Supply Chain Risk Management Framework Supply Chain Risk









- Slides: 32

Supply Chain Risk Management Framework Supply Chain Risk Leadership Council 4 Oct 2007 Confidential 1

Overview Scope § Develop a Supply Chain Risk Mgmt Framework that will allow SCLRC members to work from common terms of reference and that will help guide future SCLRC activities Deliverables § This presentation § Adjustments as they become necessary Confidential 2

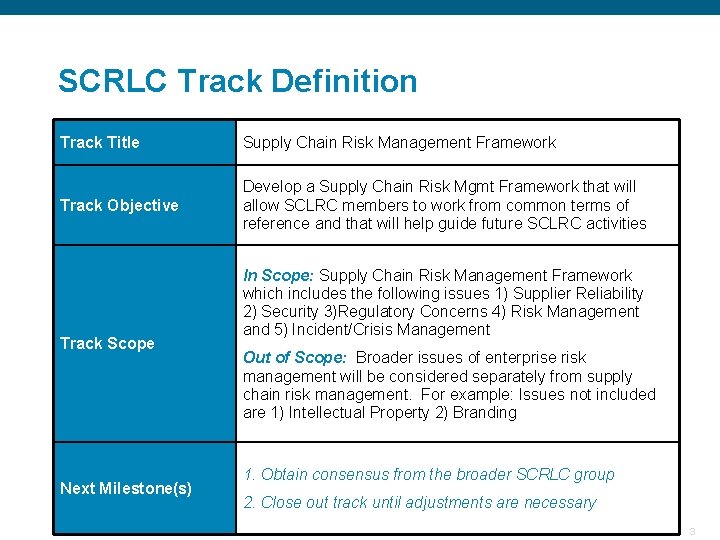
SCRLC Track Definition Track Title Supply Chain Risk Management Framework Track Objective Develop a Supply Chain Risk Mgmt Framework that will allow SCLRC members to work from common terms of reference and that will help guide future SCLRC activities Track Scope Next Milestone(s) In Scope: Supply Chain Risk Management Framework which includes the following issues 1) Supplier Reliability 2) Security 3)Regulatory Concerns 4) Risk Management and 5) Incident/Crisis Management Out of Scope: Broader issues of enterprise risk management will be considered separately from supply chain risk management. For example: Issues not included are 1) Intellectual Property 2) Branding 1. Obtain consensus from the broader SCRLC group 2. Close out track until adjustments are necessary Confidential 3

Team Members and Sources Team Members § Ely Kahn and Andrew Cox, TSA § Tim Astley, Zurich § Brent Myers, Fed. Ex § Craig Babcock, P&G § Ravi Anupindi, University of Michigan Sources § Committee of Sponsoring Organizations of the Treadway Commission (COSO), Enterprise Risk Management - Integrated Framework, 2004 § Supply Chain Risks and Risk Sharing Instruments, Robert Lindroth & Andreas Norrman, 2001 Confidential 4

Definition of SCRM Supply Chain Risk Management (SCRM) is the practice of managing the risk of any factor or event that can materially disrupt a supply chain whether within a single company or spread across multiple companies. The ultimate purpose of supply chain risk management is to enable cost avoidance, customer service, and market position. Supply chain risks can be grouped into 3 broad categories: physical, process, and institutional risks Confidential 5

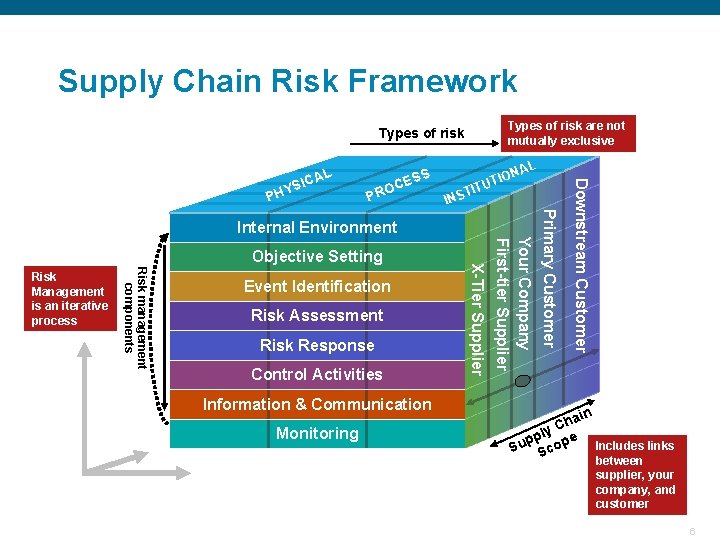
Supply Chain Risk Framework Types of risk are not mutually exclusive Types of risk YS PH ESS OC PR L NA O I UT TIT INS Event Identification Risk Assessment Risk Response Control Activities Information & Communication Monitoring Your Company First-tier Supplier Risk management components Risk Management is an iterative process X-Tier Supplier Objective Setting Primary Customer Internal Environment Downstream Customer L ICA n hai C ly pp ope Includes links u S Sc between supplier, your company, and customer Confidential 6

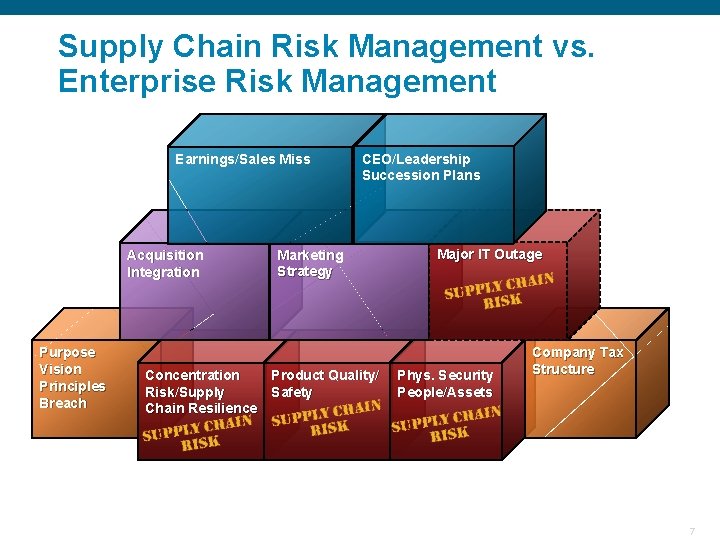
Supply Chain Risk Management vs. Enterprise Risk Management Earnings/Sales Miss Acquisition Integration Purpose Vision Principles Breach CEO/Leadership Succession Plans Marketing Strategy Concentration Product Quality/ Risk/Supply Safety Chain Resilience Confidential Major IT Outage Phys. Security People/Assets Company Tax Structure 7

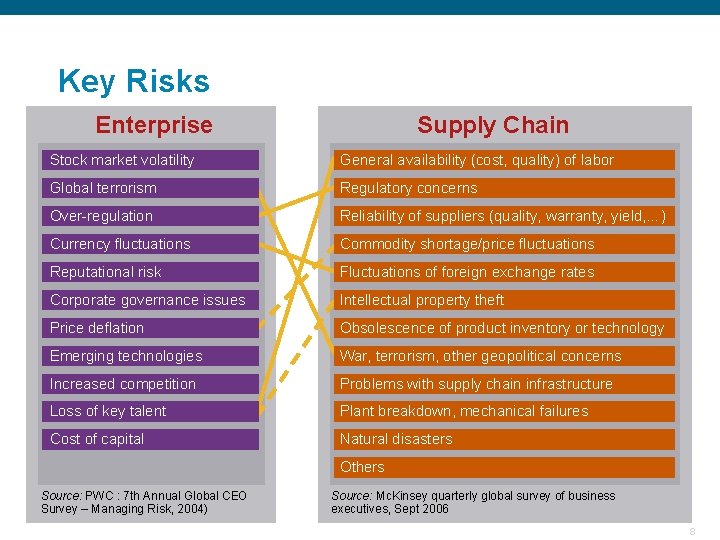
Key Risks Enterprise Supply Chain Stock market volatility General availability (cost, quality) of labor Global terrorism Regulatory concerns Over-regulation Reliability of suppliers (quality, warranty, yield, …) Currency fluctuations Commodity shortage/price fluctuations Reputational risk Fluctuations of foreign exchange rates Corporate governance issues Intellectual property theft Price deflation Obsolescence of product inventory or technology Emerging technologies War, terrorism, other geopolitical concerns Increased competition Problems with supply chain infrastructure Loss of key talent Plant breakdown, mechanical failures Cost of capital Natural disasters Others Source: PWC : 7 th Annual Global CEO Survey – Managing Risk, 2004) Source: Mc. Kinsey quarterly global survey of business executives, Sept 2006 Confidential 8

Risk Management Components Confidential 9

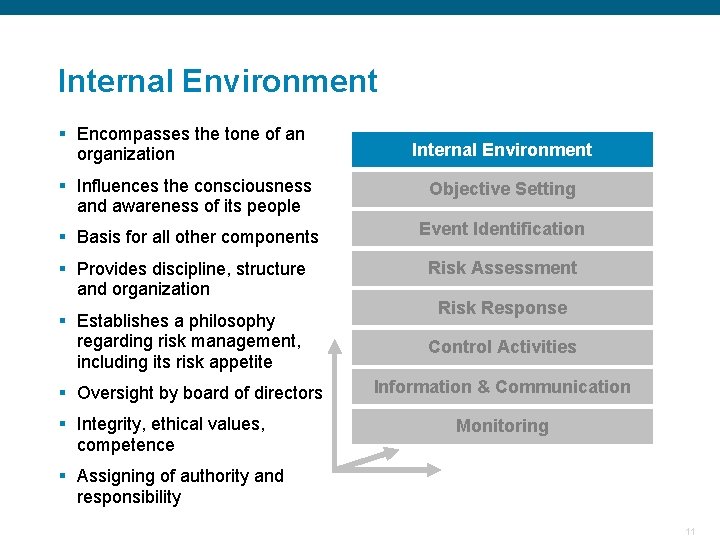
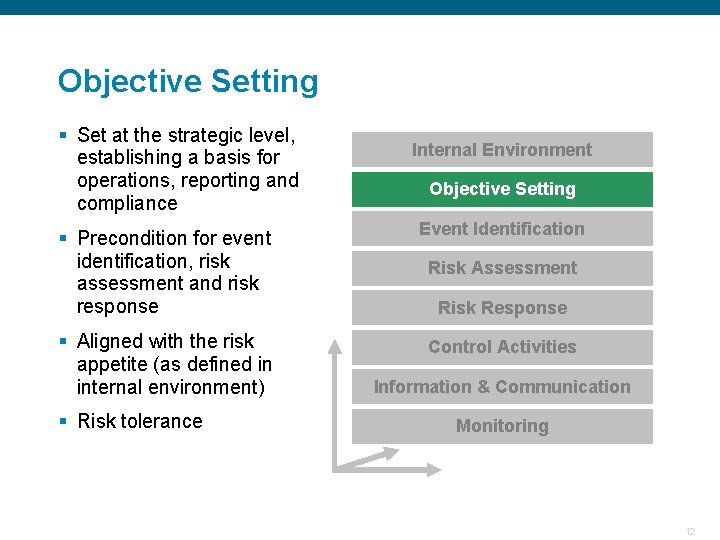
Risk Management Components of SCRM Internal Environment § Internal Environment Objective Setting § Objective Setting Event Identification § Event Identification Risk Assessment § Risk Response § Control Activities § Information & Communication Monitoring § Monitoring The components should be looked at as being interrelated. Confidential 10

Internal Environment § Encompasses the tone of an organization Internal Environment § Influences the consciousness and awareness of its people Objective Setting § Basis for all other components Event Identification § Provides discipline, structure and organization § Establishes a philosophy regarding risk management, including its risk appetite § Oversight by board of directors § Integrity, ethical values, competence Risk Assessment Risk Response Control Activities Information & Communication Monitoring § Assigning of authority and responsibility Confidential 11

Objective Setting § Set at the strategic level, establishing a basis for operations, reporting and compliance Internal Environment Objective Setting § Precondition for event identification, risk assessment and risk response Event Identification § Aligned with the risk appetite (as defined in internal environment) Control Activities Risk Assessment Risk Response Information & Communication § Risk tolerance Monitoring Confidential 12

Event Identification § Management identifies potential events Internal Environment § Differentiates risks and opportunities. Objective Setting § Events that may have a negative impact represent risks, which require management response § Events that may have a positive impact represent natural offsets (opportunities), which management channels back to strategy setting. § Involves identifying those incidents, occurring internally or externally, that could affect strategy and achievement of objectives. § Addresses how internal and external factors combine and interact to influence the risk profile. Confidential Event Identification Risk Assessment Risk Response Control Activities Information & Communication Monitoring 13

Event Identification Possible techniques Internal Environment § Event inventories Objective Setting § Scenario analysis § Internal analysis Event Identification § Escalation or threshold triggers Risk Assessment § Facilitated workshops and interviews § Process flow analysis § Leading event indicators Risk Response Control Activities Information & Communication Monitoring § Loss event data methodologies § Interdependencies Confidential 14

Event Identification Categorization of events (with reference to other framework axes), e. g. § External Internal Environment Objective Setting Event Identification - Economic - Environment Risk Assessment - Political Risk Response - Social Control Activities - Technological § Internal Information & Communication - Infrastructure Monitoring - Personnel - Process - Technology Confidential 15

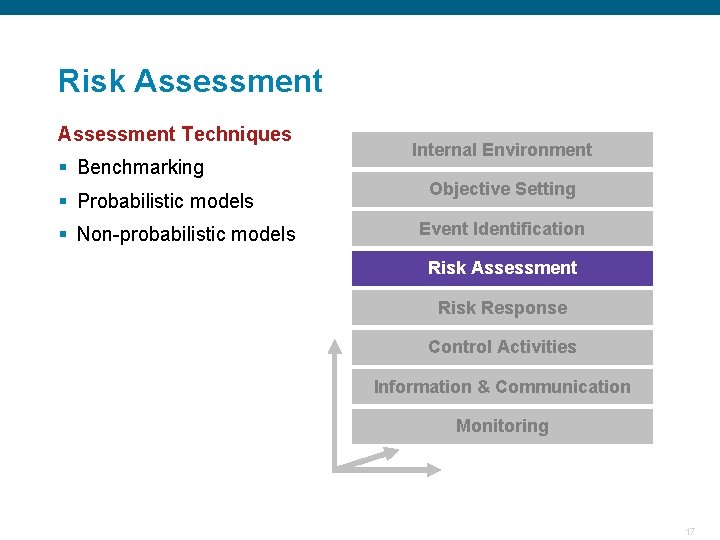
Risk Assessment § Allows an entity to understand the extent to which potential events might impact objectives. Internal Environment Objective Setting § Assesses risks from two perspectives: Event Identification - Likelihood - Impact § Employs a combination of both qualitative and quantitative risk assessment methodologies. Risk Assessment Risk Response § Relates time horizons to objective horizons. Control Activities § Assesses risk on both an inherent and a residual basis. Information & Communication Monitoring § Impact of events should be assessed individually or by category across the entity Confidential 16

Risk Assessment Techniques § Benchmarking Internal Environment Objective Setting § Probabilistic models § Non-probabilistic models Event Identification Risk Assessment Risk Response Control Activities Information & Communication Monitoring Confidential 17

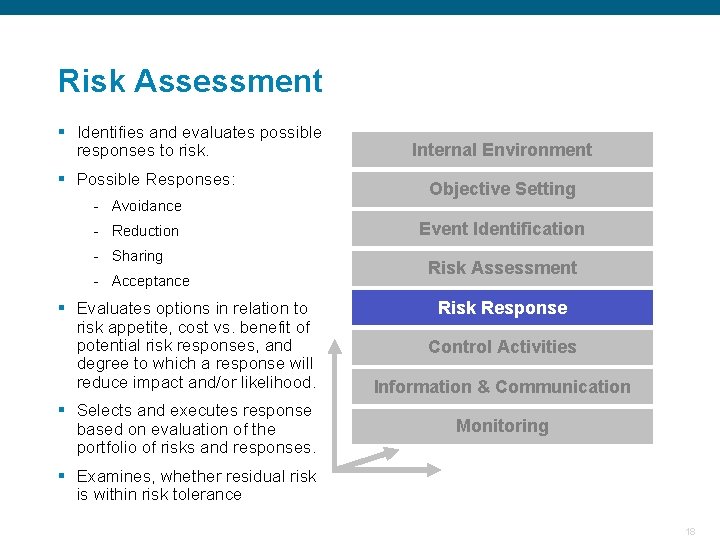
Risk Assessment § Identifies and evaluates possible responses to risk. § Possible Responses: Internal Environment Objective Setting - Avoidance Event Identification - Reduction - Sharing Risk Assessment - Acceptance § Evaluates options in relation to risk appetite, cost vs. benefit of potential risk responses, and degree to which a response will reduce impact and/or likelihood. § Selects and executes response based on evaluation of the portfolio of risks and responses. Risk Response Control Activities Information & Communication Monitoring § Examines, whether residual risk is within risk tolerance Confidential 18

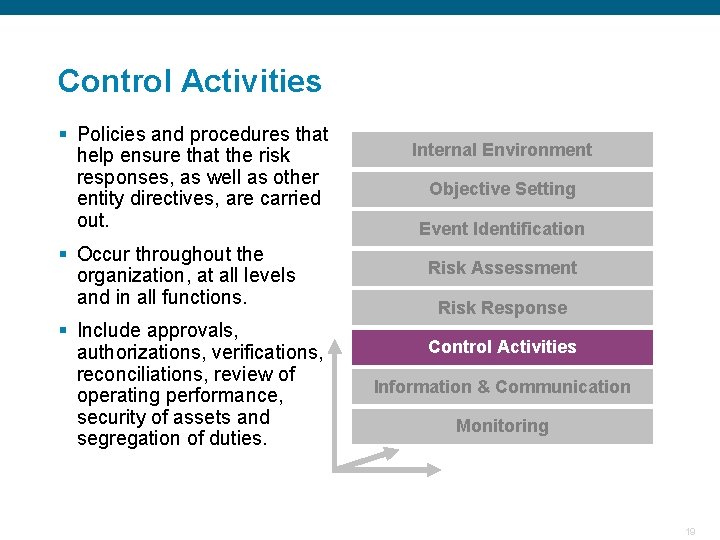
Control Activities § Policies and procedures that help ensure that the risk responses, as well as other entity directives, are carried out. § Occur throughout the organization, at all levels and in all functions. § Include approvals, authorizations, verifications, reconciliations, review of operating performance, security of assets and segregation of duties. Confidential Internal Environment Objective Setting Event Identification Risk Assessment Risk Response Control Activities Information & Communication Monitoring 19

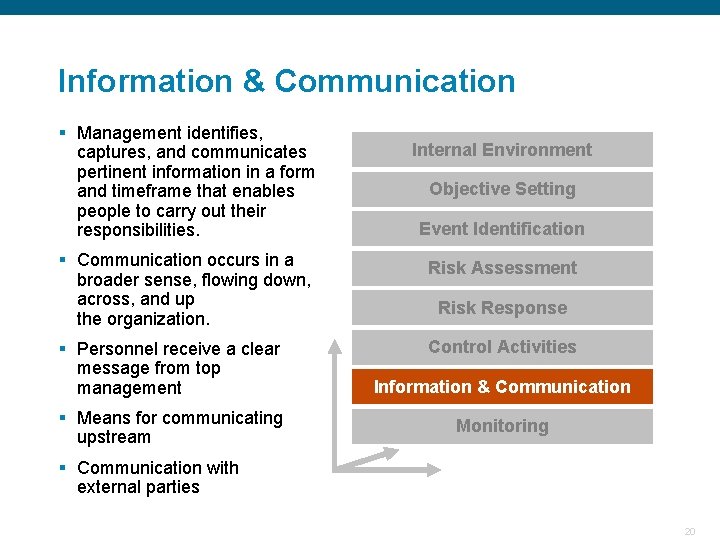
Information & Communication § Management identifies, captures, and communicates pertinent information in a form and timeframe that enables people to carry out their responsibilities. Internal Environment Objective Setting Event Identification § Communication occurs in a broader sense, flowing down, across, and up the organization. Risk Assessment § Personnel receive a clear message from top management Control Activities § Means for communicating upstream Risk Response Information & Communication Monitoring § Communication with external parties Confidential 20

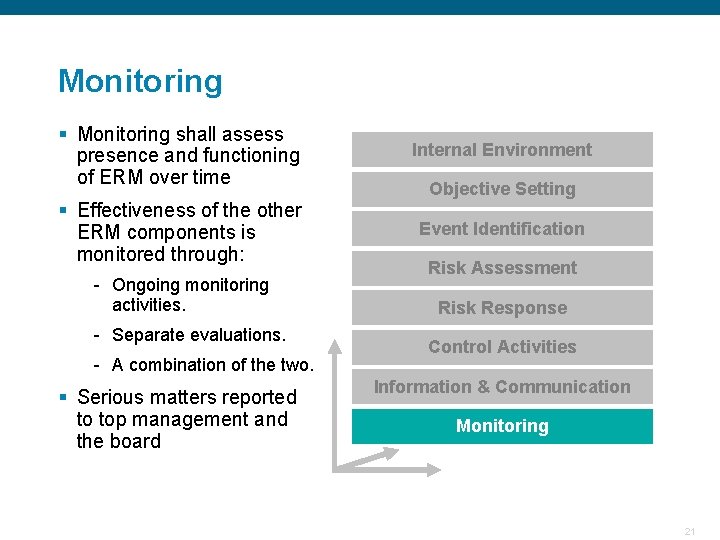
Monitoring § Monitoring shall assess presence and functioning of ERM over time Internal Environment § Effectiveness of the other ERM components is monitored through: Event Identification - Ongoing monitoring activities. Objective Setting Risk Assessment Risk Response - Separate evaluations. - A combination of the two. § Serious matters reported to top management and the board Confidential Control Activities Information & Communication Monitoring 21

Issues to be aware of § Risk Management is an iterative discipline---Risks must be revisited on a regular basis § Need to balance the audit approach (avoid or mitigate risk) vs. proactive approach (deal actively with risks) § Need to recognise role of risk management in realizing strategic objectives § Risk should be seen as a necessary component and factor in strategic opportunity. § There might be an economic benefit in accepting a particular risk, the focus should be on the risk-return tradeoff § Risk quantification needs to be included as well as the focus on risk mitigation. § Need to adequately reflected the external environment even though some risk-factors are beyond management’s control § Need to recognise correlation of risks – often difficult § Risk management is a coordinating function § Risk management is a dynamic process, not a check list approach § Need to recognise risk to reputation Confidential 22

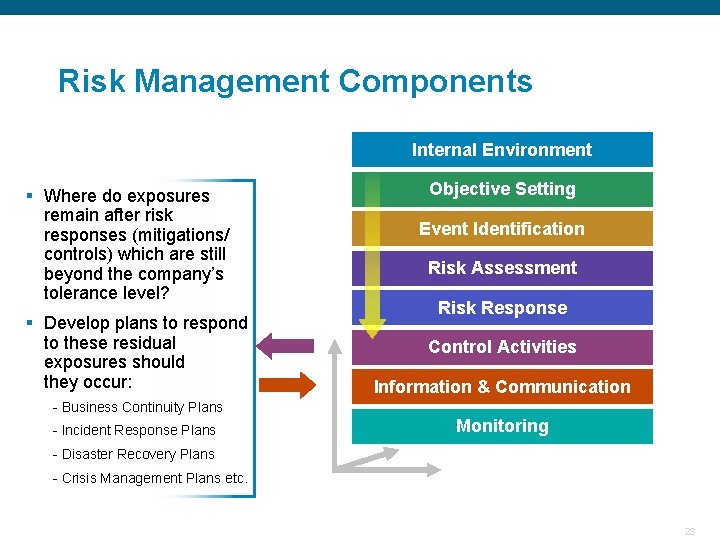
Risk Management Components Internal Environment Objective Setting § Where do exposures remain after risk responses (mitigations/ controls) which are still beyond the company’s tolerance level? Event Identification Risk Assessment Risk Response § Develop plans to respond to these residual exposures should they occur: Control Activities Information & Communication - Business Continuity Plans Monitoring - Incident Response Plans - Disaster Recovery Plans - Crisis Management Plans etc. Confidential 23

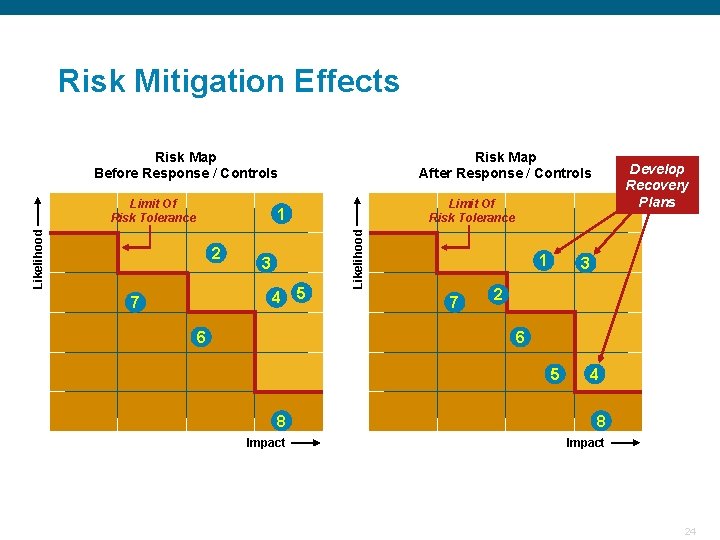
Risk Mitigation Effects Risk Map Before Response / Controls Limit Of Risk Tolerance Risk Map After Response / Controls Limit Of Risk Tolerance 3 4 7 5 6 Likelihood 1 2 Develop Recovery Plans 1 7 3 2 6 5 4 8 8 Impact Confidential 24

Incident Management “Planning P” http: //www. dfg. ca. gov/ospr/organizational/msb/readiness/2006%20 IMH. pdf Confidential 25

Types of Risk Confidential 26

Types of Risk § Physical Disruptions: Destruction of critical infrastructure in the supply chain - Critical Infrastructure includes the material components or assets necessary for the continuous operation of the transportation system including equipment and personnel § Process Disruptions: Events that involve day-to-day operations of supply chain processes - Processes include the rules, actions, decisions, and information flows that give life to the physical level and are necessary for efficient and effective operation of the transportation system. Processes are what allow material components to work together—physically or virtually—as a system or supply chain PH AL YSIC L NA ESS TIO C U O T I T PR INS § Institutional Disruptions: Events that involve changes in company or supply-network governance and strategy. - Institutional considerations include the policies, guidance, and organizations that empower and constrain the operation of the supply chain to meet large-scale company goals. Public sector examples of institutional disruptions include federal legislation, national policies, and state regulations. Private sector examples include company reorganizations, mergers, market shifts, and technology breakthroughs. Confidential 27

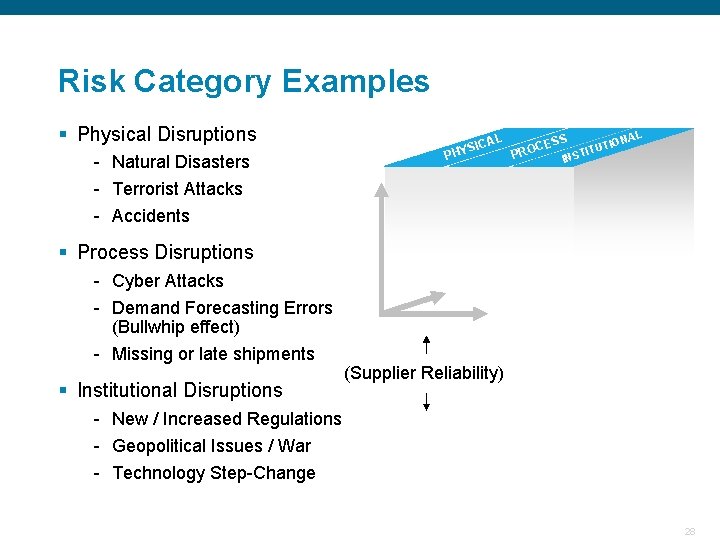
Risk Category Examples § Physical Disruptions AL YSIC PH - Natural Disasters - Terrorist Attacks - Accidents L NA ESS TIO C U O T I T PR INS § Process Disruptions - Cyber Attacks - Demand Forecasting Errors (Bullwhip effect) - Missing or late shipments § Institutional Disruptions (Supplier Reliability) - New / Increased Regulations - Geopolitical Issues / War - Technology Step-Change Confidential 28

Supply Chain Scope Confidential 29

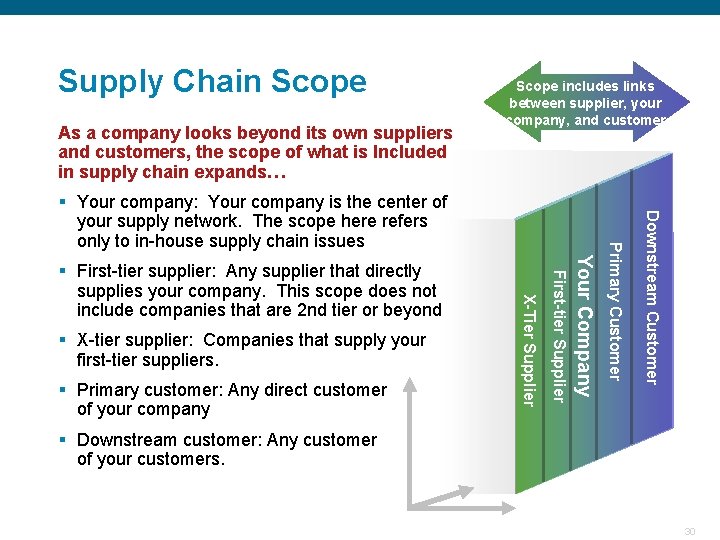
Supply Chain Scope As a company looks beyond its own suppliers and customers, the scope of what is Included in supply chain expands… Scope includes links between supplier, your company, and customer Downstream Customer Your Company § Primary customer: Any direct customer of your company First-tier Supplier § X-tier supplier: Companies that supply your first-tier suppliers. X-Tier Supplier § First-tier supplier: Any supplier that directly supplies your company. This scope does not include companies that are 2 nd tier or beyond Primary Customer § Your company: Your company is the center of your supply network. The scope here refers only to in-house supply chain issues § Downstream customer: Any customer of your customers. Confidential 30

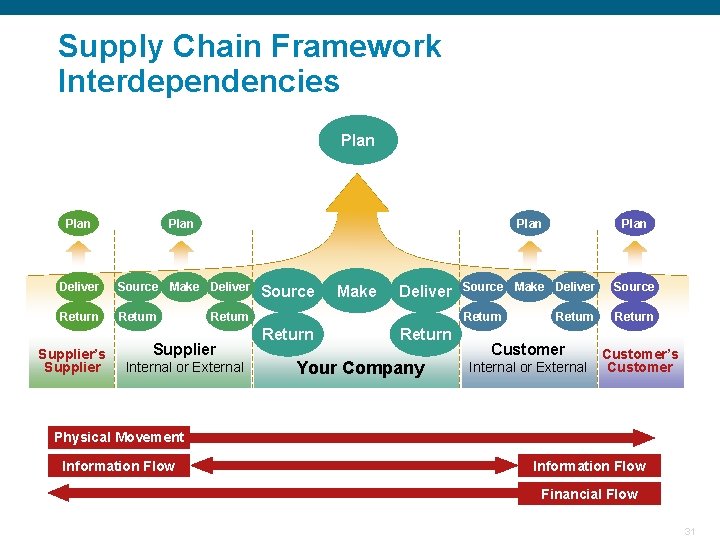
Supply Chain Framework Interdependencies Plan Deliver Source Make Deliver Return Supplier’s Supplier Source Make Deliver Return Supplier Internal or External Return Your Company Plan Source Make Deliver Source Return Customer Internal or External Customer’s Customer Physical Movement Information Flow Financial Flow Confidential 31

Next Steps § Discussion - Close out track? - How do we use this framework? Confidential 32