PeertoPeer Security in Wireless Ad Hoc Networks Common

















- Slides: 55

Peer-to-Peer Security in Wireless Ad Hoc Networks + Common. Sense. Net Jean-Pierre Hubaux EPFL, Switzerland 1

Outline g g Brief presentation of the MICS/Terminodes project Mobility helps peer-to-peer security Cooperation between nodes in multi-hop wireless networks Three more projects : i. Cooperation without incentives i. Power-efficient broadcast in all-wireless networks i. Water management by means of sensor networks 2

National Competence Centers in Research g g g Initiative of the Swiss National Science Foundation Call for proposals in late 1998, for several scientific areas (including Medicine and Physics) Proposals have to be substantial (yearly budget around 3 Mio Euros/year) and long term (from 2001 to 2010) 200+ proposals have been submitted in the first round 14 proposals finally selected (in 2000) The Mobile Infomation and Communication Systems or Terminodes proposal is the only selected in the area of communications; official start : November 2001 3

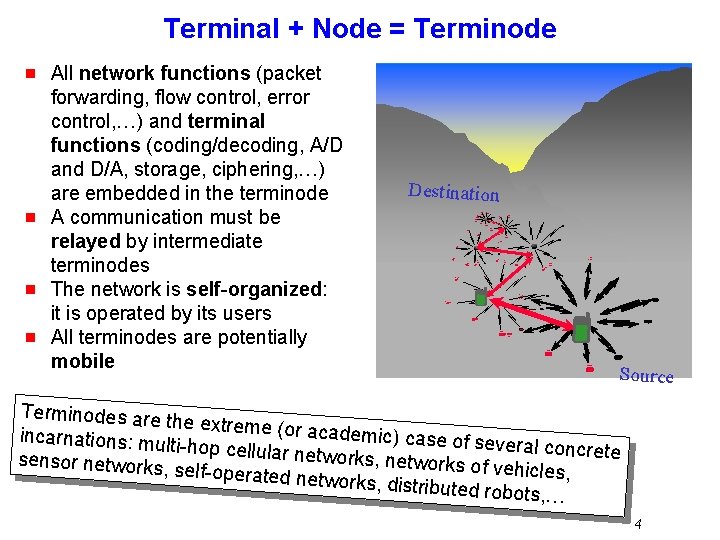
Terminal + Node = Terminode g g All network functions (packet forwarding, flow control, error control, …) and terminal functions (coding/decoding, A/D and D/A, storage, ciphering, …) are embedded in the terminode A communication must be relayed by intermediate terminodes The network is self-organized: it is operated by its users All terminodes are potentially mobile Destination Source Terminodes are the extreme (or a cademic) case o incarnations: mu f several concrete lti-hop cellular ne tw o rks, networks of sensor networks vehicles, , self-operated n etworks, distribu ted robots, … 4

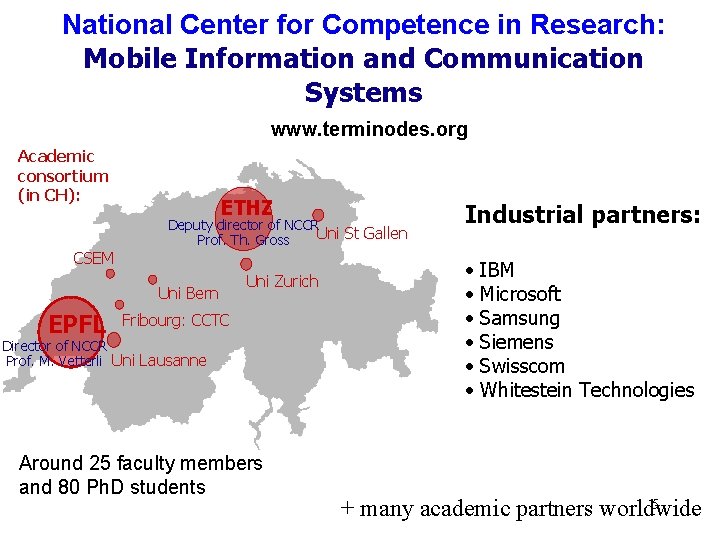
National Center for Competence in Research: Mobile Information and Communication Systems www. terminodes. org Academic consortium (in CH): ETHZ Deputy director of NCCR Uni St Gallen Prof. Th. Gross CSEM Uni Bern EPFL Uni Zurich Fribourg: CCTC Director of NCCR Prof. M. Vetterli Uni Lausanne Around 25 faculty members and 80 Ph. D students Industrial partners: • • • IBM Microsoft Samsung Siemens Swisscom Whitestein Technologies 5 + many academic partners worldwide

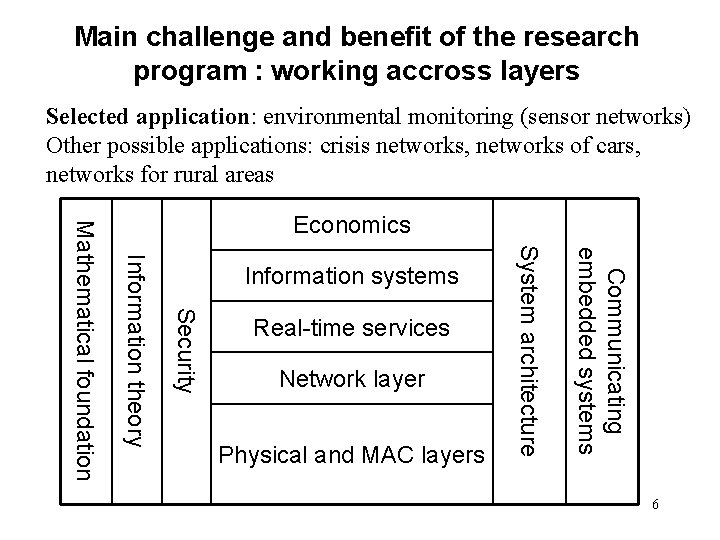
Main challenge and benefit of the research program : working accross layers Selected application: environmental monitoring (sensor networks) Other possible applications: crisis networks, networks of cars, networks for rural areas Network layer Physical and MAC layers Communicating embedded systems Real-time services System architecture Information systems Security Information theory Mathematical foundation Economics 6

Mobility Helps Peer-to-Peer Security Peer-to-peer Authentication and Key Establishment in Mobile Networks Joint work with Levente Buttyan+ and Srdjan Capkun + Now with Laboratory of Cryptography and Systems Security (Cry. S) Department of Telecommunications, Budapest University of Technology and Economics 7

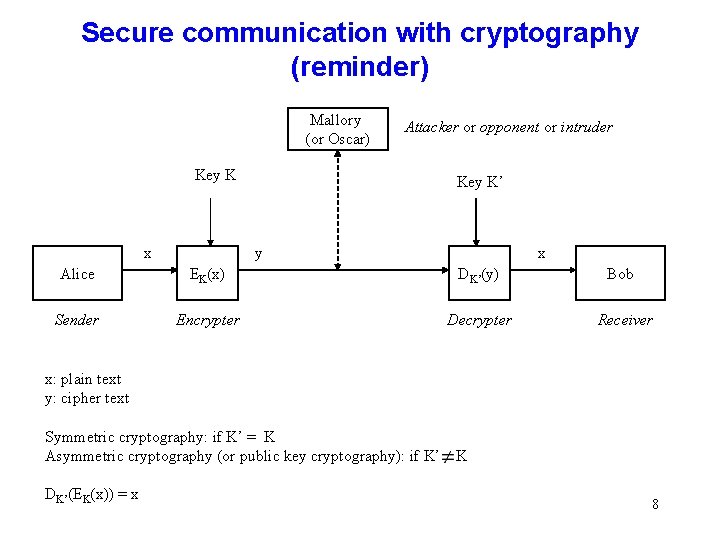
Secure communication with cryptography (reminder) Mallory (or Oscar) Attacker or opponent or intruder Key K x Key K’ y x Alice EK(x) DK’(y) Sender Encrypter Decrypter Bob Receiver x: plain text y: cipher text Symmetric cryptography: if K’ = K Asymmetric cryptography (or public key cryptography): if K’ DK’(EK(x)) = x K 8

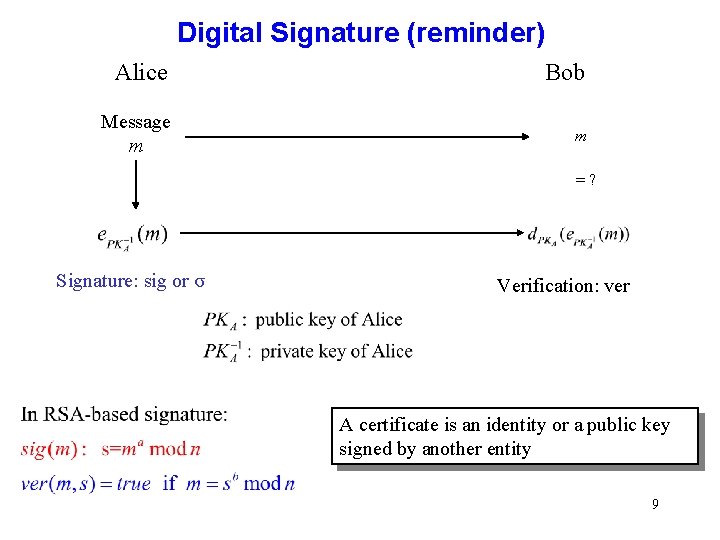
Digital Signature (reminder) Alice Bob Message m m =? Signature: sig or σ Verification: ver A certificate is an identity or a public key signed by another entity 9

Does mobility increase or reduce security ? g Very often, people move to increase security: g In spite of the popularity of PDAs and cellular phones, this mobility has not been exploited so far to provide digital security Mobility is usually perceived as a major security challenge: g g g i. Face to face meetings i. Transport of assets and physical documents i. Authentication by physical presence i. Wireless channel i. Unpredictable location of the user i. Sporadic availability of the user i. Higher vulnerability of the device i. Smaller computing capability of the device So far, client-server security has been considered as the priority (ebusiness, cellular telephony, …) Peer-to-peer security is still in its infancy 10

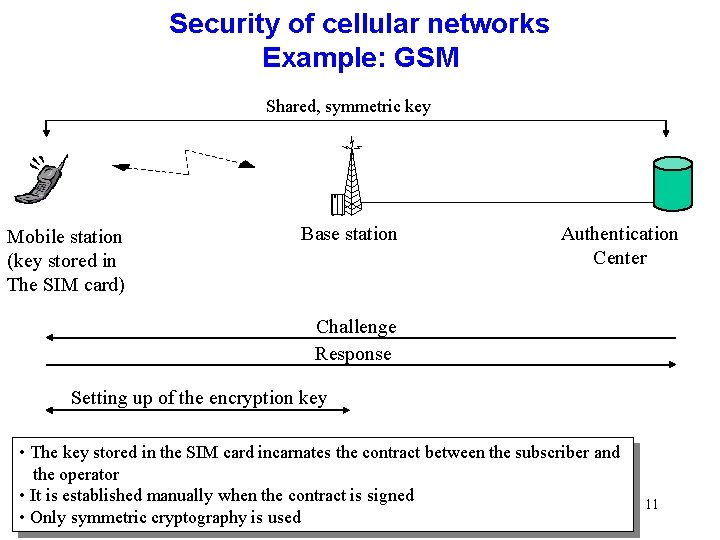
Security of cellular networks Example: GSM Shared, symmetric key Mobile station (key stored in The SIM card) Base station Authentication Center Challenge Response Setting up of the encryption key • The key stored in the SIM card incarnates the contract between the subscriber and the operator • It is established manually when the contract is signed • Only symmetric cryptography is used 11

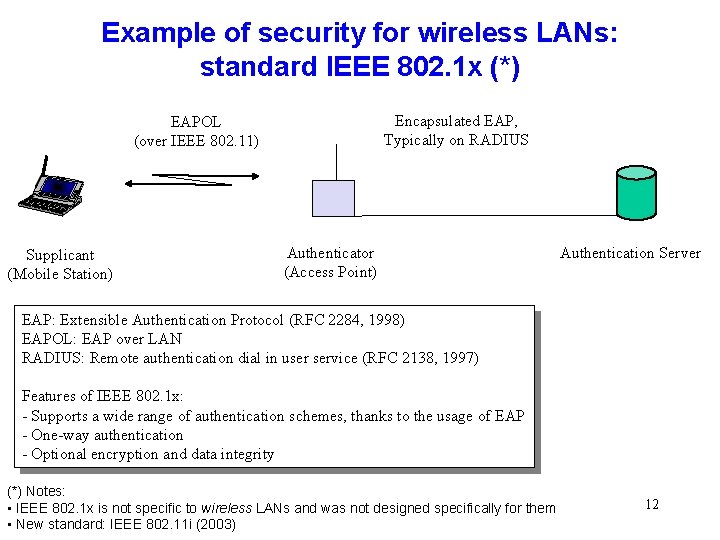
Example of security for wireless LANs: standard IEEE 802. 1 x (*) Encapsulated EAP, Typically on RADIUS EAPOL (over IEEE 802. 11) Supplicant (Mobile Station) Authenticator (Access Point) Authentication Server EAP: Extensible Authentication Protocol (RFC 2284, 1998) EAPOL: EAP over LAN RADIUS: Remote authentication dial in user service (RFC 2138, 1997) Features of IEEE 802. 1 x: - Supports a wide range of authentication schemes, thanks to the usage of EAP - One-way authentication - Optional encryption and data integrity (*) Notes: • IEEE 802. 1 x is not specific to wireless LANs and was not designed specifically for them • New standard: IEEE 802. 11 i (2003) 12

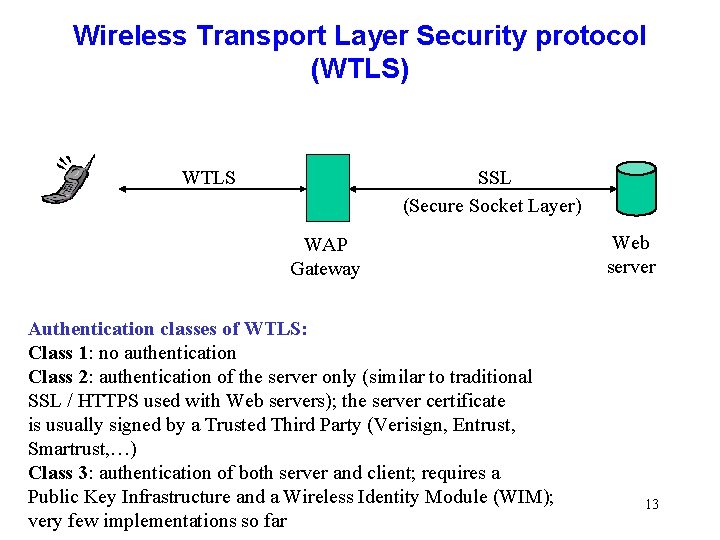
Wireless Transport Layer Security protocol (WTLS) SSL (Secure Socket Layer) WTLS WAP Gateway Authentication classes of WTLS: Class 1: no authentication Class 2: authentication of the server only (similar to traditional SSL / HTTPS used with Web servers); the server certificate is usually signed by a Trusted Third Party (Verisign, Entrust, Smartrust, …) Class 3: authentication of both server and client; requires a Public Key Infrastructure and a Wireless Identity Module (WIM); very few implementations so far Web server 13

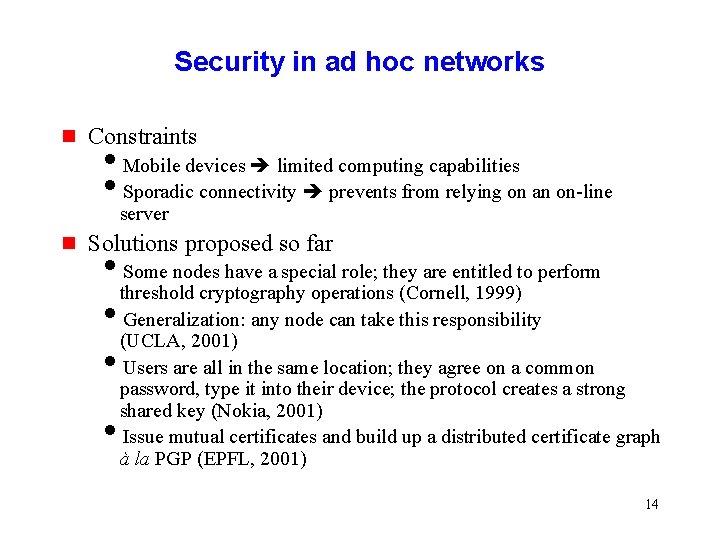
Security in ad hoc networks g Constraints i. Mobile devices limited computing capabilities i. Sporadic connectivity prevents from relying on an on-line server g Solutions proposed so far i. Some nodes have a special role; they are entitled to perform threshold cryptography operations (Cornell, 1999) i. Generalization: any node can take this responsibility (UCLA, 2001) i. Users are all in the same location; they agree on a common password, type it into their device; the protocol creates a strong shared key (Nokia, 2001) i. Issue mutual certificates and build up a distributed certificate graph à la PGP (EPFL, 2001) 14

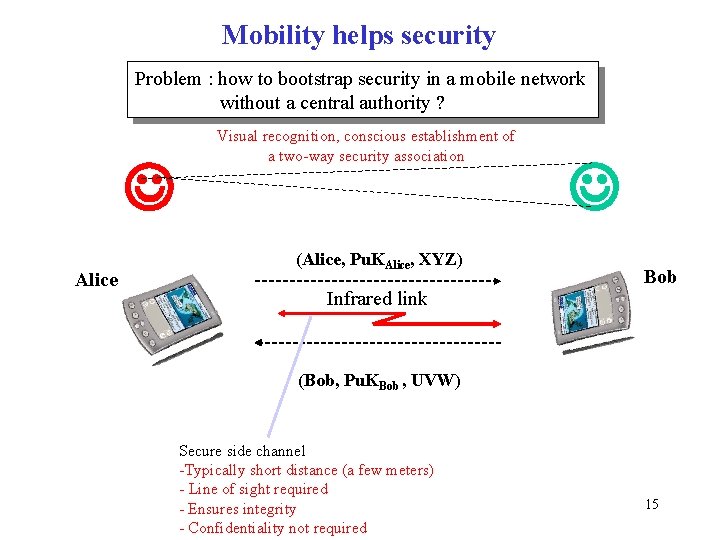
Mobility helps security Problem : how to bootstrap security in a mobile network without a central authority ? Alice Visual recognition, conscious establishment of a two-way security association (Alice, Pu. KAlice, XYZ) Infrared link Bob (Bob, Pu. KBob , UVW) Secure side channel -Typically short distance (a few meters) - Line of sight required - Ensures integrity - Confidentiality not required 15

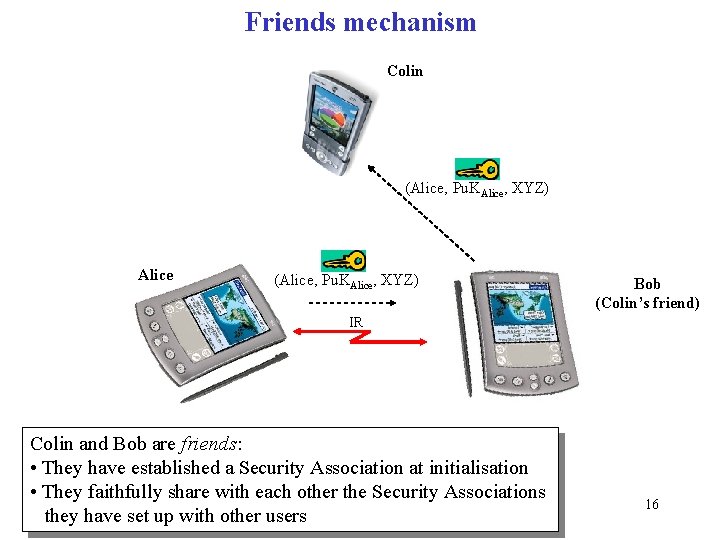
Friends mechanism Colin (Alice, Pu. KAlice, XYZ) Alice (Alice, Pu. KAlice, XYZ) Bob (Colin’s friend) IR Colin and Bob are friends: • They have established a Security Association at initialisation • They faithfully share with each other the Security Associations they have set up with other users 16

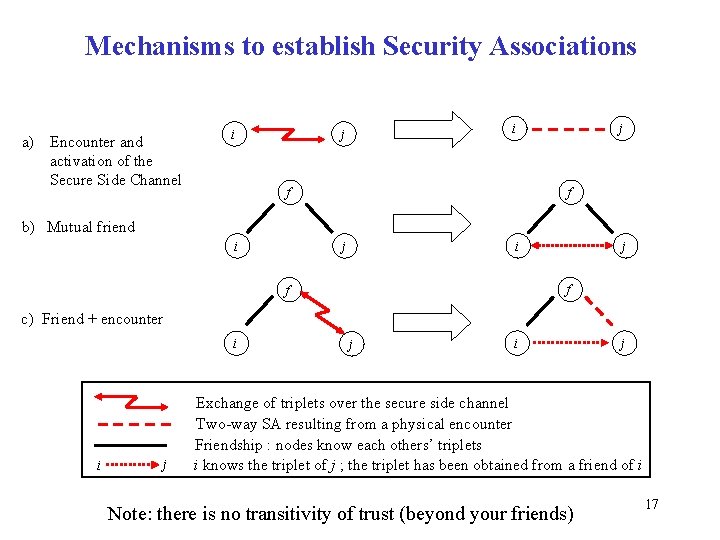
Mechanisms to establish Security Associations a) Encounter and activation of the Secure Side Channel i i j j f f b) Mutual friend i i j j f f c) Friend + encounter i i j j i j Exchange of triplets over the secure side channel Two-way SA resulting from a physical encounter Friendship : nodes know each others’ triplets i knows the triplet of j ; the triplet has been obtained from a friend of i Note: there is no transitivity of trust (beyond your friends) 17

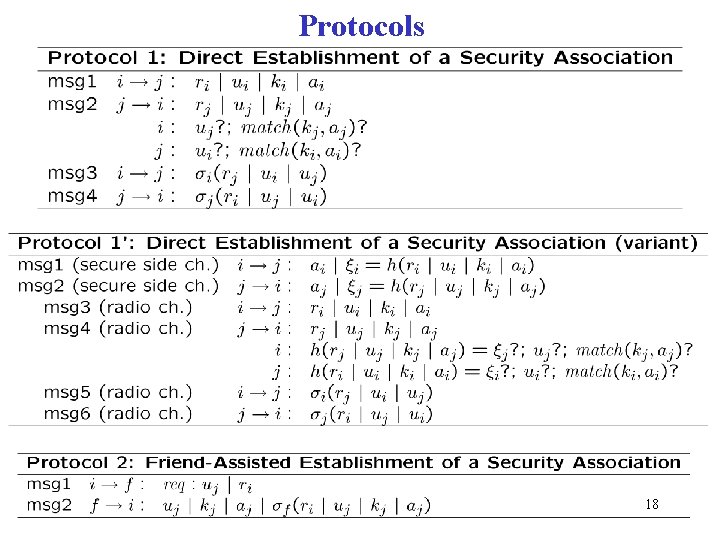
Protocols 18

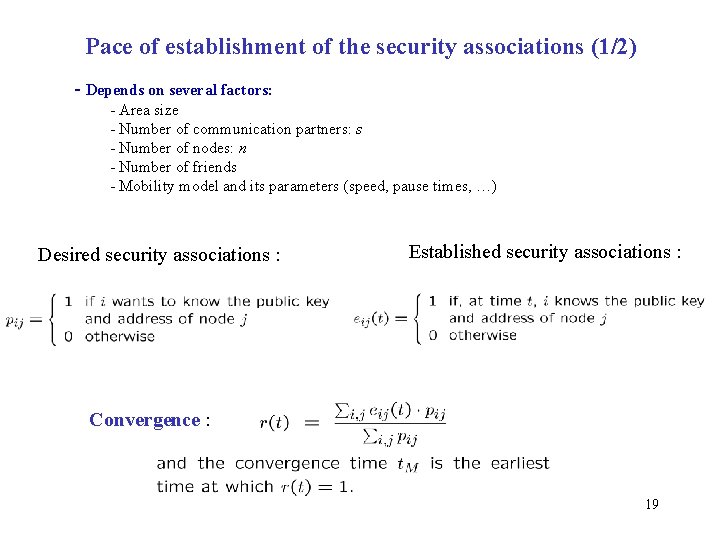
Pace of establishment of the security associations (1/2) - Depends on several factors: - Area size - Number of communication partners: s - Number of nodes: n - Number of friends - Mobility model and its parameters (speed, pause times, …) Desired security associations : Established security associations : Convergence : 19

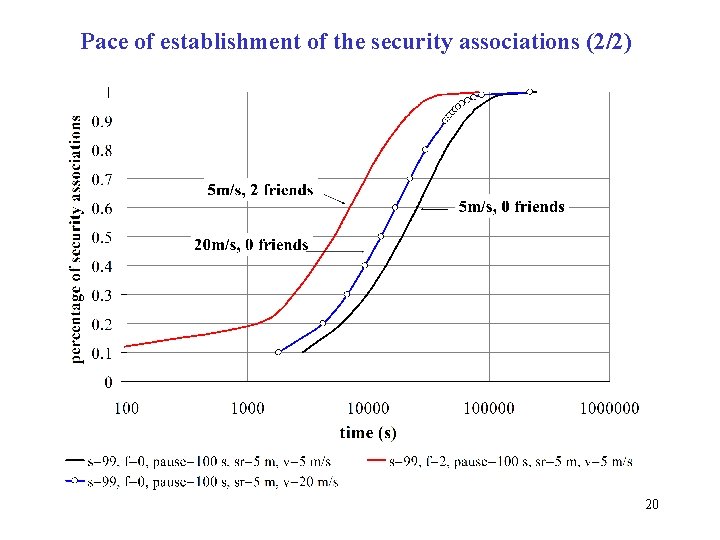
Pace of establishment of the security associations (2/2) 20

Conclusion on Mobility Helps Security • • • Mobility can help security in mobile ad hoc networks, from the networking layer up to the applications The proposed solution also supports re-keying The proposed solution can easily be implemented with both symmetric and asymmetric cryptography S. Capkun, J. P. Hubaux, and L. Buttyan Mobility Helps Security in Ad Hoc Networks Fourth ACM Symposium on Mobile Networking and Computing (Mobi. Hoc), Annapolis, June 2003 S. Capkun, L. Buttyan, and J. -P. Hubaux Self-Organized Public-Key Management for Mobile Ad Hoc Networks IEEE Transactions on Mobile Computing, Vol. 2, Nr. 1, 2003 21

Cooperation between Nodes in Hybrid Ad Hoc Networks Jean-Pierre Hubaux 1 Joint work with Naouel Ben Salem 1, Levente Buttyan 2, and Markus Jakobsson 3 EPFL/School of Information and Communication 2 Budapest University of Technology and Economics 3 RSA Labs 1 22

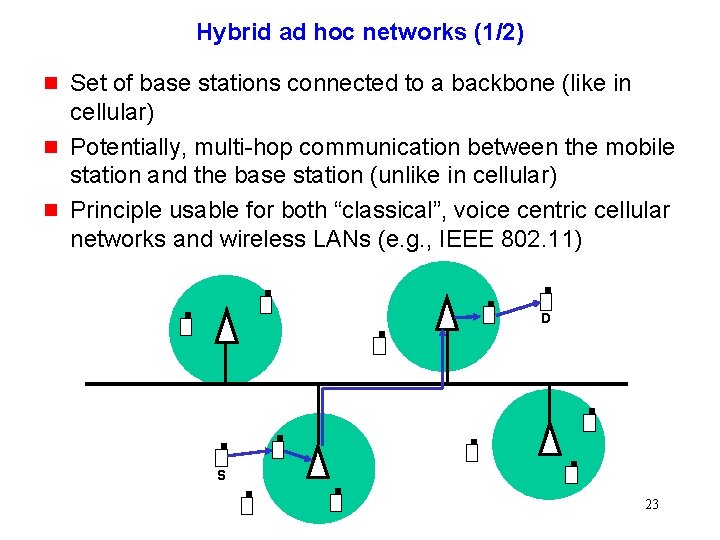
Hybrid ad hoc networks (1/2) g g g Set of base stations connected to a backbone (like in cellular) Potentially, multi-hop communication between the mobile station and the base station (unlike in cellular) Principle usable for both “classical”, voice centric cellular networks and wireless LANs (e. g. , IEEE 802. 11) D S 23

Hybrid ad hoc networks (2/2) g Expected benefits: i. Energy consumption of the mobile stations can be reduced i. Immediate side effect: Reduced interference i. Number of base stations (fixed antennas) can be reduced i. Coverage of the network can be increased i. Closely located mobile stations can communicate independently from the infrastructure (ad hoc networking) g Problem: How to encourage the nodes to relay packets for the benefit of other nodes? 24

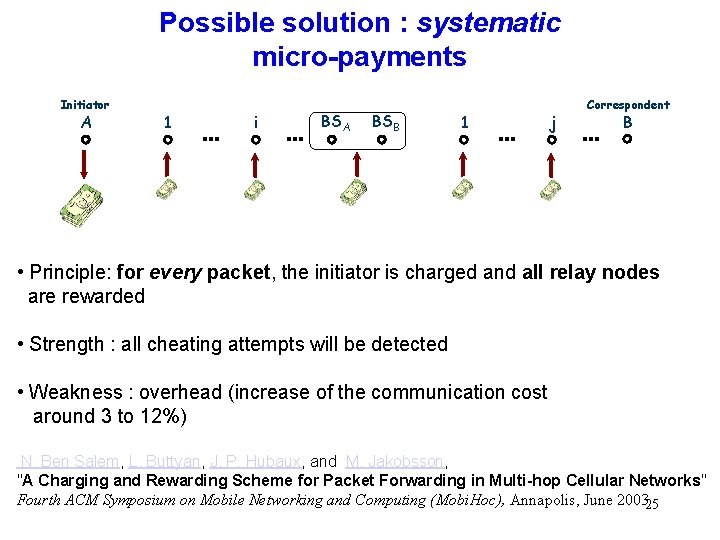
Possible solution : systematic micro-payments Initiator A 1 i BSA BSB 1 j Correspondent B • Principle: for every packet, the initiator is charged and all relay nodes are rewarded • Strength : all cheating attempts will be detected • Weakness : overhead (increase of the communication cost around 3 to 12%) N. Ben Salem, L. Buttyan, J. P. Hubaux, and M. Jakobsson, "A Charging and Rewarding Scheme for Packet Forwarding in Multi-hop Cellular Networks" Fourth ACM Symposium on Mobile Networking and Computing (Mobi. Hoc), Annapolis, June 200325

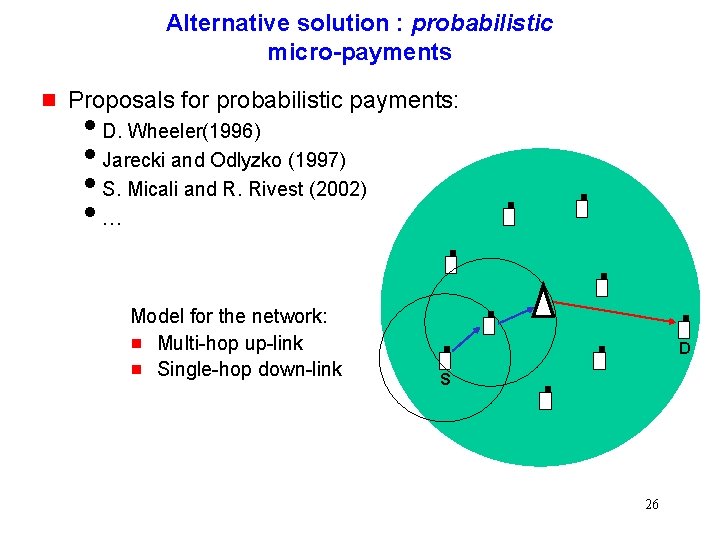
Alternative solution : probabilistic micro-payments g Proposals for probabilistic payments: i. D. Wheeler(1996) i. Jarecki and Odlyzko (1997) i. S. Micali and R. Rivest (2002) i… Model for the network: g Multi-hop up-link g Single-hop down-link D S 26

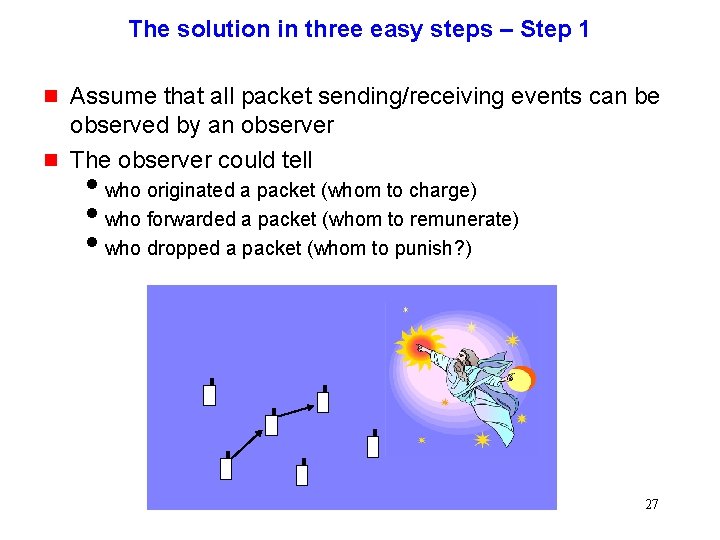
The solution in three easy steps – Step 1 g g Assume that all packet sending/receiving events can be observed by an observer The observer could tell iwho originated a packet (whom to charge) iwho forwarded a packet (whom to remunerate) iwho dropped a packet (whom to punish? ) 27

The solution in three easy steps – Step 2 g Assume that every node honestly reports its own sending/receiving events to the operator The operator could tell g Problems: g iwho originated a packet (whom to charge) iwho forwarded a packet (whom to remunerate) iwho dropped a packet (whom to punish? ) inodes may not be motivated to send reports inodes may lie (send false reports) ireporting all events may be a huge overhead 28

The solution in three easy steps – Step 3 g Nodes get paid for their reports nodes are motivated to send reports • Events to be reported are selected probabilistically this drastically reduces the overhead • Neighbors are remunerated as well this further increases the motivation to cooperate • Based on the received reports, the operator performs statistical analysis (auditing) this allows detection of cheating behavior 29

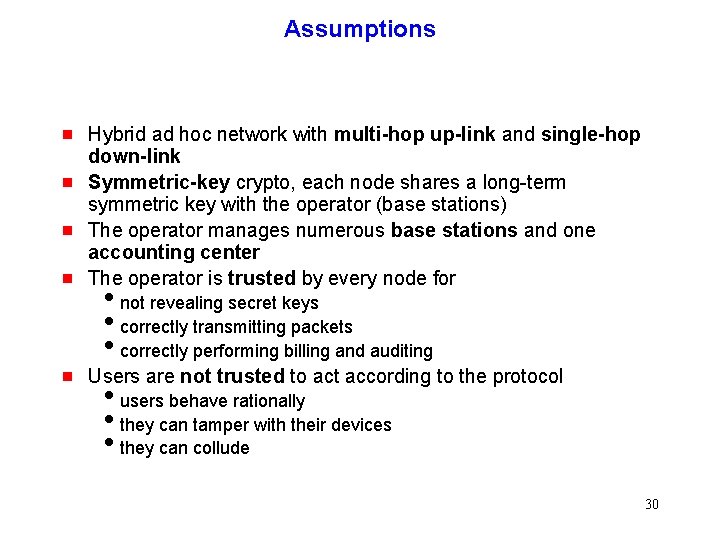
Assumptions g Hybrid ad hoc network with multi-hop up-link and single-hop down-link Symmetric-key crypto, each node shares a long-term symmetric key with the operator (base stations) The operator manages numerous base stations and one accounting center The operator is trusted by every node for g Users are not trusted to act according to the protocol g g g inot revealing secret keys icorrectly transmitting packets icorrectly performing billing and auditing iusers behave rationally ithey can tamper with their devices ithey can collude 30

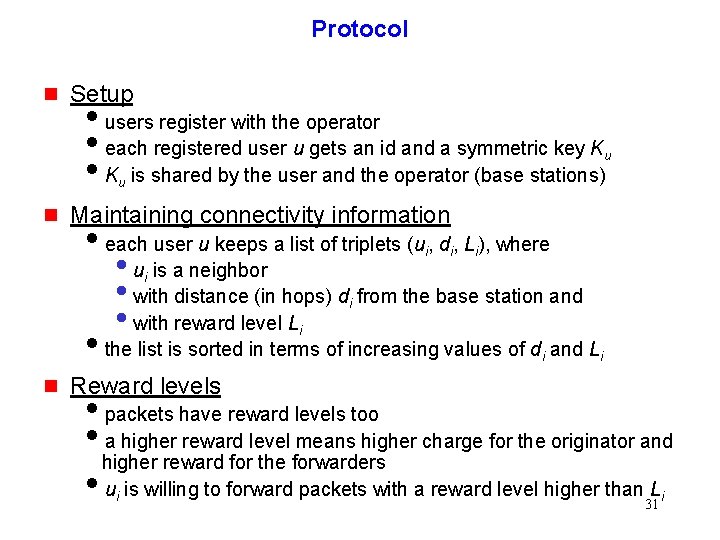
Protocol g Setup g Maintaining connectivity information iusers register with the operator ieach registered user u gets an id and a symmetric key Ku is shared by the user and the operator (base stations) ieach user u keeps a list of triplets (ui, di, Li), where • u is a neighbor • with distance (in hops) d from the base station and • with reward level L i ithe list is sorted in terms of increasing values of di and Li g Reward levels ipackets have reward levels too ia higher reward level means higher charge for the originator and higher reward for the forwarders iui is willing to forward packets with a reward level higher than Li 31

Packet origination g Originator o wants to send payload p io selects a reward level L icomputes a MAC: m = MACKo( L | p ) itransmits [ o | L | p | m ] according to the Packet Transmission Protocol MAC : Message Authentication Code 32

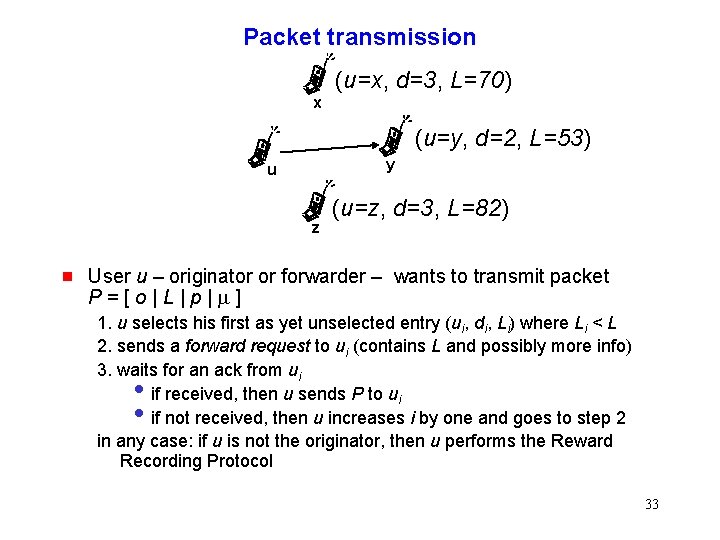
Packet transmission (u=x, d=3, L=70) x (u=y, d=2, L=53) y u z g (u=z, d=3, L=82) User u – originator or forwarder – wants to transmit packet P=[o|L|p|m] 1. u selects his first as yet unselected entry (ui, di, Li) where Li < L 2. sends a forward request to ui (contains L and possibly more info) 3. waits for an ack from ui if received, then u sends P to ui if not received, then u increases i by one and goes to step 2 in any case: if u is not the originator, then u performs the Reward Recording Protocol • • 33

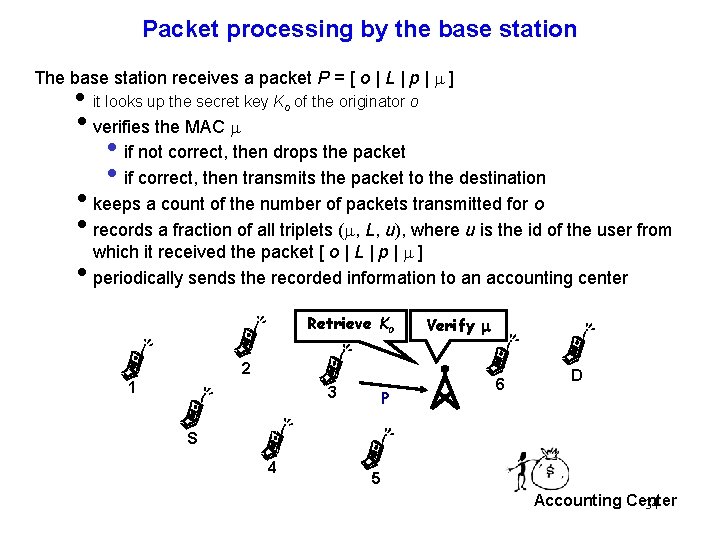
Packet processing by the base station The base station receives a packet P = [ o | L | p | m ] i it looks up the secret key Ko of the originator o iverifies the MAC m • if not correct, then drops the packet • if correct, then transmits the packet to the destination ikeeps a count of the number of packets transmitted for o irecords a fraction of all triplets (m, L, u), where u is the id of the user from which it received the packet [ o | L | p | m ] iperiodically sends the recorded information to an accounting center Retrieve Ko 2 1 3 P Verify m 6 D S 4 5 Accounting Center 34

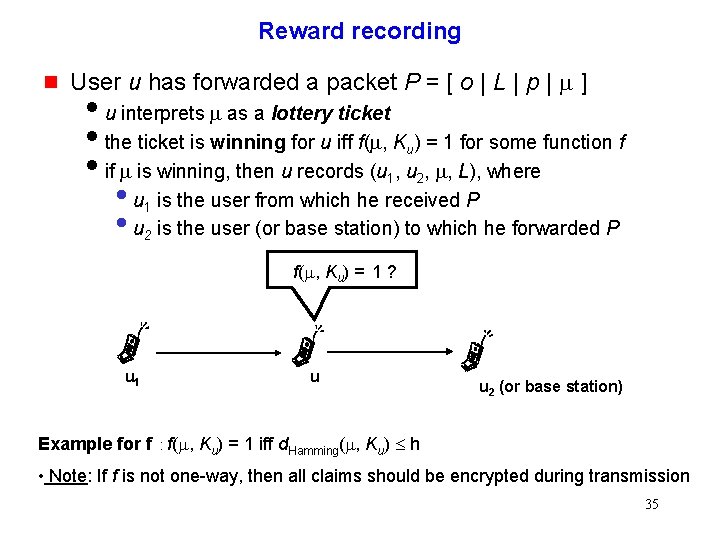
Reward recording g User u has forwarded a packet P = [ o | L | p | m ] iu interprets m as a lottery ticket ithe ticket is winning for u iff f(m, Ku) = 1 for some function f iif m is winning, then u records (u 1, u 2, m, L), where • u is the user from which he received P 2 is the user (or base station) to which he forwarded P 1 f(m, Ku) = 1 ? u 1 u u 2 (or base station) Example for f : f(m, Ku) = 1 iff d. Hamming(m, Ku) £ h • Note: If f is not one-way, then all claims should be encrypted during transmission 35

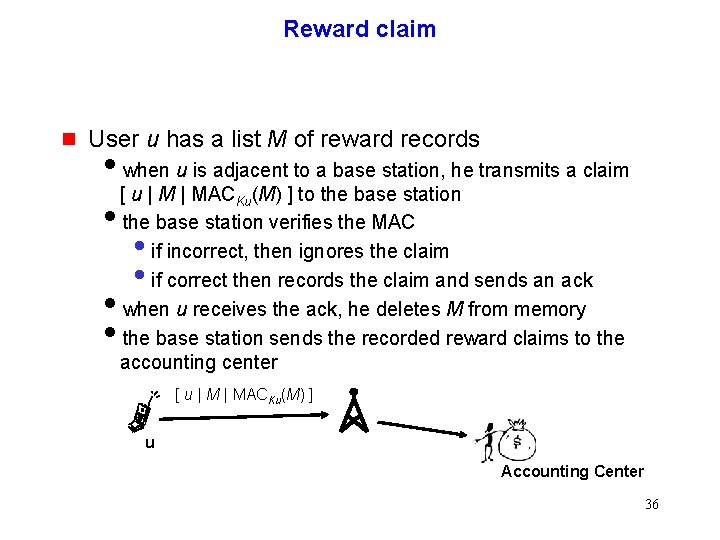
Reward claim g User u has a list M of reward records iwhen u is adjacent to a base station, he transmits a claim [ u | MACKu(M) ] to the base station ithe base station verifies the MAC if incorrect, then ignores the claim if correct then records the claim and sends an ack iwhen u receives the ack, he deletes M from memory ithe base station sends the recorded reward claims to the accounting center • • [ u | MACKu(M) ] u Accounting Center 36

Accounting g The accounting center receives ireward claims of the form: “u claims (u 1, u 2, m, L)” itraffic info recorded by the base stations of the form: “(m, L, u) from o” g g g All originators whose identity has been recorded by a base station are charged All users whose identity figures as a claimant in an accepted reward claim are credited All users whose identity appears as sending or receiving neighbor in an accepted reward claim are also credited 37

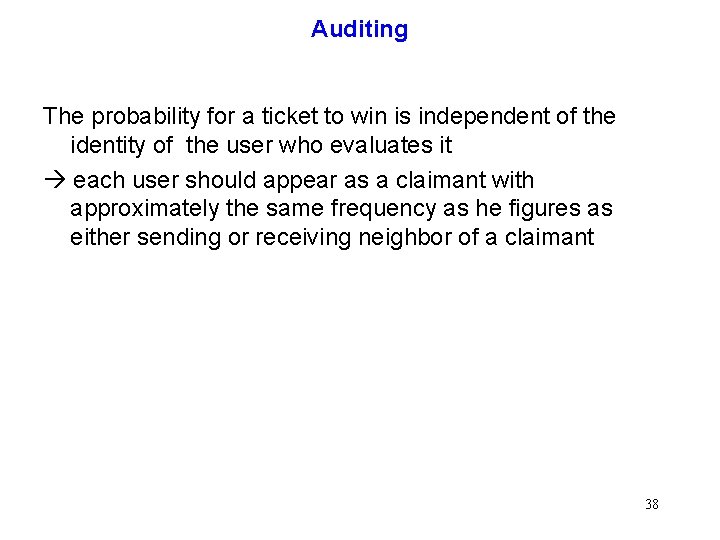
Auditing The probability for a ticket to win is independent of the identity of the user who evaluates it each user should appear as a claimant with approximately the same frequency as he figures as either sending or receiving neighbor of a claimant 38

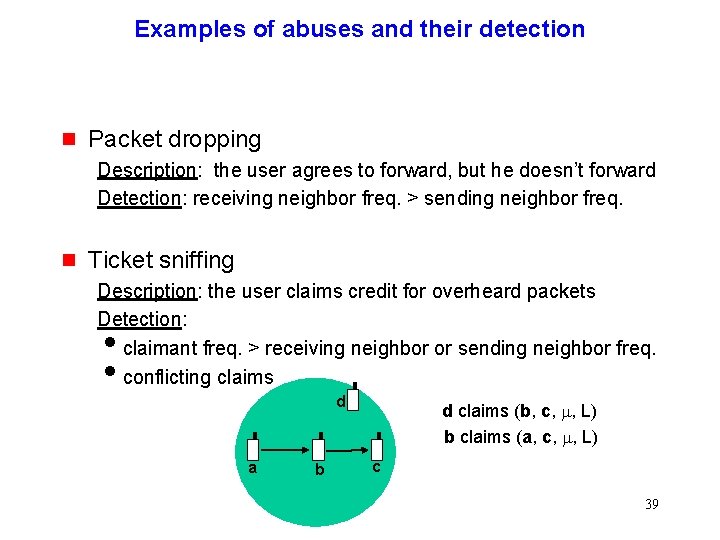
Examples of abuses and their detection g Packet dropping Description: the user agrees to forward, but he doesn’t forward Detection: receiving neighbor freq. > sending neighbor freq. g Ticket sniffing Description: the user claims credit for overheard packets Detection: iclaimant freq. > receiving neighbor or sending neighbor freq. iconflicting claims d a b d claims (b, c, m, L) b claims (a, c, m, L) c 39

Conclusion on the probabilistic encouragement for collaboration g g Cooperation between nodes can be fostered by micropayments Probabilistic micro-payments can drastically reduce the overhead The operator can fine tune the detection mechanisms according to the level of observed cheating Future work i. Study attacks by malicious users i. Pricing issues (e. g. , computation of the reward levels) M. Jakobsson, J. P. Hubaux, and L. Buttyan A Micro-Payment Scheme Encouraging Collaboration in Multi-hop Cellular Networks Proceedings of Financial Crypto 2003 40

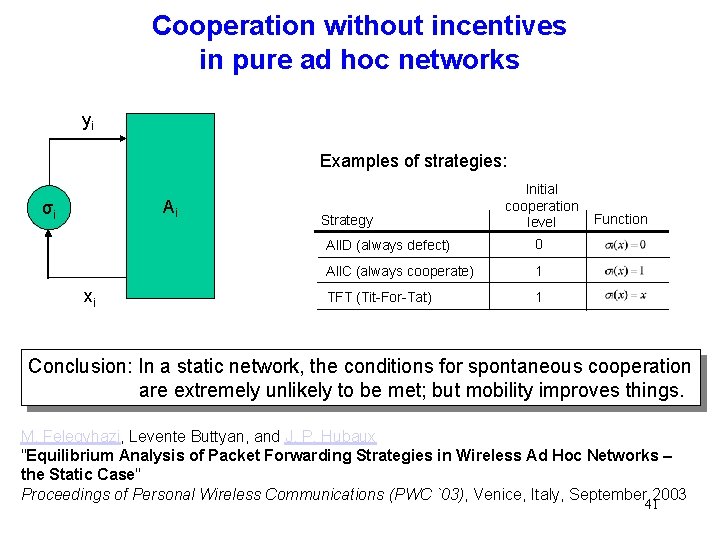
Cooperation without incentives in pure ad hoc networks yi Examples of strategies: Ai σi xi Strategy Initial cooperation level All. D (always defect) 0 All. C (always cooperate) 1 TFT (Tit-For-Tat) 1 Function Conclusion: In a static network, the conditions for spontaneous cooperation are extremely unlikely to be met; but mobility improves things. M. Felegyhazi, Levente Buttyan, and J. P. Hubaux "Equilibrium Analysis of Packet Forwarding Strategies in Wireless Ad Hoc Networks – the Static Case" Proceedings of Personal Wireless Communications (PWC `03), Venice, Italy, September 2003 41

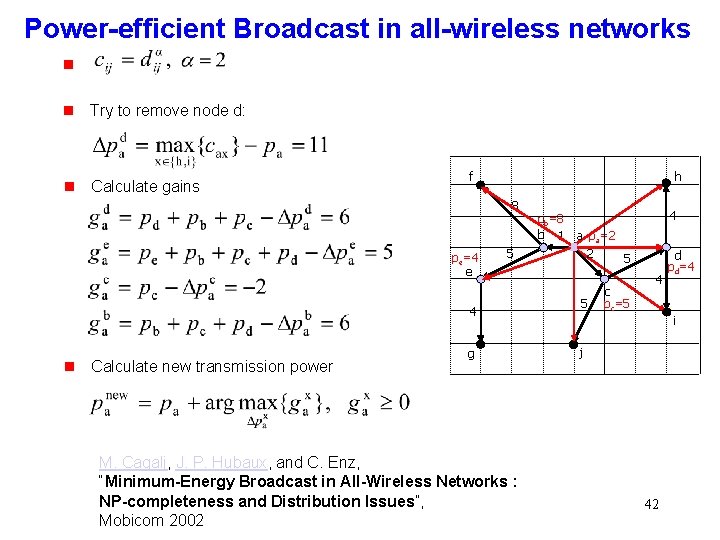
Power-efficient Broadcast in all-wireless networks g g Try to remove node d: g Calculate gains h f 8 pe=4 e Calculate new transmission power 4 a pa=2 5 4 g pb=8 b 1 g M. Cagalj, J. P. Hubaux, and C. Enz, “Minimum-Energy Broadcast in All-Wireless Networks : NP-completeness and Distribution Issues”, Mobicom 2002 2 5 5 c pc=5 4 d pd=4 i j 42

COMMON-Sense Net: Agriculture and water management with the use of wireless sensor networks Joint work with IISc 43

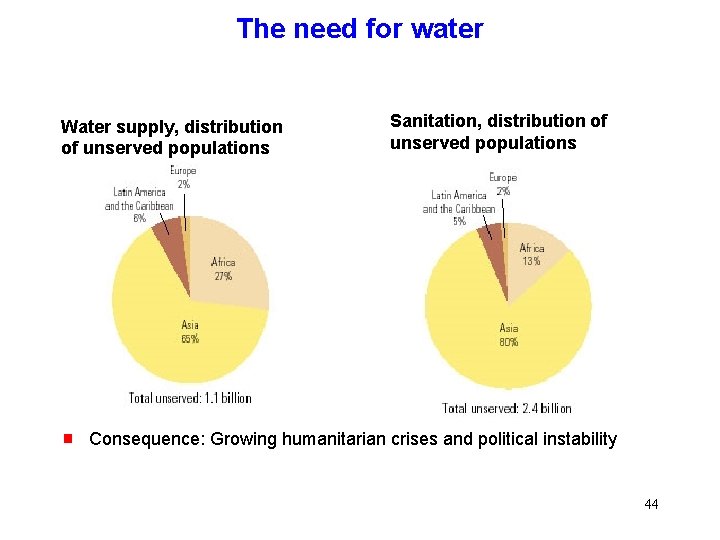
The need for water Water supply, distribution of unserved populations g Sanitation, distribution of unserved populations Consequence: Growing humanitarian crises and political instability 44

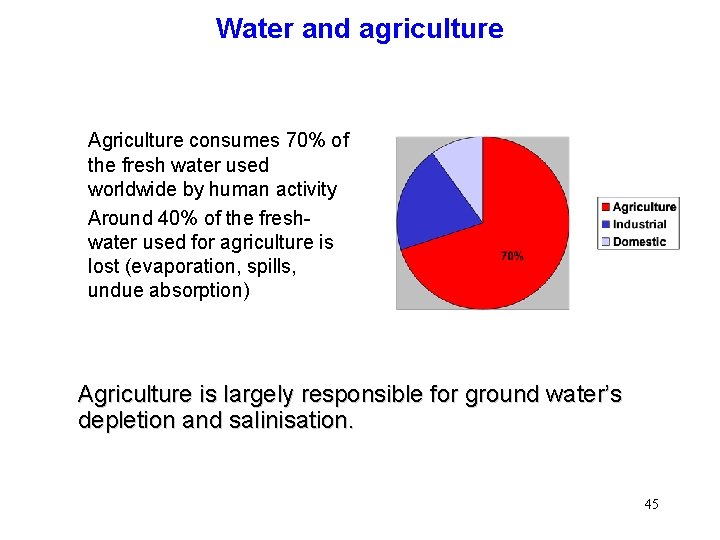
Water and agriculture Agriculture consumes 70% of the fresh water used worldwide by human activity Around 40% of the freshwater used for agriculture is lost (evaporation, spills, undue absorption) Agriculture is largely responsible for ground water’s depletion and salinisation. 45

Assumptions g An optimized water management in agriculture is needed g Optimised water management means better information gathering on the soil’s and plants’ condition g Sensors and sensors networks can provide this enhanced information 46

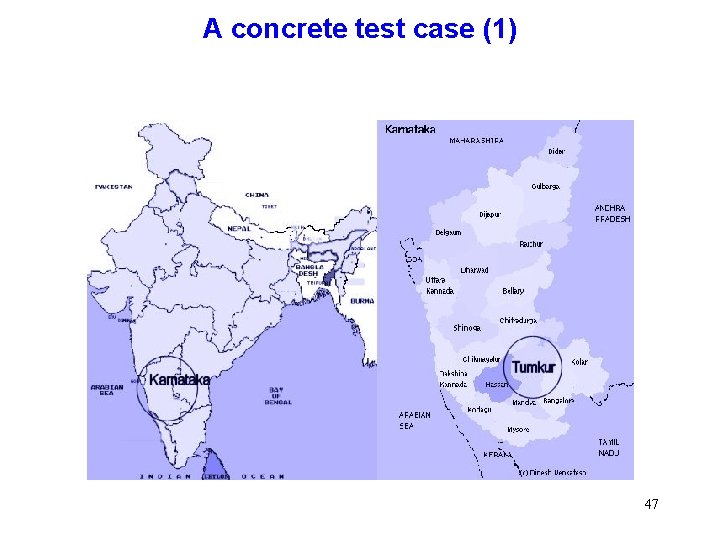
A concrete test case (1) 47

A concrete test case (2) g g 25 villages over a radius of 25 km Marginal farmers (< 1 ha) and small farmers (< 2 ha) No powered irrigation Cultures: groundnut (for oil), cereals millets (finger millet -locally known as Ragi-, sorghum) rice in some irrigated patches 48

User requirements A better access to critical data and information to help farmers in their decision making process g. Soil: humidity, salinity g. Ground-water: level, quality (nitrates, phosphates) g. Local meteorological data: temperature, radiance, wind velocity and direction. . . g. Global meteorological data: weather forecast, seasonal estimates. . . g. Cultural and social issues are critical 49

50

System characteristics g g g Self-organizing network of heterogenous wireless sensor-nodes (ease of deployment, non-intrusiveness) Nodes communicate in a multihop fashion Low data-rate Scalability and adaptability to network changes Node failure detection and adaptability Internet-connectivity 51

Technical requirements g. Communication Range : around 500 m (up to 1 km) g. Power-saving mechanisms: life-time of every node over 1 year (the longer the better) g. Possibility to connect heterogenous sensors to a communication node: « universal » port g. Costs-constraints 52

Project consortium Indian Partners g g g Centre for Electronics Design and Technology (CEDT/IISc) Centre for Atmospheric and Oceanic Studies (CAOS/IISc) Chennakeshava Trust Swiss Partners g g g Laboratory for computer Communications and Applications (LCA/EPFL) Laboratory of Hydrology and Planning (HYDRAM/EPFL) HEC, Lausanne (UNIL) 53

COMMON-Sense Agenda g g g g g June 2003: Build-up of the consortium July-August 2003: Project proposal Fall 2003: Development of first prototype August 31 st: Project submitted to SDC/EPFL cooperation fund January 2004: Project approved February 2004: Project meeting in Bangalore March-April 2004: Gathering of final user requirements May 2004: System High-Level Design June-November 2004: Work on first release December 2004: Outdoor testing of prototype 54

Conclusion g g Ad hoc and sensor networks raise new challenges in a number of areas Security in particular needs to be redesigned from scratch The solutions very much depend on the presence and role of an authority This is an exciting and promising research area… Presented papers available online at: http: //lcawww. epfl. ch/hubaux/ or Google (hubaux) home page 55