Cybersecurity Compliance of Air Force Education Systems Navigating

Cybersecurity Compliance of Air Force Education Systems Navigating the Steps from Requirement to Authorization to Operate Mr. Aaron Gauthier AETC ITSP AETC RT&E AO Staff 1 Aug 2017 Heritage to Horizon 1

Agenda n Set the Stage n Portfolio Registration n Risk Management Framework (RMF) in Air Education and Training Command (AETC) n Other Considerations -- Cloud n AETC Vignette n Closing Thoughts Heritage to Horizon 2

SET THE STAGE Heritage to Horizon 3
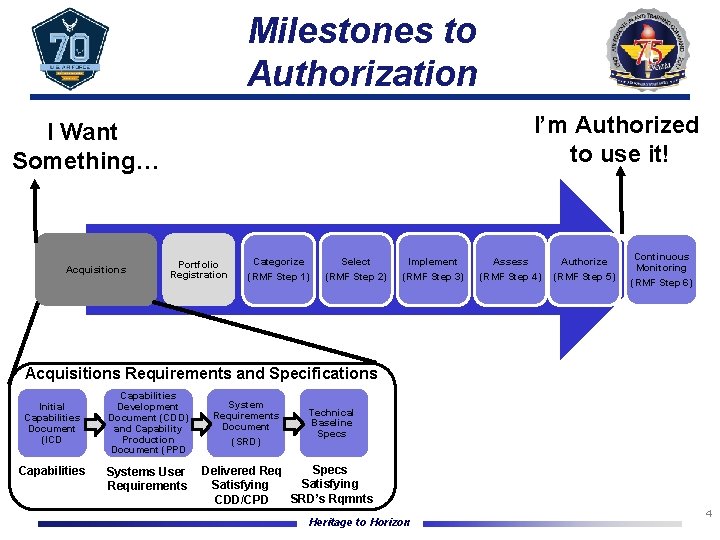
Milestones to Authorization I’m Authorized to use it! I Want Something… Acquisitions Portfolio Registration Categorize (RMF Step 1) Select (RMF Step 2) Implement (RMF Step 3) Assess (RMF Step 4) Authorize (RMF Step 5) Continuous Monitoring (RMF Step 6) Acquisitions Requirements and Specifications Initial Capabilities Document (ICD Capabilities Development Document (CDD) and Capability Production Document (PPD Systems User Requirements System Requirements Document (SRD) Technical Baseline Specs Delivered Req Satisfying SRD’s Rqmnts CDD/CPD Heritage to Horizon 4

Why Risk Management Framework (RMF)… n Clinger Cohen Act n Requires agencies to analyze, track, and evaluate the risks and results of major capital investments for information systems, and Report on program performance n Defines IT as Any equipment or interconnected system or subsystem of equipment…if the equipment is used by the executive agency directly or is used by a contractor under a contract n Does not include any equipment acquired by a federal contractor incidental to a federal contract. FISMA. . . Federal Information Security Modernization Act of 2014 (FISMA 2014) n Comprehensive framework to protect the government’s information, operations, and assets n Requires agency CIO’s to conduct quarterly/annual security program reviews n Heritage to Horizon 5

Why Risk Management Framework (RMF)… n NIST n Statutory responsibilities under the Federal Information Security Management Act (FISMA), Public Law (P. L. ) 107347. n NIST is responsible for developing information security standards and guidelines, including minimum requirements for federal information systems n Do. D Policy - Do. DI 8510. 01, RMF for Do. D Information Technology (IT) n Applicability - All Do. D IT that receive, process, store, display, or transmit Do. D information…Do. D-controlled IT operated by a contractor or other entity on behalf of the Do. D. n Policy aligns with National Institute of Standards and Technology (NIST) Special Publication (SP) Heritage to Horizon 6
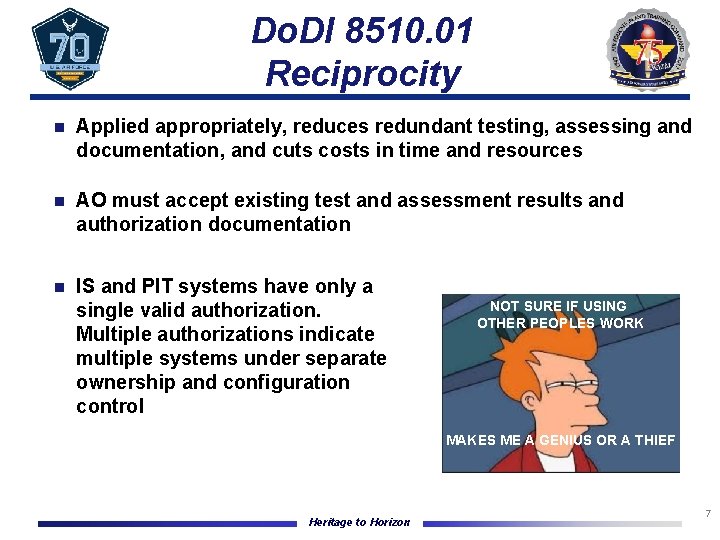
Do. DI 8510. 01 Reciprocity n Applied appropriately, reduces redundant testing, assessing and documentation, and cuts costs in time and resources n AO must accept existing test and assessment results and authorization documentation n IS and PIT systems have only a single valid authorization. Multiple authorizations indicate multiple systems under separate ownership and configuration control NOT SURE IF USING OTHER PEOPLES WORK MAKES ME A GENIUS OR A THIEF Heritage to Horizon 7

PORTFOLIO REGISTRATION Heritage to Horizon 8
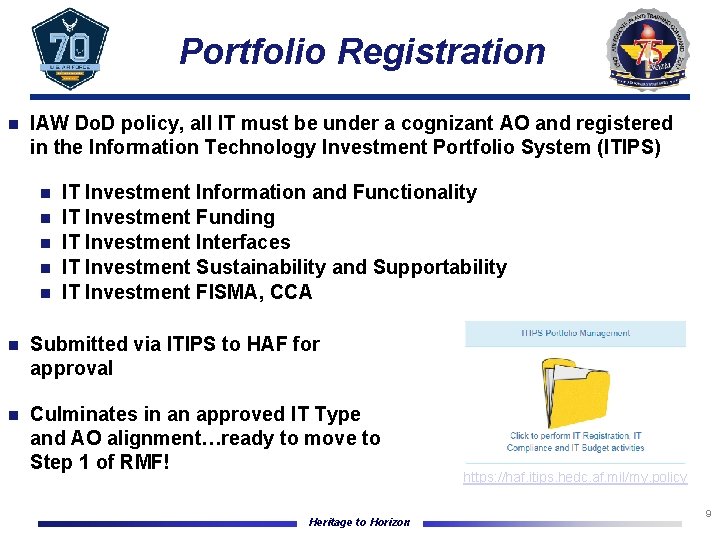
Portfolio Registration n IAW Do. D policy, all IT must be under a cognizant AO and registered in the Information Technology Investment Portfolio System (ITIPS) n n n IT Investment Information and Functionality IT Investment Funding IT Investment Interfaces IT Investment Sustainability and Supportability IT Investment FISMA, CCA n Submitted via ITIPS to HAF for approval n Culminates in an approved IT Type and AO alignment…ready to move to Step 1 of RMF! Heritage to Horizon https: //haf. itips. hedc. af. mil/my. policy 9

RMF IN AETC Heritage to Horizon 10
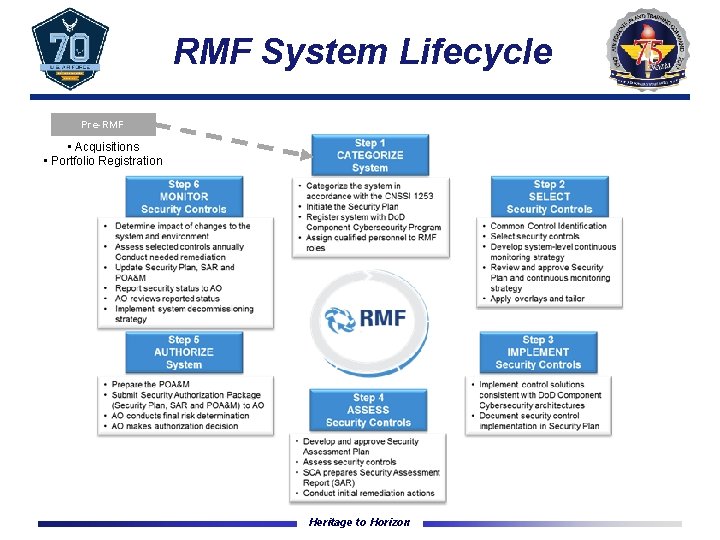
RMF System Lifecycle Pre-RMF • Acquisitions • Portfolio Registration Heritage to Horizon
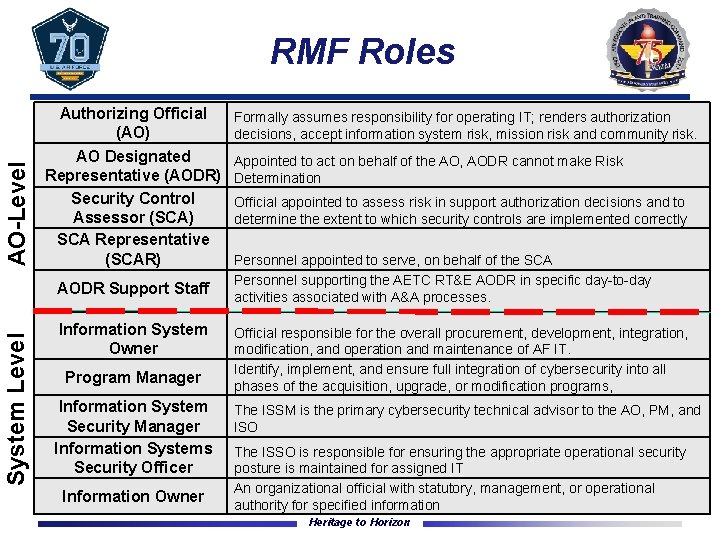
AO-Level RMF Roles Authorizing Official (AO) AO Designated Representative (AODR) Security Control Assessor (SCA) SCA Representative (SCAR) System Level AODR Support Staff Information System Owner Program Manager Information System Security Manager Information Systems Security Officer Information Owner Formally assumes responsibility for operating IT; renders authorization decisions, accept information system risk, mission risk and community risk. Appointed to act on behalf of the AO, AODR cannot make Risk Determination Official appointed to assess risk in support authorization decisions and to determine the extent to which security controls are implemented correctly Personnel appointed to serve, on behalf of the SCA Personnel supporting the AETC RT&E AODR in specific day-to-day activities associated with A&A processes. Official responsible for the overall procurement, development, integration, modification, and operation and maintenance of AF IT. Identify, implement, and ensure full integration of cybersecurity into all phases of the acquisition, upgrade, or modification programs, The ISSM is the primary cybersecurity technical advisor to the AO, PM, and ISO The ISSO is responsible for ensuring the appropriate operational security posture is maintained for assigned IT An organizational official with statutory, management, or operational authority for specified information Heritage to Horizon
RMF Step-1 Information Categorization n NIST SP 800 -60, explains how Federal government agencies categorize information and information systems n Security Categorization is the key first step in the Risk Management Framework because of its effect on selection of security n Agencies shall identify all of the applicable information types that are representative of input, stored, processed, and/or output data from each system. Heritage to Horizon 13
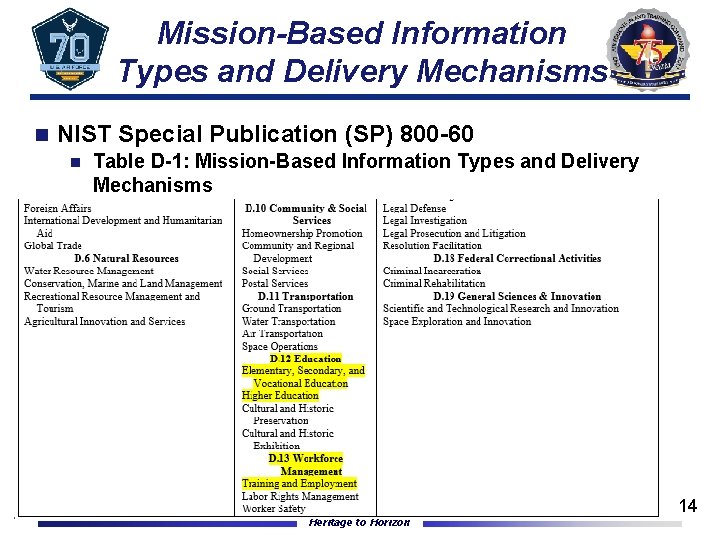
Mission-Based Information Types and Delivery Mechanisms n NIST Special Publication (SP) 800 -60 n Table D-1: Mission-Based Information Types and Delivery Mechanisms Heritage to Horizon 14
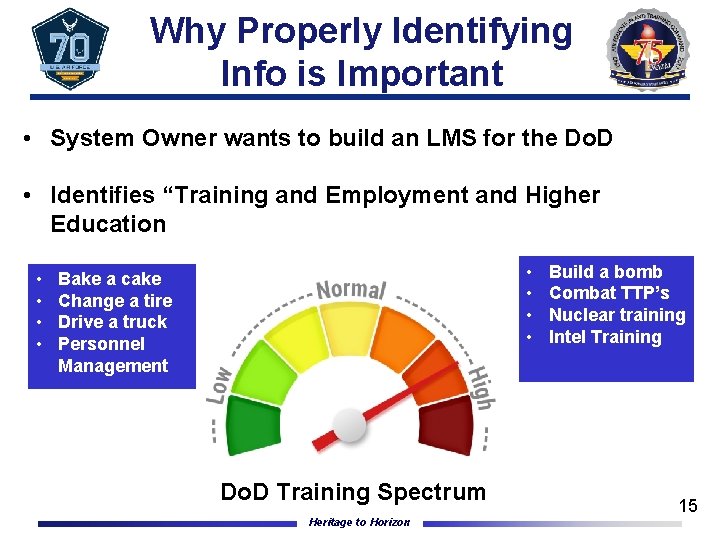
Why Properly Identifying Info is Important • System Owner wants to build an LMS for the Do. D • Identifies “Training and Employment and Higher Education • • Bake a cake Change a tire Drive a truck Personnel Management Do. D Training Spectrum Heritage to Horizon Build a bomb Combat TTP’s Nuclear training Intel Training 15
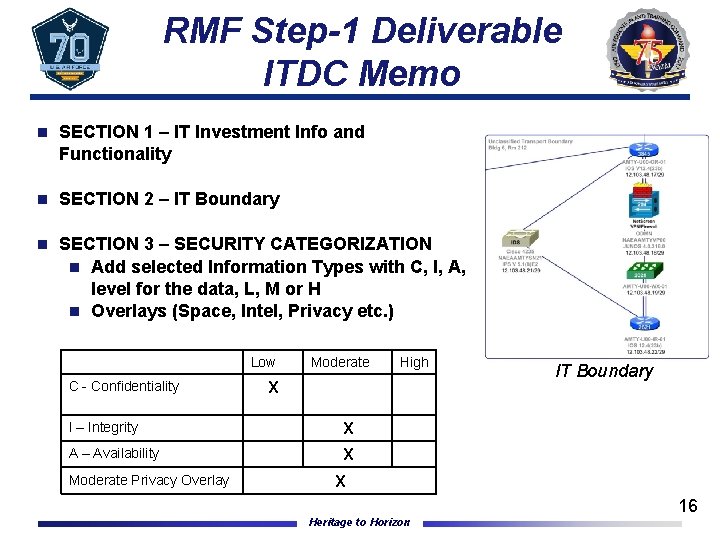
RMF Step-1 Deliverable ITDC Memo n SECTION 1 – IT Investment Info and Functionality n SECTION 2 – IT Boundary n SECTION 3 – SECURITY CATEGORIZATION n Add selected Information Types with C, I, A, level for the data, L, M or H n Overlays (Space, Intel, Privacy etc. ) Low C - Confidentiality Moderate X I – Integrity X A – Availability X Moderate Privacy Overlay High IT Boundary X Heritage to Horizon 16
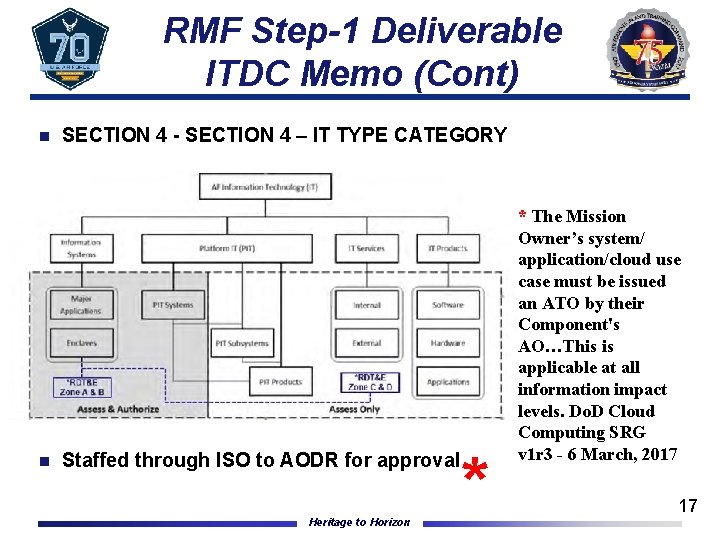
RMF Step-1 Deliverable ITDC Memo (Cont) n n SECTION 4 - SECTION 4 – IT TYPE CATEGORY * Staffed through ISO to AODR for approval Heritage to Horizon * The Mission Owner’s system/ application/cloud use case must be issued an ATO by their Component's AO…This is applicable at all information impact levels. Do. D Cloud Computing SRG v 1 r 3 - 6 March, 2017 17
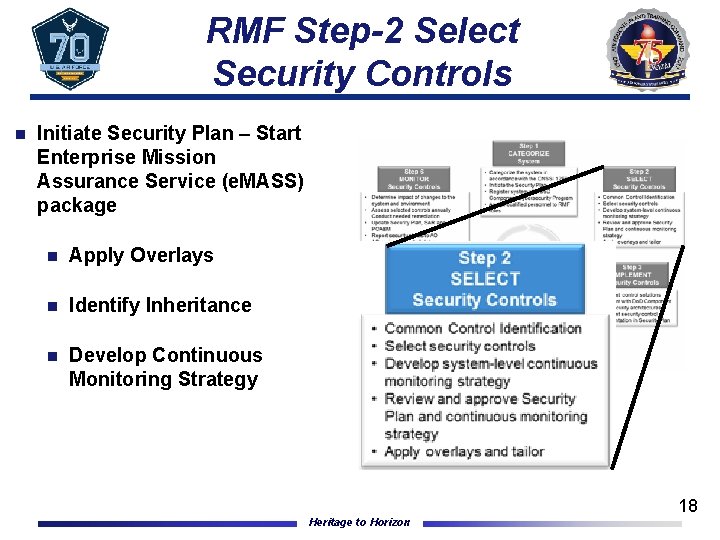
RMF Step-2 Select Security Controls n Initiate Security Plan – Start Enterprise Mission Assurance Service (e. MASS) package n Apply Overlays n Identify Inheritance n Develop Continuous Monitoring Strategy Heritage to Horizon 18
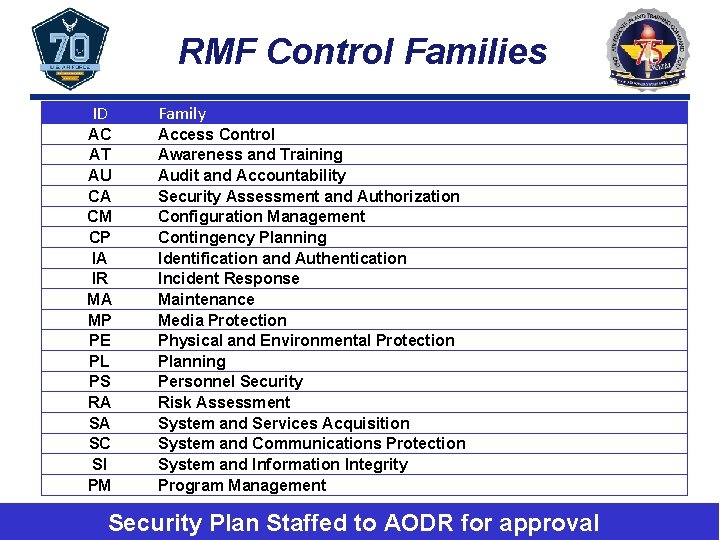
RMF Control Families ID Family AC AT AU CA CM CP IA IR MA MP PE PL PS RA SA SC SI PM Access Control Awareness and Training Audit and Accountability Security Assessment and Authorization Configuration Management Contingency Planning Identification and Authentication Incident Response Maintenance Media Protection Physical and Environmental Protection Planning Personnel Security Risk Assessment System and Services Acquisition System and Communications Protection System and Information Integrity Program Management Heritage to Horizon Security Plan Staffed to AODR for approval 19
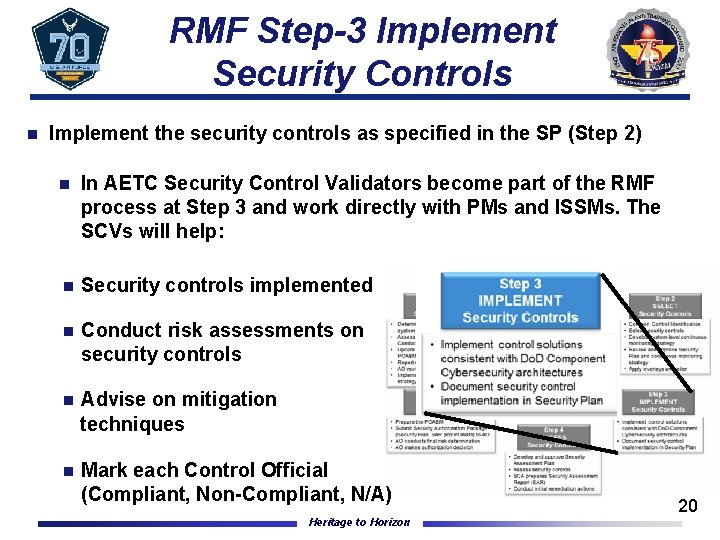
RMF Step-3 Implement Security Controls n Implement the security controls as specified in the SP (Step 2) n In AETC Security Control Validators become part of the RMF process at Step 3 and work directly with PMs and ISSMs. The SCVs will help: n Security controls implemented n Conduct risk assessments on security controls Advise on mitigation techniques n n Mark each Control Official (Compliant, Non-Compliant, N/A) Heritage to Horizon 20
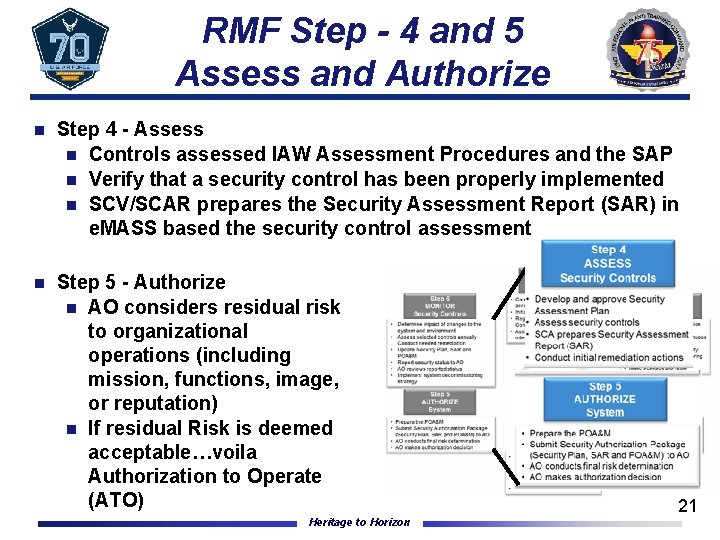
RMF Step - 4 and 5 Assess and Authorize n Step 4 - Assess n Controls assessed IAW Assessment Procedures and the SAP n Verify that a security control has been properly implemented n SCV/SCAR prepares the Security Assessment Report (SAR) in e. MASS based the security control assessment n Step 5 - Authorize n AO considers residual risk to organizational operations (including mission, functions, image, or reputation) n If residual Risk is deemed acceptable…voila Authorization to Operate (ATO) Heritage to Horizon 21
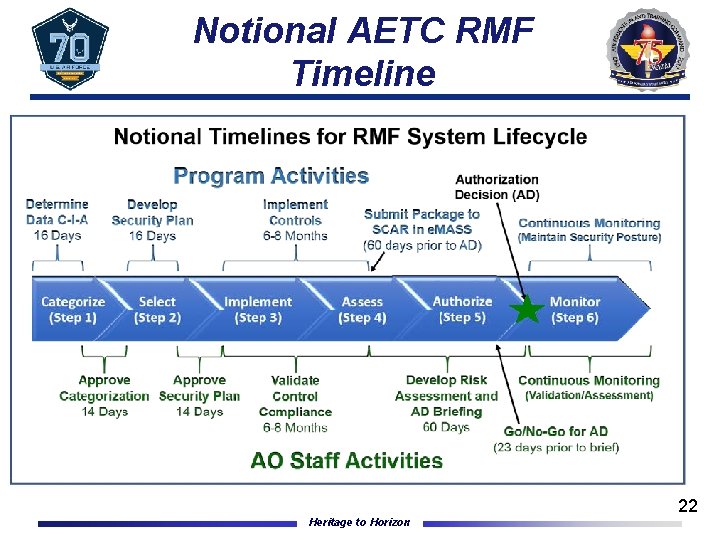
Notional AETC RMF Timeline Heritage to Horizon 22

OTHER CONSIDERATIONS E. G. “CLOUD” Cloud computing is not just a technology, it’s also a new model for organizing, contracting and delivering information technology systems. Heritage to Horizon 23
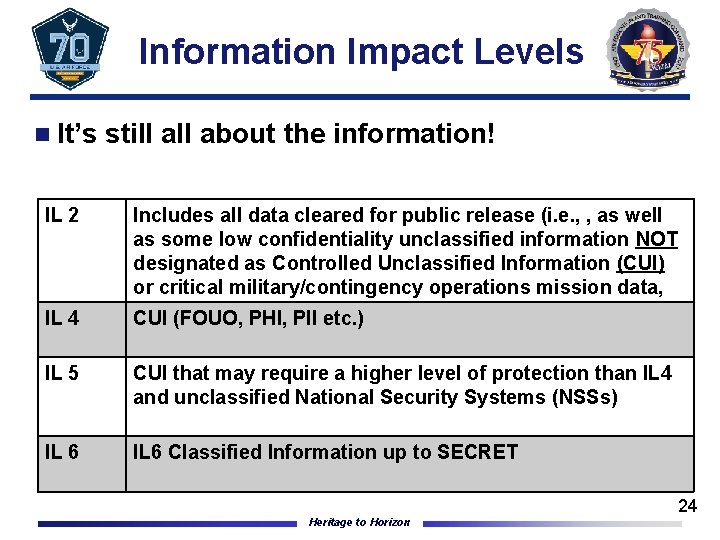
Information Impact Levels n It’s still about the information! IL 2 Includes all data cleared for public release (i. e. , , as well as some low confidentiality unclassified information NOT designated as Controlled Unclassified Information (CUI) or critical military/contingency operations mission data, IL 4 CUI (FOUO, PHI, PII etc. ) IL 5 CUI that may require a higher level of protection than IL 4 and unclassified National Security Systems (NSSs) IL 6 Classified Information up to SECRET Heritage to Horizon 24
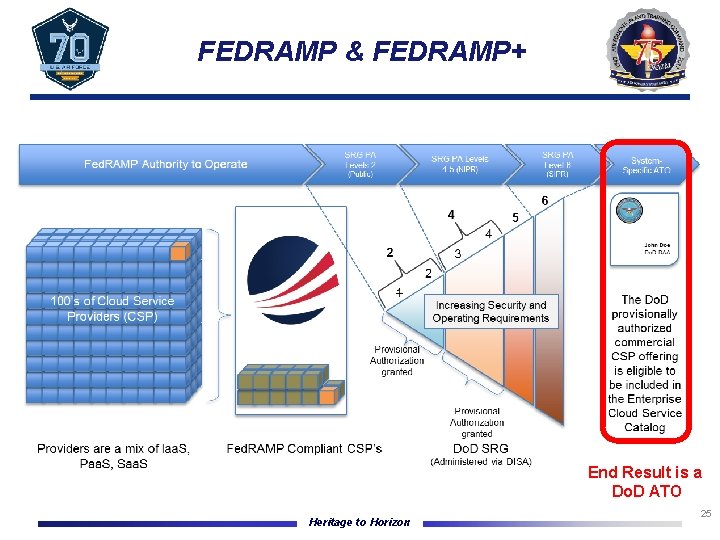
FEDRAMP & FEDRAMP+ End Result is a Do. D ATO Heritage to Horizon 25
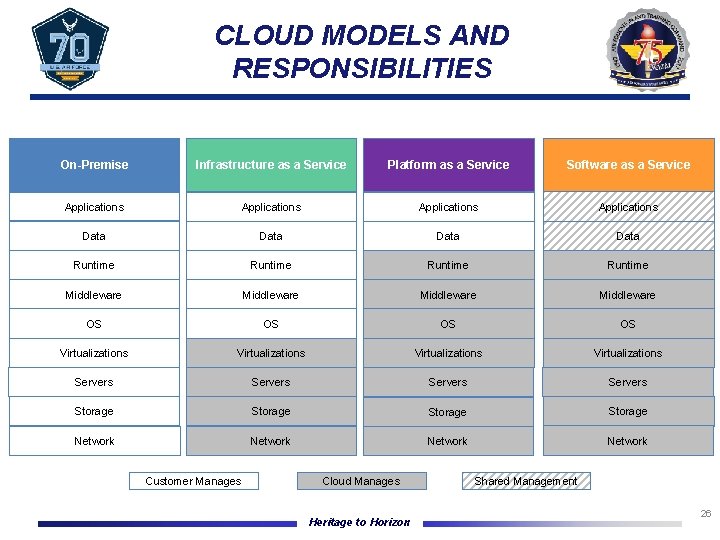
CLOUD MODELS AND RESPONSIBILITIES On-Premise Infrastructure as a Service Platform as a Service Software as a Service Applications Data Runtime Middleware OS OS Virtualizations Servers Storage Network Customer Manages Cloud Manages Heritage to Horizon Shared Management 26
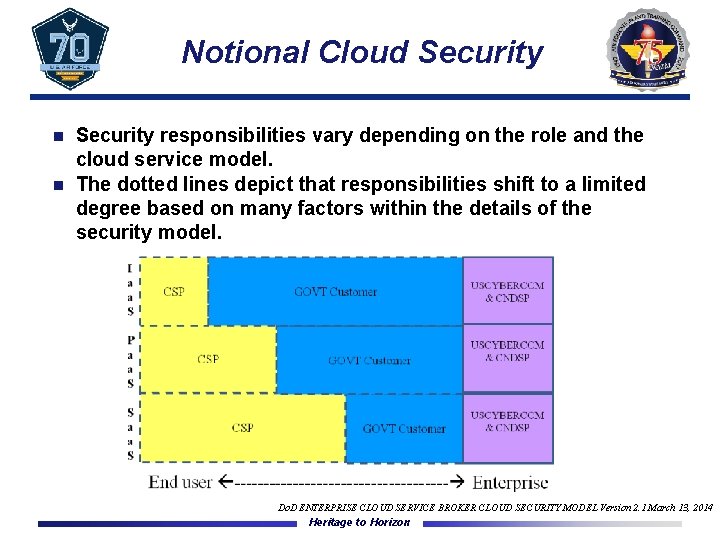
Notional Cloud Security responsibilities vary depending on the role and the cloud service model. n The dotted lines depict that responsibilities shift to a limited degree based on many factors within the details of the security model. n Do. D ENTERPRISE CLOUD SERVICE BROKER CLOUD SECURITY MODEL Version 2. 1 March 13, 2014 Heritage to Horizon
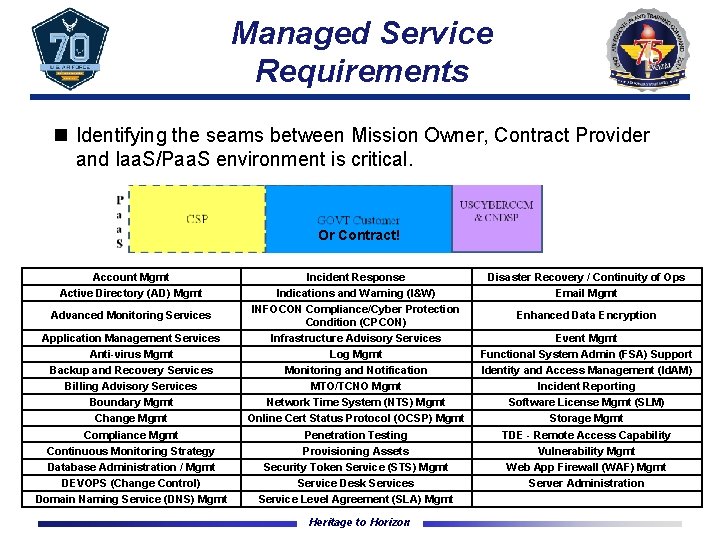
Managed Service Requirements n Identifying the seams between Mission Owner, Contract Provider and Iaa. S/Paa. S environment is critical. Or Contract! Account Mgmt Active Directory (AD) Mgmt Advanced Monitoring Services Application Management Services Anti-virus Mgmt Backup and Recovery Services Billing Advisory Services Boundary Mgmt Change Mgmt Compliance Mgmt Continuous Monitoring Strategy Database Administration / Mgmt DEVOPS (Change Control) Domain Naming Service (DNS) Mgmt Incident Response Indications and Warning (I&W) INFOCON Compliance/Cyber Protection Condition (CPCON) Infrastructure Advisory Services Log Mgmt Monitoring and Notification MTO/TCNO Mgmt Network Time System (NTS) Mgmt Online Cert Status Protocol (OCSP) Mgmt Penetration Testing Provisioning Assets Security Token Service (STS) Mgmt Service Desk Services Service Level Agreement (SLA) Mgmt Heritage to Horizon Disaster Recovery / Continuity of Ops Email Mgmt Enhanced Data Encryption Event Mgmt Functional System Admin (FSA) Support Identity and Access Management (Id. AM) Incident Reporting Software License Mgmt (SLM) Storage Mgmt TDE - Remote Access Capability Vulnerability Mgmt Web App Firewall (WAF) Mgmt Server Administration
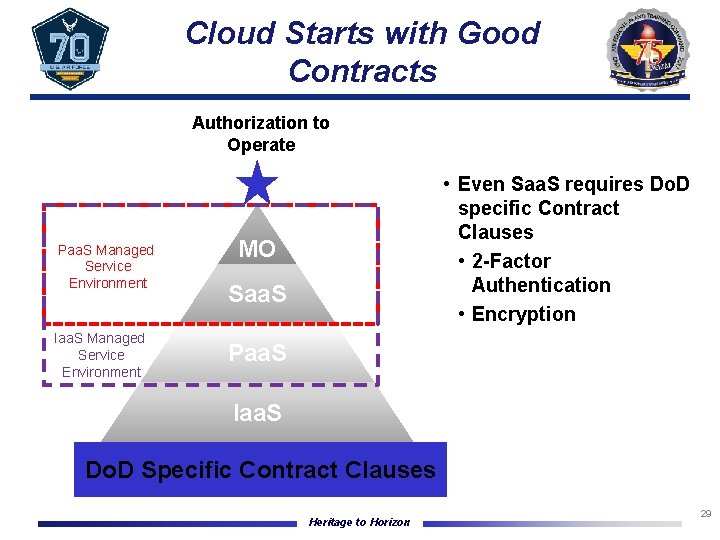
Cloud Starts with Good Contracts Authorization to Operate Paa. S Managed Service Environment Iaa. S Managed Service Environment • Even Saa. S requires Do. D specific Contract Clauses • 2 -Factor Authentication • Encryption MO Saa. S Paa. S Iaa. S Do. D Specific Contract Clauses Heritage to Horizon 29

AETC VIGNETTE Heritage to Horizon 30
We Are Ensnared By Our Legacy Systems Heritage to Horizon 31
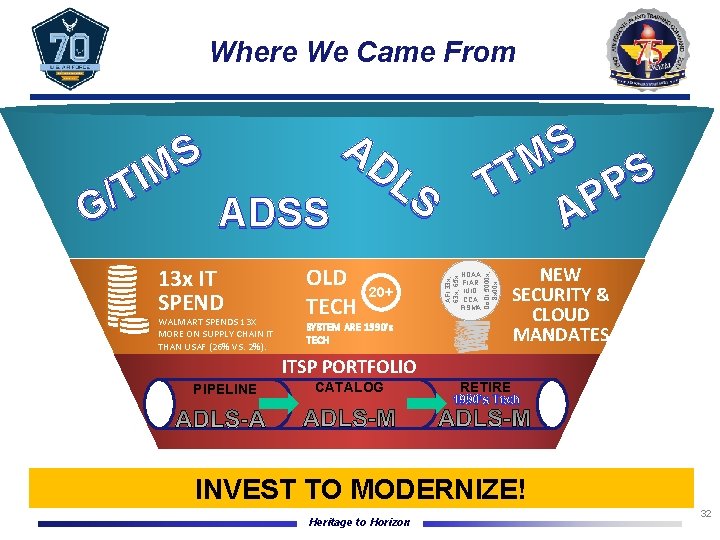
Where We Came From WALMART SPENDS 13 X MORE ON SUPPLY CHAIN IT THAN USAF (26% VS. 2%). OLD TECH 20+ NDAA FIAR IUID CCA FISMA Do. DI 5000 x, 8 x 00 x 13 x IT SPEND S M S T T P P A AFI 33 x, 63 x, 65 x S M I T / G ADSS AD LS SYSTEM ARE 1990’s TECH NEW SECURITY & CLOUD MANDATES ITSP PORTFOLIO PIPELINE CATALOG RETIRE 1990’s Tech INVEST TO MODERNIZE! Heritage to Horizon 32
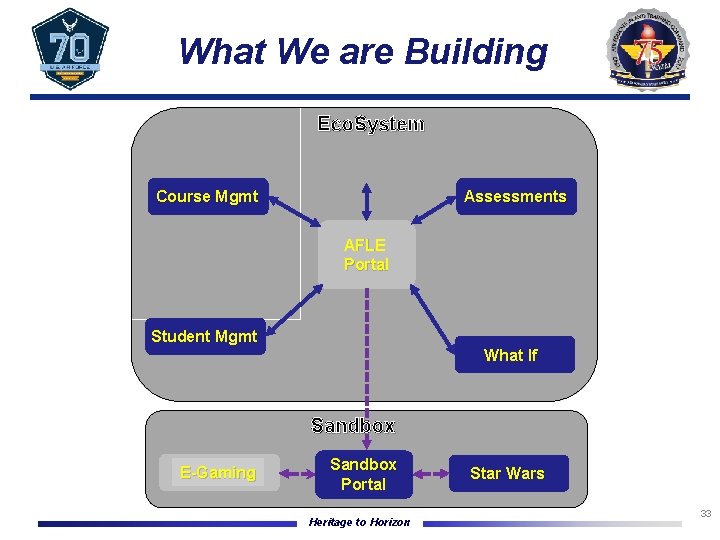
What We are Building Eco. System Course Mgmt Assessments AFLE Portal Student Mgmt What If Sandbox E-Gaming Sandbox Portal Heritage to Horizon Star Wars 33
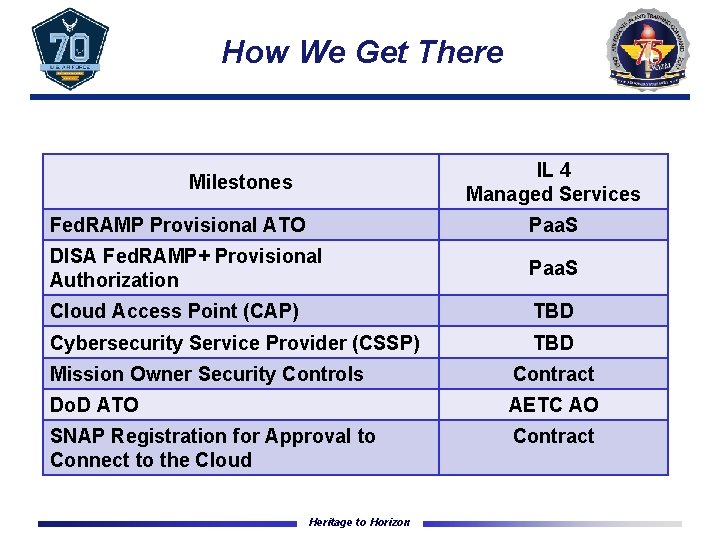
How We Get There IL 4 Managed Services Milestones Fed. RAMP Provisional ATO Paa. S DISA Fed. RAMP+ Provisional Authorization Paa. S Cloud Access Point (CAP) TBD Cybersecurity Service Provider (CSSP) TBD Mission Owner Security Controls Contract Do. D ATO AETC AO SNAP Registration for Approval to Connect to the Cloud Contract Heritage to Horizon

CLOSING THOUGHTS Heritage to Horizon 35

Closing Thoughts n It’s all about the information! n RMF is complex, hire an expert or plan to do a lot of research n Thorough contracts make for a successful Cloud investment n Know Your references… Heritage to Horizon 36
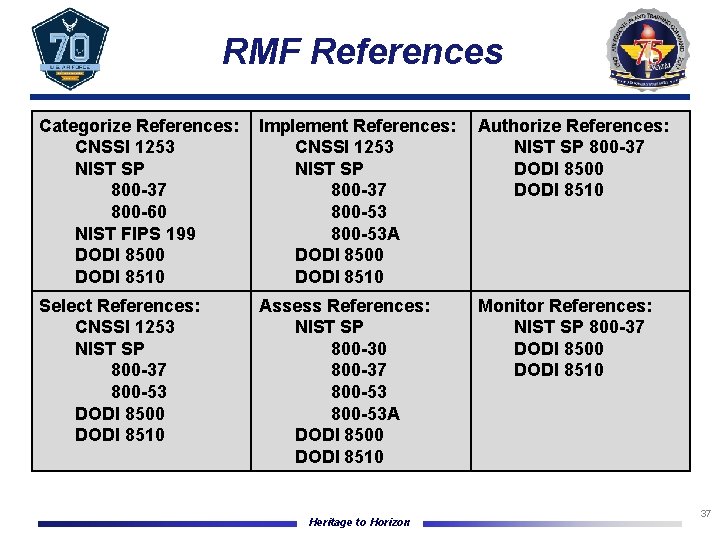
RMF References Categorize References: Implement References: CNSSI 1253 NIST SP 800 -37 800 -60 800 -53 NIST FIPS 199 800 -53 A DODI 8500 DODI 8510 Authorize References: NIST SP 800 -37 DODI 8500 DODI 8510 Select References: CNSSI 1253 NIST SP 800 -37 800 -53 DODI 8500 DODI 8510 Monitor References: NIST SP 800 -37 DODI 8500 DODI 8510 Assess References: NIST SP 800 -30 800 -37 800 -53 A DODI 8500 DODI 8510 Heritage to Horizon 37
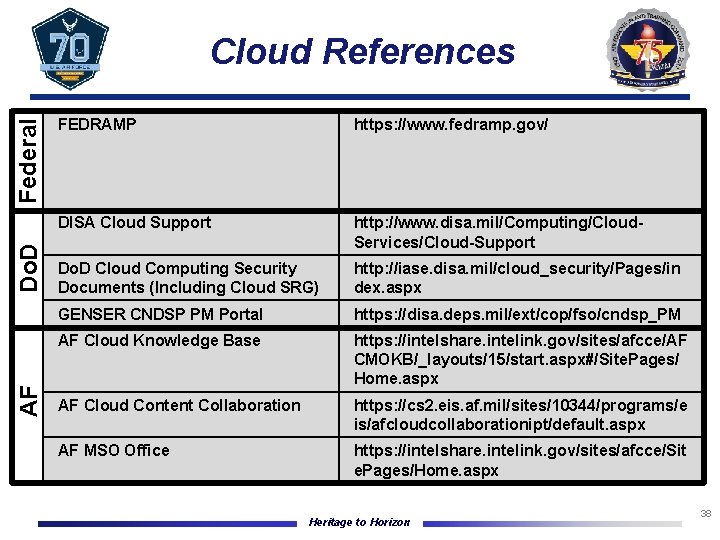
AF Do. D Federal Cloud References FEDRAMP https: //www. fedramp. gov/ DISA Cloud Support http: //www. disa. mil/Computing/Cloud. Services/Cloud-Support Do. D Cloud Computing Security Documents (Including Cloud SRG) http: //iase. disa. mil/cloud_security/Pages/in dex. aspx GENSER CNDSP PM Portal https: //disa. deps. mil/ext/cop/fso/cndsp_PM AF Cloud Knowledge Base https: //intelshare. intelink. gov/sites/afcce/AF CMOKB/_layouts/15/start. aspx#/Site. Pages/ Home. aspx AF Cloud Content Collaboration https: //cs 2. eis. af. mil/sites/10344/programs/e is/afcloudcollaborationipt/default. aspx AF MSO Office https: //intelshare. intelink. gov/sites/afcce/Sit e. Pages/Home. aspx Heritage to Horizon 38

Questions? Heritage to Horizon 39

Backup Slides Heritage to Horizon 40

Clinger Cohen Act (6) INFORMATION TECHNOLOGY. —The term ‘‘information technology’’— n (A) with respect to an executive agency means any equipment or interconnected system or subsystem of equipment, used in the automatic acquisition, storage, analysis, evaluation, manipulation, management, movement, control, display, switching, interchange, transmission, or reception of data or information by the executive agency, if the equipment is used by the executive agency directly or is used by a contractor under a contract with the executive agency that requires the use— n (i) of that equipment; or n (ii) of that equipment to a significant extent in the performance of a service or the furnishing of a product; n (B) includes computers, ancillary equipment (including imaging peripherals, input, output, and storage devices necessary for security and surveillance), peripheral equipment designed to be controlled by the central processing unit of a computer, software, firmware and similar procedures, services (including support services), and related resources; but n (C) does not include any equipment acquired by a federal contractor incidental to a federal contract. n Heritage to Horizon 41
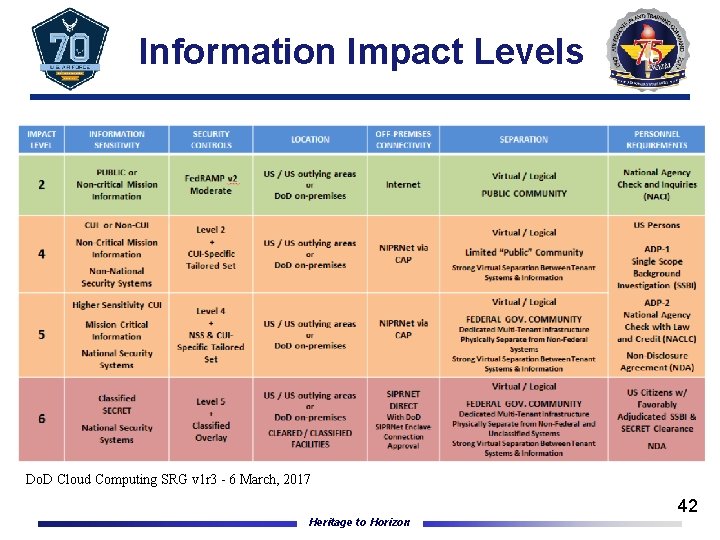
Information Impact Levels Do. D Cloud Computing SRG v 1 r 3 - 6 March, 2017 Heritage to Horizon 42
- Slides: 42