MIS 5202 Welcome to IT Governance MIS 5202






















- Slides: 34

MIS 5202 Welcome to IT Governance

MIS 5202 IT Governance • • • Welcome to the course A look at the syllabus A look at the semester schedule Dive into the Stars Ambulance case Review the definition of IT Governance Review COBIT 5

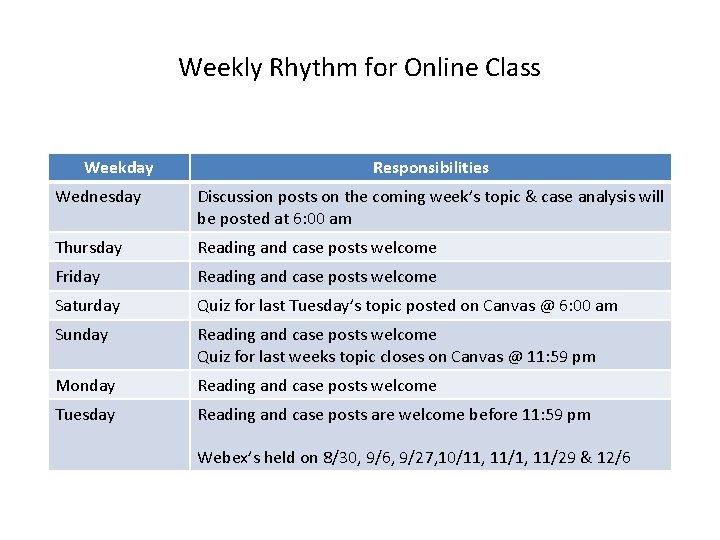
Weekly Rhythm for Online Class Weekday Responsibilities Wednesday Discussion posts on the coming week’s topic & case analysis will be posted at 6: 00 am Thursday Reading and case posts welcome Friday Reading and case posts welcome Saturday Quiz for last Tuesday’s topic posted on Canvas @ 6: 00 am Sunday Reading and case posts welcome Quiz for last weeks topic closes on Canvas @ 11: 59 pm Monday Reading and case posts welcome Tuesday Reading and case posts are welcome before 11: 59 pm Webex’s held on 8/30, 9/6, 9/27, 10/11, 11/29 & 12/6


What is IT Governance?

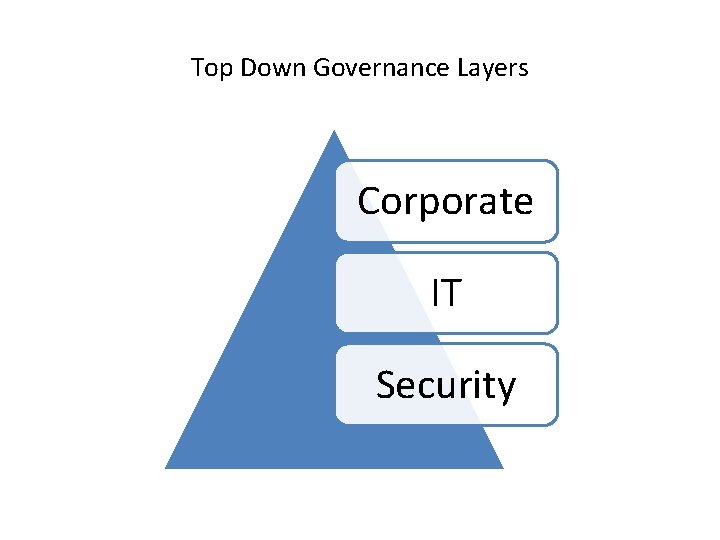
Top Down Governance Layers Corporate IT Security

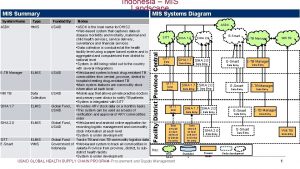
IT Security exists where Governance, Risk and Compliance overlap

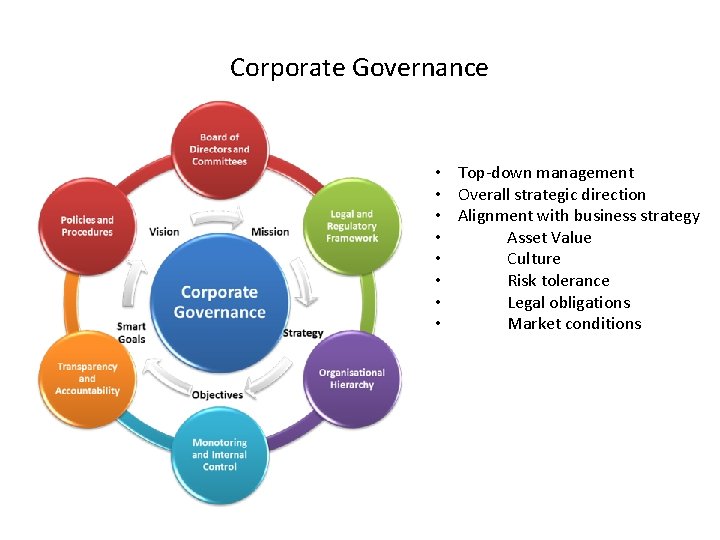
Corporate Governance • Top-down management • Overall strategic direction • Alignment with business strategy • Asset Value • Culture • Risk tolerance • Legal obligations • Market conditions

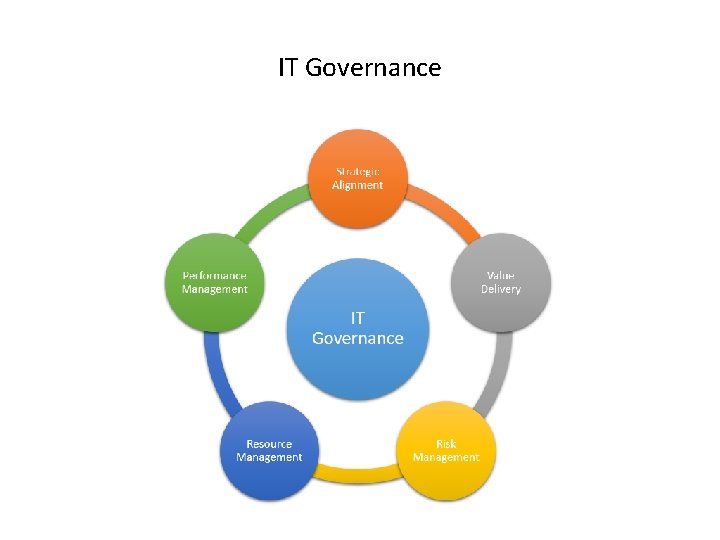
IT Governance

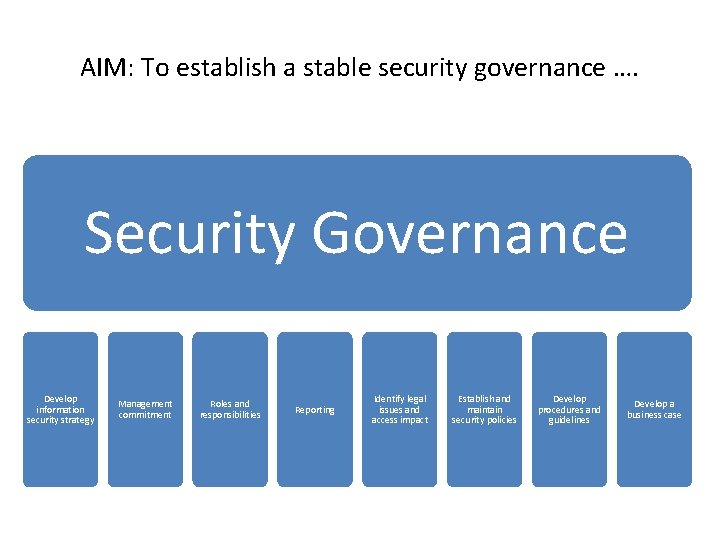
AIM: To establish a stable security governance …. Security Governance Develop information security strategy Management commitment Roles and responsibilities Reporting Identify legal issues and access impact Establish and maintain security policies Develop procedures and guidelines Develop a business case

How do you “see” Governance? • Strategic – Board Level – CIO – CISO • Operations – System Admins – Subject Matter Experts • Holistic vs targeted


What is the concept of governance? • Governance has been defined to refer to structures and processes that are designed to ensure accountability, transparency, responsiveness, rule of law, stability, equity and inclusiveness, empowerment, and broadbased participation.

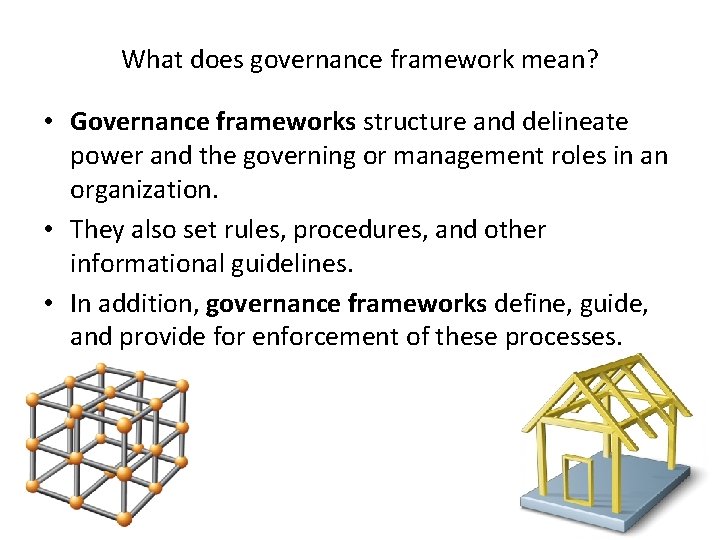
What does governance framework mean? • Governance frameworks structure and delineate power and the governing or management roles in an organization. • They also set rules, procedures, and other informational guidelines. • In addition, governance frameworks define, guide, and provide for enforcement of these processes.

Good IT Governance = Right Things, Done Right

What is IT Governance? • Its about doing the right thing… – Who gets to decide? – Are we working on things that will produce the most value to the organization? – Are we protecting the organization? • and then, doing them right. – Do we conform to all laws and regulations? – Do we use our resources well? – Are we meeting our service objectives?



The Star Air Ambulance Case CASE STUDY

The Star Air Ambulance Case • Read the case • As groups discuss the answers to these questions: – Identify three or four of the most critical challenges facing the new CIO? – What is the overall issue facing the new CIO? – What questions would you, as CIO, want senior management to answer?

COBIT 5 FRAMEWORK

• COBIT 5 provides the next generation of ISACA’s guidance on the enterprise governance and management of IT. • Builds on more than 15 years of practical usage • Evolved from an auditing framework to controls • Now to a governance for enterprise IT (GEIT) framework, showing a management strategy for enterprise IT.

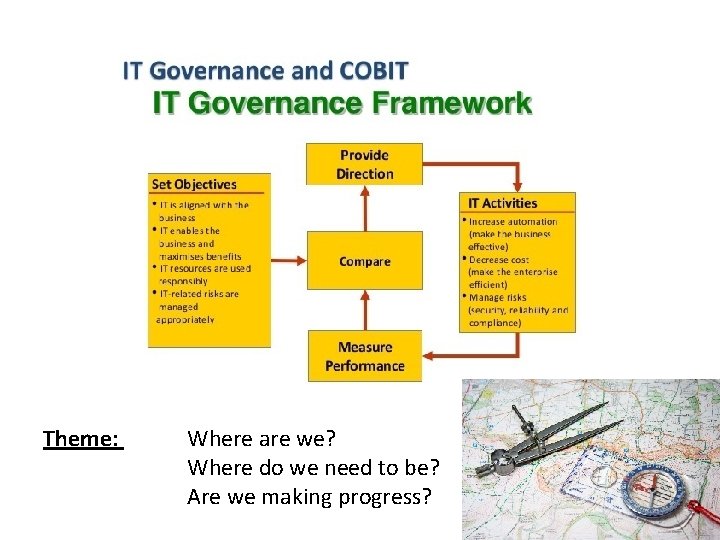
Theme: Where are we? Where do we need to be? Are we making progress?

Business Framework for Governance of Enterprise IT

What is COBIT 5? • • Its about best practice framework It tries to cover IT end-to-end What you need to be thinking about when running (or auditing) IT Its not about the technology, – its about the processes used to deliver technology • Its about how to decide what you do • (Right Things) – then how to do them in an efficient, effective and secure manner • (Done Right) • It is critical that you understand the processes it recommends

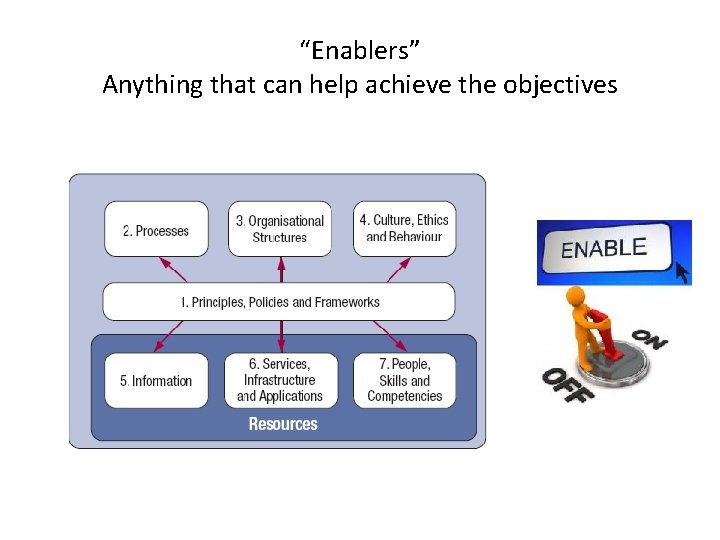
“Enablers” Anything that can help achieve the objectives

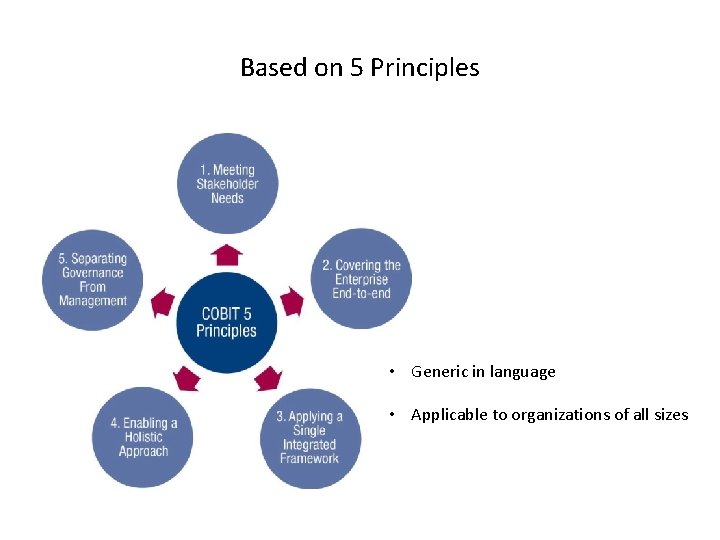
Based on 5 Principles • Generic in language • Applicable to organizations of all sizes

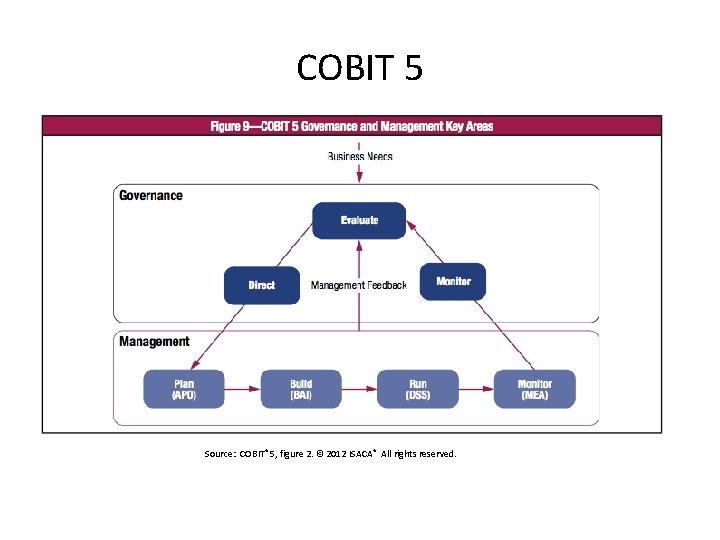
COBIT 5 Source: COBIT® 5, figure 2. © 2012 ISACA ® All rights reserved.

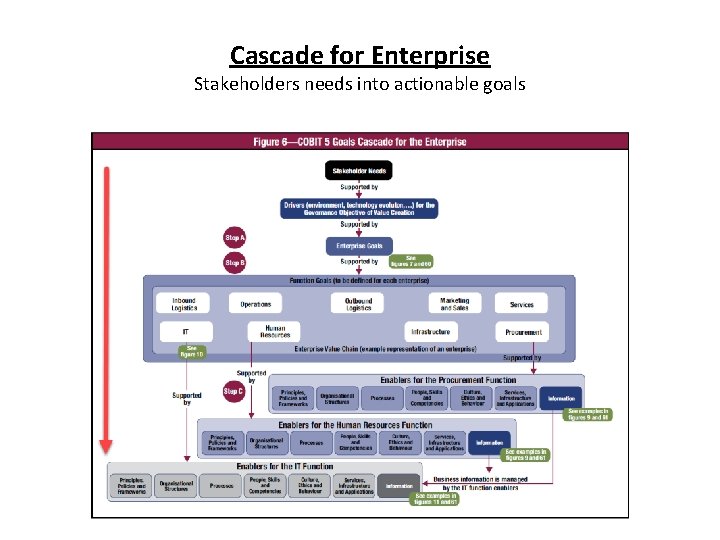
Cascade for Enterprise Stakeholders needs into actionable goals



Two Security Specific COBIT topics • Align, Plan, Organize APO 13: Manage Security – Define, operate and monitor systems for IT Management – Five goals • • • Support IT & Business Support Management of IT and enterprise risk Transparency of IT costs and benefits Ensure security of information infrastructure Reliable information for decision making

DSS 05: Operational Processes – Protect Enterprise Information – Maintain acceptable level of risk – Establish and maintain roles and access – Security monitoring

7 Control Objectives 1. 2. 3. 4. 5. 6. 7. Protect against malware Manage network connectivity and security Manage endpoint security Manage user ID and access Control physical access to IT Manage sensitive documents Monitor infrastructure for security events
 Welcome welcome this is our christmas story
Welcome welcome this is our christmas story Mis realidades mis valores proyecto de vida
Mis realidades mis valores proyecto de vida Cuales son mis creencias
Cuales son mis creencias La sobrina de mi padre es
La sobrina de mi padre es Mis mai a mis tachwedd
Mis mai a mis tachwedd Mis mai a mis tachwedd
Mis mai a mis tachwedd Good governance of medicine
Good governance of medicine Data governance council maturity model
Data governance council maturity model Marketability in good governance
Marketability in good governance Hpe information management and governance
Hpe information management and governance Difference between e governance and e government
Difference between e governance and e government E-governance
E-governance The purpose of corporate governance
The purpose of corporate governance Participatory governance
Participatory governance Public sector governance models
Public sector governance models Governance leadership and management
Governance leadership and management Microsoft grc
Microsoft grc Basel committee corporate governance
Basel committee corporate governance Acnc governance standard 5
Acnc governance standard 5 Polycentric governance
Polycentric governance Malaysia patient safety goals
Malaysia patient safety goals Meaning of corporate governance
Meaning of corporate governance Chapter 10 corporate governance
Chapter 10 corporate governance Demystifying healthcare data governance
Demystifying healthcare data governance Cadbury report ppt
Cadbury report ppt Backround
Backround Materi kuliah it governance
Materi kuliah it governance University governance models
University governance models Corporate governance in sri lanka
Corporate governance in sri lanka Self service bi governance
Self service bi governance Pdpc ai governance
Pdpc ai governance Kebijakan publik dan good governance
Kebijakan publik dan good governance Corporate governance definitie
Corporate governance definitie Incident-driven policing definition
Incident-driven policing definition Mdm project deliverables
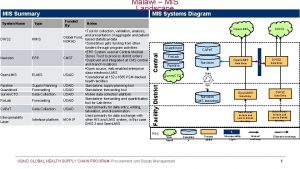
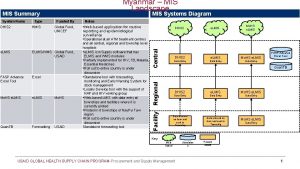
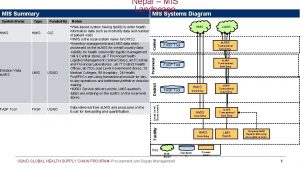
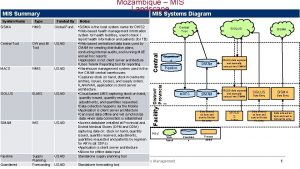
Mdm project deliverables