Strong and Alternative Authentication Rafa ukawiecki Strategic Consultant































- Slides: 37

Strong and Alternative Authentication Rafał Łukawiecki Strategic Consultant, Project Botticelli Ltd rafal@projectbotticelli. co. uk www. projectbotticelli. co. uk Copyright 2006 © Microsoft Corp & Project Botticelli Ltd. E&OE. For informational purposes only. No warranties of any kind are made and you have to verify all information before relying on it. You can re-use this presentation as long as you read, agree, and follow the guidelines described in the “Comments” field in File/Properties. This presentation is based on work of many authors from Microsoft, Oxford Computer Group and other companies. Please see the “Introductions” presentation for acknowledgments.

2 Objectives Revisit the foundation of IAM from the perspective of modern, strong and specialised authentication mechanisms Explain ways of integrating them within a Microsoft framework containing heterogeneous systems Highlight some remaining issues and opportunities

3 Session Agenda Public Key Infrastructure Smartcards and Alacris OTPs and Secur. ID Biometrics

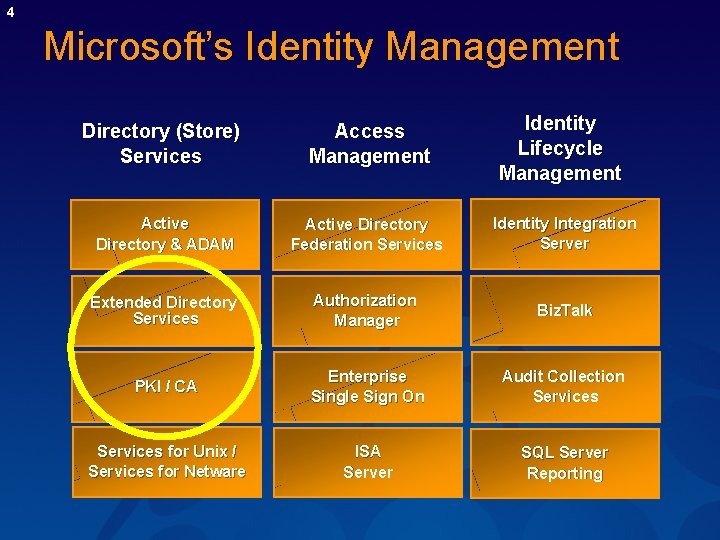
4 Microsoft’s Identity Management Directory (Store) Services Access Management Identity Lifecycle Management Active Directory & ADAM Active Directory Federation Services Identity Integration Server Extended Directory Services Authorization Manager Biz. Talk PKI / CA Enterprise Single Sign On Audit Collection Services for Unix / Services for Netware ISA Server SQL Server Reporting

5 Public Key Infrastructure

6 PKI Infrastructure for practical use of cryptographic mechanisms for authentication and authorisation purposes Not new! Very well tested and based on sound principles. Unfortunately, too complex from a today’s typical user’s perspective

7 Strong Authentication Unlike most password systems, PKI-based authentication relies on certificates and protocols that provide highest level of strength in terms of veracity of authentication No secrets are exchanged in open No reusable data is sent away Man-in-the-middle is usually not possible Scientific edge to understanding strength Protection of certificates requires additional devices, and, perhaps, passwords

8 Microsoft Certificate Authority in Windows Server 2003 Standards Supported: RFC 2459 Support (CRLs and Certificate Profiles) X. 509 v 3, v 4 RFC 2797 (CMC) SCEP (Simple Certificate Enrollment Protocol) PKCS #1, 7, 8, 10, 12 RFCs 2311, 2312, 2313, 2527, 2587, 2631, 2632, 2633, 2634 RFC 2560 (OCSP – Online Certificate Status Protocol) Supports Auto enrollment, Client Certificate Distribution Built into the OS, API/CLI/Web Interface

9 Windows as CA Windows consumes and provides PKI and CA services This is referred to as one of three “Extended Certificate Services” in terms of IAM The other two being: Smartcard Management and Information Rights Management Apart from replacing passwords, this leads to a very powerful form of Single Sign-On Interoperability depends on mutual recognition of CA roots and certificate claims

10 Modular Architecture Windows OS uses multiple, user-selectable, Cryptographic Services Providers (CSPs) to implement core functionality, such as encryption etc. Communication with CSPs is achieved through a number of APIs, of which the most fundamental is Crypto. API (CAPI, CAPICOM) CSPs vary widely, which can compromise security Microsoft has recently (Dec 05) shipped a generic CSP that can be used where custom ones are not economical If this is of interest to you, please review significant new mechanisms and APIs in Windows Vista

11 Cryptography Recommendation At present (December 2005), consider using the following cryptographic mechanisms available in Windows in preference to others: AES-128 (or AES-192, or AES-256) RSA 2048 (or longer) “SHA-2” (i. e. SHA-256, or SHA-512) DSA Avoid the following, if possible: 3 DES (speed) RC 2 (superseded but generally fine) RC 4 (issues, but can be overcome) DESX (esoteric) Do not use at all: DES (strength)

12 Cryptography Tomorrow US NSA and NIST recommendation as of Feb 2005 is to implement “Suite-B” protocols This is very rarely done in today’s software Good news: Microsoft announced support for Suite-B in Windows Vista (and Longhorn Server)

14 Smartcards/Tokens and Alacris

15 Why Smartcards? Smartcards are physical devices that protect a private cryptographic key from being copied or used without additional authentication Basically: Do not store a private key on the computer itself if possible If you do, ensure it is well protected, e. g. using Windows default Protected Storage service, DPAPI etc.

16 Form Factors Smartcards are not always “cards”, so they are sometimes referred to as Tokens USB devices Bluetooth devices Incl. : Mobile Phones Active RFIDs (Radio Frequency Identifiers) On-board silicone chips, sometimes being part of other chips (Trusted Platform Modules, such as TPM v 1. 2) Note: this is a future direction being adopted by forms of “Trusted Computing Base/Infrastructure”

17 Secondary Authentication (Optional) Smartcards usually do not provide their services, or any access to the private key, unless a secondary authentication succeeds: PINs and passwords Not sent across networks, this is locally processed on board of the card Biometrics (see later) Co-presence of other devices RFIDs Note: the authenticator may be on board of the “card” reader (more secure), or may be a function of the PC or host computer (less secure or less trustworthy)

18 Smartcard Compatibility with Windows Entirely dependent on the presence of a suitable CSP (Cryptographic Service Provider) Typically installed when hardware “reader” device is installed Many providers exist Microsoft promotes a. NET-based smartcard through Axalto consortium Windows Vista allows a broader range of smartcards to be supported, including: Card Communication Modules Common CSPs CNG (Open Cryptographic Interface for Windows)

19 Word About Smartcards Some smartcards are “dumb”, i. e. they are only a memory chip, so key can be easily stolen Not recommended, not approved to Common Criteria (FIPS 140 -2) Not all smartcards are equal Not all have an on-board RNG (Random Number Generator) Some cannot generate keys and rely on the reader or the host Self-destruct is possible on some

20 Smartcard Lifecycle - id. Nexus Users will, of course, lose smartcards They will expire Need for: Provisioning, maintenance etc. Lifecycle management of smartcards has not been a function of Windows, but is implemented in Alacris’ id. Nexus Alacris has been acquired by Microsoft on 19 Sept 2005

21 id. Nexus (Alacris) Identity Assurance Management System Integrates with: Windows 2003 PKI Entrust (CA) Supports: Lifecycle Management (incl. Provisioning) Smartcard Logon OCSP through Alacris Identity Validation System Client and server for Online Certificate Status Protocol Used by IIS, IE, Outlook and many others Common Criteria certified

22 OTPs and Secur. ID

23 One Time Passwords (OTPs) Usually: hardware that generates a single-use value that functions as a password Trust between the device and the remote system is implemented as physical relationship E. g. precise clock synchronisation, as in RSA Secur. ID As with smartcards, secondary authentication is possible (PIN, biometrics etc. ) OTP devices are frequently called Security Tokens, or Tokens A bit confusing, as some smartcards are also known as tokens, e. g. Aladdin Token)

24 OTP or Smartcard? Effective functionality and security strengths are surprisingly similar, however: Ease of initial deployment: OTPs have an advantage, as most smartcard systems require presence of PKI first Extensibility Both are similar, though OTPs have an incremental cost for each additional system being interconnected Universal Integration Smartcards and PKI, being based on standards, tend to have a more universal appeal (as long as PKI is compatible, which usually is the case) than OTPs

25 RSA Secur. ID Probably the best known OTP system Like most OTPs, it functions as a client-based Single Sign-On system Requires additional servers/services Integrates very well with Microsoft IAM Unlike smartcards, requires no readers With web-based thin-client applications, even no additional client software is needed

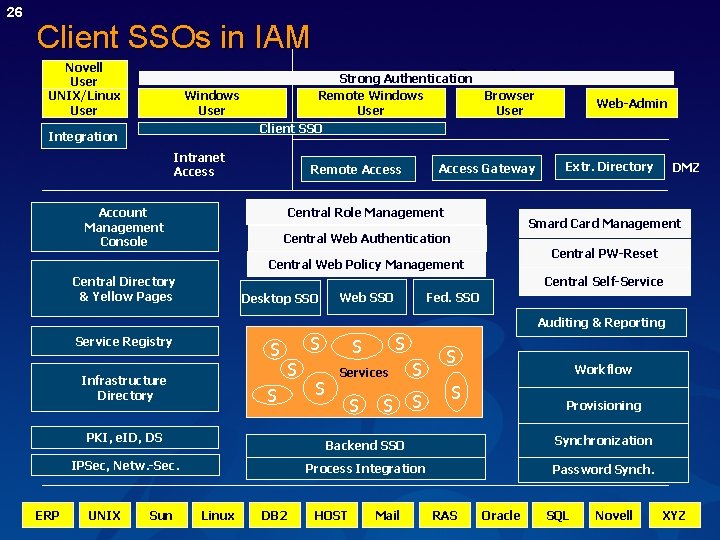
26 Client SSOs in IAM Novell User UNIX/Linux User Remote Access Strong Authentication Remote Windows Browser User Windows User Web-Admin Client SSO Integration Intranet Access Gateway Remote Access Central Role Management Account Management Console Extr. Directory DMZ Smard Card Management Central Web Authentication Central PW-Reset Central Web Policy Management Central Directory & Yellow Pages Central Self-Service Desktop SSO Web SSO Fed. SSO Auditing & Reporting Service Registry S Infrastructure Directory S S S PKI, e. ID, DS IPSec, Netw. -Sec. ERP UNIX Sun Linux DB 2 S Services S S S Workflow S Provisioning Backend SSO Synchronization Process Integration Password Synch. HOST Mail RAS Oracle SQL Novell XYZ

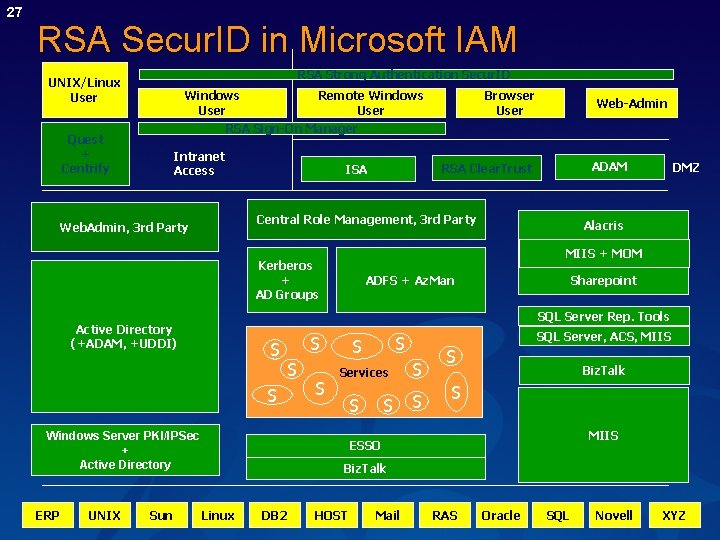
27 RSA Secur. ID in Microsoft IAM RSA Strong Authentication. Remote Secur. IDAccess UNIX/Linux User Windows User Remote Windows User Web-Admin RSA Sign-On Manager Quest + Centrify Intranet Access Alacris ADFS + Az. Man Sharepoint 3 rd Party SQL Server Rep. Tools Active Directory ADAM / AD+UDDI) / UDDI (+ADAM, S AD S S S Windows Server PKI/IPSec Windows CA or Keon + Active Directory Sun DMZ Sharepoint ++ MIIS + MOM Kerberos + AD Groups UNIX ADAM RSA Clear. Trust ISA Central Role Management, 3 rd Party Web. Admin, 3 rd Party ERP Browser User Linux DB 2 S SQL Server, ACS, MIIS S S Services S S S Biz. Talk S ESSO MIIS Biz. Talk MIIS HOST Mail RAS Oracle SQL Novell XYZ

28 Biometrics

29 Biometrics Identification (rather than authentication) of a human subject by means of scanning their physical characteristics, such as: Image (face, iris, retina, hands, papillary lines) Sound (voice print identification, footsteps) Movement (writing characteristics, facial ticks) Chemical (body odour, breath, hair composition, possibly even DNA analysis) Physiology (pulse, blood pressure, temperature, blood oxygen content, intraoccular fluid pressure) These are typically secondary verifiers to avoid inanimate objects being used to fool the scanner

30 Biometrics Generally, an over-hyped area: be careful and sceptical Useful as a secondary protection of a private key on a smartcard in a controlled environment Advantage: Simple and works in some environs, e. g. immigration Weakness: Not useful for at-home, remote etc. applications as no way to ensure it is your real fingerprint, iris, retina etc. being scanned Biometric data can be stolen and can be used to fake identity – no way to change it later Still many positive and negative false matches

31 Controlled Environments Presence of a Trusted Observer – Guard, Officer, Witness… Trustworthiness of biometrics relies on the trust in the scanner/reader and trust in the correct application of the scan procedure Scanner Trust: There must be no easy way of “replaying” the biometric sequence, bypassing the device In reality, this means device must have construction that cannot be easily compromised, and must have a pre-arranged, trusted and confidential connection to the Relying Party Today, this requires a controlled environment Procedure Trust: Ensuring that it is a real fingerprint/iris/retina being scanned, rather than a replica

32 Meaningless Application Example: Using a keyboard-based fingerprint scanner to allow a home user to log into an online banking site Problems: Copies of fingerprints will be readily available on the keyboard. What if the keyboard is stolen? What if someone breaks into the room and uses your keyboard? How does the bank know it is really a finger being scanned? Future: Perhaps devices will exist that can overcome these issues, but that is not likely to happen very soon

33 False Negatives/Positives Today’s biometrics still suffers from a large pool of false matches According to UK Home Office 2005 research, it would be necessary to scan one iris/retina and fingers of both hands to reduce the mismatches to an acceptable level Future? Very bright, as we overcome this problem.

34 Role of Biometrics Mainly: secondary authentication for a smartcards/token/OTP device Also Primary identification in controlled environments Simplified authentication for low-security applications But: that is not strong authentication

35 Summary

36 Summary Strong authentication removes the need for user -managed passwords Most today’s solutions are based either on smartcards or OTP tokens, and require some client-specific integration Biometrics is an interesting enhancement of identification and, perhaps, authentication but has limited applications at present www. microsoft. com/idm & www. microsoft. com/itsshowtime & www. microsoft. com/technet

37 Special Thanks This seminar was prepared with the help of: Oxford Computer Group Ltd Expertise in Identity and Access Management (Microsoft Partner) IT Service Delivery and Training www. oxfordcomputergroup. com Microsoft, with special thanks to: Daniel Meyer – thanks for many slides Steven Adler, Ronny Bjones, Olga Londer – planning and reviewing Philippe Lemmens, Detlef Eckert – Sponsorship Bas Paumen & NGN - feedback

38 Q&A Please complete evaluation forms when you receive them – thank you. Read more about IAM at: www. microsoft. com/idm Watch other seminars at: www. microsoft. com/itsshowtime Find all IT Pro technical information at: www. microsoft. com/technet
 Be strong be strong be strong in the lord
Be strong be strong be strong in the lord Peer entity authentication and data origin authentication
Peer entity authentication and data origin authentication Iff
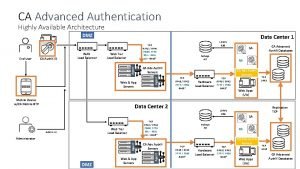
Iff Ca advanced authentication
Ca advanced authentication Ośrodek rafa jarosławiec
Ośrodek rafa jarosławiec Rafa consulting
Rafa consulting How to remember strong acids and strong bases
How to remember strong acids and strong bases Strong acid strong base titration curve
Strong acid strong base titration curve Ionic equation of titration
Ionic equation of titration Strong acid strong base titration
Strong acid strong base titration Weak base strong acid titration curve
Weak base strong acid titration curve What are strong bases
What are strong bases Strategic complements
Strategic complements Io model strategic management
Io model strategic management Analysing the 6 strategic options megxit
Analysing the 6 strategic options megxit Strategic fit vs strategic intent
Strategic fit vs strategic intent Ward temple and family history leader
Ward temple and family history leader Modern data architecture consulting
Modern data architecture consulting Consultant mediu
Consultant mediu Claudia norman a marketing consultant
Claudia norman a marketing consultant Judith james educational consultant
Judith james educational consultant Behavioral genetics consultant
Behavioral genetics consultant Rcem consultant sign off
Rcem consultant sign off Open source consultant
Open source consultant Knowledge management consultancy
Knowledge management consultancy Verizon ip centrex
Verizon ip centrex United states lactation consultant association
United states lactation consultant association What is a consultant radiographer
What is a consultant radiographer Calling script for hr recruiter
Calling script for hr recruiter Stuart minty
Stuart minty Talent acquisition consultant philips
Talent acquisition consultant philips Nous hospital consultant
Nous hospital consultant Test consultant capgemini
Test consultant capgemini Fdot consultant acquisition plan
Fdot consultant acquisition plan Epicor configurator
Epicor configurator Nutra metrix
Nutra metrix Scan based trading consultant
Scan based trading consultant Rodan and fields tax write offs
Rodan and fields tax write offs