Network Security and Cryptography Indrajit Das Dept of




- Slides: 28

Network Security and Cryptography Indrajit Das Dept. of IT, MSIT I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 1

OUTLINE v v v v Security and Security services Cryptography and its techniques Message Digest Message Authentication Code Digital Signature Firewall Access Control I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 2

Security v. Computer Security ØA mechanism that is designed to detect, prevent, or recover data from a attack. v. Network Security Ømeasures to protect data during their transmission v. Internet Security Ømeasures to protect data during their transmission over a collection of interconnected networks v. Attack ØAny action that compromises the security of information. v. Threat ØA potential for violation of security. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 3

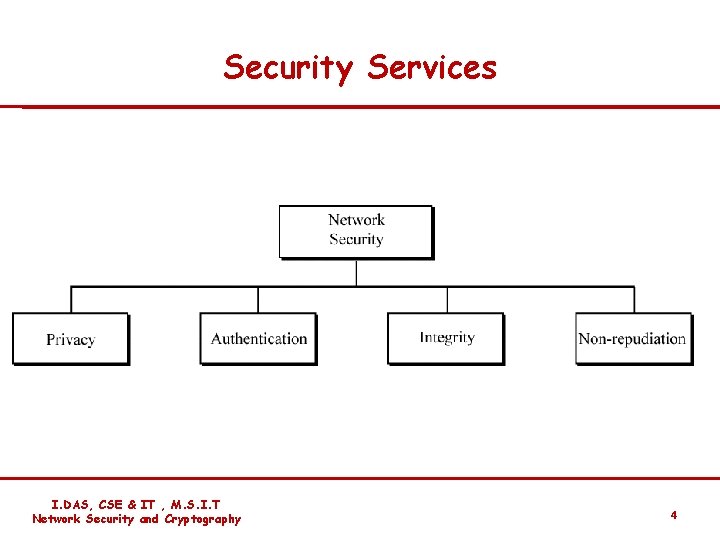
Security Services I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 4

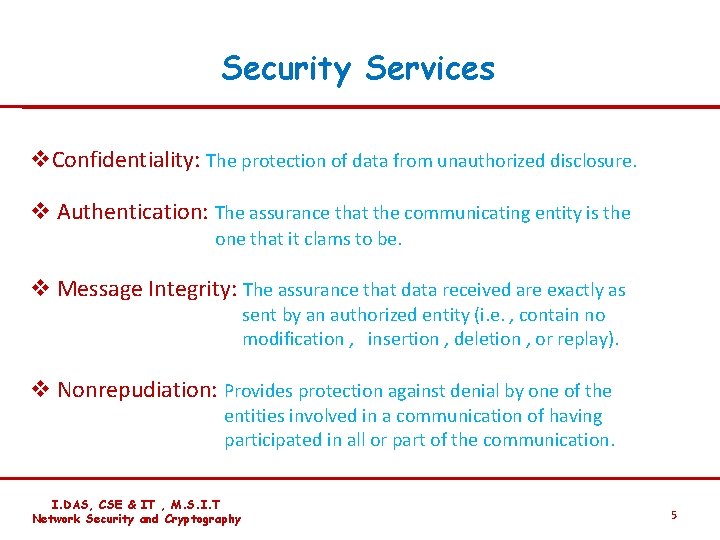
Security Services v. Confidentiality: The protection of data from unauthorized disclosure. v Authentication: The assurance that the communicating entity is the one that it clams to be. v Message Integrity: The assurance that data received are exactly as sent by an authorized entity (i. e. , contain no modification , insertion , deletion , or replay). v Nonrepudiation: Provides protection against denial by one of the entities involved in a communication of having participated in all or part of the communication. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 5

Cryptography v. Cryptography ØIt is the art of achieving security by encoding the messages to make them non – readable. v. Plain Text ØIt signifies a message that can be understood by the sender, the recipient, and also by anyone else who gets an access to that message. v. Cipher Text ØWhen a plain text is codified using any suitable scheme, the resulting message is called as cipher text. v. Encryption ØThe process of encoding plain text into cipher text is called as Encryption. v. Decryption ØWhereas the cipher text back into plain text is called as Decryption. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 6

Two aspects of Encryption and Decryption process v Algorithm v Key In general , the algorithm used for encryption and decryption process is usually known to every body. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 7

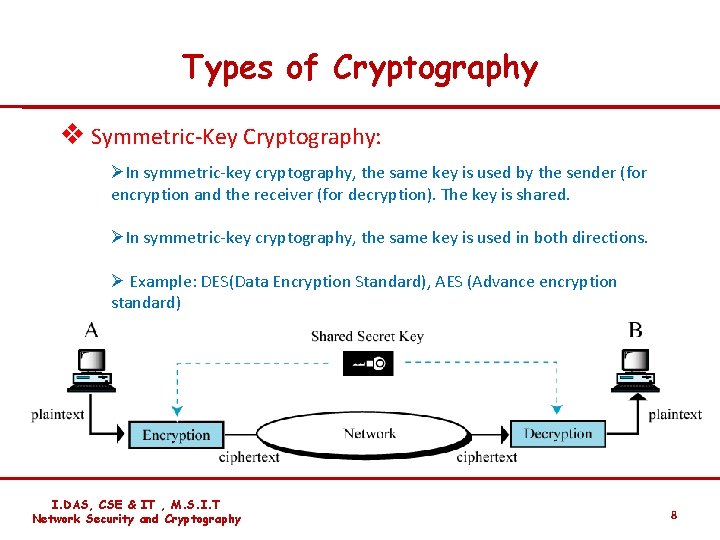
Types of Cryptography v Symmetric-Key Cryptography: ØIn symmetric-key cryptography, the same key is used by the sender (for encryption and the receiver (for decryption). The key is shared. ØIn symmetric-key cryptography, the same key is used in both directions. Ø Example: DES(Data Encryption Standard), AES (Advance encryption standard) I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 8

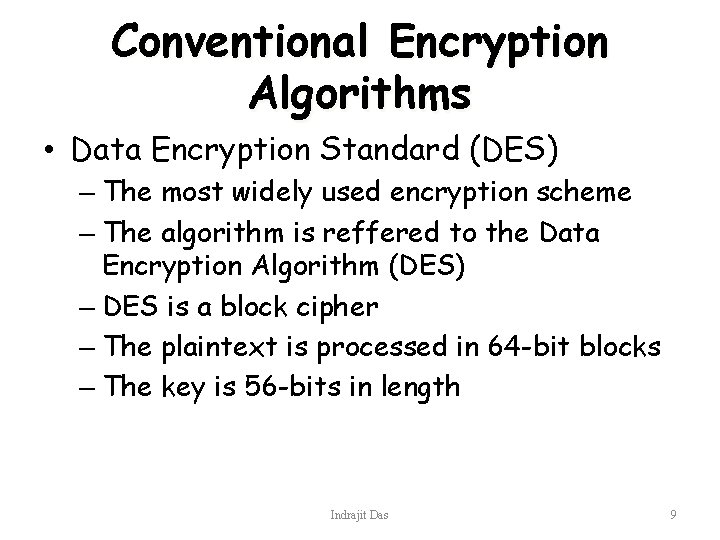
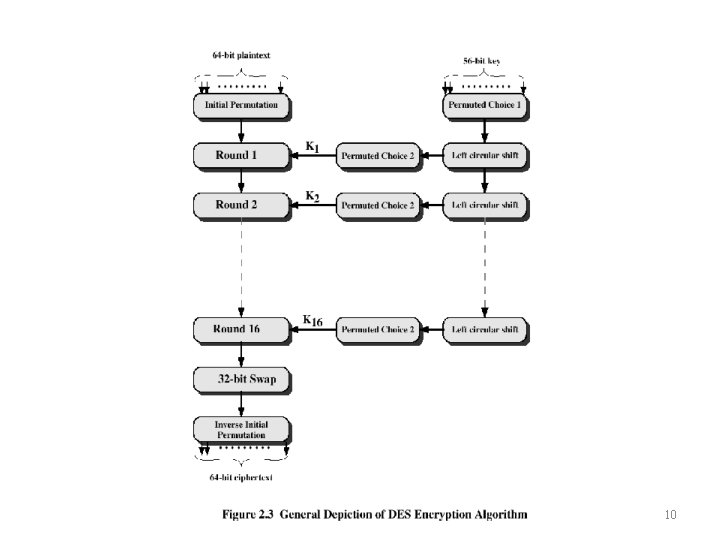
Conventional Encryption Algorithms • Data Encryption Standard (DES) – The most widely used encryption scheme – The algorithm is reffered to the Data Encryption Algorithm (DES) – DES is a block cipher – The plaintext is processed in 64 -bit blocks – The key is 56 -bits in length Indrajit Das 9

Indrajit Das 10

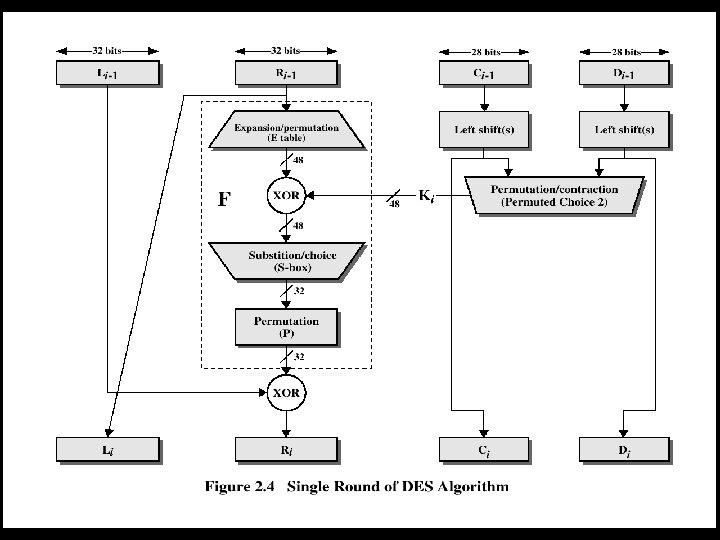
Indrajit Das 11

DES • The overall processing at each iteration: – Li = Ri-1 – Ri = Li-1 F(Ri-1, Ki) • Concerns about: – The algorithm and the key length (56 bits) Indrajit Das 12

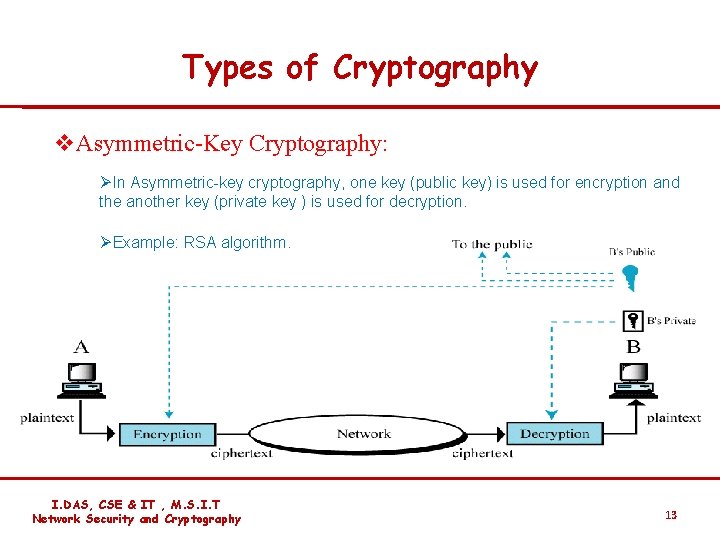
Types of Cryptography v. Asymmetric-Key Cryptography: ØIn Asymmetric-key cryptography, one key (public key) is used for encryption and the another key (private key ) is used for decryption. ØExample: RSA algorithm. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 13

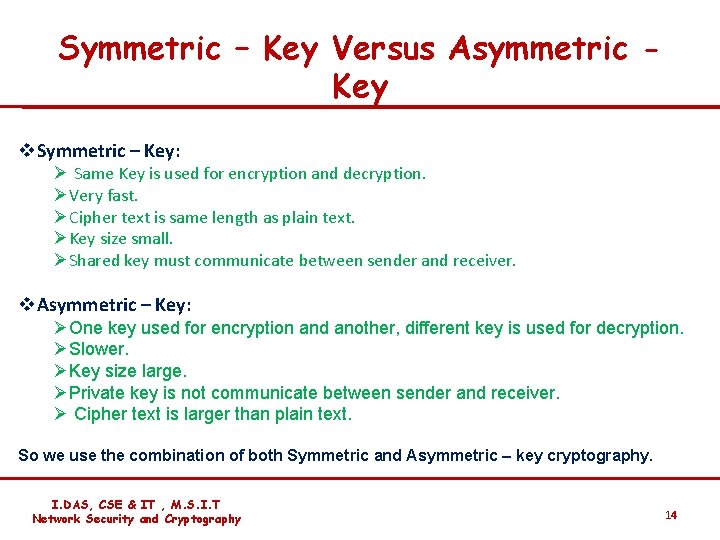
Symmetric – Key Versus Asymmetric Key v. Symmetric – Key: Ø Same Key is used for encryption and decryption. ØVery fast. ØCipher text is same length as plain text. ØKey size small. ØShared key must communicate between sender and receiver. v. Asymmetric – Key: ØOne key used for encryption and another, different key is used for decryption. ØSlower. ØKey size large. ØPrivate key is not communicate between sender and receiver. Ø Cipher text is larger than plain text. So we use the combination of both Symmetric and Asymmetric – key cryptography. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 14

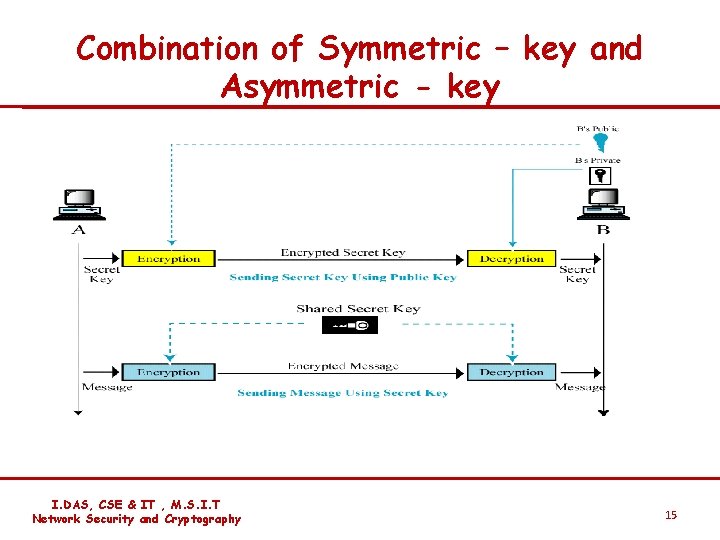
Combination of Symmetric – key and Asymmetric - key I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 15

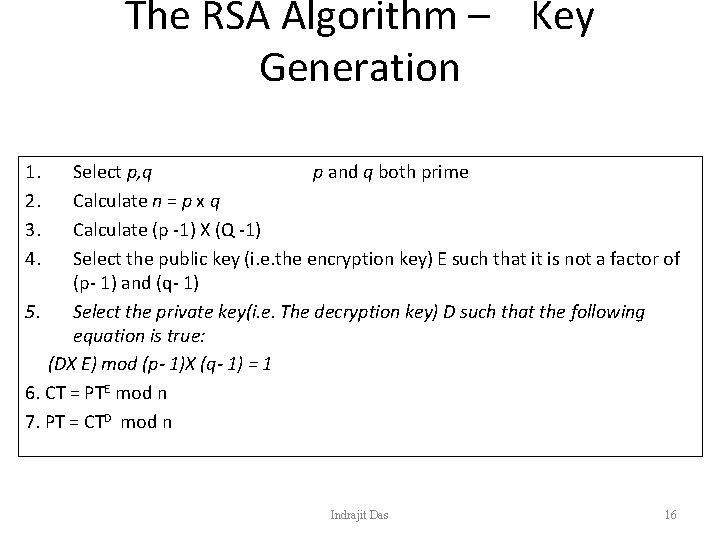
The RSA Algorithm – Key Generation 1. 2. 3. 4. Select p, q p and q both prime Calculate n = p x q Calculate (p -1) X (Q -1) Select the public key (i. e. the encryption key) E such that it is not a factor of (p- 1) and (q- 1) 5. Select the private key(i. e. The decryption key) D such that the following equation is true: (DX E) mod (p- 1)X (q- 1) = 1 6. CT = PTE mod n 7. PT = CTD mod n Indrajit Das 16

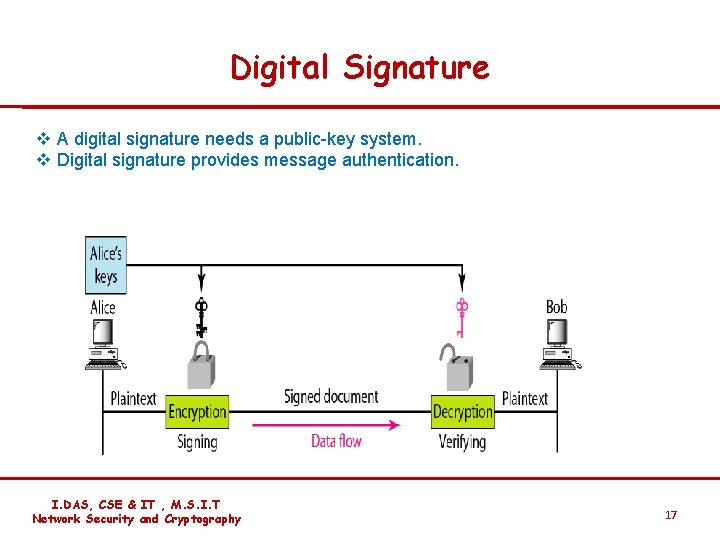
Digital Signature v A digital signature needs a public-key system. v Digital signature provides message authentication. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 17

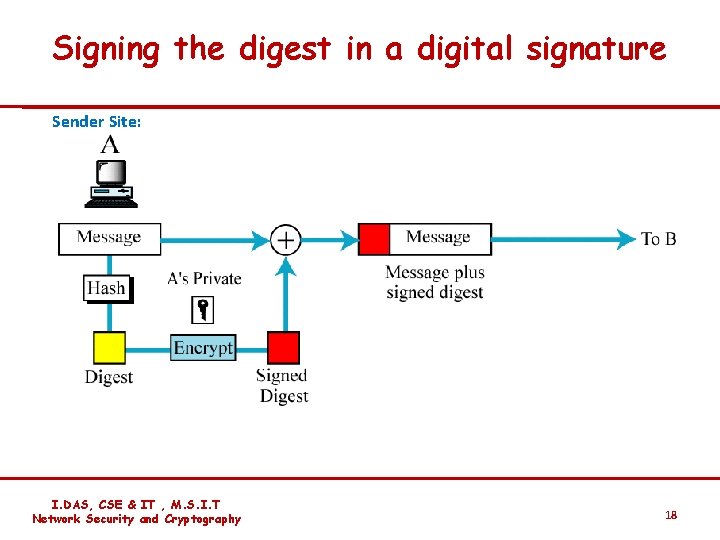
Signing the digest in a digital signature Sender Site: I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 18

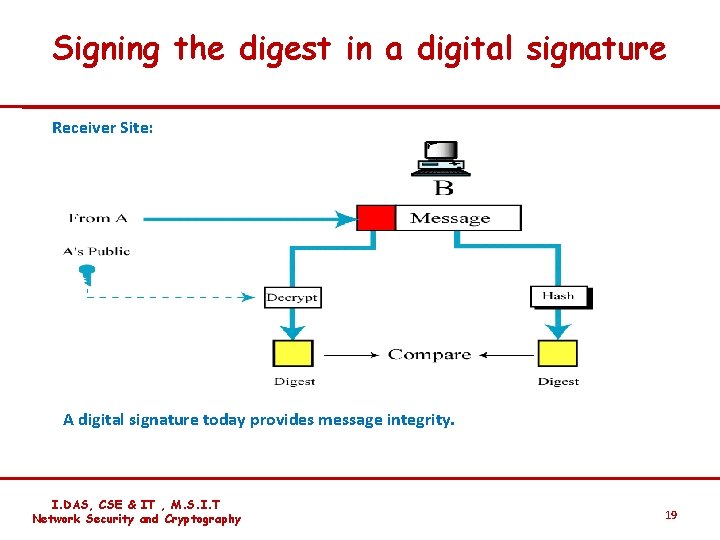
Signing the digest in a digital signature Receiver Site: A digital signature today provides message integrity. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 19

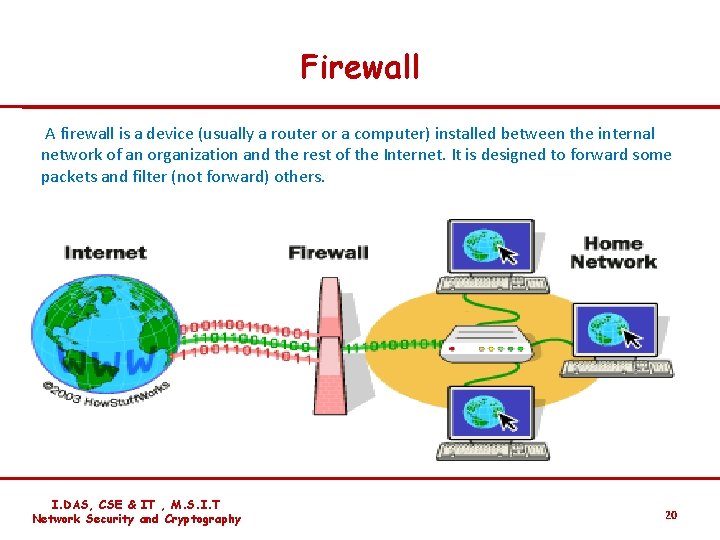
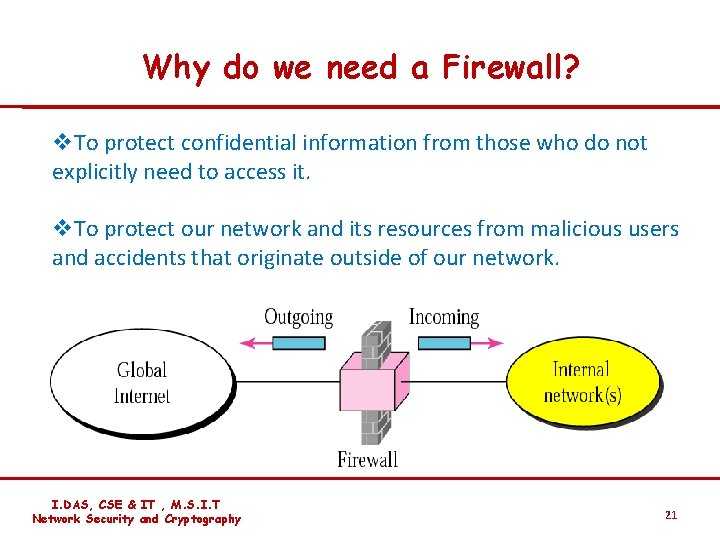
Firewall A firewall is a device (usually a router or a computer) installed between the internal network of an organization and the rest of the Internet. It is designed to forward some packets and filter (not forward) others. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 20

Why do we need a Firewall? v. To protect confidential information from those who do not explicitly need to access it. v. To protect our network and its resources from malicious users and accidents that originate outside of our network. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 21

Types of Firewall v. Packet Filters Ø Looks at each packet entering or leaving the network and accepts or rejects it based on user-defined rules. v Application Gateways or Proxy Server ØApplies security mechanisms to specific applications, such as FTP and Telnet servers. The proxy server effectively hides the true IP addresses. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 22

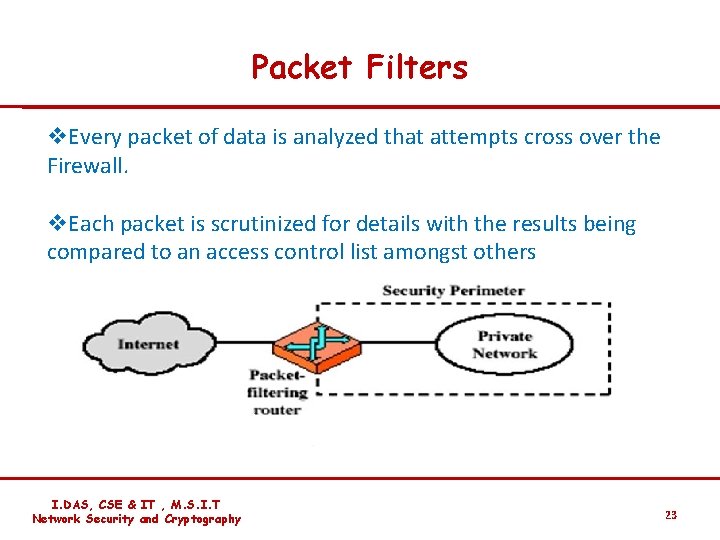
Packet Filters v. Every packet of data is analyzed that attempts cross over the Firewall. v. Each packet is scrutinized for details with the results being compared to an access control list amongst others I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 23

Application Gateway/ Proxy Server v An internal user contacts the application gateway using TCP/IP application, such as HTTP or TELNET. v The application gateway asks the user about the remote host with which the user wants to set up a connection for actual communication ( i. e, its domain name or IP address, etc. ). The application gateway also asks for the user id and the password required to access the services of the application gateway. v The user provides this information to the application gateway. v The application gateway now accesses the remote host on behalf of the user , and passes the packets of the user to the remote host. v The application gateway now encrypted the packet and add its own IP address as a source IP address. This way, the IP addresses of the computers of the internal users are hidden from the outside world. v The application gateway acts like a proxy of the user. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 24

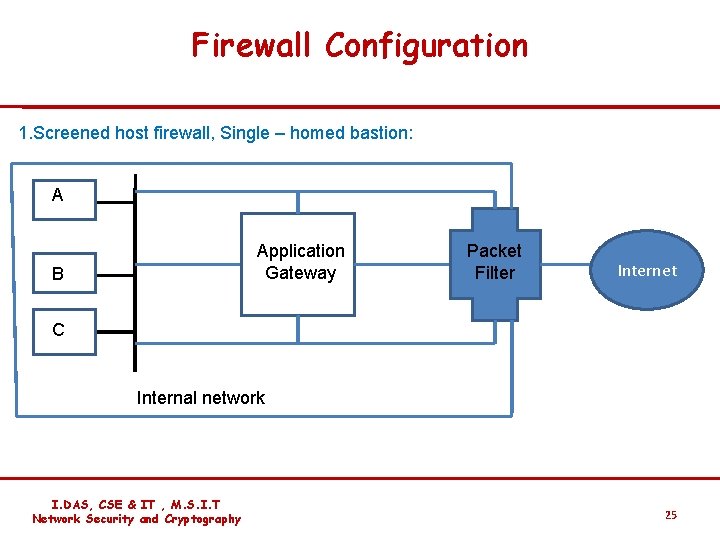
Firewall Configuration 1. Screened host firewall, Single – homed bastion: AA Application Gateway B Packet Filter Internet C Internal network I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 25

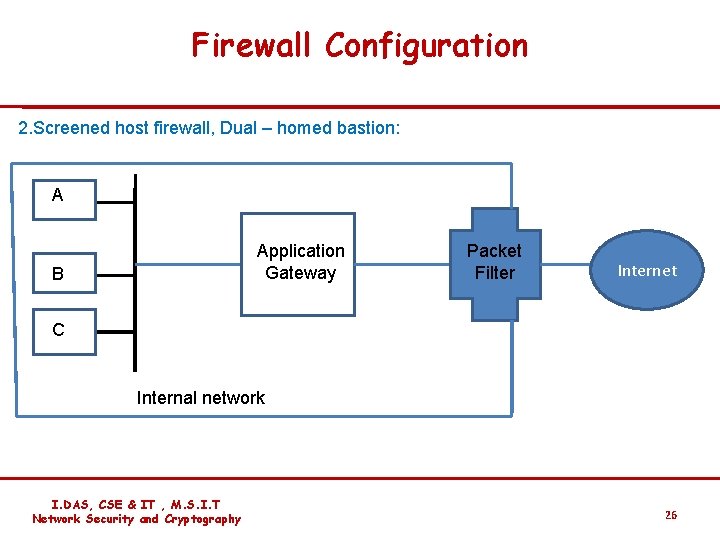
Firewall Configuration 2. Screened host firewall, Dual – homed bastion: AA Application Gateway B Packet Filter Internet C Internal network I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 26

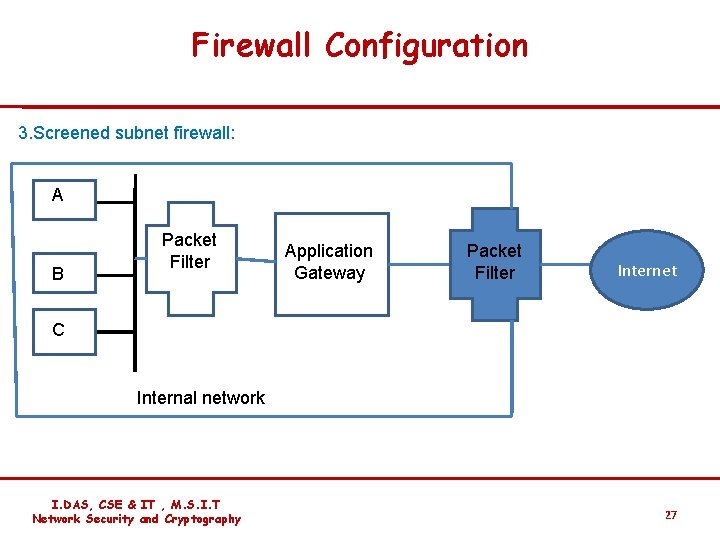
Firewall Configuration 3. Screened subnet firewall: AA B Packet Filter Application Gateway Packet Filter Internet C Internal network I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 27

Limitations of Firewall v Insider intrusion. v Direct Internet traffic. v Virus attacks. I. DAS, CSE & IT , M. S. I. T Network Security and Cryptography 28