ISSA NOVA SIG Risk Management Framework Life Boat

ISSA – NOVA SIG Risk Management Framework Life. Boat Meetup “A Field Guide to Using the Risk Management Framework” RMF 11 Jun 2016

RMF Life. Boat Meetup • RMF Life. Boat Meetup members are requested to encourage and help each other at their discretion • Build our RMF expertise by studying NIST RMF material before the free Life. Boat meetings • Meet some Saturdays 11 am-1 pm in a private room at the Olive Garden in Vienna, VA • Decide WHAT to study ahead and WHEN we will next meet at the close of each session. • Follow-up meeting announcements at URL: http: //www. meetup. com/NCR-Risk. Management-Framework-Lifeboat – Do sign-up for subsequent meetings 2

Introduce Yourself • How did you get into Cyber Security? • What brought you here today? • What can you contribute to the group? 3

Agenda 11 June, 2016 • Definitons • Previous Meeting Presentation Highlight: – “A Field Guide to Using the Risk Management Framework – Background & Step 1” by John Brown (ISSO) • Current Presentation: – “A Field Guide to Using the Risk Management Framework – Continued…” by John Brown (ISSO) • Future Topics Selection 4

Definitions • The RMF provides a disciplined and structured process that combines information system security and risk management activities into the system development life cycle and authorizes their use for an enterprise. • The RMF changes the traditional focus of C&A as a static, procedural activity to a more dynamic approach that provides the capability to more effectively manage information systemrelated security risks in diverse environments of complex and sophisticated cyber threats and ever-increasing system vulnerabilities. RMF Knowledge Service 5

Definitions • Vulnerability – Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source. • Threat – The potential for a threat-source to successfully exploit a particular information system vulnerability. • Threat Source – Synonymous with Threat Agent. • Likelihood: The probability that a given threat is capable of exploiting a given vulnerability. • Risk: Resulting from the operation of an information system given the potential impact of a threat and the likelihood of that threat occurring. FIPS 200 6
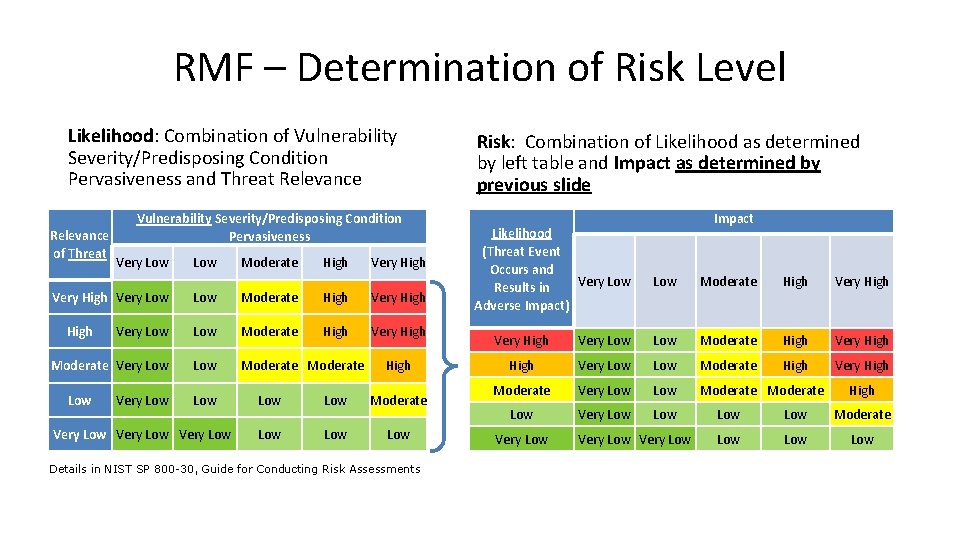
RMF – Determination of Risk Level Likelihood: Combination of Vulnerability Severity/Predisposing Condition Pervasiveness and Threat Relevance of Threat Vulnerability Severity/Predisposing Condition Pervasiveness Very Low Very High Very Low Moderate High Very High Low Moderate High Very High Moderate Very Low Moderate High Low Very Low High Low Moderate Low Low Details in NIST SP 800 -30, Guide for Conducting Risk Assessments Risk: Combination of Likelihood as determined by left table and Impact as determined by previous slide Likelihood (Threat Event Occurs and Very Low Results in Adverse Impact) Impact Low Moderate High Very Low Low Moderate High Very High Moderate Very Low Moderate Low Very Low High Low Moderate Low Low

Current Presentation “A Field Guide to Using the Risk Management Framework” By John Brown (ISSO) Ø John Brown’s Information Technology career spans 40+ years. Over the course of that time he held many job titles. He remains passionate about each career experience. He is now an independent consultant performing duties as an Information System Security Officer (ISSO). One of his proudest achievements was winning the ISSO of the year award for all of DHS. He won that award while taking on one of the hardest challenges at Transportation Security Administration (TSA). He earned his cherished DHS award as the TSA ISSO for the network infrastructure and an integral participant consolidating datacenters into the brand new DHS mega center. John always works tirelessly to bridge the gap between operations and security compliance. Ø John contributed and built his ISSO expertise at several government agencies including USDA, USSS, NGB and the VA. He honed his skills utilizing the NIST Risk Management Framework at these agencies. John wrote numerous security plans, Contingency Plans, Business Impact Assessments, Security Assessment Reports, and POA&Ms. He has been able to obtain a coveted Authority to Operate (ATO) for most systems he worked on. Ø John has also spent 20+ years in the performance management, modeling and simulation field on a vendor team supporting tool deployment and consulting. He started as a programmer then systems analyst. He considers himself more of a generalist because of this varied background. 8

Future Topics Selection 1. Continue with RMF Steps 2. Finding the Threat inside the network 3. Threat Modeling - Elevation of Privilege (Eo. P) Threat Modeling Card Game • Date of next meeting 9

End of Slides 11 June 2016 10
Current Cyber Event – Ransomware, The future Cyber Black Swan Event? Recent “Malicious Virus” Med Star Timeline • Early Monday morning, shut down its email and vast records database • Stated “Med. Star acted quickly with a decision to take down all system interfaces to prevent the virus from spreading throughout the organization, ” • Pop-ups on computer screens stating that they had been infected by a virus and asking for ransom in Bit. Coins. Emails notifications asking for Bit. Coin payments also reported. • Revert to seldom-used paper charts and records. “Everything will be slowed down tremendously. ” “It’s huge. ” 11

Timeline continue • Mid-week was able restore majority of services, but many individual work stations remain offline. • “The system may be working, but if no one can access it, what use is that? ” National Nurses United representative Stephen Frum • Med Star $18, 100 ransom compare to $17, 000 paid by LA Hollywood Presbyterian Med Center on Feb 5, 2106 12

Post Attack Analysis • Typical ransomware can infect a computer if the recipient clicks a dangerous link or downloads material masquerading as a benign attachment. • "When they are attacked they usually see a countdown screen, a clock counting down the time they have until the offer expires and their data is deleted, " • Cyber. Wire reports it was a “a server-side Samsam infection” ransomware variant – Also known as MSIL, Samas – FBI has been warning US businesses about through several alerts sent out in the last two months – Unlike with previous ransomware, this one is selfsufficient. “Once installed on a machine there is no beaconing or C 2 activity” 13
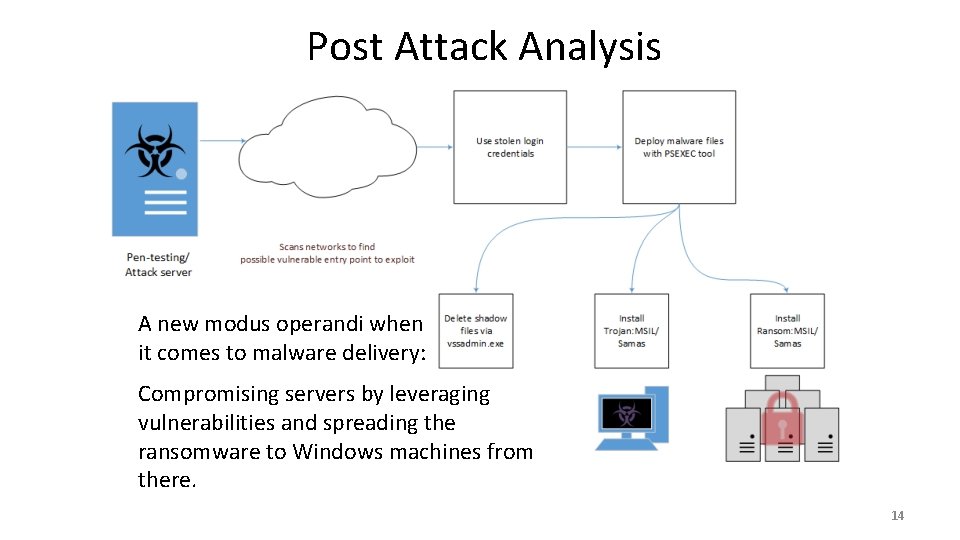
Post Attack Analysis A new modus operandi when it comes to malware delivery: Compromising servers by leveraging vulnerabilities and spreading the ransomware to Windows machines from there. 14

It is “currently” all about the money!!! • Special Agent Chris Stangl, a section chief at the FBI’s cyber division, said in a recent interview that ransomware attacks are becoming increasingly prevalent as more and more victims pay up. In a ninemonth period in 2014, the FBI investigated 1, 838 complaints of such attacks, which cost those targeted more than $23. 7 million. In 2015, agents investigated 2, 453 complaints, costing targets $24. 1 million. • Why Hold Hospitals Ransom? – "Willie" Sutton, a prolific American bank robber, replied to a reporter’s question why he robbed banks, "Because that's where the money is. " – Single victim with deep financial pockets – Time sensitive patient records • Huge confidence and financial impact 15

Future of Ransomware? • Targeting Businesses – Law firm client data—especially merger-and-acquisition data • Ransomware: How Hackers Are Shaking Down Police Departments – Some Maine police agencies reported having to pay ransom to hackers in order to keep their files. – In Tewksbury, Massachusetts the police chief said he paid a $500 bounty to get back the department's data. • Same tools and techniques can be used for other purposes! 16

Counter Measures • Easy actions: – Up to date anti-virus and current patching – Backing of critical data in multiple locations • “A Notional Framework for applying Antifragile thinking” 17

End of Slides 2 Apr 2016 18
![Recent Phishing Email -----Original Message----From: e. Pay. Pal [mailto: info@steaua. com] Sent: Friday, January Recent Phishing Email -----Original Message----From: e. Pay. Pal [mailto: info@steaua. com] Sent: Friday, January](http://slidetodoc.com/presentation_image/43df73323cf2717d4a42e6588ac50c1e/image-19.jpg)
Recent Phishing Email -----Original Message----From: e. Pay. Pal [mailto: info@steaua. com] Sent: Friday, January 29, 2016 2: 12 PM To: undisclosed-recipients: Subject: [SPAM]Important Account information. Last warning ! Important information: We regret to inform you that we’re initiating the closure of your Pay. Pal account because of certain activity that took place relating to your account. This measure is necessary to protect us from potential financial losses. In addition, your related e. Bay account will remain closed due to this current Pay. Pal action. This is your last warning ! We haven't been able to verify your identity using the information you provided, so we need some additional documentation from you. Please log in to your Pay. Pal account: http: //yhhbvalve. com/js/the. Onlice. Pay. Pal. Resolution. Center/avoid. Pay. Pal. Account. Closu re/logintoyour. Pay. Palaccount/PPlog. In. html To remove your account limitations you may need one of these Debit Cards: * 5581 -588 X-XXXX * 5311 -06 XX-XXXX. 19

Root Site -- http: //yhhbvalve. com/ 20
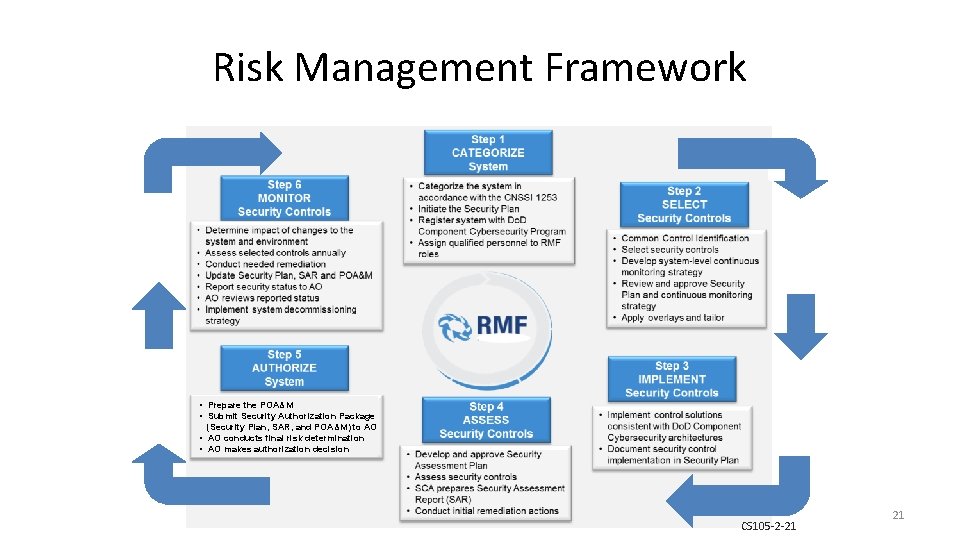
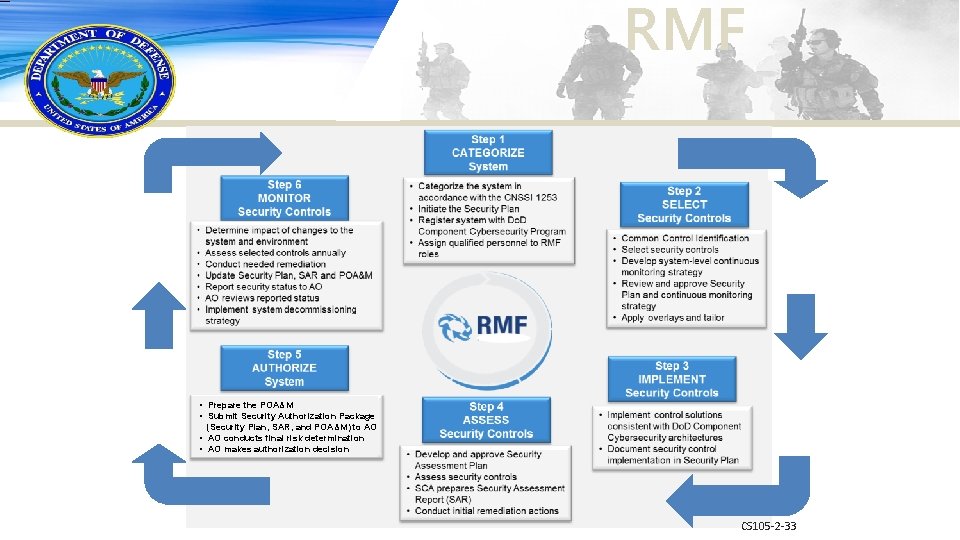
Risk Management Framework • Prepare the POA&M • Submit Security Authorization Package (Security Plan, SAR, and POA&M) to AO • AO conducts final risk determination • AO makes authorization decision CS 105 -2 -21 21

What is “the Cloud” • NIST SP 800 -144: Guidelines on Security and Privacy in Public Cloud Computing, December 2011, 80 pgs. • NIST SP 800 -145: The NIST Definition of Cloud Computing, September 2011, 7 pgs. • NIST SP 800 -146: Cloud Computing Synopsis and Recommendations, May 2012, 81 pgs. • ITL Bulletin: Cloud Computing: A Review of Features, Benefits, Risks, and Recommendations For Secure, Efficient Implementations, June 2012, 13 pgs. • • • Chinese Love Our Uploaded Data 22
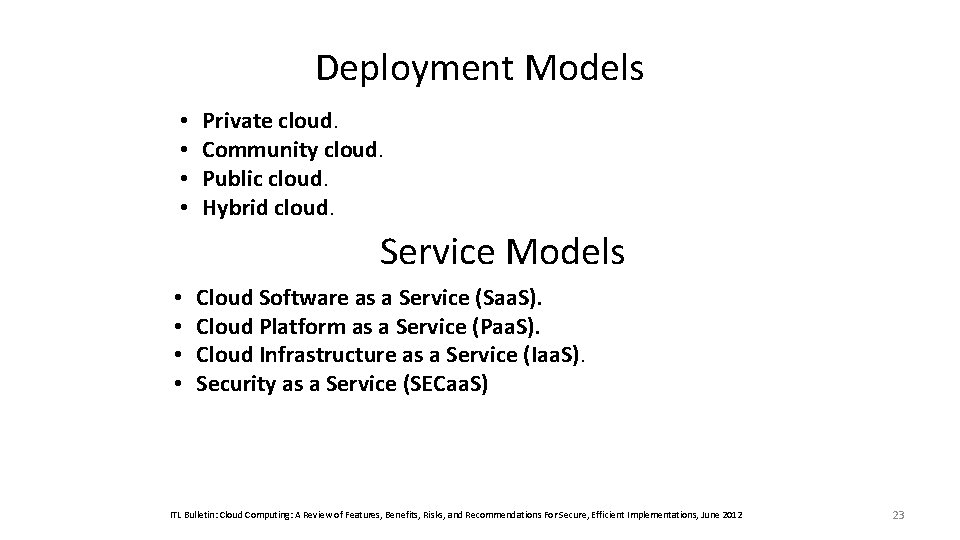
Deployment Models • • Private cloud. Community cloud. Public cloud. Hybrid cloud. Service Models • • Cloud Software as a Service (Saa. S). Cloud Platform as a Service (Paa. S). Cloud Infrastructure as a Service (Iaa. S). Security as a Service (SECaa. S) ITL Bulletin: Cloud Computing: A Review of Features, Benefits, Risks, and Recommendations For Secure, Efficient Implementations, June 2012 23

End slides 30 Jan 2016 24

Characteristics of Cloud Computing 1. With cloud computing, organizations can have on-demand self-service for computing capabilities, such as server time and network storage when needed, and through a single provider. 2. Capabilities for different platforms, such as mobile phones, laptops computers, and personal digital assistants, are available through broad network access. 3. The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. • While the location of the resources, such as storage, processing, memory, network bandwidth, and virtual machines, is not controlled by the subscriber, it may be possible for the subscriber to specify the country, state, or data center that provides the cloud services. 4. Cloud capabilities can be provided to the subscriber rapidly and elastically, allowing the subscriber to either increase or decrease services. The capabilities available often appear to be unlimited to the subscriber and can be purchased in any quantity at any time. 5. Cloud systems automatically control and optimize resource use through a measured service capability that is appropriate for the type of service provided. Resource usage can be monitored, controlled, and reported providing transparency for both the provider and the consumer of the utilized service. ITL Bulletin: Cloud Computing: A Review of Features, Benefits, Risks, and Recommendations For Secure, Efficient Implementations, June 2012 25
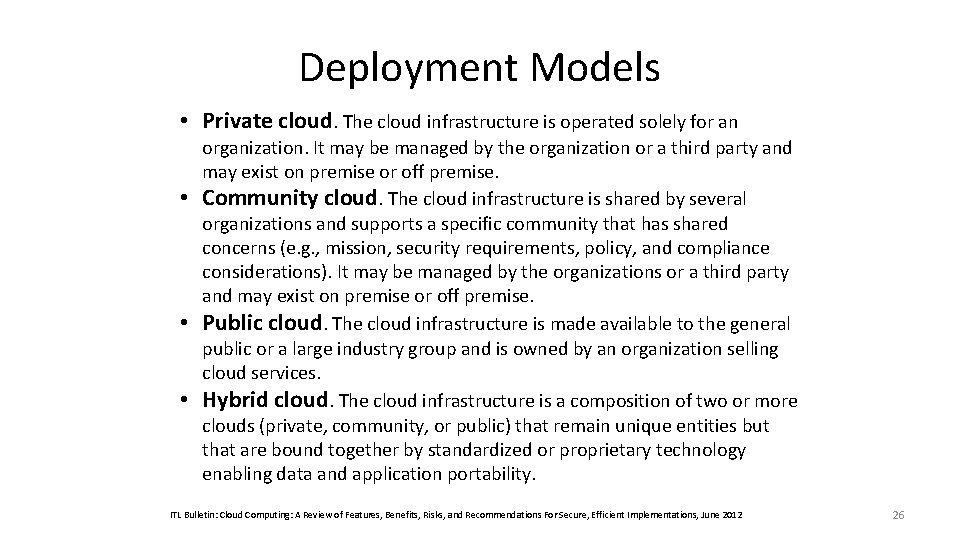
Deployment Models • Private cloud. The cloud infrastructure is operated solely for an • • • organization. It may be managed by the organization or a third party and may exist on premise or off premise. Community cloud. The cloud infrastructure is shared by several organizations and supports a specific community that has shared concerns (e. g. , mission, security requirements, policy, and compliance considerations). It may be managed by the organizations or a third party and may exist on premise or off premise. Public cloud. The cloud infrastructure is made available to the general public or a large industry group and is owned by an organization selling cloud services. Hybrid cloud. The cloud infrastructure is a composition of two or more clouds (private, community, or public) that remain unique entities but that are bound together by standardized or proprietary technology enabling data and application portability. ITL Bulletin: Cloud Computing: A Review of Features, Benefits, Risks, and Recommendations For Secure, Efficient Implementations, June 2012 26
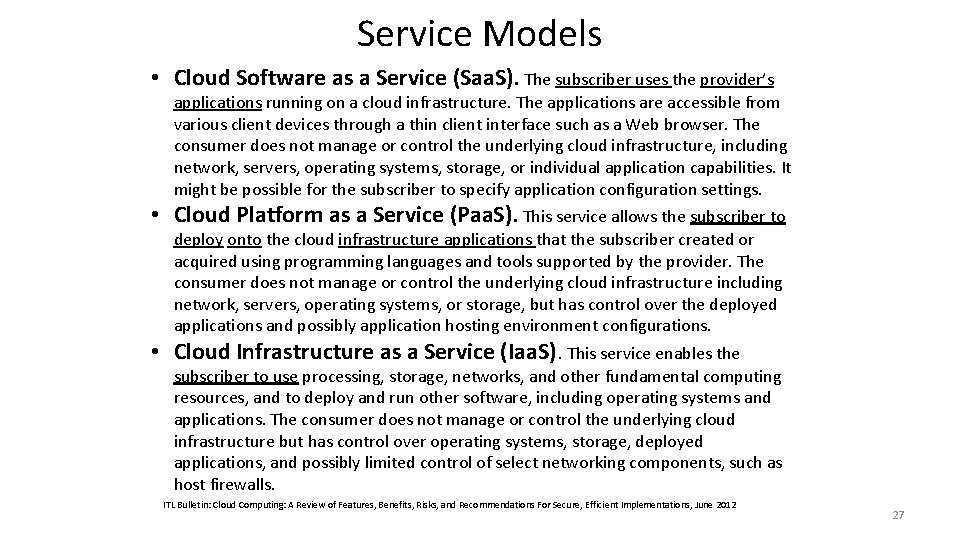
Service Models • Cloud Software as a Service (Saa. S). The subscriber uses the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through a thin client interface such as a Web browser. The consumer does not manage or control the underlying cloud infrastructure, including network, servers, operating systems, storage, or individual application capabilities. It might be possible for the subscriber to specify application configuration settings. • Cloud Platform as a Service (Paa. S). This service allows the subscriber to deploy onto the cloud infrastructure applications that the subscriber created or acquired using programming languages and tools supported by the provider. The consumer does not manage or control the underlying cloud infrastructure including network, servers, operating systems, or storage, but has control over the deployed applications and possibly application hosting environment configurations. • Cloud Infrastructure as a Service (Iaa. S). This service enables the subscriber to use processing, storage, networks, and other fundamental computing resources, and to deploy and run other software, including operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, deployed applications, and possibly limited control of select networking components, such as host firewalls. ITL Bulletin: Cloud Computing: A Review of Features, Benefits, Risks, and Recommendations For Secure, Efficient Implementations, June 2012 27
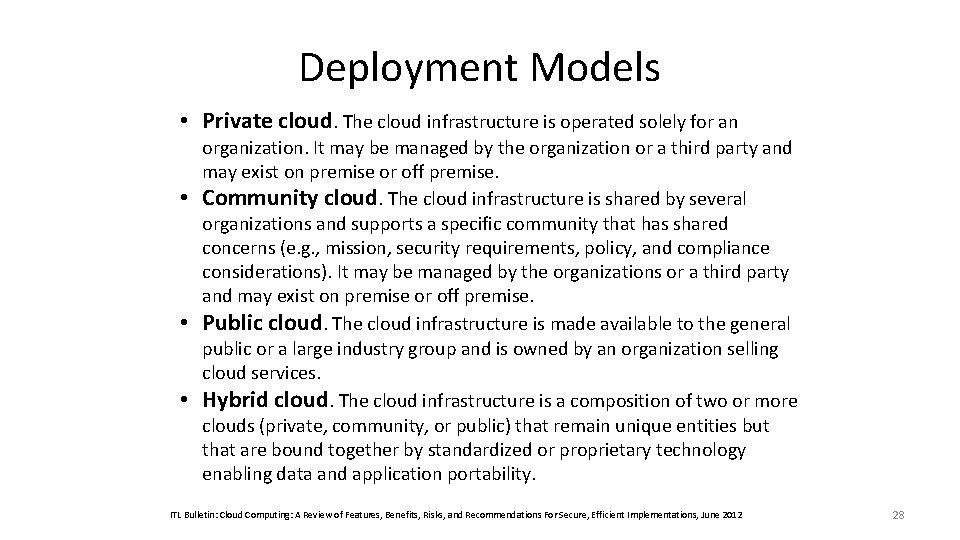
Deployment Models • Private cloud. The cloud infrastructure is operated solely for an • • • organization. It may be managed by the organization or a third party and may exist on premise or off premise. Community cloud. The cloud infrastructure is shared by several organizations and supports a specific community that has shared concerns (e. g. , mission, security requirements, policy, and compliance considerations). It may be managed by the organizations or a third party and may exist on premise or off premise. Public cloud. The cloud infrastructure is made available to the general public or a large industry group and is owned by an organization selling cloud services. Hybrid cloud. The cloud infrastructure is a composition of two or more clouds (private, community, or public) that remain unique entities but that are bound together by standardized or proprietary technology enabling data and application portability. ITL Bulletin: Cloud Computing: A Review of Features, Benefits, Risks, and Recommendations For Secure, Efficient Implementations, June 2012 28

Security as a Service (SECaa. S) • A business model in which a large service provider integrates their security services into a corporate infrastructure on a subscription basis more cost effectively than most individuals or corporations can provide on their own, when total cost of ownership is considered. • In this scenario, security is delivered as a service from the cloud, without requiring on-premises hardware avoiding substantial capital outlays. (Wikipedia) Gartner: Cloud-based security as a service set to take off • These security services often include authentication, anti-virus, anti-malware/spyware, intrusion detection, and security event management, among others. (Wikipedia) • Cloud-based single sign-on (SSO) is a benefit to employees because they don’t have to remember a lot of passwords, and it’s a plus for the IT department in password management and provisioning. 29
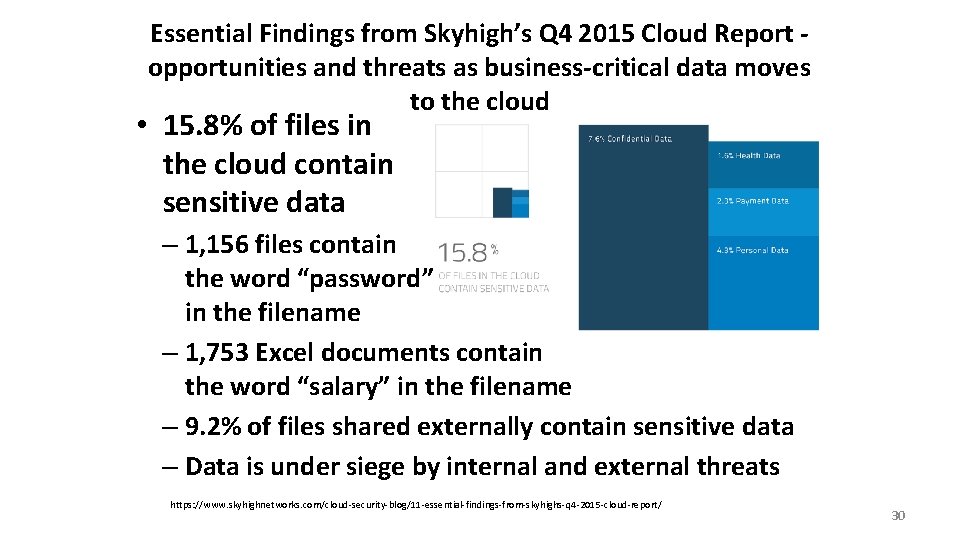
Essential Findings from Skyhigh’s Q 4 2015 Cloud Report opportunities and threats as business-critical data moves to the cloud • 15. 8% of files in the cloud contain sensitive data – 1, 156 files contain the word “password” in the filename – 1, 753 Excel documents contain the word “salary” in the filename – 9. 2% of files shared externally contain sensitive data – Data is under siege by internal and external threats https: //www. skyhighnetworks. com/cloud-security-blog/11 -essential-findings-from-skyhighs-q 4 -2015 -cloud-report/ 30

Cloud Computing Predictions For 2016 1. Hybrid Clouds Become The Next-Gen Infrastructure Foundation 2. Security Will Continue To Be A Top Concern 3. Cloud-Native Apps Become The Norm 4. Barriers To Entering The Cloud All But Disappear 5. Containers Become Mainstream (Development Speed) 6. Movement To Cloud Data Storage (For Security Purposes) 7. Io. T Becomes Relevant 8. Hyper-Converged Cloud Platforms To Keep Up With The Speed Of Growth • In 2016, a notable cloud disaster will happen with a famous enough brand. http: //www. informationweek. com/cloud/infrastructure-as-a-service/8 -cloud-computing-predictions-for-2016/d/d-id/1323598 31

Cloud Computing and Digital Forensics Cindy Faith (Neither cloud nor forensics SME) January 9, 2016 Complete Presentation in NCR RMF Lifeboat Meetup Library
RMF • Prepare the POA&M • Submit Security Authorization Package (Security Plan, SAR, and POA&M) to AO • AO conducts final risk determination • AO makes authorization decision CS 105 -2 -33
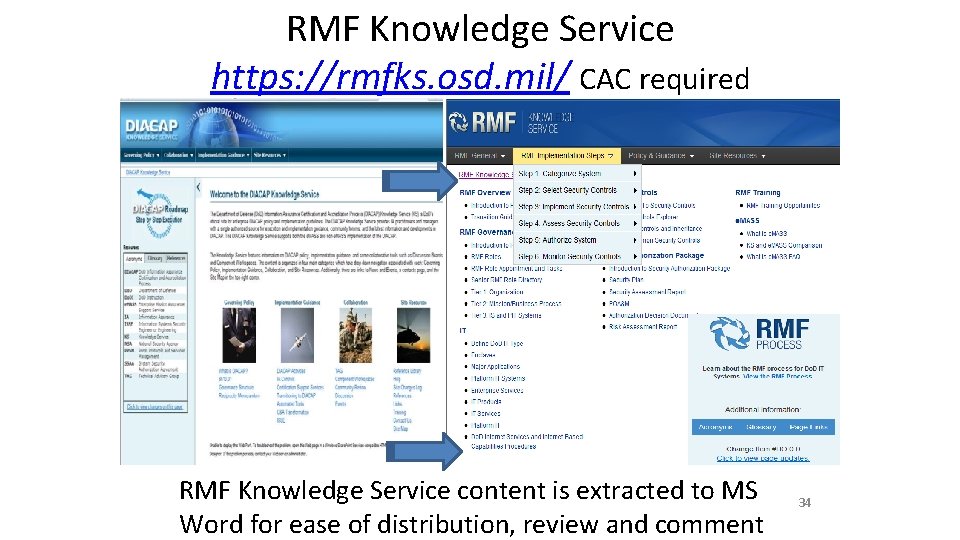
RMF Knowledge Service https: //rmfks. osd. mil/ CAC required RMF Knowledge Service content is extracted to MS Word for ease of distribution, review and comment 34

Hacking the RMF Knowledge Service (KS) • RMF KS Hacking – Become intimately familiar with RMF so that one can make recommendations for improvement – Employer Interview “noteworthy contribution” • Use “Open Source” methodology – Transferred to MS Word for ease of review and comment. Additions & Change feedback to KS. – Eventually, build offline, disk based, HTML knowledge service. 35

RMF Step 5 – Authorize System – Prepare the plan of action and milestones based on the findings and recommendations of the security assessment report excluding any remediation actions taken – Determine the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the Nation – Assemble the security authorization package and submit the package to the authorizing official. CS 105 -2 -36
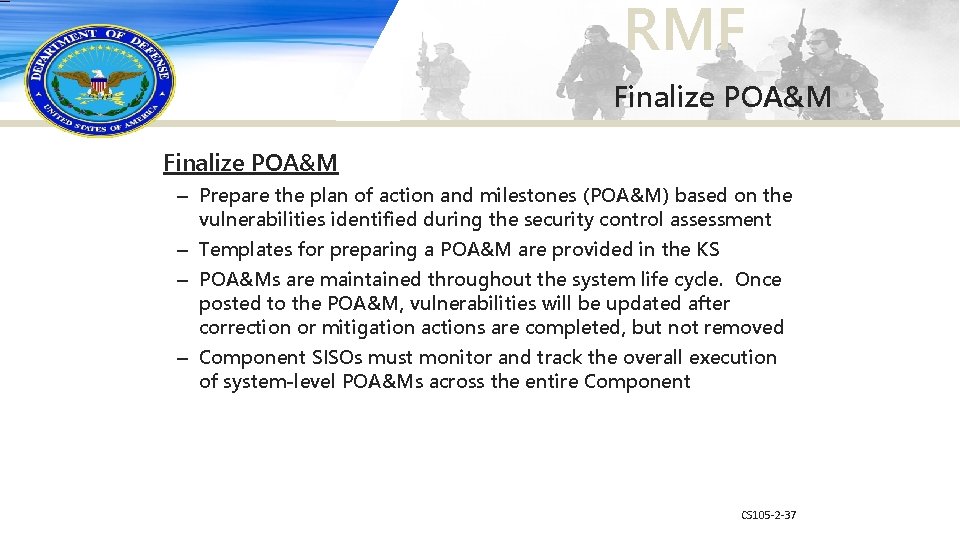
RMF Finalize POA&M – Prepare the plan of action and milestones (POA&M) based on the vulnerabilities identified during the security control assessment – Templates for preparing a POA&M are provided in the KS – POA&Ms are maintained throughout the system life cycle. Once posted to the POA&M, vulnerabilities will be updated after correction or mitigation actions are completed, but not removed – Component SISOs must monitor and track the overall execution of system-level POA&Ms across the entire Component CS 105 -2 -37
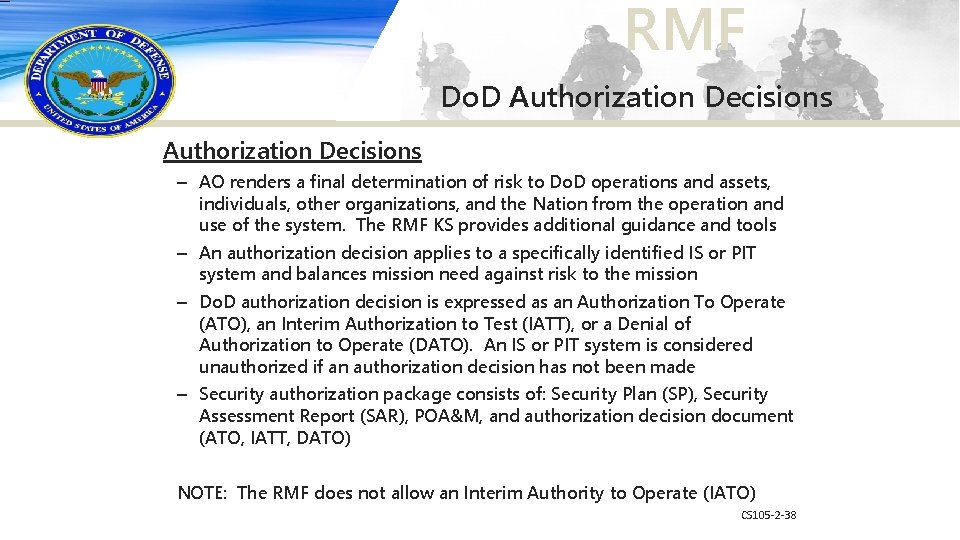
RMF Do. D Authorization Decisions – AO renders a final determination of risk to Do. D operations and assets, individuals, other organizations, and the Nation from the operation and use of the system. The RMF KS provides additional guidance and tools – An authorization decision applies to a specifically identified IS or PIT system and balances mission need against risk to the mission – Do. D authorization decision is expressed as an Authorization To Operate (ATO), an Interim Authorization to Test (IATT), or a Denial of Authorization to Operate (DATO). An IS or PIT system is considered unauthorized if an authorization decision has not been made – Security authorization package consists of: Security Plan (SP), Security Assessment Report (SAR), POA&M, and authorization decision document (ATO, IATT, DATO) NOTE: The RMF does not allow an Interim Authority to Operate (IATO) CS 105 -2 -38

RMF Do. D Authorization Decisions (Cont. ) Authorization Decision and Authorization Decision Documents – If overall risk is determined to be acceptable, and there are no NC controls with a level of risk of “Very High” or “High, ” then the authorization decision should be issued as an ATO – NC controls with a level of risk of “Very High” or “High” exist that cannot be corrected or mitigated immediately, but overall system risk is determined to be acceptable due to mission criticality, then the authorization decision should be issued as an ATO with conditions and only with permission of the responsible Do. D Component CIO – NC controls with a level of risk of “Very High” or “High” must also be reported to the Do. D ISRMC – If risk is determined to be unacceptable, the authorization decision should be issued in the form of a DATO – If the risk determination is being made to permit testing of the system in an operational information environment or with live data, and the risk is acceptable, then the authorization decision should be issued in the form of an IATT – Operation of a system under an IATT in an operational environment is for testing purposes only (i. e. , the system will not be used for operational purposes during the IATT period) CS 105 -2 -39
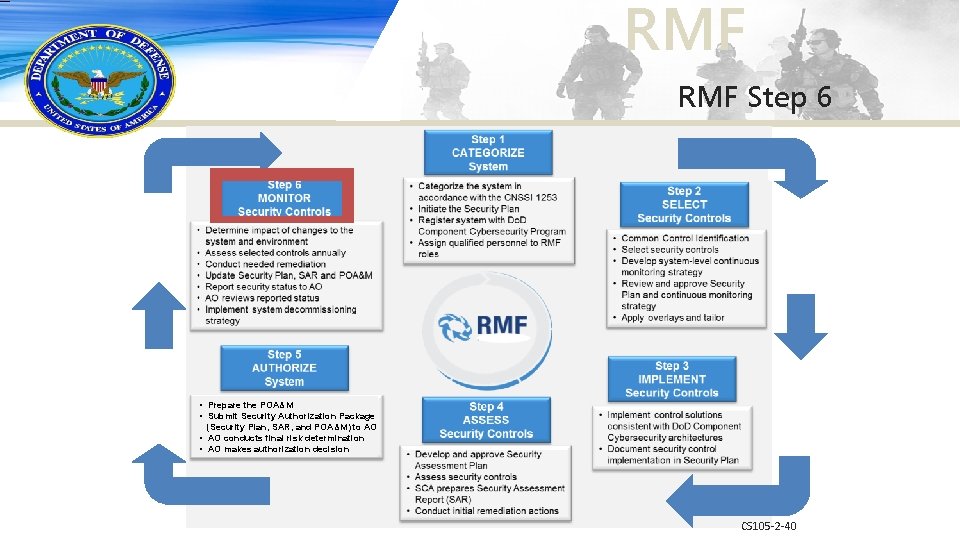
RMF Step 6 • Prepare the POA&M • Submit Security Authorization Package (Security Plan, SAR, and POA&M) to AO • AO conducts final risk determination • AO makes authorization decision CS 105 -2 -40

RMF Step 6 – Monitor Security Controls – Determine the security impact of proposed or actual changes to the information system and its environment of operation – Assess a selected subset of the technical, management, and operational security controls annually that are employed within and inherited by the information system in accordance with the organization-defined monitoring strategy – Conduct selected remediation actions based on the results of ongoing monitoring activities, assessment of risk, and the outstanding items in the plan of action and milestones – Update the security plan, security assessment report, and plan of action and milestones based on the results of the continuous monitoring process CS 105 -2 -41

RMF Step 6 -Monitor Security Controls (Continued) – Report the security status of the information system (including the effectiveness of security controls employed within and inherited by the system) to the AO on an ongoing basis in accordance with the organization-defined monitoring strategy – AO reviews the reported security status of the information system (including the effectiveness of security controls employed within and inherited by the system) on an ongoing basis in accordance with the monitoring strategy to determine whether the risk to organizational operations, organizational assets, individuals, other organizations, or the Nation remains acceptable – The assessor must provide a written and signed (or if digital, Do. D PKIcertified digitally signed) report in the SAR format to the AO that indicates the results of an annual assessment of selected security controls – Implement an information system decommissioning strategy which executes required actions when a system is removed from service CS 105 -2 -42
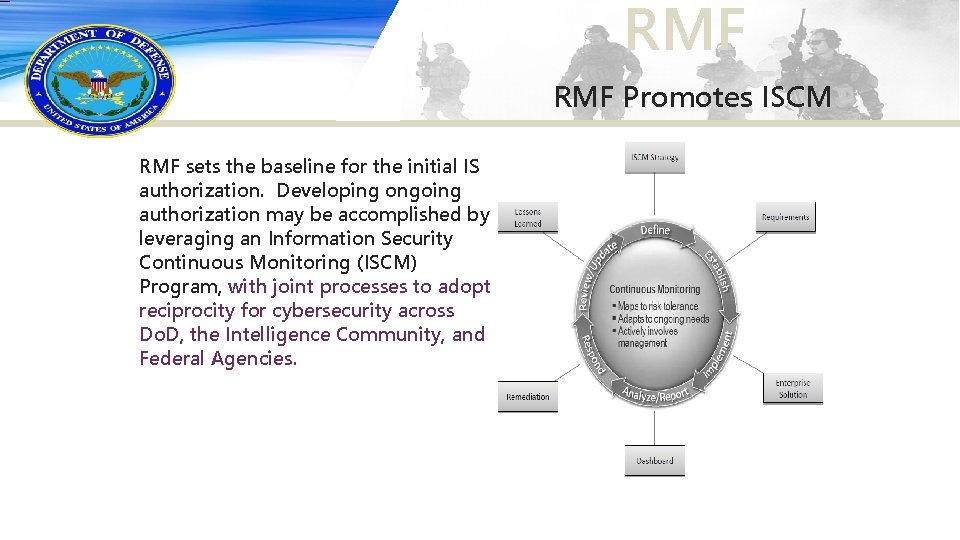
RMF Promotes ISCM RMF sets the baseline for the initial IS authorization. Developing ongoing authorization may be accomplished by leveraging an Information Security Continuous Monitoring (ISCM) Program, with joint processes to adopt reciprocity for cybersecurity across Do. D, the Intelligence Community, and Federal Agencies.

Agenda Oct 24, 2015 • Review new materials of previous topics: – Cyber Security Summit last Tuesday – Authorization Boundary Webinar last Friday – RASCI Chart in Do. D Program Manager’s Guidebook for Integrating the Cybersecurity Risk Management Framework (RMF) into the System Acquisition, Lifecycle May 26, 2015 • New topics: – RMF Tool Kit (Free) – NIST Special Publication 800 -53 A R 4, Assessing Security and Privacy Controls in Federal Information Systems and Organizations, Building Effective Assessment Plans, Dec 2014 – RMF v 5, Step 4, Assess Security Controls 44
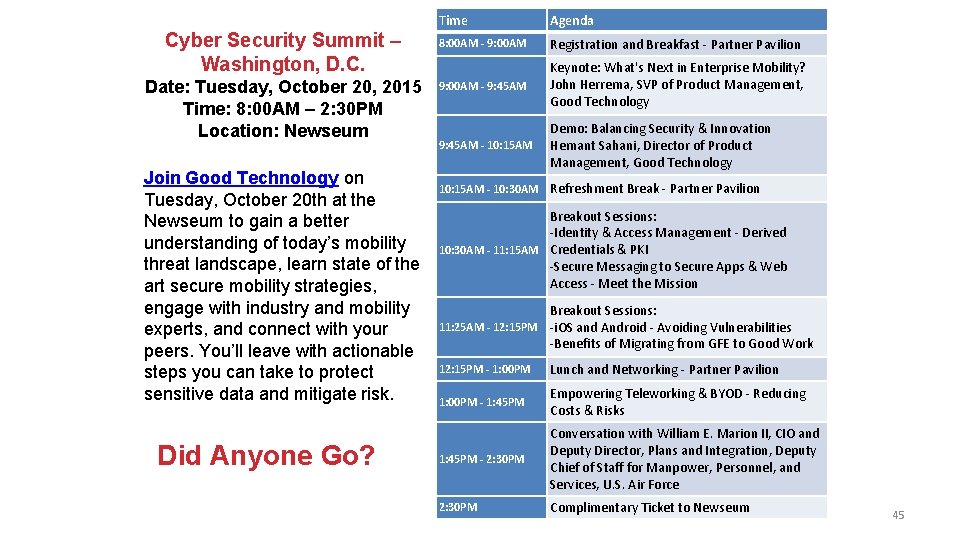
Cyber Security Summit – Washington, D. C. Date: Tuesday, October 20, 2015 Time: 8: 00 AM – 2: 30 PM Location: Newseum Join Good Technology on Tuesday, October 20 th at the Newseum to gain a better understanding of today’s mobility threat landscape, learn state of the art secure mobility strategies, engage with industry and mobility experts, and connect with your peers. You’ll leave with actionable steps you can take to protect sensitive data and mitigate risk. Did Anyone Go? Time Agenda 8: 00 AM - 9: 00 AM Registration and Breakfast - Partner Pavilion 9: 00 AM - 9: 45 AM Keynote: What's Next in Enterprise Mobility? John Herrema, SVP of Product Management, Good Technology 9: 45 AM - 10: 15 AM Demo: Balancing Security & Innovation Hemant Sahani, Director of Product Management, Good Technology 10: 15 AM - 10: 30 AM Refreshment Break - Partner Pavilion Breakout Sessions: -Identity & Access Management - Derived 10: 30 AM - 11: 15 AM Credentials & PKI -Secure Messaging to Secure Apps & Web Access - Meet the Mission Breakout Sessions: 11: 25 AM - 12: 15 PM -i. OS and Android - Avoiding Vulnerabilities -Benefits of Migrating from GFE to Good Work 12: 15 PM - 1: 00 PM Lunch and Networking - Partner Pavilion 1: 00 PM - 1: 45 PM Empowering Teleworking & BYOD - Reducing Costs & Risks 1: 45 PM - 2: 30 PM Conversation with William E. Marion II, CIO and Deputy Director, Plans and Integration, Deputy Chief of Staff for Manpower, Personnel, and Services, U. S. Air Force 2: 30 PM Complimentary Ticket to Newseum 45
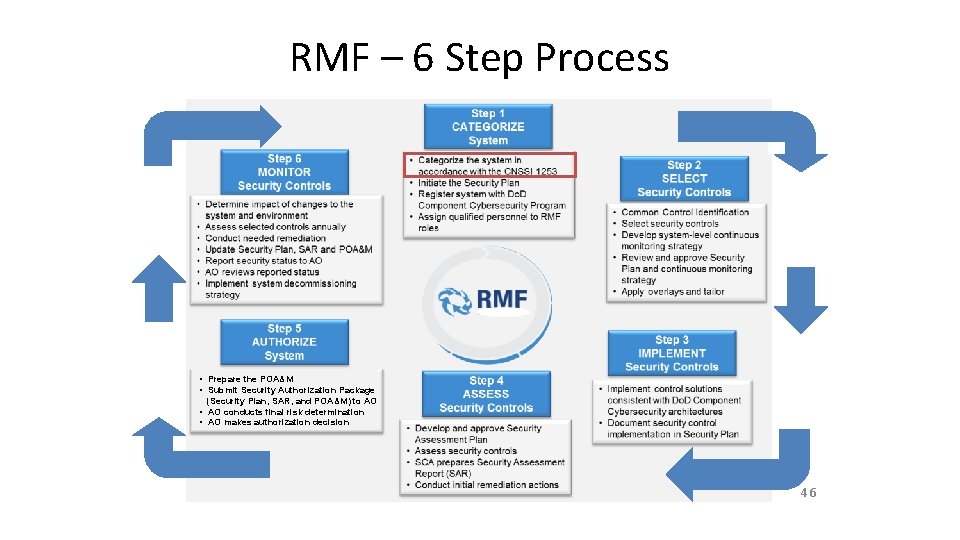
RMF – 6 Step Process • Prepare the POA&M • Submit Security Authorization Package (Security Plan, SAR, and POA&M) to AO • AO conducts final risk determination • AO makes authorization decision 46

Free NIST RMF Training - Authorization Boundary • Step 1: Categorize the System • Previous RMF training You. Tube video @ http: //m. youtube. com/watch? v=NNd. Dg. R-q. Adw • A deep dive on how to properly scope and define an Authorization Boundary • Webinar recorded and posted on You. Tube@ https: //www. youtube. com/watch? v=ik 5 AH_c. Ma. FE 47
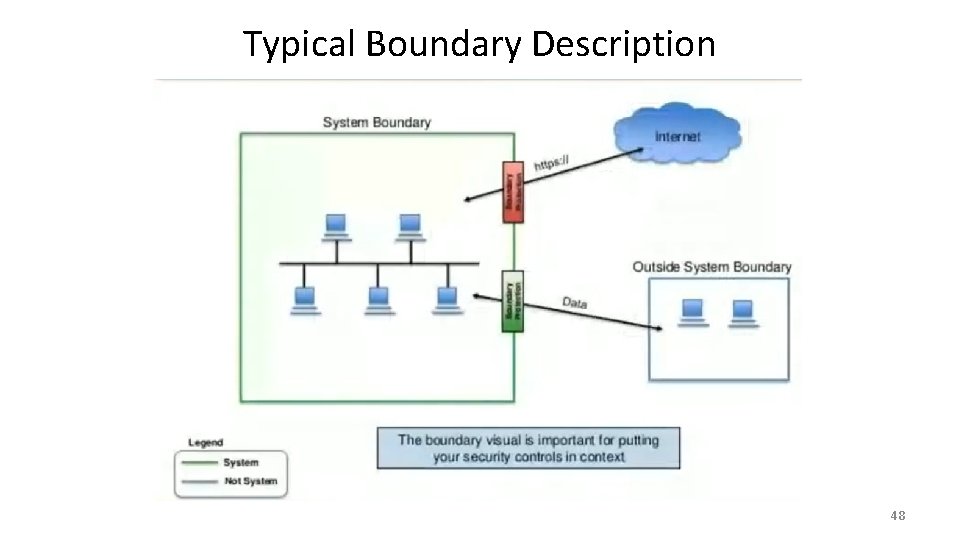
Typical Boundary Description 48
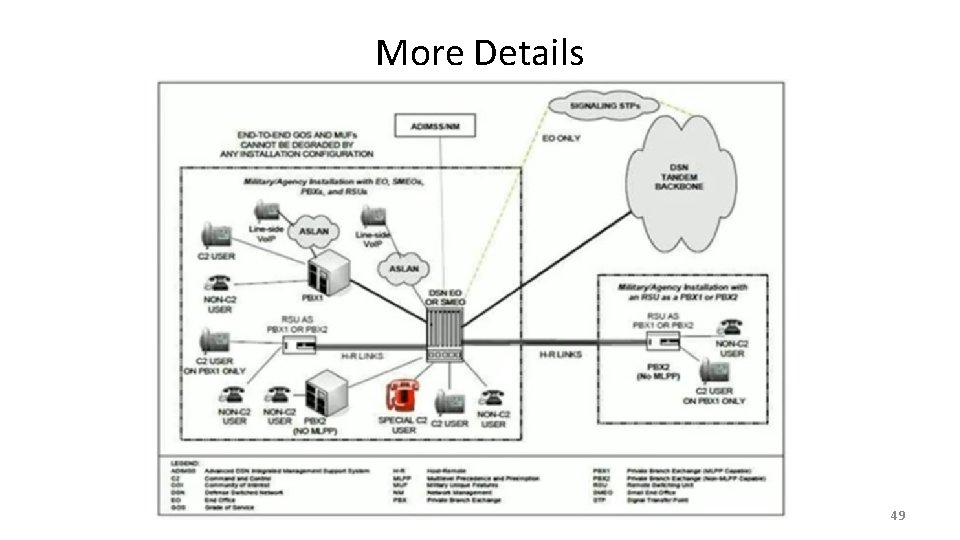
More Details 49

• RASCI Chart in Do. D Program Manager’s Guidebook for Integrating the Cybersecurity Risk Management Framework (RMF) into the System Acquisition Lifecycle, May 26, 2015 50

RMF Tool Kit Free on-line RMF study resource that boosts: ✓ IA Controls Worksheet ✓ 800+ Assessment Procedures ✓ 10 Hours e-Learning ✓ 100 How To Videos ✓ Study Guides & more View Introduction Video http: //fismacs. com/videos/IAWorksheet. mp 4 Developed by Charlene Deaver-Vazquez Owner, FISMA Compliance Solutions, Linked In @ https: //www. linkedin. com/in/charlene deavervazquez To obtain access, you may register with your email address @ http: //www. fismacs. com/RMFTool-Kit. html 51
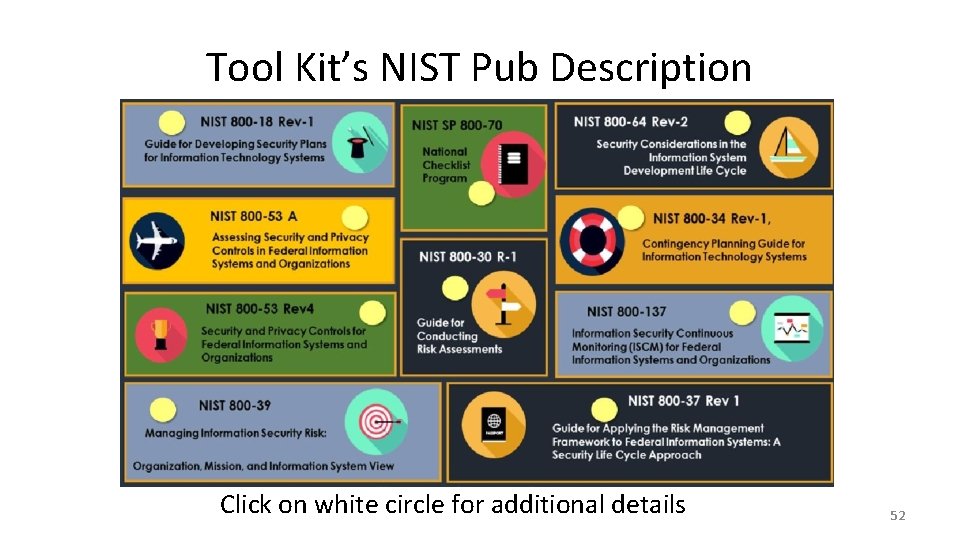
Tool Kit’s NIST Pub Description Click on white circle for additional details 52

NIST Special Publication 800 -53 • Implement set of security controls in NIST SP 800 -53 r 4, “Security and Privacy Controls for Federal Information Systems and Organizations” (462 pages) • Validation procedures of security controls in NIST SP 800 -53 A r 4 “Guide for Assessing the Security Controls in Federal Information Systems. ” (487 pages) 53
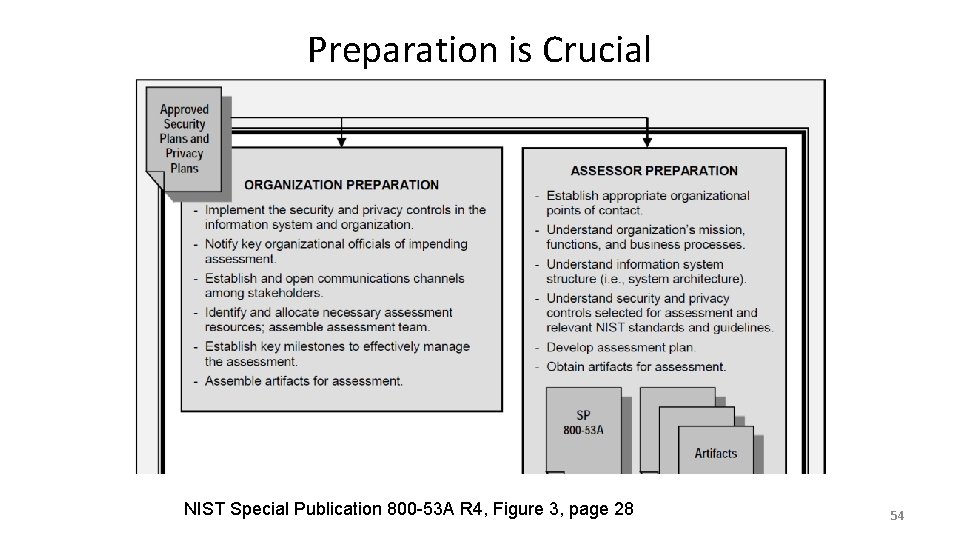
Preparation is Crucial NIST Special Publication 800 -53 A R 4, Figure 3, page 28 54
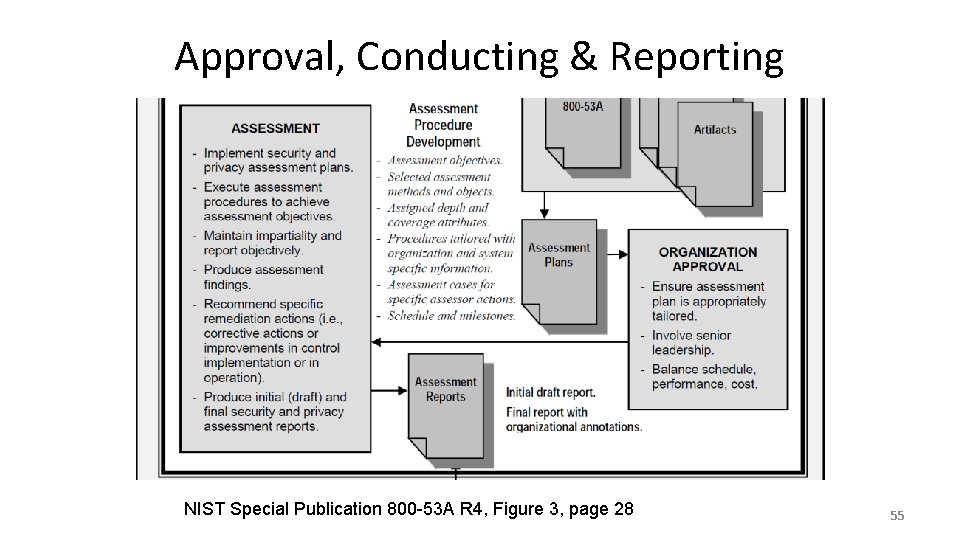
Approval, Conducting & Reporting NIST Special Publication 800 -53 A R 4, Figure 3, page 28 55
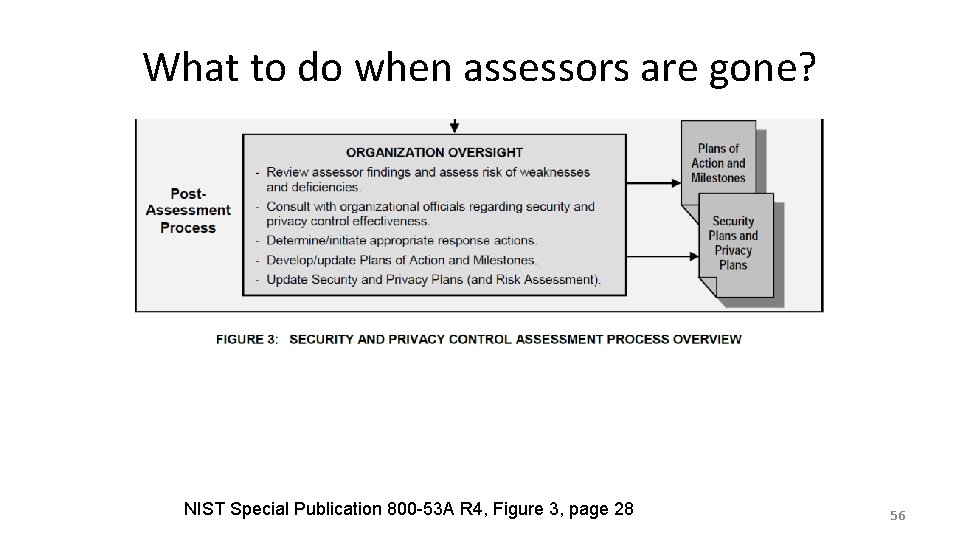
What to do when assessors are gone? NIST Special Publication 800 -53 A R 4, Figure 3, page 28 56
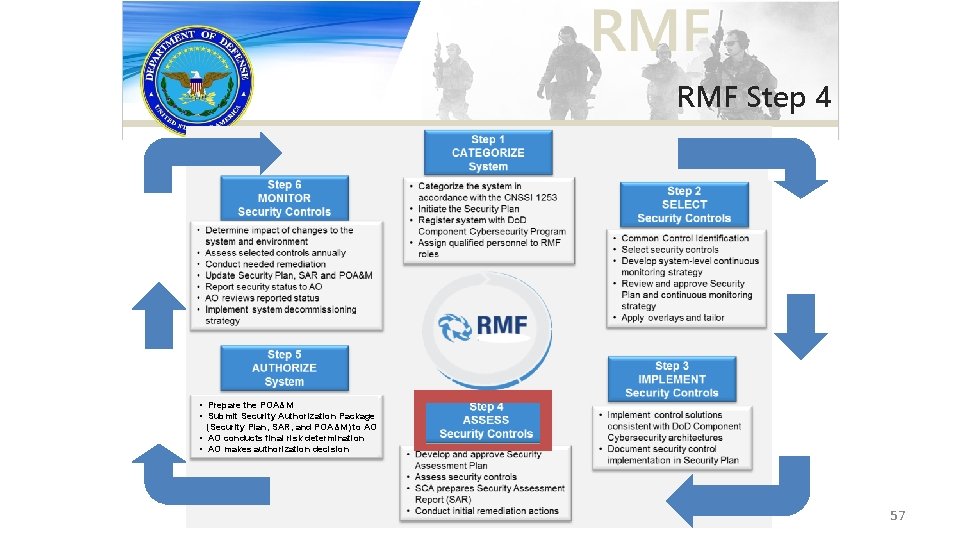
RMF Step 4 • Prepare the POA&M • Submit Security Authorization Package (Security Plan, SAR, and POA&M) to AO • AO conducts final risk determination • AO makes authorization decision 57

Step 4 – Assess Security Controls – Assess the security controls in accordance with the assessment procedures defined in the security assessment plan – Develop, review, and approve a plan to assess the security controls – Prepare the security assessment report documenting the issues, findings, and recommendations from the security control assessment – Conduct initial remediation actions on security controls based on the findings and recommendations of the security assessment report and reassess remediated control(s), as appropriate 58

Assessment Steps Develop the Security Assessment Plan – The Security Control Assessor (SCA) develops the Security Assessment Plan • Ensures assessment activities are coordinated for interoperability, DT&E and OT&E events • Selects appropriate procedures to assess those controls • Tailors the assessment procedures • Finalizes the plan and obtains approval – The AO approves the Security Assessment Plan Do. D RMF KS contains guidance on assessment procedures – Explains integration of assessment procedures of applicable Security Technical Implementation Guides (STIGs), any associated Control Correlation Identifiers (CCIs), or Security Requirements Guides (SRGs) 59

Conduct the Assessment – NIST SP 800 -30 is the guide for conducting risk assessments – The KS is the authoritative source for Do. D security control assessment procedures – SRG and STIG compliance results will be used as part of the overall security control assessment – SCAs will maximize the reuse of existing assessments (i. e. , a leveraged authorization) – The SCA will determine a risk level for every non-compliant (NC) security control in the system baseline – Vulnerability severity values will be assigned to all NC controls by the SCA 60

Conduct the Assessment (Continued) – The results of all security control assessments in the control set will be recorded in the Security Assessment Report (SAR) – The SCA must determine and document in the SAR an assessment of overall system level of risk – The risk assessment must address the impact of all NC controls and clearly communicate the SCA’s conclusion on system cybersecurity risk 61

Security Assessment Report Create the Security Assessment Report – The SAR documents the SCA’s findings of compliance with assigned security controls based on actual assessment results – The SAR addresses security controls in a NC status, including existing and planned mitigations – A SAR is always required before an authorization decision – If a compelling mission or business need requires the rapid development of a new system, assessment activity and a SAR are still required 62

63
Cyber Security in the News • http: //www. cnbc. com/cybersecurity/ 64
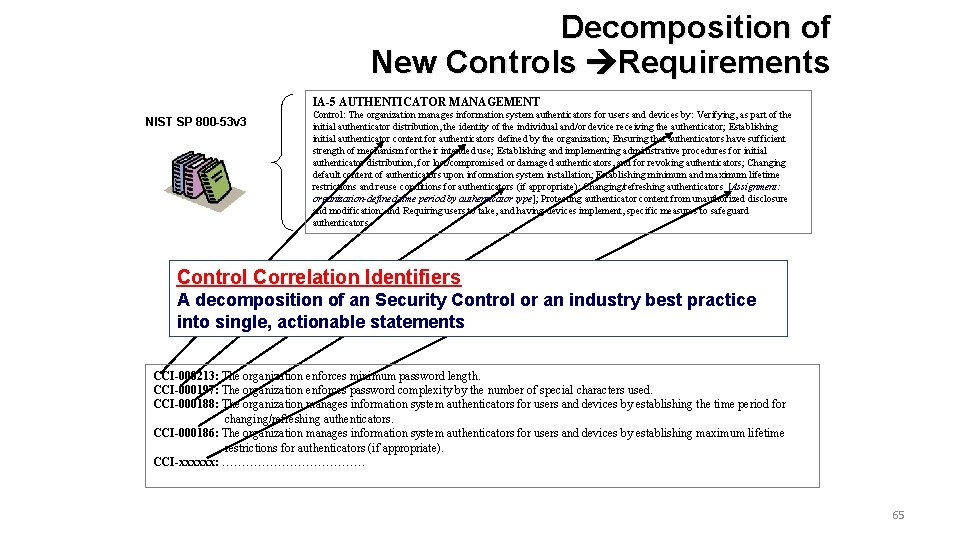
Decomposition of New Controls Requirements IA-5 AUTHENTICATOR MANAGEMENT NIST SP 800 -53 v 3 Control: The organization manages information system authenticators for users and devices by: Verifying, as part of the initial authenticator distribution, the identity of the individual and/or device receiving the authenticator; Establishing initial authenticator content for authenticators defined by the organization; Ensuring that authenticators have sufficient strength of mechanism for their intended use; Establishing and implementing administrative procedures for initial authenticator distribution, for lost/compromised or damaged authenticators, and for revoking authenticators; Changing default content of authenticators upon information system installation; Establishing minimum and maximum lifetime restrictions and reuse conditions for authenticators (if appropriate); Changing/refreshing authenticators [Assignment: organization-defined time period by authenticator type]; Protecting authenticator content from unauthorized disclosure and modification; and Requiring users to take, and having devices implement, specific measures to safeguard authenticators. Control Correlation Identifiers A decomposition of an Security Control or an industry best practice into single, actionable statements CCI-000213: The organization enforces minimum password length. CCI-000197: The organization enforces password complexity by the number of special characters used. CCI-000188: The organization manages information system authenticators for users and devices by establishing the time period for changing/refreshing authenticators. CCI-000186: The organization manages information system authenticators for users and devices by establishing maximum lifetime restrictions for authenticators (if appropriate). CCI-xxxxxx: ……………… 65
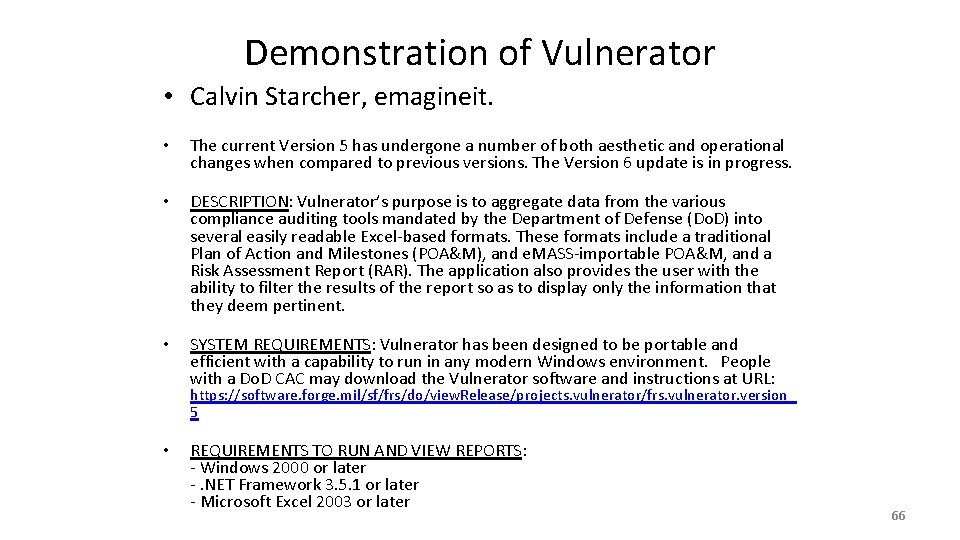
Demonstration of Vulnerator • Calvin Starcher, emagineit. • The current Version 5 has undergone a number of both aesthetic and operational changes when compared to previous versions. The Version 6 update is in progress. • DESCRIPTION: Vulnerator’s purpose is to aggregate data from the various compliance auditing tools mandated by the Department of Defense (Do. D) into several easily readable Excel-based formats. These formats include a traditional Plan of Action and Milestones (POA&M), and e. MASS-importable POA&M, and a Risk Assessment Report (RAR). The application also provides the user with the ability to filter the results of the report so as to display only the information that they deem pertinent. • SYSTEM REQUIREMENTS: Vulnerator has been designed to be portable and efficient with a capability to run in any modern Windows environment. People with a Do. D CAC may download the Vulnerator software and instructions at URL: https: //software. forge. mil/sf/frs/do/view. Release/projects. vulnerator/frs. vulnerator. version_ 5 • REQUIREMENTS TO RUN AND VIEW REPORTS: - Windows 2000 or later -. NET Framework 3. 5. 1 or later - Microsoft Excel 2003 or later 66

Do. DI 8510. 01 – Risk Management Framework (RMF) for Do. D IT • New approach for Do. D to manage Cybersecurity risk – RMF adds another dimension to the Do. D Risk Management Process • A 6 step process that emphasizes continuous monitoring and timely correction of deficiencies • Adopts NIST’s Risk Management Framework, used by Civil and Intelligence communities • Moves from a checklist-driven process to a risk based approach • Embeds the RMF steps and activities in the Do. D Acquisition Lifecycle • Promotes Development and Operational Test & Evaluation (DT&E and OT&E) integration • Implements Cybersecurity via security controls vice numerous policies and memos • Supports and encourages use of automated tools 67
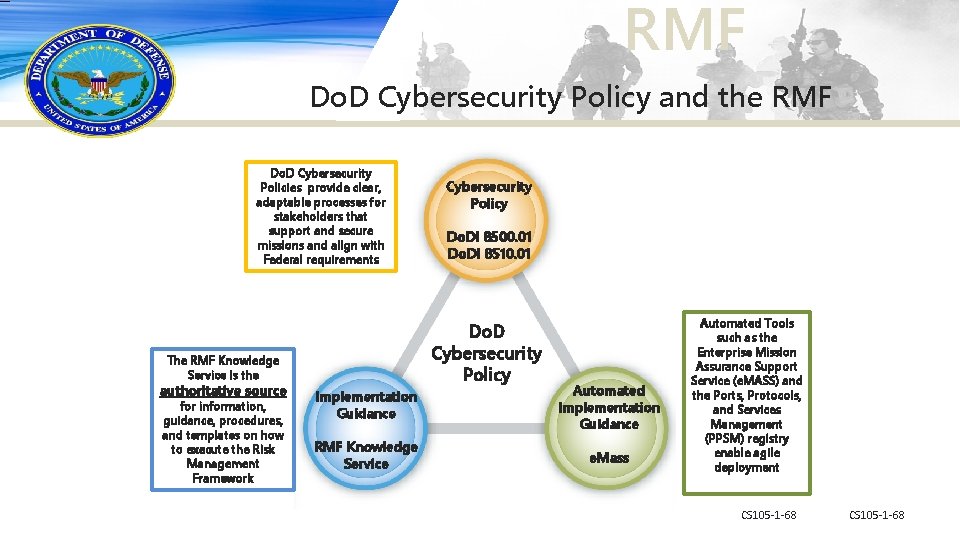
RMF Do. D Cybersecurity Policy and the RMF Do. D Cybersecurity Policies provide clear, adaptable processes for stakeholders that support and secure missions and align with Federal requirements for information, guidance, procedures, and templates on how to execute the Risk Management Framework Do. DI 8500. 01 Do. DI 8510. 01 Do. D Cybersecurity Policy The RMF Knowledge Service is the authoritative source Cybersecurity Policy Implementation Guidance Automated Implementation Guidance RMF Knowledge Service e. Mass Automated Tools such as the Enterprise Mission Assurance Support Service (e. MASS) and the Ports, Protocols, and Services Management (PPSM) registry enable agile deployment CS 105 -1 -68
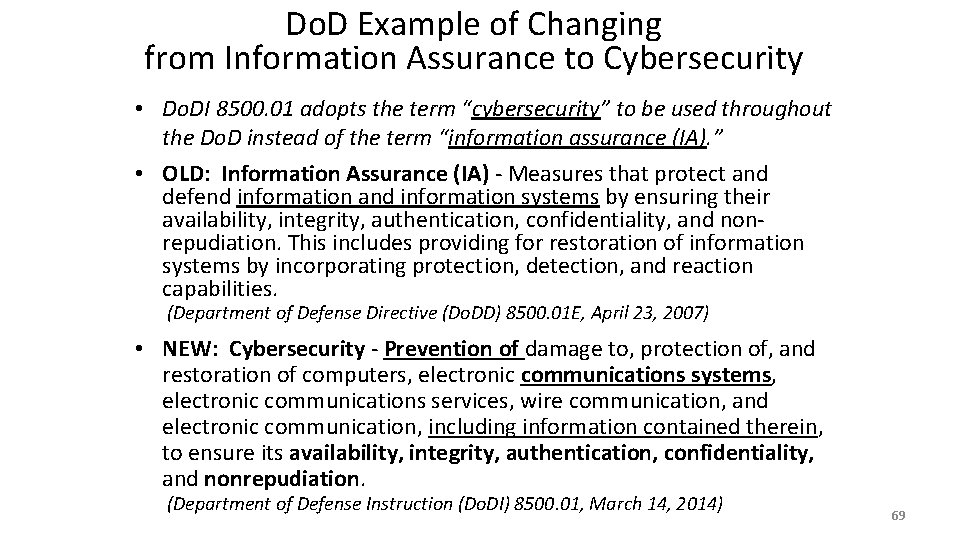
Do. D Example of Changing from Information Assurance to Cybersecurity • Do. DI 8500. 01 adopts the term “cybersecurity” to be used throughout the Do. D instead of the term “information assurance (IA). ” • OLD: Information Assurance (IA) - Measures that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and nonrepudiation. This includes providing for restoration of information systems by incorporating protection, detection, and reaction capabilities. (Department of Defense Directive (Do. DD) 8500. 01 E, April 23, 2007) • NEW: Cybersecurity - Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation. (Department of Defense Instruction (Do. DI) 8500. 01, March 14, 2014) 69
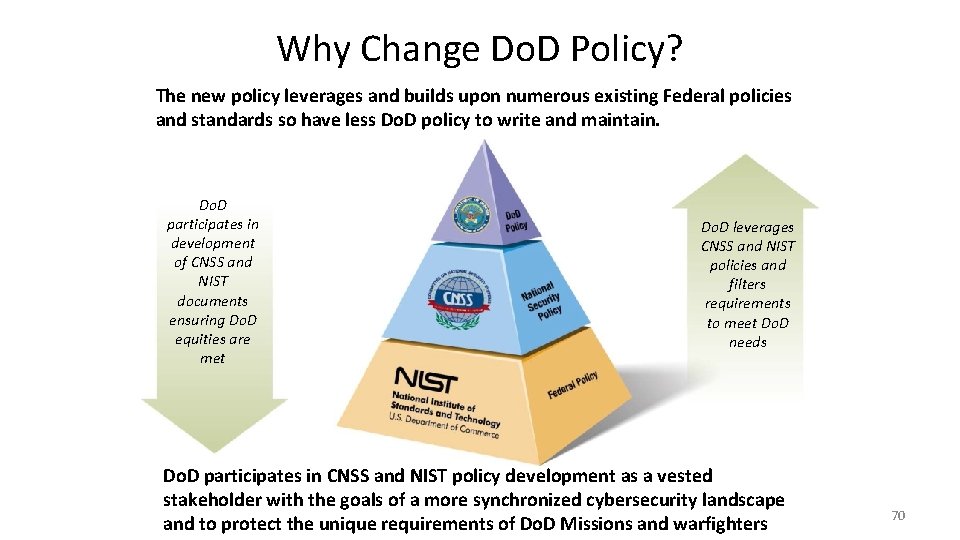
Why Change Do. D Policy? The new policy leverages and builds upon numerous existing Federal policies and standards so have less Do. D policy to write and maintain. Do. D participates in development of CNSS and NIST documents ensuring Do. D equities are met Do. D leverages CNSS and NIST policies and filters requirements to meet Do. D needs Do. D participates in CNSS and NIST policy development as a vested stakeholder with the goals of a more synchronized cybersecurity landscape and to protect the unique requirements of Do. D Missions and warfighters 70
Password Cracking • Techniques – Rainbow Tables – Brute Force – Dictionary/Word Lists – Hybrid • Rock. You. com (Dec 2009) – 14. 3 million unique clear text passwords 71
25 GPU HPC Cluster • Presented by Jeremi Gosney at Passwords^12 Conference – 5 - 4 U Servers – 25 Radeon GPUs – Hashcat 72
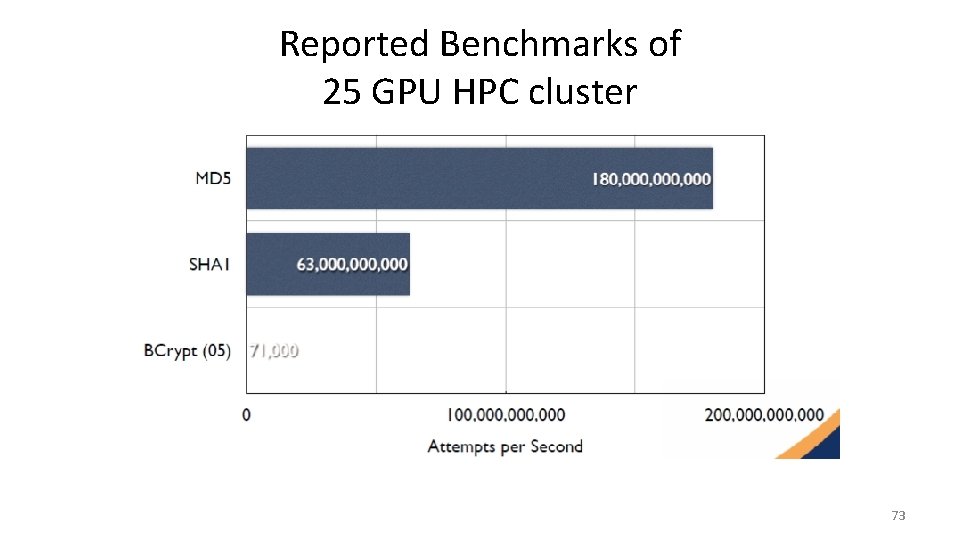
Reported Benchmarks of 25 GPU HPC cluster 73

74

Ashley Madison • Used bcrypt with load factor of 12 • Dean Pierce used 4 AMD Radeon R 9 290 Cards • Over 5 days cracked 4, 007 passwords of first 6 million using Rock. You list • Estimated 19, 493 yrs for 6 m and 116, 958 yrs for all 36 m 75
Ashley Madison • Used bcrypt with load factor of 12 • Dean Pierce used 4 AMD Radeon R 9 290 Cards • Over 5 days cracked 4, 007 passwords of first 6 million using Rock. You list • Estimated 19, 493 yrs for 6 m and 116, 958 yrs for all 36 m • Cyno. Sure Prime • 15. 26 m logins used $loginkey which was username concatenated with password in lowercase • $loginkey was then hashed with MD 5 • Able to crack 11 m in days not years 76
Essential RMF Process Pictures • • Process Cycle Overview Process Task Overview Specific Task IDs and Flowchart For Categorize, Select, and Implement Steps – Roles and Responsibilities Flowchart – Outputs, Captured Items, and Do. D Guidance 77
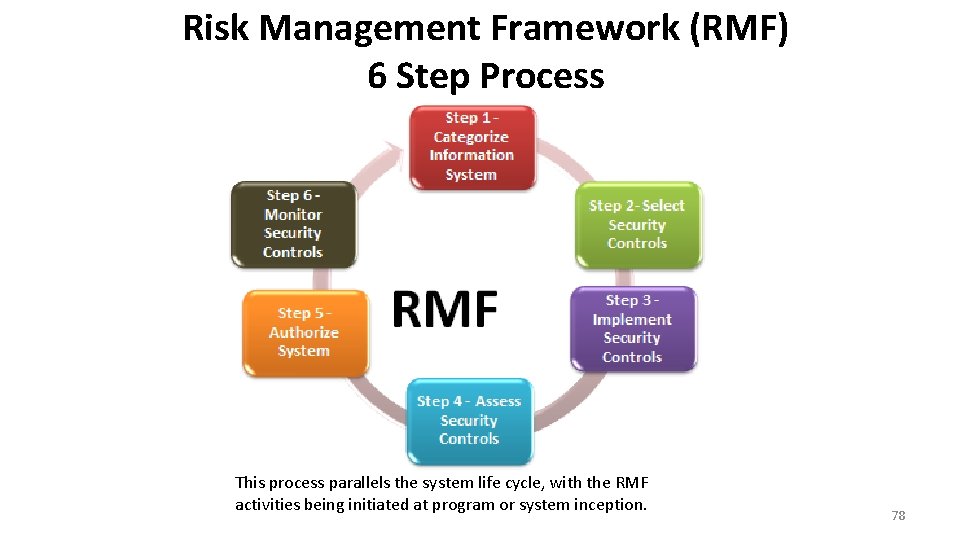
Risk Management Framework (RMF) 6 Step Process This process parallels the system life cycle, with the RMF activities being initiated at program or system inception. 78
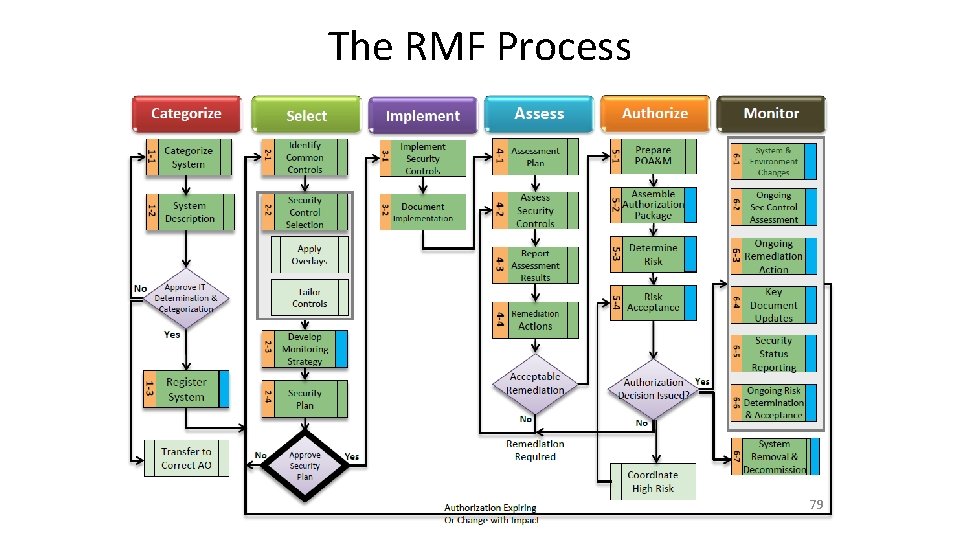
The RMF Process 79
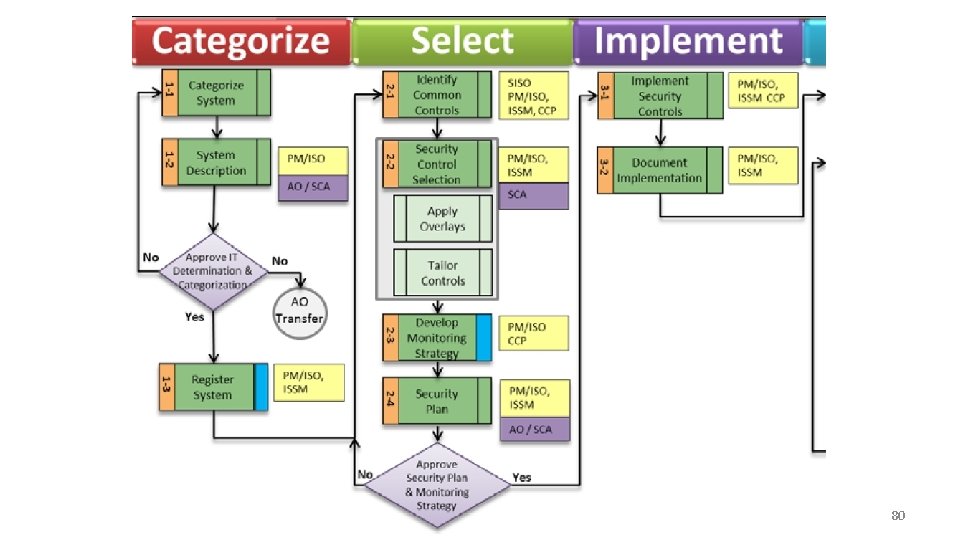
80
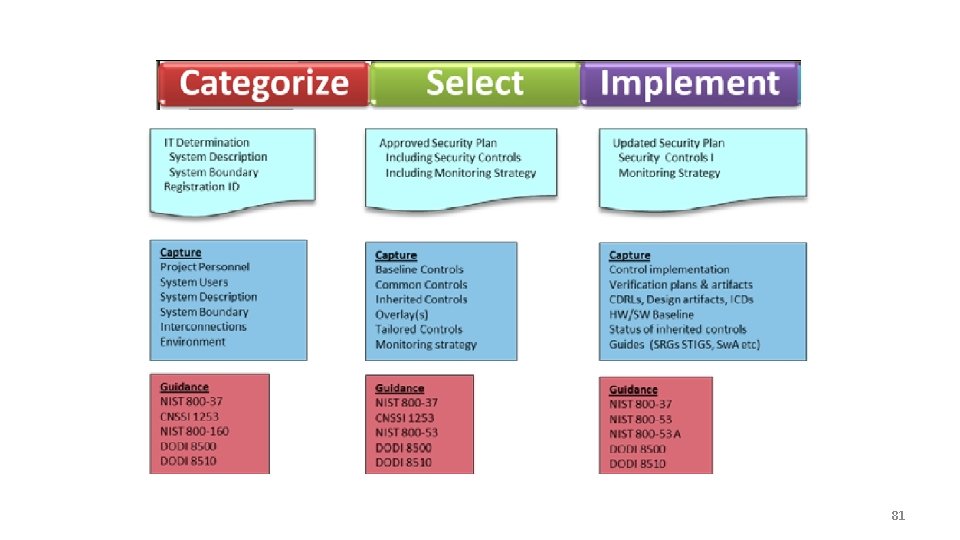
81
- Slides: 81