Next slide Pg Dn or Click Previous slide











































- Slides: 48

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Information Insecurity Part II: The Solution E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 1

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Basic rule of systems Complex problems are never solved, they are only transformed corollary You don’t “fix” security. You manage it E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 2

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Information security principles 1 Information must be available to those authorized to have it 2 Information will only be disclosed at the appropriate time only to those authorized to have it 3 Information will only be modified by those authorized to do so Source ISO 17799: Code of Practice for the Management of Information Security E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 3

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Information security principles 4 (2) Existence of a legal framework defining Protection of intellectual property rights, including software Protection of privacy in cyberspace Effectiveness of the provision of digital signatures Prosecution of cyber-criminals Covering information processed, stored and transmitted in e-form E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 4

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc What is your role in Infosec? Defender: one of the good guys Chief Information Officer Security manager Systems administrator Network administrator Enlightened User E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 5

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc How good a defender ? It really is your choice Due diligence Negligence Dereliction of duty Misconduct Sabotage Criminal damage Aiding and abbetting crime E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 6

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc What is your role in Infosec? A “special guy”: good or bad are relative Auditor (Security, internal, external) Ethical hacker Security consultant Vendors of security products Vendors of other ICT projects Info Security legislator E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 7

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc What is your role in Infosec? Bystander “Surely, it’s a technical problem” “Nothing to do with me” “Not in my job description” “What, change password again? ” “What’s wrong using my birthday as a password? ” “OK so my son used my employer’s notebook to download some shareware – what’s the big deal? ” E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 8

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc What is your role in Infosec? Obstacle “No way can I increase your budget” “We have a freeze on recruitment” “It’s not compatible with our corporate culture” “The trade unions won’t have it” E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 9

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Defender’s 1 st step: Culture Security relies on everyone Security requires many processes Security contains many projects which never end Only the paranoid succeed and survive E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 10

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Defender’s 2 nd step: Reality check 100% security can NOT be achieved Technology is not enough to guarantee security Legislation is not enough to guarantee security Security resources must match risk Good security practices become barriers E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 11

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Building effective defences needs more than technology Requirements definition Organization Asset valuation Policies and compliance Building blocks Technical defences Awareness Standards Best practices E. Gelbstein A. Kamal 1 2 3 Incident response Digital forensics Legislation Information Insecurity Part II: The Solution 4 Tests Certification Audits 12

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Recommendations for Executives to help contain the headache 1. Assign responsibility for information security 2. Ask your CIO to certify in writing the security status of your organization’s systems 3. Ask your CIO to document all known vulnerabilities 4. Engage a trusted ethical hacker to regularly attack your facilities and systems E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 13

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Security organization Effective Defences 1 Who is responsible for information security in the organization as a whole and at its various locations ? Who does this person report to ? Who reviews this person’s performance and monitors her/his effectiveness ? How is security managed with contractors, temporary personnel and outsourcers ? Who is responsible for dealing with a security incident ? E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 14

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective defences 1 Effective Defences 1 Requirements definition What threats? What value what to protect? What vulnerabilities? How much funding can be made available to implement, operate and manage? E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 15

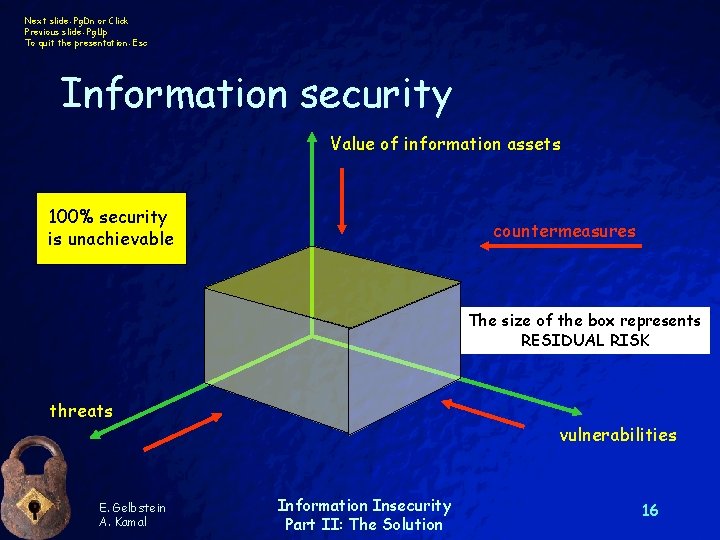
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Information security Value of information assets 100% security is unachievable countermeasures The size of the box represents RESIDUAL RISK threats E. Gelbstein A. Kamal vulnerabilities Information Insecurity Part II: The Solution 16

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc How much security is enough? Complexity and cost of security Military Major outsourcers Stock exchanges Fund transfers Major banks Telephone companies Low tech manufacturing 0 1 2 3 4 5 6 7 8 9 Acceptable level of residual risk E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 17

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 1 Asset valuation & impact analysis What is the value* of o Data disclosed modified unavailable destroyed o Intellectual property o Systems (software, hardware) o Documents o The Organisation’s reputation etc * Financial, commercial, reputation, political, etc E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 18

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 1 When does misuse become abuse? Theft and fraud Proprietary information Software and equipment Employer’s time Disclosure Financial gain Modifying personal data (e. g. holiday records) Misuse of system privileges Inappropriate access to - data - websites - others’ e-mail Deletion of data e-mailing of offensive material, jokes, etc Installation of unauthorized software Downloading large files (music, video) Personal use of employer’s systems and facilities Confidential information Embarrassing information Internal gossip and politics E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 19

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Policies and compliance Effective Defences 1 POLICIES are formal statements of how an organization manages information security Scope Documentation Dissemination Maintenance Compliance E. Gelbstein A. Kamal Policies without effective compliance measures are ineffective Information Insecurity Part II: The Solution 20

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Scope of policies Effective Defences 1 Acceptable personal use or corporate resources e-mail policies for corporate and personal use Creation, change and management of passwords System / Resource access Employer’s right to monitor and right to access Use of encryption Physical access and remote access Software installation Mobile communications and computing Database administration Employee background checks (pre- and during employment) list goes on. . . E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 21

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 1 An e-mail policy would cover Legal liability (harassment, copyright, libel, etc) Offensive language/material Non-disclosure Corporate practices regarding encryption Personal use of corporate e-mail Employer’s right to monitor Retention and archival Junk and other non-productive e-mail Attachments Executable code including macros Audio and video files Other large files Virus, worm, other infectious software Non-compliance etc. . . E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 22

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 1 Policies: reality test Policies must make sense to the personnel to be followed (30% of all attacks are internal) Three options regarding compliance Don’t bother too much Tight monitoring and zero tolerance Managed program to address internal abuses Policies have no credibility E. Gelbstein A. Kamal Create martyrs Loss of trust Information Insecurity Part II: The Solution 23

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective defences 2 Building blocks non-repudiation confidentiality audit authentication integrity authorization E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 24

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Building blocks Effective Defences 2 (2) Authentication Prove you are who you say you are Authorization The security system checks what you may do with the system Confidentiality Data can only be seen by someone authorized to do so Integrity Data can only be modified by someone authorized to do so Non-repudation Ability to prove that the information received is the same as the information sent Audit System records of who did what and when E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 25

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Technical defences Effective Defences 2 Data access rights Tools Database security Physical access control System security Infrastructure LAN & server security - No single point of failure - UPS and standby - Clusters, fail-soft, RAID, alternative routing - proxy servers, firewalls Firewall security Logical access control Diagnostics and monitoring System administration Virus management software Encryption software E. Gelbstein A. Kamal All properly installed, configured and tested by trained personnel Information Insecurity Part II: The Solution 26

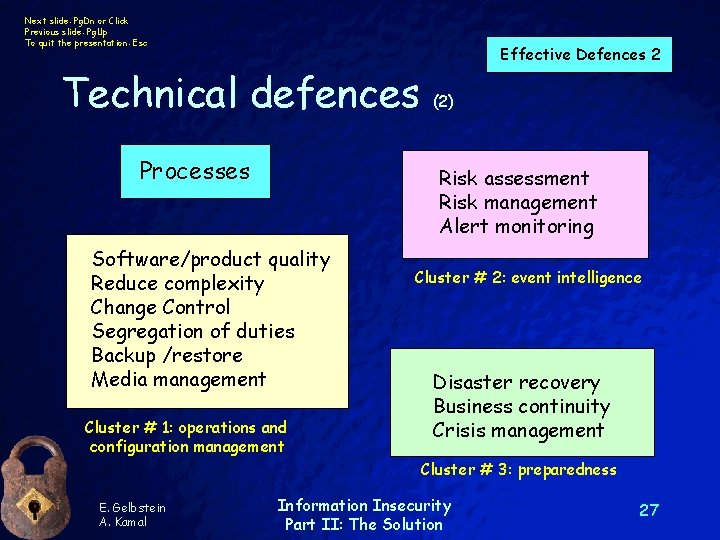
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Technical defences Processes Effective Defences 2 (2) Risk assessment Risk management Alert monitoring Software/product quality Reduce complexity Change Control Segregation of duties Backup /restore Media management Cluster # 1: operations and configuration management Cluster # 2: event intelligence Disaster recovery Business continuity Crisis management Cluster # 3: preparedness E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 27

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 2 sections of ISO 17799 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. Develop and implement security policies Put in place a security organization Maintain an information asset classification Address personnel issues of security Implement physical and environmental security Ensure adequate network and computer operations Implement system and network access controls Build security into systems development Have disaster recovery and resumption plans Compliance with legislation and best practices E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 28

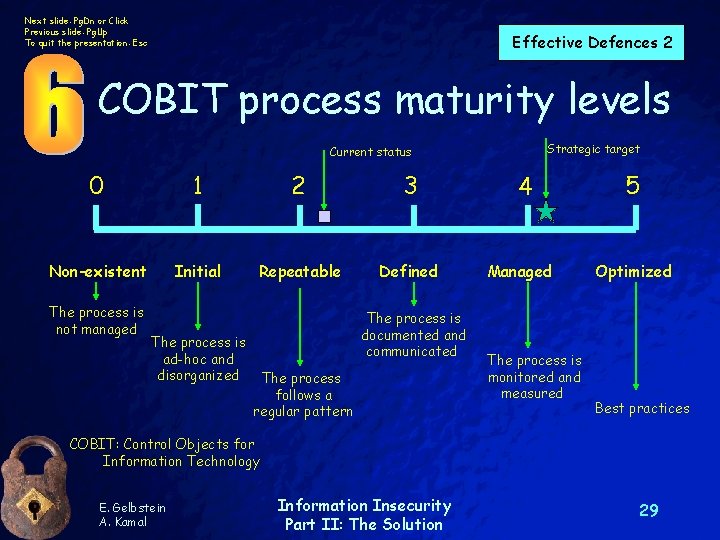
Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 2 COBIT process maturity levels Strategic target Current status 0 1 2 3 4 5 Non-existent Initial Repeatable Defined Managed Optimized The process is not managed The process is ad-hoc and disorganized The process is documented and communicated The process follows a regular pattern The process is monitored and measured Best practices COBIT: Control Objects for Information Technology E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 29

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Justifying investments Effective Defences 2 Demonstrating value has always been the BIG challenge for technical practitioners Typical ROSI (Return On Security Investment) analysis: cost benefit “We spent a million dollars” “We think we have not been hacked” The industry is unable to agree on a better way E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 30

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc More about ROSI Effective Defences 2 Some of the intangible factors: No security metrics standards No warranties from vendors or outsourcers– only “best efforts” The same is true for Financial controls Fire prevention arrangements E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 31

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 2 ways to tighten security 1. 2. 3. 4. 5. 6. 7. Promote awareness Know the assets you must protect Invest wisely (“more” may not be “better”) Survey the threatscape – who are the enemy? Be vigilant Understand actively manage risk Ensure security is engineered and designed into the infrastructure 8. Remember it is more than a technical matter 9. Detect and respond E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 32

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 2 Awareness Management I. T. personnel Disaster recovery, continuity and crisis plans Trusted insider risks – signals Breaches of security, subsequent “digital autopsy” Vendor bulletins about vulnerabilities Hacker activities CERT and other alerts Procedures and policies What to do when an incident occurs All other personnel E. Gelbstein A. Kamal Policies and need for compliance What to do when an incident occurs Best practices Information Insecurity Part II: The Solution 33

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 2 good personal practices 1. 2. 3. 4. 5. 6. Use hard to guess passwords and ensure non-disclosure Make regular backups of your critical data Use effective protection against malicious code Use a firewall between your computer and the Internet Do not stay on-line unnecessarily or when inactive Look for and install quickly software updates and patches from (trusted) vendors 7. Be careful of e-mail attachments from strangers and from known persons if the subject line is unusual E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 34

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 2 ways to protect your privacy 1. 2. 3. 4. 5. 6. Set up your browser to secure personal information Don’t reveal personal details unless you are sure Actively manage cookies Keep a “clean” e-mail address Remember you may be monitored at work Beware of websites that offer rewards in exchange for your contact or other information 7. Never reply to spam mail 8. Only reveal critical information to a “https” website 9. Use encryption if appropriate E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 35

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 2 A word of caution Tools and good practices increase security. For the end-user, they become a kind of obstacle race Mwf 1 U 4 z. X Hard to remember passwords prominently displayed on Post-it™ Notes E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 36

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective defences 3 Effective Defences 3 Incident response Intrusion detection Emergency Response Team Problem containment Problem resolution Restoring normal operations Digital forensics Determine attack mechanism Review adequacy of arrangements Search for evidence Action plan for internal causes Action plan for external causes (also called digital autopsy) E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 37

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc How do you respond ? Effective Defences 3 Option 1 Hackers please note This facility is secured Monday and Friday, 09: 00 to 17: 00 CET Please do not visit at any other time We thank you for your understanding Option 2 Emergency response plan + team E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 38

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 3 things to do if (when) attacked 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. Don’t panic ! Call in your incident response team Contain the problem and avoid the “quick fix” Take good notes in case you need to take legal action Have your backup facilities ready Get rid of the problem Use trusted, uncompromised, communications Know what to say, to whom and when Know when to involve crime investigators Conduct an autopsy of the event and your response E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 39

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective defences 4 How do you know you have not been attacked ? How do you know that your arrangements will work ? tests audits digital autopsy certification Who tests the testers? E. Gelbstein A. Kamal Like your annual medical it’s no guarantee of good health but it might diagnose a problem Information Insecurity Part II: The Solution 40

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 4 e-evidence Volume and manageability Who else has copies ? Indexing, classification Retention, archival Media and software Right to access Right to remove Right to destroy E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 41

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc e-evidence Headaches Effective Defences 4 (2) Hard to trace, particularly cross-border Hard to quantify losses Lack of clarity what is court-admissible Civil litigation Contractual issues Harassment, bullying, impropriety Containable fraud Criminal litigation Out of court settlements are common E. Gelbstein A. Kamal Information Insecurity Part II: The Solution Sabotage Industrial espionage Major fraud 42

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc e-evidence Effective Defences 4 (3) Follow proper procedures for seizure Seize computer, media and paperwork Assess risk of logical bomb Protect the suspect computer from tampering Discover, recover and report E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 43

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 4 ways to support e-forensics 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. Follow authorized seizure process (ask the lawyers!) Seize and secure equipment, media and papers Shutdown the computer – record it with a video camera Document the hardware configuration Transport to secure location and protect chain of evidence Ensure the computer remains uncompromised Make bitstream backups of hard disk and all media Authenticate data with 128 bit checksum Only use backups for subsequent analysis Document the system’s time and date E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 44

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 4 ways to support e-forensics (2) 11. Identify all anomalies Hidden disk partitions, hidden files, encrypted files evidence of erased files, file slack, presence of steganographic software 12. 13. 14. 15. Examine e-mail, Internet, Temporary files Fully document all the findings Retain copies of all software used for analysis Only use fully licensed forensic software E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 45

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 4 things to worry about 1. 2. 3. 4. 5. 6. 7. 8. Time elapsed between an attack and it being discovery The size of incident logs (may inhibit discovery) Examining incident logs is boring (easy to miss things) The trusted insider Hard to know what’s what in a multi-vendor environment Good security staff are hard to find and harder to keep Hard to define a return on security investment Management detachment (denial of having a role to play) E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 46

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Effective Defences 4 things to worry about 9. 10. 11. 12. 13. 14. (2) Limited international cyber-crime legislation Certificate Authorities: the new trust issue Vendors not liable for product vulnerabilities Executives who believe security is not a real issue Liabilities arising from lack of due diligence Need to take cyber-crime insurance E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 47

Next slide: Pg. Dn or Click Previous slide: Pg. Up To quit the presentation: Esc Conclusion Sounds daunting? It is. You have two options: a. Be prepared (Act now) or b. Improvise when it happens (React then) E. Gelbstein A. Kamal Information Insecurity Part II: The Solution 48