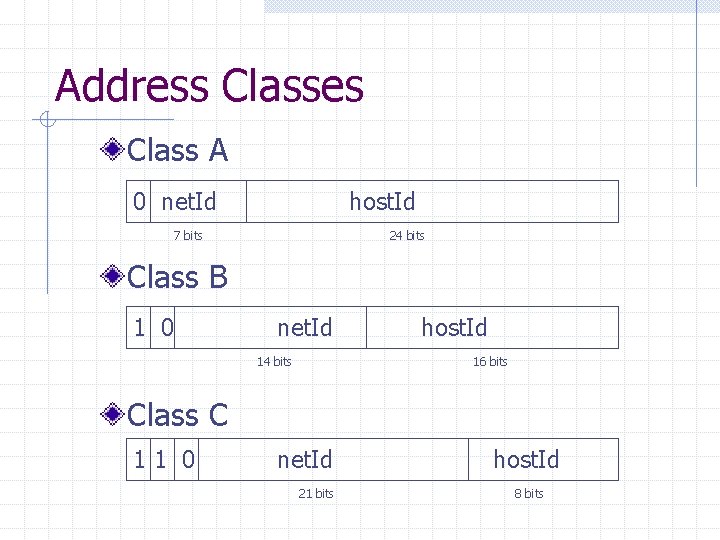
Address Classes Class A 0 net. Id host. Id 7 bits 24 bits Class B 1 0 net. Id 14 bits host. Id 16 bits Class C 11 0 net. Id 21 bits host. Id 8 bits

IP Address Classes (contd. ) Two more classes n n 1110 : multicast addressing 1111 : reserved Significance of address classes? Why this conceptual form?

Addresses and Hosts Since net. Id is encoded into IP address, each host will have a unique IP address for each of its network connections Hence, IP addresses refer to network connections and not hosts Why will hosts have multiple network connections?

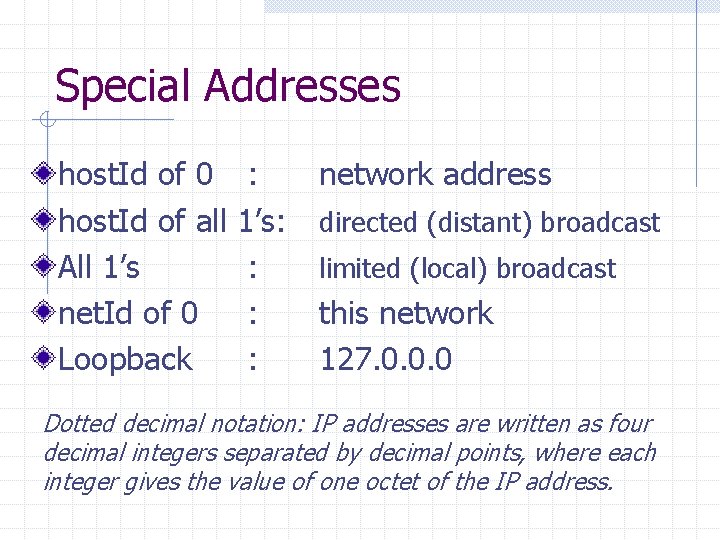
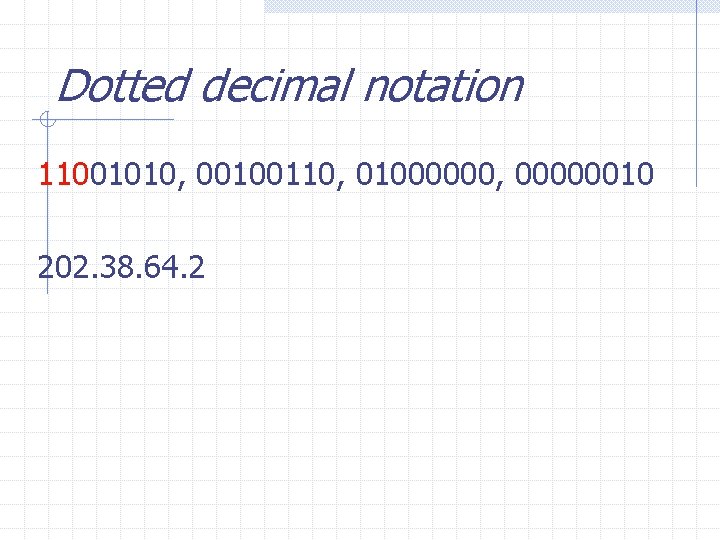
Special Addresses host. Id of 0 host. Id of all All 1’s net. Id of 0 Loopback : 1’s: : network address directed (distant) broadcast limited (local) broadcast this network 127. 0. 0. 0 Dotted decimal notation: IP addresses are written as four decimal integers separated by decimal points, where each integer gives the value of one octet of the IP address.

Dotted decimal notation 11001010, 00100110, 01000000, 00000010 202. 38. 64. 2

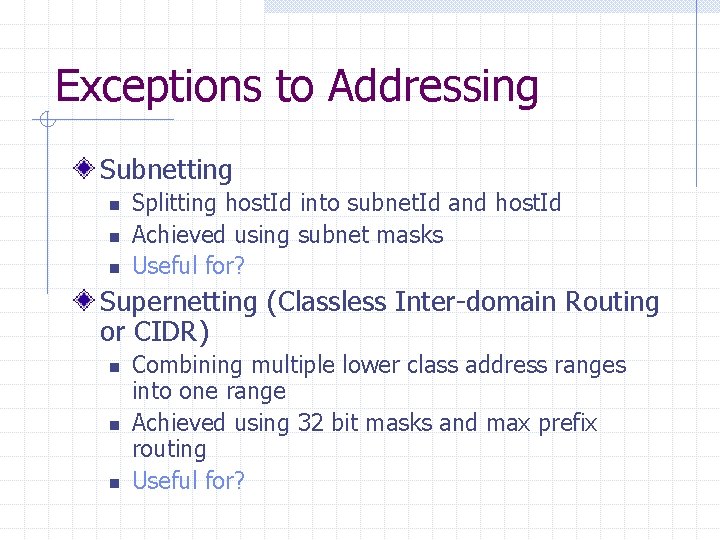
Exceptions to Addressing Subnetting n n n Splitting host. Id into subnet. Id and host. Id Achieved using subnet masks Useful for? Supernetting (Classless Inter-domain Routing or CIDR) n n n Combining multiple lower class address ranges into one range Achieved using 32 bit masks and max prefix routing Useful for?

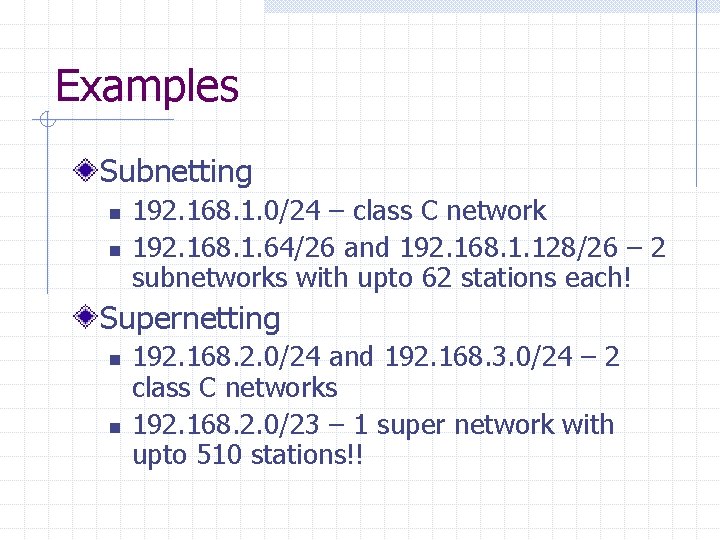
Examples Subnetting n n 192. 168. 1. 0/24 – class C network 192. 168. 1. 64/26 and 192. 168. 1. 128/26 – 2 subnetworks with upto 62 stations each! Supernetting n n 192. 168. 2. 0/24 and 192. 168. 3. 0/24 – 2 class C networks 192. 168. 2. 0/23 – 1 super network with upto 510 stations!!

Weaknesses Mobility Switching address classes Notion of host vs. IP address

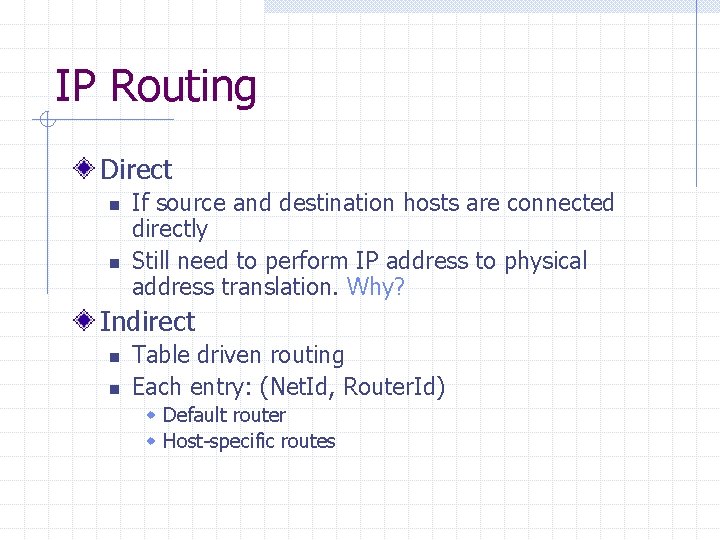
IP Routing Direct n n If source and destination hosts are connected directly Still need to perform IP address to physical address translation. Why? Indirect n n Table driven routing Each entry: (Net. Id, Router. Id) w Default router w Host-specific routes

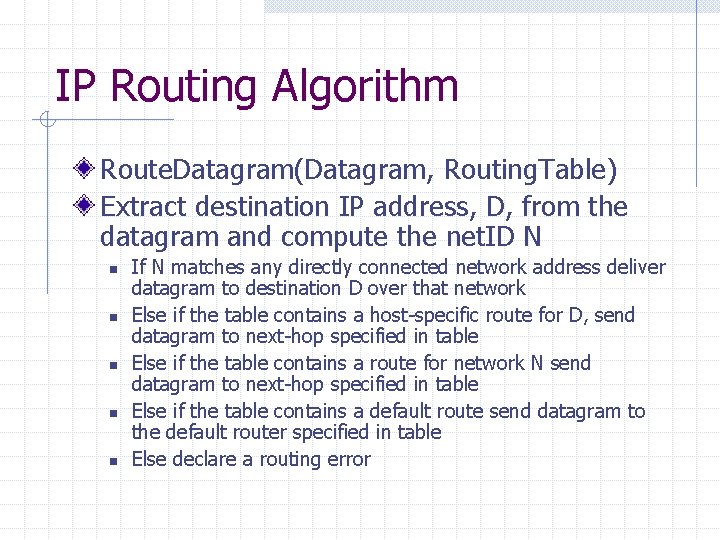
IP Routing Algorithm Route. Datagram(Datagram, Routing. Table) Extract destination IP address, D, from the datagram and compute the net. ID N n n n If N matches any directly connected network address deliver datagram to destination D over that network Else if the table contains a host-specific route for D, send datagram to next-hop specified in table Else if the table contains a route for network N send datagram to next-hop specified in table Else if the table contains a default route send datagram to the default router specified in table Else declare a routing error

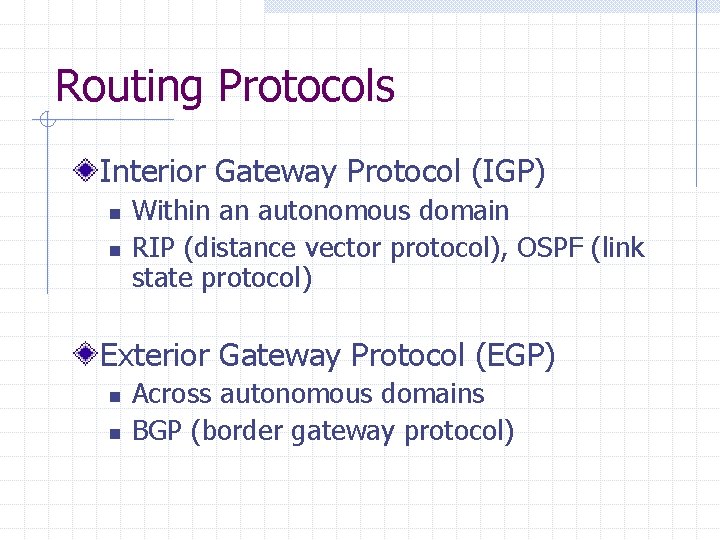
Routing Protocols Interior Gateway Protocol (IGP) n n Within an autonomous domain RIP (distance vector protocol), OSPF (link state protocol) Exterior Gateway Protocol (EGP) n n Across autonomous domains BGP (border gateway protocol)

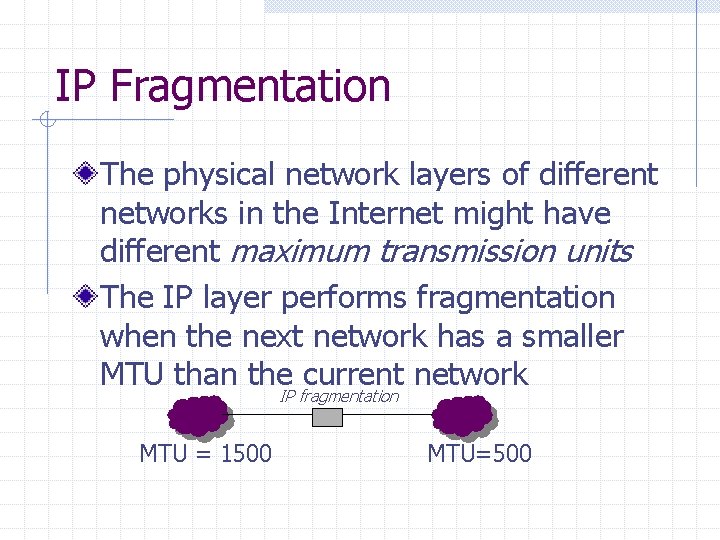
IP Fragmentation The physical network layers of different networks in the Internet might have different maximum transmission units The IP layer performs fragmentation when the next network has a smaller MTU than the current network IP fragmentation MTU = 1500 MTU=500

IP Reassembly Fragmented packets need to be put together Where does reassembly occur? What are the trade-offs?

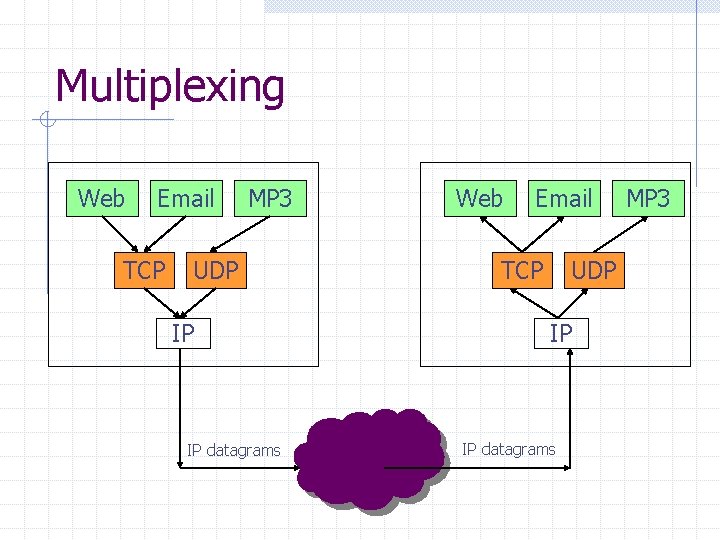
Multiplexing Web Email TCP MP 3 UDP IP IP datagrams Web Email TCP UDP IP IP datagrams MP 3

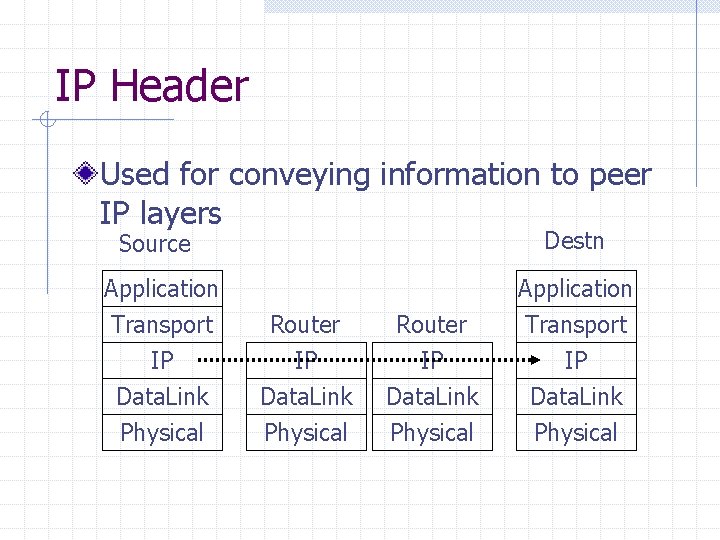
IP Header Used for conveying information to peer IP layers Destn Source Application Transport IP Data. Link Physical Router IP Data. Link Physical Application Transport IP Data. Link Physical

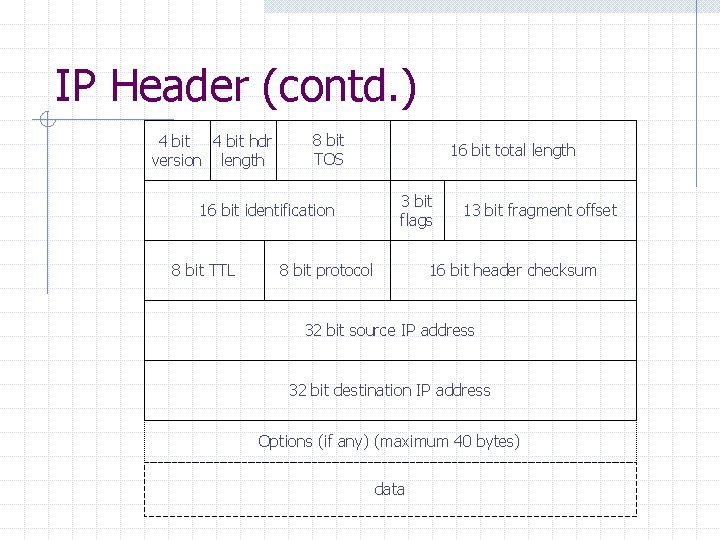
IP Header (contd. ) 4 bit hdr version length 8 bit TOS 16 bit identification 8 bit TTL 16 bit total length 3 bit flags 8 bit protocol 13 bit fragment offset 16 bit header checksum 32 bit source IP address 32 bit destination IP address Options (if any) (maximum 40 bytes) data

Internet Protocol (IP): Recap Addressing Routing Fragmentation and Reassembly Quality of Service Multiplexing and Demultiplexing

Transmission Control Protocol (TCP)

Transmission Control Protocol (TCP) End-to-end transport protocol Responsible for reliability, congestion control, flow control, and sequenced delivery Applications that use TCP: http (web), telnet, ftp (file transfer), smtp (email), chat Applications that don’t: multimedia (typically) – use UDP instead

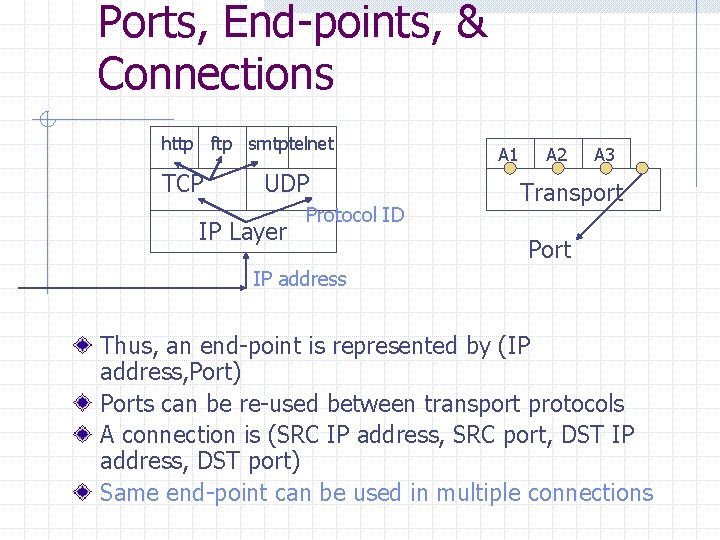
Ports, End-points, & Connections http ftp smtptelnet TCP UDP IP Layer Protocol ID A 1 A 2 A 3 Transport Port IP address Thus, an end-point is represented by (IP address, Port) Ports can be re-used between transport protocols A connection is (SRC IP address, SRC port, DST IP address, DST port) Same end-point can be used in multiple connections

TCP Connection Establishment Connection Maintenance n n Reliability Congestion control Flow control Sequencing Connection Termination

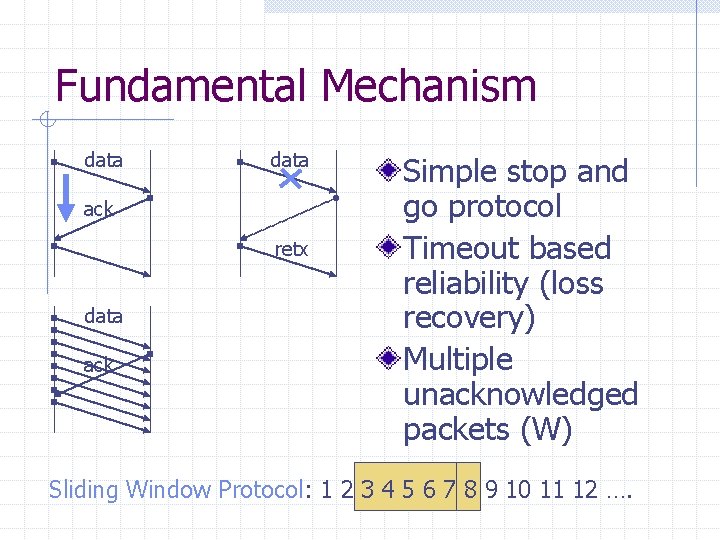
Fundamental Mechanism data ack retx data ack Simple stop and go protocol Timeout based reliability (loss recovery) Multiple unacknowledged packets (W) Sliding Window Protocol: 1 2 3 4 5 6 7 8 9 10 11 12 ….

Active and Passive Open How do applications initiate a connection? One end (server) registers with the TCP layer instructing it to “accept” connections at a certain port The other end (client) initiates a “connect” request which is “accept”-ed by the server

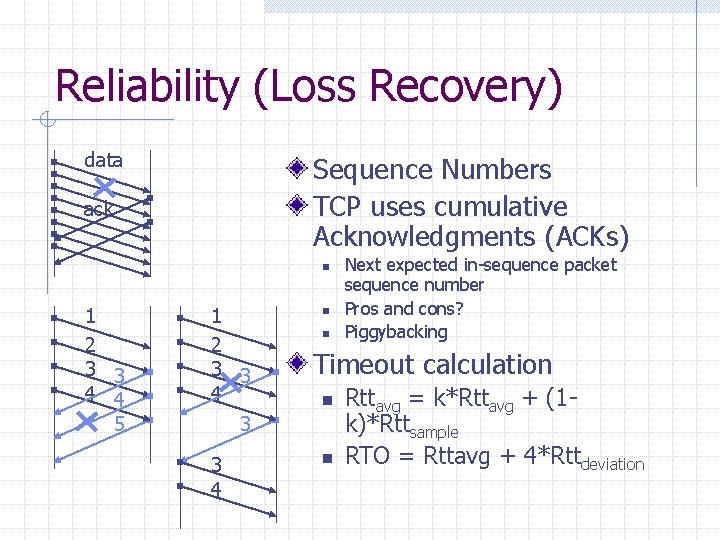
Reliability (Loss Recovery) data Sequence Numbers TCP uses cumulative Acknowledgments (ACKs) ack n 1 2 3 3 4 4 5 1 2 3 3 4 n n Next expected in-sequence packet sequence number Pros and cons? Piggybacking Timeout calculation n n Rttavg = k*Rttavg + (1 k)*Rttsample RTO = Rttavg + 4*Rttdeviation

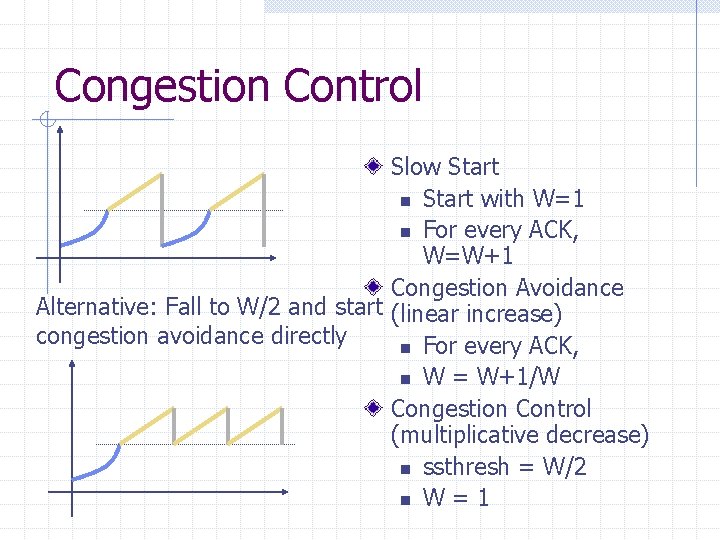
Congestion Control Slow Start n Start with W=1 n For every ACK, W=W+1 Congestion Avoidance Alternative: Fall to W/2 and start (linear increase) congestion avoidance directly n For every ACK, n W = W+1/W Congestion Control (multiplicative decrease) n ssthresh = W/2 n W = 1

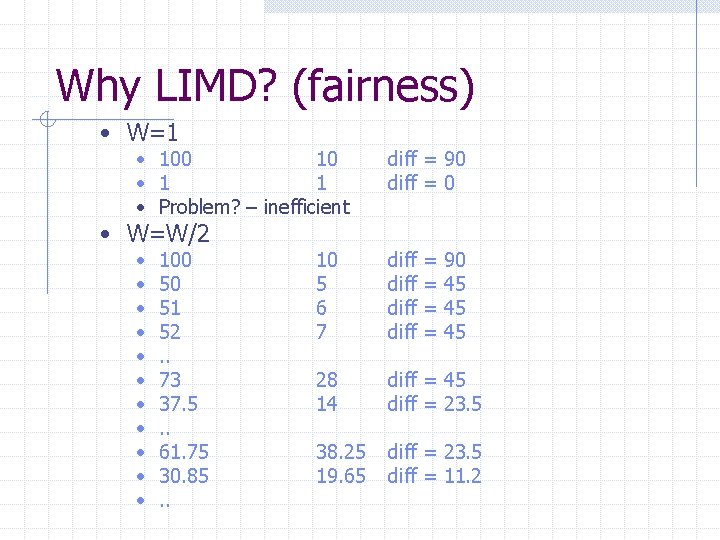
Why LIMD? (fairness) • W=1 • 100 10 • 1 1 • Problem? – inefficient diff = 90 diff = 0 • • • 10 5 6 7 diff 28 14 diff = 45 diff = 23. 5 38. 25 19. 65 diff = 23. 5 diff = 11. 2 • W=W/2 100 50 51 52. . 73 37. 5. . 61. 75 30. 85. . = = 90 45 45 45

Flow Control Prevent sender from overwhelming the receiver Receiver in every ACK advertises the available buffer space at its end Window calculation n MIN(congestion control window, flow control window)

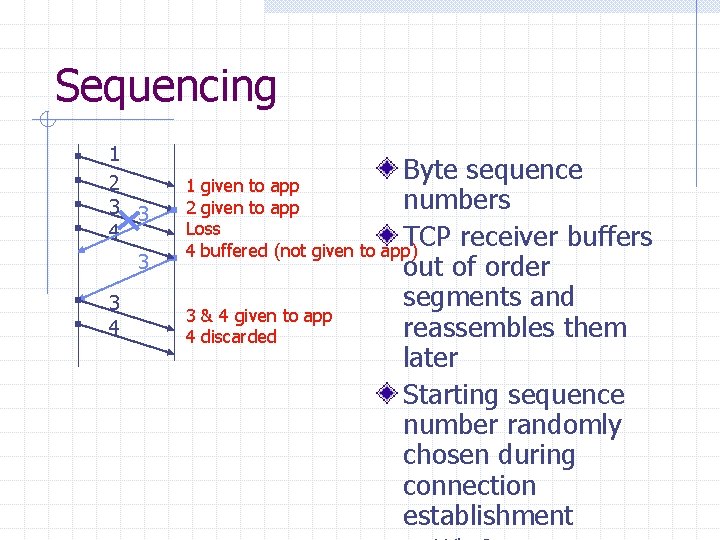
Sequencing 1 2 3 3 4 Byte sequence 1 given to app numbers 2 given to app Loss TCP receiver buffers 4 buffered (not given to app) out of order segments and 3 & 4 given to app reassembles them 4 discarded later Starting sequence number randomly chosen during connection establishment

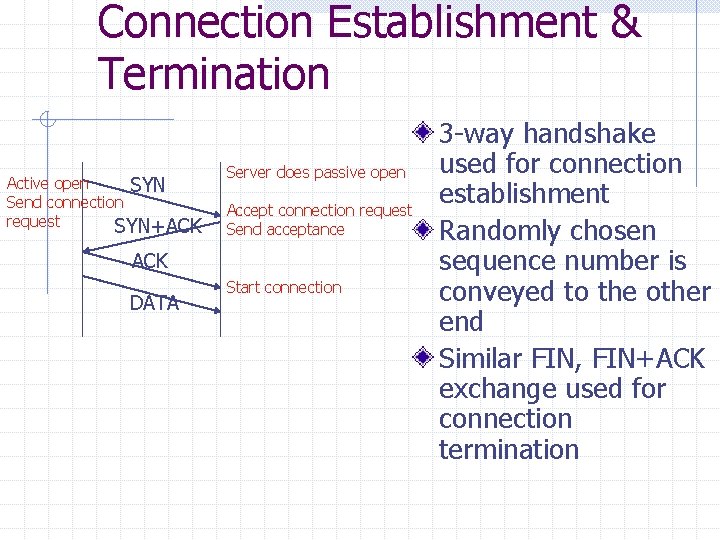
Connection Establishment & Termination Active open SYN Send connection request SYN+ACK Server does passive open Accept connection request Send acceptance ACK DATA Start connection 3 -way handshake used for connection establishment Randomly chosen sequence number is conveyed to the other end Similar FIN, FIN+ACK exchange used for connection termination

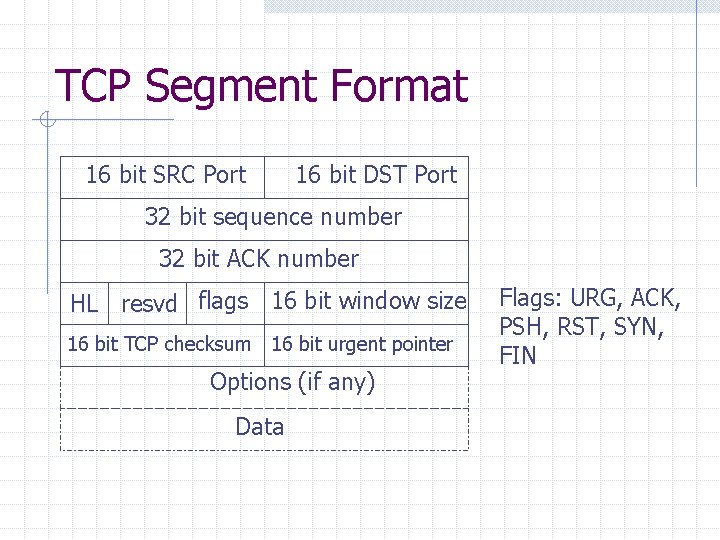
TCP Segment Format 16 bit SRC Port 16 bit DST Port 32 bit sequence number 32 bit ACK number HL resvd flags 16 bit window size 16 bit TCP checksum 16 bit urgent pointer Options (if any) Data Flags: URG, ACK, PSH, RST, SYN, FIN

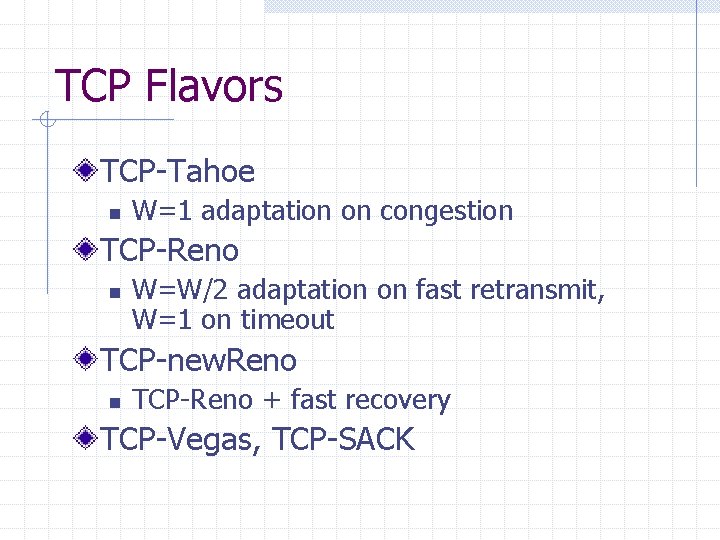
TCP Flavors TCP-Tahoe n W=1 adaptation on congestion TCP-Reno n W=W/2 adaptation on fast retransmit, W=1 on timeout TCP-new. Reno n TCP-Reno + fast recovery TCP-Vegas, TCP-SACK

TCP Tahoe Slow-start Congestion control upon time-out or DUPACKs When the sender receives 3 duplicate ACKs for the same sequence number, sender infers a loss Congestion window reduced to 1 and slowstart performed again Simple Congestion control too aggressive

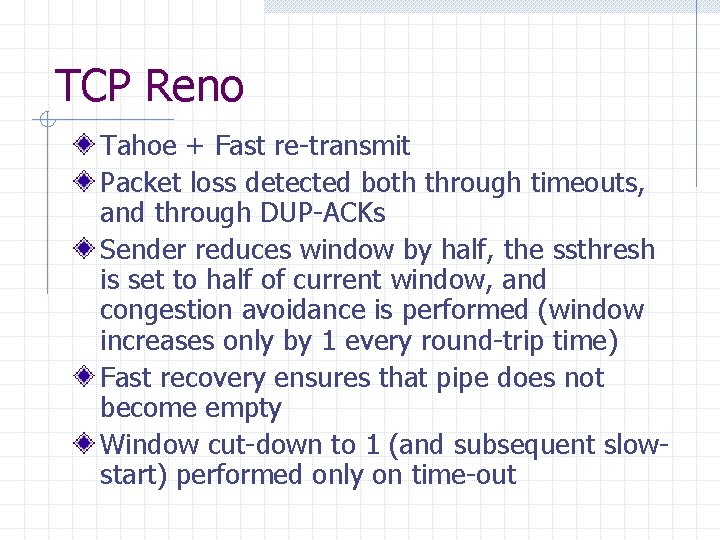
TCP Reno Tahoe + Fast re-transmit Packet loss detected both through timeouts, and through DUP-ACKs Sender reduces window by half, the ssthresh is set to half of current window, and congestion avoidance is performed (window increases only by 1 every round-trip time) Fast recovery ensures that pipe does not become empty Window cut-down to 1 (and subsequent slowstart) performed only on time-out

TCP New-Reno TCP-Reno with more intelligence during fast recovery In TCP-Reno, the first partial ACK will bring the sender out of the fast recovery phase Results in timeouts when there are multiple losses In TCP New-Reno, partial ACK is taken as an indication of another lost packet (which is immediately retransmitted). Sender comes out of fast recovery only after all outstanding packets (at the time of first loss) are ACKed

TCP SACK TCP (Tahoe, Reno, and New-Reno) uses cumulative acknowledgements When there are multiple losses, TCP Reno and New-Reno can retransmit only one lost packet per round-trip time What about TCP-Tahoe? SACK enables receiver to give more information to sender about received packets allowing sender to recover from multiplepacket losses faster

TCP SACK (Example) Assume packets 5 -25 are transmitted Let packets 5, 12, and 18 be lost Receiver sends back a CACK=5, and SACK=(6 -11, 13 -17, 19 -25) Sender knows that packets 5, 12, and 18 are lost and retransmits them immediately

Other TCP flavors TCP Vegas n n Uses round-trip time as an early-congestion -feedback mechanism Reduces losses TCP FACK n Intelligently uses TCP SACK information to optimize the fast recovery mechanism further

User Datagram Protocol (UDP) Simpler cousin of TCP No reliability, sequencing, congestion control, flow control, or connection management! Serves solely as a labeling mechanism for demultiplexing at the receiver end Use predominantly by protocols that do no require the strict service guarantees offered by TCP (e. g. real-time multimedia protocols) Additional intelligence built at the application layer if needed

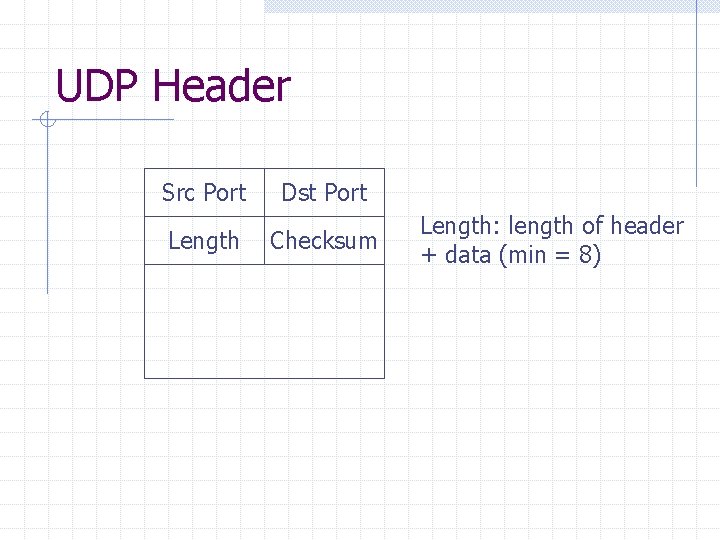
UDP Header Src Port Length Dst Port Checksum Length: length of header + data (min = 8)

Recap TCP Connection management Reliability Flow control Congestion control TCP flavors UDP