Networks Network Protocols jamiedrfrostmaths com www drfrostmaths com

- Slides: 30

Networks : : Network Protocols jamie@drfrostmaths. com www. drfrostmaths. com @Dr. Frost. Maths Last modified: 30 th July 2019

www. drfrostmaths. com Registering on the Dr. Frost. Maths platform allows you to save all the code and progress in the various Computer Science mini-tasks. It also gives you access to the maths platform allowing you to practise GCSE and A Level questions from Edexcel, OCR and AQA. Everything is completely free. Why not register? With Computer Science questions by: Your code on any mini-tasks will be preserved. Note: The Tiffin/DFM Computer Science course uses Java. Script as its core language. Most code examples are therefore in Java. Script. Using these slides: Green question boxes can be clicked while in Presentation mode to reveal. ? Slides are intentionally designed to double up as revision notes for students, while being optimised for classroom usage. The Mini-Tasks on the DFM platform are purposely ordered to correspond to these slides, giving your flexibility over your lesson structure.

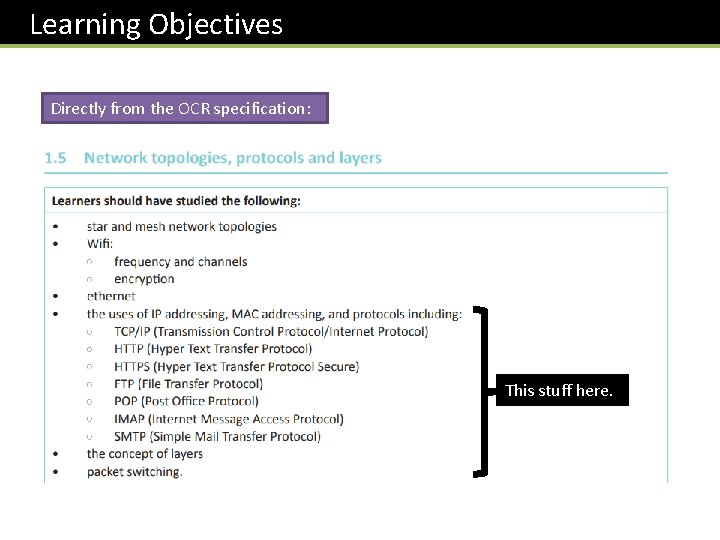
Learning Objectives Directly from the OCR specification: This stuff here.

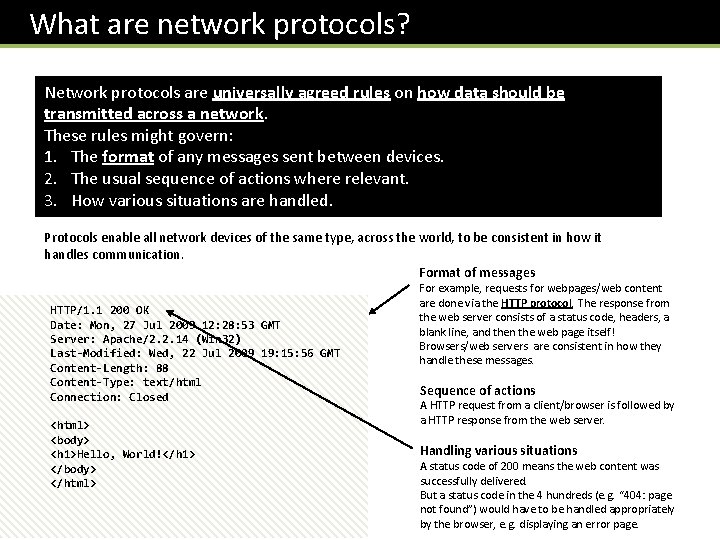
What are network protocols? Network protocols are universally agreed rules on how data should be transmitted across a network. These rules might govern: 1. The format of any messages sent between devices. 2. The usual sequence of actions where relevant. 3. How various situations are handled. Protocols enable all network devices of the same type, across the world, to be consistent in how it handles communication. Format of messages HTTP/1. 1 200 OK Date: Mon, 27 Jul 2009 12: 28: 53 GMT Server: Apache/2. 2. 14 (Win 32) Last-Modified: Wed, 22 Jul 2009 19: 15: 56 GMT Content-Length: 88 Content-Type: text/html Connection: Closed <html> <body> <h 1>Hello, World!</h 1> </body> </html> For example, requests for webpages/web content are done via the HTTP protocol. The response from the web server consists of a status code, headers, a blank line, and then the web page itself! Browsers/web servers are consistent in how they handle these messages. Sequence of actions A HTTP request from a client/browser is followed by a HTTP response from the web server. Handling various situations A status code of 200 means the web content was successfully delivered. But a status code in the 4 hundreds (e. g. “ 404: page not found”) would have to be handled appropriately by the browser, e. g. displaying an error page.

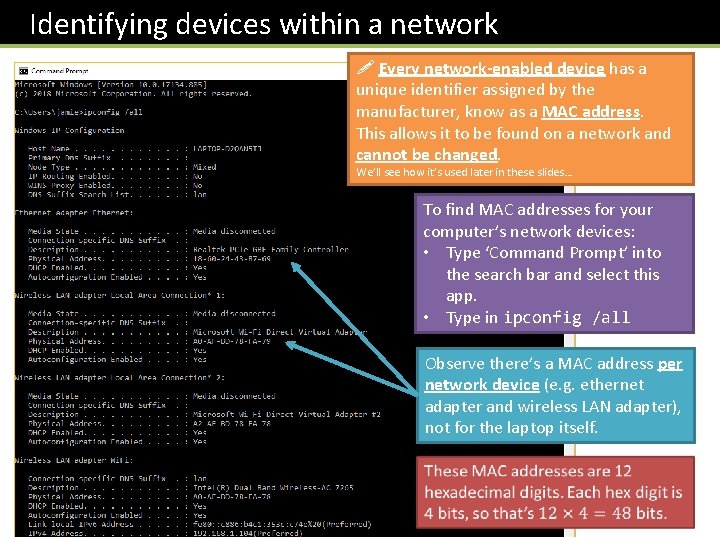
Identifying devices within a network ! Every network-enabled device has a unique identifier assigned by the manufacturer, know as a MAC address. This allows it to be found on a network and cannot be changed. We’ll see how it’s used later in these slides… To find MAC addresses for your computer’s network devices: • Type ‘Command Prompt’ into the search bar and select this app. • Type in ipconfig /all Observe there’s a MAC address per network device (e. g. ethernet adapter and wireless LAN adapter), not for the laptop itself.

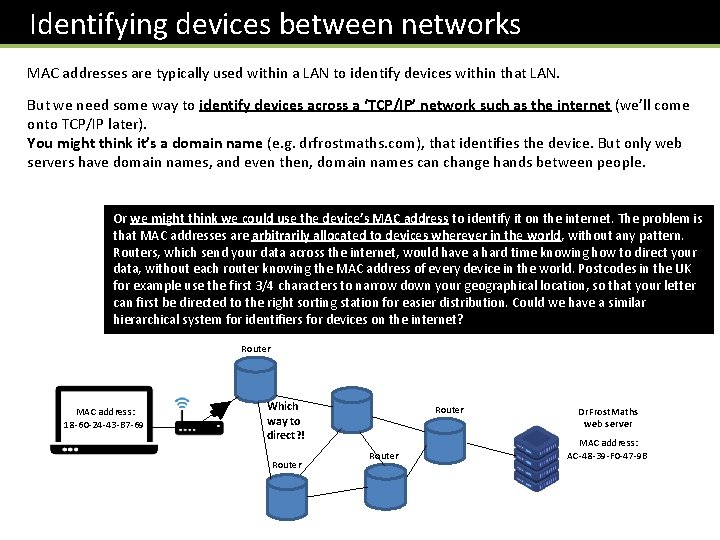
Identifying devices between networks MAC addresses are typically used within a LAN to identify devices within that LAN. But we need some way to identify devices across a ‘TCP/IP’ network such as the internet (we’ll come onto TCP/IP later). You might think it’s a domain name (e. g. drfrostmaths. com), that identifies the device. But only web servers have domain names, and even then, domain names can change hands between people. Or we might think we could use the device’s MAC address to identify it on the internet. The problem is that MAC addresses are arbitrarily allocated to devices wherever in the world, without any pattern. Routers, which send your data across the internet, would have a hard time knowing how to direct your data, without each router knowing the MAC address of every device in the world. Postcodes in the UK for example use the first 3/4 characters to narrow down your geographical location, so that your letter can first be directed to the right sorting station for easier distribution. Could we have a similar hierarchical system for identifiers for devices on the internet? Router MAC address: 18 -60 -24 -43 -B 7 -69 Which way to direct? ! Router Dr. Frost. Maths web server MAC address: AC-48 -39 -F 0 -47 -9 B

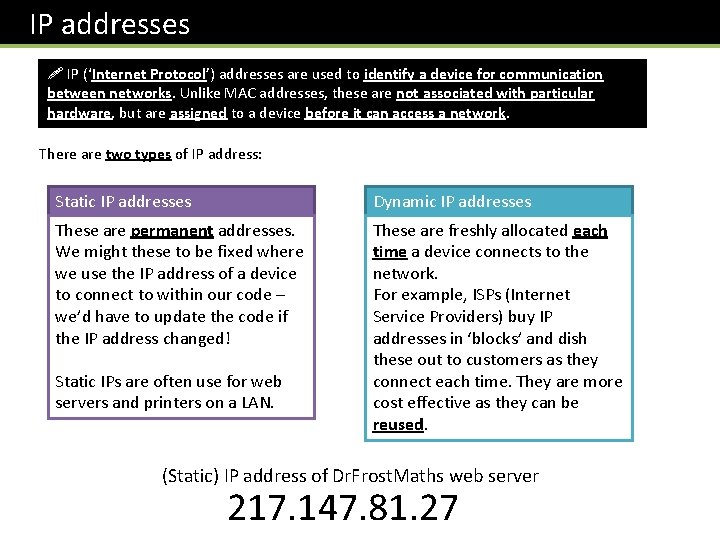
IP addresses ! IP (‘Internet Protocol’) addresses are used to identify a device for communication between networks. Unlike MAC addresses, these are not associated with particular hardware, but are assigned to a device before it can access a network. There are two types of IP address: Static IP addresses Dynamic IP addresses These are permanent addresses. We might these to be fixed where we use the IP address of a device to connect to within our code – we’d have to update the code if the IP address changed! These are freshly allocated each time a device connects to the network. For example, ISPs (Internet Service Providers) buy IP addresses in ‘blocks’ and dish these out to customers as they connect each time. They are more cost effective as they can be reused. Static IPs are often use for web servers and printers on a LAN. (Static) IP address of Dr. Frost. Maths web server 217. 147. 81. 27

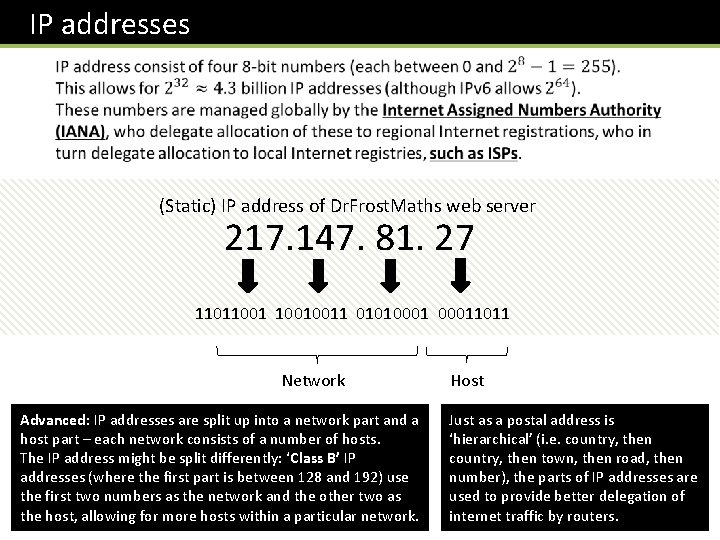
IP addresses (Static) IP address of Dr. Frost. Maths web server 217. 147. 81. 27 110110010011 010100011011 Network Advanced: IP addresses are split up into a network part and a host part – each network consists of a number of hosts. The IP address might be split differently: ‘Class B’ IP addresses (where the first part is between 128 and 192) use the first two numbers as the network and the other two as the host, allowing for more hosts within a particular network. Host Just as a postal address is ‘hierarchical’ (i. e. country, then town, then road, then number), the parts of IP addresses are used to provide better delegation of internet traffic by routers.

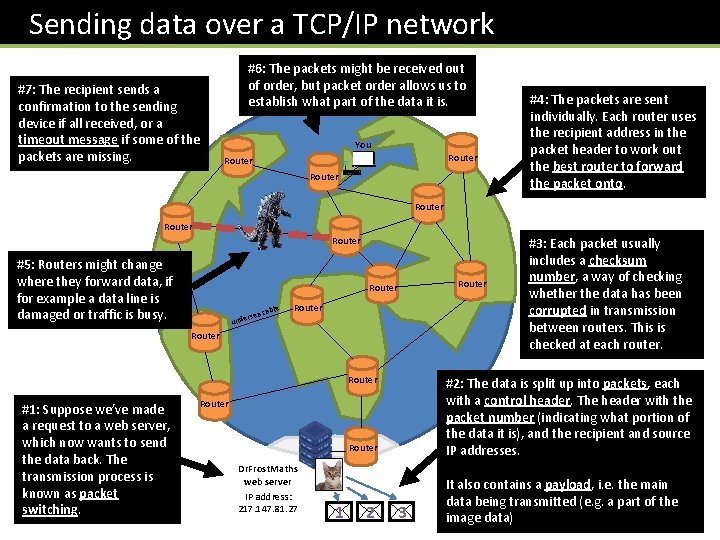
Sending data over a TCP/IP network #7: The recipient sends a confirmation to the sending device if all received, or a timeout message if some of the packets are missing. #6: The packets might be received out of order, but packet order allows us to establish what part of the data it is. You Router #4: The packets are sent individually. Each router uses the recipient address in the packet header to work out the best router to forward the packet onto. Router #5: Routers might change where they forward data, if for example a data line is damaged or traffic is busy. Router able sea c r unde Router #1: Suppose we’ve made a request to a web server, which now wants to send the data back. The transmission process is known as packet switching. #2: The data is split up into packets, each with a control header. The header with the packet number (indicating what portion of the data it is), and the recipient and source IP addresses. Router Dr. Frost. Maths web server IP address: 217. 147. 81. 27 1 2 Router #3: Each packet usually includes a checksum number, a way of checking whether the data has been corrupted in transmission between routers. This is checked at each router. 3 It also contains a payload, i. e. the main data being transmitted (e. g. a part of the image data)

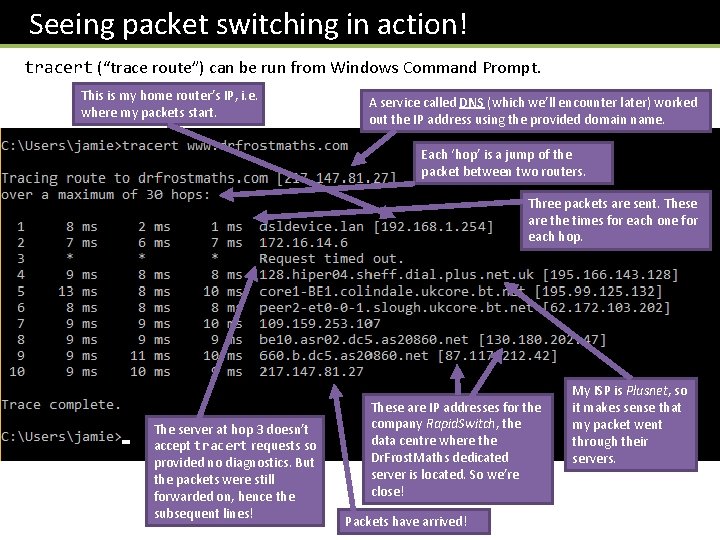
Seeing packet switching in action! tracert (“trace route”) can be run from Windows Command Prompt. This is my home router’s IP, i. e. where my packets start. A service called DNS (which we’ll encounter later) worked out the IP address using the provided domain name. Each ‘hop’ is a jump of the packet between two routers. Three packets are sent. These are the times for each one for each hop. The server at hop 3 doesn’t accept tracert requests so provided no diagnostics. But the packets were still forwarded on, hence the subsequent lines! These are IP addresses for the company Rapid. Switch, the data centre where the Dr. Frost. Maths dedicated server is located. So we’re close! Packets have arrived! My ISP is Plusnet, so it makes sense that my packet went through their servers.

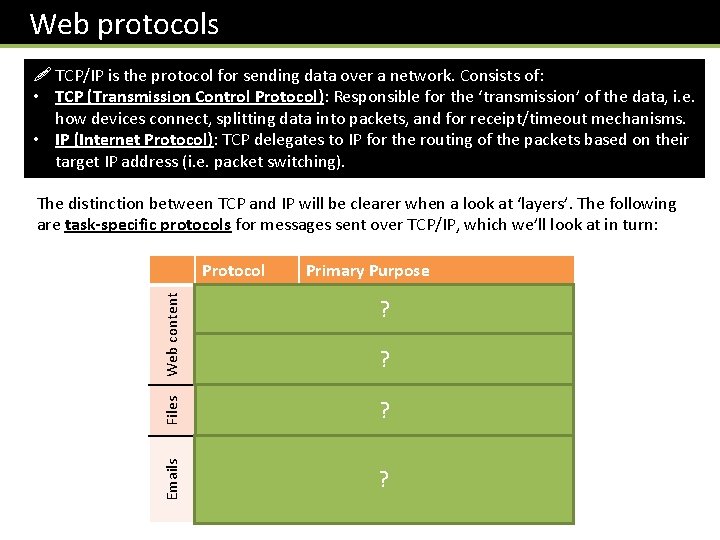
Web protocols ! TCP/IP is the protocol for sending data over a network. Consists of: • TCP (Transmission Control Protocol): Responsible for the ‘transmission’ of the data, i. e. how devices connect, splitting data into packets, and for receipt/timeout mechanisms. • IP (Internet Protocol): TCP delegates to IP for the routing of the packets based on their target IP address (i. e. packet switching). Primary Purpose Web content HTTP Requesting/sending web content ? (web pages, images, videos, …) HTTPS As above but data is encrypted. FTP For sending/receiving files. SMTP For sending emails. POP 3 For receiving emails. ? Emails Protocol Files The distinction between TCP and IP will be clearer when a look at ‘layers’. The following are task-specific protocols for messages sent over TCP/IP, which we’ll look at in turn: IMAP ? ?

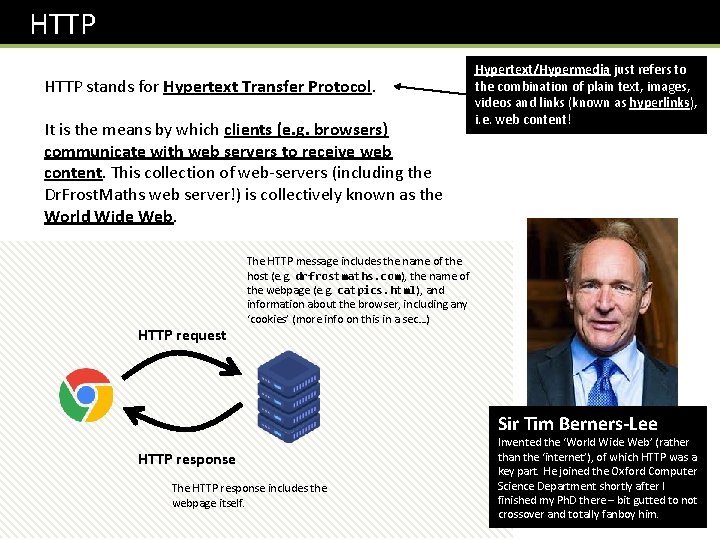
HTTP stands for Hypertext Transfer Protocol. It is the means by which clients (e. g. browsers) communicate with web servers to receive web content. This collection of web-servers (including the Dr. Frost. Maths web server!) is collectively known as the World Wide Web. HTTP request Hypertext/Hypermedia just refers to the combination of plain text, images, videos and links (known as hyperlinks), i. e. web content! The HTTP message includes the name of the host (e. g. drfrostmaths. com), the name of the webpage (e. g. catpics. html), and information about the browser, including any ‘cookies’ (more info on this in a sec…) Sir Tim Berners-Lee HTTP response The HTTP response includes the webpage itself. Invented the ‘World Wide Web’ (rather than the ‘internet’), of which HTTP was a key part. He joined the Oxford Computer Science Department shortly after I finished my Ph. D there – bit gutted to not crossover and totally fanboy him.

Example HTTP request… (technical detail not in the syllabus) I wrote a quick PHP script to output all the ‘headers’ in the HTTP request sent from my browser (in this case Chrome). Feel free to run it yourself! The domain name on which the server is listening. This is to do with browser caching. Basically the browser is requesting a ‘freshly generated’ copy of the page. The browser is expressing a preference for an encrypted response, e. g. via https. Once the content of the webpage is delivered to the client/browser, there’s no need to keep a connection open to the server. However, were you to play the “Dr. Frost. Maths Live!” game, the connection would be kept open so that you could receive game updates. This is a list of all the media types that the browser will accept in response to this HTTP request. Media types (previously known as ‘MIME’ types) indicates what type of content it is. Text/html for example is just “Text or HTML”. A cookie is a small file that the web server stores on the client computer, intended to remember something about the user. For example, it allows your browser to ‘remember’ that you are logged in to a website when you load each page. Here PHPSESSID is an identifying number issued by my server when someone logs in. It corresponds to a logged in user account. Since the server has your account information associated with this id, it knows who is logged in when it receives this id from your browser. Notice that the id is an extremely long string, making it difficult to forge someone else’s login. These ‘session ids’ expire and are generated on-the-fly each time you log in, so you won’t be able to use it to log in as me! There’s a lot to this one, and is intended to give information about what the browser supports. The format is: Mozilla/<version> (<system-information>) <platform> (<platform-details>) <extensions> • Mozilla is a free software community, for example developing the Firefox browser. Mozilla/5. 0 just says the client/browser is Mozilla compatible. • This is information about the machine I’m running the browser on. It’s a 64 -bit Windows machine. • Gecko and KHTML (‘Konqueror’) are rendering engines (i. e. to display/’render’ web content on your browser) developed by Mozilla and Linux respectively.

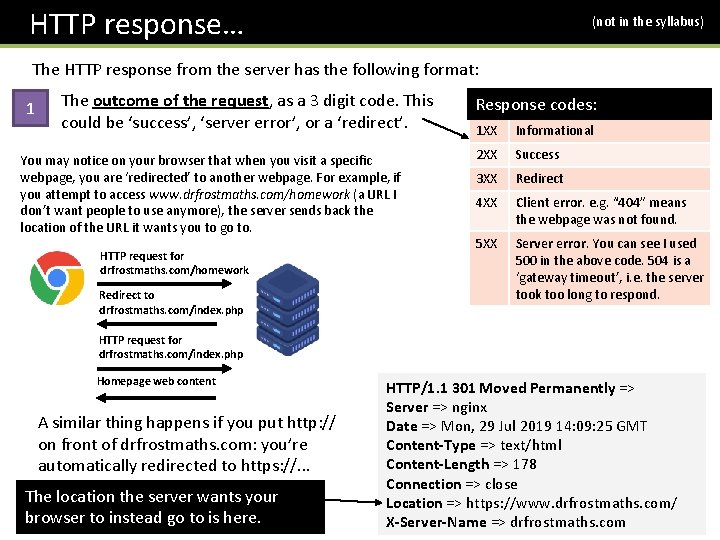
HTTP response… (not in the syllabus) The HTTP response from the server has the following format: 1 The outcome of the request, as a 3 digit code. This could be ‘success’, ‘server error’, or a ‘redirect’. You may notice on your browser that when you visit a specific webpage, you are ‘redirected’ to another webpage. For example, if you attempt to access www. drfrostmaths. com/homework (a URL I don’t want people to use anymore), the server sends back the location of the URL it wants you to go to. HTTP request for drfrostmaths. com/homework Redirect to drfrostmaths. com/index. php Response codes: 1 XX Informational 2 XX Success 3 XX Redirect 4 XX Client error. e. g. “ 404” means the webpage was not found. 5 XX Server error. You can see I used 500 in the above code. 504 is a ‘gateway timeout’, i. e. the server took too long to respond. HTTP request for drfrostmaths. com/index. php Homepage web content A similar thing happens if you put http: // on front of drfrostmaths. com: you’re automatically redirected to https: //. . . The location the server wants your browser to instead go to is here. HTTP/1. 1 301 Moved Permanently => Server => nginx Date => Mon, 29 Jul 2019 14: 09: 25 GMT Content-Type => text/html Content-Length => 178 Connection => close Location => https: //www. drfrostmaths. com/ X-Server-Name => drfrostmaths. com

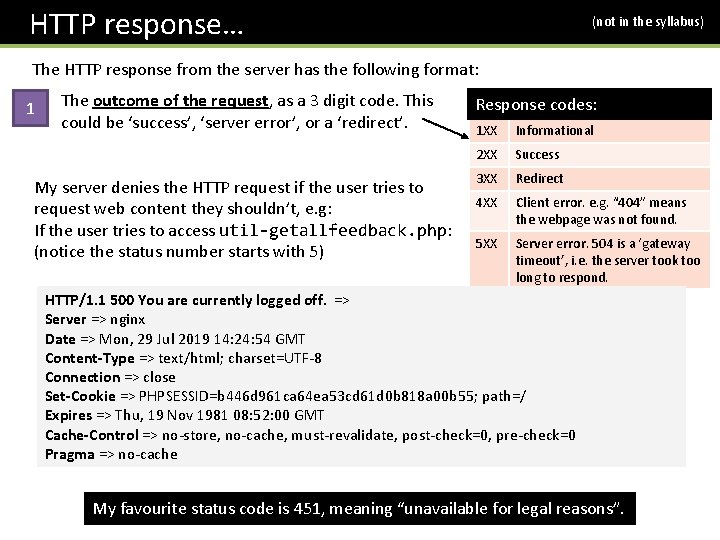
HTTP response… (not in the syllabus) The HTTP response from the server has the following format: 1 The outcome of the request, as a 3 digit code. This could be ‘success’, ‘server error’, or a ‘redirect’. My server denies the HTTP request if the user tries to request web content they shouldn’t, e. g: If the user tries to access util-getallfeedback. php: (notice the status number starts with 5) Response codes: 1 XX Informational 2 XX Success 3 XX Redirect 4 XX Client error. e. g. “ 404” means the webpage was not found. 5 XX Server error. 504 is a ‘gateway timeout’, i. e. the server took too long to respond. HTTP/1. 1 500 You are currently logged off. => Server => nginx Date => Mon, 29 Jul 2019 14: 24: 54 GMT Content-Type => text/html; charset=UTF-8 Connection => close Set-Cookie => PHPSESSID=b 446 d 961 ca 64 ea 53 cd 61 d 0 b 818 a 00 b 55; path=/ Expires => Thu, 19 Nov 1981 08: 52: 00 GMT Cache-Control => no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma => no-cache My favourite status code is 451, meaning “unavailable for legal reasons”.

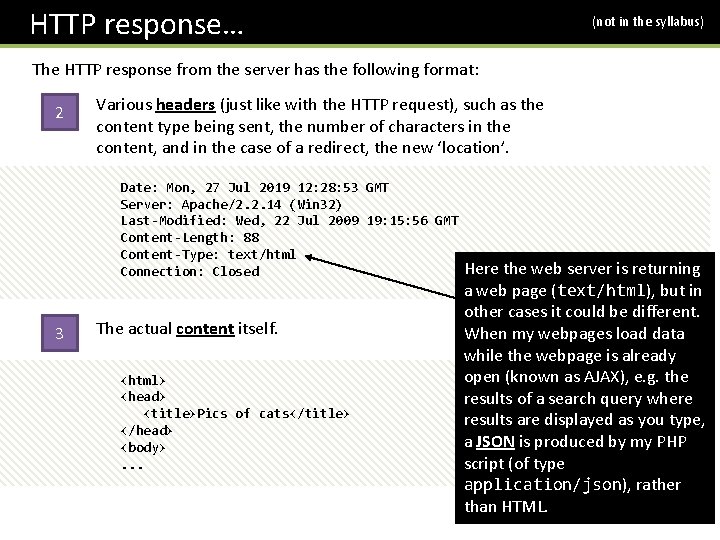
HTTP response… (not in the syllabus) The HTTP response from the server has the following format: 2 Various headers (just like with the HTTP request), such as the content type being sent, the number of characters in the content, and in the case of a redirect, the new ‘location’. Date: Mon, 27 Jul 2019 12: 28: 53 GMT Server: Apache/2. 2. 14 (Win 32) Last-Modified: Wed, 22 Jul 2009 19: 15: 56 GMT Content-Length: 88 Content-Type: text/html Connection: Closed 3 The actual content itself. <html> <head> <title>Pics of cats</title> </head> <body>. . . Here the web server is returning a web page (text/html), but in other cases it could be different. When my webpages load data while the webpage is already open (known as AJAX), e. g. the results of a search query where results are displayed as you type, a JSON is produced by my PHP script (of type application/json), rather than HTML.

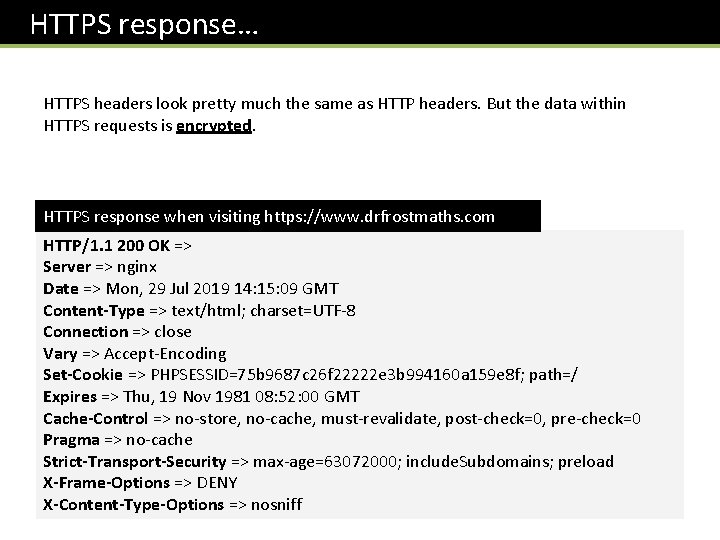
HTTPS response… HTTPS headers look pretty much the same as HTTP headers. But the data within HTTPS requests is encrypted. HTTPS response when visiting https: //www. drfrostmaths. com HTTP/1. 1 200 OK => Server => nginx Date => Mon, 29 Jul 2019 14: 15: 09 GMT Content-Type => text/html; charset=UTF-8 Connection => close Vary => Accept-Encoding Set-Cookie => PHPSESSID=75 b 9687 c 26 f 22222 e 3 b 994160 a 159 e 8 f; path=/ Expires => Thu, 19 Nov 1981 08: 52: 00 GMT Cache-Control => no-store, no-cache, must-revalidate, post-check=0, pre-check=0 Pragma => no-cache Strict-Transport-Security => max-age=63072000; include. Subdomains; preload X-Frame-Options => DENY X-Content-Type-Options => nosniff

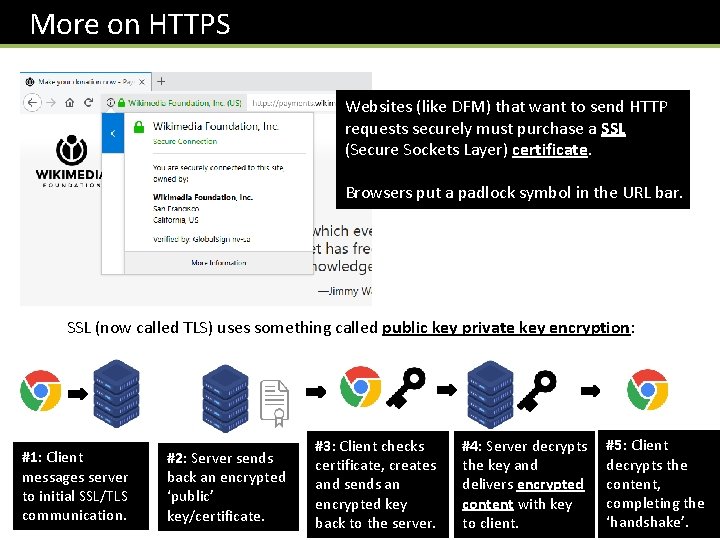
More on HTTPS Websites (like DFM) that want to send HTTP requests securely must purchase a SSL (Secure Sockets Layer) certificate. Browsers put a padlock symbol in the URL bar. SSL (now called TLS) uses something called public key private key encryption: #1: Client messages server to initial SSL/TLS communication. #2: Server sends back an encrypted ‘public’ key/certificate. #3: Client checks certificate, creates and sends an encrypted key back to the server. #4: Server decrypts the key and delivers encrypted content with key to client. #5: Client decrypts the content, completing the ‘handshake’.

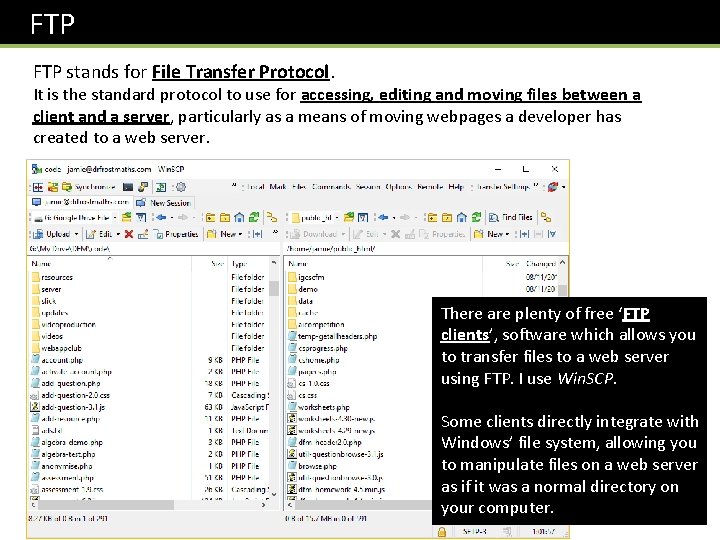
FTP stands for File Transfer Protocol. It is the standard protocol to use for accessing, editing and moving files between a client and a server, particularly as a means of moving webpages a developer has created to a web server. There are plenty of free ‘FTP clients’, software which allows you to transfer files to a web server using FTP. I use Win. SCP. Some clients directly integrate with Windows’ file system, allowing you to manipulate files on a web server as if it was a normal directory on your computer.

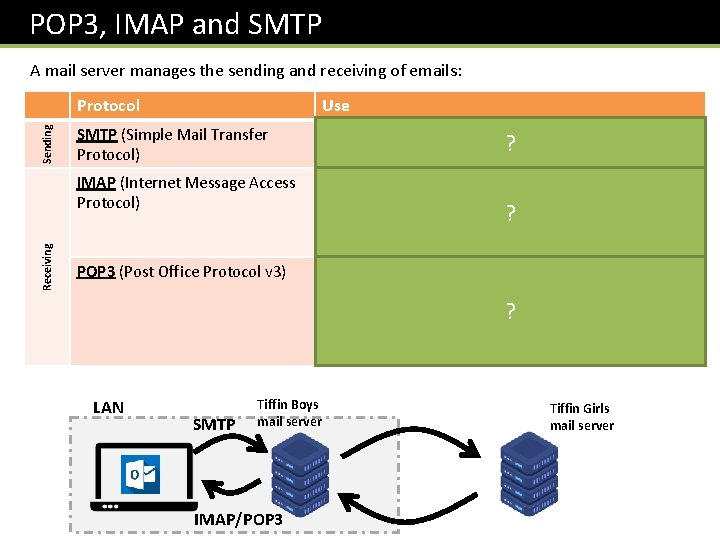
POP 3, IMAP and SMTP Receiving Sending A mail server manages the sending and receiving of emails: Protocol Use SMTP (Simple Mail Transfer Protocol) For outgoing emails sent from client to mail server. IMAP (Internet Message Access Protocol) Used to receive emails from the server. Messages stored on the server and can be accessed/synced ? across multiple devices. Message only removed from server if you delete it. POP 3 (Post Office Protocol v 3) Another protocol for receiving emails. Emails stored on a single device rather than server. Incoming emails to the mail ? server will be deleted after being passed on to the client, unless you request a copy to be kept. LAN SMTP ? Tiffin Boys mail server IMAP/POP 3 Tiffin Girls mail server

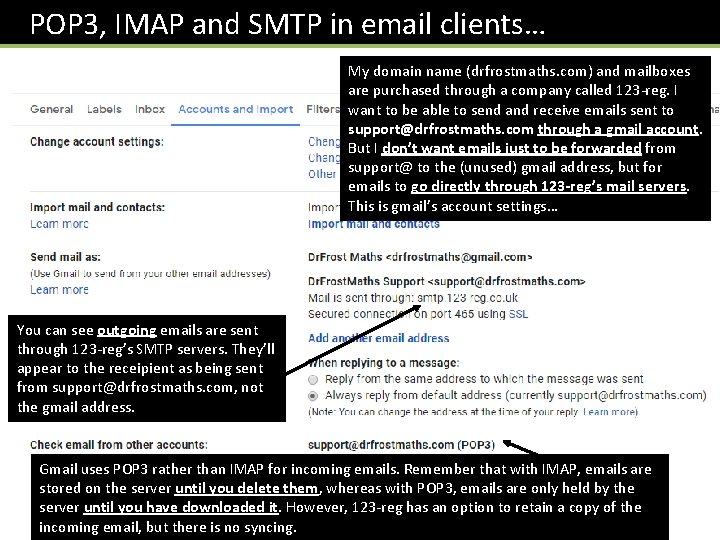
POP 3, IMAP and SMTP in email clients… My domain name (drfrostmaths. com) and mailboxes are purchased through a company called 123 -reg. I want to be able to send and receive emails sent to support@drfrostmaths. com through a gmail account. But I don’t want emails just to be forwarded from support@ to the (unused) gmail address, but for emails to go directly through 123 -reg’s mail servers. This is gmail’s account settings… You can see outgoing emails are sent through 123 -reg’s SMTP servers. They’ll appear to the receipient as being sent from support@drfrostmaths. com, not the gmail address. Gmail uses POP 3 rather than IMAP for incoming emails. Remember that with IMAP, emails are stored on the server until you delete them, whereas with POP 3, emails are only held by the server until you have downloaded it. However, 123 -reg has an option to retain a copy of the incoming email, but there is no syncing.

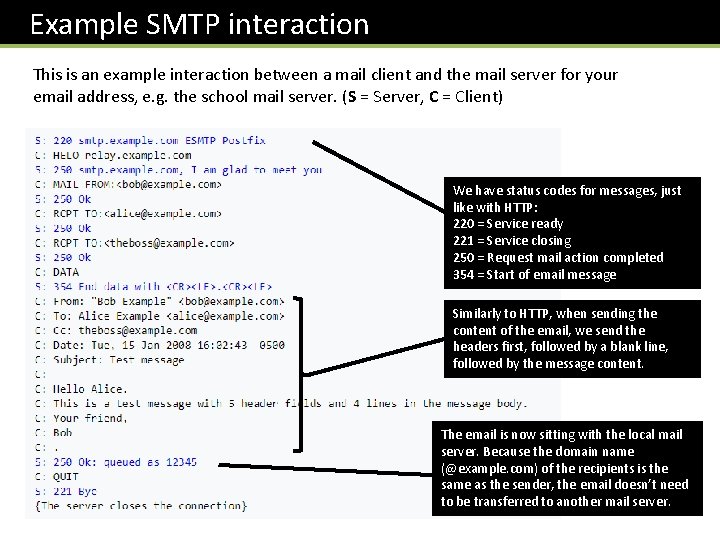
Example SMTP interaction This is an example interaction between a mail client and the mail server for your email address, e. g. the school mail server. (S = Server, C = Client) We have status codes for messages, just like with HTTP: 220 = Service ready 221 = Service closing 250 = Request mail action completed 354 = Start of email message Similarly to HTTP, when sending the content of the email, we send the headers first, followed by a blank line, followed by the message content. The email is now sitting with the local mail server. Because the domain name (@example. com) of the recipients is the same as the sender, the email doesn’t need to be transferred to another mail server.

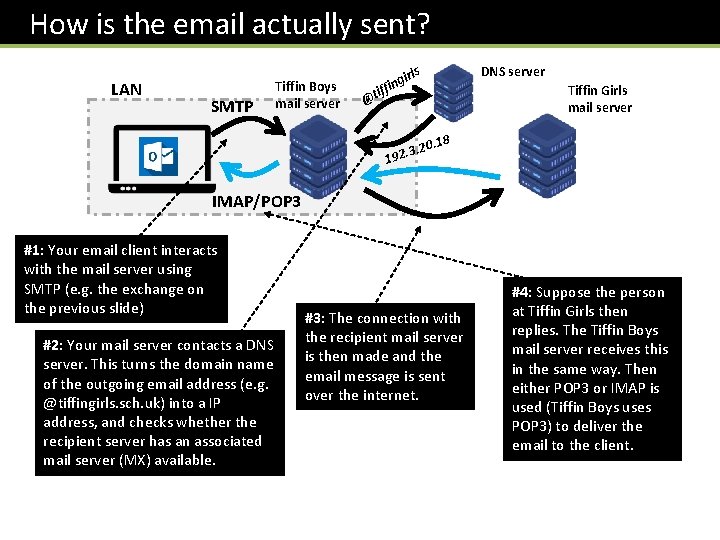
How is the email actually sent? LAN SMTP Tiffin Boys mail server DNS server irls ing iff @t Tiffin Girls mail server 0. 18 3. 2 192. IMAP/POP 3 #1: Your email client interacts with the mail server using SMTP (e. g. the exchange on the previous slide) #2: Your mail server contacts a DNS server. This turns the domain name of the outgoing email address (e. g. @tiffingirls. sch. uk) into a IP address, and checks whether the recipient server has an associated mail server (MX) available. #3: The connection with the recipient mail server is then made and the email message is sent over the internet. #4: Suppose the person at Tiffin Girls then replies. The Tiffin Boys mail server receives this in the same way. Then either POP 3 or IMAP is used (Tiffin Boys uses POP 3) to deliver the email to the client.

Exam Question ?

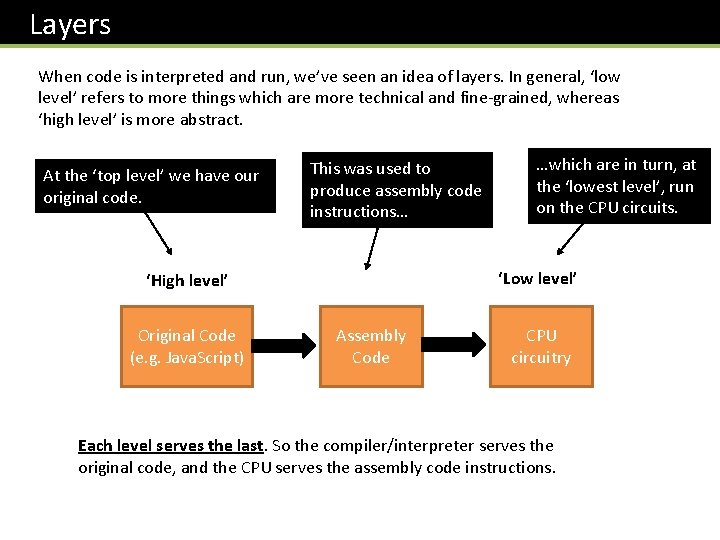
Layers When code is interpreted and run, we’ve seen an idea of layers. In general, ‘low level’ refers to more things which are more technical and fine-grained, whereas ‘high level’ is more abstract. At the ‘top level’ we have our original code. This was used to produce assembly code instructions… ‘Low level’ ‘High level’ Original Code (e. g. Java. Script) …which are in turn, at the ‘lowest level’, run on the CPU circuits. Assembly Code CPU circuitry Each level serves the last. So the compiler/interpreter serves the original code, and the CPU serves the assembly code instructions.

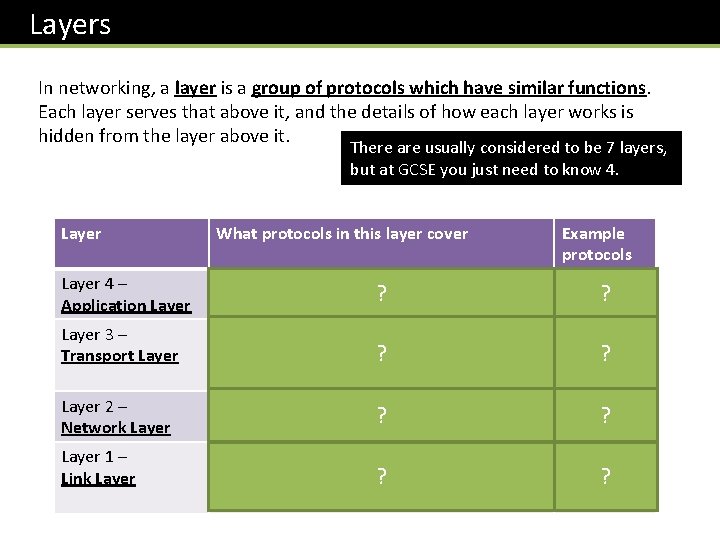
Layers In networking, a layer is a group of protocols which have similar functions. Each layer serves that above it, and the details of how each layer works is hidden from the layer above it. There are usually considered to be 7 layers, but at GCSE you just need to know 4. Layer What protocols in this layer cover Example protocols Layer 4 – Application Layer What the data actually represents, e. g. ? websites, files or emails. HTTP, ? SMTP, FTP Layer 3 – Transport Layer For the data flow, i. e. how devices connect, splitting data into packets and ? receipt/timeout mechanisms. TCP Layer 2 – Network Layer Routing of packets across the network. Use ? by routers. IP Layer 1 – Link Layer Data flow over a physical network, i. e. how bits are transmitted using electrical signals ? across wires. Ethernet ? ? ?

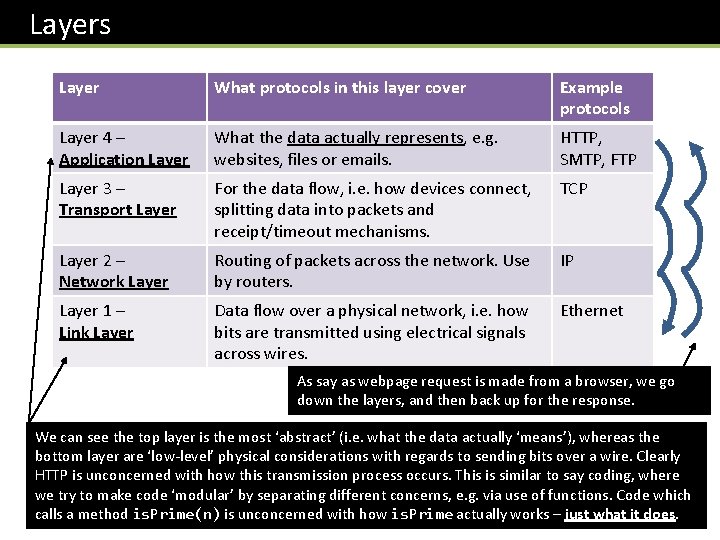
Layers Layer What protocols in this layer cover Example protocols Layer 4 – Application Layer What the data actually represents, e. g. websites, files or emails. HTTP, SMTP, FTP Layer 3 – Transport Layer For the data flow, i. e. how devices connect, splitting data into packets and receipt/timeout mechanisms. TCP Layer 2 – Network Layer Routing of packets across the network. Use by routers. IP Layer 1 – Link Layer Data flow over a physical network, i. e. how bits are transmitted using electrical signals across wires. Ethernet As say as webpage request is made from a browser, we go down the layers, and then back up for the response. We can see the top layer is the most ‘abstract’ (i. e. what the data actually ‘means’), whereas the bottom layer are ‘low-level’ physical considerations with regards to sending bits over a wire. Clearly HTTP is unconcerned with how this transmission process occurs. This is similar to say coding, where we try to make code ‘modular’ by separating different concerns, e. g. via use of functions. Code which calls a method is. Prime(n) is unconcerned with how is. Prime actually works – just what it does.

Layers ! Advantages of using layers 1. Breaks network communication into separate distinct concerns, so developers/manufacturers/engineers can concentrate one task at a time. 2. More generally, use of protocols within each layer ensures manufacturers/network operators produce software/hardware that works together within the network. 3. Layers are self-contained, meaning each can be exchanged without affecting other layers.

Reminder of OCR specification This stuff here.

Example Exam Questions ? ?