Secure Coding CSH 6 Chapter 38 Writing Secure
























![What Is a Buffer Overflow? double array[8] Programming concept: array(0) Ø Define (declare, dimension) What Is a Buffer Overflow? double array[8] Programming concept: array(0) Ø Define (declare, dimension)](https://slidetodoc.com/presentation_image_h/ed2cc74a5bb89f27b4247554de771635/image-30.jpg)


















- Slides: 60

Secure Coding CSH 6 Chapter 38 “Writing Secure Code” Lester E. Nichols, M. E. Kabay, & Timothy Braithwaite 1 Copyright © 2020 M. E. Kabay. All rights reserved.

Topics ØIntroduction ØPolicy & Management Issues ØTechnical & Procedural Issues ØTypes of Software Errors ØAssurance Tools & Techniques 2 Copyright © 2020 M. E. Kabay. All rights reserved.

Introduction Ø Chapter / lecture serves as overview & introduction to large subject Ø Secure coding complex issue Ø Involves human factors & technical issues Ø Requires coordination & cooperation of many sectors in organization Ø Starts with a few funny (or scary) examples of SQA failures 3 Copyright © 2020 M. E. Kabay. All rights reserved.

Easter Egg in Excel 97 Ø Undocumented keystrokes would activate flight simulator using full-screen graphics q 1. On a new Worksheet, Press F 5 q 2. Type X 97: L 97 and Enter q 3. Press the Tab key q 4. Hold Ctrl-Shift q 5. Click on the Chart Wizard toolbar button q 6. Use mouse to fly around - Right button forward/ Left button reverse Ø Included rolling credits of developer names Ø Pressing ESC would crash some systems Ø http: //www. youtube. com/watch? v=c 6 n. Y 0 Qk. G 9 n. Q 4 Copyright © 2020 M. E. Kabay. All rights reserved.

Secret Writer’s Society (1998) Ø Game for children Ø Read kids’ writing back to them out loud Ø Included filter of prohibited nasty words q. Curses, obscenities… Ø Bug: proceeded to read ALL the bad words out loud to the children! Ø “Children and parents were startled by the streams of foul language erupting from their computers. ” Ø “The company's response was to deny that it was a significant problem. ” 5 Copyright © 2020 M. E. Kabay. All rights reserved.

Belligerent Crapper (2001) Ø A 51 -year-old woman was subjected to a harrowing twohour ordeal [on 16 Apr 2001] when she was imprisoned in a hi-tech public convenience. Ø Maureen Shotton, from Whitley Bay, was captured by the maverick cyberloo during a shopping trip to Newcastleupon-Tyne. Ø The toilet, which boasts state-of-the-art electronic autoflush and door sensors, steadfastly refused to release Maureen, and further resisted attempts by passers-by to force the door. Ø Maureen was finally liberated when the fire brigade ripped the roof off the cantankerous crapper. Ø Maureen's terrifying experience confirms that it is a short step from belligerent bogs to Terminator-style cyborgs hunting down and exterminating mankind. [RISKS 21: 35] 6 Copyright © 2020 M. E. Kabay. All rights reserved.

Waldo Goes Wild (2005) Ø UCSF Medical Center q“Waldo” (named after famous Heinlein story) dispensed pills & potions q. Size of a small washing machine Ø Waldo suddenly refused to return to dispensary for new pills Ø Went roaring past destination at high speed Ø Crashed into radiation oncology department q. Patient examination in progress Ø “The psychotic pill pusher reportedly refused to leave, sending both doctor and patient fleeing for their lives. ” 7 Copyright © 2020 M. E. Kabay. All rights reserved.

SCADA System Insecurity Ø Supervisory Control and Data Acquisition Systems Ø INFOSEC Year in Review database 8 Copyright © 2020 M. E. Kabay. All rights reserved.

Policy & Management Issues Ø Security of code has become essential q Strategic importance q Yet many SW projects produce üInadequate functionality (wrong goals) üBuggy code (not achieving goals) Ø Fundamental problems q Short-term accounting fails to recognize long-term benefits of investing in low-bug code q Difficulty in proving negative: absence of bugs Ø Topics on following slides: q Software TQM q Due Diligence q Regulatory & Compliance Considerations 9 Copyright © 2020 M. E. Kabay. All rights reserved.

Software TQM Ø Software must adapt to constantly changing needs q. ISO 9000 family of standards q. Plan-do-check-act / plan-fix-monitor-assess Ø Integrate security planning into every phase of SW cycle q. Analysis, requirements, design, coding, implementation q. Cannot effectively or efficiently retrofit security Ø Expect iterative approach to compliance q. Must cope with changing threat environment q. Include security in modifications 10 Copyright © 2020 M. E. Kabay. All rights reserved.

Due Diligence Ø Management must integrate security into performance metrics Ø Evolving security information forces changes in best practices Ø Boards / C-level executives becoming personally liable for failures Ø Must establish & document security risk management in SW development q. Thus demonstrate compliance with current standards q. Meet standard of due care and diligence in exercising fiduciary responsibilities 11 Copyright © 2020 M. E. Kabay. All rights reserved.

Regulatory & Compliance Considerations Ø Specific regulations usually dictate need for records; e. g. , q. Sarbanes-Oxley q. Gramm-Leach-Bliley q. Health Insurance Portability & Accountability Act Ø Keep records of problems q. Identification date & agent q. Severity (implications, systems affected) q. Report to management q. Remediation target & completion date 12 Copyright © 2020 M. E. Kabay. All rights reserved.

Technical & Procedural Issues Ø Development team often under time pressure q. Sales / management personnel may value time to market over lack of bugs q. Must fight to adhere to systematic SW development methodology with adequate prevention, monitoring & correction of errors Ø Topics on following slides: q. Requirements Analysis q. Design q. Operating System q. Best Practices & Guidelines q. Languages 13 Copyright © 2020 M. E. Kabay. All rights reserved.

Requirements Analysis Ø Staircase principle: delaying correction multiplies cost of error 10 x q. Requirements analysis q. Requirements definition q. Design q. Coding q. Implementation Ø Analysis must include discussions of security needs (confidentiality, control, integrity, authenticity, availability, utility) Ø Definition must explicitly define function goals that include these security aspects 14 Copyright © 2020 M. E. Kabay. All rights reserved.

Design Ø Data structures design instantiates information model Ø Logic design instantiates relationships among elements of model Ø Procedural model instantiates data flow and object relations q. Include access privileges, restrictions Ø Project planning must allow for adequate software quality assurance [See CSH 6 Chapter 39, “Software Development & Quality Assurance”] 15 Copyright © 2020 M. E. Kabay. All rights reserved.

Operating System Ø OS is at core of security implementation Ø Secure OS implements q. Completeness: all access to information managed by kernel q. Isolation: kernel protected against unauthorized access q. Verifiability: kernel proven to meet design specifications 16 Copyright © 2020 M. E. Kabay. All rights reserved.

Best Practices & Guidelines (1) 17 Ø Excellent guides to best practices: q. NIST Special Publications Series 800 ühttp: //csrc. nist. gov/publications/Pubs. SPs. ht ml q. List of recommendations in § 38. 3. 4 (below) Ø Impose strong I&A Ø Document code thoroughly Ø Use local variables, not global variables, when storing sensitive data Ø Reinitialize temporary storage immediately after the last legitimate use Ø Limit functionality in a specific module to what is required for a specific job Copyright © 2020 M. E. Kabay. All rights reserved.

Best Practices (2) Ø Define views of data in databases that conform to functional requirements and limit access to sensitive data Ø Use strong encryption (not homegrown encryption) Ø Disallow access by programmers to production databases Ø Randomize or otherwise mask sensitive data when generating test subsets from production data Ø Use test-coverage monitors Ø Integrate logging capability into all applications 18 Copyright © 2020 M. E. Kabay. All rights reserved.

Best Practices (3) Ø Create log-file records with cryptographically sound message authentication code (MAC) that itself includes the MAC of the preceding record Ø Log all process initiations for a program and log process termination Ø Log all modifications to records Ø Use record-level locking Ø Unlock a sequence of locks in the inverse order of the lock sequence to prevent deadlocks Ø Sign your source code using digital signatures Ø Use checksums in production executables 19 Copyright © 2020 M. E. Kabay. All rights reserved.

Best Practices (4) Ø Design code holistically, including tests of what should not be accepted Ø Establish criteria for defining and determining sensitivity of data being processed Ø Implement formal SQA control processes Ø Identify mandatory OS & NW security settings for code to run securely Ø Verify digital signatures of routines being loaded for execution Ø Verify digital signatures or checksums of all executables being loaded at system restart 20 Copyright © 2020 M. E. Kabay. All rights reserved.

Microsoft SQA Project Ø Nov 2001: Bill Gates -- two top priorities q. Improving reliability of MS sw q. Conquering market for "tablet" computers Ø Jan 2002: Trustworthy Computing initiative launched q. Choose security over features q. Emphasize security right out of the box q. Privacy key concern Ø Feb 2002: MS hires top security expert q. Scott Charney – famous expert q. Oversee MS strategies for enhanced security 21 Copyright © 2020 M. E. Kabay. All rights reserved.

Examples of MS SQA Books 22 Copyright © 2020 M. E. Kabay. All rights reserved.

Languages Ø To degree possible, take advantage of security features of programming tools Ø Different languages offer different advantages q. Java includes sandbox for isolation of processes q. PASCAL offers strong typing q. But C & C++ have almost no security restrictions during execution Ø Security utilities and routines available for integration q. RSA toolkits q. Textbooks (e. g, Schneier’s Applied Cryptography) 23 Copyright © 2020 M. E. Kabay. All rights reserved.

Types of Software Errors Internal Design or Implementation Ø Initialization Ø Logic Flow Ø Calculation Ø Boundary Condition Violations Ø Parameter Passing Ø Race Condition Ø Load Condition Ø Resource Exhaustion Ø Resource, Address, or Program Conflict with the Operating System or Application(s) Ø Regulatory Compliance Considerations Ø Other Errors OOPS! DARN! 24 Copyright © 2020 M. E. Kabay. All rights reserved.

Initialization Errors Ø Insidious & difficult to find Ø Failing to initialize data may leave garbage in registers q. So program may fail depending on what is in registers from some previous use q. And program may fail on 1 st use q. Intermittent problem – race condition Ø Others may always fail on 1 st use because of zero and blank values from OS or language rules Ø Some programs write initialized values to disk q. So fail only on 1 st use 25 Copyright © 2020 M. E. Kabay. All rights reserved.

Logic Flow Ø Modules pass control to each other or other programs Ø So calling wrong function causes error Ø Problems occur when code branches to subroutine lacking a RETURN code Ø Often data dependent q. Intermittent failures Ø Use DEBUG utility to check current execution, step through code 26 Copyright © 2020 M. E. Kabay. All rights reserved.

Calculation Ø Frequent problem: wrong size of storage element q. Store long value in short field q. Truncates data, leads to bad calculations Ø Errors in formula may be hard to catch q. Especially if specifics of formula are data dependent 27 Copyright © 2020 M. E. Kabay. All rights reserved.

Boundary Condition Violations Ø Critically important to define limits on acceptable data values = bounds Ø Most common error: buffer overflow q. Data exceeds expected length of storage q. Usually exploited using input buffers q. Send long data string into input which is not checked for length q. Program writes data beyond end of array q. May execute portions of data stream Ø Always check data length before storing q. Reject; or q. Truncate 28 Copyright © 2020 M. E. Kabay. All rights reserved.

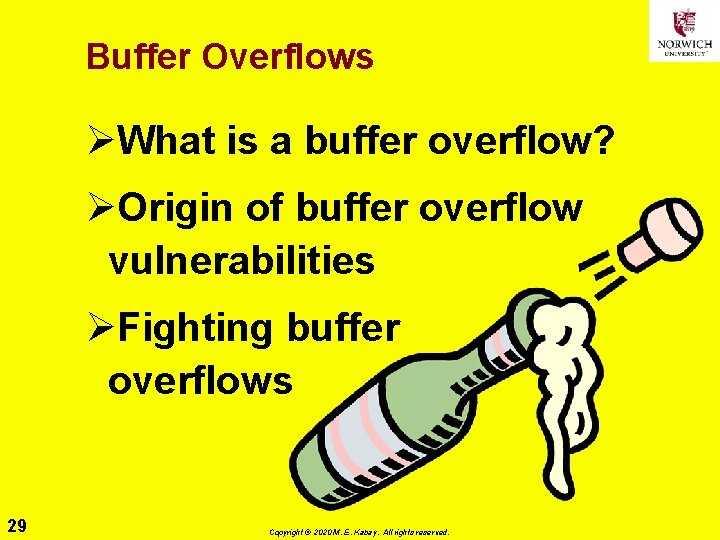
Buffer Overflows ØWhat is a buffer overflow? ØOrigin of buffer overflow vulnerabilities ØFighting buffer overflows 29 Copyright © 2020 M. E. Kabay. All rights reserved.
![What Is a Buffer Overflow double array8 Programming concept array0 Ø Define declare dimension What Is a Buffer Overflow? double array[8] Programming concept: array(0) Ø Define (declare, dimension)](https://slidetodoc.com/presentation_image_h/ed2cc74a5bb89f27b4247554de771635/image-30.jpg)
What Is a Buffer Overflow? double array[8] Programming concept: array(0) Ø Define (declare, dimension) array(1) qlist (array, indexed variable, string) array(7) qof certain size Ø To reserve area of memory for specific use during execution 30 Copyright © 2020 M. E. Kabay. All rights reserved. } Other data

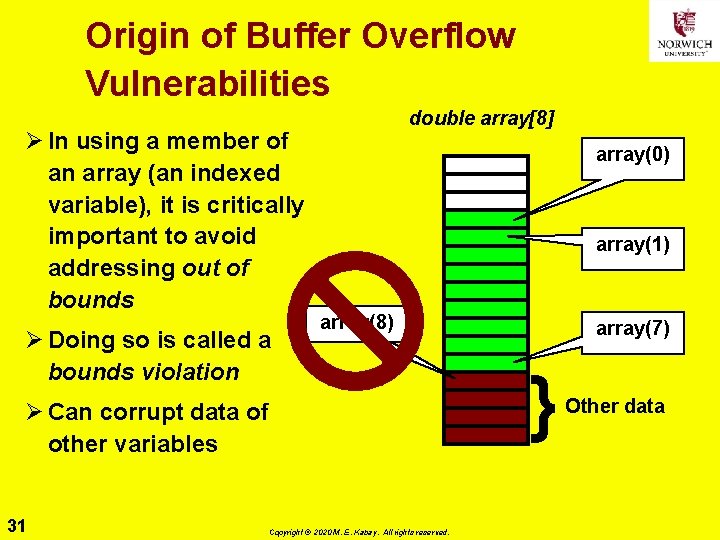
Origin of Buffer Overflow Vulnerabilities Ø In using a member of an array (an indexed variable), it is critically important to avoid addressing out of bounds Ø Doing so is called a bounds violation double array[8] array(0) array(1) array(8) Ø Can corrupt data of other variables 31 Copyright © 2020 M. E. Kabay. All rights reserved. array(7) } Other data

Consequences of Bounds Violations Possible to see Ø Compiler error Ø Run-time error Ø Program errors – bad results Ø Program crash Ø System crash But most dangerous problem occurs in interpreters Ø Programs that dynamically interpret instructions Ø E. g. , browsers, Web server programs 32 Copyright © 2020 M. E. Kabay. All rights reserved.

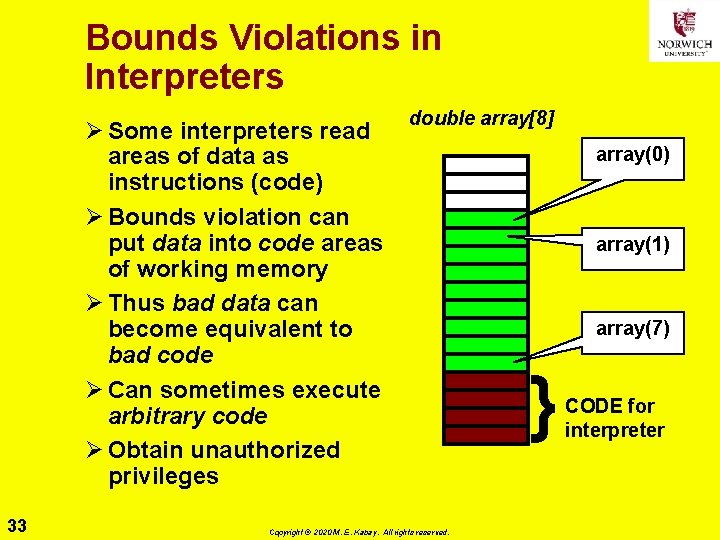
Bounds Violations in Interpreters Ø Some interpreters read areas of data as instructions (code) Ø Bounds violation can put data into code areas of working memory Ø Thus bad data can become equivalent to bad code Ø Can sometimes execute arbitrary code Ø Obtain unauthorized privileges 33 double array[8] Copyright © 2020 M. E. Kabay. All rights reserved. array(0) array(1) array(7) } CODE for interpreter

Fighting Buffer Overflows Ø Programmers need to use good quality assurance techniques q. Test long input strings q. Test below, at and above boundary conditions Ø System / network / security staff: check for new buffer overflows & install patches q. Use ICAT Metabase frequently q. Subscribe to CERT-CC alerts from http: //www. cert. org 34 Copyright © 2020 M. E. Kabay. All rights reserved.

Fighting Buffer Overflows (cont’d) Ø Managers need to understand that every buffer overflow is a failure of quality assurance Ø Stop allowing manufacturers to publish inadequately tested software as production versions Ø Stop letting manufacturers push quality assurance onto the client base Ø Complain loudly to manufacturers when there are buffer overflows in their software – and, if possible, buy competing products with better quality assurance 35 Copyright © 2020 M. E. Kabay. All rights reserved.

Parameter Passing Ø Parameters passed among routines Ø Wrong name or wrong subscript in array variable may pass wrong data Ø Can cause errors in q. Calculations q. Logic flow Ø Cascade of errors likely q. Data corruption q. Aborts 36 Copyright © 2020 M. E. Kabay. All rights reserved.

Race Condition Ø Problems occur when q. Specific sequence of events required for correct operation q. But no enforcement or guarantee of sequence Ø Known as race condition because correct operation is a race between events Ø Classic example occurs in incorrect locking strategies q. A locks 1 and then locks 2 q. B locks 2 and then locks 1 q. OK if B tries to lock 2 AFTER A locks 2 q. But deadlock if B locks 2 before A tries to locks 2 37 Copyright © 2020 M. E. Kabay. All rights reserved.

Load Condition Ø Exceeding expected q. Storage q. Transactions q. Users q. Network bandwidth utilization Ø May cause major declines in throughput q. Problems of availability Ø Should use automated testing for simulation q. Identify bottlenecks q. Take preventative actions 38 Copyright © 2020 M. E. Kabay. All rights reserved.

Resource Exhaustion Ø Exhausting resources can cause failure; e. g. , q. Cannot write to full disk q. Cannot obtain memory location q. Cannot obtain CPU in time for real-time processing q. Running out of system table entries Ø Running with inadequate main memory may lead to excessive swapping between virtual memory and main memory q. Thrashing 39 Copyright © 2020 M. E. Kabay. All rights reserved.

Interapplication Conflicts Ø OS makers routinely provide application SW makers with coding guidance & kits Ø But as OS versions & patches move on, older applications may fail q. E. g. , HP 3000 MPE increased stack requirements q. Older programs close to stack limitations crashed with stack overflows 40 Copyright © 2020 M. E. Kabay. All rights reserved.

Other Errors Ø Sending bad data to devices Ø Ignoring error codes from devices Ø Trying to use busy or missing devices Ø Improper builds of code (using wrong routines) 41 Copyright © 2020 M. E. Kabay. All rights reserved.

User Interface Ø User Virtual Machine q. Screens q. Mouse & keyboard q. Printed outputs Ø Especially important to realize that user is not telepathic: q. Cannot automatically know what designer / programmer knows and assumes (“HIT ANY KEY” → “Where’s the ANY key? ? ”) q. So programmers responsible for envisaging possible pitfalls and preventing problems Ø Documentation & training essential 42 Copyright © 2020 M. E. Kabay. All rights reserved.

Functionality (1) Ø When performance reasonably expected is missing, confusing, awkward, difficult or impossible, we have a functionality problem Ø See list of suggestions in § 38. 4. 1. 1. 2 & on following slides 43 Copyright © 2020 M. E. Kabay. All rights reserved.

Functionality (2) Ø Features are not documented Ø Required information is missing Ø A program fails to acknowledge legitimate input Ø There are factual errors or conflicting names for features Ø There is information overload Ø The material is written to an inappropriate reading level Ø The cursor disappears, or is in the wrong place Ø Screen displays are wrong Ø Instructions are obscured 44 Copyright © 2020 M. E. Kabay. All rights reserved.

Functionality (3) Ø Identical functions require different operations in different screens Ø Improperly formatted input screens exist Ø Passwords or other confidential information not obscured or protected adequately Ø Tracing user data entry or changes unavailable or incomplete Ø Segregation of duties not enforced (Can be particularly critical for organizations subject to legal and regulatory requirements) 45 Copyright © 2020 M. E. Kabay. All rights reserved.

Control (Command) Structure (1) Control structure errors can cause serious problems because they can result in: Ø Users getting lost in a program Ø Users wasting time because they must deal with confusing commands Ø Loss of data or unwanted exposure of data Ø Work delay Ø Financial cost Ø Unanticipated exposure to data leakage or compromise; can result in significant liability if consumers' personal identifying information (PII) compromised Ø Data not being encrypted as intended or being visible to unauthorized users 46 Copyright © 2020 M. E. Kabay. All rights reserved.

Control (Command) Structure (2) Some common errors listed in § 38. 4. 1. 13 include: Ø Inability to move between menus Ø Confusing and repetitive menus Ø Failure to allow adequate command-line entries Ø Requiring command-line entries that are neither intuitive nor clearly defined on screen Ø Failure of the application program to follow the operating system's conventions Ø Failure to distinguish between source and parameter files, resulting in wrong values being made available to user through interface, or failure to identify source of error 47 Copyright © 2020 M. E. Kabay. All rights reserved.

Control (Command) Structure (3) Ø Inappropriate use of keyboard, when new programs do not meet standard of a keyboard that has labeled function keys tied to standard meanings Ø Missing commands from code and screens resulting in user being unable to access information, to utilize programs, or to provide for system to be backed up and recoverable Ø Inadequate privacy or security that can result in confidential information being divulged, in complete change or loss of data without recoverability, in poor reporting, and even in undesired access by outside parties 48 Copyright © 2020 M. E. Kabay. All rights reserved.

Performance (1) Ø Speed important in interactive software Ø Problem can include q. Slow response q. Unannounced case sensitivity, q. Uncontrollable and excessively frequent automatic saves q. Inability to save q. Limited scrolling speed 49 Copyright © 2020 M. E. Kabay. All rights reserved.

Performance (2) Ø Slow operation can depend on (but is not limited to) q. OS q. Other applications running concurrently q. Memory saturation and thrashing q. Memory leakage (the failure to deallocate memory that is no longer needed) q. Disk I/O inefficiencies (e. g. , reading single records from very large blocks), q. Program conflicts (e. g. , locking errors) Ø See CSH 6 Chapter 52 “Application Controls” 50 Copyright © 2020 M. E. Kabay. All rights reserved.

Performance (3) Ø Program designs can make it difficult to change their functionality q. Response to changing requirements Ø E. g. , database design – defining primary index field q. Determines how records stored on disk q. Can greatly speed access to records during sequential reads on key values for that index q. But can be counterproductive if main method for accessing records = sequential reads on completely different index 51 Copyright © 2020 M. E. Kabay. All rights reserved.

Output Format Ø User cannot change appearance of output q. Font q. Underlining q. Boldface q. Spacing Ø Delays in printing or saving document Ø Problems in scaling tables, figures, graphs Ø Errors in displayed precision of numbers 52 Copyright © 2020 M. E. Kabay. All rights reserved.

Assurance Tools & Techniques Ø Education Resources q. See list in CSH 6 § 38. 5. 1 p 38. 13 Ø Code Examination & Application Penetration Testing See q. White Box next q. Black Box slides q. Gray Box Ø Standards & Best Practices 53 Copyright © 2020 M. E. Kabay. All rights reserved.

White Box Ø AKA glass, structural, open, clear box Ø Tests using knowledge of internals Ø Advantages of white box testing: q Easy to find out which type of input/data can help in testing q Helps in optimizing code q Helps in removing extra (useless) lines of code which can bring in hidden defects Ø Disadvantages of white box testing: q Skilled tester needed → increases cost q Nearly impossible to look into every bit of code to find hidden errors 54 Copyright © 2020 M. E. Kabay. All rights reserved.

Black Box (1) Ø Testing without knowledge of internal workings Ø AKA behavioral, functional, opaque box, closed box Ø Tester & programmer can be independent of one another Ø Avoid programmer bias toward own work Ø Test groups often used Ø Test planning can begin as soon as specifications written 55 Copyright © 2020 M. E. Kabay. All rights reserved.

Black Box (2) Advantages of black box testing: Ø More effective on larger units of code than glass box testing Ø Tester needs no knowledge of implementation, including specific programming languages Ø Tester and programmer independent of each other Ø Tests done from user's point of view Ø Help to expose ambiguities or inconsistencies in specifications. Ø Test cases can be designed as soon as specifications are complete. 56 Copyright © 2020 M. E. Kabay. All rights reserved.

Black Box (3) Disadvantages of black box testing: Ø Few possible inputs can actually be tested Ø Without clear and concise specifications, test cases hard to design Ø Unnecessary repetition of test inputs if the tester not informed of test cases programmer has already tried. Ø May leave many program paths untested Ø Cannot be directed toward specific segments of code that may be very complex 57 Copyright © 2020 M. E. Kabay. All rights reserved.

Gray Box Ø Combination of black box testing and white box testing Ø Tester does know some of internal workings of software under test Ø Applies limited number of test cases to internal workings of software under test Ø Then takes black box approach in applying inputs to software under test and observing outputs 58 Copyright © 2020 M. E. Kabay. All rights reserved.

Standards & Best Practices Ø Consensus q Perform automated testing q Make a test plan q Follow a specific methodology q Test at every stage q Test all system components Ø Standards q ISO 17799, Information Technology: Code of Practice for Information Security Management q ISO/IEC 15408, Evaluation Criteria for IT Security (the Common Criteria) q SSE-CMM, System Security Engineering Capability Maturity Model q ISO/IEC WD 15443, Information Technology: Security Techniques 59 Copyright © 2020 M. E. Kabay. All rights reserved.

Now go and study 60 Copyright © 2020 M. E. Kabay. All rights reserved.