Modelli di Controllo e Mitigazione per Attacchi DDo





- Slides: 20

Modelli di Controllo e Mitigazione per Attacchi DDo. S Filippo Farina EMEA Carrier Solution Architect www. radware. com ITNOG 5 - May 10 th, 2019

Agenda • DDo. S Security Trends • Anti-DDo. S Solution Pillars • Reference Architecture 2 www. radware. com

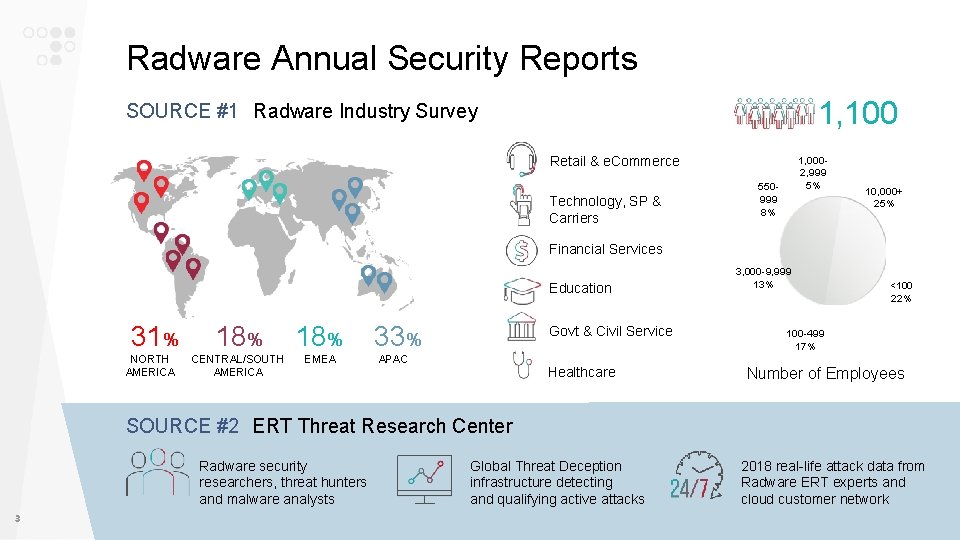
Radware Annual Security Reports 1, 100 SOURCE #1 Radware Industry Survey Retail & e. Commerce Technology, SP & Carriers 1, 0002, 999 5% 550999 8% 10, 000+ 25% Financial Services Education 31% NORTH AMERICA 18% CENTRAL/SOUTH AMERICA EMEA 33% Govt & Civil Service APAC Healthcare 3, 000 -9, 999 13% <100 22% 100 -499 17% Number of Employees SOURCE #2 ERT Threat Research Center Radware security researchers, threat hunters and malware analysts 3 Global Threat Deception infrastructure detecting and qualifying active attacks 2018 real-life attack data from Radware ERT experts and cloud customer network

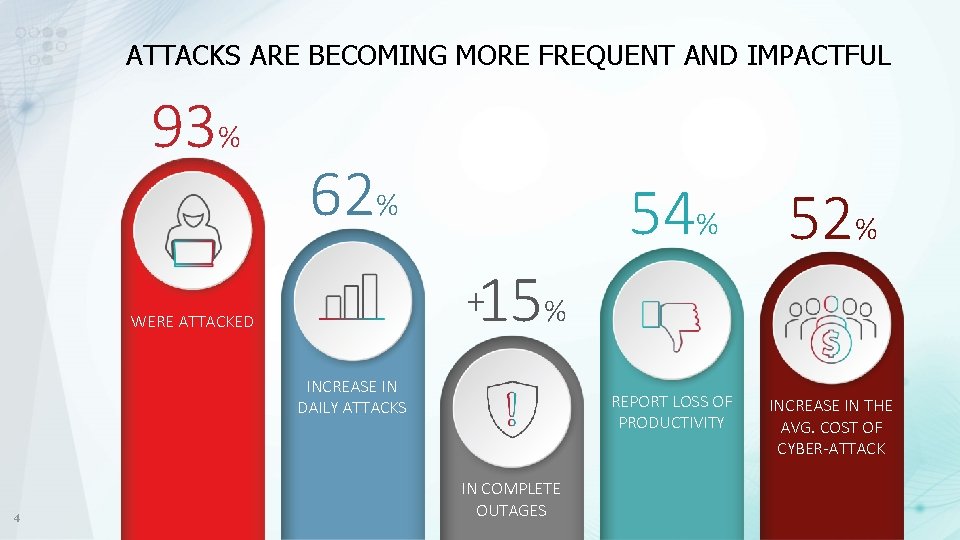
ATTACKS ARE BECOMING MORE FREQUENT AND IMPACTFUL 93% 62% 52% REPORT LOSS OF PRODUCTIVITY INCREASE IN THE AVG. COST OF CYBER-ATTACK 15% + WERE ATTACKED INCREASE IN DAILY ATTACKS 4 54% IN COMPLETE OUTAGES

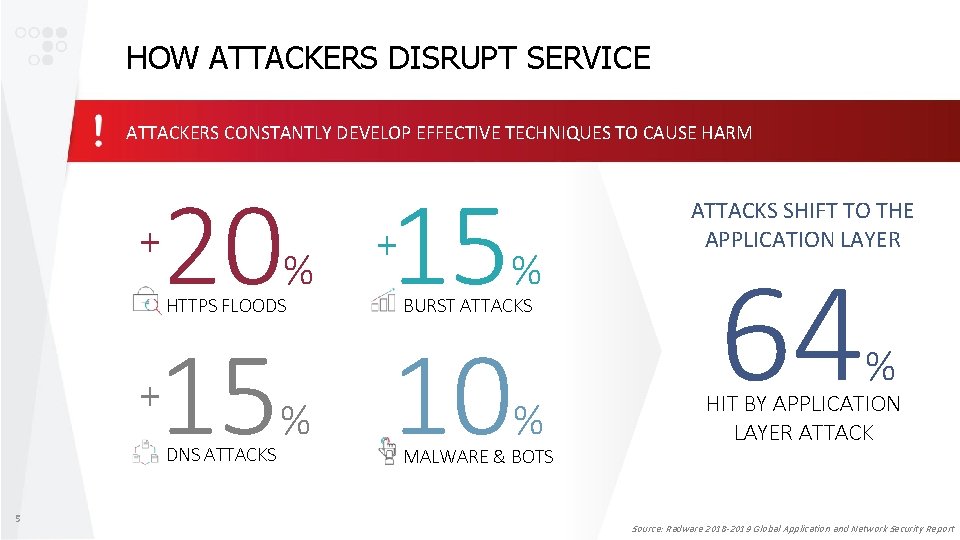
HOW ATTACKERS DISRUPT SERVICE ATTACKERS CONSTANTLY DEVELOP EFFECTIVE TECHNIQUES TO CAUSE HARM 20 15 15 10 + % HTTPS FLOODS + DNS ATTACKS 5 % + % BURST ATTACKS % MALWARE & BOTS ATTACKS SHIFT TO THE APPLICATION LAYER 64 % HIT BY APPLICATION LAYER ATTACK Source: Radware 2018 -2019 Global Application and Network Security Report

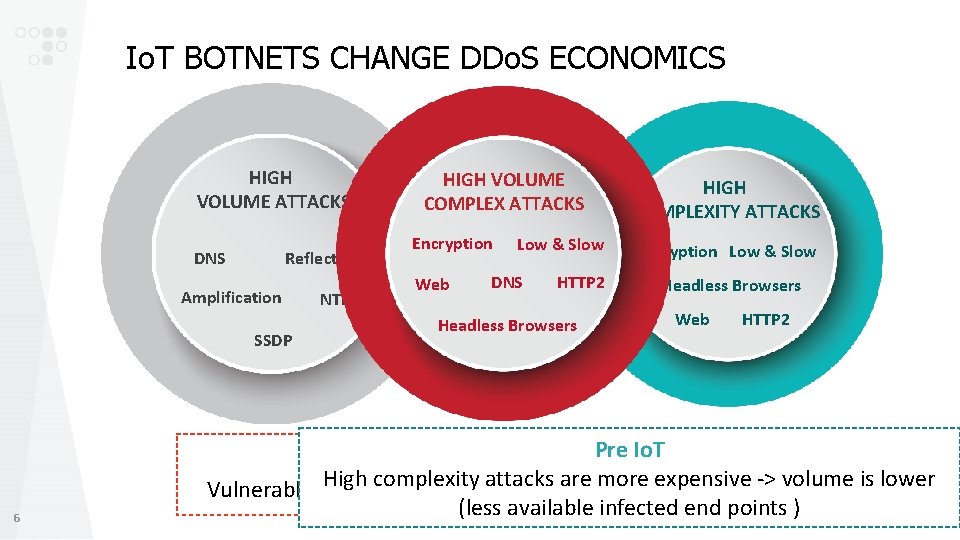
Io. T BOTNETS CHANGE DDo. S ECONOMICS HIGH VOLUME ATTACKS DNS Reflection Amplification SSDP 6 NTP HIGH VOLUME COMPLEX ATTACKS Encryption Web Low & Slow DNS HTTP 2 Headless Browsers HIGH COMPLEXITY ATTACKS Encryption Low & Slow Headless Browsers Web HTTP 2 In the Io. TPre Era. Io. T High complexity attacks are more expensive -> volume attacks is lower Vulnerable Io. T devices form huge botnets running high complexity (less available infected end points )

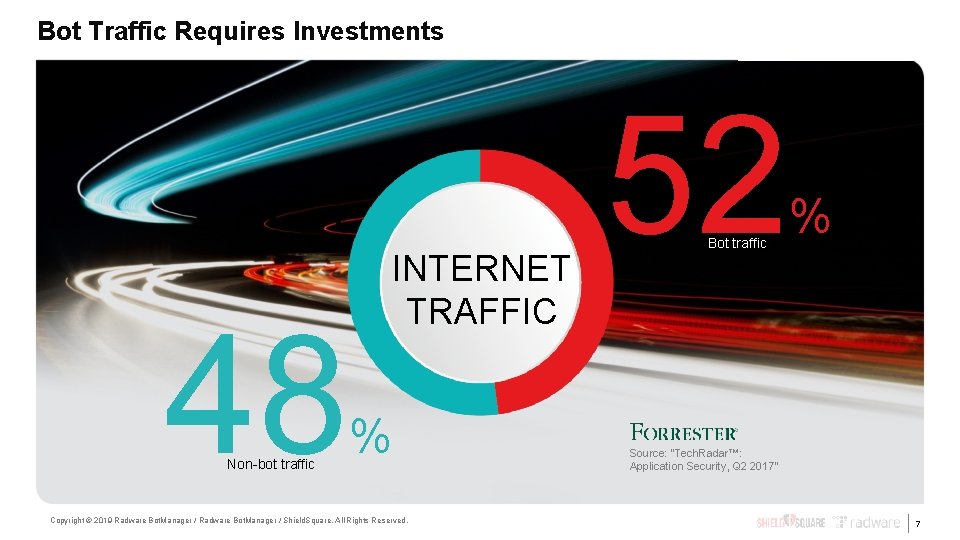
Bot Traffic Requires Investments 48 Non-bot traffic INTERNET TRAFFIC % Copyright © 2019 Radware Bot. Manager / Shield. Square. All Rights Reserved. 52 Bot traffic % Source: “Tech. Radar™: Application Security, Q 2 2017” 7

Agenda • DDo. S Security Trends • Anti-DDo. S Solution Pillars • Reference Architecture 8 www. radware. com

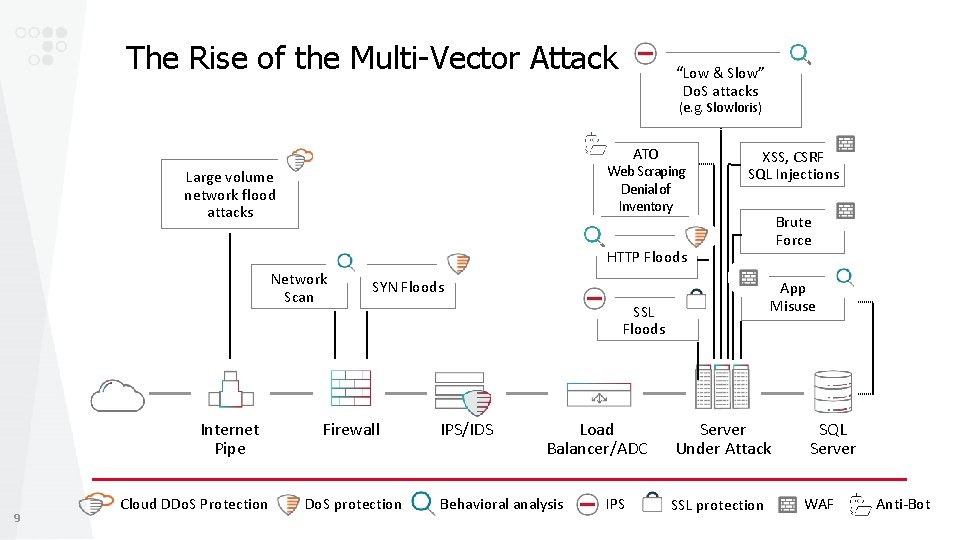
The Rise of the Multi-Vector Attack “Low & Slow” Do. S attacks (e. g. Slowloris) ATO Web Scraping Denial of Inventory Large volume network flood attacks XSS, CSRF SQL Injections Brute Force HTTP Floods Network Scan Internet Pipe 9 Cloud DDo. S Protection SYN Floods Firewall Do. S protection App Misuse SSL Floods IPS/IDS Load Balancer/ADC Behavioral analysis IPS Server Under Attack SSL protection SQL Server WAF Anti-Bot

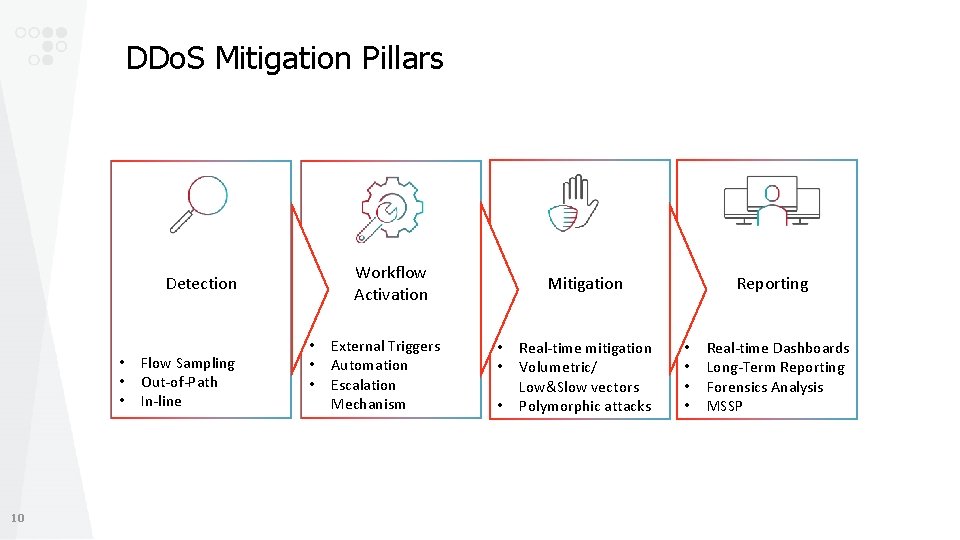
DDo. S Mitigation Pillars Workflow Activation Detection • • • 10 Flow Sampling Out-of-Path In-line • • • External Triggers Automation Escalation Mechanism Mitigation • • • Real-time mitigation Volumetric/ Low&Slow vectors Polymorphic attacks Reporting • • Real-time Dashboards Long-Term Reporting Forensics Analysis MSSP

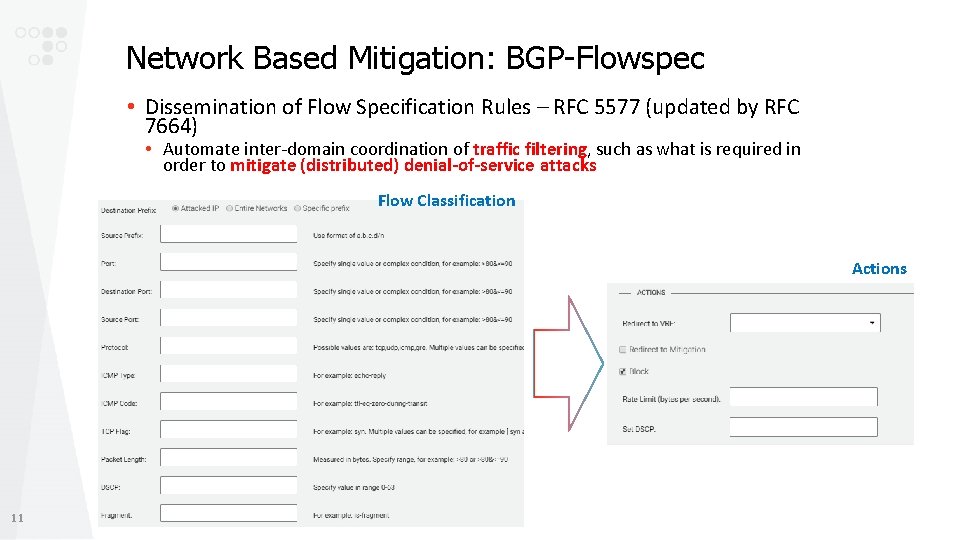
Network Based Mitigation: BGP-Flowspec • Dissemination of Flow Specification Rules – RFC 5577 (updated by RFC 7664) • Automate inter-domain coordination of traffic filtering, such as what is required in order to mitigate (distributed) denial-of-service attacks Flow Classification Actions 11

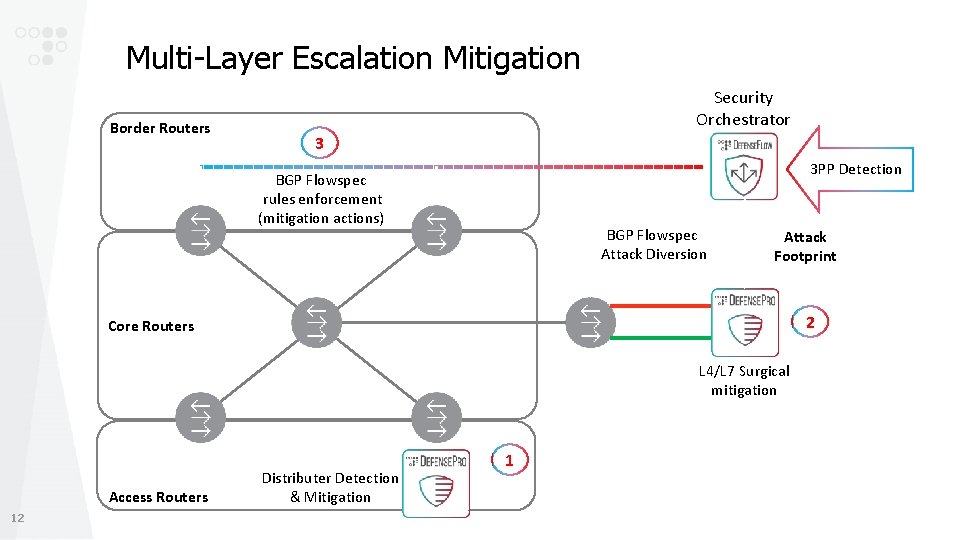
Multi-Layer Escalation Mitigation Border Routers Security Orchestrator 3 3 PP Detection BGP Flowspec rules enforcement (mitigation actions) BGP Flowspec Attack Diversion Attack Footprint 2 Core Routers L 4/L 7 Surgical mitigation Access Routers 12 Distributer Detection & Mitigation 1

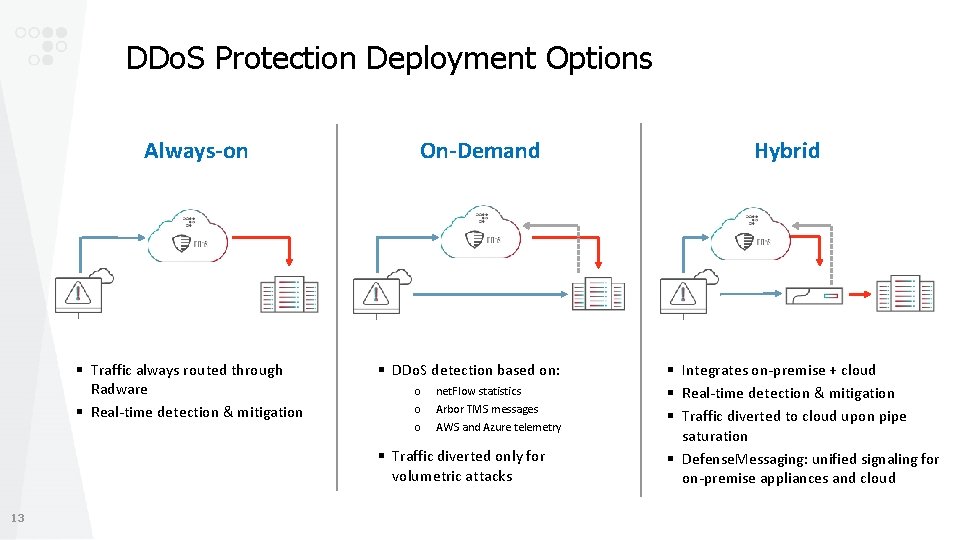
DDo. S Protection Deployment Options Always-on § Traffic always routed through Radware § Real-time detection & mitigation On-Demand § DDo. S detection based on: o o o net. Flow statistics Arbor TMS messages AWS and Azure telemetry § Traffic diverted only for volumetric attacks 13 Hybrid § Integrates on-premise + cloud § Real-time detection & mitigation § Traffic diverted to cloud upon pipe saturation § Defense. Messaging: unified signaling for on-premise appliances and cloud

Agenda • DDo. S Security Trends • Anti-DDo. S Solution Pillars • Reference Architecture 14 www. radware. com

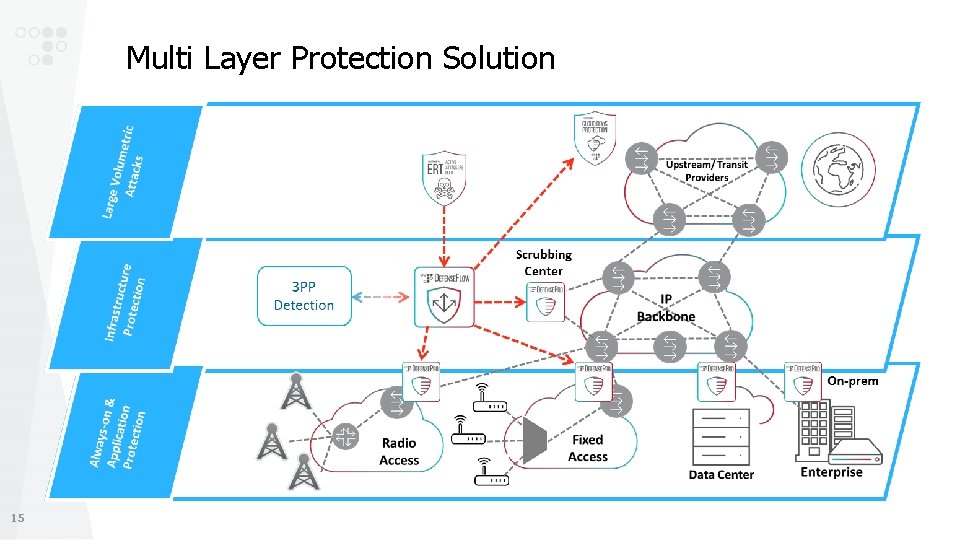
Multi Layer Protection Solution 15

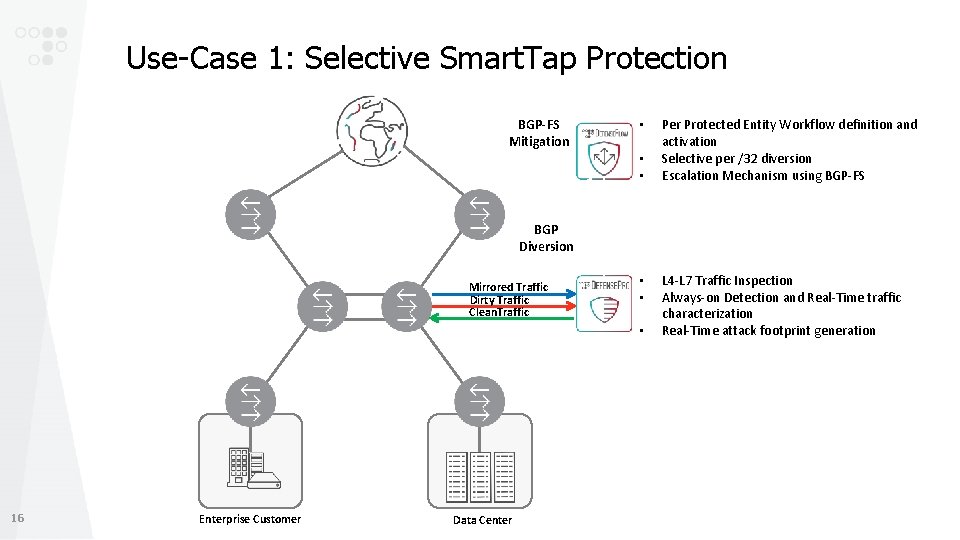
Use-Case 1: Selective Smart. Tap Protection BGP-FS Mitigation • • • Per Protected Entity Workflow definition and activation Selective per /32 diversion Escalation Mechanism using BGP-FS BGP Diversion Mirrored Traffic Dirty Traffic Clean. Traffic • • • 16 Enterprise Customer Data Center L 4 -L 7 Traffic Inspection Always-on Detection and Real-Time traffic characterization Real-Time attack footprint generation

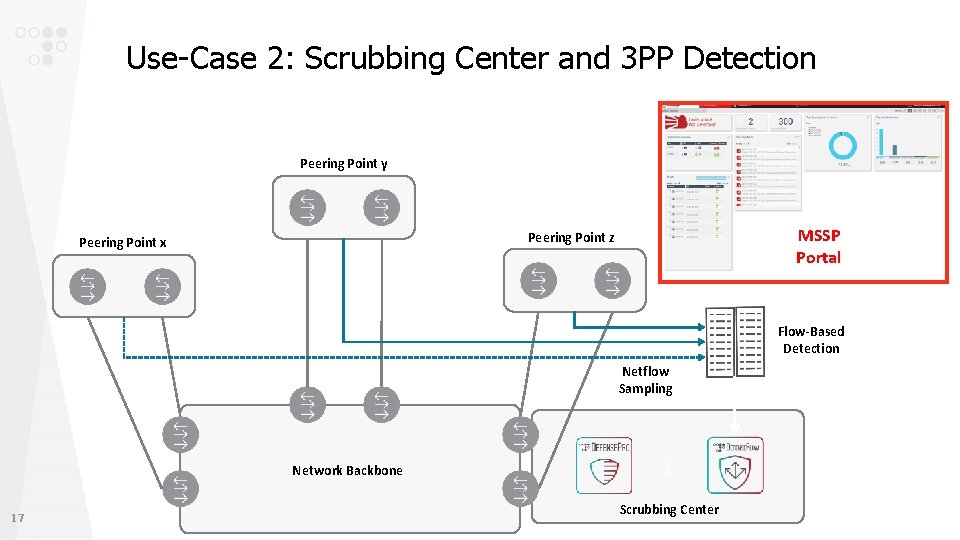
Use-Case 2: Scrubbing Center and 3 PP Detection Peering Point y MSSP Portal Peering Point z Peering Point x Flow-Based Detection Netflow Sampling Network Backbone 17 1 Scrubbing Center

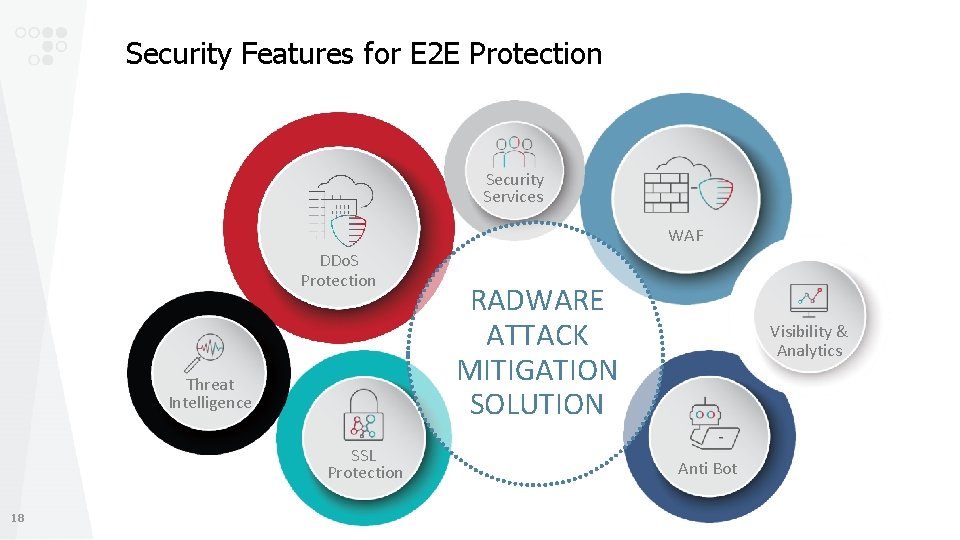
Security Features for E 2 E Protection Security Services WAF DDo. S Protection Threat Intelligence SSL Protection 18 RADWARE ATTACK MITIGATION SOLUTION Visibility & Analytics Anti Bot

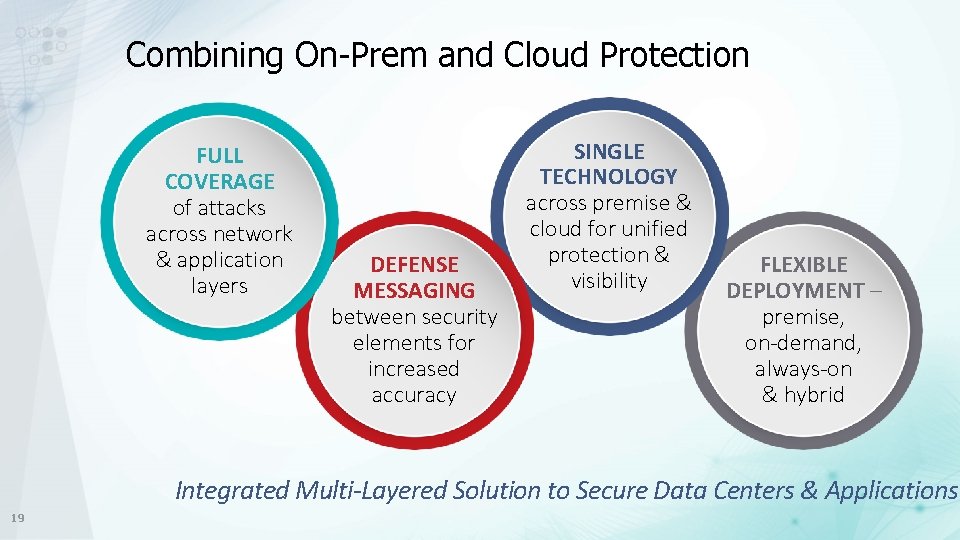
Combining On-Prem and Cloud Protection FULL COVERAGE of attacks across network & application layers DEFENSE MESSAGING between security elements for increased accuracy SINGLE TECHNOLOGY across premise & cloud for unified protection & visibility FLEXIBLE DEPLOYMENT – premise, on-demand, always-on & hybrid Integrated Multi-Layered Solution to Secure Data Centers & Applications 19

Thank You