Next slide Pg Dn or Click Previous slide























- Slides: 44

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Information Insecurity Part III: The Action Plan E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

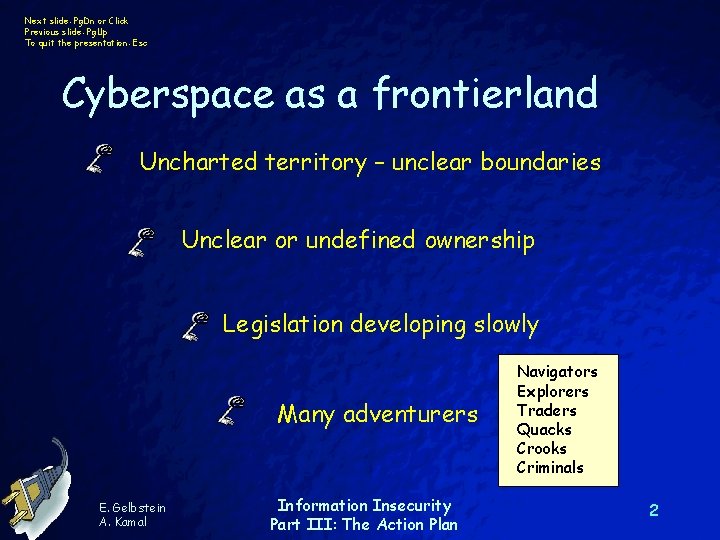
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Cyberspace as a frontierland Uncharted territory – unclear boundaries Unclear or undefined ownership Legislation developing slowly Many adventurers E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan Navigators Explorers Traders Quacks Crooks Criminals 2

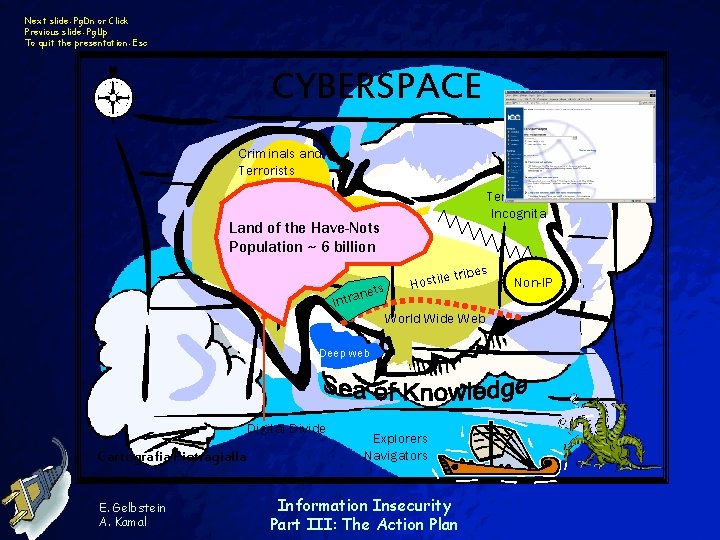
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc CYBERSPACE Criminals and Terrorists Terra Incognita Land of the Have-Nots Population ~ 6 billion ets tran ribes t Hostile In World Wide Web Deep web Digital Divide Cartografia Pietragialla E. Gelbstein A. Kamal Explorers Navigators Information Insecurity Part III: The Action Plan Non-IP

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Survivor’s guide Better charts to the cyberspace frontier are being produced. In the meantime… Best practices (keep it simple, do not reinvent the wheel) Standards (formalized compatibilities and best practices) Legislation (rules of what is not permitted) Compliance (with each of the above) E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 4

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Sources of Best Practices Enthusiasts and volunteers Happyhacker Professional associations ISSA, CASPR Government departments UK’s CCTA Consultants and commercial providers Examples of some websites follow… E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan Gartner GIGA IBM KPMG …etc… 5

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. happyhacker. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. issa. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. sans. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc E. Gelbstein A. Kamal www. itsmf. com Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. itil-itsm-world. com/security. htm E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. gigaweb. com E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 11

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Standards Formalized definitions that ensure compatibility De-jure From Organizations whose mandate is to define standards E. Gelbstein A. Kamal De-facto Usually from vendors Useful and ubiquitous Information Insecurity Part III: The Action Plan 14

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc De-jure standards (examples) Internet Engineering Task Force (IETF) TCP/IP, Html, POP, STMP, FTP, SSL and many other International Telecommunications Union (ITU) Recommendations X. 273, Open systems network layer security Recommendations X. 509, Authentication framework International Standards Organization (ISO) ISO 17799 “Code of Practice for the management of Information Security” E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 15

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Sources of de-facto standards Professional associations e. g. the IEEE Institution of Electrical and Electronic Engineers Vendor associations e. g. ECMA European Computer Manufacturers Association Vendors e. g Microsoft, Netscape, Adobe Examples follow E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 16

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc European Computer Manufacturers Association E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Institution of Electrical and Electronic Engineers E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Legislation: a little history Early difficulties Data and software incorporeal object – old laws are designed to deal with tangible objects Legal regime of intangibles needs to cater for the owner it also needs to cater for persons concerned by the content (privacy) The property status of information was/is unclear Issue 1: the law and the correctness and integrity of data Issue 2: protecting data owners for “exclusive use” Some of these remain unresolved in many countries E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 21

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Legislation: a little history 2 More early difficulties Theft, larceny, embezzlement Older definitions require the offender to “take an item of another person’s property” Fraud Under some legislation, it requires deception of a person (does NOT apply to a computer) E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 22

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Scope of cyber-legislation (1) Computer misuse Data protection Telecommunications interception National security and anti-terrorism Software copyrights and patents Search and seizure, criminal evidence Contractual obligations for suppliers E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 23

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Scope of cyber-legislation (2) Human rights: right to privacy, right to access Electronic contracts, taxation of e-commerce Censorship Obscene publications Protection of minors Consumer protection E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 24

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Scope of cyber-legislation (3) Organized crime in cyberspace On-line banking and money laundering Gambling in cyberspace Electronic signatures and certificats Defamation and libel in cyberspace National security and anti-terrorism and much, much more E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 25

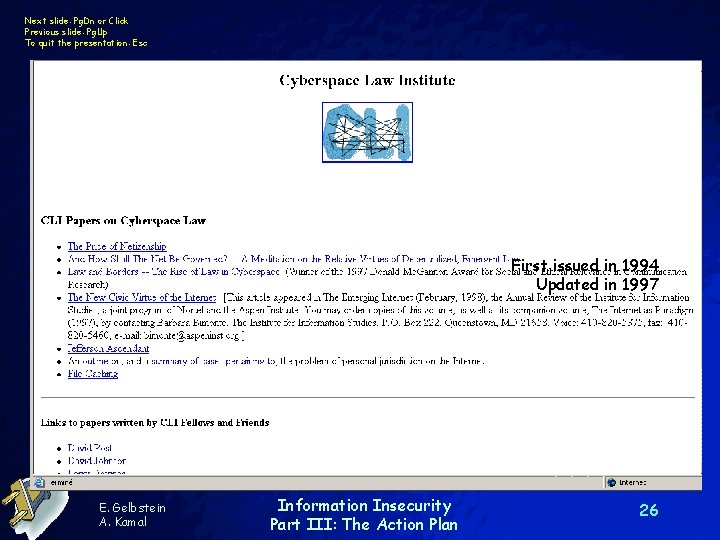
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc First issued in 1994 Updated in 1997 E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 26

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Professor David Post and others www. cli. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc International Legislation OECD: 1983 -1985 - Criminalization of computer abuse Council of Europe (COE): 1985 - Work begins towards a convention on cyber-crime United Nations – Congress on the Prevention of Crime In November 2001, formal signature by 33 countries of the COE Convention on Cybercrime E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 28

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc The COE Convention Three primary groups of provisions Unauthorized computer intrusion, malicious code, the use of computers to commit acts which are already a crime Procedures to capture and retrieve on-line and other information by issuing “Retention Orders” Cooperation between signatory states to share e-evidence Additional protocols are being developed E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 29

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Reactions to the Convention 33 States (29 Council Members) plus Canada, Japan, South Africa and the United States of America signed it. It will enter into force once ratified by 5 States (planned mid 2003) Possible conflicts with existing national legislation Non-signatory States where cybercriminals may act with impunity Misgivings Inidividual rights to privacy vs. extended surveillance powers granted to signatory countries Possilibity of personal data being transferred outside Europe to countries with less protective legislation Issuance of warrants seeking evidence and extradition Increased cost of e-business and place restrictions E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 30

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Compliance and certification General ICT audits, with focus on security (COBIT guidelines) Compliance audits against ISO 17799 or similar Security certification services The selected auditors must be deeply trusted E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 31

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. isaca. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

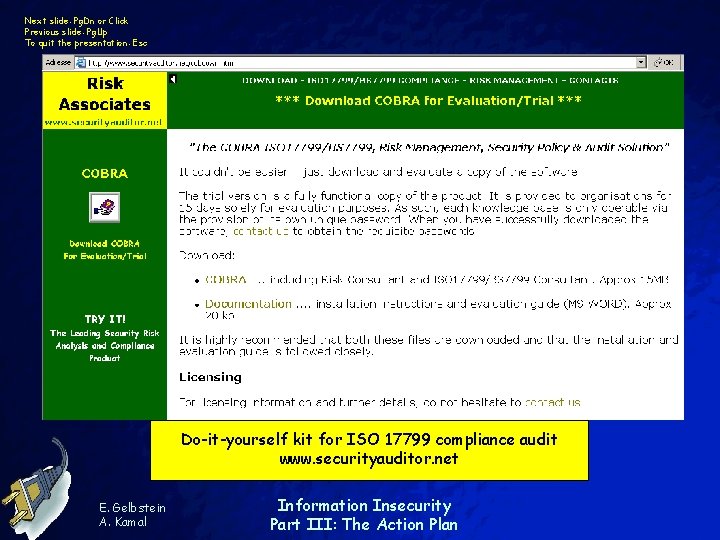
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Do-it-yourself kit for ISO 17799 compliance audit www. securityauditor. net E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. giac. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. isc 2. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc E. Gelbstein A. Kamal www. htcn. org Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Other interested parties and other civil liberties groups E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 37

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. cfenet. com E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

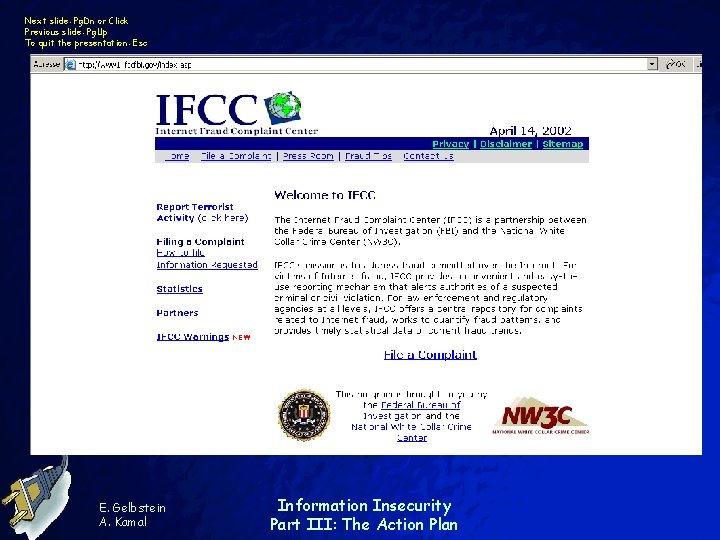
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www 1. ifccfbi. gov/index. asp E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc www. merchantfraudsquad. com E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc International Chamber of Commerce www. iccwbo. org E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Beyond insecurity and crime Cyber-terrorism and Cyber-war call for a new way of looking at our world and for further action by the International Community E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 42

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Moving forward Recommendations for immediate action purpose: help those not yet ready Work to be done purpose: avoid procrastination and develop a Law of Cyberspace before it is too late E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 43

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Recommendations 1. 2. 3. 4. 5. 6. Become aware of the Information Insecurity problem Devise an information security strategy Implement remedial procedures immediately Seek professional help without delay Identify the gaps in your country’s legislation Encourage the United Nations to embark urgently on a Law of Cyberspace E. Gelbstein A. Kamal Information Insecurity Part III: The Action Plan 44