MGT 309 Microsoft System Center Operations Manager 2007





















- Slides: 45


MGT 309 Microsoft System Center Operations Manager 2007 R 2: Driving Compliance with ACS Maarten Goet System Center Operations Manager MVP MGT 309

Presenter Introduction Maarten Goet System Center Operations Manager MVP Since 2007 Managing consultant at INOVATIV The Netherlands Lead on several large-scale ACS deployments International accountancy firm Blogs: http: //blogs. inovativ. nl & http: //www. techlog. org http: //www. systemcentercentral. com Contact Email: maarten. goet@inovativ. nl

Agenda What is compliancy? Audit Collection Services (ACS) Extending the functionality Non-Windows security monitoring Database model and reports ACS and WMI Tips and tricks from the field Lots of DEMO’s !

What is compliancy ? “Conforming to a specification or policy, standard or law that has been clearly defined” Prove instead of trust Government policies (HIPAA, SOX) versus internal policies Compliance: centrally collect, monitor, archive and report security events Auditing: maintain audit trail of internal security related activities Scalable and Secure: infrastructure must guarantee collection and integrity of huge volumes of security events

Infrastructure Optimization Security Mgmt Security Auditing Security Compliance

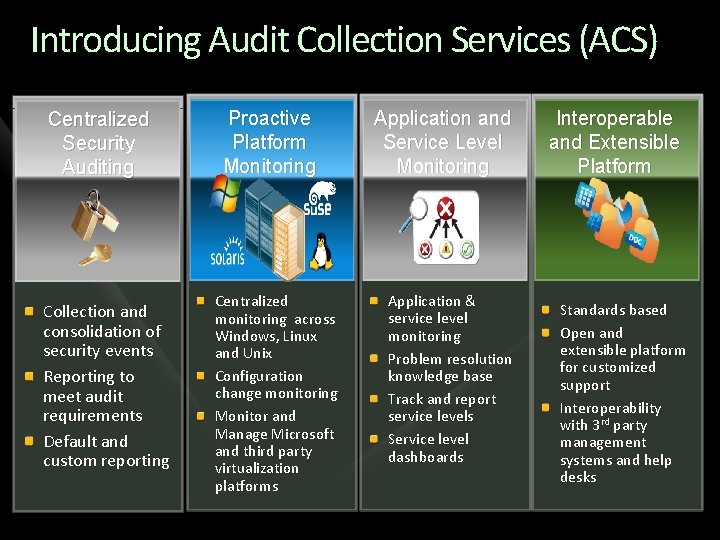
Introducing Audit Collection Services (ACS) Centralized Security Auditing Collection and consolidation of security events Reporting to meet audit requirements Default and custom reporting Proactive Platform Monitoring Centralized monitoring across Windows, Linux and Unix Configuration change monitoring Monitor and Manage Microsoft and third party virtualization platforms Application and Service Level Monitoring Application & service level monitoring Problem resolution knowledge base Track and report service levels Service level dashboards Interoperable and Extensible Platform Standards based Open and extensible platform for customized support Interoperability with 3 rd party management systems and help desks

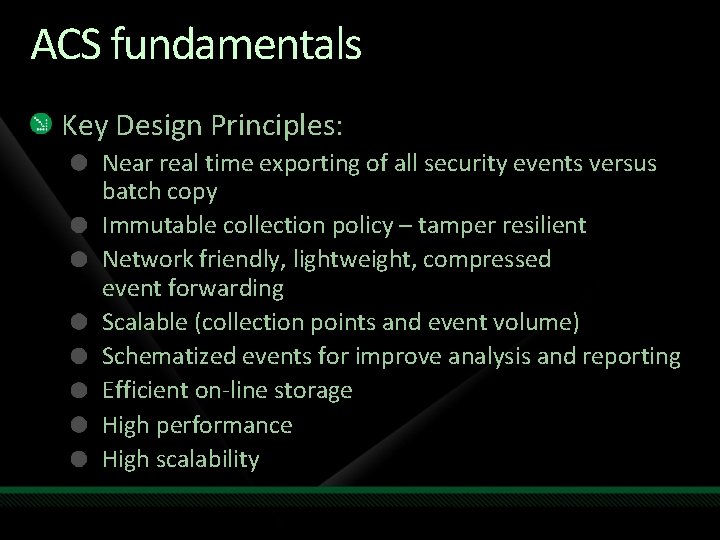
ACS fundamentals Key Design Principles: Near real time exporting of all security events versus batch copy Immutable collection policy – tamper resilient Network friendly, lightweight, compressed event forwarding Scalable (collection points and event volume) Schematized events for improve analysis and reporting Efficient on-line storage High performance High scalability

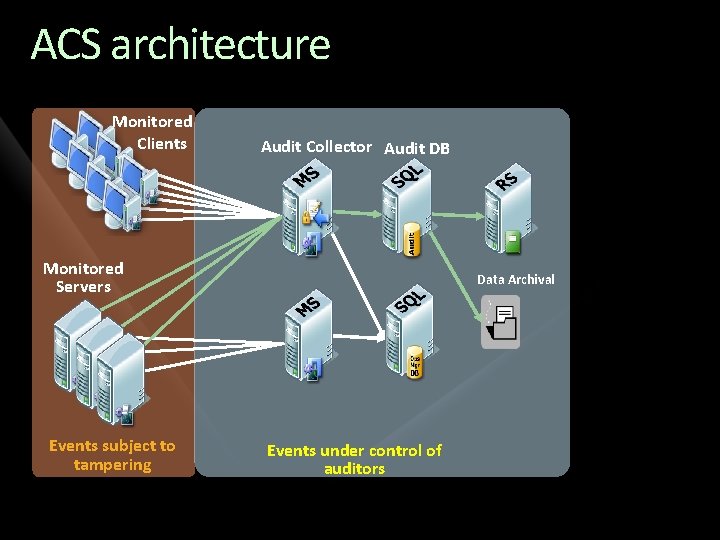
ACS architecture Monitored Clients Audit Collector Audit DB Monitored Servers Events subject to tampering Data Archival Events under control of auditors

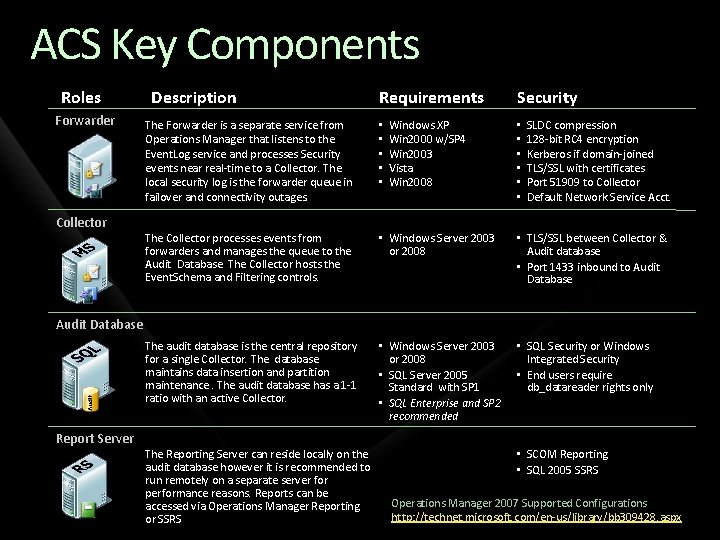
ACS Key Components Roles Forwarder Collector Description Requirements Windows XP Win 2000 w/SP 4 Win 2003 Vista Win 2008 Security The Forwarder is a separate service from Operations Manager that listens to the Event. Log service and processes Security events near real-time to a Collector. The local security log is the forwarder queue in failover and connectivity outages. • • • The Collector processes events from forwarders and manages the queue to the Audit Database. The Collector hosts the Event. Schema and Filtering controls. • Windows Server 2003 or 2008 • TLS/SSL between Collector & Audit database • Port 1433 inbound to Audit Database The audit database is the central repository for a single Collector. The database maintains data insertion and partition maintenance. The audit database has a 1 -1 ratio with an active Collector. • Windows Server 2003 or 2008 • SQL Server 2005 Standard with SP 1 • SQL Enterprise and SP 2 recommended • SQL Security or Windows Integrated Security • End users require db_datareader rights only • • • SLDC compression 128 -bit RC 4 encryption Kerberos if domain-joined TLS/SSL with certificates Port 51909 to Collector Default Network Service Acct. Audit Database Report Server The Reporting Server can reside locally on the audit database however it is recommended to run remotely on a separate server for performance reasons. Reports can be accessed via Operations Manager Reporting or SSRS • SCOM Reporting • SQL 2005 SSRS Operations Manager 2007 Supported Configurations http: //technet. microsoft. com/en-us/library/bb 309428. aspx

Secure Communication All connections are mutually authenticated Kerberos if forwarder is domain-joined TLS/SSL if forwarder is configured with certificate All data is compressed and encrypted SLDC compression 128 -bit RC 4 encryption Ensure delivery of all audits Alert on Availability and Integrity Event 4631 Forwarder Disconnected Event 4335 Event Gap Stream Detected Event 4336 Forwarder Rejected Certificates 51909 (CAC 5) Kerberos

Security Management Responding to day-to-day threats Provided by Management Packs Monitors, rules, views. . Notifications. . Develop your own management pack elements by identifying key events or look at third party solutions Free management pack for key Windows Server auditing scenarios: STAMP

Security Auditing Reporting on historical facts Forensic analysis Provided by reports Microsoft provides reports out-ofthe-box Third party reports available Develop your own reports by identifying key events and using Visual Studio Report models for ACS available as of R 2 On the CD image

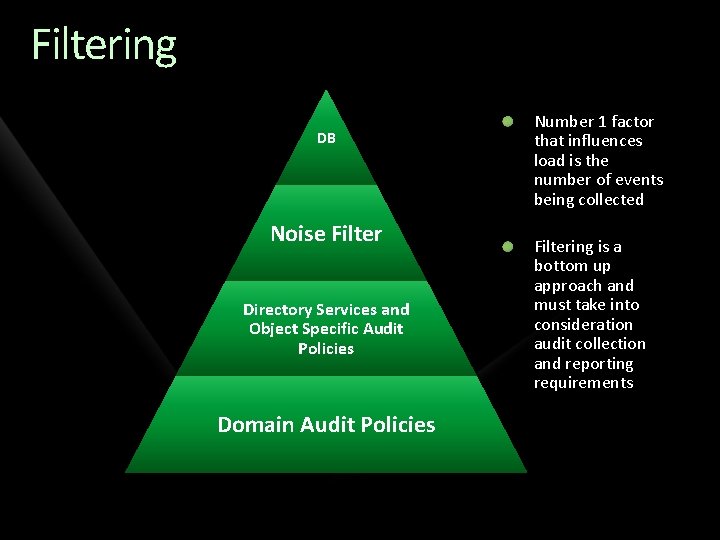
Filtering DB Noise Filter Directory Services and Object Specific Audit Policies Domain Audit Policies Number 1 factor that influences load is the number of events being collected Filtering is a bottom up approach and must take into consideration audit collection and reporting requirements

Audit Plan Developing a comprehensive audit policy is a multi-step process: Determine “what” should be audited Identify how the information is returned Implement Audit Policy and SACLs Windows Server 2003, 9 audit cat. Windows Server 2008, 50+ sub cat. Collection, triggers and analysis Start planning this in advance!

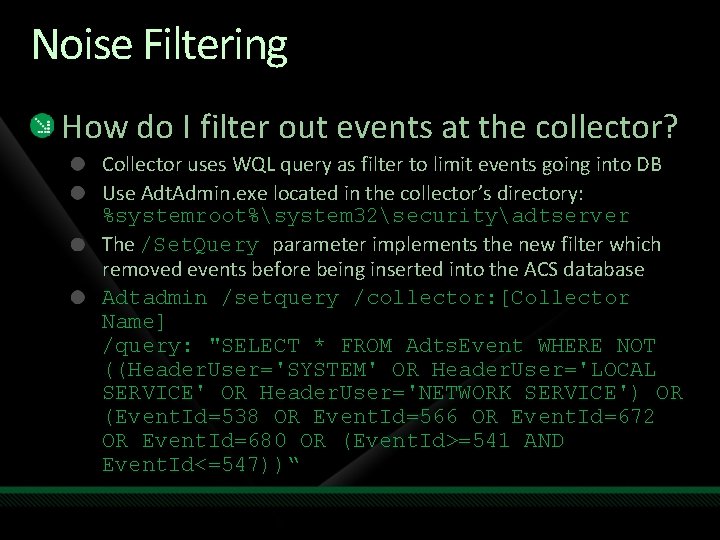
Noise Filtering How do I filter out events at the collector? Collector uses WQL query as filter to limit events going into DB Use Adt. Admin. exe located in the collector’s directory: %systemroot%system 32securityadtserver The /Set. Query parameter implements the new filter which removed events before being inserted into the ACS database Adtadmin /setquery /collector: [Collector Name] /query: "SELECT * FROM Adts. Event WHERE NOT ((Header. User='SYSTEM' OR Header. User='LOCAL SERVICE' OR Header. User='NETWORK SERVICE') OR (Event. Id=538 OR Event. Id=566 OR Event. Id=672 OR Event. Id=680 OR (Event. Id>=541 AND Event. Id<=547))“

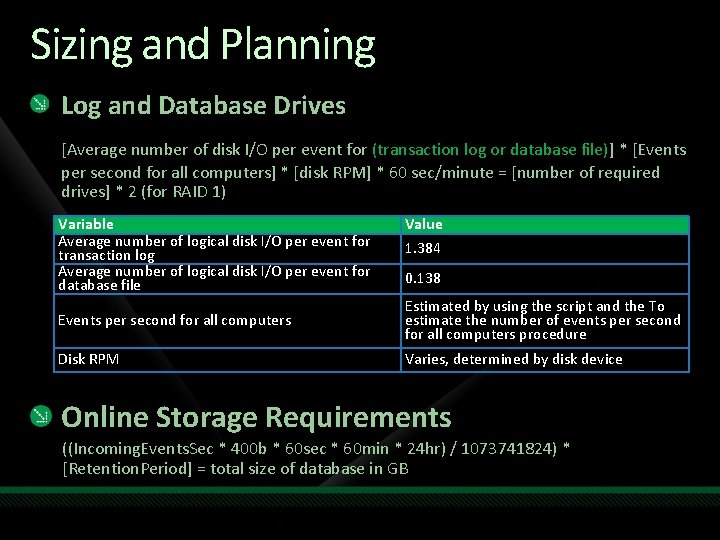
Sizing and Planning Log and Database Drives [Average number of disk I/O per event for (transaction log or database file)] * [Events per second for all computers] * [disk RPM] * 60 sec/minute = [number of required drives] * 2 (for RAID 1) Variable Average number of logical disk I/O per event for transaction log Average number of logical disk I/O per event for database file Value 1. 384 0. 138 Events per second for all computers Estimated by using the script and the To estimate the number of events per second for all computers procedure Disk RPM Varies, determined by disk device Online Storage Requirements ((Incoming. Events. Sec * 400 b * 60 sec * 60 min * 24 hr) / 1073741824) * [Retention. Period] = total size of database in GB

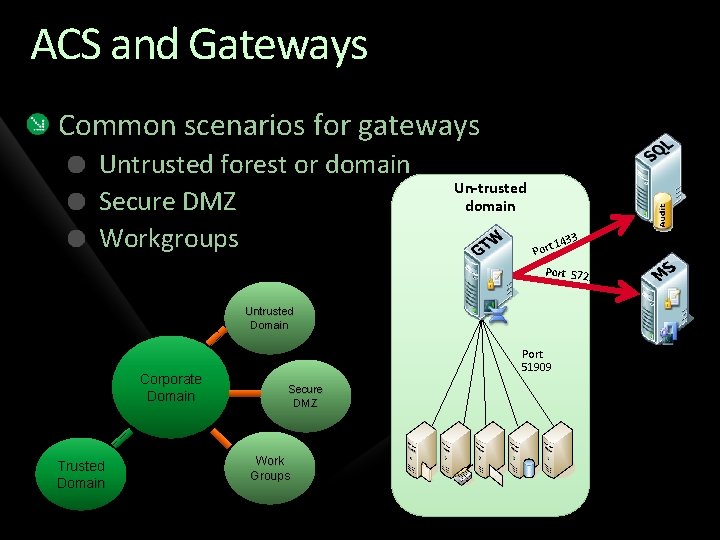
ACS and Gateways Common scenarios for gateways Untrusted forest or domain Secure DMZ Workgroups Un-trusted domain 1 Port 433 Port 5723 Untrusted Domain Corporate Domain Trusted Domain Port 51909 Secure DMZ Work Groups

Deploying Forwarders With Powershell Two scripts on the CD Can be used to enable or disable ACS forwarder for multiple agents at once Example here: http: //contoso. se/blog/? p=433

ACS Enhancement in R 2 Support for Windows Server 2008 and Windows Server 2008 R 2 New Windows Server 2008 and Windows Server 2008 R 2 integrated ACS reports Improved report performance New multi-staged indexing design that further enhance robustness and performance Support for Cross Platform by CY 2 H 09

demo Out-of-the-box ACS functionality

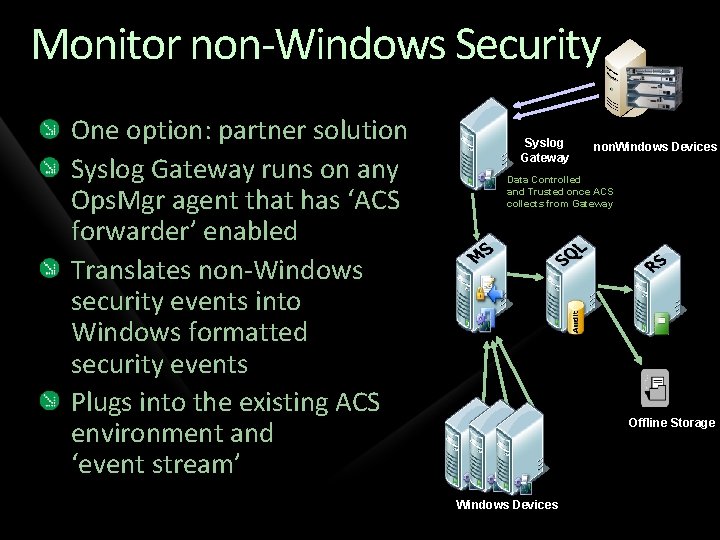
Monitor non-Windows Security One option: partner solution Syslog Gateway runs on any Ops. Mgr agent that has ‘ACS forwarder’ enabled Translates non-Windows security events into Windows formatted security events Plugs into the existing ACS environment and ‘event stream’ Syslog Gateway non. Windows Devices Data Controlled and Trusted once ACS collects from Gateway Offline Storage Windows Devices

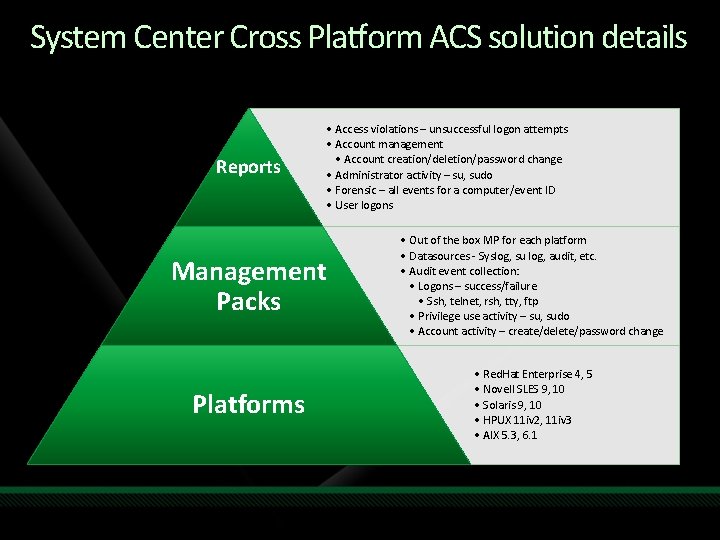
System Center Cross Platform ACS enablement Provide Audit Collection Services (ACS) for Unix and Linux systems • Leverage Ops. Mgr 2007 R 2 Cross Platform infrastructure to enable Unix/Linux auditing • Collect and aggregate audit events across enterprise systems for a singular view • Out of the box support for base OS audit events Reporting – base OS auditing reports • Access violations • Account management • Administrator activity Provide the infrastructure to enable enterprise auditing • Network devices • Applications Delivery • Out of band, dependent on Ops. Mgr 2007 R 2 • CY 2 H 09

System Center Cross Platform ACS solution details Reports • Access violations – unsuccessful logon attempts • Account management • Account creation/deletion/password change • Administrator activity – su, sudo • Forensic – all events for a computer/event ID • User logons Management Packs • Out of the box MP for each platform • Datasources - Syslog, su log, audit, etc. • Audit event collection: • Logons – success/failure • Ssh, telnet, rsh, tty, ftp • Privilege use activity – su, sudo • Account activity – create/delete/password change Platforms • Red. Hat Enterprise 4, 5 • Novell SLES 9, 10 • Solaris 9, 10 • HPUX 11 iv 2, 11 iv 3 • AIX 5. 3, 6. 1

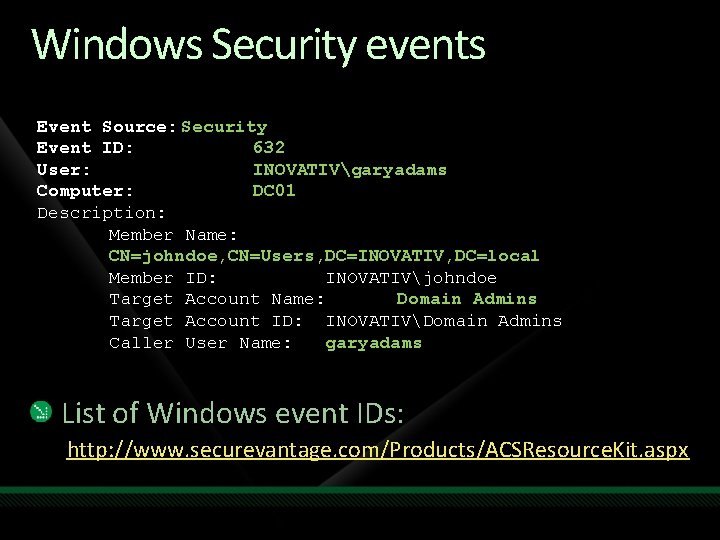
Windows Security events Event Source: Security Event ID: 632 User: INOVATIVgaryadams Computer: DC 01 Description: Member Name: CN=johndoe, CN=Users, DC=INOVATIV, DC=local Member ID: INOVATIVjohndoe Target Account Name: Domain Admins Target Account ID: INOVATIVDomain Admins Caller User Name: garyadams List of Windows event IDs: http: //www. securevantage. com/Products/ACSResource. Kit. aspx

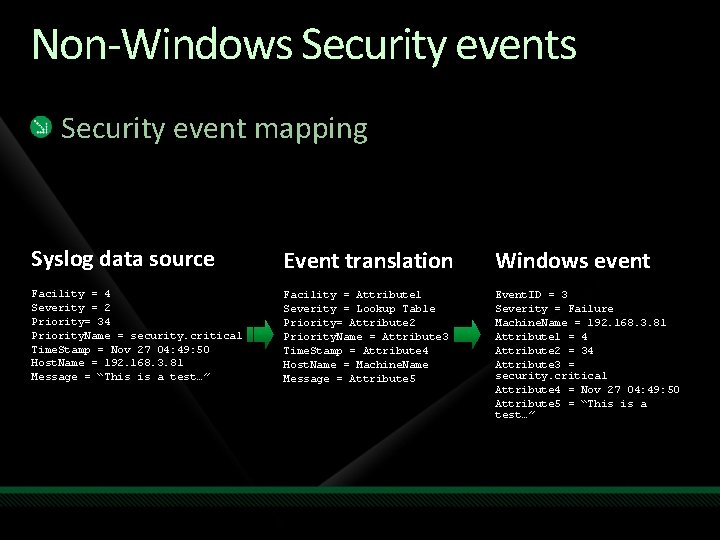
Non-Windows Security event mapping Syslog data source Event translation Windows event Facility = 4 Severity = 2 Priority= 34 Priority. Name = security. critical Time. Stamp = Nov 27 04: 49: 50 Host. Name = 192. 168. 3. 81 Message = “This is a test…” Facility = Attribute 1 Severity = Lookup Table Priority= Attribute 2 Priority. Name = Attribute 3 Time. Stamp = Attribute 4 Host. Name = Machine. Name Message = Attribute 5 Event. ID = 3 Severity = Failure Machine. Name = 192. 168. 3. 81 Attribute 1 = 4 Attribute 2 = 34 Attribute 3 = security. critical Attribute 4 = Nov 27 04: 49: 50 Attribute 5 = “This is a test…”

demo ACS and non-windows devices

Windows Management Instrumentation Available on the ACS collector Adt. Event WMI namespace Exposes key attributes to a collected security event Creation. Time Event. ID Event. Machine Primary. User String 01 -String[. . ] Use custom rules/monitors or powershell/vbscripts to query

demo Using ACS to alert real-time

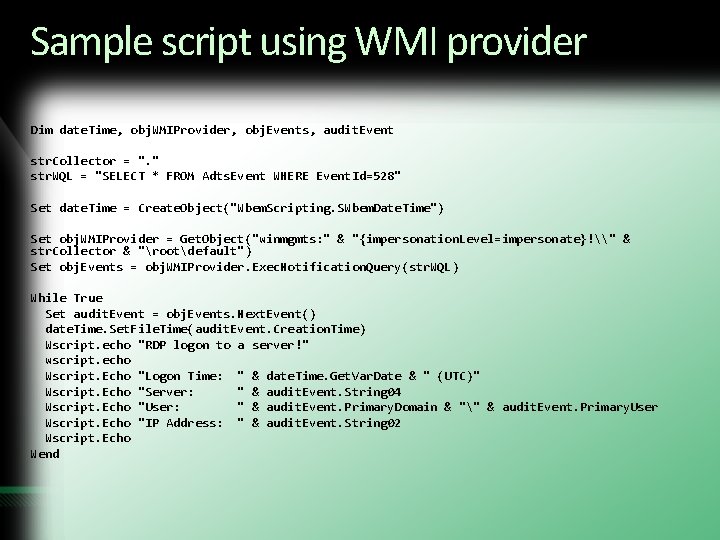
Sample script using WMI provider Dim date. Time, obj. WMIProvider, obj. Events, audit. Event str. Collector = ". " str. WQL = "SELECT * FROM Adts. Event WHERE Event. Id=528" Set date. Time = Create. Object("Wbem. Scripting. SWbem. Date. Time") Set obj. WMIProvider = Get. Object("winmgmts: " & "{impersonation. Level=impersonate}!\" & str. Collector & "rootdefault") Set obj. Events = obj. WMIProvider. Exec. Notification. Query(str. WQL) While True Set audit. Event = obj. Events. Next. Event() date. Time. Set. File. Time(audit. Event. Creation. Time) Wscript. echo "RDP logon to a server!" wscript. echo Wscript. Echo "Logon Time: " & date. Time. Get. Var. Date & " (UTC)" Wscript. Echo "Server: " & audit. Event. String 04 Wscript. Echo "User: " & audit. Event. Primary. Domain & "" & audit. Event. Primary. User Wscript. Echo "IP Address: " & audit. Event. String 02 Wscript. Echo Wend

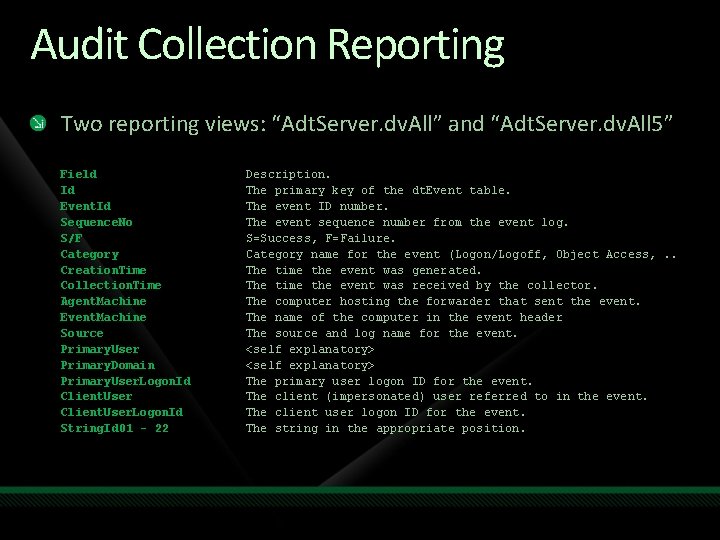
Audit Collection Reporting Two reporting views: “Adt. Server. dv. All” and “Adt. Server. dv. All 5” Field Id Event. Id Sequence. No S/F Category Creation. Time Collection. Time Agent. Machine Event. Machine Source Primary. User Primary. Domain Primary. User. Logon. Id Client. User. Logon. Id String. Id 01 - 22 Description. The primary key of the dt. Event table. The event ID number. The event sequence number from the event log. S=Success, F=Failure. Category name for the event (Logon/Logoff, Object Access, . . The time the event was generated. The time the event was received by the collector. The computer hosting the forwarder that sent the event. The name of the computer in the event header The source and log name for the event. <self explanatory> The primary user logon ID for the event. The client (impersonated) user referred to in the event. The client user logon ID for the event. The string in the appropriate position.

demo Authoring a custom ACS report

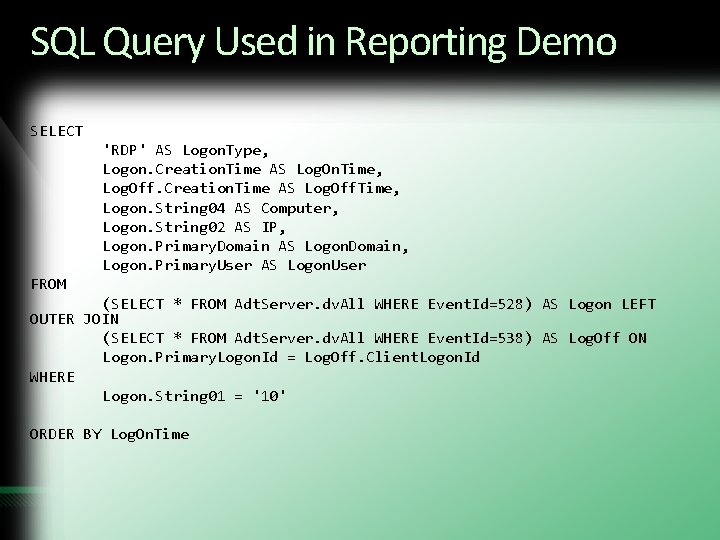
SQL Query Used in Reporting Demo SELECT 'RDP' AS Logon. Type, Logon. Creation. Time AS Log. On. Time, Log. Off. Creation. Time AS Log. Off. Time, Logon. String 04 AS Computer, Logon. String 02 AS IP, Logon. Primary. Domain AS Logon. Domain, Logon. Primary. User AS Logon. User FROM (SELECT * FROM Adt. Server. dv. All WHERE Event. Id=528) AS Logon LEFT OUTER JOIN (SELECT * FROM Adt. Server. dv. All WHERE Event. Id=538) AS Log. Off ON Logon. Primary. Logon. Id = Log. Off. Client. Logon. Id WHERE Logon. String 01 = '10' ORDER BY Log. On. Time

Extending the Functionality Create dashboards using the extensibility of the platform Service Level Dashboard v 2 Savision Live Maps Ops. Mgr solution accelerator for Visio (NEW) Use the objects delivered by Microsoft management packs or third party vendors to model your dashboard Easily provides a “security overview at a glance”

Extending the Functionality

demo Creating a security dashboard

Providing Access to Auditors Two parts to it Database Lock down the database with SQL permissions Create an AD global group for the auditors (and the collector account) Reports Change security permissions on the ACS-related folders/reports to only allow the AD global group to access them Step-by-step guide available

Tips and Tricks From the Field Monitor the integrity of the security system Plan SQL database rights Plan ACS collector ‘service account’ Create custom rules to. . report on (interactive) logins with the ACS collector ‘service account’ report on password changes of the ACS collector ‘service account’ report on AD group membership changes of ‘Auditors’ report on editing of SQL database rights report on disconnected or misconfigured ACS forwarders Your compliancy solution is only as strong as the weakest link

Tips and Tricks From the Field Use SQL enterprise Document every aspect of your ‘solution’ Collector ‘load’ will decrease when using “noise filters” Separate SQL reporting services server or not? Server configuration Use 64 -bit Use dedicated hardware / management server Plan your disks for the ACS database Use SQL enterprise edition (if SQL 2005) Use SCOM 2007 R 2 or apply hotfix 949969 and 954329 to SP 1

question & answer

More Information and Downloads Audit Collection Services on Technet http: //technet. microsoft. com/en-us/library/bb 381258(Tech. Net. 10). aspx Ops. Mgr 2007 Performance and Scalability Guide http: //download. microsoft. com/download/d/3/6/d 3633 fa 3 -ce 15 -4071 -be 51 -5 e 036 a 36 f 965/OM 2007_Perf. Scal. doc ACS Master Class Series http: //www. securevantage. com/ACSTraining. aspx ACS Resource Kit http: //www. securevantage. com/Products/ACSResource. Kit. aspx ACS focused blogs http: //www. techlog. org | http: //www. contoso. se | http: //blogs. inovativ. nl http: //www. systemcentercentral. com | http: //blogs. msdn. com/ericfitz/

Resources www. microsoft. com/teched www. microsoft. com/learning Sessions On-Demand & Community Microsoft Certification & Training Resources http: //microsoft. com/technet http: //microsoft. com/msdn Resources for IT Professionals Resources for Developers www. microsoft. com/learning Microsoft Certification and Training Resources

Track Resources Key Microsoft Sites System Center on Microsoft. com: http: //www. microsoft. com/systemcenter System Center on Tech. Net: http: //technet. microsoft. com/systemcenter/ Virtualization on Microsoft. com: http: //www. microsoft. com/virtualization Community Resources System Center Team Blog: http: //blogs. technet. com/systemcenter System Center Central: http: //www. systemcentercentral. com System Center Community: http: //www. my. ITforum. com System Center on Tech. Net Edge: http: //edge. technet. com/systemcenter System Center on Twitter: http: //twitter. com/system_center Virtualization Feed: http: //www. virtualizationfeed. com System Center Influencers Program: Content, connections, and resources for influencers in the System Center Community. For information, contact scnetsup@microsoft. com

Complete an evaluation on Comm. Net and enter to win!

© 2009 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.