Data Risk Management Framework Data Risk Management Framework


- Slides: 6

Data Risk Management Framework

Data Risk Management Framework Agenda Objectives Overview Artifact Review Practical Examples Q & A

Data Risk Management Framework Introduction What • The Data Risk Management Framework (DRMF) is a an open-source framework designed to provide organizations accurate line of sight into data risk management capabilities. • It is not a compliance framework. How • The DRMF uses a structured and strategic approach the maps efficiencies across governance, operational and technical initiatives. • The framework deconstructs data risk management into logical control areas and supporting sub-controls. • This offering fulfills an underserved need for organizations. Why • Organizations are failing to holistically address data security needs. • Data is the currency of modern business.

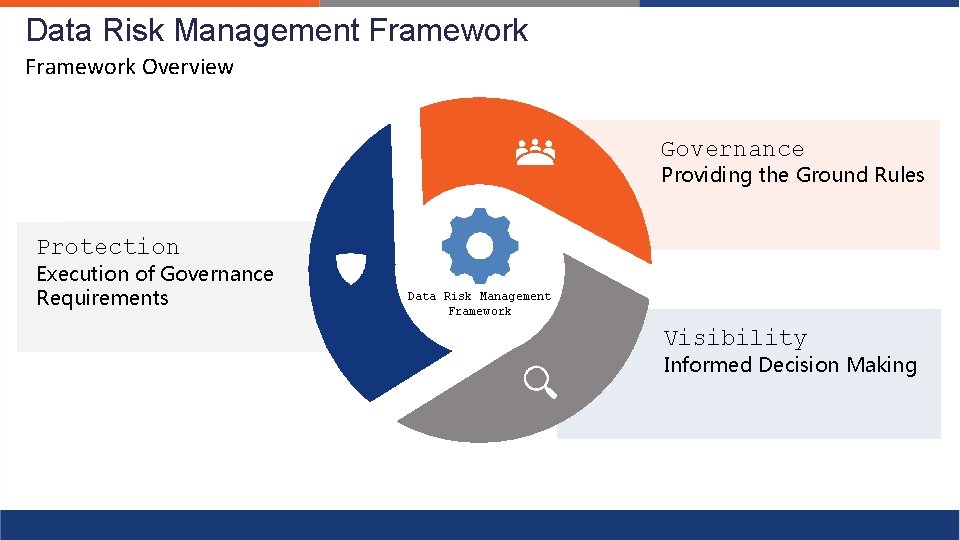
Data Risk Management Framework Overview Governance Providing the Ground Rules Protection Execution of Governance Requirements Data Risk Management Framework Visibility Informed Decision Making

DRMF – Key Drivers Industry Drivers • Current approaches to managing data risk aren’t working – they’re siloed, industry-specific, and not comprehensive. • Organizations are focusing on compliance, and they don’t know how to achieve true data risk resilience. • Organizations spend most of their time and resources on infrastructure and threat protection, not data security. • The DRMF can help organizations prioritize efforts and maximize the value of their existing portfolio of security solutions (as well as guide procurement for new tools). Benefits • Strategic approach versus fire fighting and tool buying. • Root cause analysis of organizational gaps. • A logical method for aligning security programs with organizational guidance. • Intelligent use of resources. • Outputs that are understood by business and security leadership.

Questions and Feedback