Network Security Contents Security Requirements and Attacks Confidentiality



















- Slides: 40

Network Security

Contents • Security Requirements and Attacks • Confidentiality with Conventional Encryption • Message Authentication and Hash Functions • Public-Key Encryption and Digital Signatures • IPv 4 and IPv 6 Security

Security Requirements • Confidentiality • Integrity • Availability

Passive Attacks • Release of message content (eavesdropping) – Prevented by encryption • Traffic Analysis – Fixed by traffic padding • Passive attacks are easier to prevent than to detect

Active Attacks • Involve the modification of the data stream or creation of a false data stream • Active Attacks are easier to detect than to prevent

Active Attacks (cont. ) • • Masquerade Replay Modification of messages Denial of service

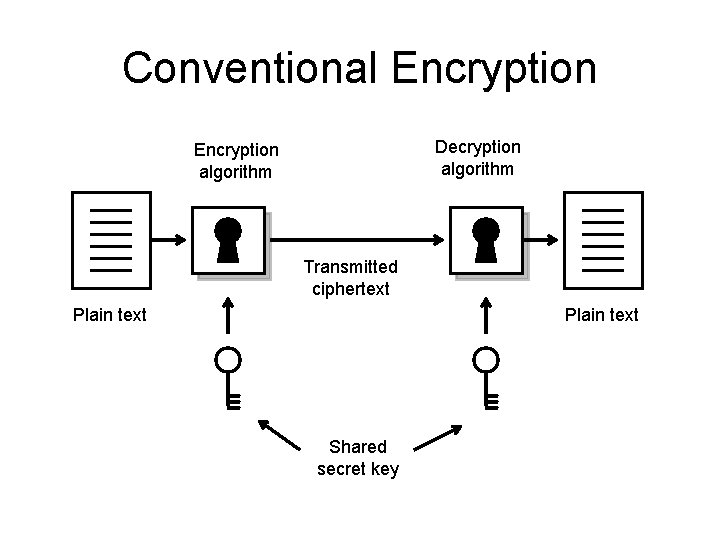
Conventional Encryption Decryption algorithm Encryption algorithm Transmitted ciphertext Plain text Shared secret key

Conventional Encryption Requirements • Knowing the algorithm, the plain text and the ciphered text, it shouldn’t be feasible to determine the key. • The key sharing must be done in a secure fashion.

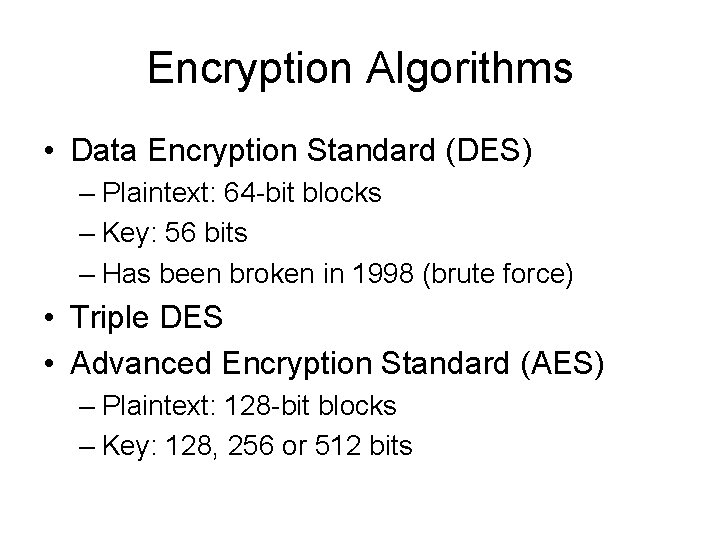
Encryption Algorithms • Data Encryption Standard (DES) – Plaintext: 64 -bit blocks – Key: 56 bits – Has been broken in 1998 (brute force) • Triple DES • Advanced Encryption Standard (AES) – Plaintext: 128 -bit blocks – Key: 128, 256 or 512 bits

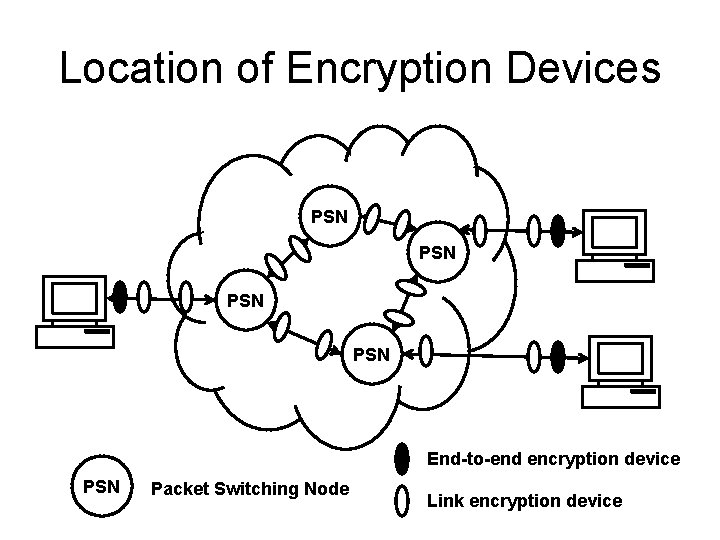
Location of Encryption Devices PSN PSN End-to-end encryption device PSN Packet Switching Node Link encryption device

Key Distribution • Manual – Selected by A, physically delivered to B – Selected by C, physically delivered to A and B • Automatic – The new key is sent encrypted with an old key – Sent through a 3 -rd party with which A and B have encrypted links

Message Authentication • Authentic message means that: – it comes from the alleged source – it has not been modified

Message Authentication Approaches • Authentication with conventional encryption • Authentication without message encryption: – when confidentiality is not necessary – when encryption is unpractical

Message Authentication Code • Uses a secret key to generate a small block of data MACM = F (KAB, M)

One-way Hash Function • Message digest – a “fingerprint” of the message • Like MAC, but without the use of a secret key • The message digest must be authenticated

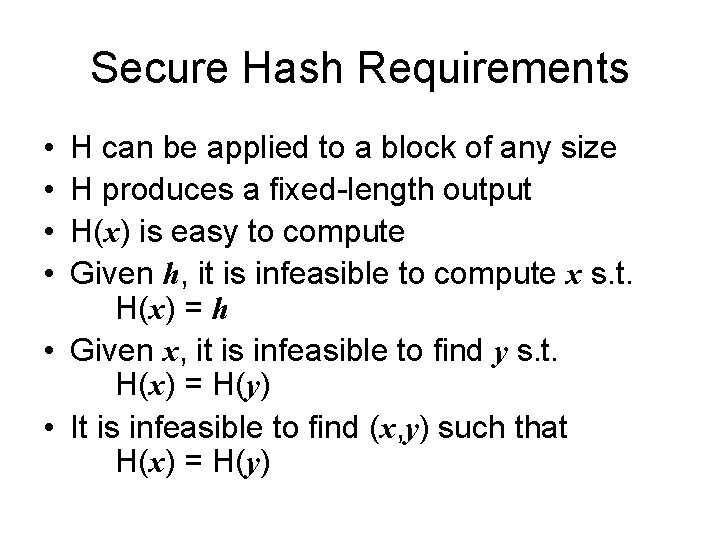
Secure Hash Requirements • • H can be applied to a block of any size H produces a fixed-length output H(x) is easy to compute Given h, it is infeasible to compute x s. t. H(x) = h • Given x, it is infeasible to find y s. t. H(x) = H(y) • It is infeasible to find (x, y) such that H(x) = H(y)

Secure Hash Functions • Message Digest v 5 (MD 5) – 128 -bit message digest – has been found to have collision weakness • Secure Hash Algorithm (SHA-1) – 160 -bit message digest

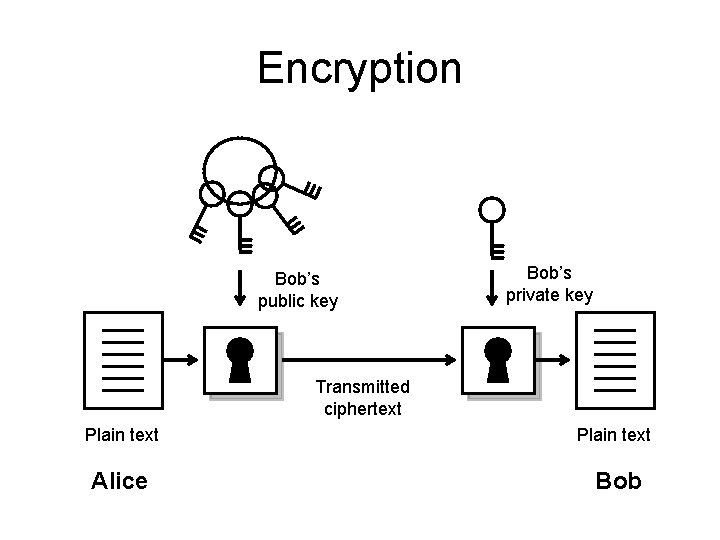
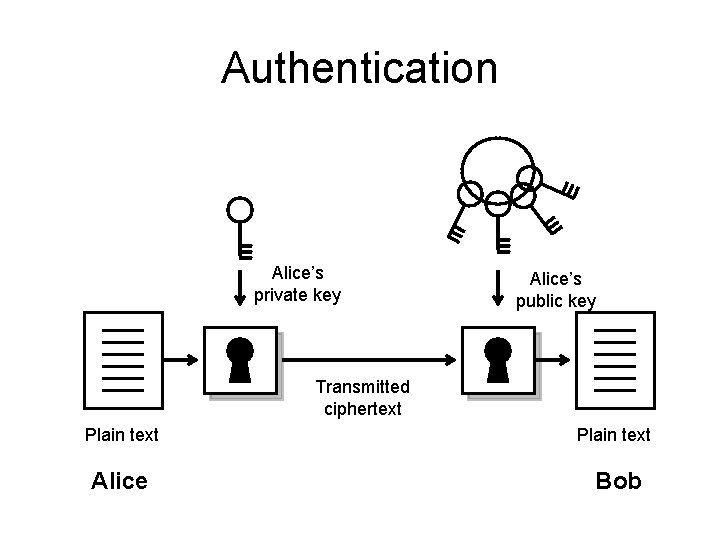
Public-Key Encryption • Each user has a pair of keys: – public key – private key • What is encrypted with one, can only be decrypted with the other

Encryption Bob’s public key Bob’s private key Transmitted ciphertext Plain text Alice Bob

Authentication Alice’s private key Alice’s public key Transmitted ciphertext Plain text Alice Bob

Digital Signature • Like authentication, only performed on a message authenticator (SHA-1)

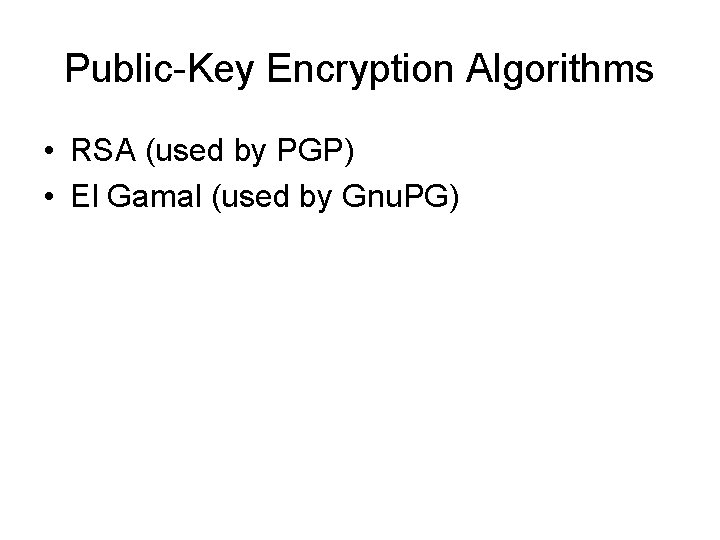
Public-Key Encryption Algorithms • RSA (used by PGP) • El Gamal (used by Gnu. PG)

Key Management • Public-Key encryption can be used to distribute secret keys for conventional encryption • Public-Key authentication: – signing authority – web of trust

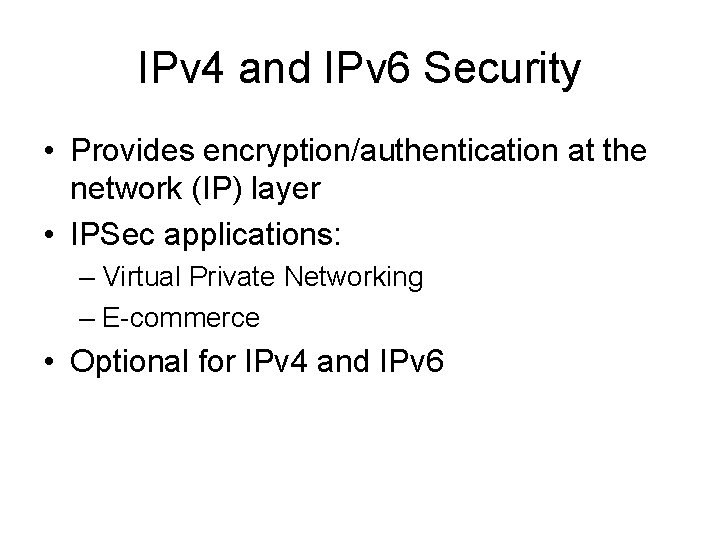
IPv 4 and IPv 6 Security • Provides encryption/authentication at the network (IP) layer • IPSec applications: – Virtual Private Networking – E-commerce • Optional for IPv 4 and IPv 6

IP Header with IPSec Information

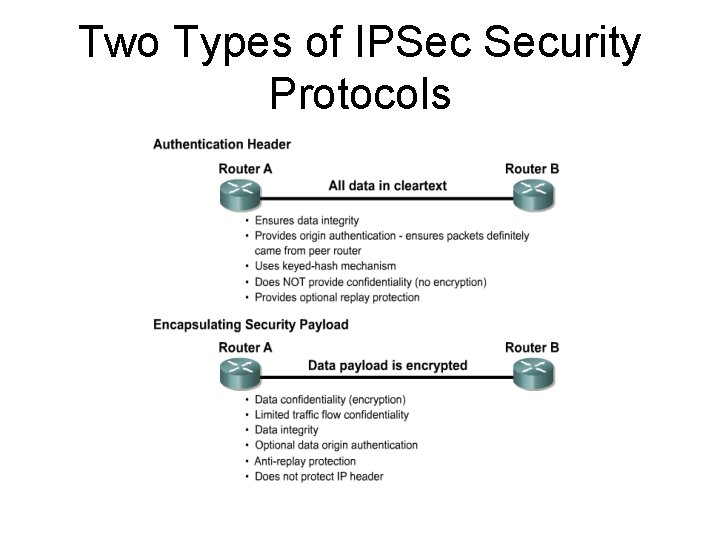
Two Types of IPSec Security Protocols

Advantages of IPSec

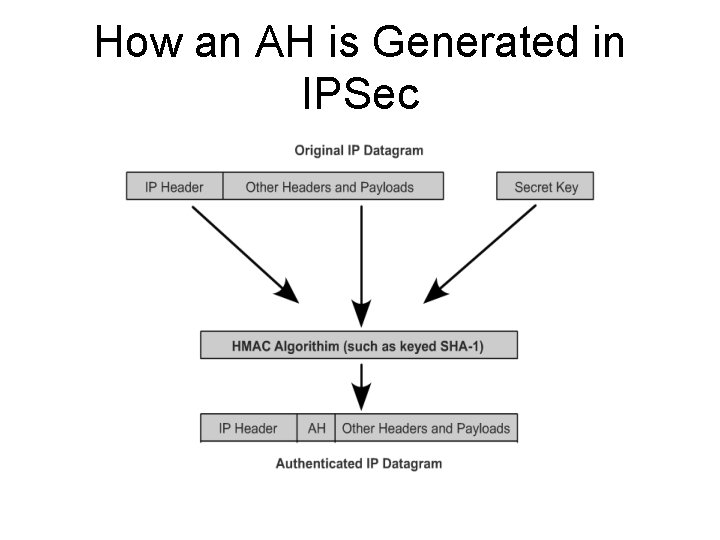
How an AH is Generated in IPSec

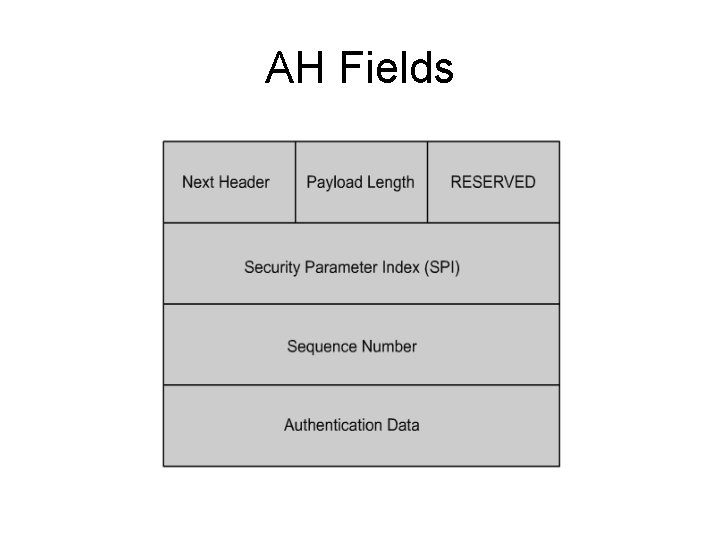
AH Fields

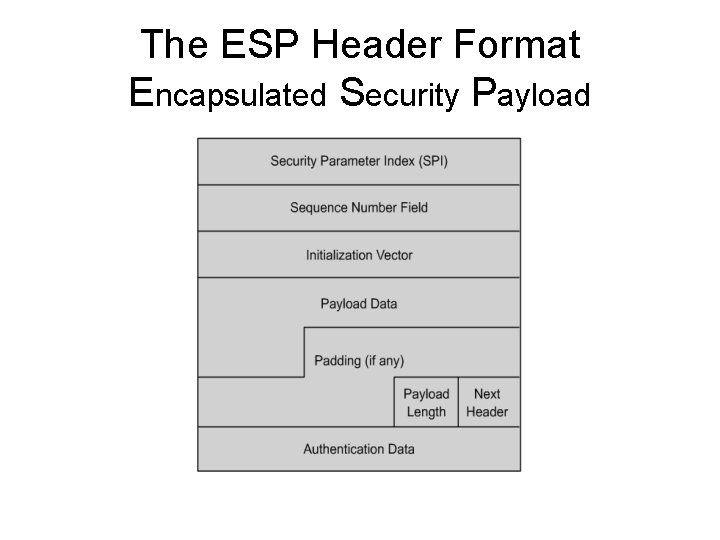
The ESP Header Format Encapsulated Security Payload

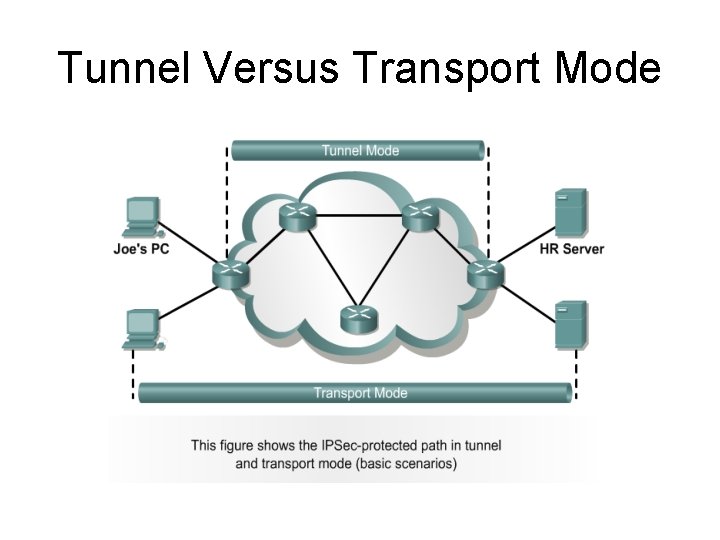
Tunnel Versus Transport Mode

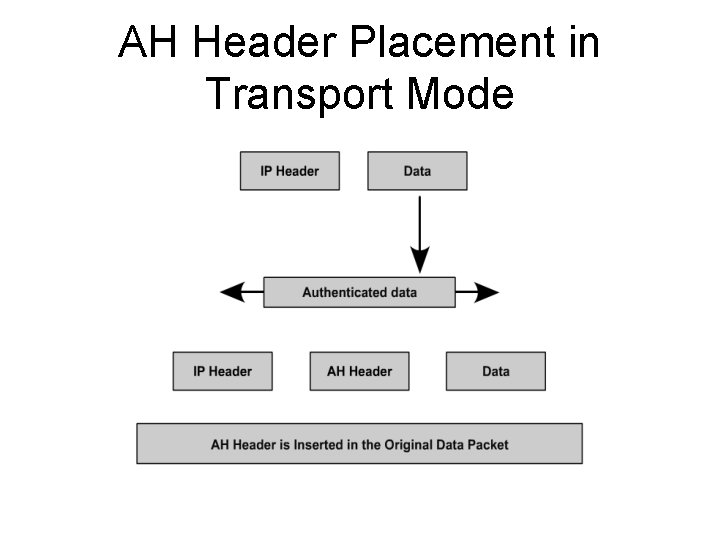
AH Header Placement in Transport Mode

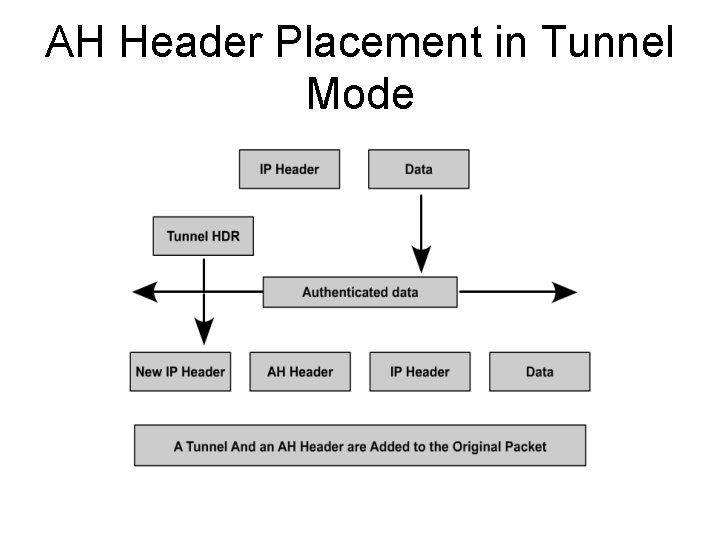
AH Header Placement in Tunnel Mode

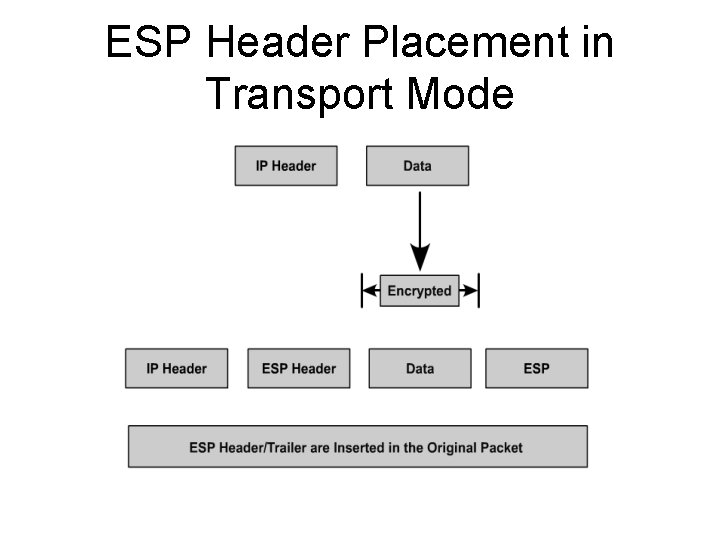
ESP Header Placement in Transport Mode

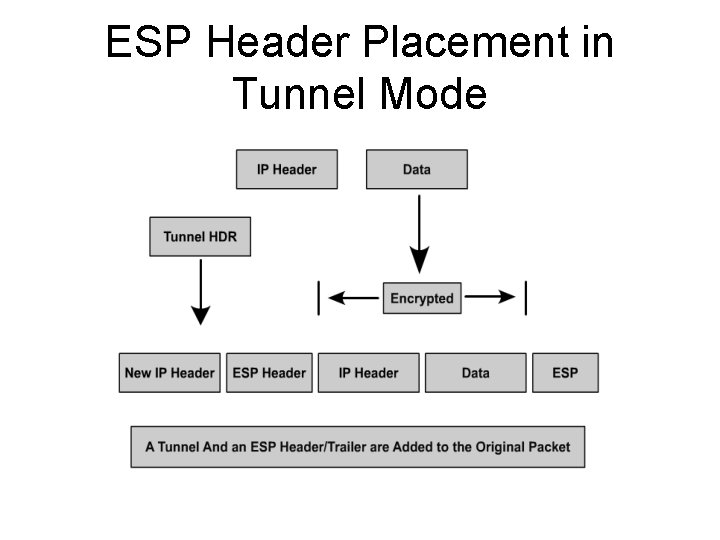
ESP Header Placement in Tunnel Mode

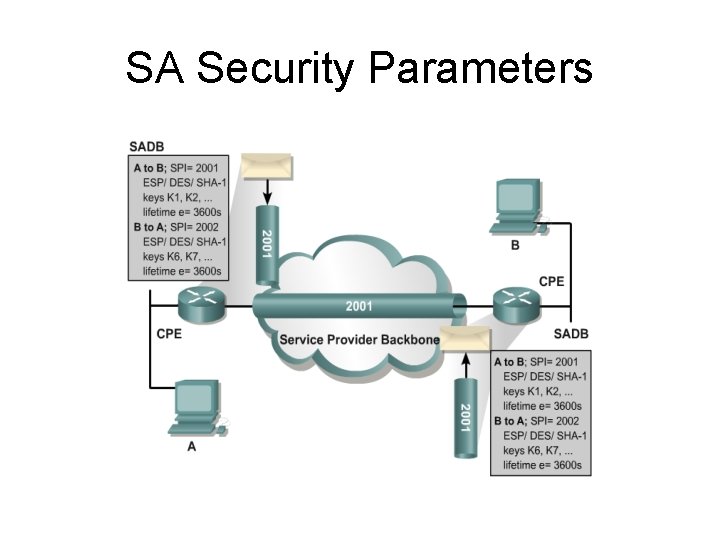
Security Association • One-way relationship between two hosts, providing security services for the payload • Uniquely identified by: – Security Parameter Index (SPI) – IP destination address – Security Protocol Identifier (AH/ESP)

SA Security Parameters

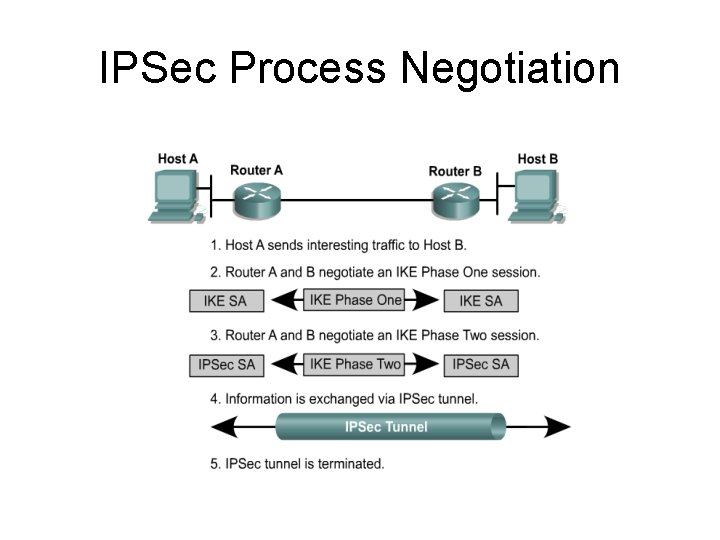
IPSec Process Negotiation

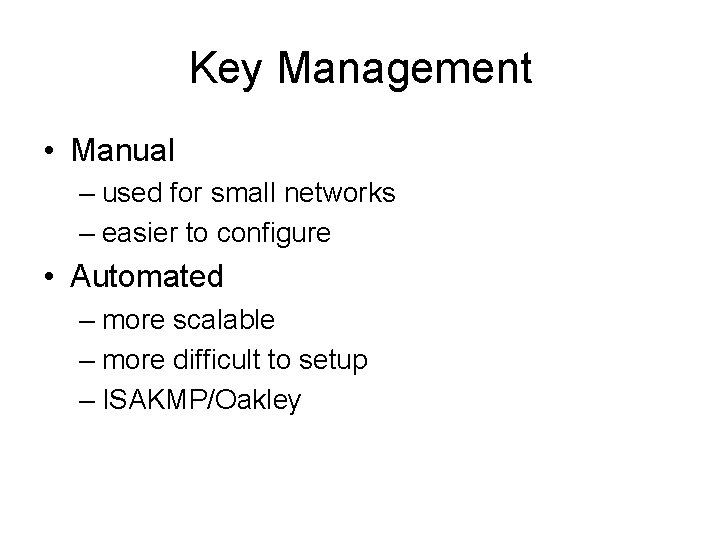
Key Management • Manual – used for small networks – easier to configure • Automated – more scalable – more difficult to setup – ISAKMP/Oakley

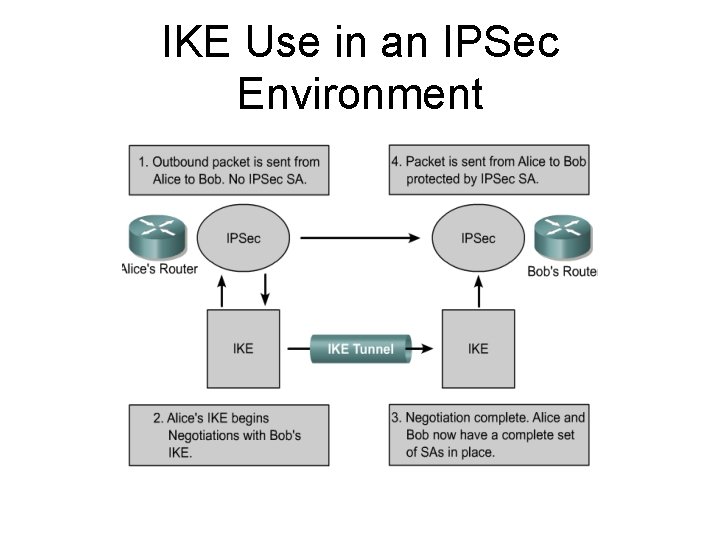
IKE Use in an IPSec Environment