Risk Management Framework RMF Acquisition of Secure Information




















- Slides: 32

Risk Management Framework (RMF) Acquisition of Secure Information Systems Training, Awareness, and Strategies for Privacy and Security Cybersecurity Acquisition Training Overview (CATO) Information Technology Category (ITC) IT Security Subcategory 08 Nov 2017

CATO Roadmap Introduction to Cybersecurity in Acquisitions Risk Management Framework (RMF) Internet of Things (Io. T) Product Tampering and Counterfeiting (PTC)

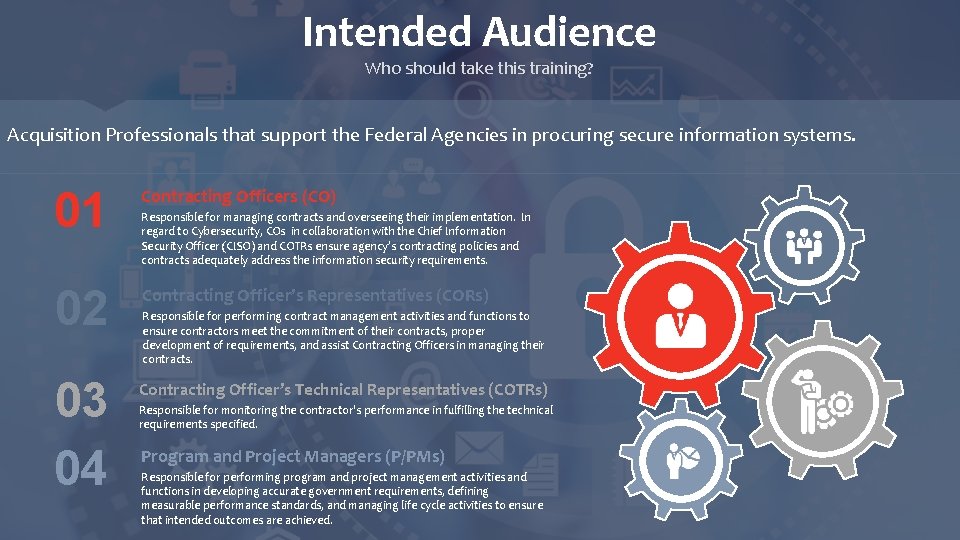
Intended Audience Who should take this training? Acquisition Professionals that support the Federal Agencies in procuring secure information systems. 01 Contracting Officers (CO) 02 Contracting Officer’s Representatives (CORs) 03 04 Contracting Officer’s Technical Representatives (COTRs) Responsible for managing contracts and overseeing their implementation. In regard to Cybersecurity, COs in collaboration with the Chief Information Security Officer (CISO) and COTRs ensure agency’s contracting policies and contracts adequately address the information security requirements. Responsible for performing contract management activities and functions to ensure contractors meet the commitment of their contracts, proper development of requirements, and assist Contracting Officers in managing their contracts. Responsible for monitoring the contractor's performance in fulfilling the technical requirements specified. Program and Project Managers (P/PMs) Responsible for performing program and project management activities and functions in developing accurate government requirements, defining measurable performance standards, and managing life cycle activities to ensure that intended outcomes are achieved.

Introduction Background and Purpose Definition The Risk Management Framework (RMF) RMF Governance Laws, Regulations, and Directives FISMA Overview and Updated FISMA Regulations RMF Overview and Life Cycle RMF Overview, Six Implementation Steps, and Applicability to the Acquisition Process Agenda

Introduction Background and Purpose Integrating information security into system acquisition requires a carefully coordinated set of activities to ensure that fundamental requirements for information security, privacy, and risk are addressed, managed, and efficiently implemented. In response to the need for agencies to develop an organization-wide approach for managing risk, the National Institute of Standards and Technology (NIST) developed Special Publication 800 -37 Rev. 1, Guide for Applying the Risk Management Framework to Federal Information Systems. This training will cover: § How Acquisition Professionals may address information system risk management. § The NIST SP 800 -37 Rev. 1 methodology that incorporates the Federal Information Security Modernization Act (FISMA) into the NIST security standards. § Guidance to provide a holistic approach for managing risk to an organization’s information and information system.

Defining RMF What is the Risk Management Framework? RMF – Developed by the NIST, provides a structured approach for managing risk resulting from the acquisition of information systems that supports the essential missions and business functions of organizations. NIST SP 800 -37 Rev. 1 “RMF provides a disciplined and structured process that integrates information security and risk management activities into the system development life cycle. ”

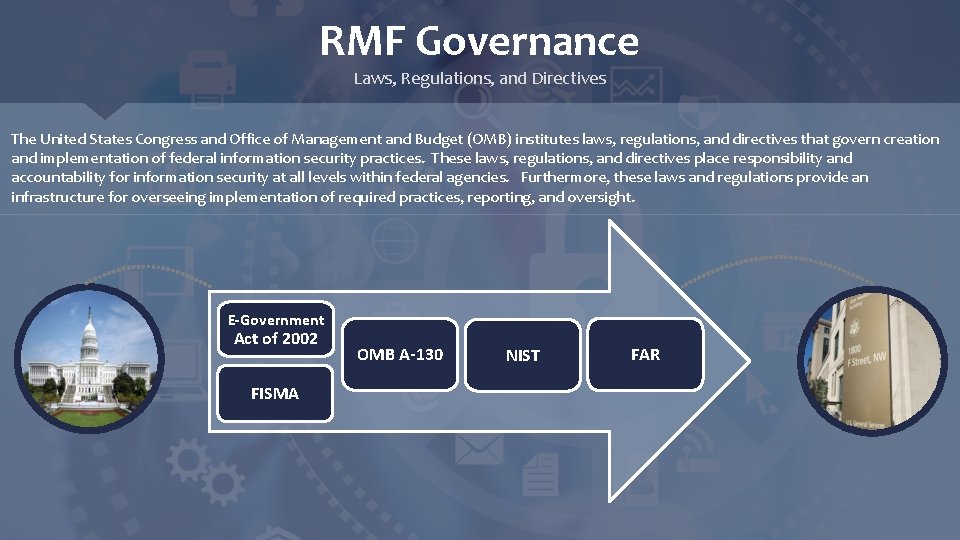
RMF Governance Laws, Regulations, and Directives The United States Congress and Office of Management and Budget (OMB) institutes laws, regulations, and directives that govern creation and implementation of federal information security practices. These laws, regulations, and directives place responsibility and accountability for information security at all levels within federal agencies. Furthermore, these laws and regulations provide an infrastructure for overseeing implementation of required practices, reporting, and oversight. E-Government Act of 2002 FISMA OMB A-130 NIST FAR

RMF Governance E-Government Act of 2002 & Federal Information Security Modernization Act The E-Government Act of 2002 ü The E-Government Act is a Federal law created to improve the methods by which government information, including information on the Internet, is organized, preserved, and made accessible to the public. Federal Information Security Management Act ü FISMA is part of the larger E-Government Act of 2002 (i. e. , Title III) introduced to improve the management of electronic government services and processes. ü FISMA is a United States federal law passed in 2002 that made it a requirement for federal agencies to develop, document, and implement an information security and protection program.

Federal Information Security Management Act (FISMA) Overview of Requirements under FISMA 2002 FISMA was originally passed on 17 December 2002 to provide a framework for the development and maintenance of minimum security controls to protect federal information systems. FISMA charged the Director of the OMB with oversight of agency information security policies and practices. § FISMA requires federal organizations to: Provide information security protections commensurate with the assessed risk. Ensure senior leaders provide information security for assets under their control. Ensure the organization has trained personnel to assist in complying with FISMA and related polices. Ensure the Chief Information Officer (CIO) reports annually on the effectiveness of the organization’s information security program. ü Develop, document, and implement an information security program. ü Develop and maintain an inventory of information systems under the control of the organization. ü ü

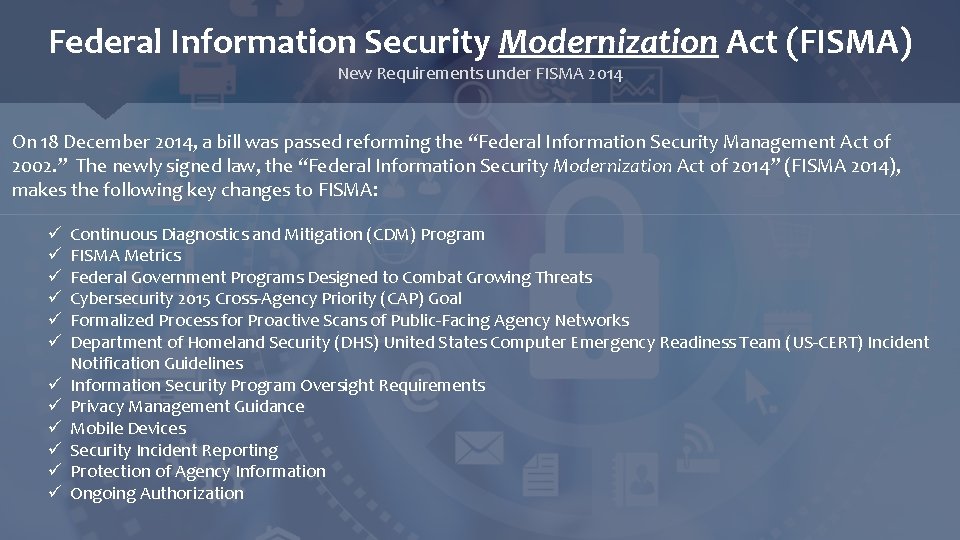
Federal Information Security Modernization Act (FISMA) New Requirements under FISMA 2014 On 18 December 2014, a bill was passed reforming the “Federal Information Security Management Act of 2002. ” The newly signed law, the “Federal Information Security Modernization Act of 2014” (FISMA 2014), makes the following key changes to FISMA: ü ü ü Continuous Diagnostics and Mitigation (CDM) Program FISMA Metrics Federal Government Programs Designed to Combat Growing Threats Cybersecurity 2015 Cross-Agency Priority (CAP) Goal Formalized Process for Proactive Scans of Public-Facing Agency Networks Department of Homeland Security (DHS) United States Computer Emergency Readiness Team (US-CERT) Incident Notification Guidelines Information Security Program Oversight Requirements Privacy Management Guidance Mobile Devices Security Incident Reporting Protection of Agency Information Ongoing Authorization

RMF Governance OMB Circular A-130 OMB is the business division of the Executive Office of the President of the United States that administers the United States federal budget and oversees the performance of federal agencies. OMB through Circular A-130, “Managing Federal Information as a Strategic Resource” establishes a minimum set of security controls to be included in information security programs, and assigns agency responsibilities for the security of federal information systems. OMB Circular A-130 requires federal agencies to: ü Plan for the security of federal information systems. ü Periodically review the security controls in their systems. ü Authorize system processing prior to operations and, periodically, thereafter. ü Ensure that appropriate officials are assigned security responsibility.

RMF Governance National Institute of Standards and Technology In accordance with FISMA, NIST is responsible for “developing standards, guidelines, and associated methods and techniques” for implementing and maintaining information security programs for risk management of information systems used or operated by an agency or contractor, excluding national security systems. There are four (4) types of NIST information security publications available: 1. Federal Information Processing Standard (FIPS) – Mandatory standards to be used by all federal agencies. 2. Special Publications (SPs) – Information security guidelines, recommendations, and reference materials. 3. NIST Interagency Reports (NISTIRs) – Research publication of a technical nature of interest to a specialized audience. 4. Information Technology Laboratory (ITL) Bulletins – Monthly publication focusing on a single topic of significant interest to the computer security community.

RMF Governance National Institute of Standards and Technology In accordance with OMB policy, for each of the six (6) steps of the RMF, NIST has developed standards and guidance to enable organizations to effectively apply the framework to the information systems supporting an organization’s mission and business process. § § § § FIPS Publication 199 (Categorize) NIST SP 800 -60 (Categorize) FIPS Publication 200 (Select) NIST SP 800 -53 (Select) NIST SP 800 Series (Implement) NIST SP 800 -53 A (Assess/Monitor) NIST SP 800 -37 (Authorize) NIST SP 800 -137 (Monitor) The above SPs should be used in conjunction with other NIST SPs that focus on procurement of information technology (IT) systems, including NIST SP 800 -64 Rev. 2, Security Considerations in the System Development Life Cycle, and NIST SP 800 -36, Guide to Selecting Information Technology Security Products. Note: Many other FIPS and NIST Special Publications provide security standards and guidance supporting FISMA legislation.

RMF Governance Laws, Regulations, and Directives Federal Acquisition Regulation (FAR) – The body of laws that govern the United States federal government’s procurement process. The FAR provides the following instruction: ü Governs the “acquisition process” by which executive agencies of the United States federal government acquire (i. e. , purchase or lease) goods and services by contract with appropriated funds. ü Mandates that agency planners for information technology acquisitions comply with FISMA and OMB Circular A-130 security requirements, resulting in the implementation of RMF. ü Directs that agencies acquiring information technology include the appropriate information technology security policies and requirements, including use of common security configurations available from NIST.

RMF Overview of the Risk Management Framework § Through implementation of the RMF, federal agencies can achieve compliance with FISMA, OMB Circular A 130, and other policies and directives. § RMF is the unified information security framework for the entire federal government. § Risk Management objectives take place throughout the system development life cycle and are critical in shaping the security capabilities of the information system.

RMF Overview of the Risk Management Framework § To integrate the risk management process throughout the organization, a three-tiered approach is employed that addresses risk at the: (1) Organization Level; (2) Mission/Business Process Level; and (3) Information System Level. 1. Organization Level – Senior leadership is responsible for providing the strategic vision, top-level goals, and objectives for the organization. 2. Mission/Business Process Level – Mid-level management is responsible for the planning and management of projects. 3. Information Systems Level – Comprised of individuals on the front lines who are developing, implementing, and operating the systems that support the organization’s core mission and business processes.

RMF Overview of the Risk Management Framework § The RMF has the following characteristics: Ø Promotes the concept of near real-time risk management and ongoing information system authorization through the implementation of robust continuous monitoring processes. Ø Encourages the use of automation to provide senior leaders the necessary information to make costeffective, risk-based decisions. Ø Integrates information security into the enterprise architecture and system development life cycle. Ø Provides emphasis on the selection, implementation, assessment, and monitoring of security controls; and the authorization of information systems. Ø Establishes responsibility and accountability for security controls deployed within organizational information systems.

RMF has emerged as a solution to bridge the gap between industry and government acquisitions, and provides a more effective way to connect cyber requirements to the contract level. In accordance with Part 39 of the FAR, when acquiring information technology, agencies must consider security of resources, protection of privacy, national security, and emergency preparedness. Integrating RMF into Information System Acquisitions Contracting Officers must understand program Cybersecurity requirements and Cybersecurity risks to: § Select the appropriate contract type. § Assure that sufficient security resources are included and identified within the contract. Organizations must provide documentation sufficient to demonstrate its systematic ability to provide IT solutions that include appropriate security safeguards for federal information.

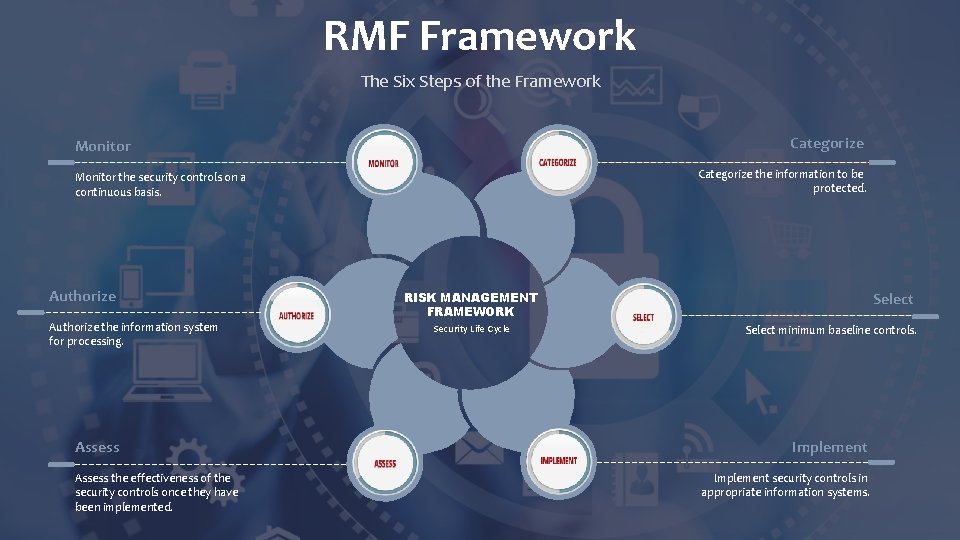
RMF Framework The Six Steps of the Framework Categorize Monitor Categorize the information to be protected. Monitor the security controls on a continuous basis. Authorize the information system for processing. Assess the effectiveness of the security controls once they have been implemented. RISK MANAGEMENT FRAMEWORK Security Life Cycle Select minimum baseline controls. Implement security controls in appropriate information systems.

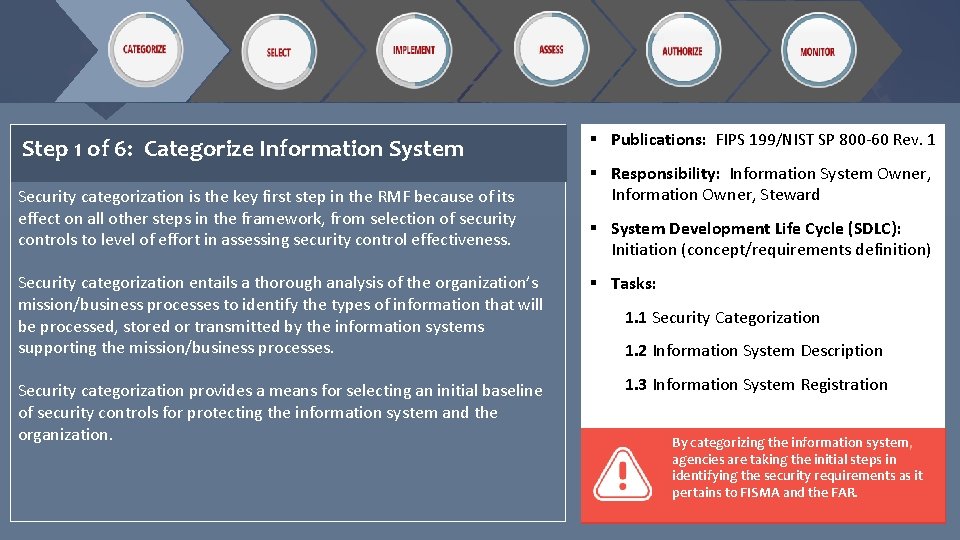
Step 1 of 6: Categorize Information System Security categorization is the key first step in the RMF because of its effect on all other steps in the framework, from selection of security controls to level of effort in assessing security control effectiveness. Security categorization entails a thorough analysis of the organization’s mission/business processes to identify the types of information that will be processed, stored or transmitted by the information systems supporting the mission/business processes. Security categorization provides a means for selecting an initial baseline of security controls for protecting the information system and the organization. § Publications: FIPS 199/NIST SP 800 -60 Rev. 1 § Responsibility: Information System Owner, Information Owner, Steward § System Development Life Cycle (SDLC): Initiation (concept/requirements definition) § Tasks: 1. 1 Security Categorization 1. 2 Information System Description 1. 3 Information System Registration By categorizing the information system, agencies are taking the initial steps in identifying the security requirements as it pertains to FISMA and the FAR.

Step 2 of 6: Select Security Controls The purpose of Step 2, the Select Step, is to specify appropriate security controls to meet the minimum security requirements as defined by the General Services Administration (GSA) baseline configuration standards and to ensure the integrity, confidentiality, and availability of the information and information system in accordance with the organization’s protection strategy. The security control selection process includes activities designed to determine the required controls that will be implemented to reduce threats and manage risks from operating the organization’s information systems. § Publications: FIPS 200/NIST SP 800 -53 Rev. 4 § Responsibility: Chief Information Officer or Senior Information Security Officer, Information Security Architect, Common Control Provider, Information System Owner, Authorizing Official, Designated Representative. § SDLC: Initiation (concept/requirements definition) § Tasks: 2. 1 Common Control Identification 2. 2 Security Control Selection 2. 3 Monitoring Strategy 2. 4 Security Plan Approval Selecting the appropriate security controls ensures the information systems design and configuration is compliant and commensurate with the information security objectives identified within the contract.

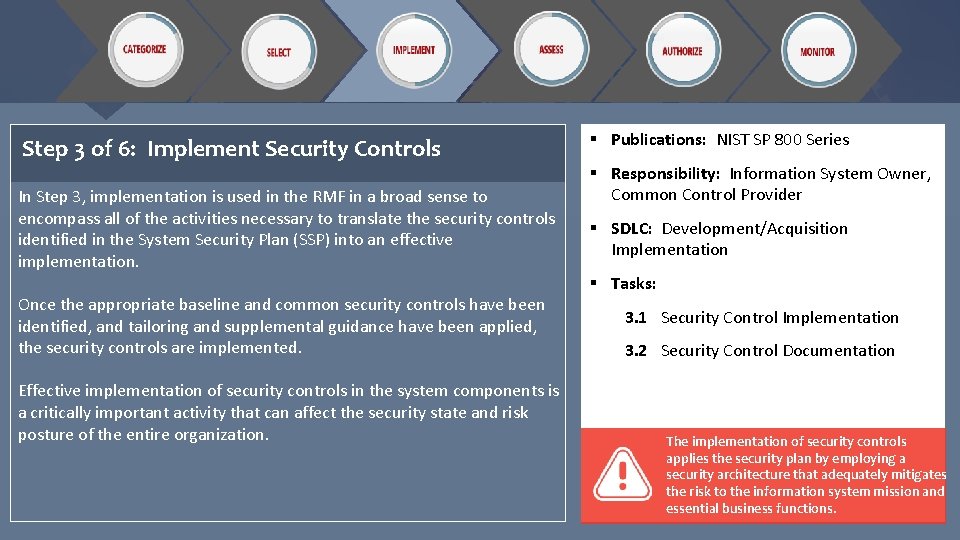
Step 3 of 6: Implement Security Controls In Step 3, implementation is used in the RMF in a broad sense to encompass all of the activities necessary to translate the security controls identified in the System Security Plan (SSP) into an effective implementation. Once the appropriate baseline and common security controls have been identified, and tailoring and supplemental guidance have been applied, the security controls are implemented. Effective implementation of security controls in the system components is a critically important activity that can affect the security state and risk posture of the entire organization. § Publications: NIST SP 800 Series § Responsibility: Information System Owner, Common Control Provider § SDLC: Development/Acquisition Implementation § Tasks: 3. 1 Security Control Implementation 3. 2 Security Control Documentation The implementation of security controls applies the security plan by employing a security architecture that adequately mitigates the risk to the information system mission and essential business functions.

Step 4 of 6: Assess Security Controls Step 4 in the RMF is to assess. Once security controls are implemented, they should be assessed for effectiveness. Security control assessment is a process employed by an organization to review the management, operational, and technical security controls in an information system. The assessment determines the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system. The Security Control Assessor (SCA) will develop, review, and approve a Security Assessment Plan (SAP) to assess the security controls. The plan will ensure assessment activities are coordinated for interoperability and identify appropriate procedures to assess those controls. The Authorizing Official (AO) approves the Security Assessment Plan. § Publications: NIST SP 800 -53 A Rev. 4 § Responsibility: Information System Owner, Common Control Provider, Security Control Assessor § SDLC: Development/Acquisition Implementation § Tasks: 4. 1 Assessment Preparation 4. 2 Security Control Assessment 4. 3 Security Assessment Report 4. 4 Remediation Actions The security control assessment validates the system compliance with functional security requirements and ensures appropriate security standards are incorporated.

Step 5 of 6: Authorize Information Systems Step 5, security authorization, is the official management decision of a senior organizational official to authorize operation of an information system and to explicitly accept the risk to organizational operations and assets, individuals, other organizations, and the Nation based on the implementation of an agreed-upon set of security controls. The Security Assessment Plan completed in RMF Step 4 provides AOs with the information needed for understanding the current security state of the organization’s information systems and supporting infrastructure, and the current risk posture of the organization. Security authorization requires managers at all levels to implement the appropriate security controls for the information system, given: • • • Mission/business requirements Technical constraints Operational constraints Cost/schedule constraints Risk-related considerations When performing security authorization activities, the level of effort, resources expended, and actions taken should be commensurate with the security category of the information system. § Publications: NIST SP 800 -37 Rev. 1 § Responsibility: Information System Owner, Common Control Provider, Authorizing Official or Designated Representative § SDLC: Implementation § Tasks: 5. 1 Plan of Action and Milestones 5. 2 Security Authorization Package 5. 3 Risk Determination 5. 4 Risk Acceptance Authorization of the information system confirms that the Cybersecurity risk was appropriately evaluated, mitigated, and accepted by the Authorizing Official; with this acceptance, the system is authorized to operate and is compliant with the FAR.

Step 6 of 6: Monitor Security Controls § Publications: NIST SP 800 -53 A Rev. 4, NIST SP 800 -137 The final step, Step 6, is a critical aspect of the security authorization process. It is the post-authorization period involving the continuous monitoring of an information system’s security controls, which includes analyzing and documenting any proposed or actual changes to the information system or its environment of operation. § Responsibility: Information System Owner, Information system monitoring activities are most effective when integrated into the broader life cycle management processes carried out by the organization and not executed as stand-alone, security-centric activities. The ultimate objective of the continuous monitoring program is to determine if the security controls in the information system continue to be effective over time in light of the inevitable changes to hardware, software, and firmware that occur in the system, as well as changes in the environment in which the system operates. Common Control Provider, Authorizing Official § SDLC: Operation/Maintenance § Tasks: 6. 1 6. 2 6. 3 6. 4 6. 5 6. 6 6. 7 System and Environment Changes Ongoing Security Control Assessments Ongoing Remediation Actions Key Updates Security Status Reporting Ongoing Risk Determination and Acceptance System Decommissioning Contracts must identify adequate resources for the continuous collection and evaluation of risk-based assessment data to enforce continuous monitoring.

When acquiring information technology, agencies shall comply with the appropriate information technology security policies and requirements, including use of common security configurations available from NIST. Contracting Officers should consider the rapidly changing nature of information technology through market research and the application of technology refreshment techniques. When acquiring information systems, agencies may procure only certified software, hardware, and applications that are identified on their agency’s approved product list. Integrating RMF into Information System Acquisitions In accordance with the FAR Section 39. 101, contracting and program office officials are jointly responsible for assessing, monitoring, and controlling risk when selecting projects for investment and during program implementation. Appropriate techniques should be applied to manage and mitigate risk during the acquisition of information technology. Techniques include, but are not limited to: continuous collection and evaluation of risk-based assessment data; prototyping prior to implementation; post implementation reviews to determine actual project cost, benefits and returns; and focusing on risks and returns using quantifiable measures.

Essential Awareness Items For Contracting Officers In regard to information system acquisition, Contracting Officers are engaged at a high level and must be aware of all policies, rules, and regulations so that contracts reflect the mandated security requirements for information systems including, but not limited to, OMB Circular A-130, FISMA, and the FAR. Important Questions to Ask: • Is the system new or already created and/or established? • Are the system point of contacts (POC) identified? • What is the system categorization? • Does the system process personally identifiable information (PII) or protected health information (PHI)? • Is the system inventory up-to-date? • What is the Authorization to Operation (ATO) status and or conditions?

Essential Awareness Items For Program and Project Managers In regard to information system acquisition, Program and Project Managers are engaged at a high level and must be aware of all policies, rules, and regulations so that information systems are managed effectively to ensure compliance with the mandated security requirements including, but not limited to, OMB Circular A-130, FISMA, and the FAR. Key Awareness Items: ü Ensure to assign qualified personnel to RMF roles and document team member assignments in the SSP. ü Ensure the Information Systems Security Manager (ISSM)/Information Systems Security Officer (ISSO) categorizes the information system based on the impact due to a loss of confidentiality, integrity, and availability of the information or information system according to information provided by the Information Owner. ü Ensure the ISSM documents the description, including the system/authorization boundary in the SSP. ü Ensure the ISSM, after the initial assessment, conducts remediation actions based on the findings and recommendations in the Plan of Action and Milestones (POA&M). ü Ensure the ISSM (and ISSO, as appropriate) develops a strategy for continuous monitoring of security control effectiveness.

Conclusion The End Risk management is critical in procuring secure information systems so that agencies are able to achieve their mission and goals. Because of the severity of the security threats faced by organizations today, information security legislation has been enacted to provide regulations and guidance for implementing information security safeguards for federal information systems. To that end, NIST developed the Risk Management Framework that delineates a multistep process for categorizing systems and for selecting, implementing, and assessing security controls; as well as authorizing systems for operation, and monitoring security controls through the life cycle of an information system. There is great benefit to be obtained in reducing risk from procuring information systems by integrating Cybersecurity into the acquisition programs to ensure resilient systems.

Questions & Answers What would you like clarification on?

THANK YOU Thank you for attending this training session. Going forward, we hope you are able to utilize aspects of the program which were of particular benefit to your day-to-day work. We look forward to seeing you at our next session. Please feel free to share any comments you may wish to make about this or any future programs.

Contact Information For more information regarding RMF activities or to learn more about the recommended security practices for ITC, contact Shon Lyublanovits (shondrea. lyublanovits@gsa. gov).