A Taxonomy of DDo S Attack and DDo
















- Slides: 29

A Taxonomy of DDo. S Attack and DDo. S Defense Mechanisms¤ Jelena Mirkovic Computer and Information Sciences Department University of Delaware Peter Reiher 3564 Boelter Hall Computer Science Department UCLA CS 495 – Spring 2005 Northwestern University Sausan Yazji 9/14/2021 1

Overview n Distributed denial-of-service (DDo. S) is a rapidly growing problem n Variety approaches for the attacks and the defense Mechanisms n Two taxonomies for classifying attacks and defenses: n n 9/14/2021 Highlight commonalities and important features of attack strategies Classify the body of existing DDo. S defenses based on their design decisions 2

Background n The DDo. S attack mechanisms are changing consistently n The Security measures to deal with the attacks are changing consistently n Setting apart and emphasizing crucial features of attack and defense mechanisms n Abstracting detailed differences between the attacks and defense mechanism 9/14/2021 3

Why? n What are the different ways of perpetrating a DDo. S n n n n attack? Why is DDo. S a difficult problem to handle? What attacks have been handled effectively by existing defense systems? What attacks still remain undressed and why? How would the defense mechanism behave in case of unrelated attack? What are the defense mechanism vulnerabilities? Can the defense mechanism complement each other and how? How can we contribute to the DDo. S field? 9/14/2021 4

Proposed Taxonomy n Covers known attacks and also realistic potential threat n Covers published and commercial approaches n The proposed taxonomy is not: n n n 9/14/2021 as detailed as possible dividing attacks and defenses in an exclusive manner The depth and width of the proposed taxonomies are not suitable for a traditional numbering of headings proposing or advocating any specific DDo. S defense mechanism 5

DDOS ATTACK OVERVIEW n Do. S is an explicit attempt to prevent the legitimate use of a service n DDo. S deploys multiple attacks to attain this goal 9/14/2021 6

What makes DDo. S attacks possible? n Internet security is highly interdependent n Internet resources are limited n Intelligence and resources are not collocated n Accountability is not enforced n Control is distributed 9/14/2021 7

How are DDo. S attacks performed? n Recruit multiple agent machines n Exploit the vulnerable recruited machines n Infect the exploited machines with the attack code n Use the infected machines to recruit new agents n Distribute the attack code using useful applications n Hide the identity of agent machines through spoofing 9/14/2021 8

Why do people perpetrate DDo. S attacks? n Personal reasons n Prestige n Material gain n Political reasons 9/14/2021 9

Taxonomy of DDo. S Attack Mechanisms 9/14/2021 10

DA: Degree of Automation n DA 1: Manual n DA 2: CM 2: Indirect Communication n DA 3: Automatic n DA 2 and DA 3: HSS: Host Scanning and Vulnerability Scanning Strategy n n n 9/14/2021 DA 2 and DA 3: HSS 1: Random Scanning DA 2 and DA 3: HSS 2: Hit list Scanning DA 2 and DA 3: HSS 3: Signpost Scanning DA 2 and DA 3: HSS 5: Local Subnet Scanning 11

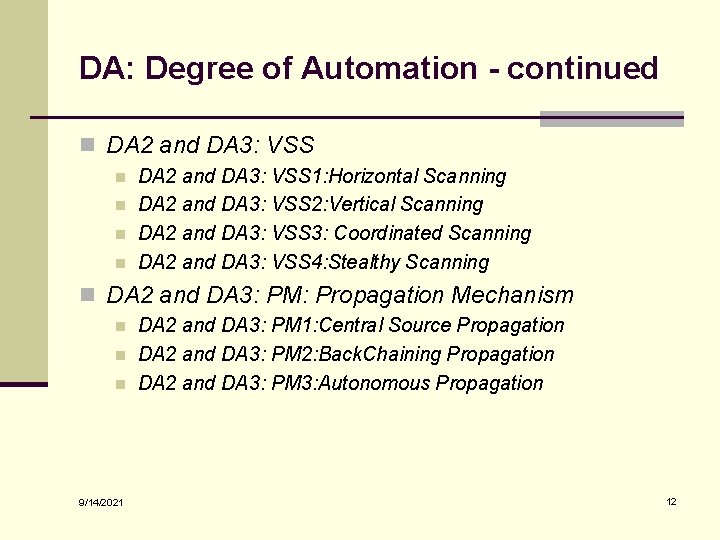
DA: Degree of Automation - continued n DA 2 and DA 3: VSS n n DA 2 and DA 3: VSS 1: Horizontal Scanning DA 2 and DA 3: VSS 2: Vertical Scanning DA 2 and DA 3: VSS 3: Coordinated Scanning DA 2 and DA 3: VSS 4: Stealthy Scanning n DA 2 and DA 3: PM: Propagation Mechanism n n n 9/14/2021 DA 2 and DA 3: PM 1: Central Source Propagation DA 2 and DA 3: PM 2: Back. Chaining Propagation DA 2 and DA 3: PM 3: Autonomous Propagation 12

EW: Exploited. Weakness to Deny Service n EW 1: Semantic n EW 2: Brute. Force 9/14/2021 13

SAV: Source Address Validity n SAV 1: Spoofed Source Address n SAV 1: AR: Address Routability n SAV 1: AR 1: Routable Source Address n SAV 1: AR 2: Non. Routable Source Address n SAV 1: ST: Spoofing Technique n n SAV 1: ST 1: Random Spoofed Source Address SAV 1: ST 2: Subnet Spoofed Source Address SAV 1: ST 3: En Route Spoofed Source Address SAV 1: ST 4: Fixed Spoofed Source Address n SAV 2: Valid Source Address 9/14/2021 14

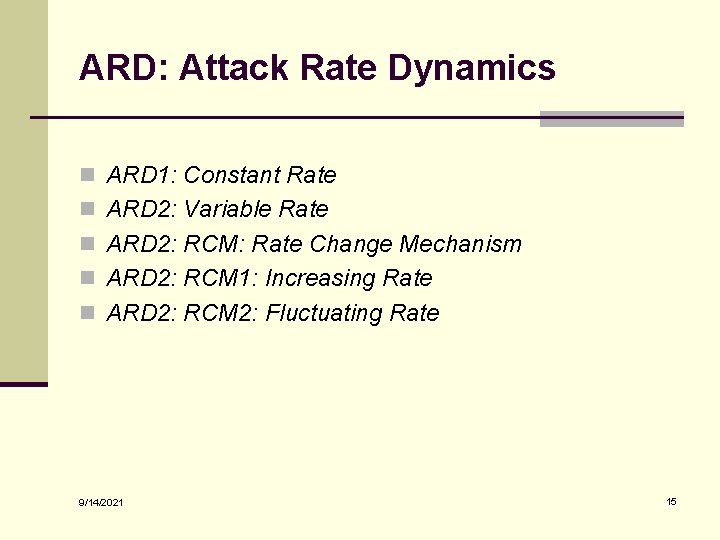
ARD: Attack Rate Dynamics n ARD 1: Constant Rate n ARD 2: Variable Rate n ARD 2: RCM: Rate Change Mechanism n ARD 2: RCM 1: Increasing Rate n ARD 2: RCM 2: Fluctuating Rate 9/14/2021 15

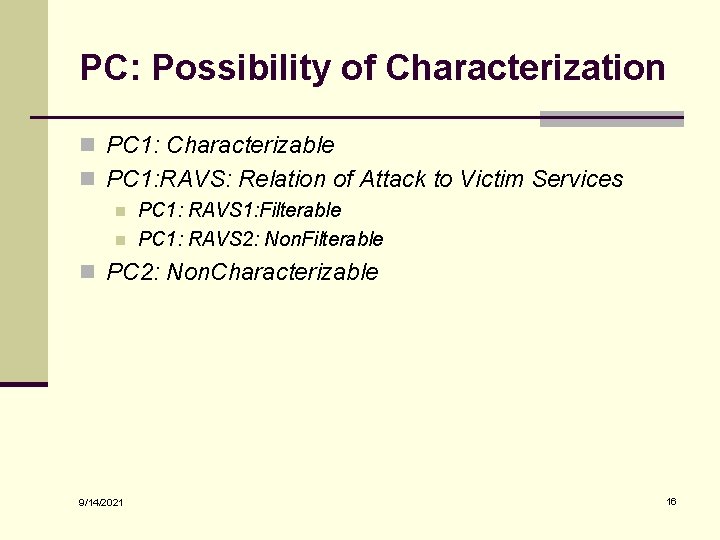
PC: Possibility of Characterization n PC 1: Characterizable n PC 1: RAVS: Relation of Attack to Victim Services n n PC 1: RAVS 1: Filterable PC 1: RAVS 2: Non. Filterable n PC 2: Non. Characterizable 9/14/2021 16

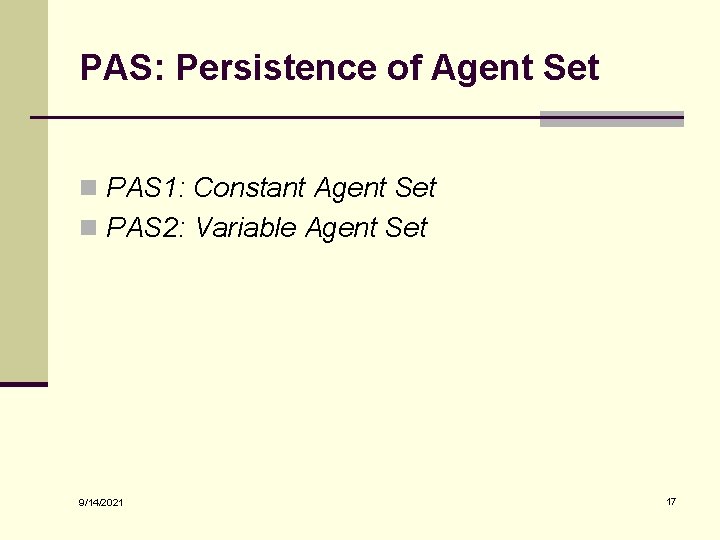
PAS: Persistence of Agent Set n PAS 1: Constant Agent Set n PAS 2: Variable Agent Set 9/14/2021 17

VT: Victim Type n VT 1: Application n VT 2: Host n VT 3: Resource Attacks n VT 4: Network Attacks n VT 5: Infrastructure 9/14/2021 18

IV: Impact on the Victim n IV 1: Disruptive n IV 1: PDR: Possibility of Dynamic Recovery n n n IV 1: PDR 1: Self Recoverable IV 1: PDR 2: Human Recoverable IV 1: PDR 3: Non Recoverable n IV 2: Degrading 9/14/2021 19

DDOS DEFENSE CHALLENGE No real complete solution is proposed for the DDo. S yet: n n n 9/14/2021 Need for a distributed response at many points on the Internet Economic and social factors Lack of detailed attack information Lack of defense system benchmarks Difficulty of large-scale testing 20

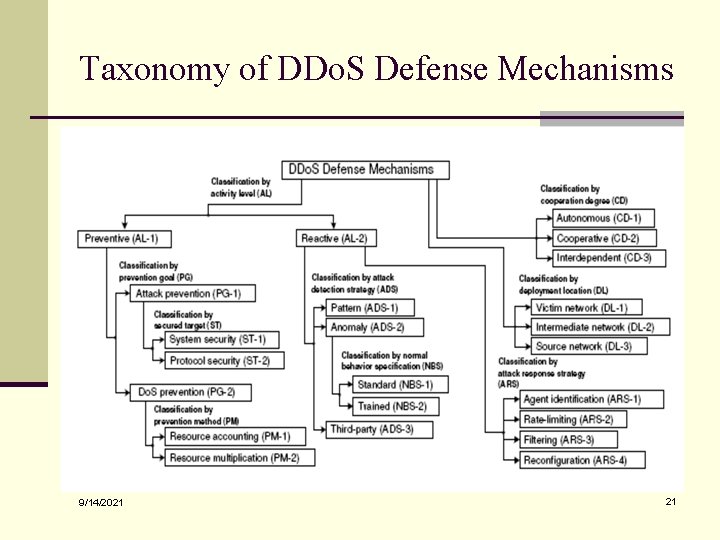
Taxonomy of DDo. S Defense Mechanisms 9/14/2021 21

AL: Activity Level n AL 1: Preventive n AL 1: PG: Prevention Goal n n AL 1: PG 1: Attack Prevention AL 1: PG 1: ST: Secured Target § AL 1: PG 1: ST 1: System Security § AL 1: PG 1: ST 2: Protocol Security n AL 1: PG 2: Do. S Prevention n AL 1: PG 2: PM: Prevention Method § AL 1: PG 2: PM 1: Resource Accounting § AL 1: PG 2: PM 2: Resource Multiplication 9/14/2021 22

AL: Activity Level - Continued n AL 2: Reactive n AL 2: ADS: Attack Detection Strategy n n n 9/14/2021 AL 2: ADS 1: Pattern Detection AL 2: ADS 2: Anomaly Detection AL 2: ADS 2: NBS: Normal Behavior Specification § AL 2: ADS 2: NBS 1: Standard § AL 2: ADS 2: NBS 2: Trained AL 2: ADS 3: Third Party Detection AL 2: ARS: Attack Response Strategy n AL 2: ARS 1: Agent Identification n AL 2: ARS 2: Rate Limiting n AL 2: ARS 3: Filtering n AL 2: ARS 4: Reconfiguration 23

CD: Cooperation Degree n CD 1: Autonomous n Firewalls n Intrusion Detection Systems n CD 2: Cooperative n n Can operate autonomously at a single deployment point Aggregate Congestion Control (ACC) System n CD 3: Interdependent n n n 9/14/2021 Cannot operate autonomously at a single deployment point Trace Back Mechanism Secure Overlay Services 24

DL: Deployment Location n DL 1: Victim Network n n Protect this network from DDo. S attacks Respond to attacks by alleviating the impact on the victim n DL 2: Intermediate Network n n Provide defense service to a large number of Internet hosts Push-back and trace-back techniques n DL 3: Source Network n n 9/14/2021 Prevent network customers from generating DDo. S attacks Low motivation 25

USING THE TAXONOMIES n A map of DDo. S research field n Exploring new attack strategies n DDo. S benchmark generation n Common vocabulary n Design of attack class-specific solutions n Understanding solution constrains n Identifying unexplored research areas 9/14/2021 26

RELATEDWORK n Classification of Do. S attacks according to: n n Target Type Consumed Resource Exploited Vulnerability Number of Agent Machines n Focusing on computer attacks in general n Discussion of the DDo. S problem and of some defense approaches n Classification of the DDo. S defense field only, Intrusion Detection n New studies: n n 9/14/2021 focus on taxonomy of computer incidents Generation of a DDo. S attack overview 27

CONCLUSION n Help the community think about the threats we face n n n and the possible countermeasures Foster easier cooperation among researchers Facilitate communication and offer common language for discussing solutions Clarify how different mechanisms are likely to work in concert Identify areas of remaining weaknesses that require additional work Help developing common metrics and benchmarks for DDo. S defense evaluation Offer a foundation for classifying threats and defenses in DDo. S field 9/14/2021 28

A Taxonomy of DDo. S Attack and DDo. S Defense Mechanisms QUESTIONS? 9/14/2021 29
 Active attack and passive attack
Active attack and passive attack Passive attack and active attack
Passive attack and active attack Kendall and marzano taxonomy
Kendall and marzano taxonomy Ddo auto attack
Ddo auto attack Drawing and disbursing officer
Drawing and disbursing officer Ddo church and the cult
Ddo church and the cult Duties of drawing and disbursing officer
Duties of drawing and disbursing officer Gated wye friction loss
Gated wye friction loss The amorphous body of the amoeba has no discernable
The amorphous body of the amoeba has no discernable Automated generation and analysis of attack graphs
Automated generation and analysis of attack graphs Dumbking plant
Dumbking plant Unit 15 plant structures and taxonomy
Unit 15 plant structures and taxonomy What is the taxonomy of a domestic dog
What is the taxonomy of a domestic dog Cell structure and taxonomy
Cell structure and taxonomy Taxonomy and taxidermy
Taxonomy and taxidermy Dichotomous key for fungi
Dichotomous key for fungi Sunflower classification
Sunflower classification Dichotomous key for cars
Dichotomous key for cars Metadata and taxonomy
Metadata and taxonomy Metadata and taxonomy
Metadata and taxonomy Bubonic plague
Bubonic plague Metadata and taxonomy
Metadata and taxonomy Ddo sapphire of defense
Ddo sapphire of defense Ddo simulator.
Ddo simulator. Ddo housekeeping
Ddo housekeeping Detour ddo
Detour ddo Ddo template guidelines
Ddo template guidelines Ddo template version 4
Ddo template version 4 Sos ddo
Sos ddo Ddo s
Ddo s